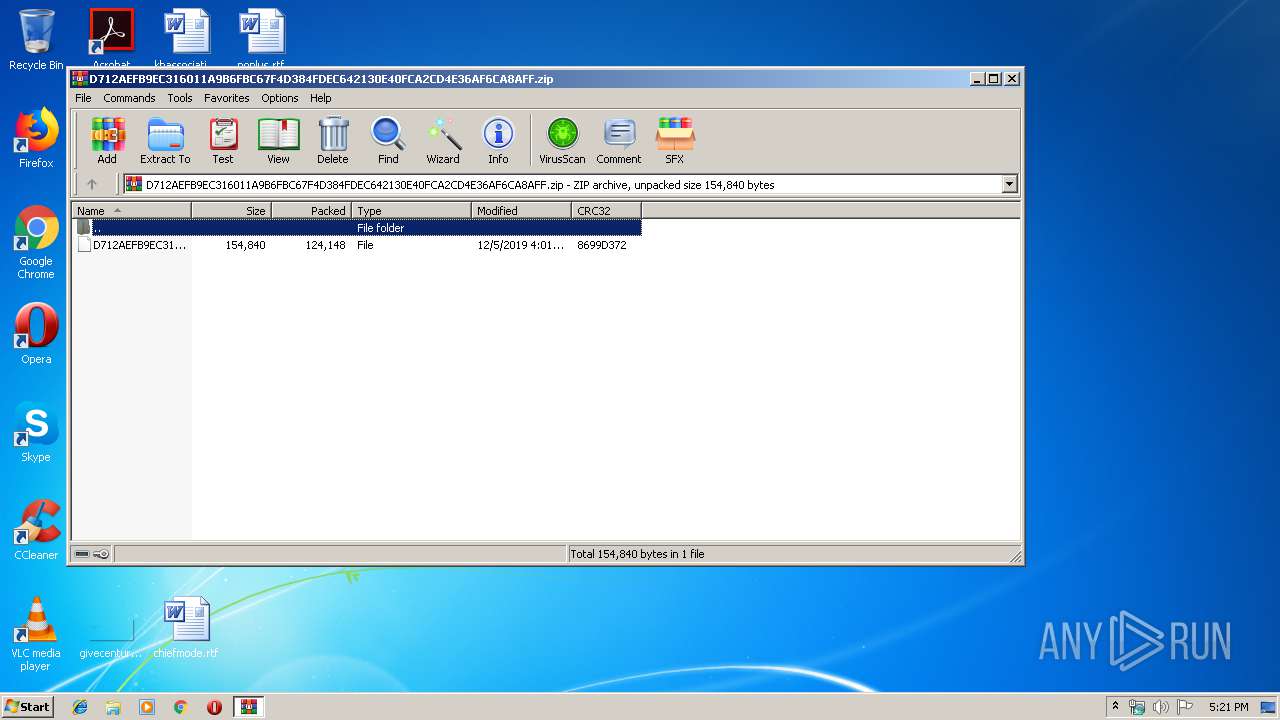
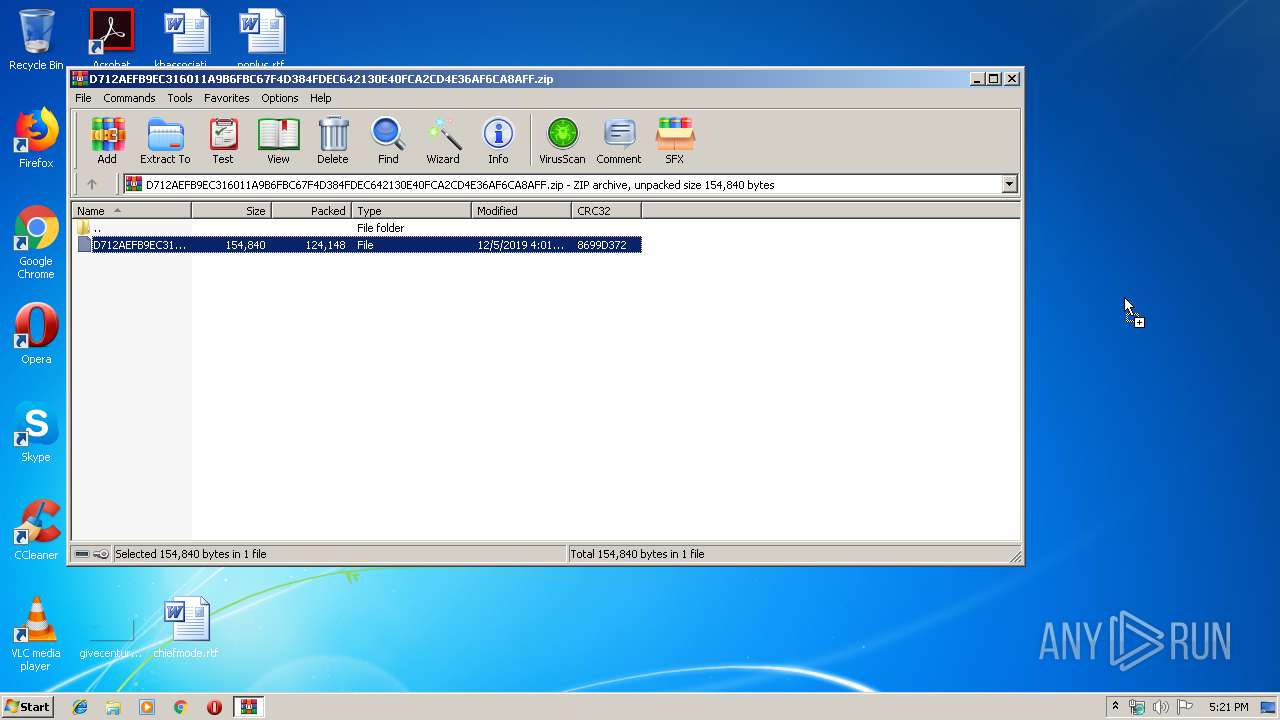
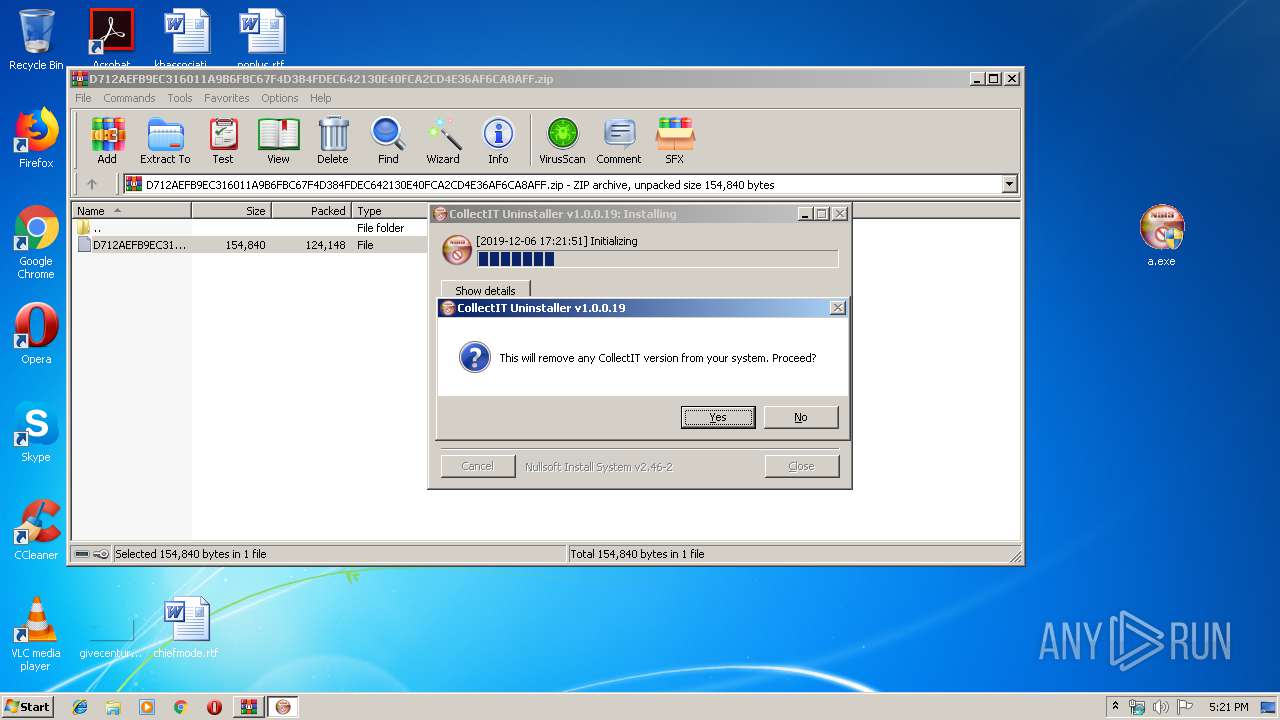
| File name: | D712AEFB9EC316011A9B6FBC67F4D384FDEC642130E40FCA2CD4E36AF6CA8AFF.zip |
| Full analysis: | https://app.any.run/tasks/38631b1d-944d-4943-b7d4-b133bb93cb7e |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2019, 17:21:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 77BA92DE34A00EF4EFFF23B6FD5DC947 |
| SHA1: | AAF5F33AB5BE3009F8B3F9E25E6E86595B605058 |
| SHA256: | 509902774D4D01C3CAB5E000FE8F5D3777BC67154D6AFE7911B62E21DCB241D2 |
| SSDEEP: | 3072:jMLvxG1AARC9pYEJxk+O1xoZCa/mqnYa2JEojOEVjWSZerA:ivx6lRCkEJgxBcnBojOYjNAA |
MALICIOUS
Application was dropped or rewritten from another process
- a.exe (PID: 2480)
- a.exe (PID: 3860)
- ns17C6.tmp (PID: 2456)
- ns167D.tmp (PID: 3316)
Loads dropped or rewritten executable
- a.exe (PID: 3860)
SUSPICIOUS
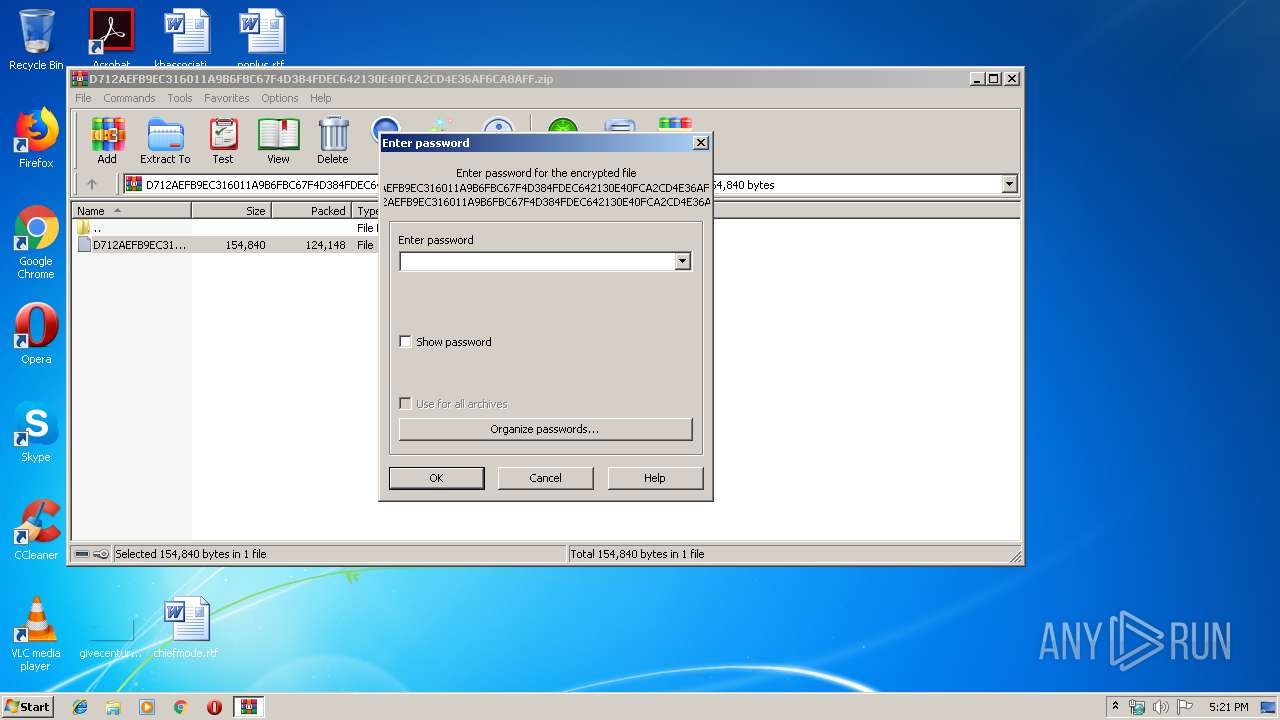
Executable content was dropped or overwritten
- a.exe (PID: 3860)
- WinRAR.exe (PID: 592)
Starts application with an unusual extension
- a.exe (PID: 3860)
INFO
Manual execution by user
- a.exe (PID: 3860)
- a.exe (PID: 2480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:12:05 16:01:14 |
| ZipCRC: | 0x8699d372 |
| ZipCompressedSize: | 124148 |
| ZipUncompressedSize: | 154840 |
| ZipFileName: | D712AEFB9EC316011A9B6FBC67F4D384FDEC642130E40FCA2CD4E36AF6CA8AFF |
Total processes
49
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 592 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\D712AEFB9EC316011A9B6FBC67F4D384FDEC642130E40FCA2CD4E36AF6CA8AFF.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1740 | C:\Windows\system32\net1 helpmsg 1060 | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2112 | C:\Windows\system32\net1 helpmsg 1060 | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
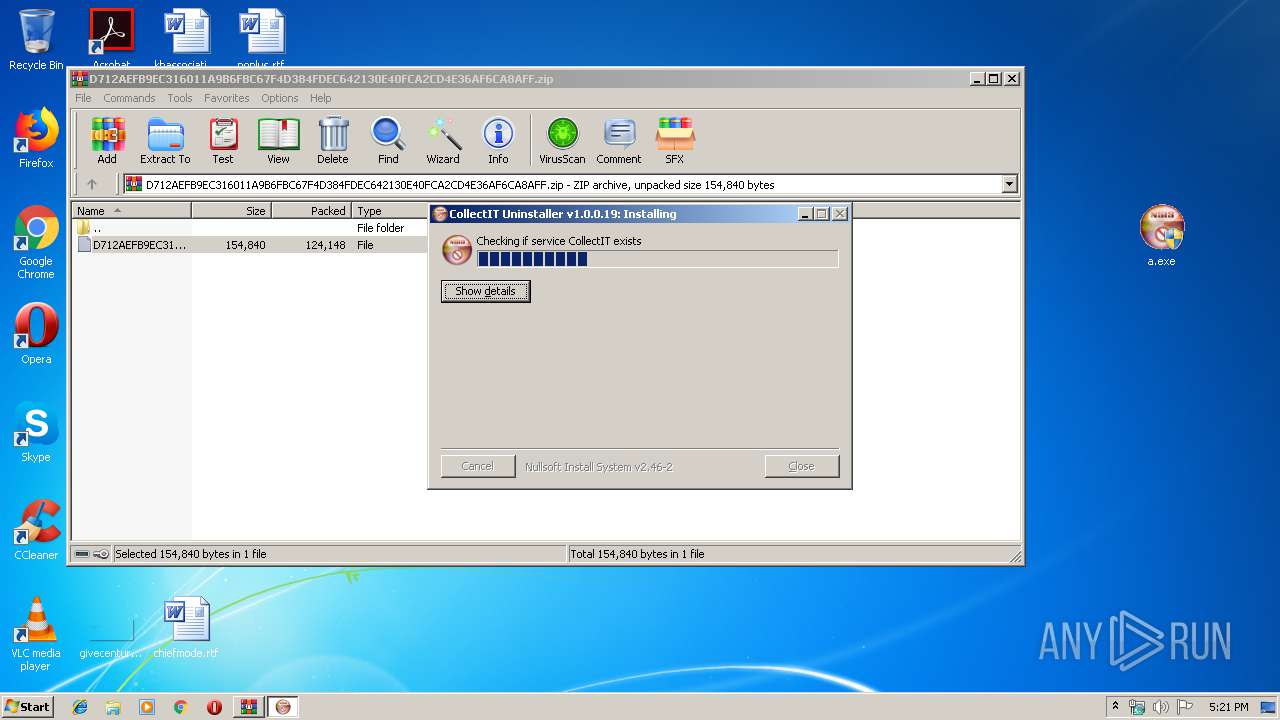
| 2388 | net helpmsg 1060 | C:\Windows\system32\net.exe | — | ns167D.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2456 | "C:\Users\admin\AppData\Local\Temp\nsv650.tmp\ns17C6.tmp" net helpmsg 1060 | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\ns17C6.tmp | — | a.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
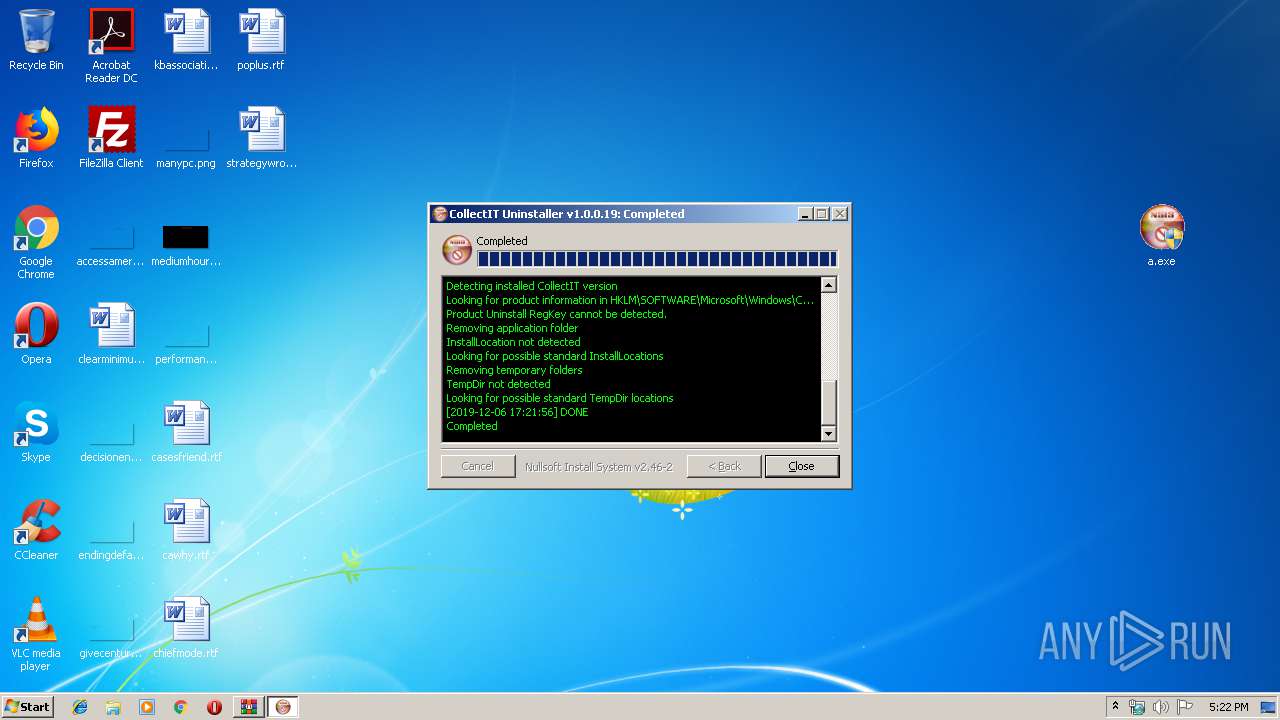
| 2480 | "C:\Users\admin\Desktop\a.exe" | C:\Users\admin\Desktop\a.exe | — | explorer.exe | |||||||||||
User: admin Company: SoftWatch Integrity Level: MEDIUM Description: CollectIT Uninstaller Exit code: 3221226540 Version: 1.0.0.19 Modules
| |||||||||||||||
| 3316 | "C:\Users\admin\AppData\Local\Temp\nsv650.tmp\ns167D.tmp" net helpmsg 1060 | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\ns167D.tmp | — | a.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3856 | net helpmsg 1060 | C:\Windows\system32\net.exe | — | ns17C6.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
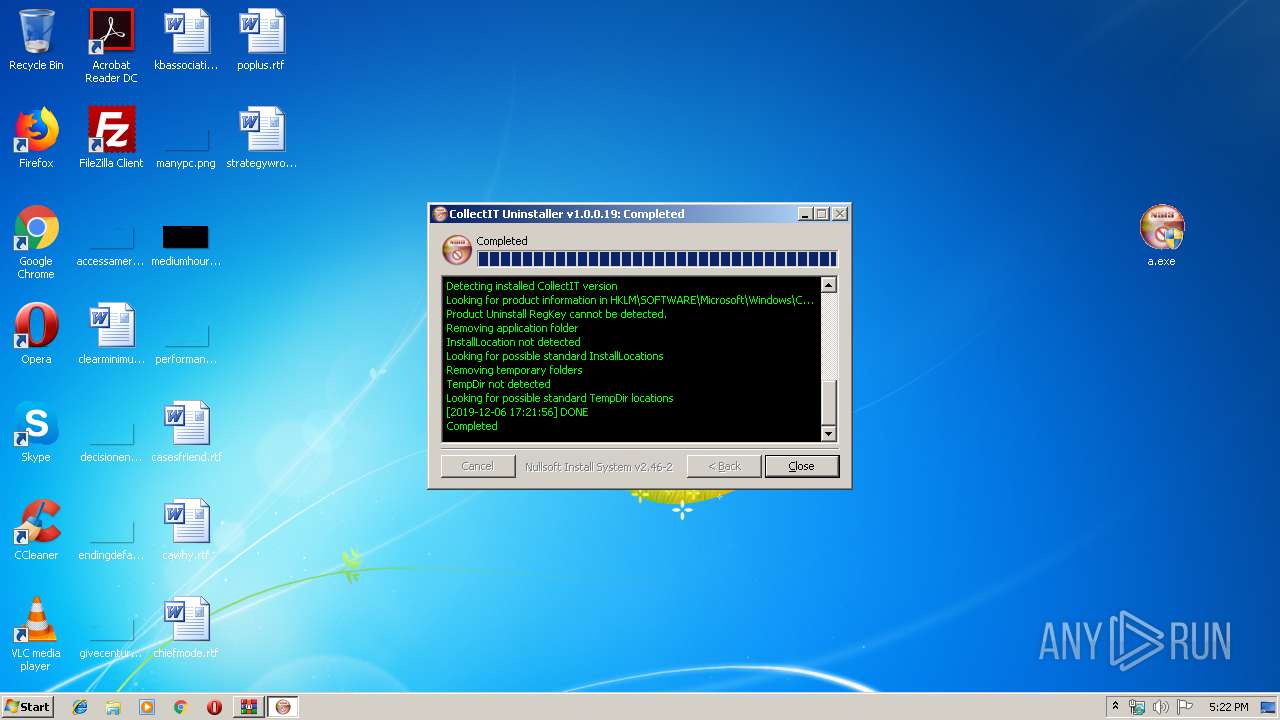
| 3860 | "C:\Users\admin\Desktop\a.exe" | C:\Users\admin\Desktop\a.exe | explorer.exe | ||||||||||||
User: admin Company: SoftWatch Integrity Level: HIGH Description: CollectIT Uninstaller Exit code: 0 Version: 1.0.0.19 Modules
| |||||||||||||||
Total events
449
Read events
440
Write events
9
Delete events
0
Modification events
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\D712AEFB9EC316011A9B6FBC67F4D384FDEC642130E40FCA2CD4E36AF6CA8AFF.zip | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
7
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3860 | a.exe | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\ns167D.tmp | — | |
MD5:— | SHA256:— | |||
| 3860 | a.exe | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\UserInfo.dll | executable | |
MD5:3B6CF5CEA952E974F0575BF9D0C67149 | SHA256:CC2F27DFDA0EBF7DF9E6F756108D31304E8DDCC17A6F30D6B803A57C3C1A967B | |||
| 3860 | a.exe | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\nsExec.dll | executable | |
MD5:E20748AC10DD71384DA1B32CEA317EF9 | SHA256:D974FE15381B03E72FB2E8E72322304220AD795E3916F6F91C01996FD75C0AAA | |||
| 592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb592.39997\D712AEFB9EC316011A9B6FBC67F4D384FDEC642130E40FCA2CD4E36AF6CA8AFF | executable | |
MD5:B0624FAC93F75504974C61A0F05C49FF | SHA256:D712AEFB9EC316011A9B6FBC67F4D384FDEC642130E40FCA2CD4E36AF6CA8AFF | |||
| 3860 | a.exe | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\FindProcDLL.dll | executable | |
MD5:8614C450637267AFACAD1645E23BA24A | SHA256:0FA04F06A6DE18D316832086891E9C23AE606D7784D5D5676385839B21CA2758 | |||
| 3860 | a.exe | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\ns17C6.tmp | executable | |
MD5:— | SHA256:— | |||
| 3860 | a.exe | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\SimpleSC.dll | executable | |
MD5:D63975CE28F801F236C4ACA5AF726961 | SHA256:E0C580BBE48A483075C21277C6E0F23F3CBD6CE3EB2CCD3BF48CF68F05628F43 | |||
| 3860 | a.exe | C:\Users\admin\AppData\Local\Temp\nsv650.tmp\System.dll | executable | |
MD5:991D09235944414AE51BE4DD7611F7F7 | SHA256:D6C484987DEE670450E73105DB9FE59F0DA272504461B39ED50B61CDE0D8E26F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report