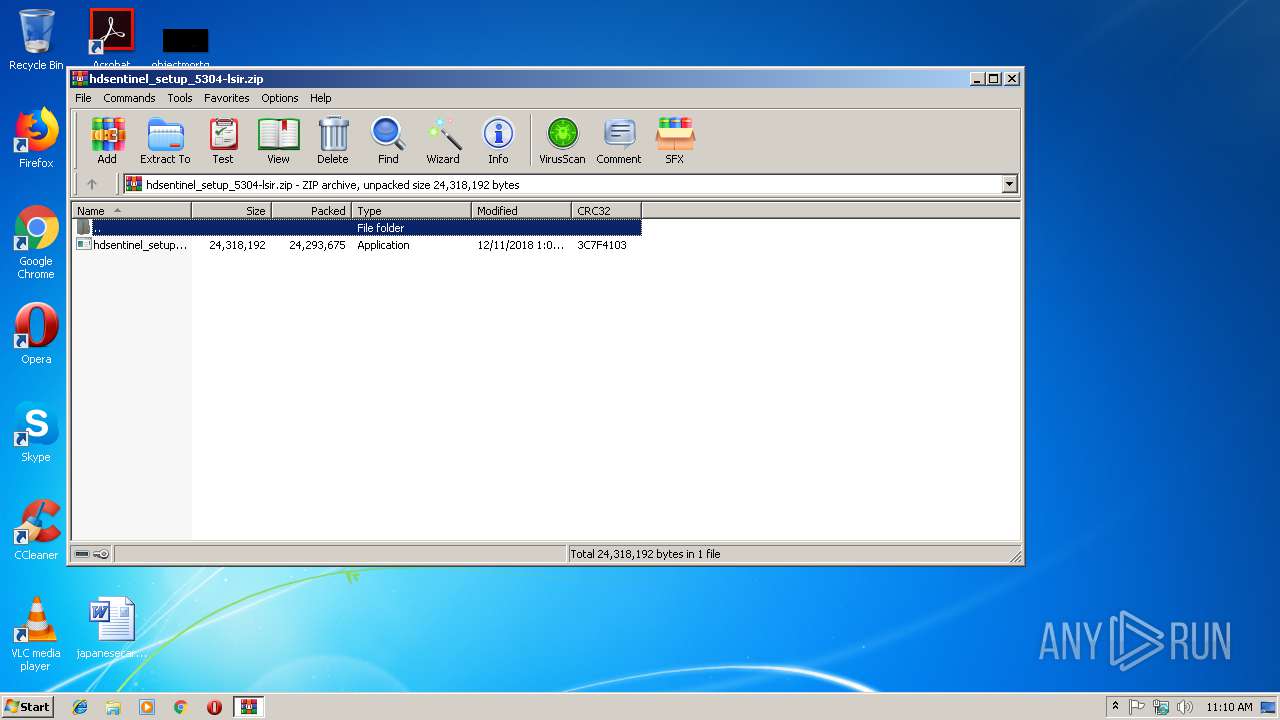
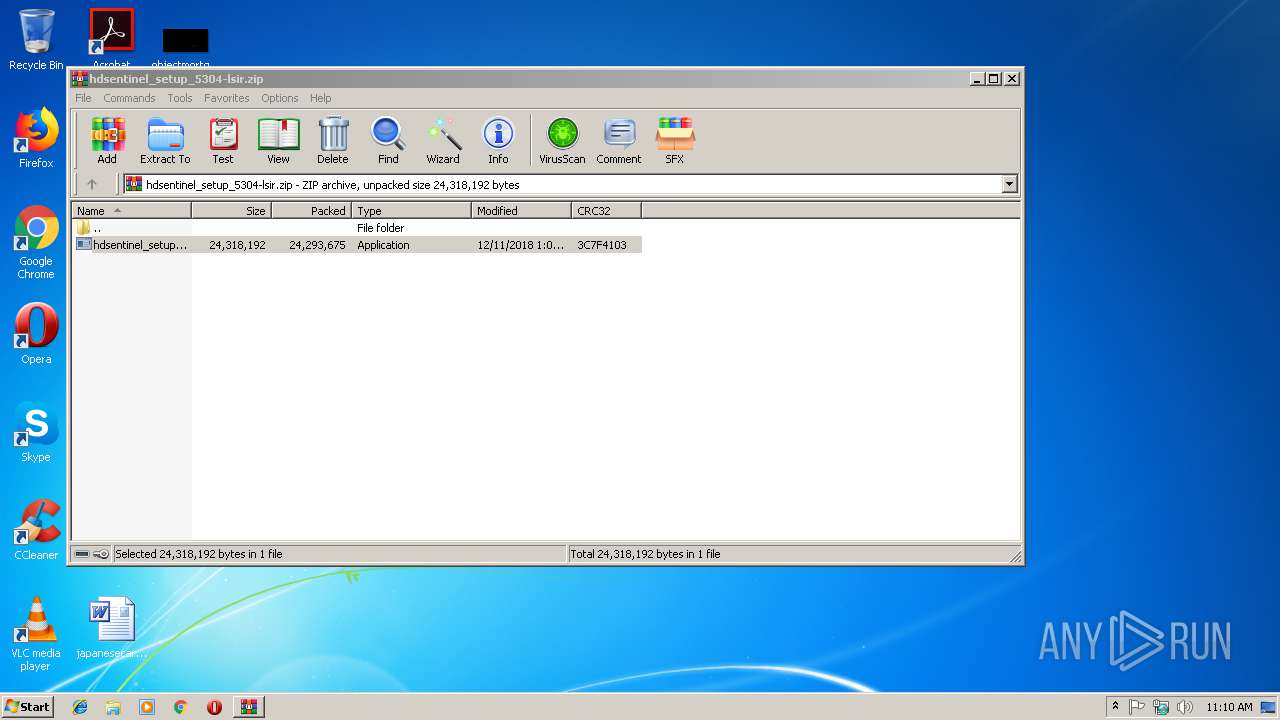
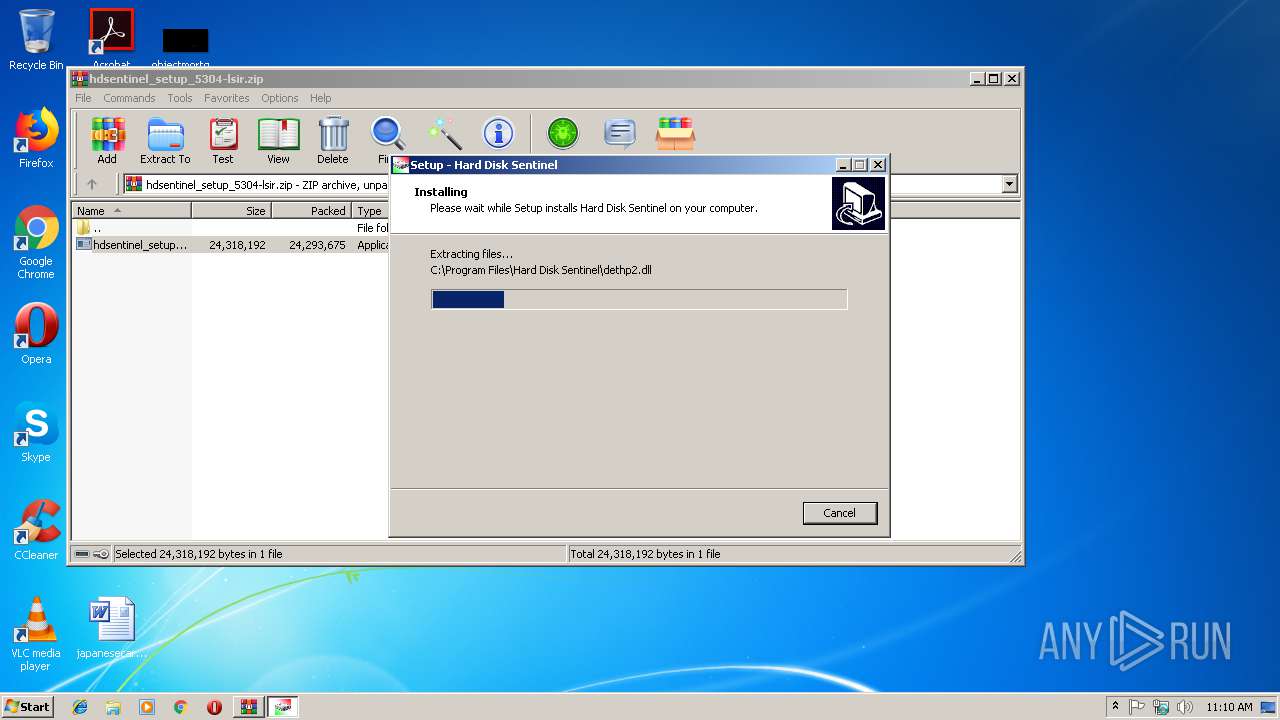
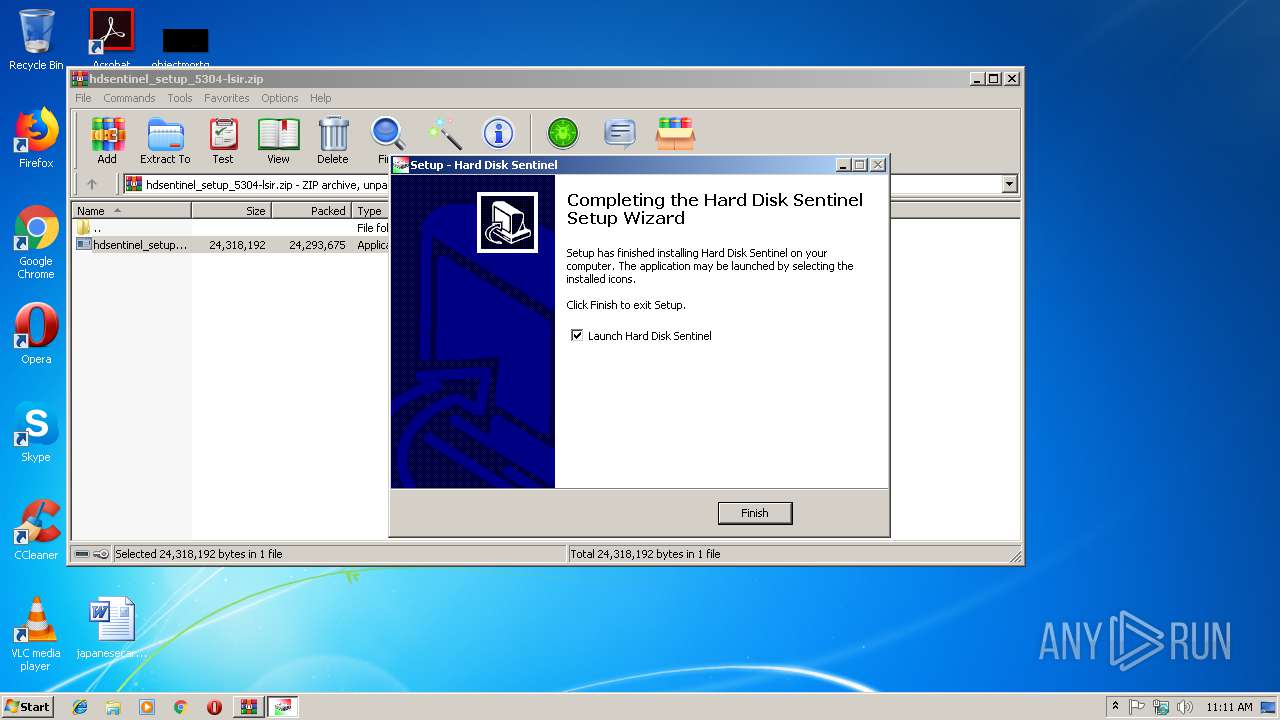
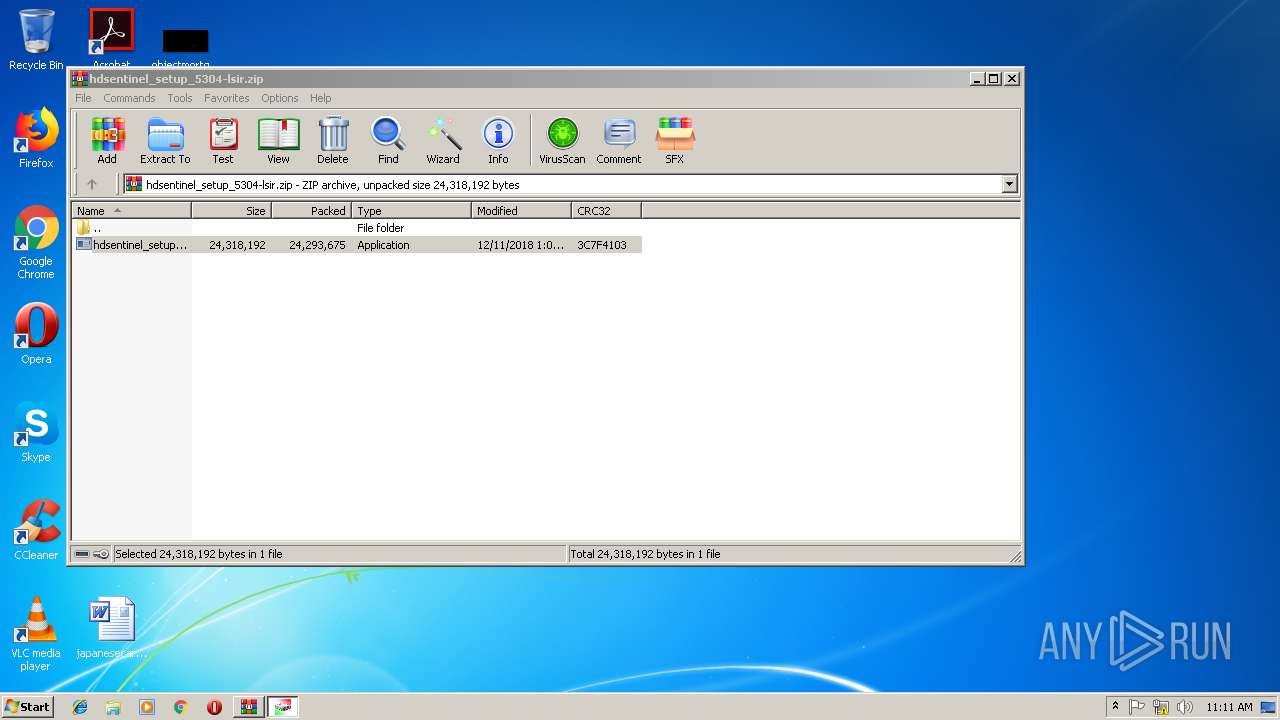
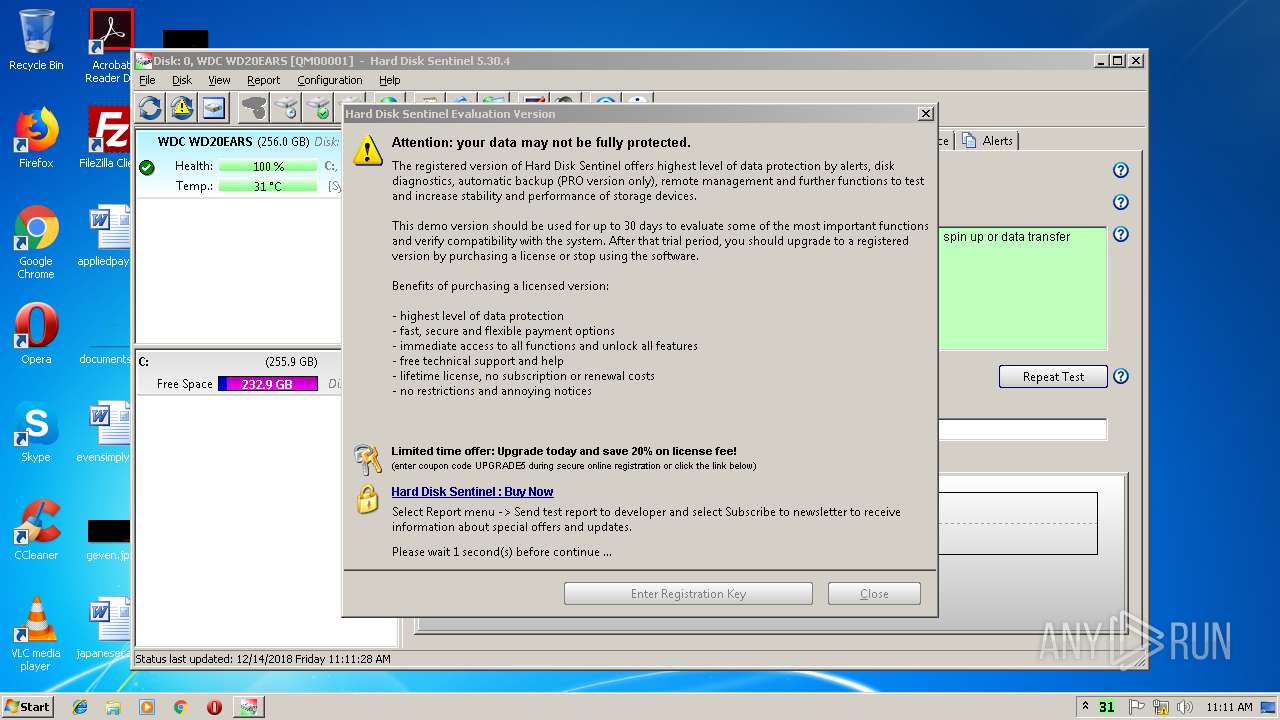
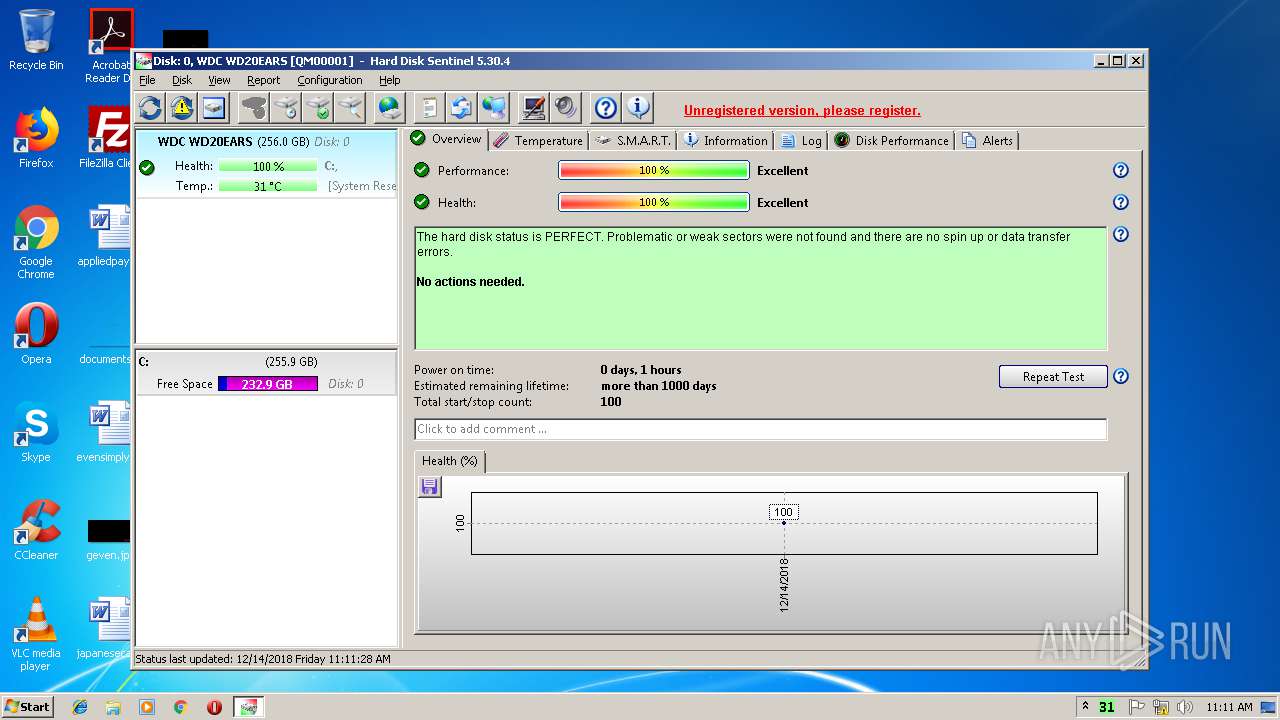
| download: | hdsentinel_setup_5304-lsir.zip |
| Full analysis: | https://app.any.run/tasks/00210cf0-84ae-4fe9-88b2-027ef648e02c |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2018, 11:09:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | DD61E509504E2879513C61032C60B6B7 |
| SHA1: | D5D458A329273BDB7A46DCB48A5990699D7E5AA1 |
| SHA256: | 504A7544223C7368FABC45270A38704A1031DE5666BFD408F43C1412551B49A5 |
| SSDEEP: | 393216:pntobv6Bn1EBCYB22tCFejdPq3I4ovx94LU3zjHjjGNd2LAmv/7M7ZNvIyzrbi37:EbCZoL2DFeVq3Kx94LU3XjjGEAWIEyzo |
MALICIOUS
Application was dropped or rewritten from another process
- hdsentinel_setup.exe (PID: 2296)
- hdsentinel_setup.exe (PID: 2436)
- HDSentinel.exe (PID: 4084)
- detect.dll (PID: 3692)
- detect.dll (PID: 2468)
- detect.dll (PID: 3952)
- detect.dll (PID: 3028)
- HDSAction.exe (PID: 3084)
- detect.dll (PID: 864)
- detect.dll (PID: 4024)
- detect.dll (PID: 2892)
- HDSentinel.exe (PID: 4092)
- HDSentinel.exe (PID: 1760)
Loads dropped or rewritten executable
- HDSentinel.exe (PID: 4084)
- svchost.exe (PID: 844)
Loads the Task Scheduler COM API
- CSCRIPT.exe (PID: 3488)
- CSCRIPT.exe (PID: 3852)
- CSCRIPT.exe (PID: 2772)
- CSCRIPT.exe (PID: 3784)
- CSCRIPT.exe (PID: 3924)
SUSPICIOUS
Executable content was dropped or overwritten
- hdsentinel_setup.exe (PID: 2296)
- WinRAR.exe (PID: 4056)
- hdsentinel_setup.exe (PID: 2436)
- hdsentinel_setup.tmp (PID: 2820)
Creates files in the user directory
- hdsentinel_setup.tmp (PID: 2820)
- HDSentinel.exe (PID: 4084)
Modifies the open verb of a shell class
- HDSentinel.exe (PID: 4084)
Starts application with an unusual extension
- HDSentinel.exe (PID: 4084)
Creates files in the program directory
- HDSentinel.exe (PID: 4084)
Executes scripts
- HDSentinel.exe (PID: 4084)
Creates files in the Windows directory
- svchost.exe (PID: 844)
Reads internet explorer settings
- HDSAction.exe (PID: 3084)
Starts Internet Explorer
- HDSentinel.exe (PID: 4084)
Low-level read access rights to disk partition
- HDSentinel.exe (PID: 4084)
INFO
Application was dropped or rewritten from another process
- hdsentinel_setup.tmp (PID: 2692)
- hdsentinel_setup.tmp (PID: 2820)
Loads dropped or rewritten executable
- hdsentinel_setup.tmp (PID: 2820)
Creates a software uninstall entry
- hdsentinel_setup.tmp (PID: 2820)
Changes internet zones settings
- iexplore.exe (PID: 4008)
- iexplore.exe (PID: 3804)
Changes settings of System certificates
- iexplore.exe (PID: 1812)
Creates files in the program directory
- hdsentinel_setup.tmp (PID: 2820)
Reads internet explorer settings
- iexplore.exe (PID: 1812)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1812)
Reads Internet Cache Settings
- iexplore.exe (PID: 1812)
Creates files in the user directory
- iexplore.exe (PID: 1812)
Reads settings of System Certificates
- HDSentinel.exe (PID: 4084)
Application launched itself
- iexplore.exe (PID: 3804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:12:11 13:07:11 |
| ZipCRC: | 0x3c7f4103 |
| ZipCompressedSize: | 24293675 |
| ZipUncompressedSize: | 24318192 |
| ZipFileName: | hdsentinel_setup.exe |
Total processes
71
Monitored processes
27
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 844 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | "C:\Program Files\Hard Disk Sentinel\detect.dll" *WMIC2* . "C:\Users\admin\AppData\Local\Temp\181214111145093.54802575.tmp" Select * FROM Win32_DiskDrive | C:\Program Files\Hard Disk Sentinel\detect.dll | — | HDSentinel.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
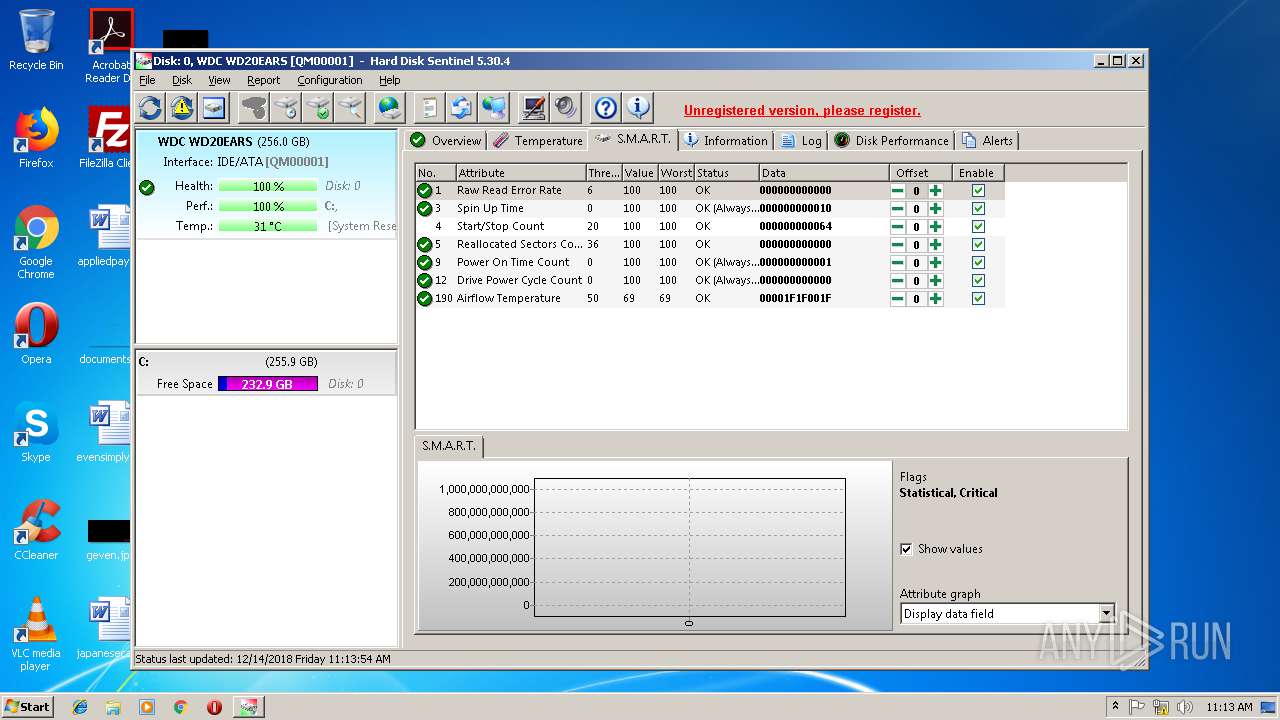
| 1760 | "C:\Program Files\Hard Disk Sentinel\HDSentinel.exe" | C:\Program Files\Hard Disk Sentinel\HDSentinel.exe | — | explorer.exe | |||||||||||
User: admin Company: H.D.S. Hungary Integrity Level: MEDIUM Description: Hard Disk Sentinel Exit code: 3221226540 Version: 5.30.0.0 Modules
| |||||||||||||||
| 1812 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4008 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
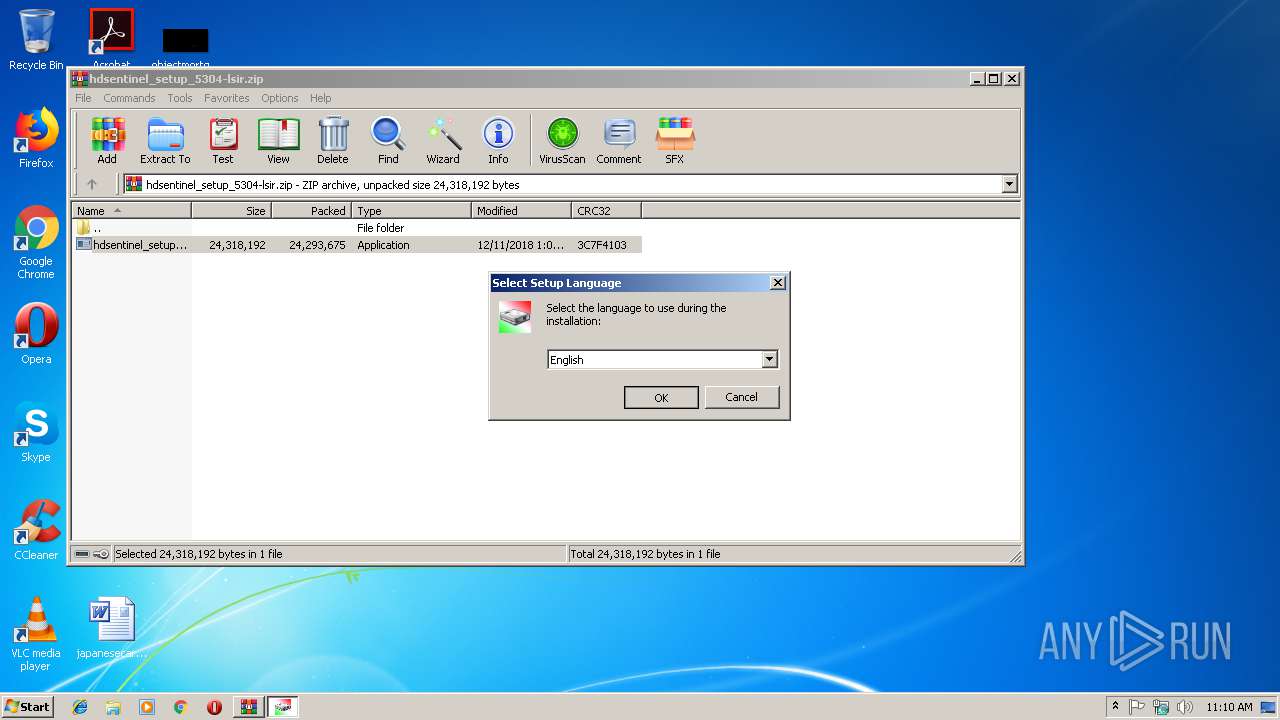
| 2296 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4056.34590\hdsentinel_setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4056.34590\hdsentinel_setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Janos Mathe Integrity Level: MEDIUM Description: Hard Disk Sentinel Setup Exit code: 0 Version: 5.30.0.0 Modules
| |||||||||||||||
| 2376 | fsutil behavior query disabledeletenotify | C:\Windows\system32\fsutil.exe | — | HDSentinel.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: fsutil.exe Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2436 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4056.34590\hdsentinel_setup.exe" /SPAWNWND=$2015E /NOTIFYWND=$3013C | C:\Users\admin\AppData\Local\Temp\Rar$EXa4056.34590\hdsentinel_setup.exe | hdsentinel_setup.tmp | ||||||||||||
User: admin Company: Janos Mathe Integrity Level: HIGH Description: Hard Disk Sentinel Setup Exit code: 0 Version: 5.30.0.0 Modules
| |||||||||||||||
| 2468 | "C:\Program Files\Hard Disk Sentinel\detect.dll" *WMIC2* . "C:\Users\admin\AppData\Local\Temp\181214111145317.8015659.tmp" Select * FROM NVRAID_Disk_Device | C:\Program Files\Hard Disk Sentinel\detect.dll | — | HDSentinel.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\AppData\Local\Temp\is-26ESH.tmp\hdsentinel_setup.tmp" /SL5="$3013C,23970703,56832,C:\Users\admin\AppData\Local\Temp\Rar$EXa4056.34590\hdsentinel_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-26ESH.tmp\hdsentinel_setup.tmp | — | hdsentinel_setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2772 | CSCRIPT //NOLOGO "C:\Users\admin\AppData\Roaming\Hard Disk Sentinel\hds_control_check.vbs" | C:\Windows\system32\CSCRIPT.exe | — | HDSentinel.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
2 092
Read events
1 851
Write events
238
Delete events
3
Modification events
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\hdsentinel_setup_5304-lsir.zip | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4056) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
54
Suspicious files
7
Text files
87
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-JD0FE.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-JRR86.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-6C8O3.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-JPQCR.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-IK1EU.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-49MSK.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-RU4HC.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-54TA8.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-C37SU.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | hdsentinel_setup.tmp | C:\Program Files\Hard Disk Sentinel\is-K7E9L.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
30
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3832 | iexplore.exe | GET | 301 | 87.229.73.241:80 | http://www.hdsentinel.com/store.php | HU | html | 244 b | unknown |
3804 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
1812 | iexplore.exe | GET | 301 | 87.229.73.241:80 | http://www.hdsentinel.com/store.php | HU | html | 244 b | unknown |
4008 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3084 | HDSAction.exe | 87.229.73.241:443 | www.hdsentinel.com | Deninet KFT | HU | unknown |
1812 | iexplore.exe | 87.229.73.241:80 | www.hdsentinel.com | Deninet KFT | HU | unknown |
4008 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1812 | iexplore.exe | 87.229.73.241:443 | www.hdsentinel.com | Deninet KFT | HU | unknown |
1812 | iexplore.exe | 2.18.232.15:443 | s7.addthis.com | Akamai International B.V. | — | whitelisted |
1812 | iexplore.exe | 216.58.215.238:443 | apis.google.com | Google Inc. | US | whitelisted |
4084 | HDSentinel.exe | 87.229.73.241:443 | www.hdsentinel.com | Deninet KFT | HU | unknown |
3832 | iexplore.exe | 87.229.73.241:80 | www.hdsentinel.com | Deninet KFT | HU | unknown |
3804 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3832 | iexplore.exe | 87.229.73.241:443 | www.hdsentinel.com | Deninet KFT | HU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.hdsentinel.com |
| unknown |
www.bing.com |
| whitelisted |
apis.google.com |
| whitelisted |
s7.addthis.com |
| whitelisted |