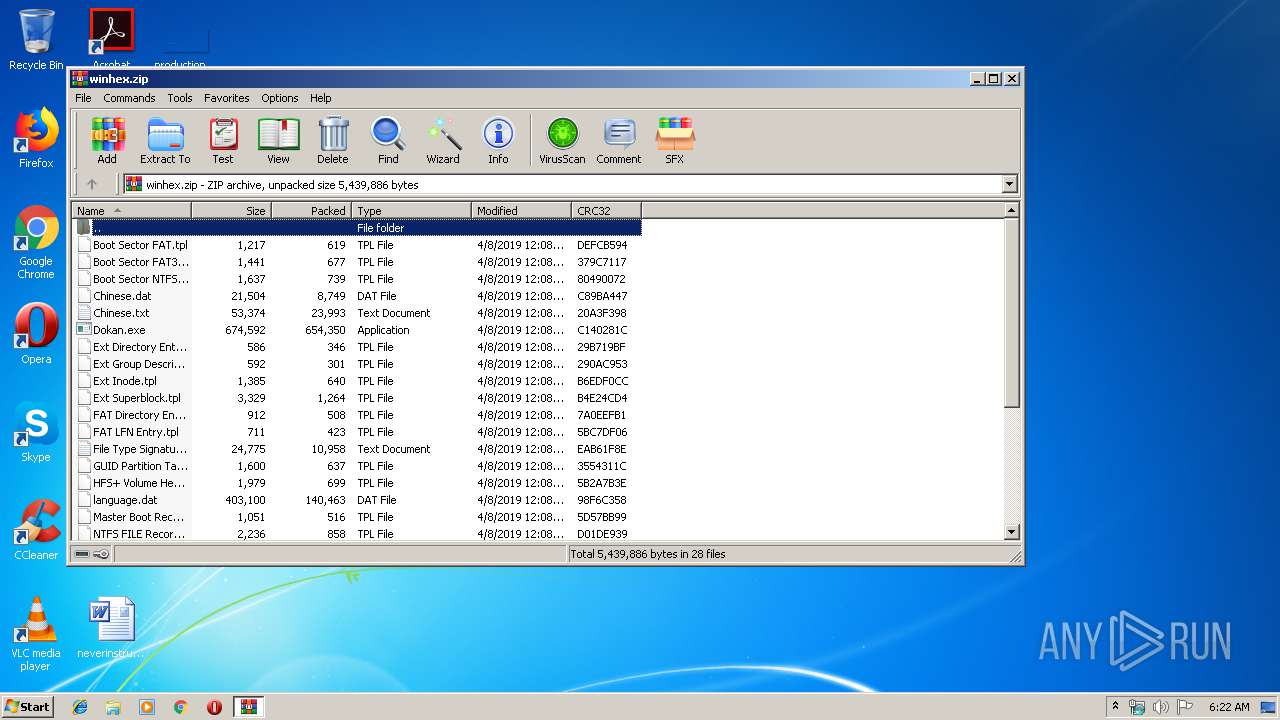
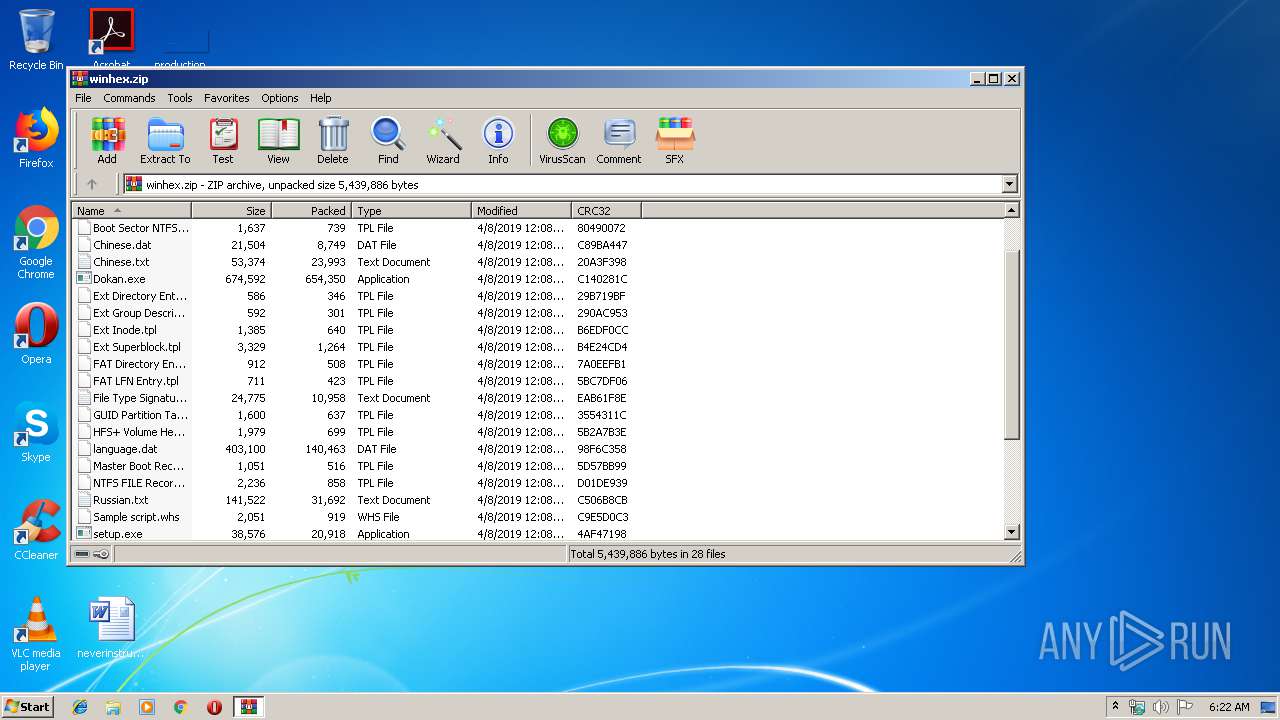
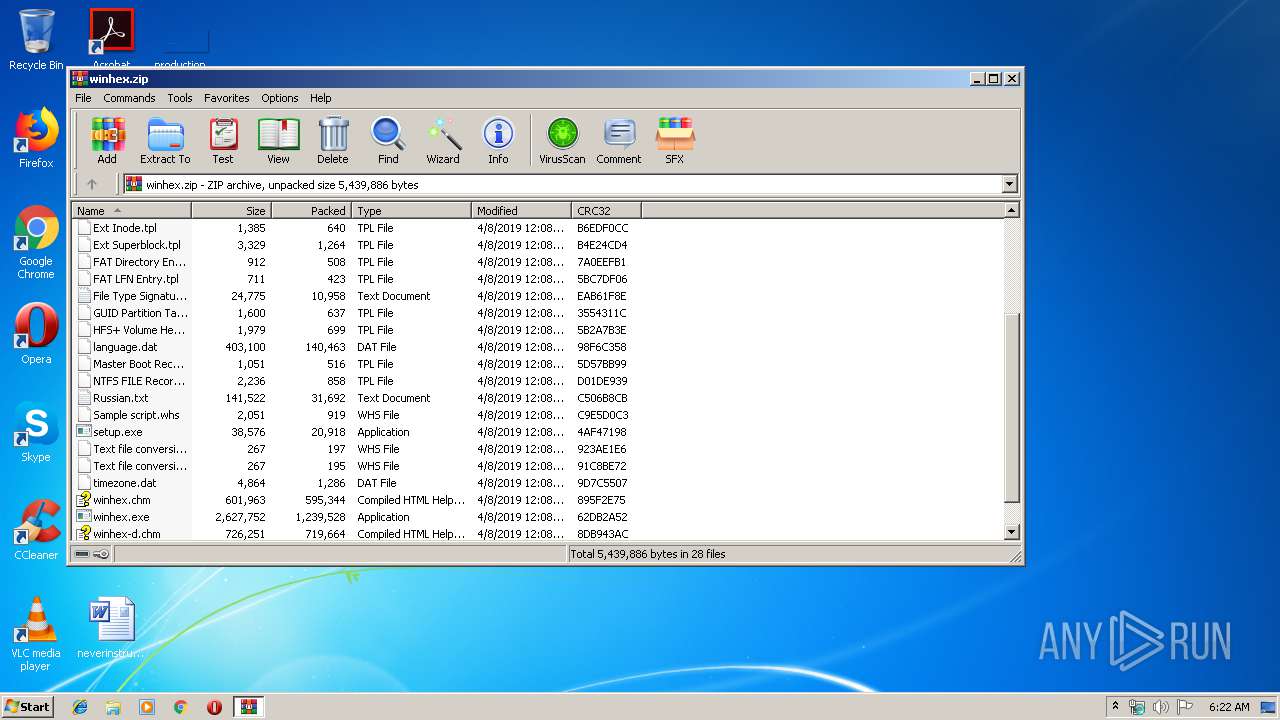
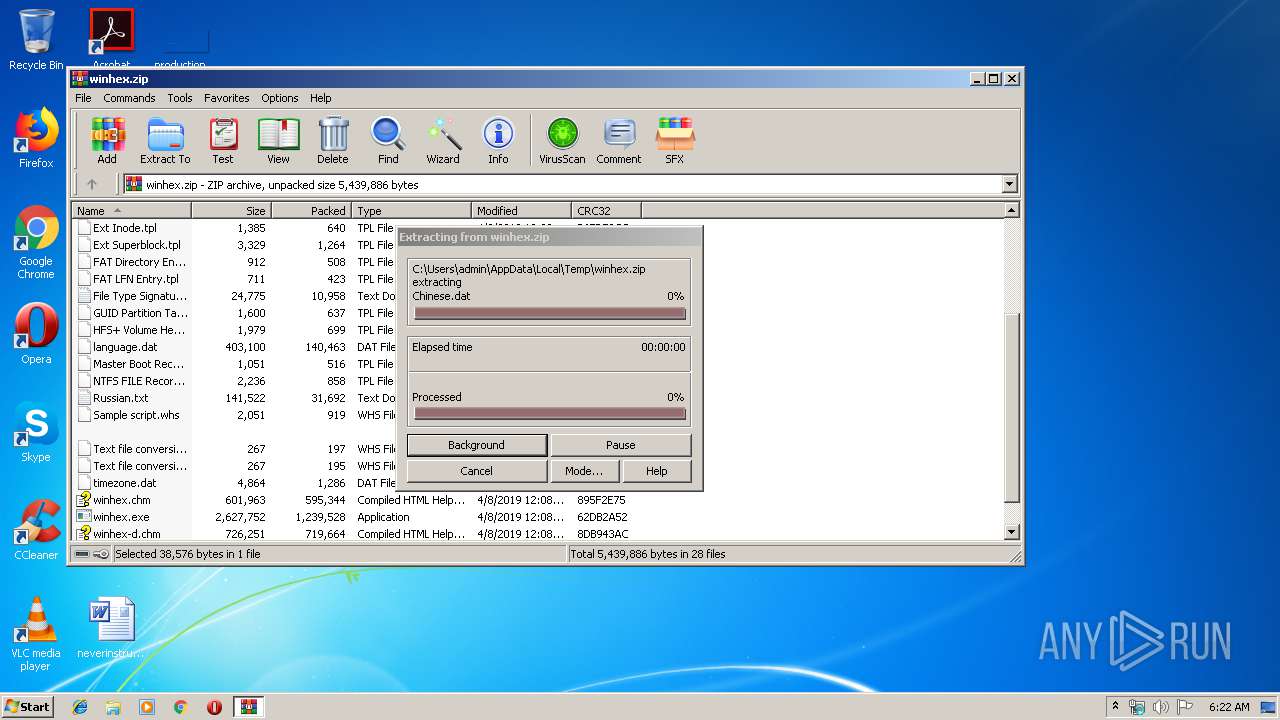
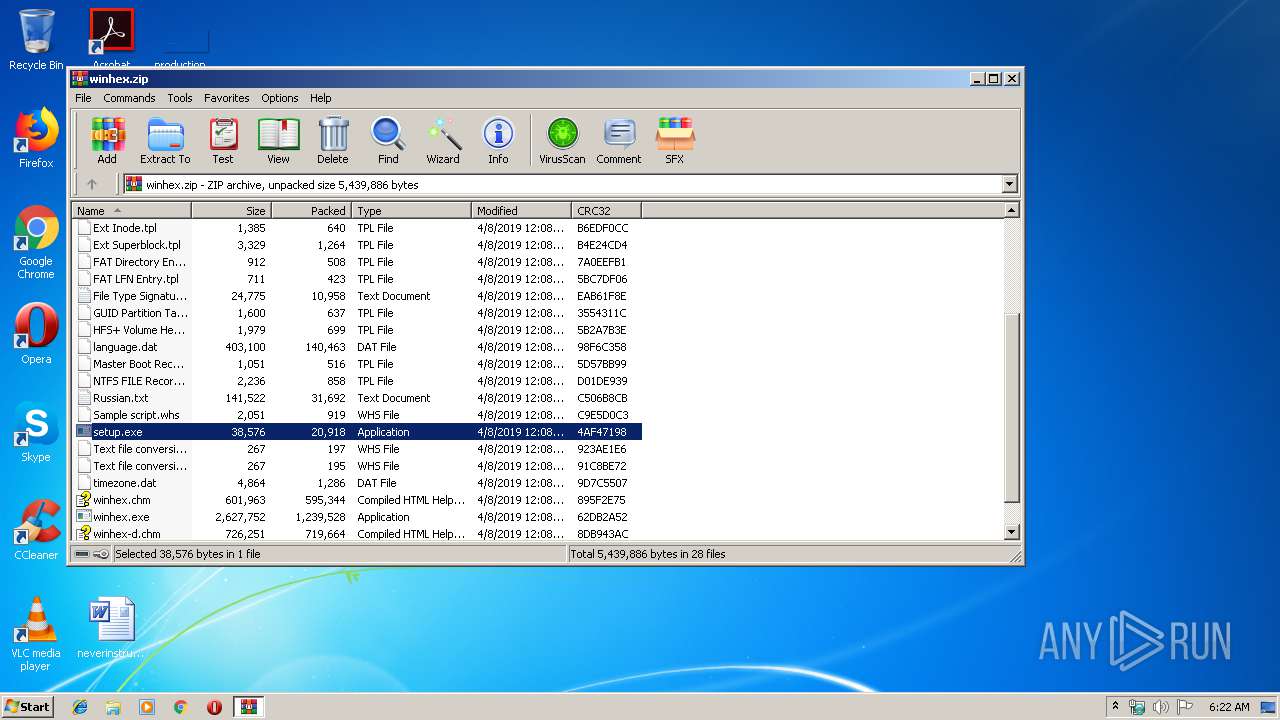
| File name: | winhex.zip |
| Full analysis: | https://app.any.run/tasks/95480ccd-918e-41e4-8d19-cd879b2fe41d |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 05:22:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 61A9A0C13391476C5F23C456F86BFBA9 |
| SHA1: | F670EAC27209A469BD836B00921FDC51631B021F |
| SHA256: | 5077181BE75D19FED2F2F8E55B7D50A603F9C561FCD9C55BF6141F0DDEB364D6 |
| SSDEEP: | 49152:N0KRPwJnykbmiFFt5U6HpUB6ihqGhJ3e4Aoz/OjgX/QF90bNnYdwfyShrz:NxRoxyNiFFt5JHCk0qGhZZOsINyyw |
MALICIOUS
Application was dropped or rewritten from another process
- setup.exe (PID: 3172)
- setup.exe (PID: 3168)
- WinHex.exe (PID: 3200)
Loads dropped or rewritten executable
- WinHex.exe (PID: 3200)
Changes settings of System certificates
- WinHex.exe (PID: 3200)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3004)
- setup.exe (PID: 3168)
Creates a software uninstall entry
- setup.exe (PID: 3168)
Creates files in the program directory
- setup.exe (PID: 3168)
Modifies the open verb of a shell class
- WinHex.exe (PID: 3200)
Adds / modifies Windows certificates
- WinHex.exe (PID: 3200)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:04:08 19:08:01 |
| ZipCRC: | 0xdefcb594 |
| ZipCompressedSize: | 619 |
| ZipUncompressedSize: | 1217 |
| ZipFileName: | Boot Sector FAT.tpl |
Total processes
37
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3004 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\winhex.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3168 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: X-Ways Software Technology AG Integrity Level: HIGH Description: X-Ways setup program Exit code: 0 Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\setup.exe | — | WinRAR.exe | |||||||||||
User: admin Company: X-Ways Software Technology AG Integrity Level: MEDIUM Description: X-Ways setup program Exit code: 3221226540 Modules
| |||||||||||||||
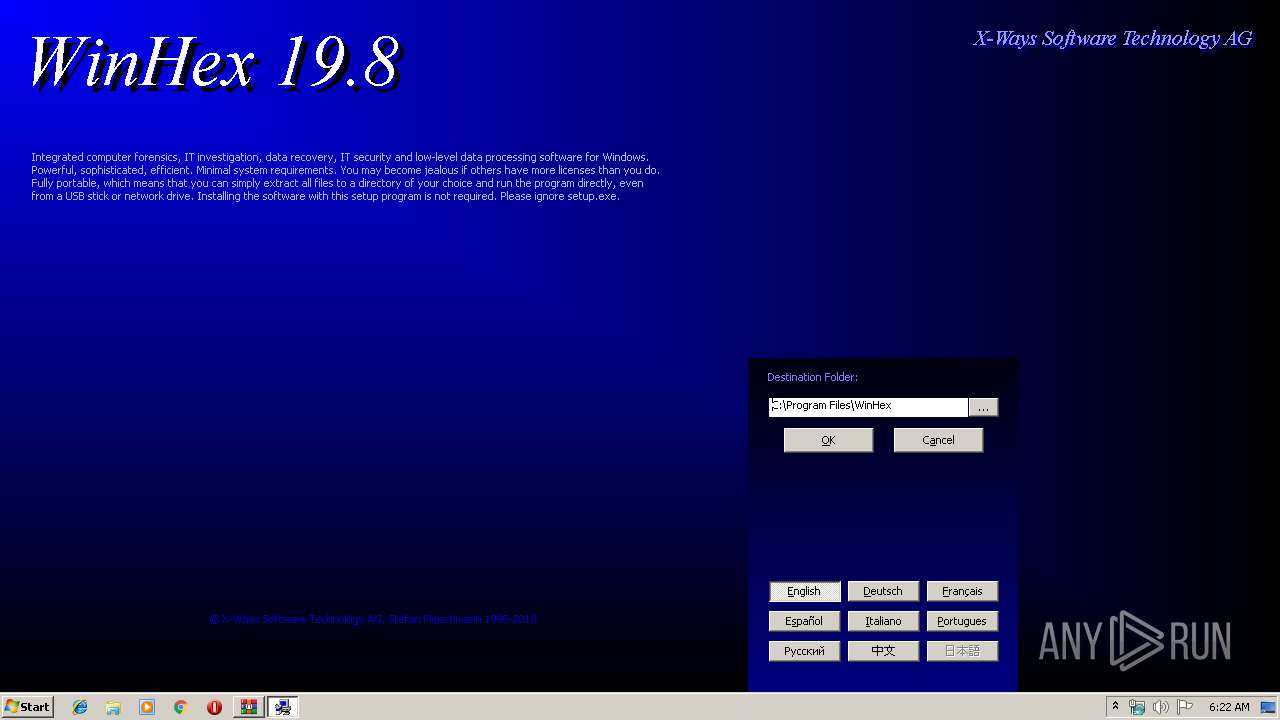
| 3200 | "C:\Program Files\WinHex\WinHex.exe" | C:\Program Files\WinHex\WinHex.exe | setup.exe | ||||||||||||
User: admin Company: X-Ways Software Technology AG Integrity Level: HIGH Description: WinHex Exit code: 0 Version: 19.8 Modules
| |||||||||||||||
Total events
650
Read events
605
Write events
45
Delete events
0
Modification events
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\winhex.zip | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\hhctrl.ocx,-452 |
Value: Compiled HTML Help file | |||
Executable files
10
Suspicious files
4
Text files
38
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Boot Sector NTFS.tpl | text | |
MD5:FA31D4E4FC767BDA92DD25734629445C | SHA256:C221D32E6360DFFE0272DDF5411C853CE7F056CCE10E955AB589AFC2FCD784FC | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Chinese.dat | executable | |
MD5:833AB5B37FEBB906DBFA095B8793D46E | SHA256:BF96BCD2180B7D5F1C5C50D1F3D146160B8A1AD642C0049C8CF283EC5BF1A172 | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Boot Sector FAT32.tpl | text | |
MD5:42B5387BE8B65CC1AE1FD77A3FA7C1D9 | SHA256:6A7DF566070F7CE6D1778C9932B231E2916AE7E7F26EB009378B6A8DB9D169A8 | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Ext Group Descriptor.tpl | text | |
MD5:FF950548020E68C9ECC737959623D163 | SHA256:1705EDF4117C3C3DFBAE8F76D268437EC27FF8AD2AC7FC4DD4C8616FBB7825E1 | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Ext Directory Entry.tpl | text | |
MD5:7D02E2EE25C47B445BC99777DD279A2C | SHA256:2B23038AF1DF80B7F404AE0C3E03DFA3DECE95185EE1275D1BE7E5533FA60A42 | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Russian.txt | text | |
MD5:— | SHA256:— | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\language.dat | binary | |
MD5:— | SHA256:— | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Chinese.txt | text | |
MD5:CB1C4125F7A7C8201C3B2DA95D57D907 | SHA256:99581218C7B2D23AE939B23C9214FF37E4EB835458060E8C5269CC19CFF82DD6 | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\Ext Inode.tpl | text | |
MD5:1D289762E99B093DF7F9CD6290EC997C | SHA256:3BF09A19E830F142AD19525479EE25A1595D1343FC45368975A1435EA9885CBA | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3004.26820\NTFS FILE Record.tpl | text | |
MD5:C93FD6F1834ABEE78A70A5BEB584D754 | SHA256:6ECF91001A559202201F8BA1F59FE39140772E5B3C0F7DB500EF9240549A4F21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3200 | WinHex.exe | 172.217.16.163:443 | google.de | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.de |
| whitelisted |