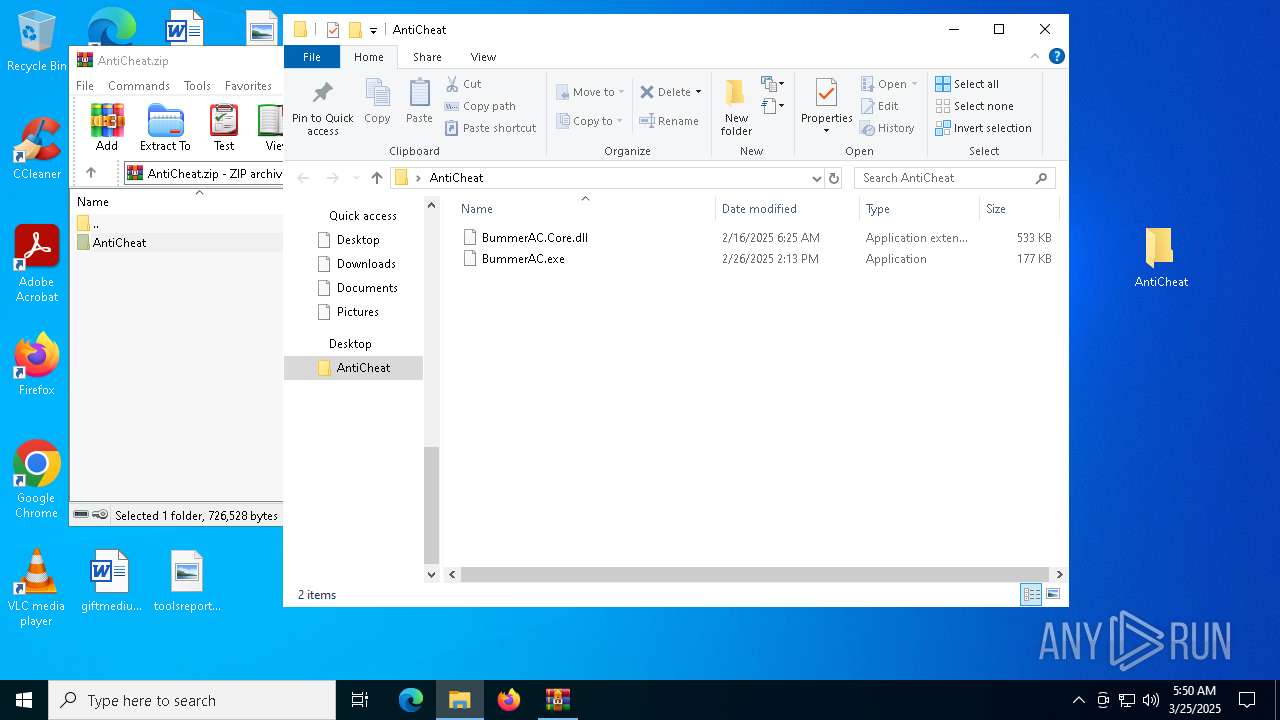
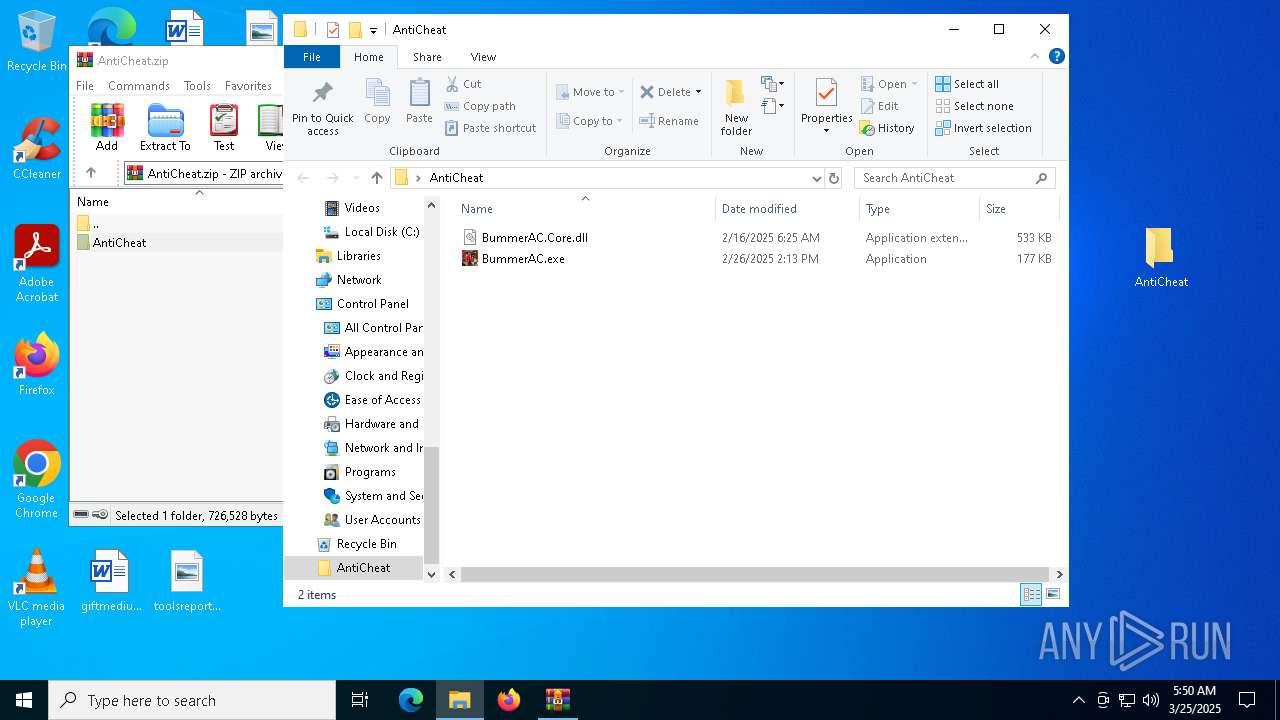
| File name: | AntiCheat.zip |
| Full analysis: | https://app.any.run/tasks/9d1e8ef9-f083-4059-928d-253cad575995 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 05:50:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 51A716BCEEC898BFFCE561DBE8263DA7 |
| SHA1: | 00289892A19D0725A4C336A80486DC045F40F8FF |
| SHA256: | 5068037850346B4111E22D6A3BCC376FD55B2A5ECE8FF87DDB75B0E31A19B258 |
| SSDEEP: | 24576:90GpAbvDrGPIVniYYdJwN0O5xEtlrB5YEzs3iz5tT2f35T6wk/gr95MHuT54bK:90GpAbvXGAVniYYdJwN0O5xulrB5rzs3 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4776)
Changes Windows Defender settings
- BummerAC.exe (PID: 5064)
- BummerAC.exe (PID: 6156)
Adds path to the Windows Defender exclusion list
- BummerAC.exe (PID: 5064)
- BummerAC.exe (PID: 6156)
SUSPICIOUS
Script adds exclusion path to Windows Defender
- BummerAC.exe (PID: 5064)
- BummerAC.exe (PID: 6156)
Starts POWERSHELL.EXE for commands execution
- BummerAC.exe (PID: 5064)
- BummerAC.exe (PID: 6156)
INFO
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 4448)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4776)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 4448)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 904)
- BackgroundTransferHost.exe (PID: 4448)
- BackgroundTransferHost.exe (PID: 5984)
- BackgroundTransferHost.exe (PID: 5508)
- notepad.exe (PID: 1280)
- Taskmgr.exe (PID: 1760)
Manual execution by a user
- BummerAC.exe (PID: 5064)
- BummerAC.exe (PID: 1328)
- notepad.exe (PID: 1280)
- Taskmgr.exe (PID: 6516)
- Taskmgr.exe (PID: 1760)
- BummerAC.exe (PID: 5228)
- BummerAC.exe (PID: 6156)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 4448)
Checks supported languages
- BummerAC.exe (PID: 5064)
- ShellExperienceHost.exe (PID: 5416)
Reads the computer name
- BummerAC.exe (PID: 5064)
- ShellExperienceHost.exe (PID: 5416)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 976)
- powershell.exe (PID: 3180)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 976)
- powershell.exe (PID: 3180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:16 06:25:06 |
| ZipCRC: | 0x935b0e50 |
| ZipCompressedSize: | 500996 |
| ZipUncompressedSize: | 545280 |
| ZipFileName: | AntiCheat/BummerAC.Core.dll |
Total processes
158
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | "powershell.exe" -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | BummerAC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
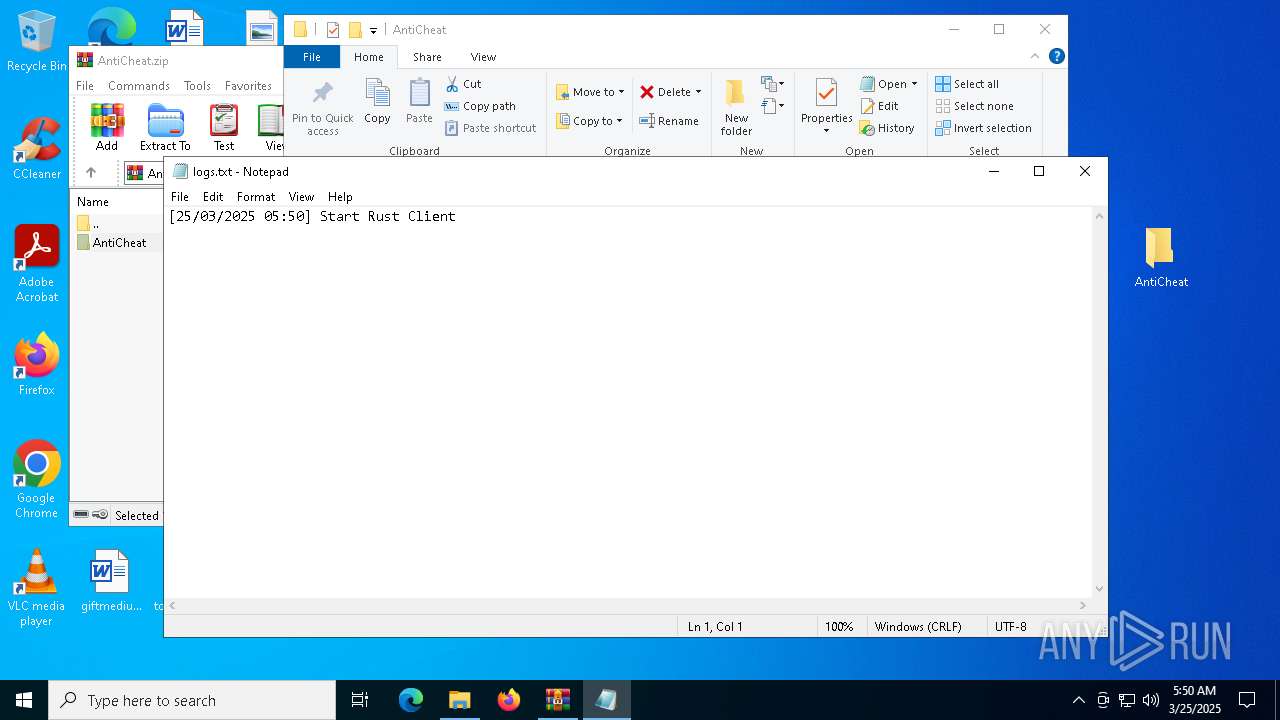
| 1280 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\AntiCheat\logs.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Users\admin\Desktop\AntiCheat\BummerAC.exe" | C:\Users\admin\Desktop\AntiCheat\BummerAC.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BummerAC Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1760 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | "powershell.exe" -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | BummerAC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\AntiCheat.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
16 276
Read events
16 251
Write events
24
Delete events
1
Modification events
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AntiCheat.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5508) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5508) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
2
Suspicious files
6
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4448 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\89496350-c85b-40d9-b84c-dbe16a9c1b1b.down_data | — | |
MD5:— | SHA256:— | |||
| 4776 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4776.14740\AntiCheat\BummerAC.Core.dll | executable | |
MD5:C3393D7EA27D828AF430054AA3ED29BC | SHA256:65CAD4E37CA3DE8F91DBAC2B4C8F11A680E19C3C5EFC4B603D657664A3AA335A | |||
| 4448 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 4448 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:A946EB079B134AF5E1F99DE1D8956D66 | SHA256:C556E188A8EFEEE27D20FC82CE9F33FCEA231823C24F35D9FA085D4FE6FB71A2 | |||
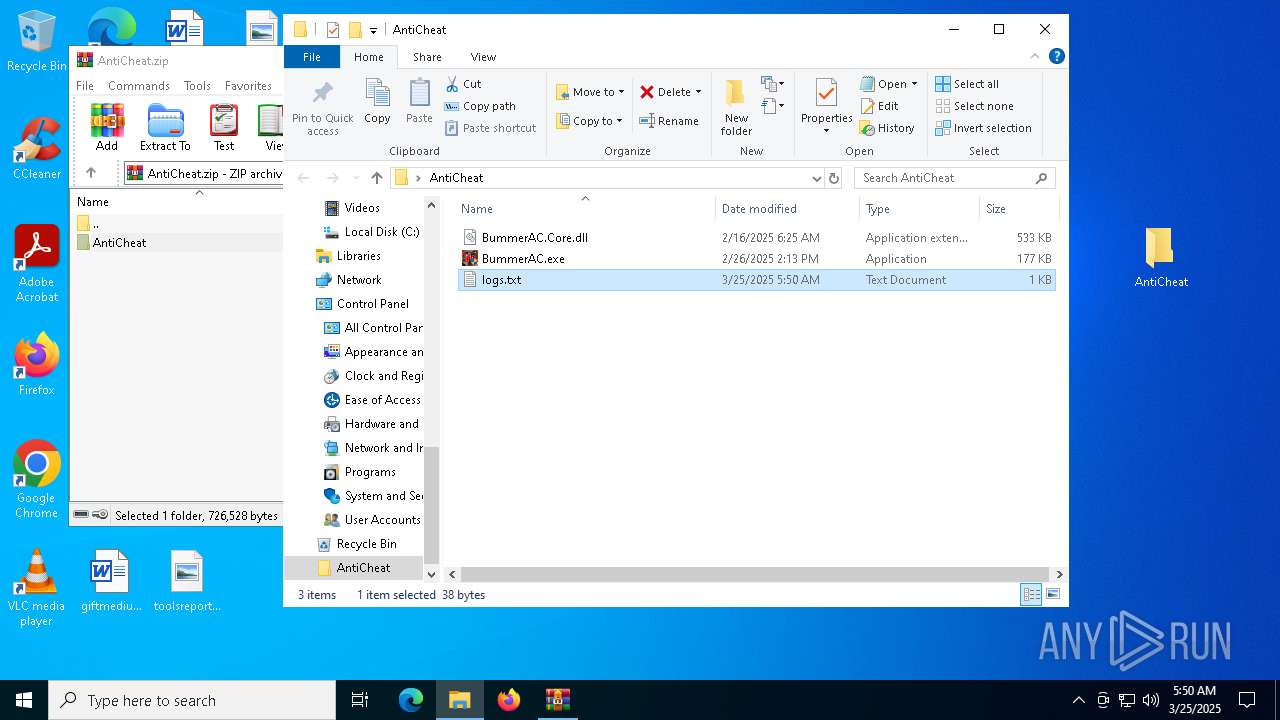
| 5064 | BummerAC.exe | C:\Users\admin\Desktop\AntiCheat\logs.txt | text | |
MD5:A2E4A430D43DA44E74D0710C8C141DB3 | SHA256:7E9AAE5589D05D3319D8C66794239E1DE6B1FA87B6C9F57A9782D8B00ADD684F | |||
| 976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0yikjiiy.2wf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qstebo1k.0jj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pdxb1yhm.xfl.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4448 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\89496350-c85b-40d9-b84c-dbe16a9c1b1b.070200d0-f7d1-4434-9cb8-a9bd89945943.down_meta | binary | |
MD5:6181A99B73E4FF274F811E3E5FDC0336 | SHA256:BFE912E23A7588863BD1DABB2A5319742E30AE2BF7933B803F5D794AC609AF3F | |||
| 4776 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4776.14740\AntiCheat\BummerAC.exe | executable | |
MD5:C3DB94D736FE0F82977992D20CF88B48 | SHA256:F71E33FB796AA327C8BA72A0E0FDCAAD5C2D0654494A6722F329BD173B403F22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5720 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4448 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2236 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2236 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5720 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5720 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |