| download: | /vir/Email-Worm.Win32.Sobig.c |
| Full analysis: | https://app.any.run/tasks/a4b59ea8-d061-4d4a-a3bb-a9a6ea9712db |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2024, 19:27:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 6FFABB00D059B6C4656EA20948AB42BE |
| SHA1: | 00B82AC93BB0A0A9193FD22984B751EF0CD01817 |
| SHA256: | 50AA3D1B780554CF6353C9D67B1338F45978270942FDEA0BC2A1C6E31D4F158C |
| SSDEEP: | 1536:7iJNuXejwUFdb/hpB/tGJZgRnEC66OeN5sM:mvwejwU/ZIJZgBEBeNL |
MALICIOUS
Changes the autorun value in the registry
- Email-Worm.Win32.Sobig.c.exe (PID: 2076)
SUSPICIOUS
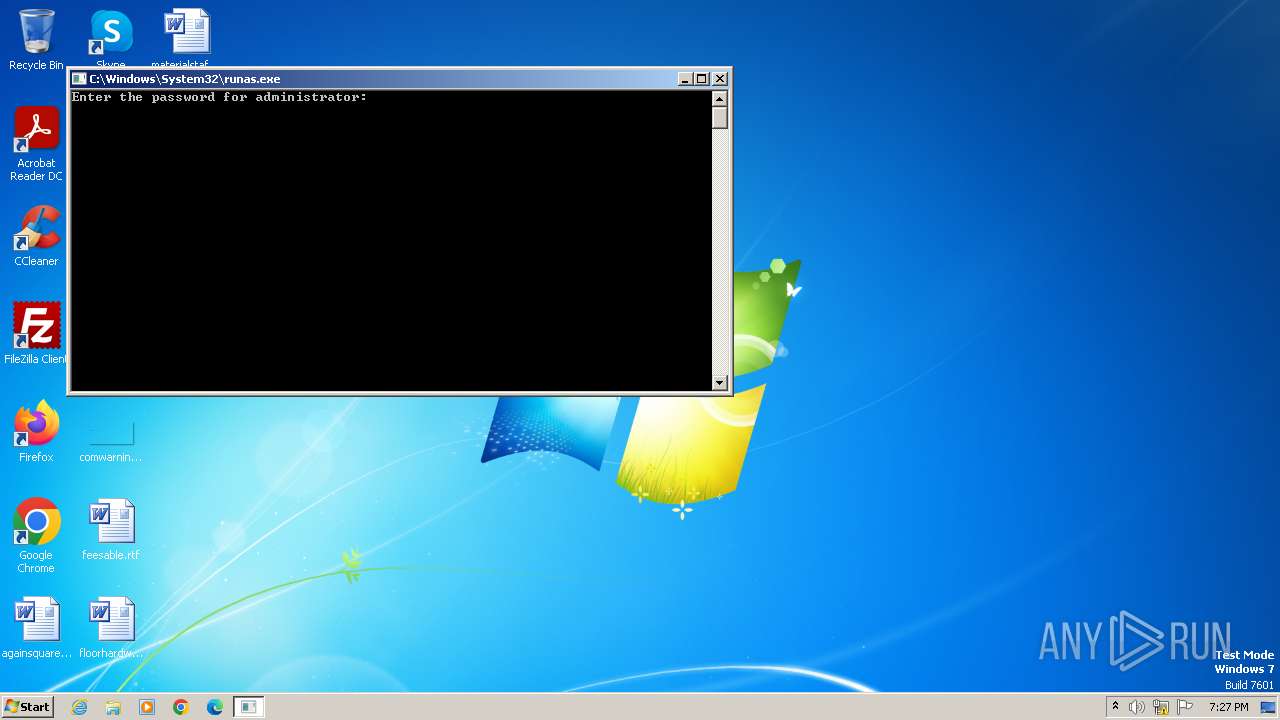
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 1040)
Starts itself from another location
- Email-Worm.Win32.Sobig.c.exe (PID: 2076)
Executable content was dropped or overwritten
- Email-Worm.Win32.Sobig.c.exe (PID: 2076)
INFO
Reads the computer name
- mscvb32.exe (PID: 2260)
- wmpnscfg.exe (PID: 2280)
Checks supported languages
- Email-Worm.Win32.Sobig.c.exe (PID: 2076)
- mscvb32.exe (PID: 2260)
- wmpnscfg.exe (PID: 2280)
Manual execution by a user
- wmpnscfg.exe (PID: 2280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE Yoda's Crypter (63.7) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.7) |
| .exe | | | Win32 Executable (generic) (10.8) |
| .exe | | | Generic Win/DOS Executable (4.8) |
| .exe | | | DOS Executable Generic (4.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2003:05:30 17:22:12+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 57344 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 69632 |
| EntryPoint: | 0x1f2d0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1040 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\Email-Worm.Win32.Sobig.c.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2076 | C:\Users\admin\Desktop\Email-Worm.Win32.Sobig.c.exe | C:\Users\admin\Desktop\Email-Worm.Win32.Sobig.c.exe | runas.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2260 | C:\Windows\mscvb32.exe dwaqr | C:\Windows\mscvb32.exe | Email-Worm.Win32.Sobig.c.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Modules
| |||||||||||||||
| 2280 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
207
Read events
205
Write events
2
Delete events
0
Modification events
| (PID) Process: | (2076) Email-Worm.Win32.Sobig.c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | System MScvb |
Value: C:\Windows\mscvb32.exe | |||
| (PID) Process: | (2076) Email-Worm.Win32.Sobig.c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | System MScvb |
Value: C:\Windows\mscvb32.exe | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2076 | Email-Worm.Win32.Sobig.c.exe | C:\Windows\mscvb32.exe | executable | |
MD5:6FFABB00D059B6C4656EA20948AB42BE | SHA256:50AA3D1B780554CF6353C9D67B1338F45978270942FDEA0BC2A1C6E31D4F158C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2260 | mscvb32.exe | 129.132.2.21:123 | — | — | — | unknown |
2260 | mscvb32.exe | 138.96.64.10:123 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
A.ROOT-SERVERS.NET |
| unknown |