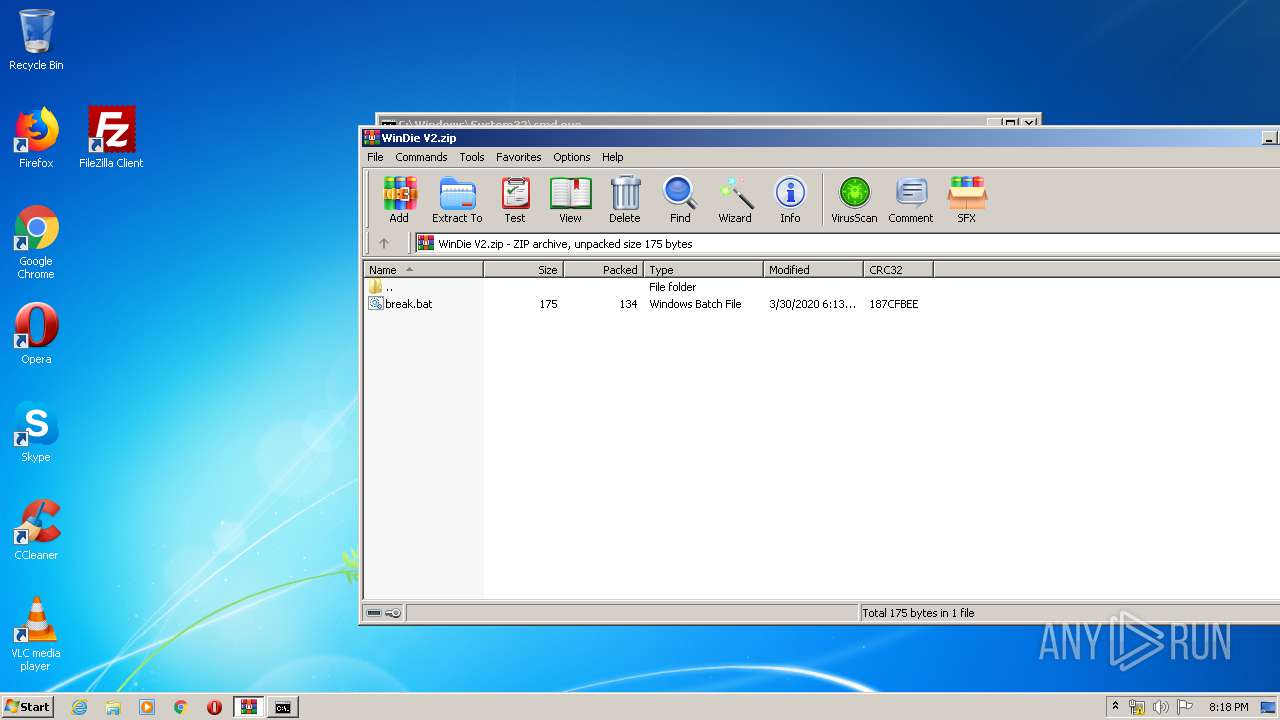
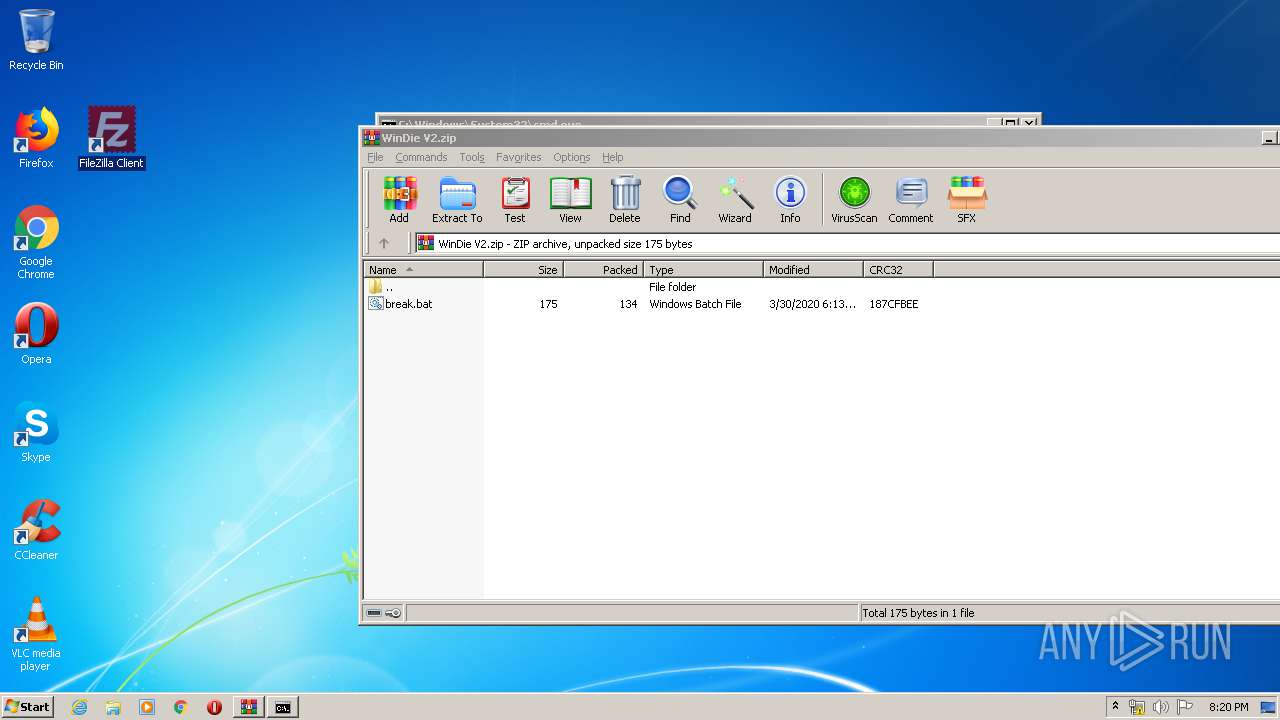
| File name: | WinDie V2.zip |
| Full analysis: | https://app.any.run/tasks/d58ea1db-ed23-42f5-945a-7ca2dd877248 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 19:16:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E73ADC10887397F92E2D32F46CACE641 |
| SHA1: | B5E611406C489AE597C3B35547902EFCB39835AD |
| SHA256: | 503ACC26F96A3A89305C1F601579CE6741B595F7702058BB1FDD6768837396D7 |
| SSDEEP: | 6:5j9BuVxVjfaJ3uQsIbEEHeHxlLEwBuuauwWuB+lit/:5j9BaVjf8eyJHeRywBLbkBai1 |
MALICIOUS
Actions looks like stealing of personal data
- cmd.exe (PID: 3228)
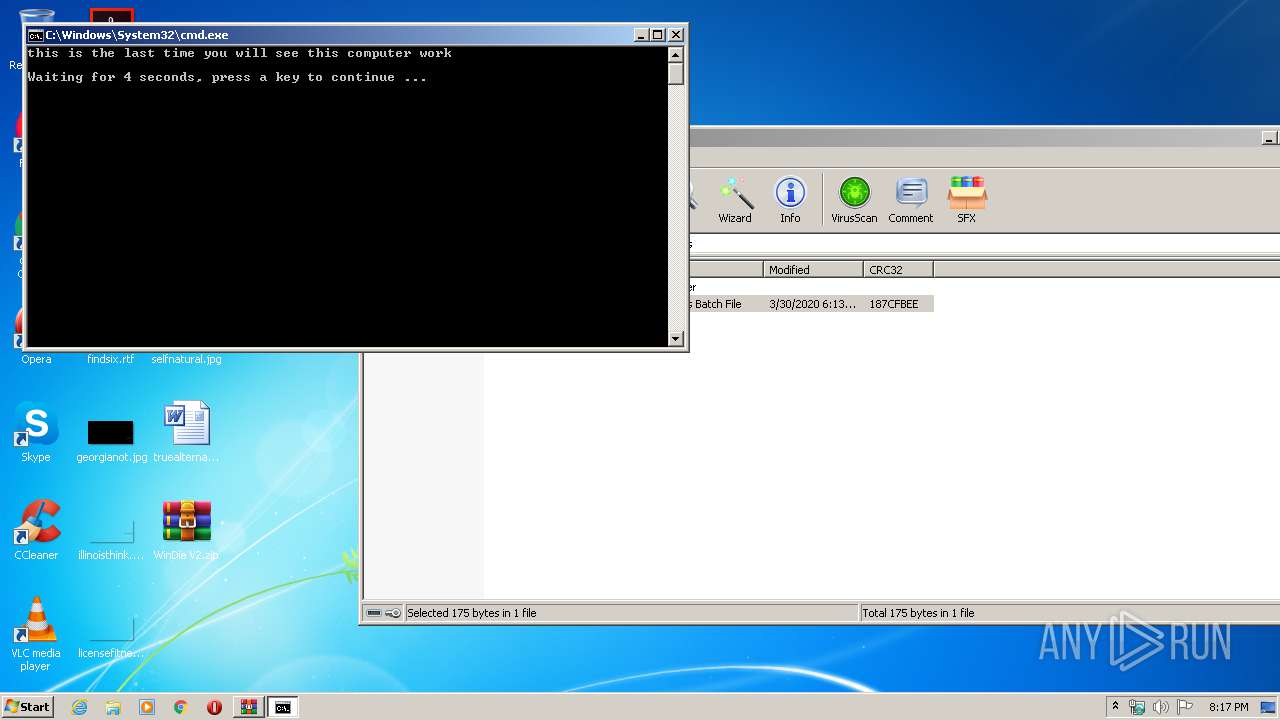
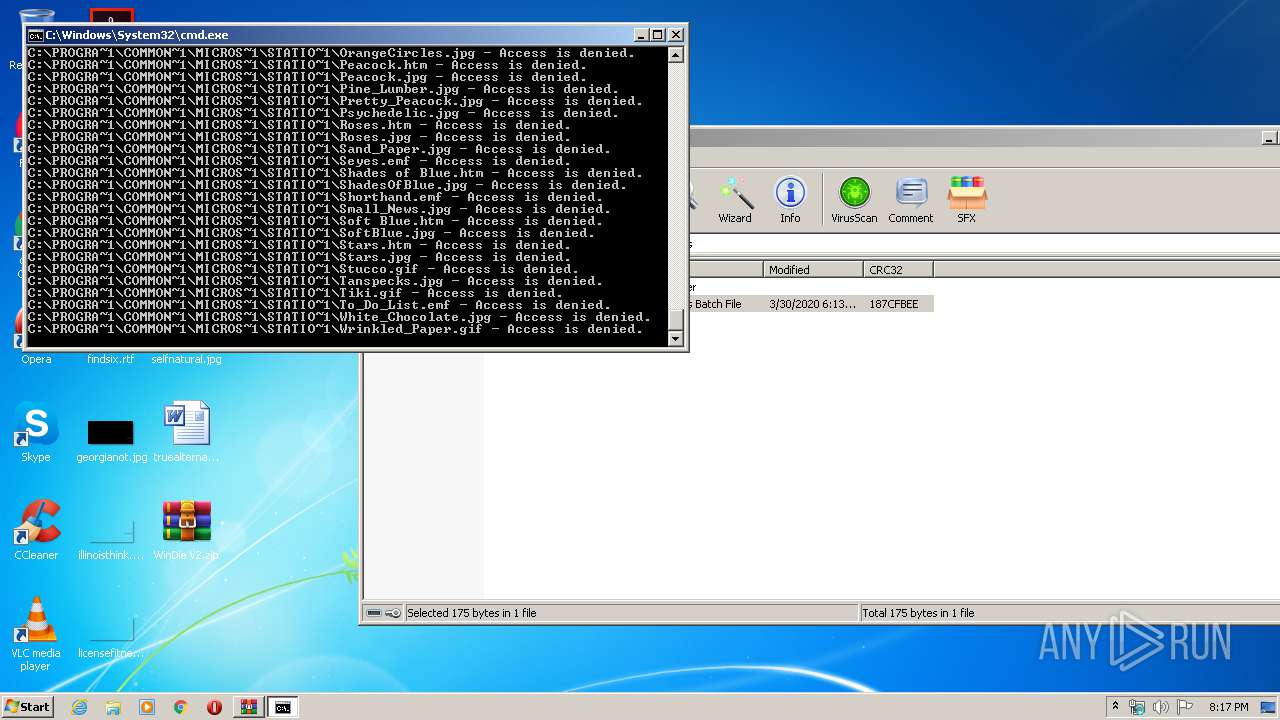
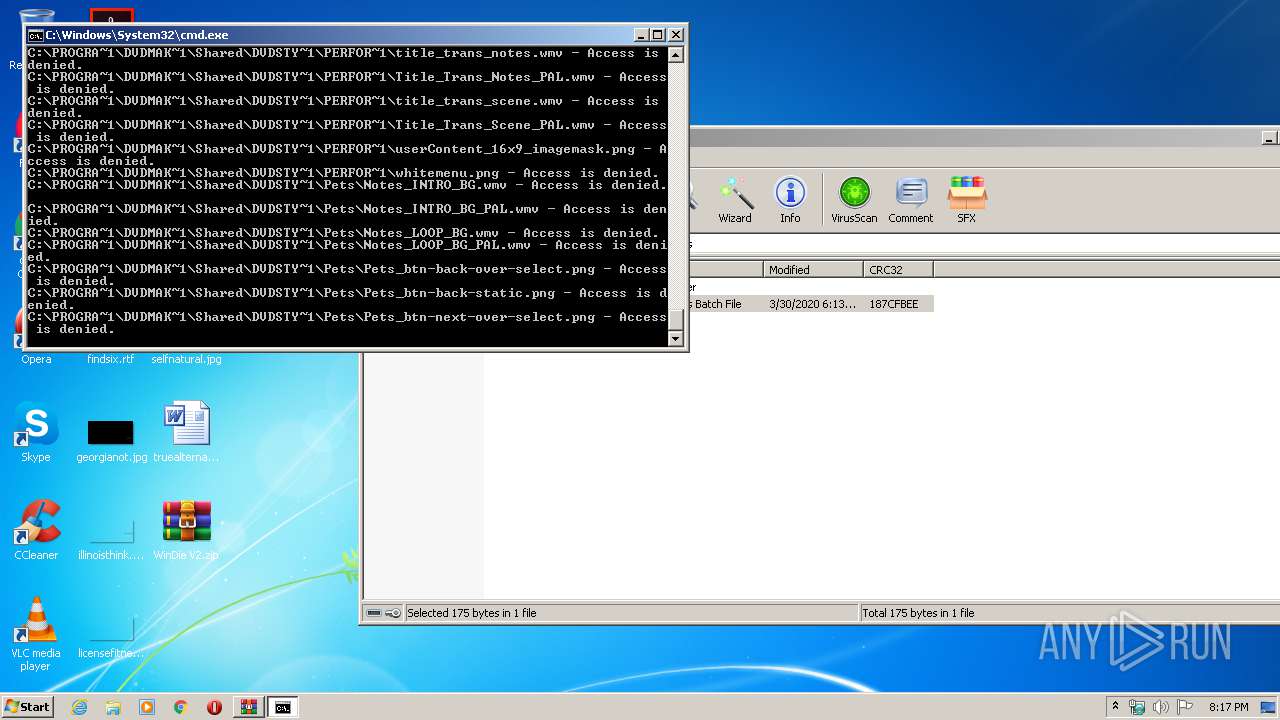
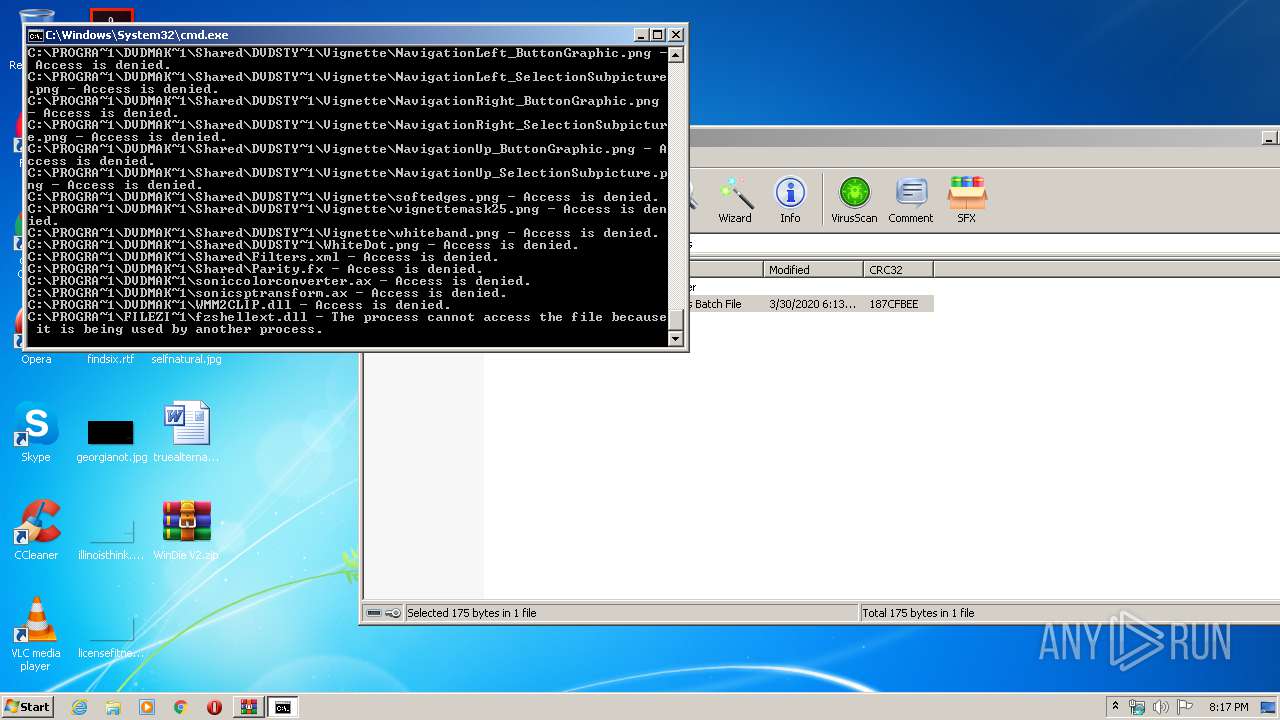
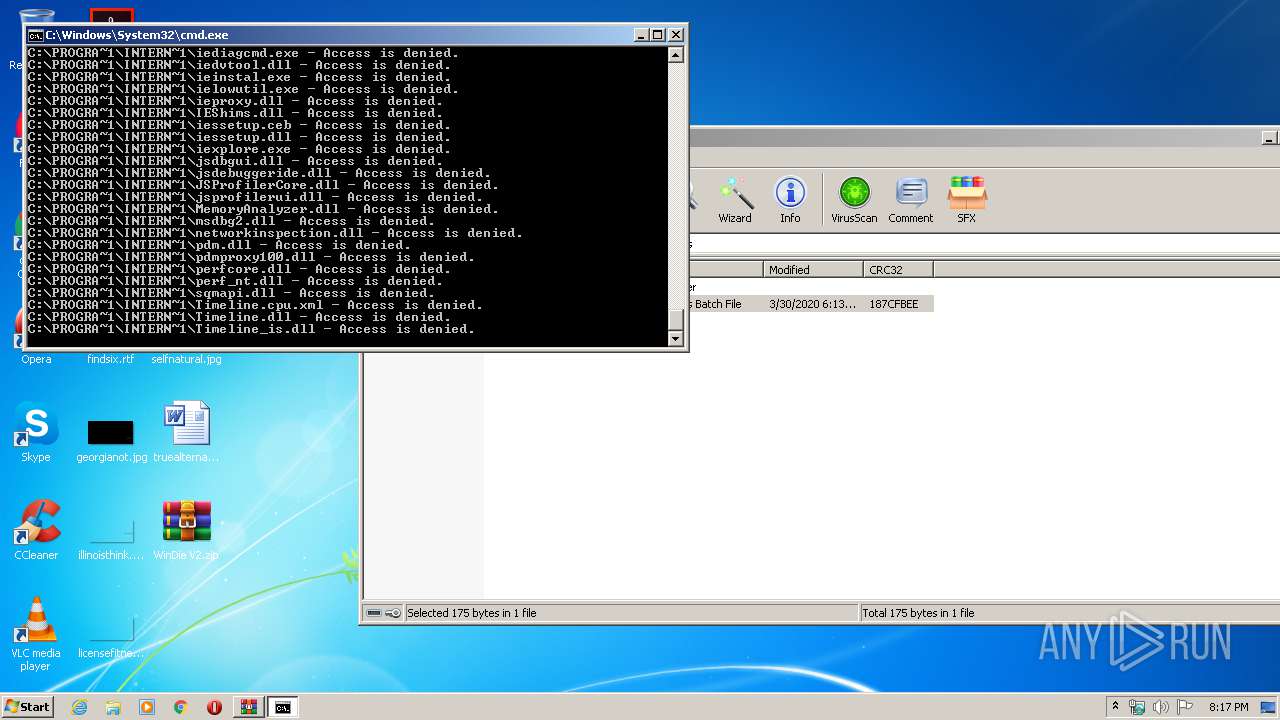
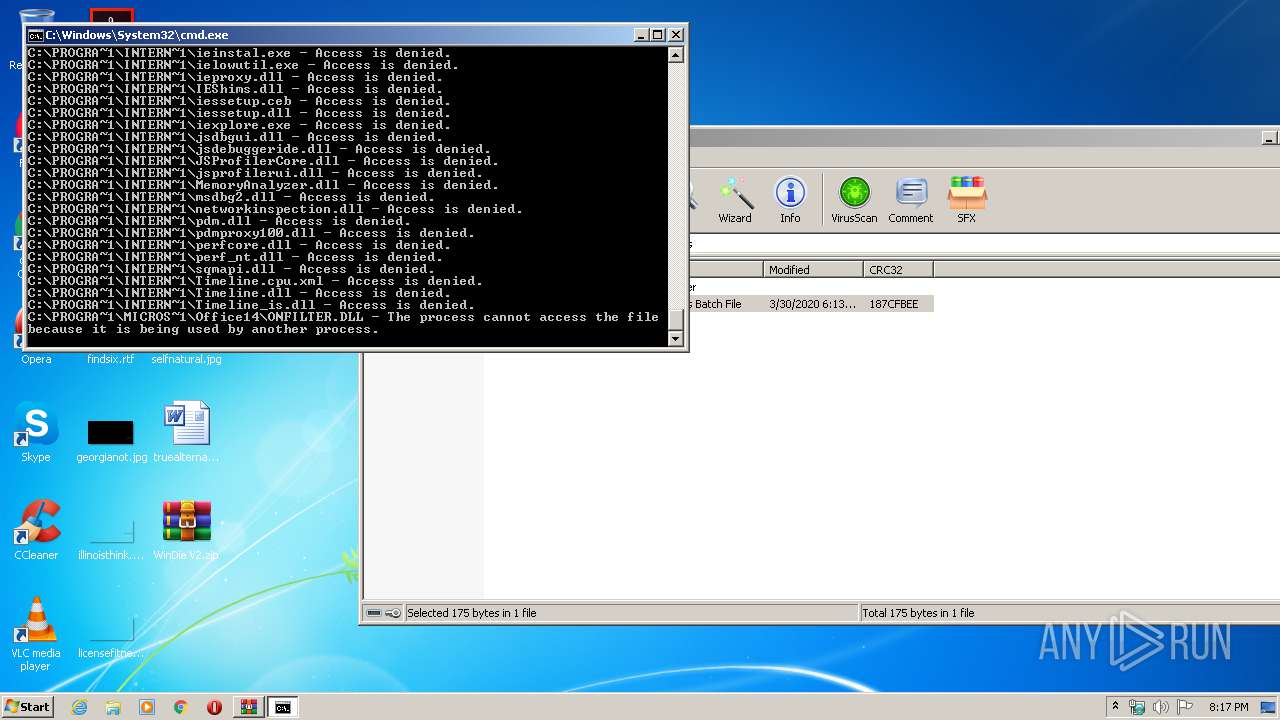
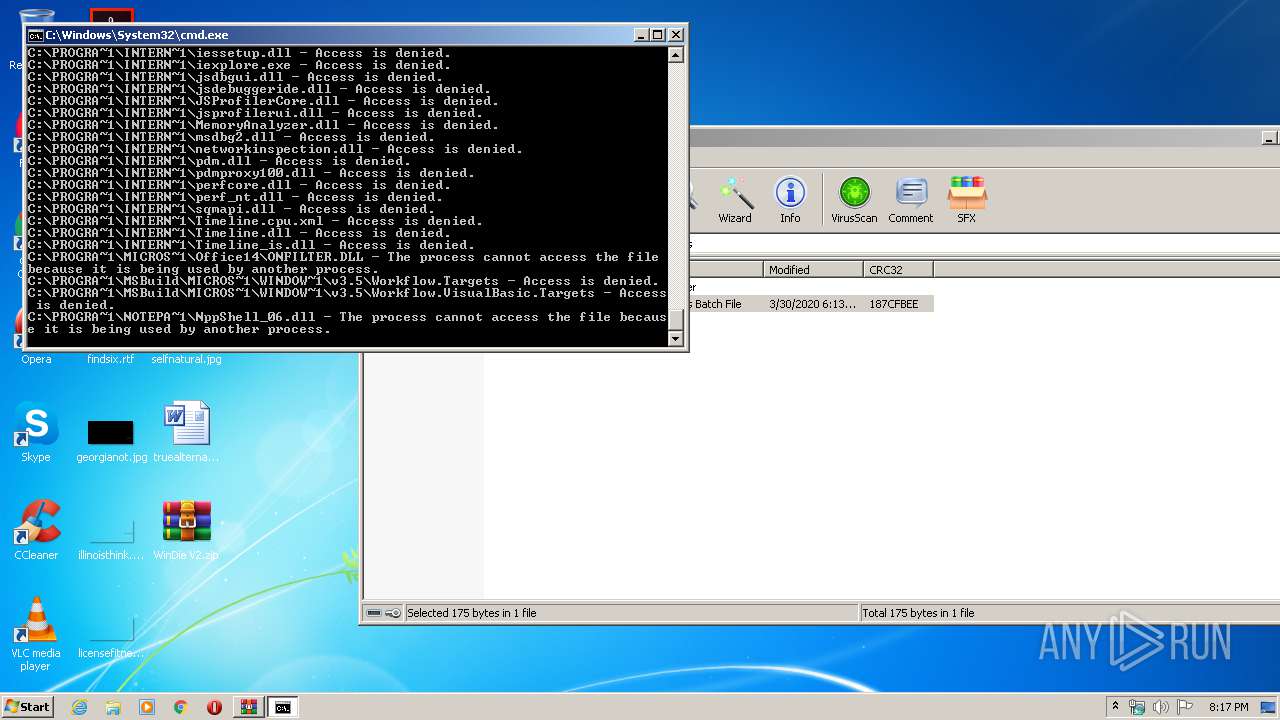
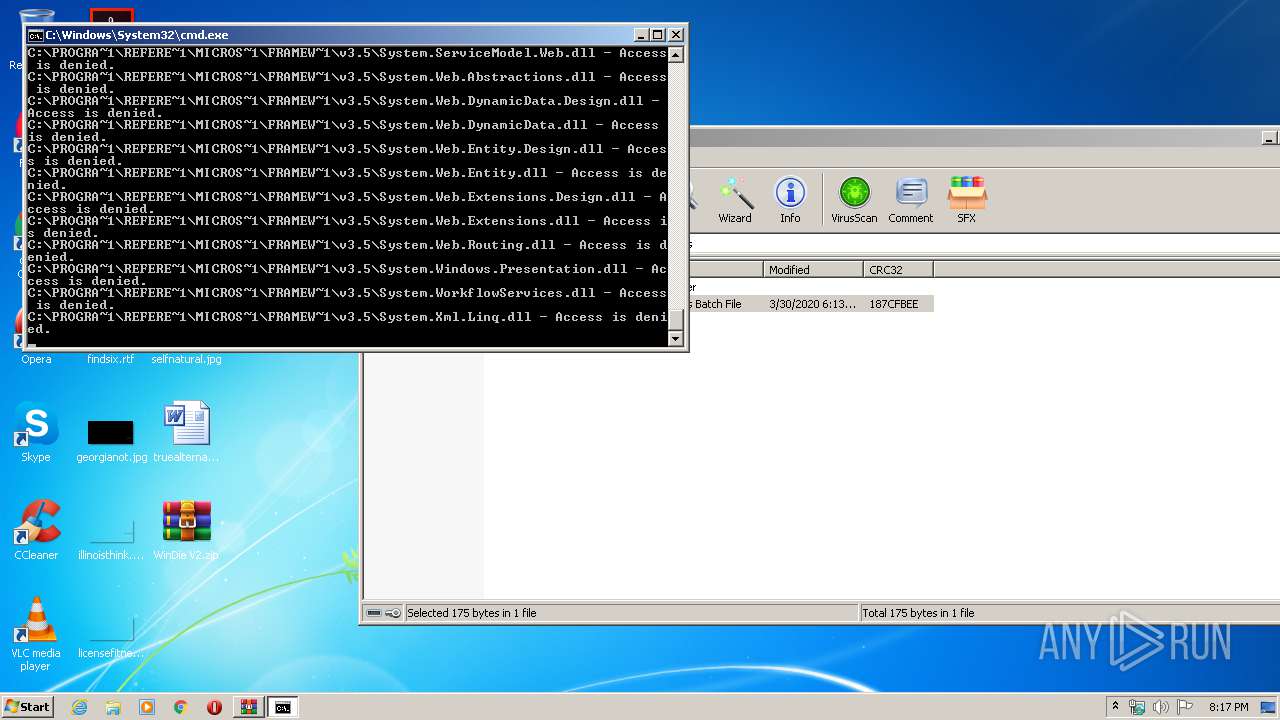
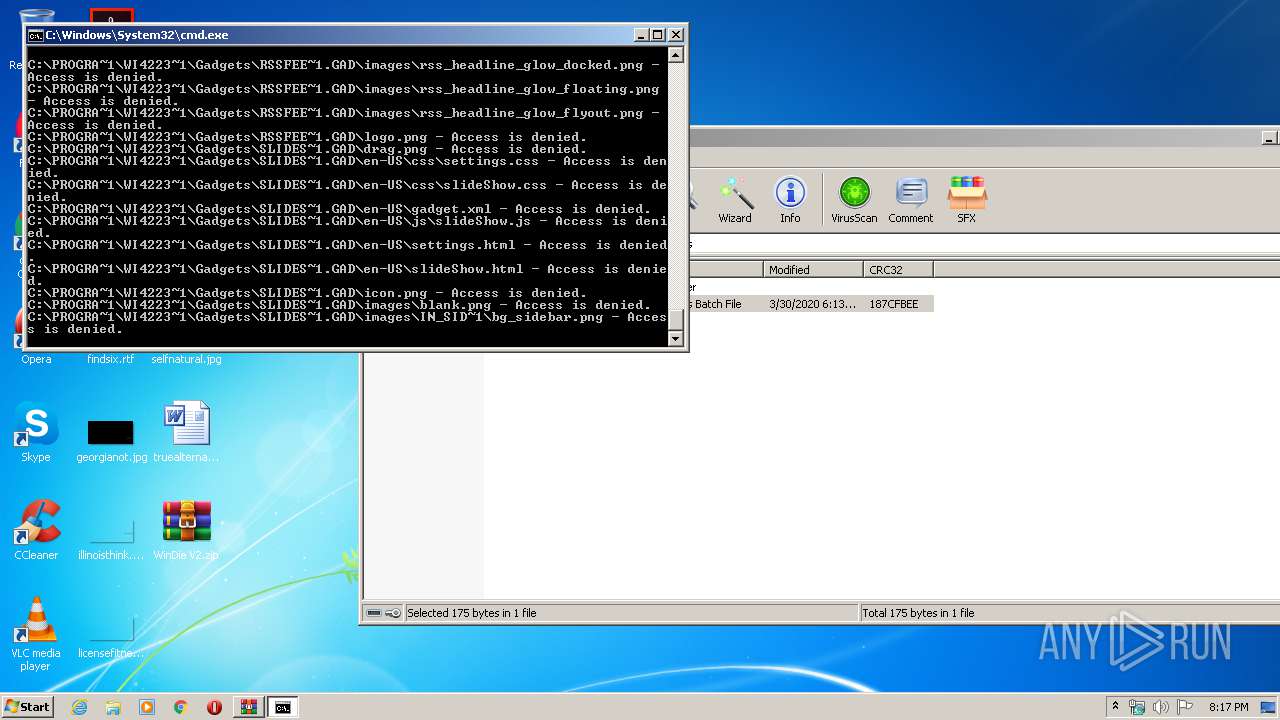
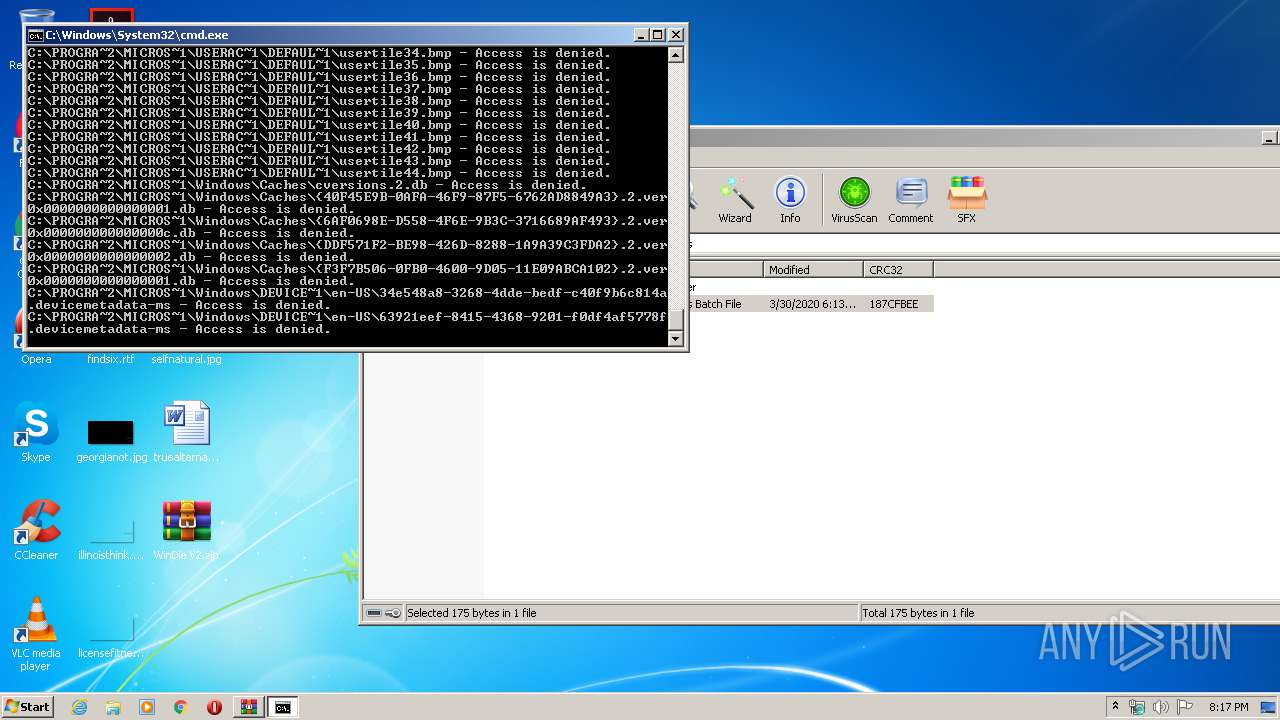
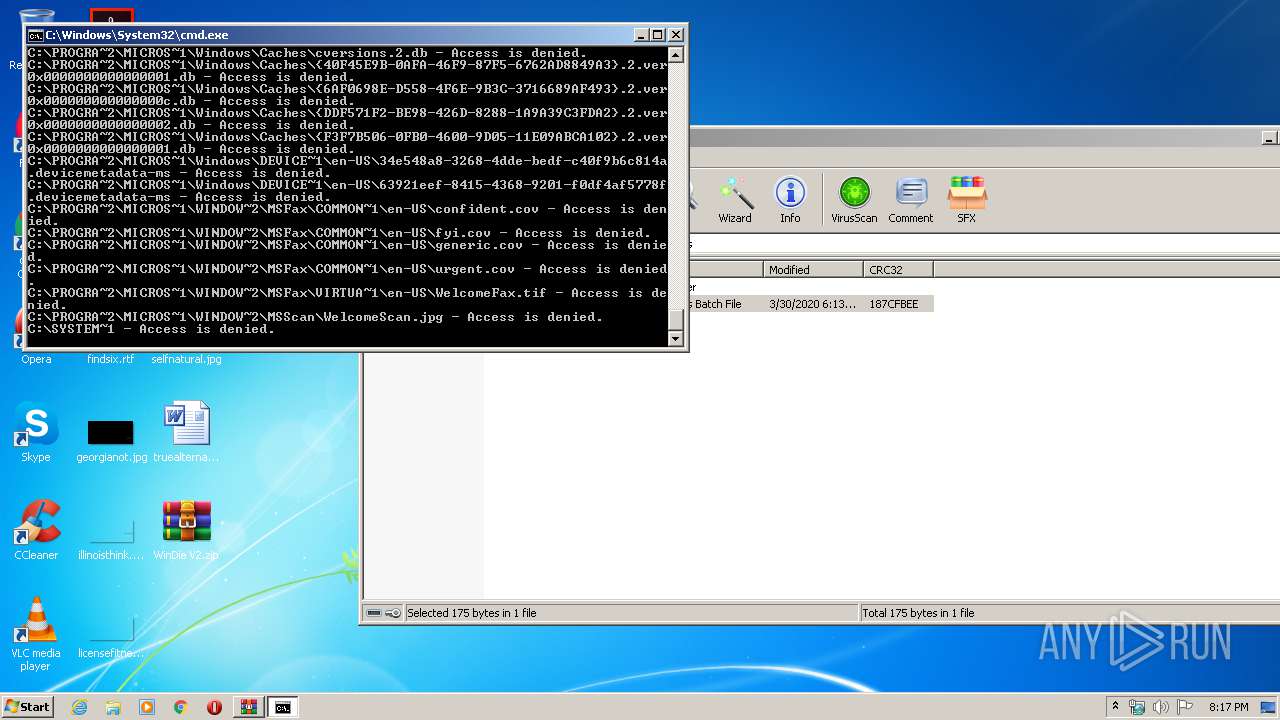
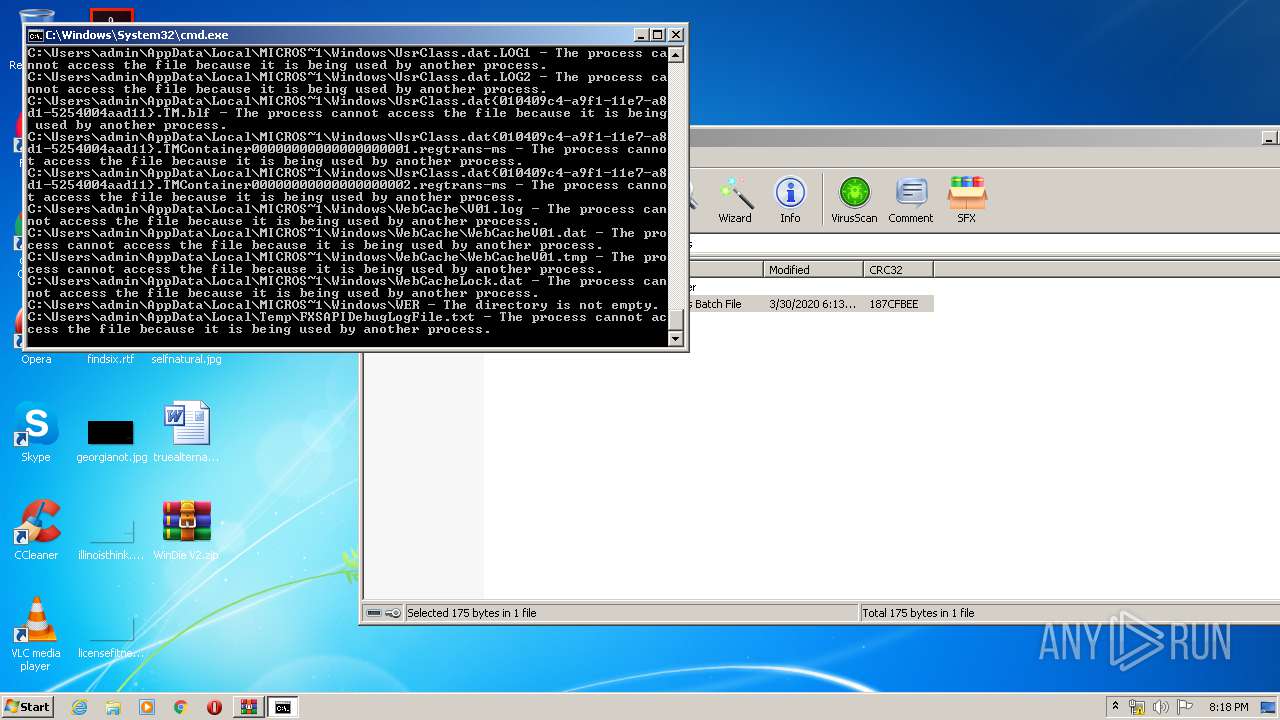
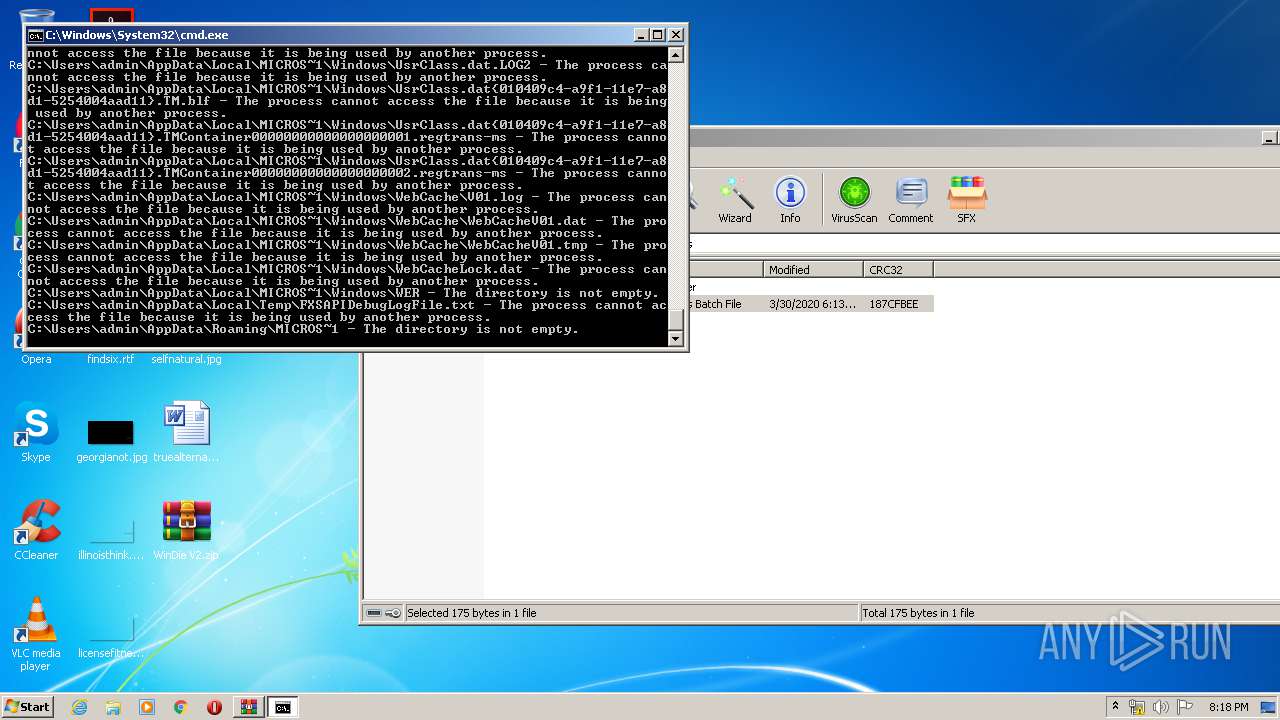
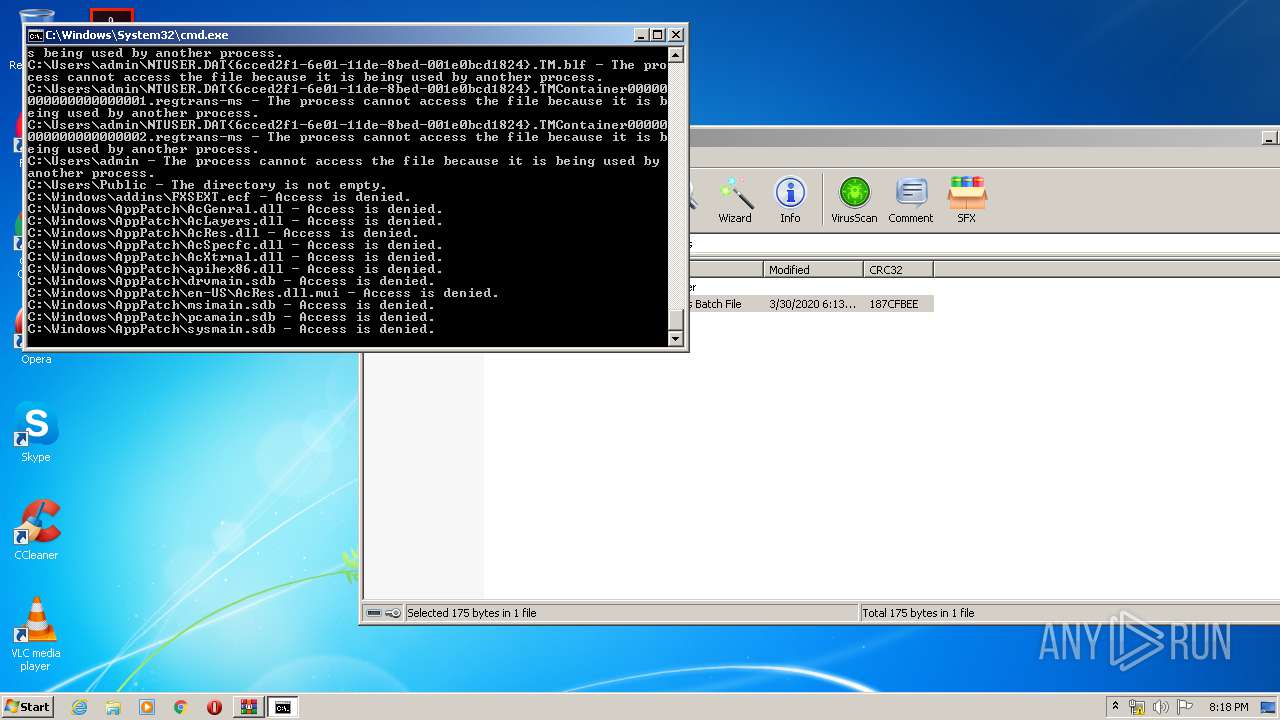
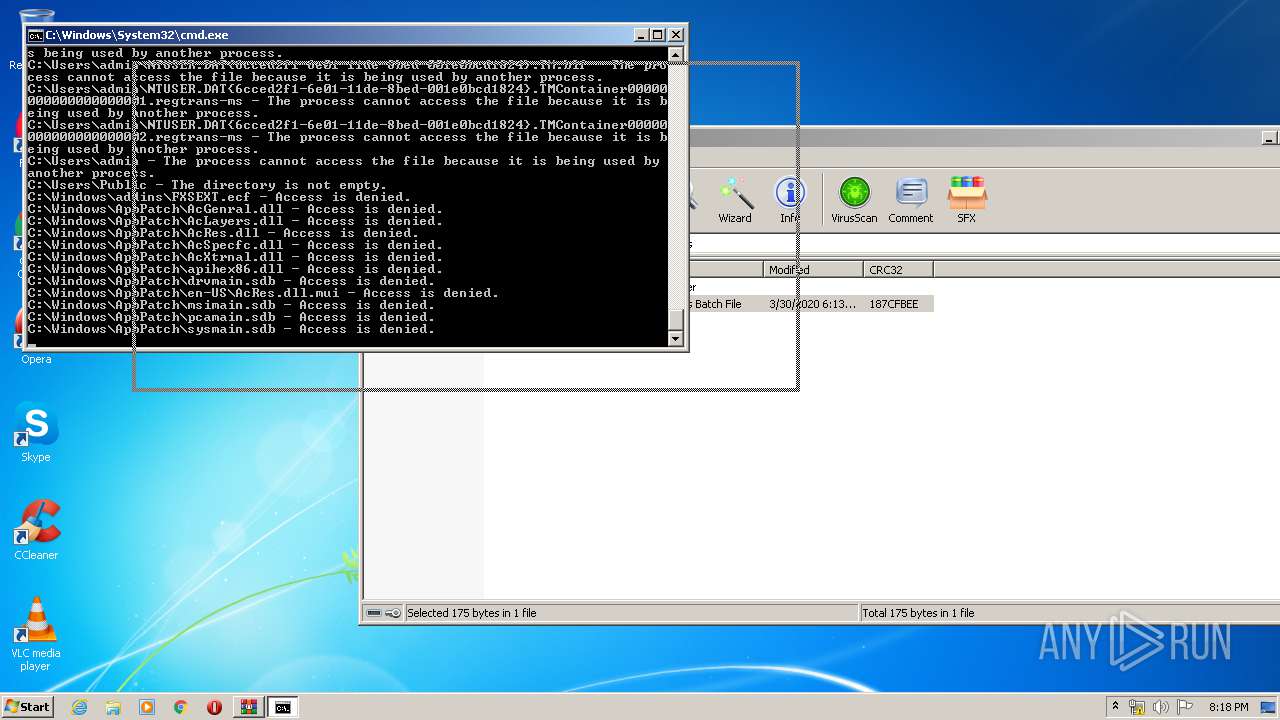
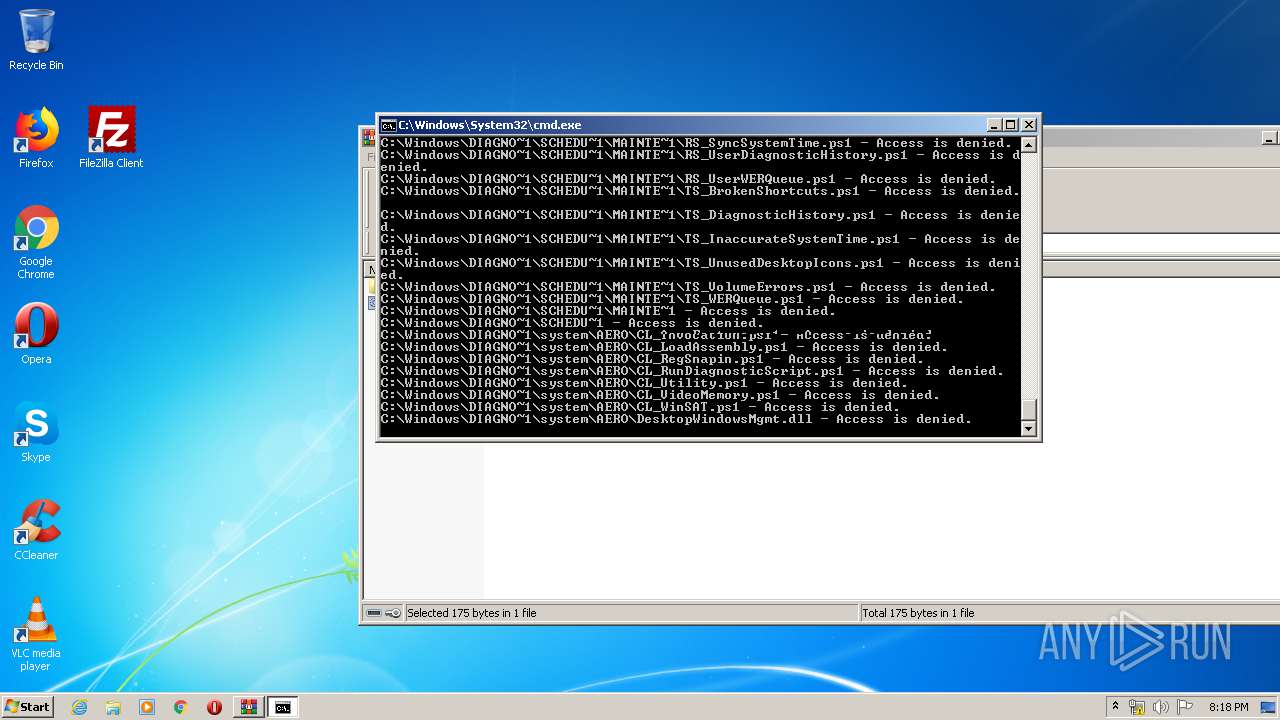
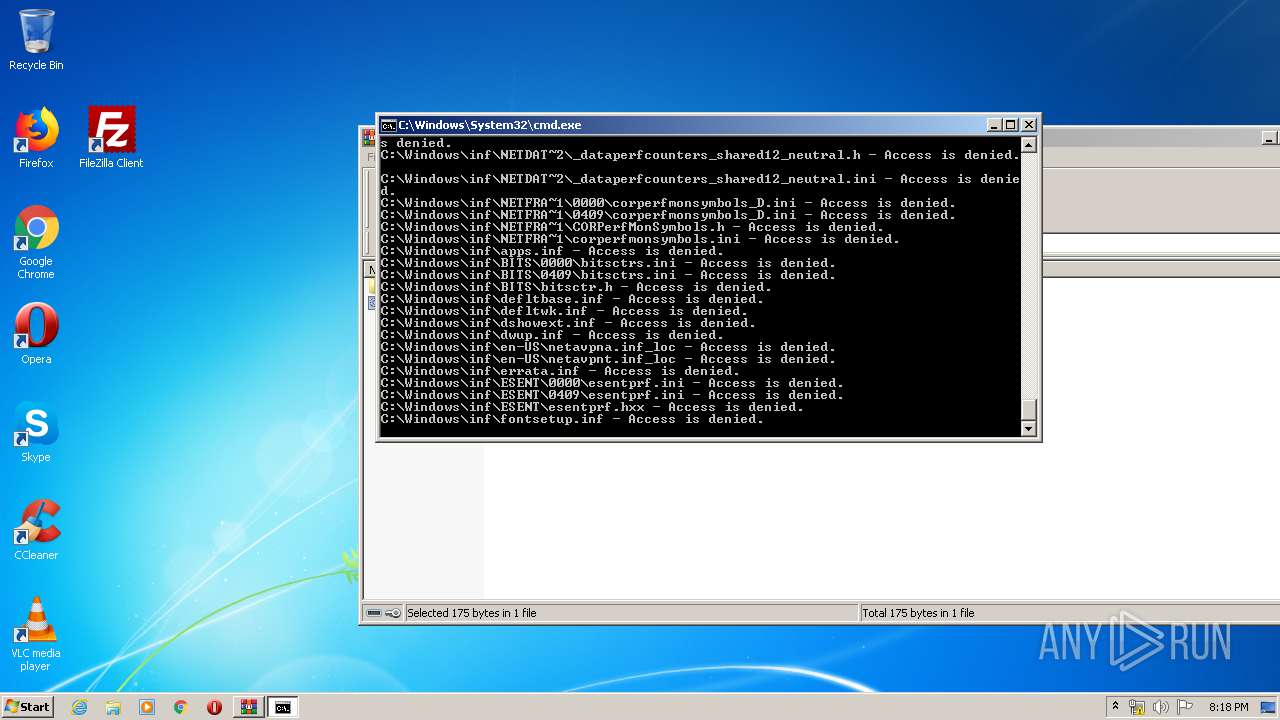
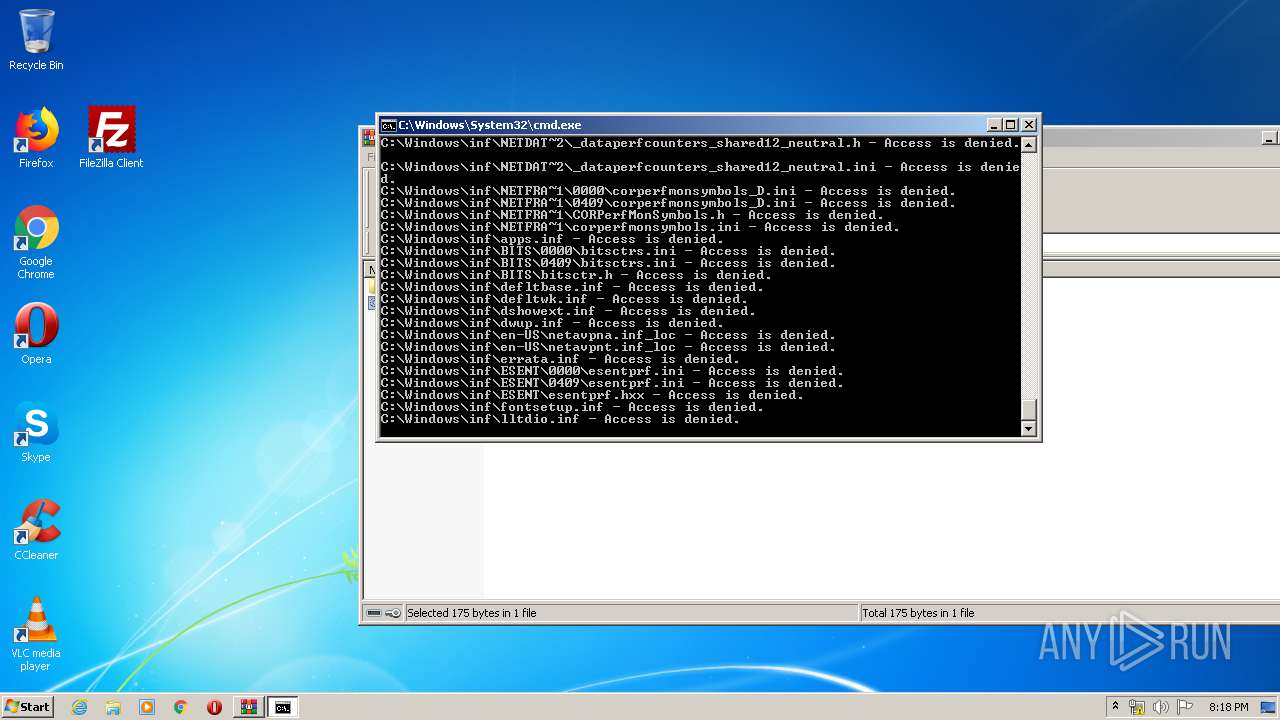
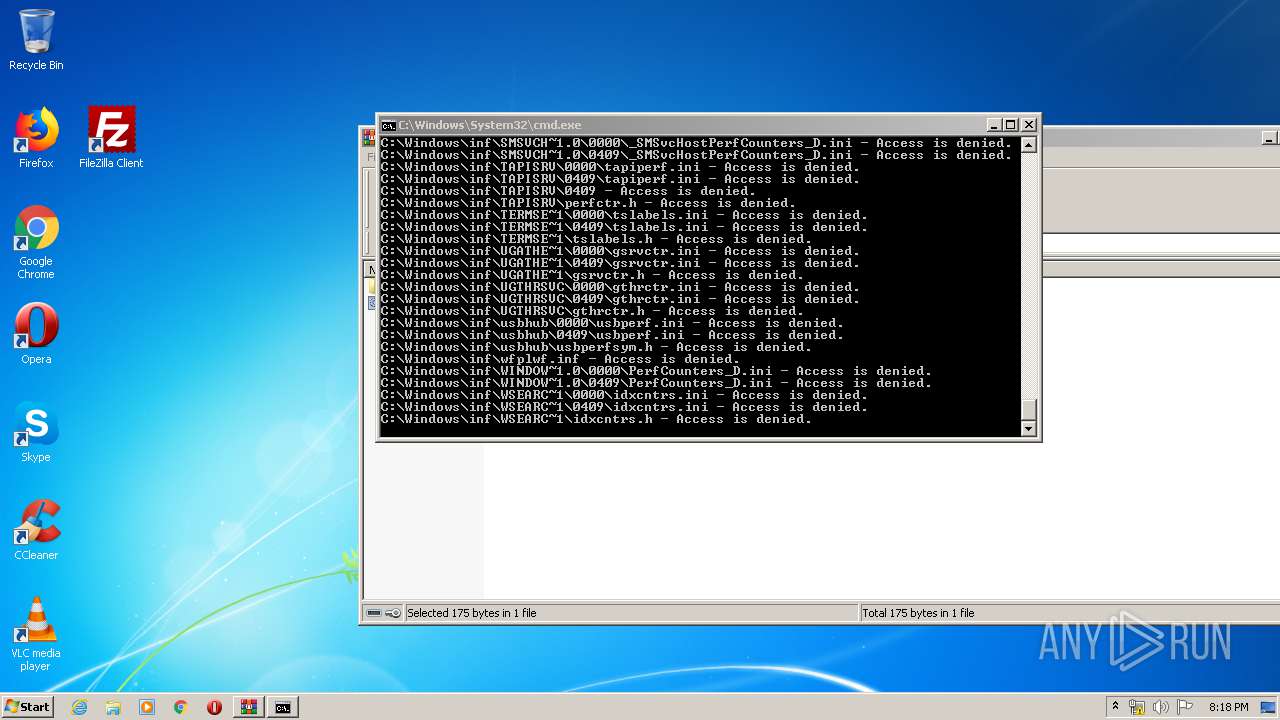
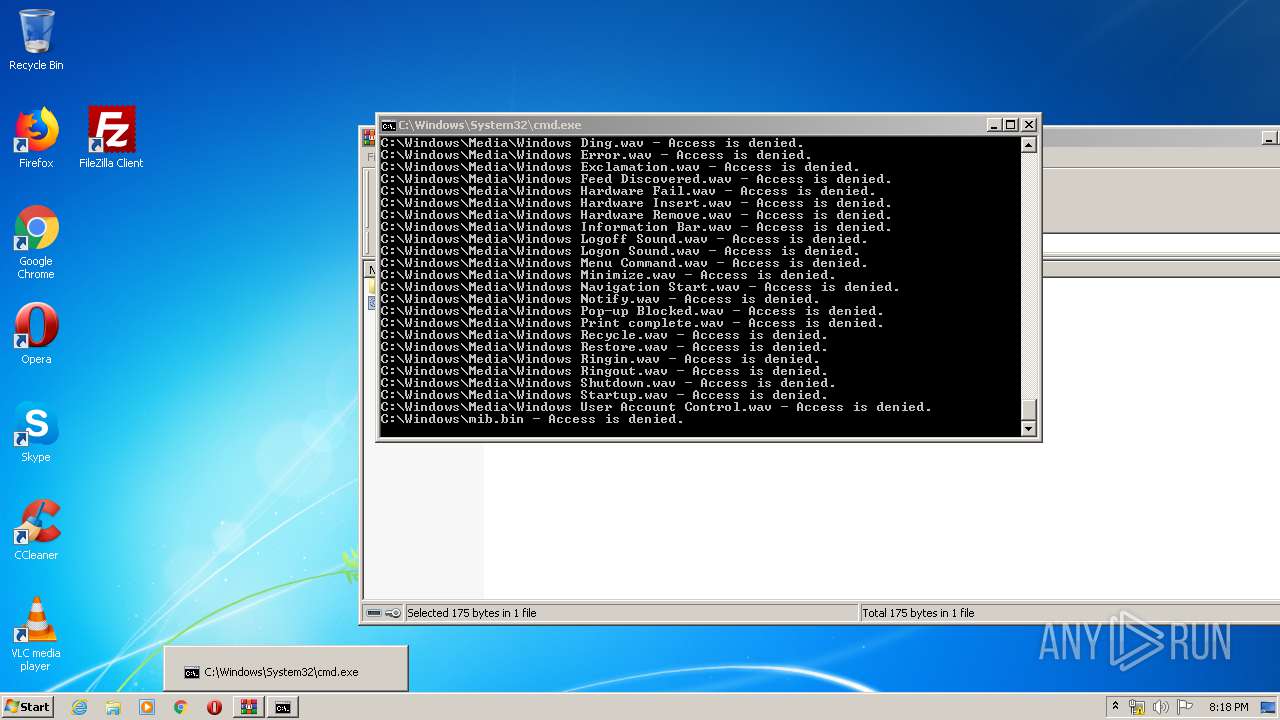
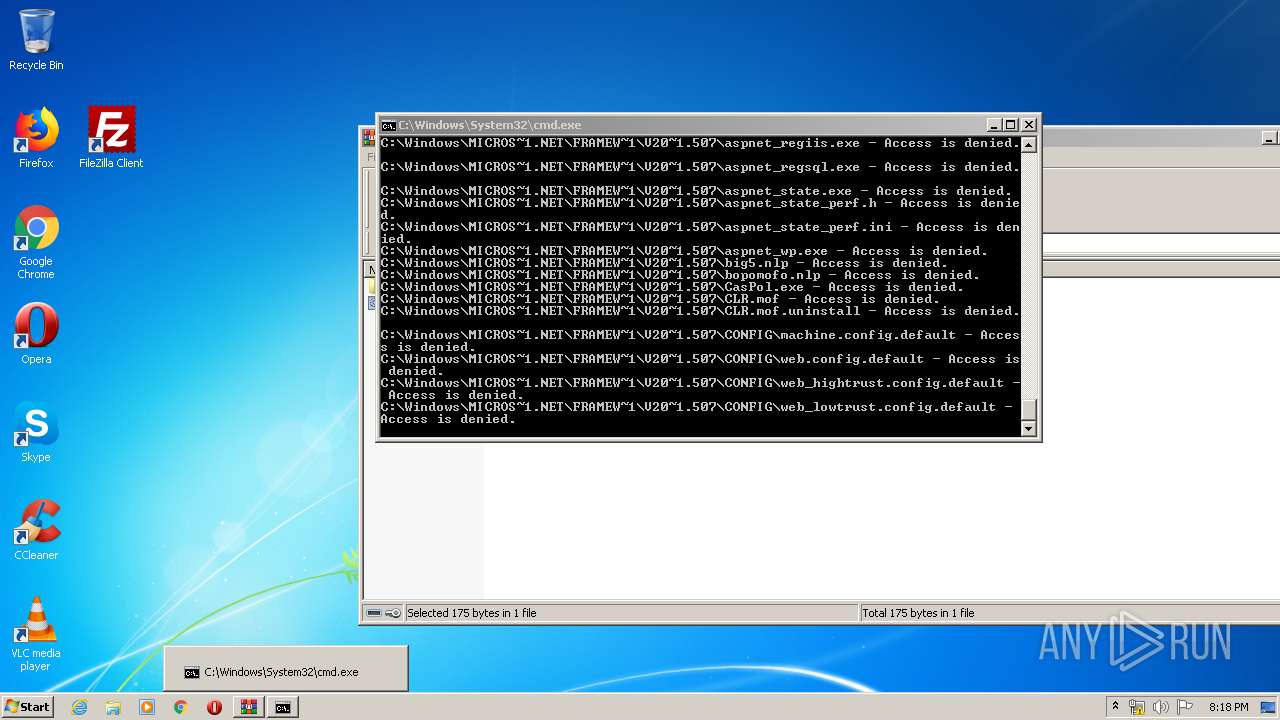
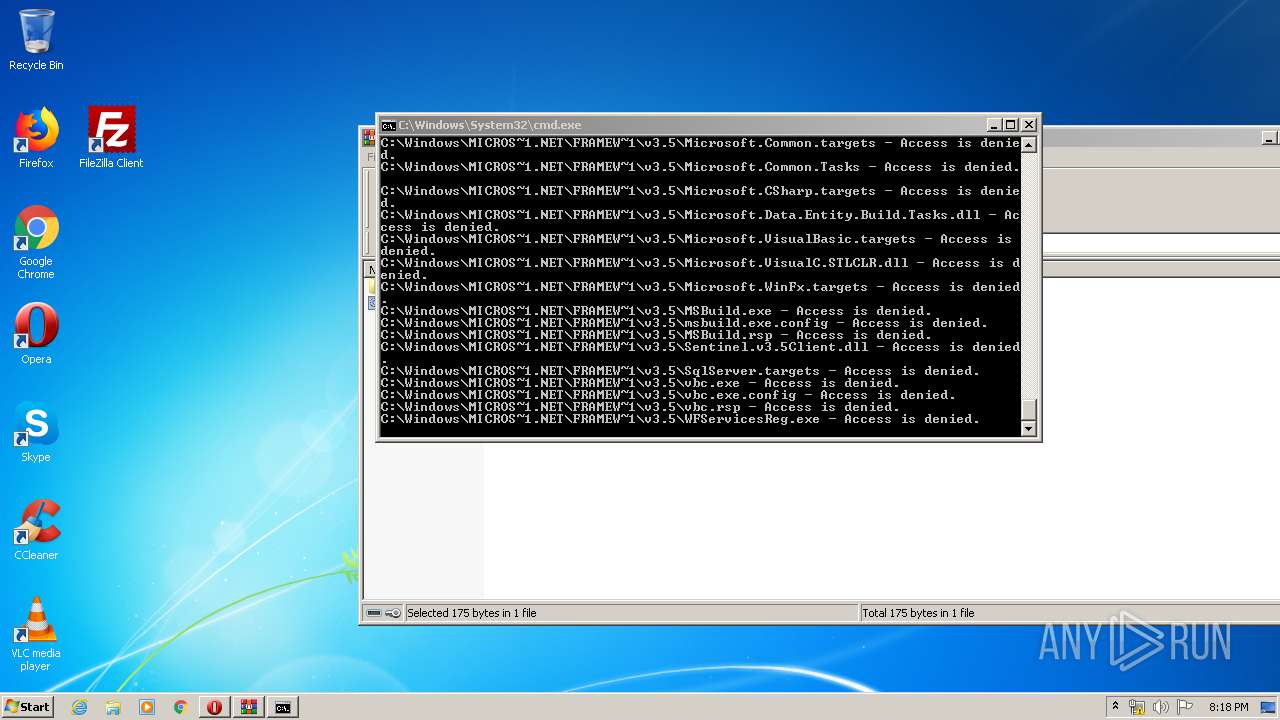
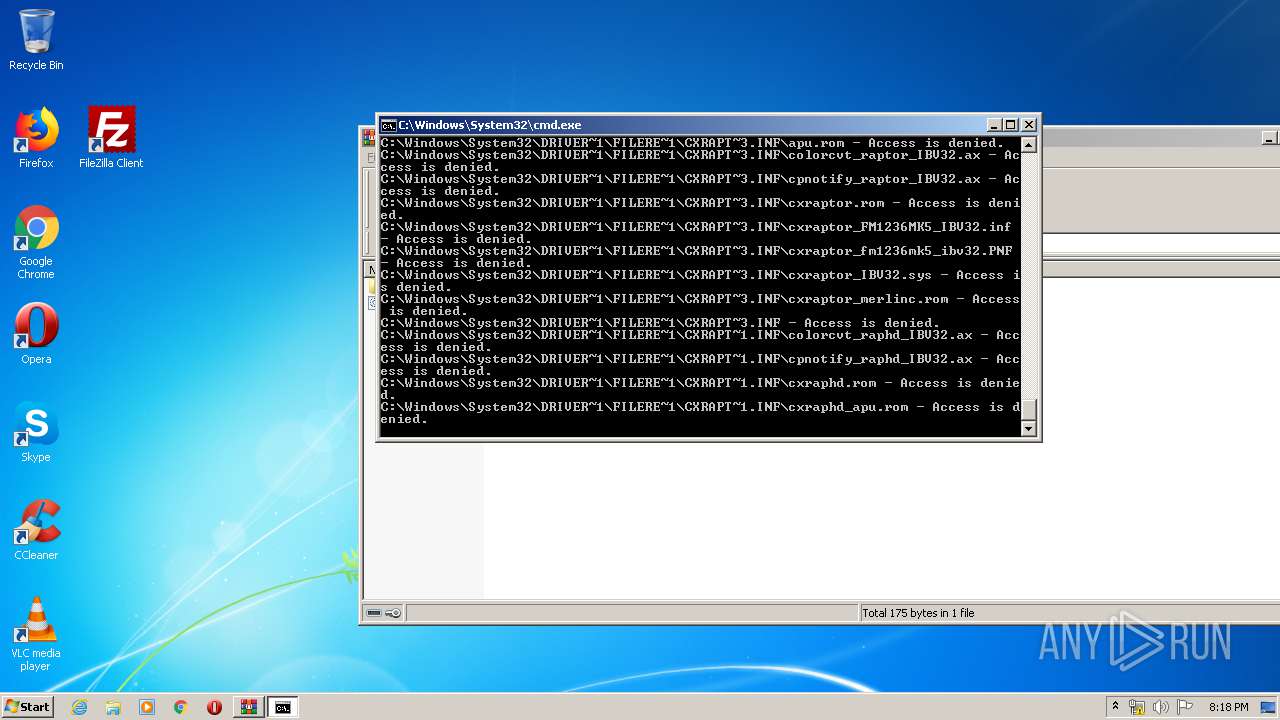
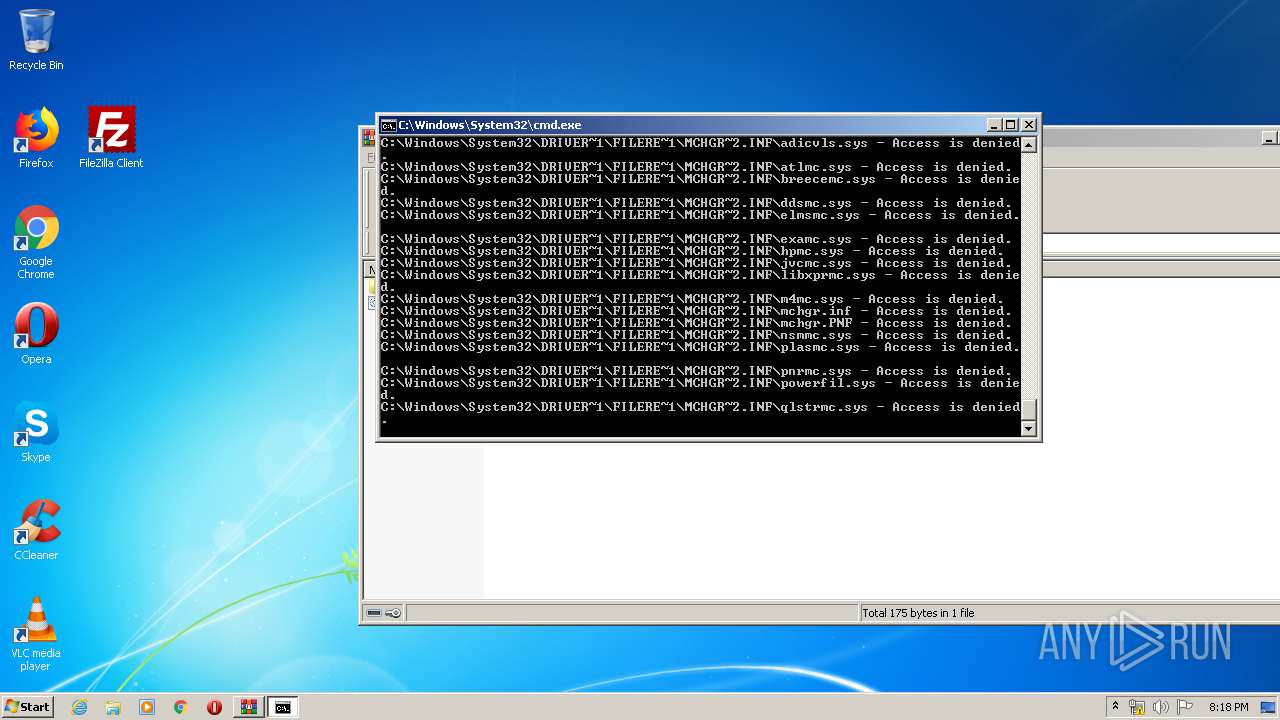
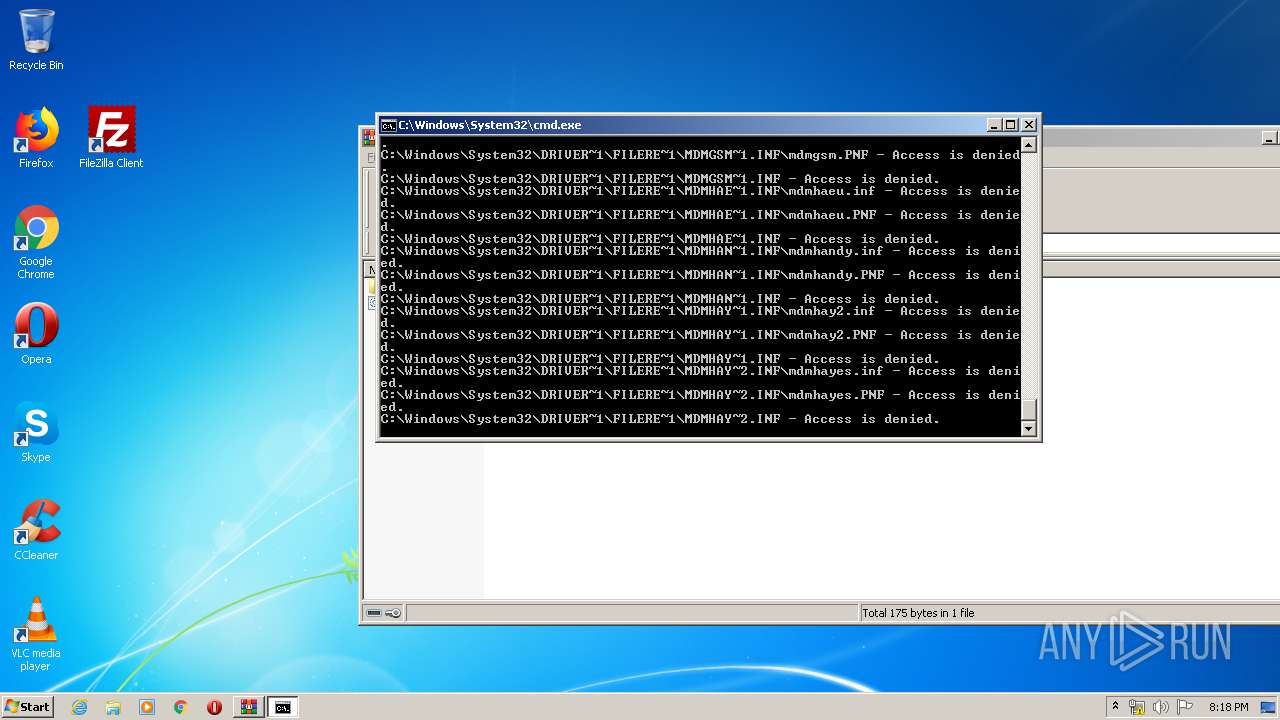
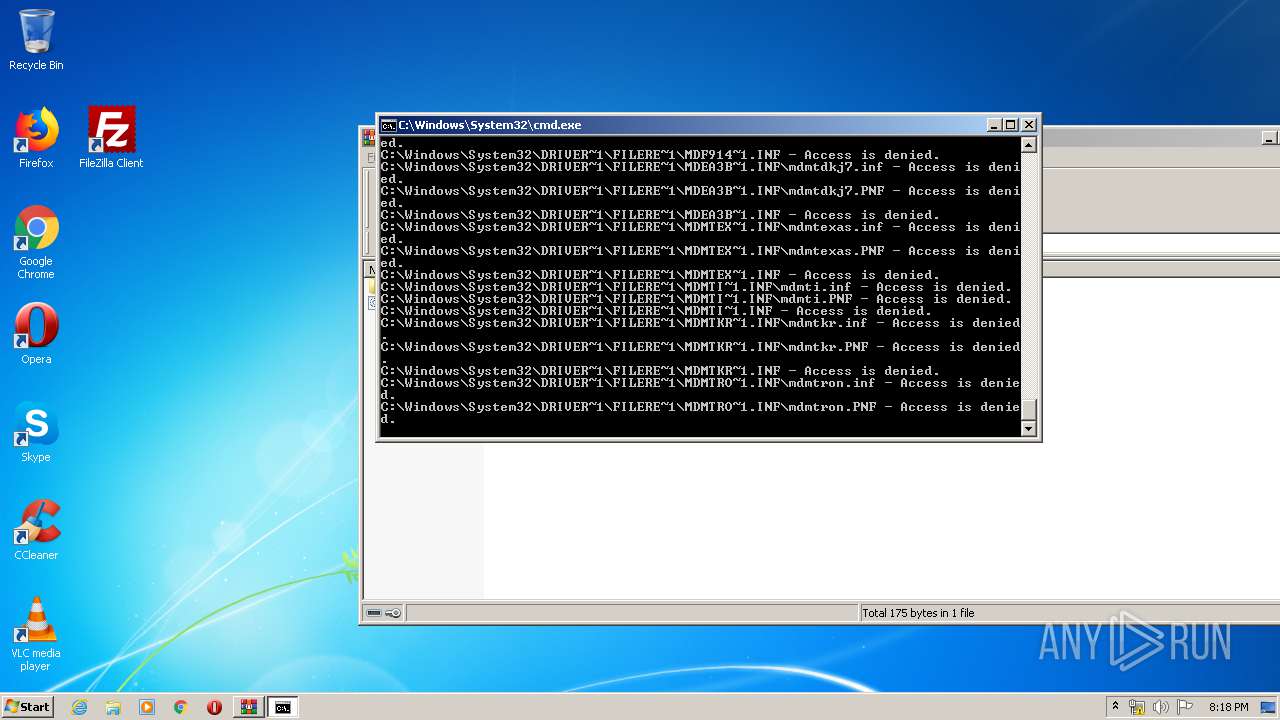
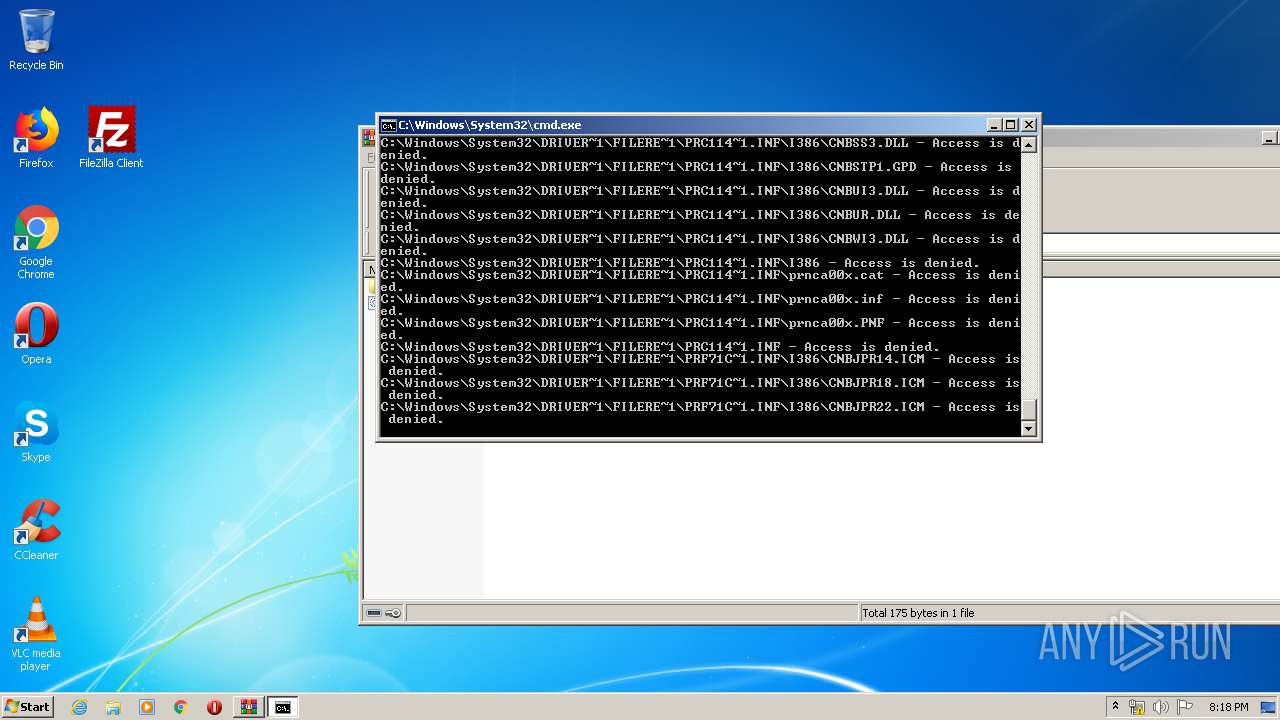
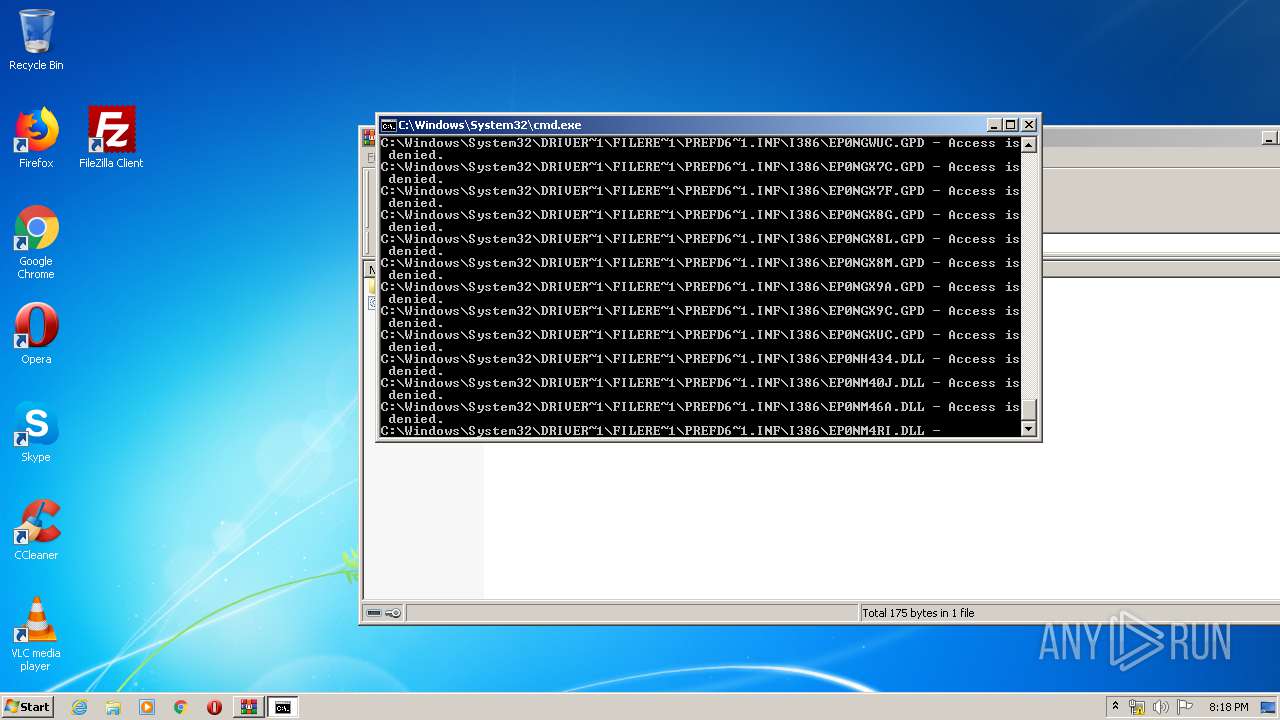
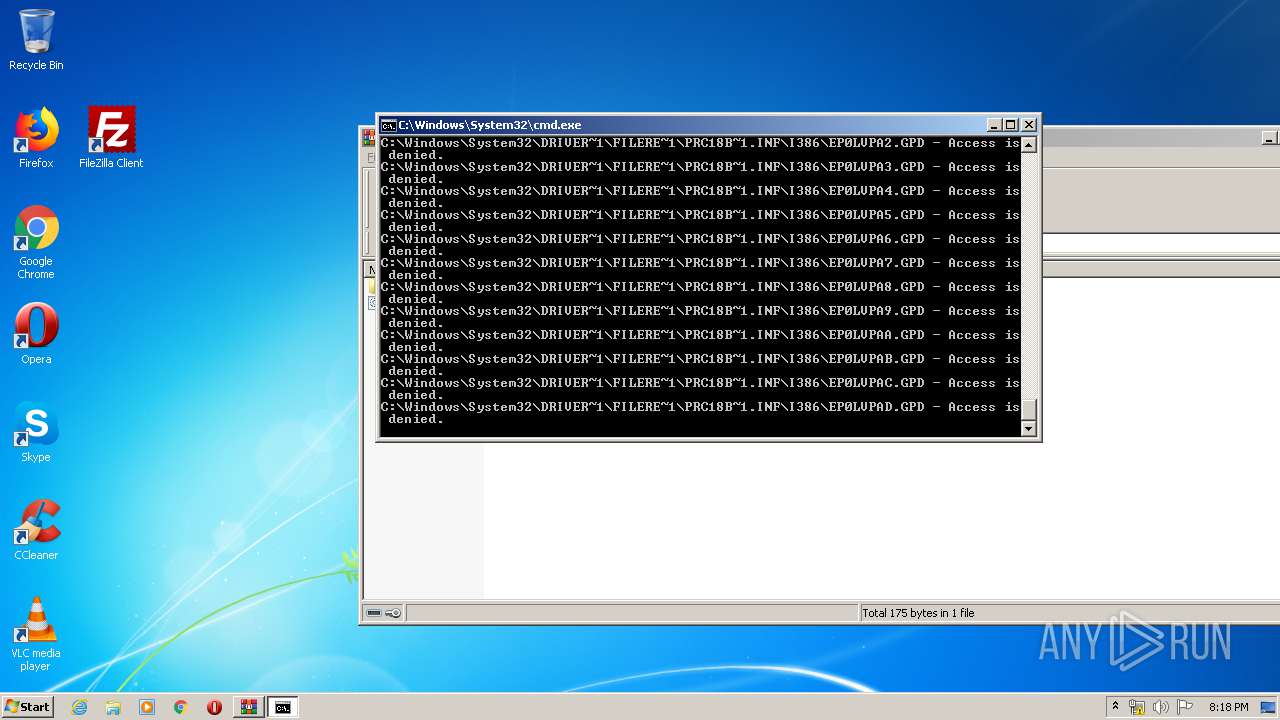
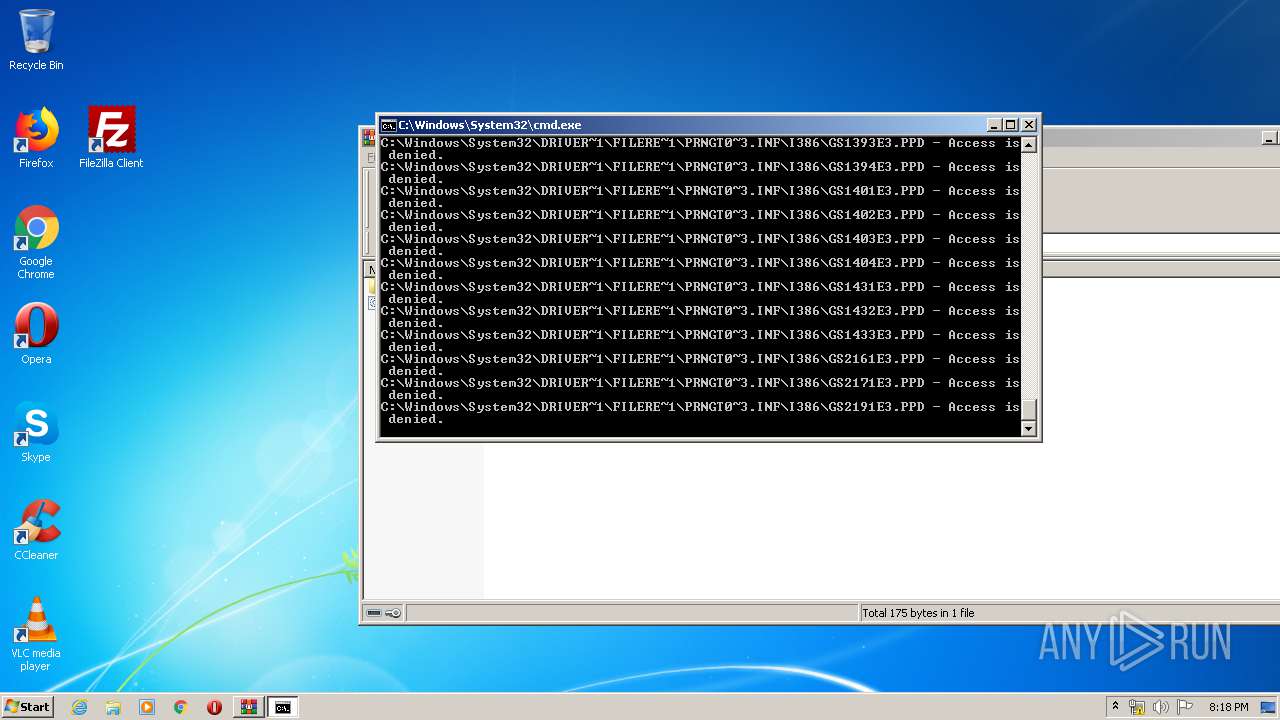
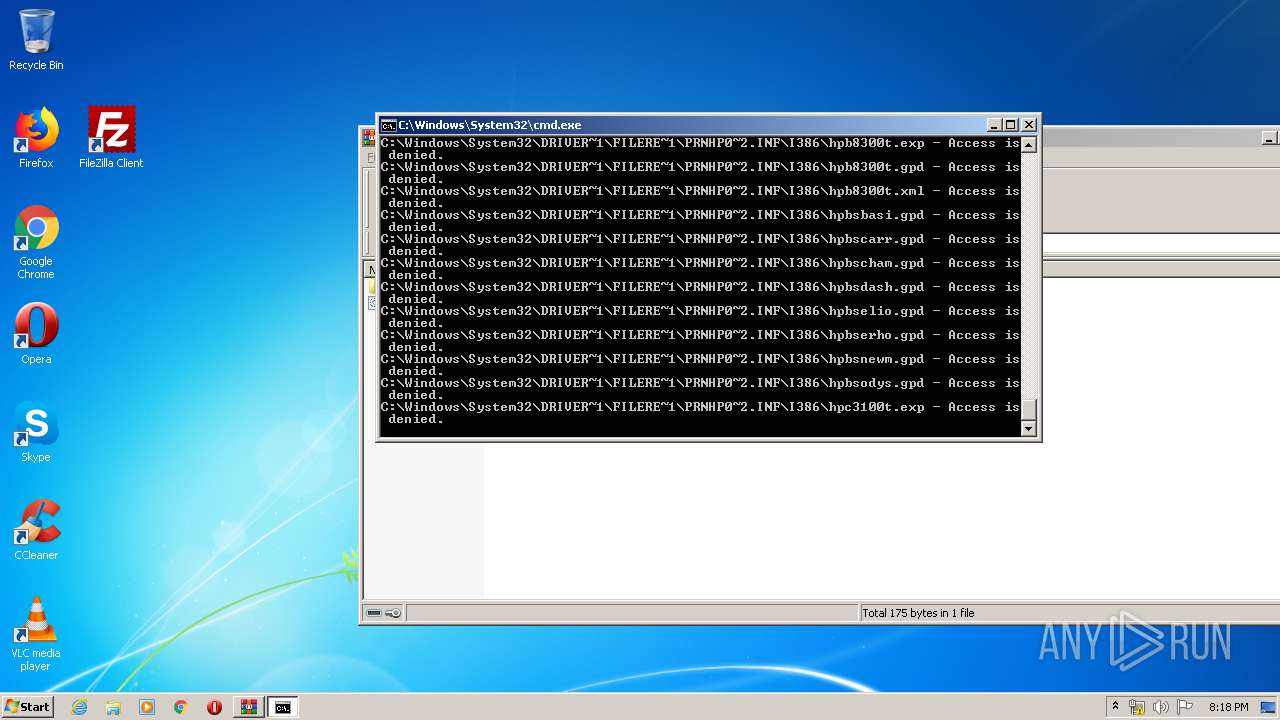
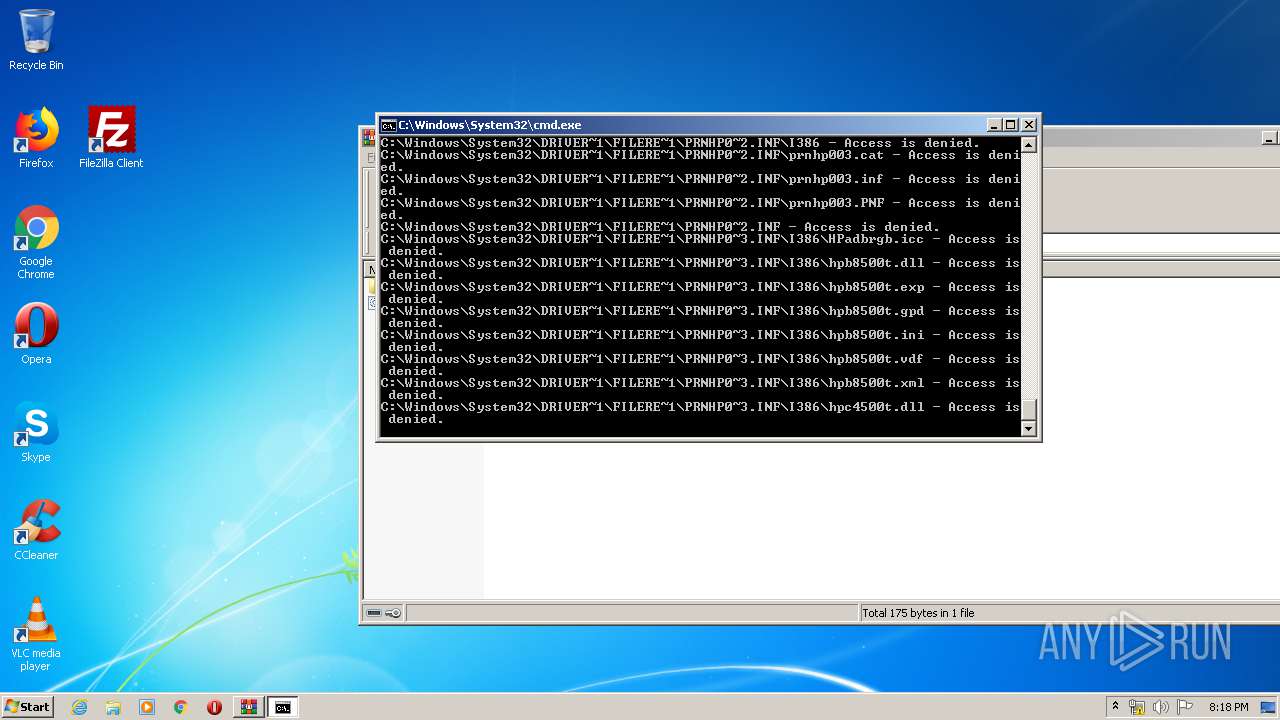
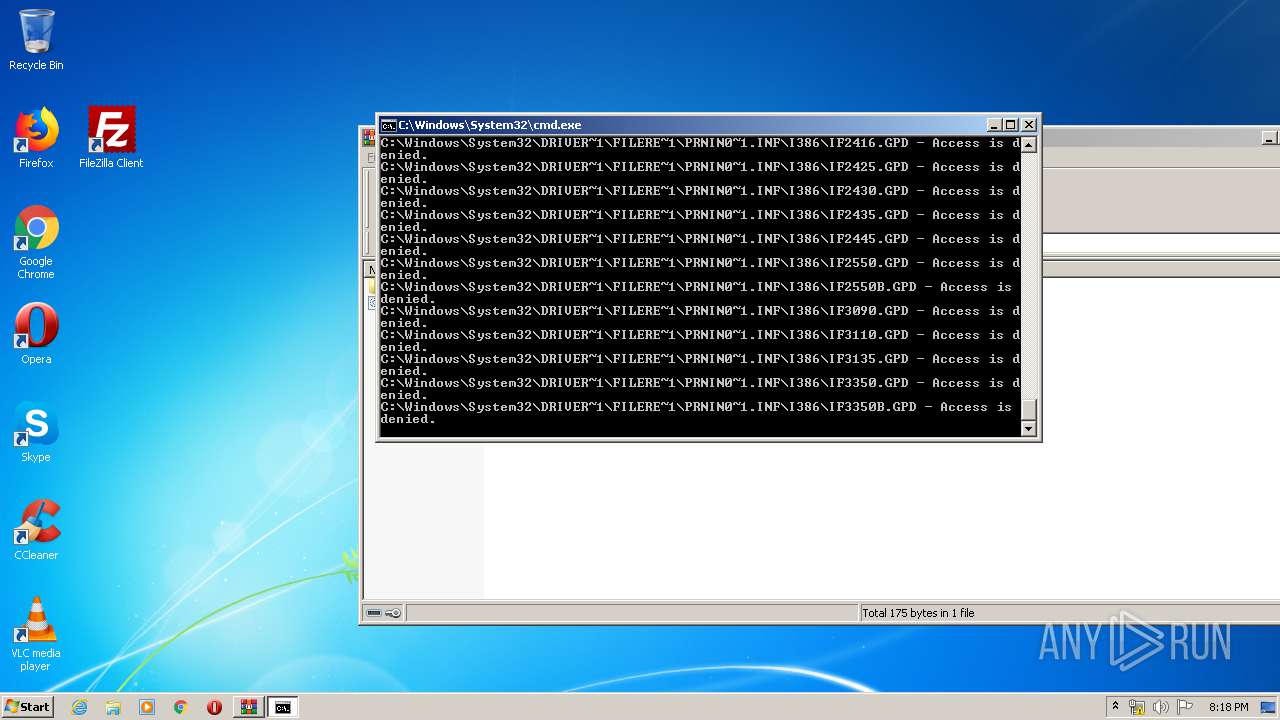
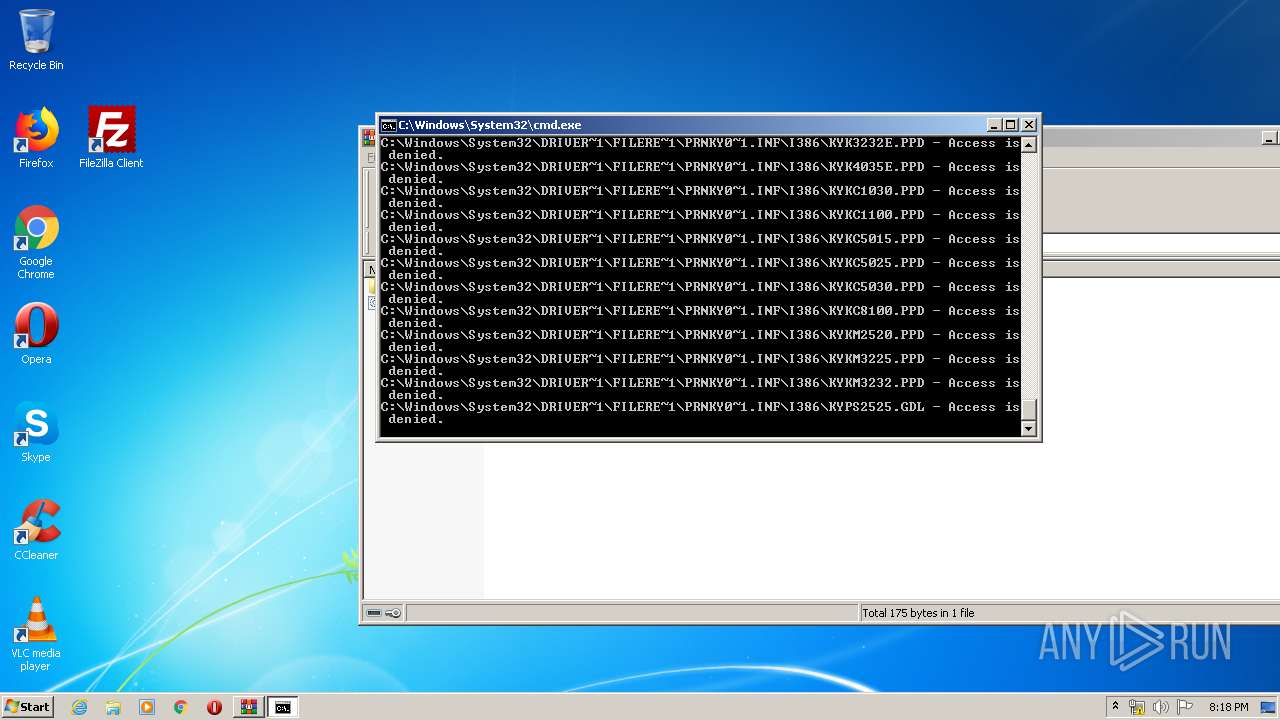
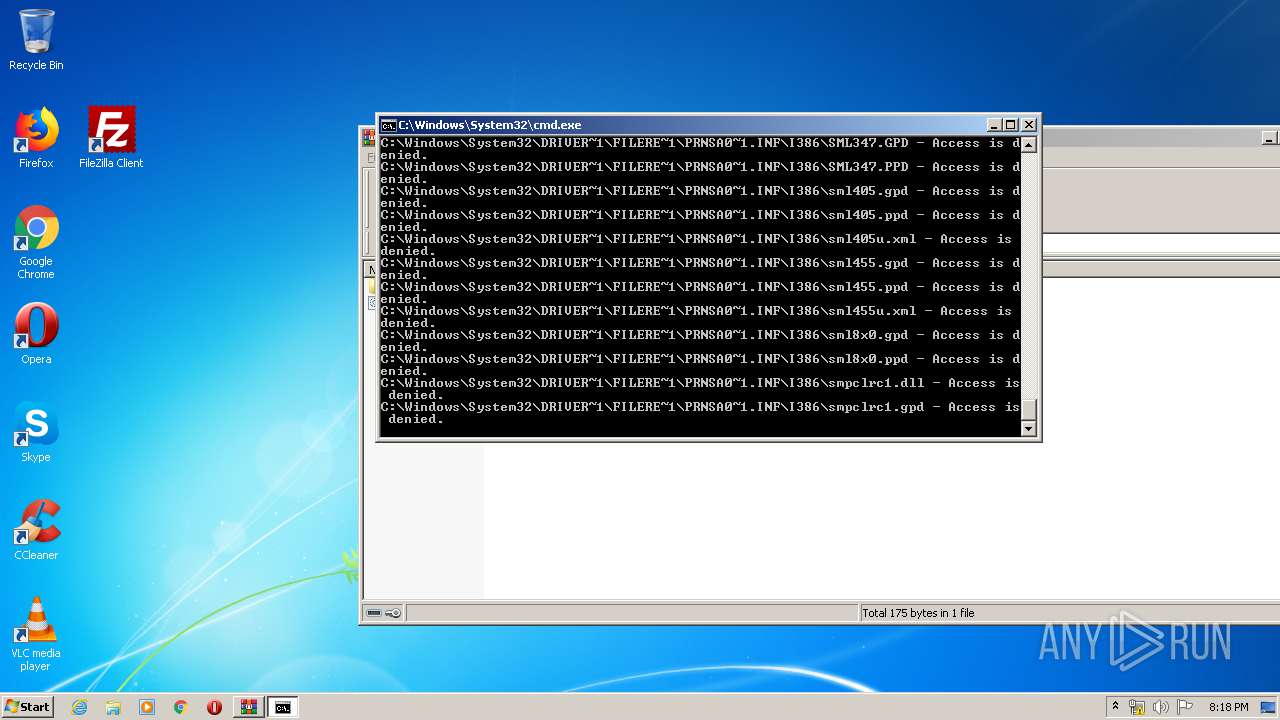
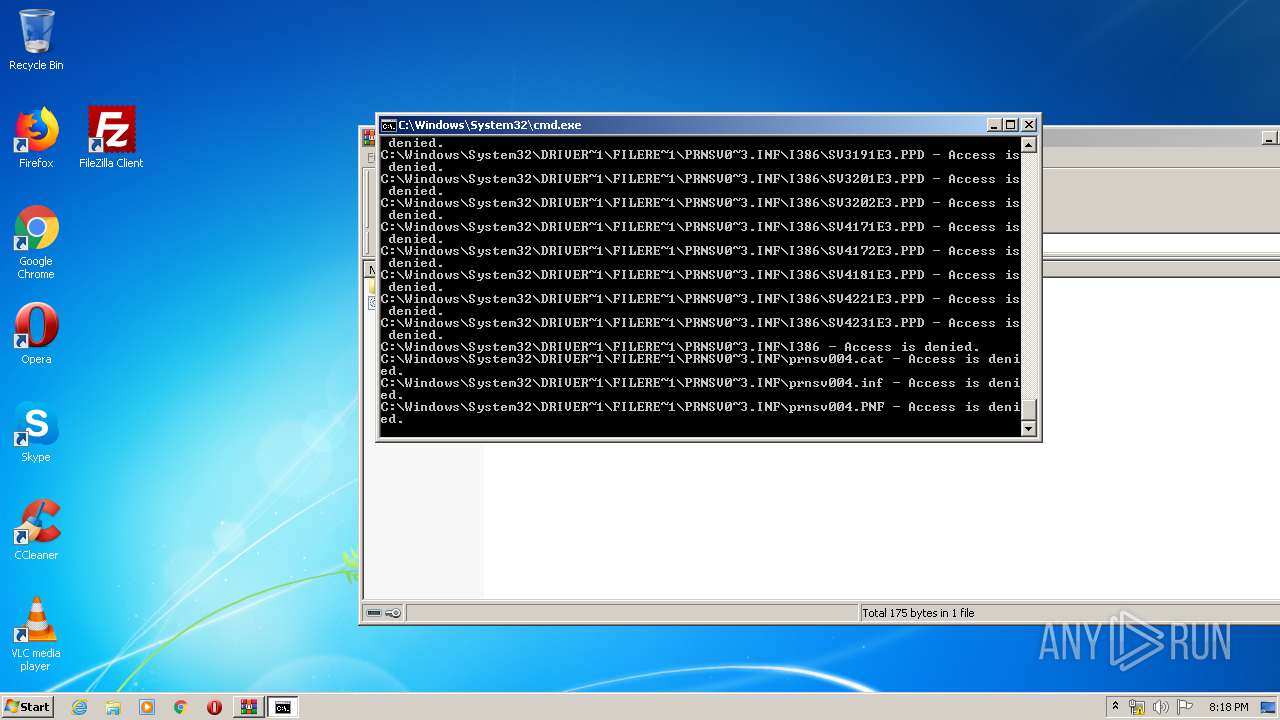
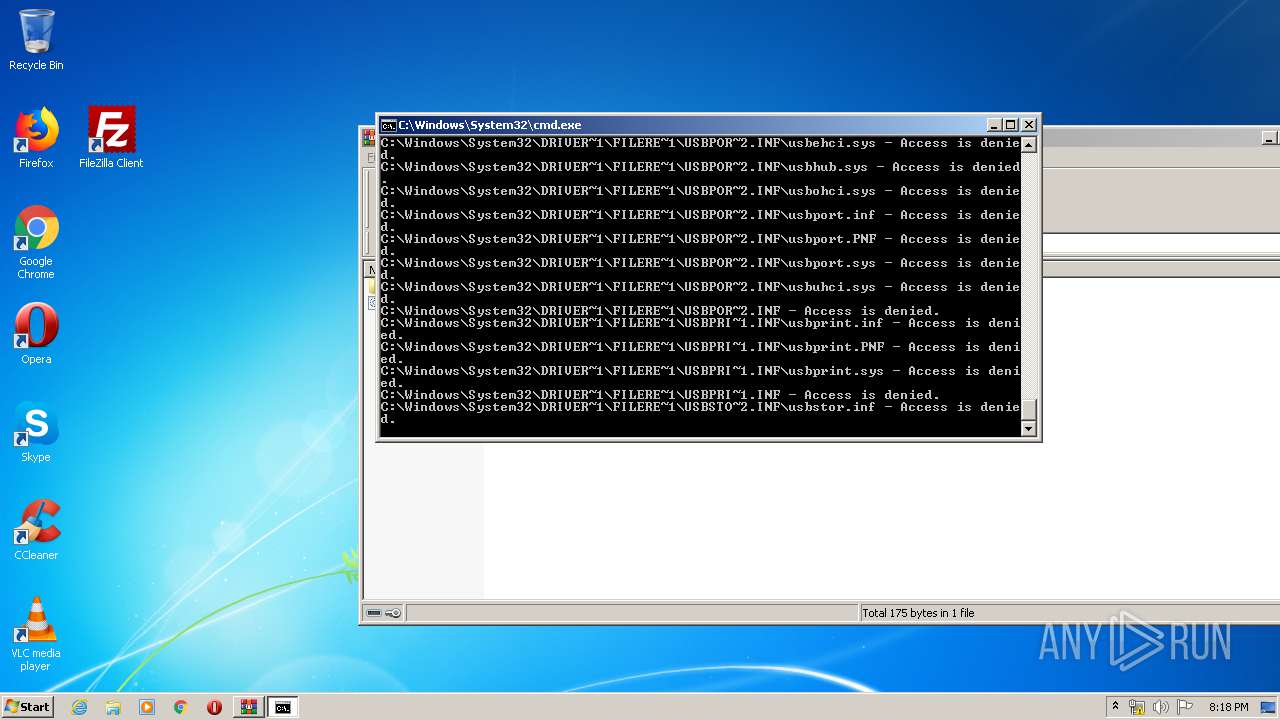
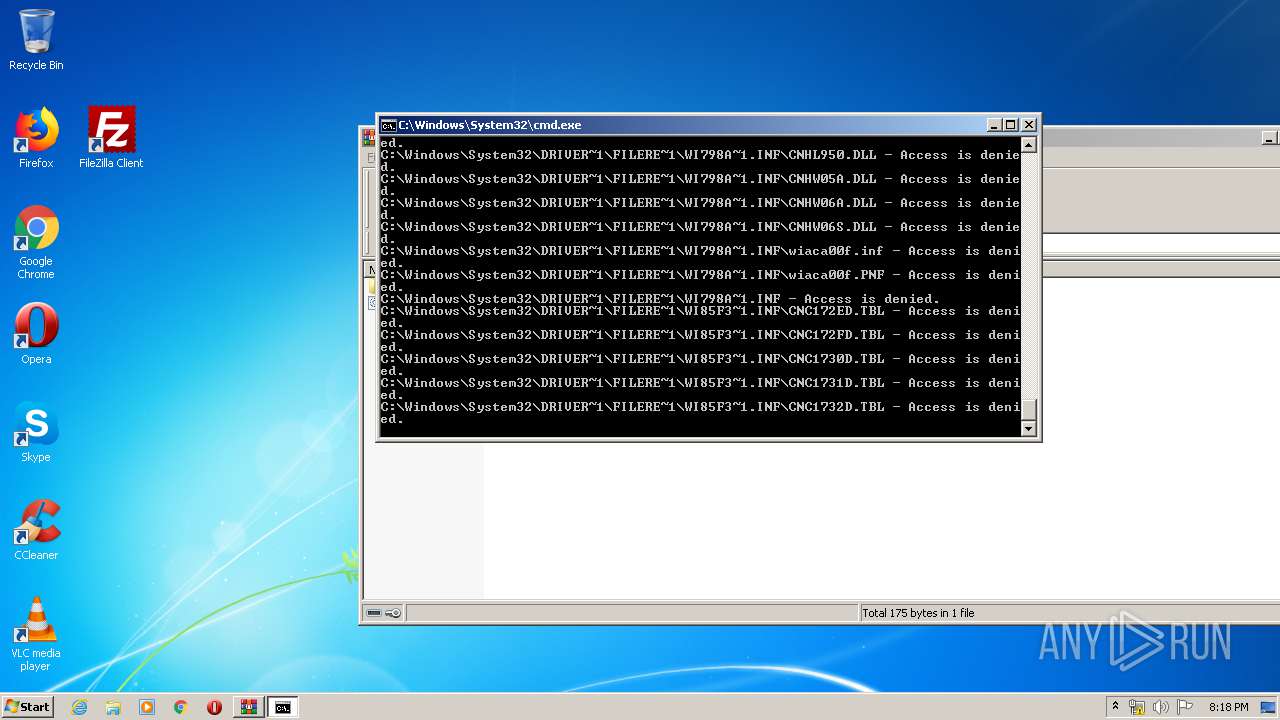
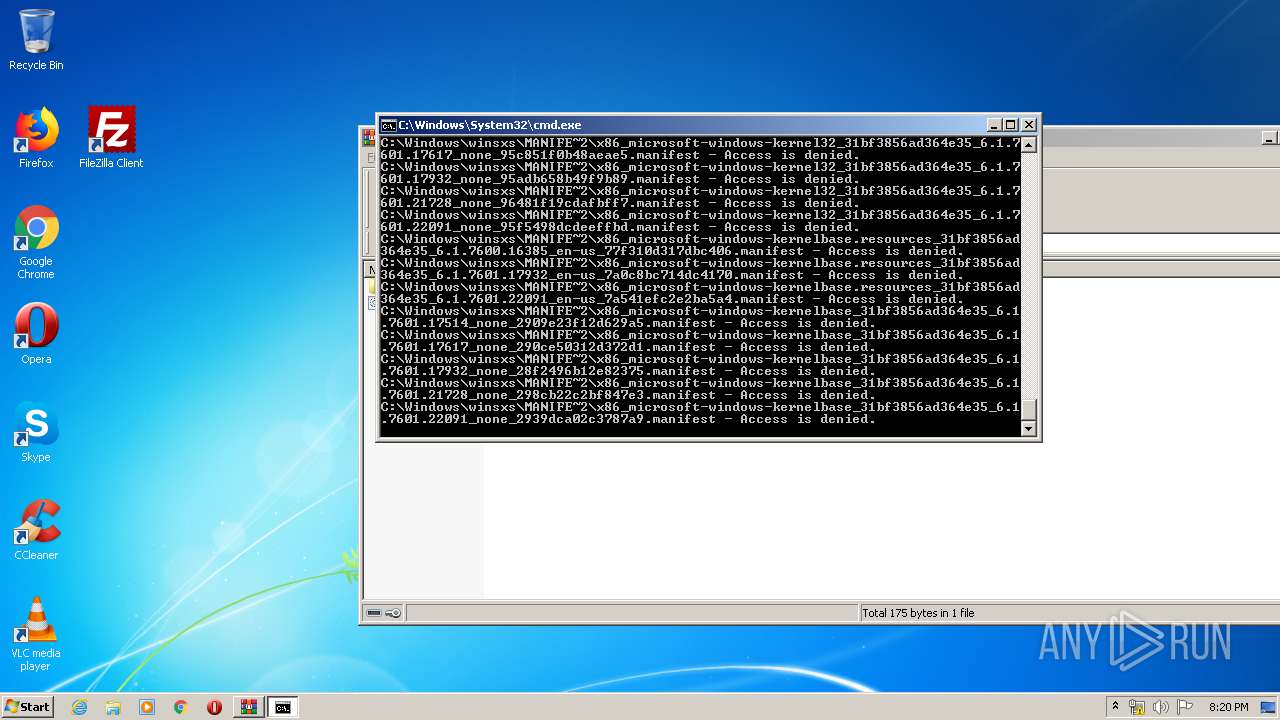
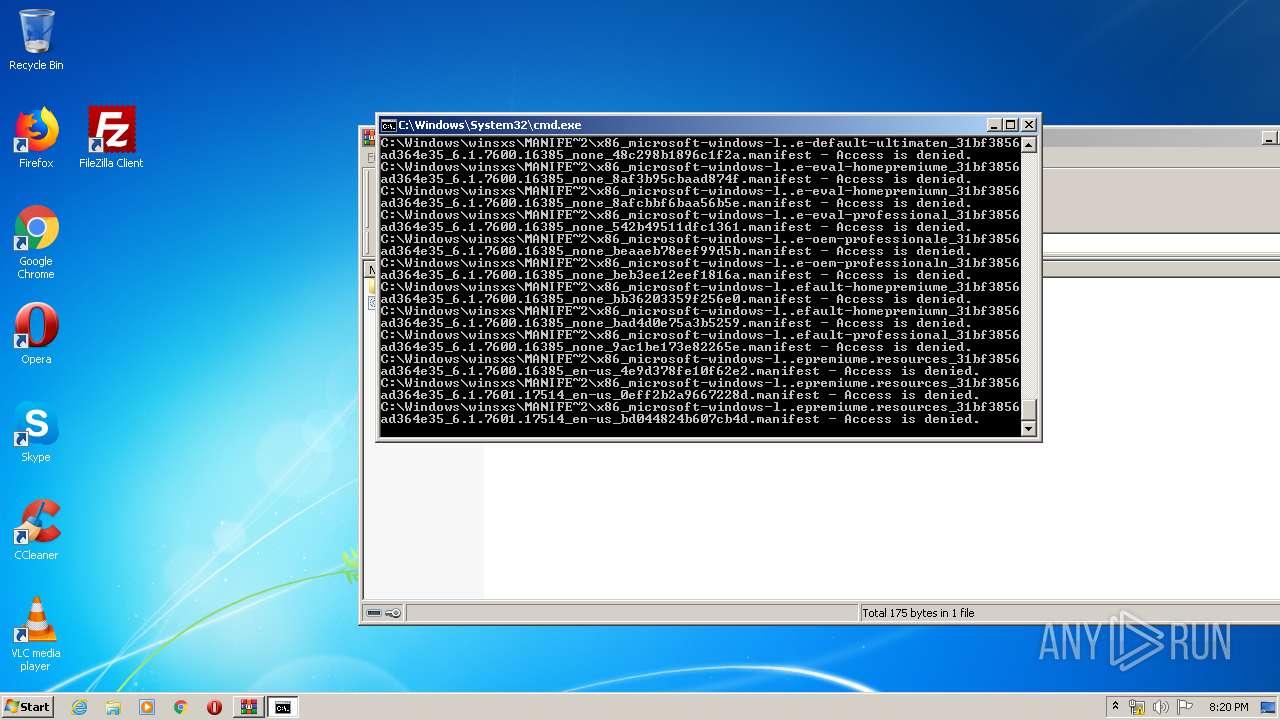
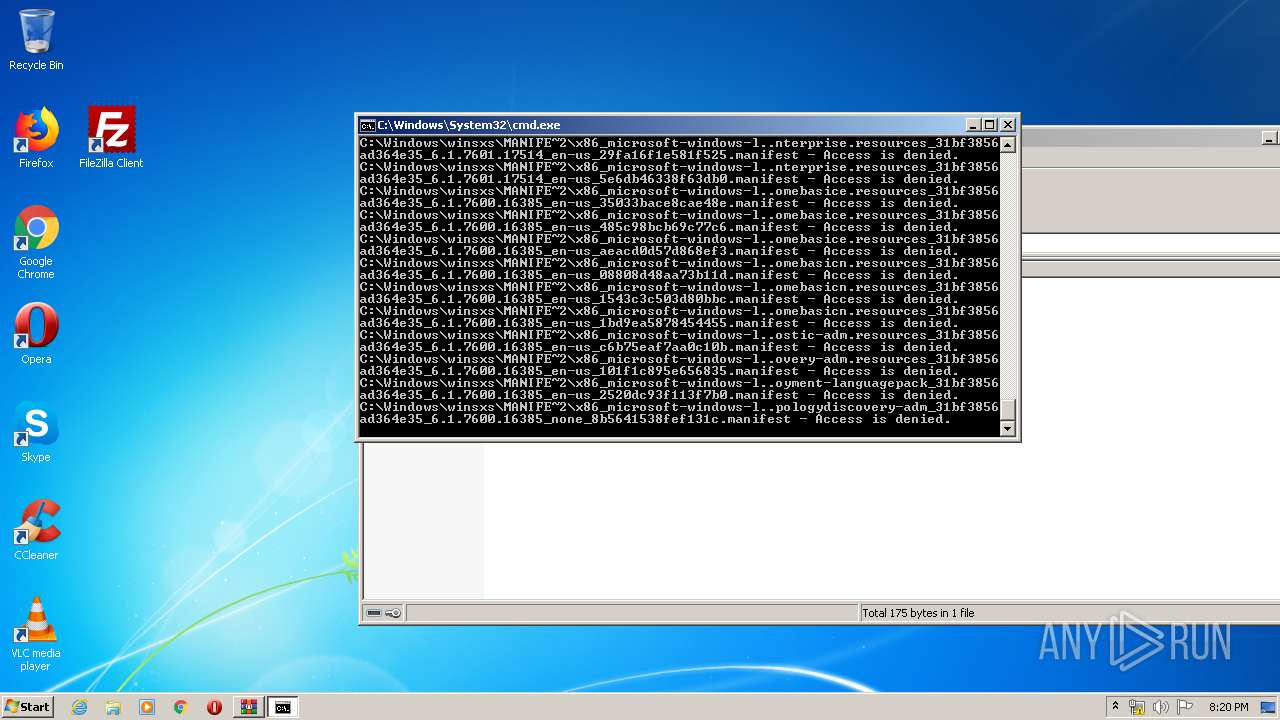
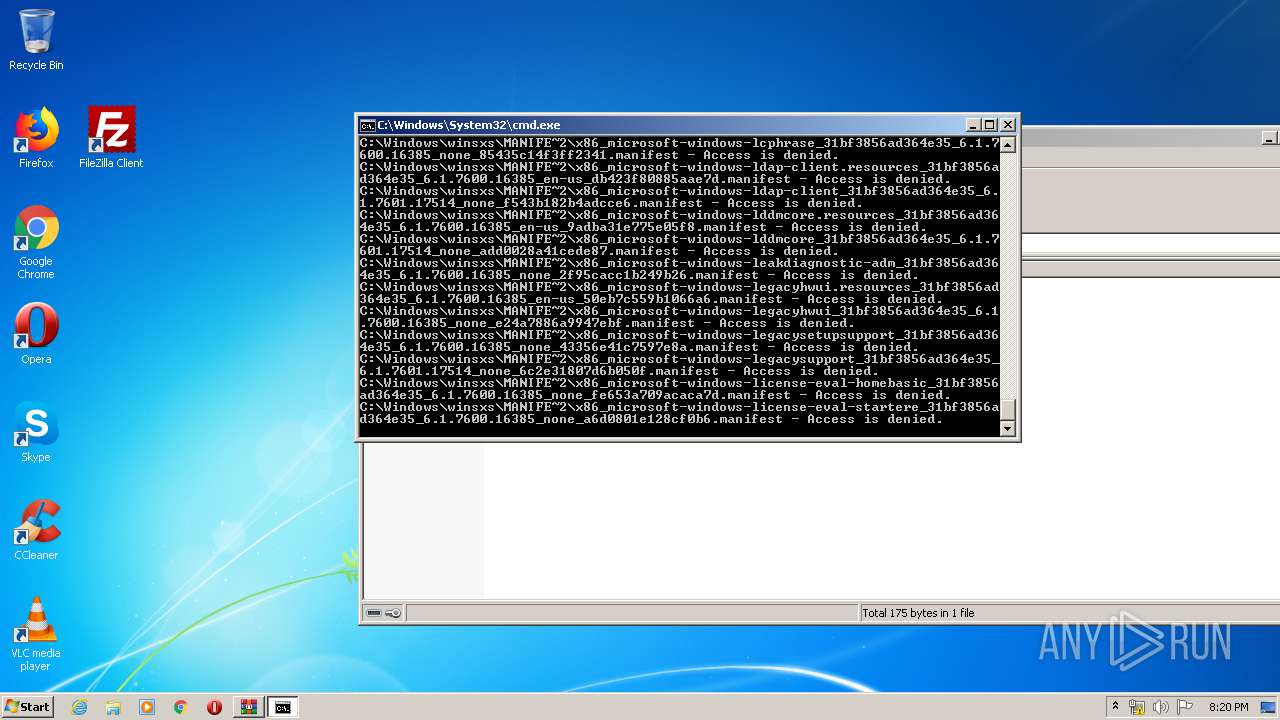
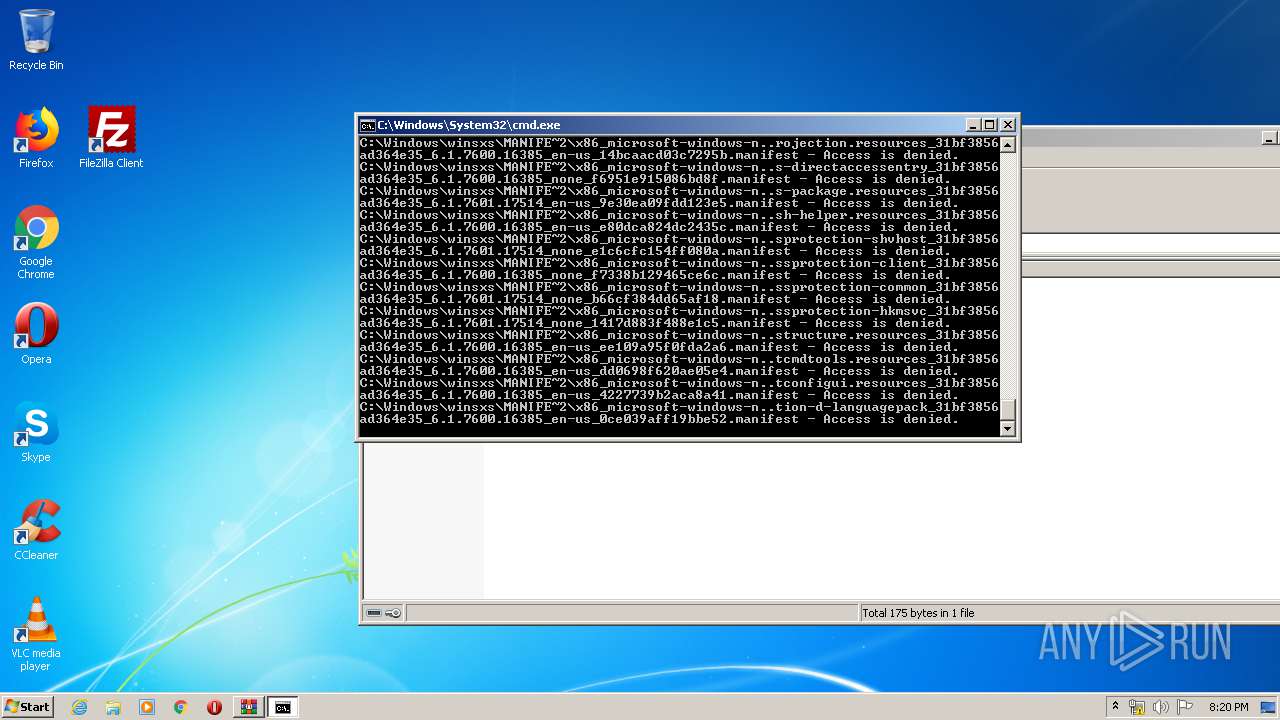
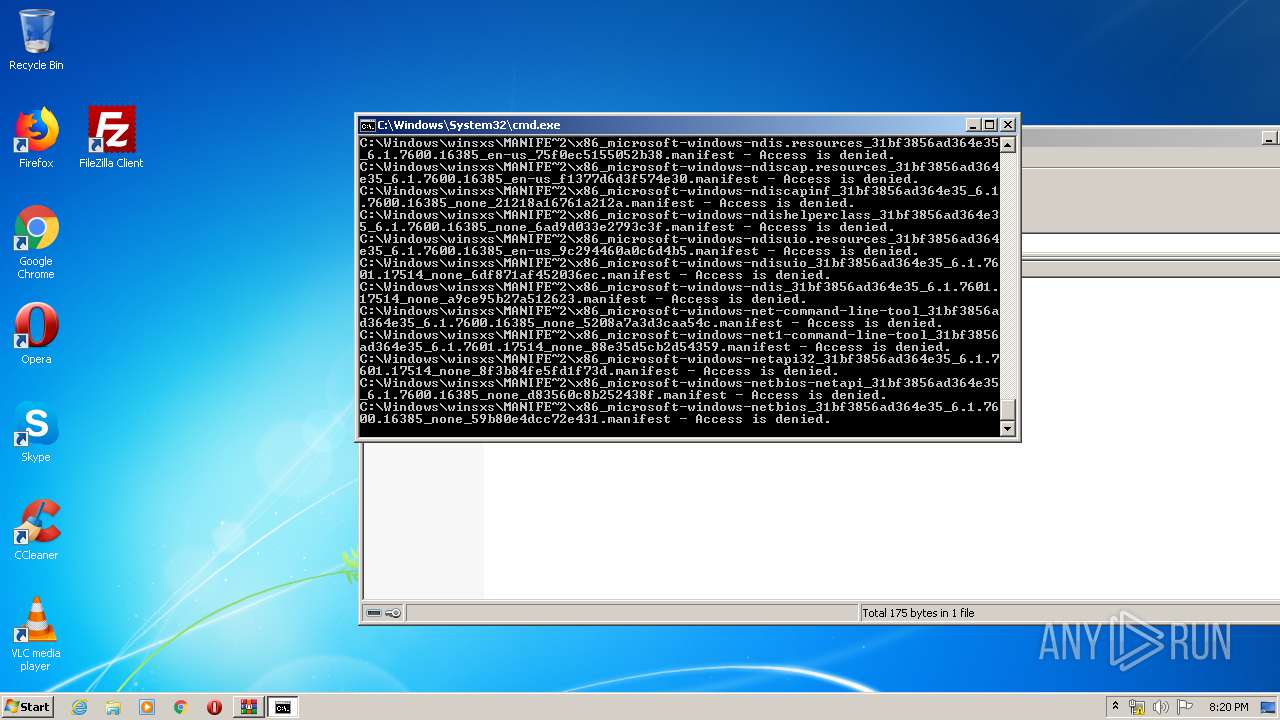
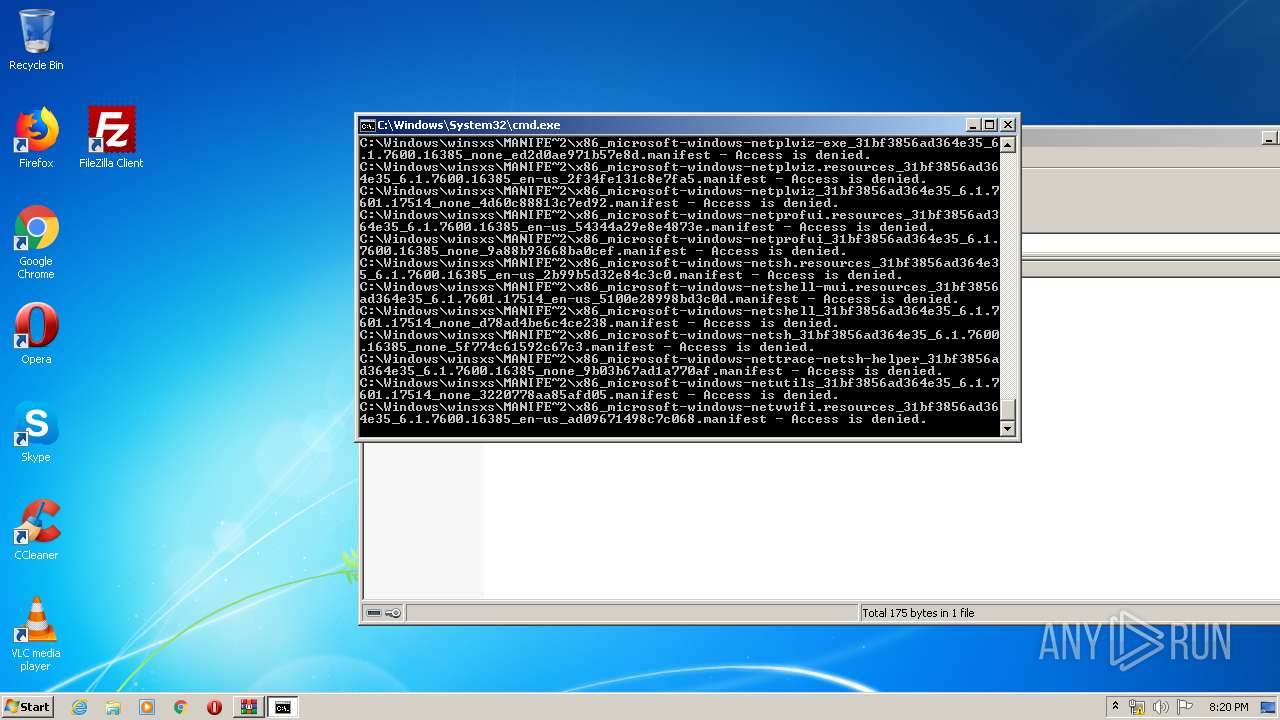
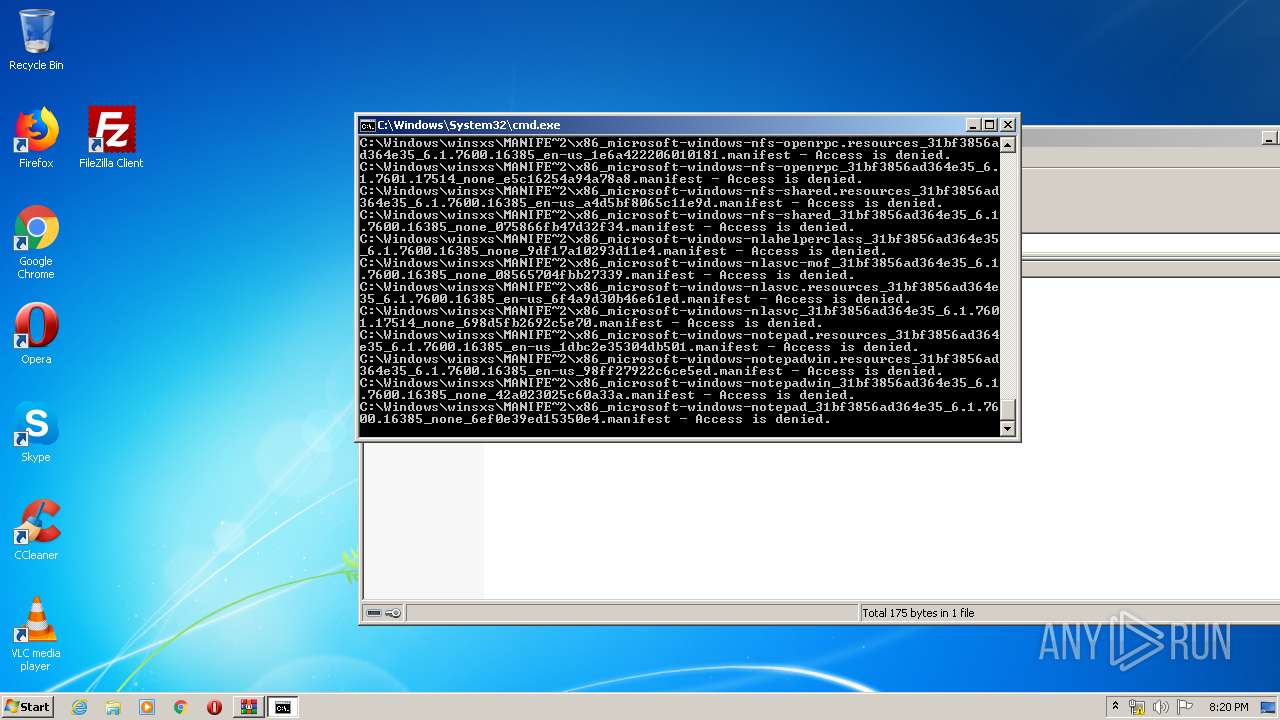
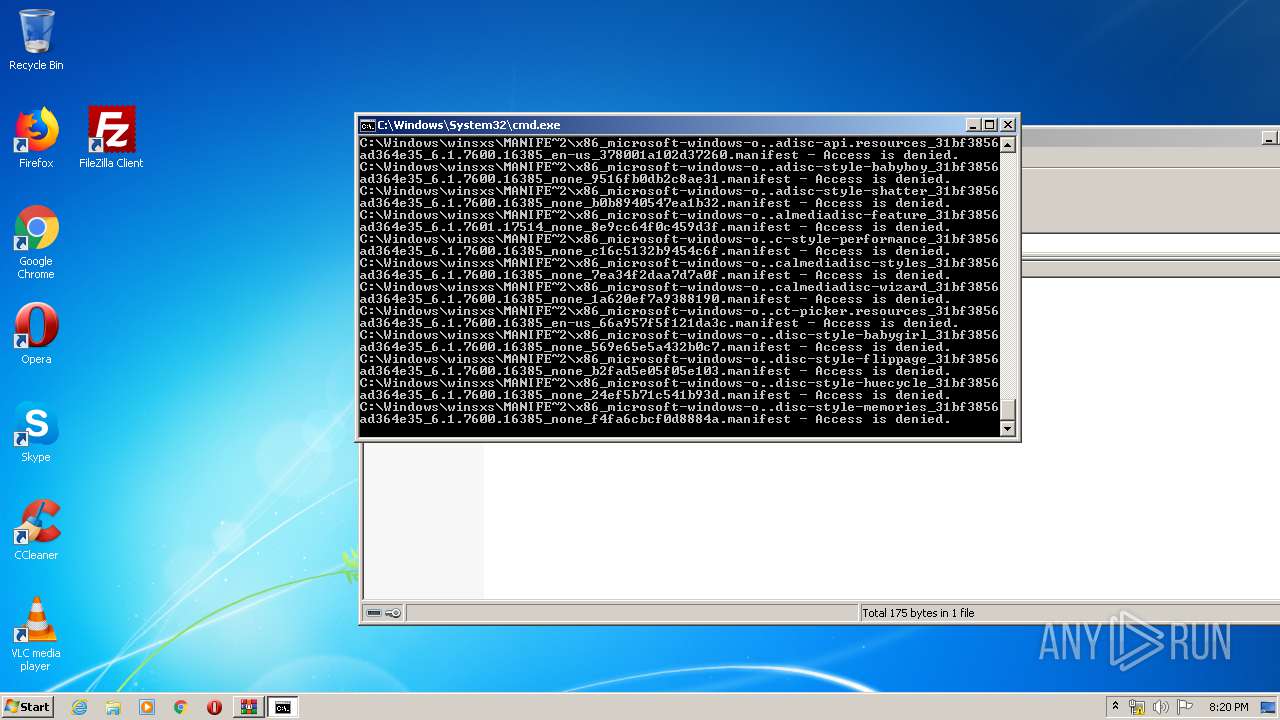
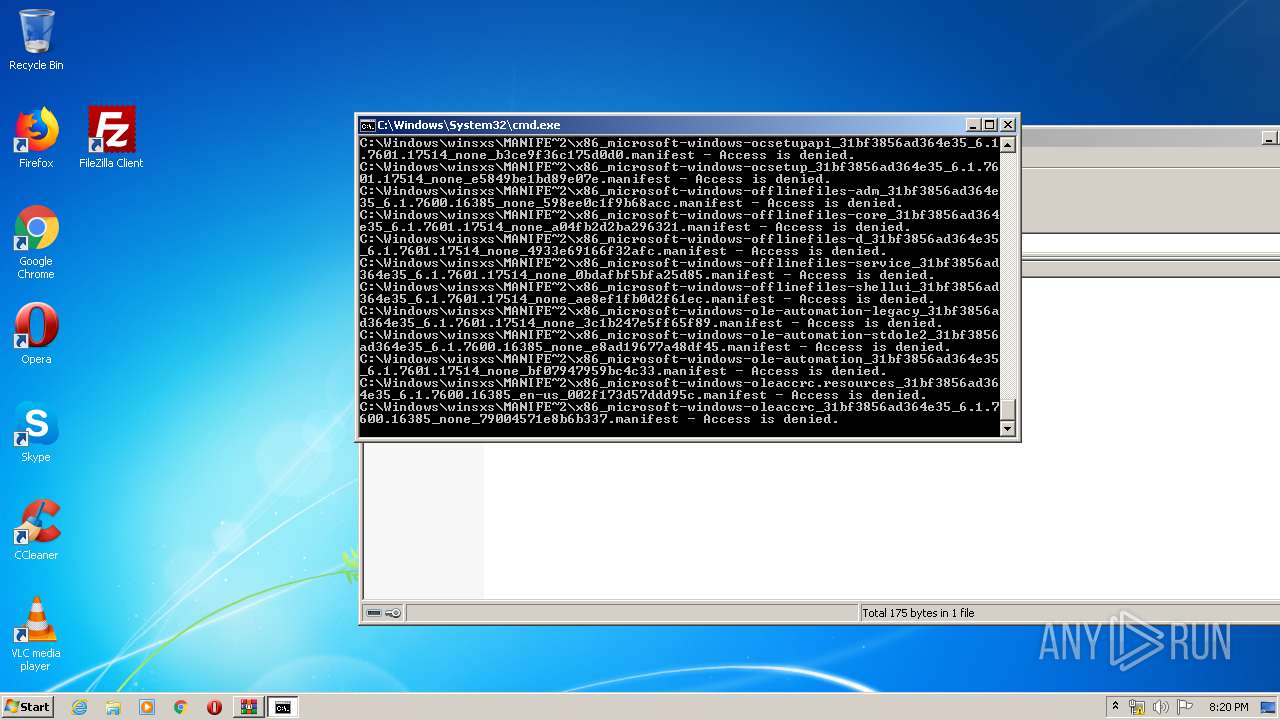
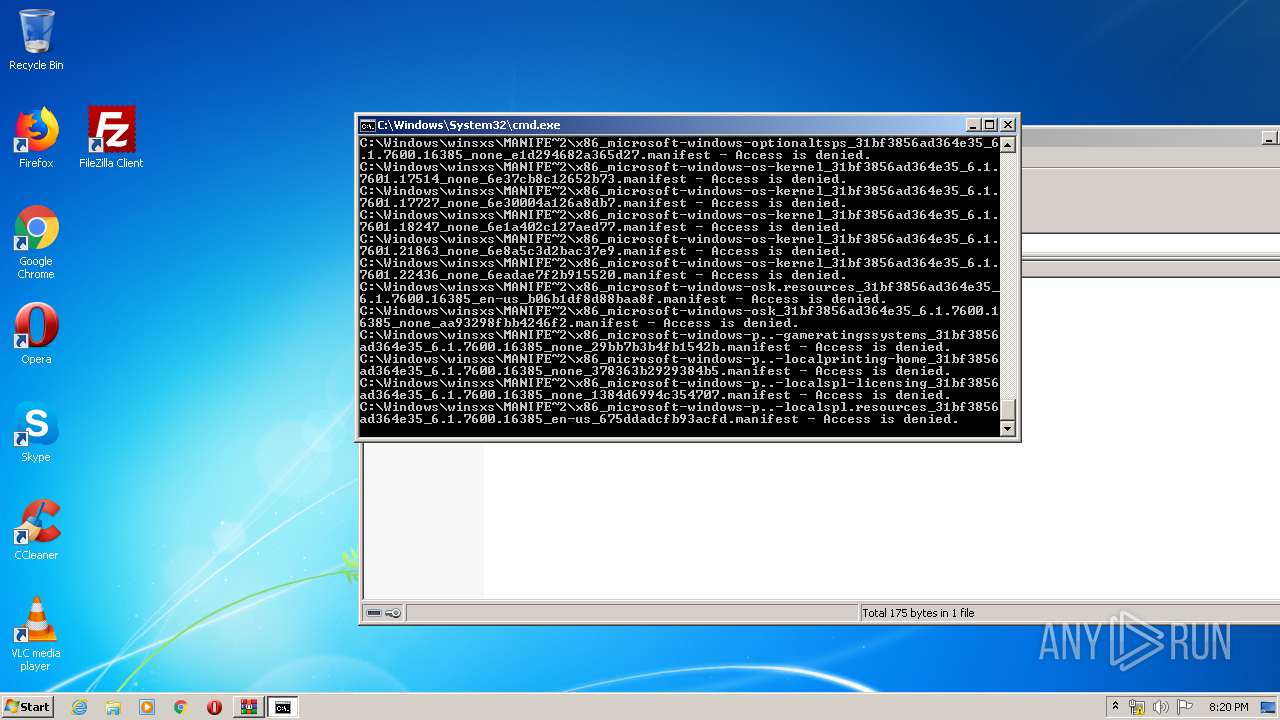
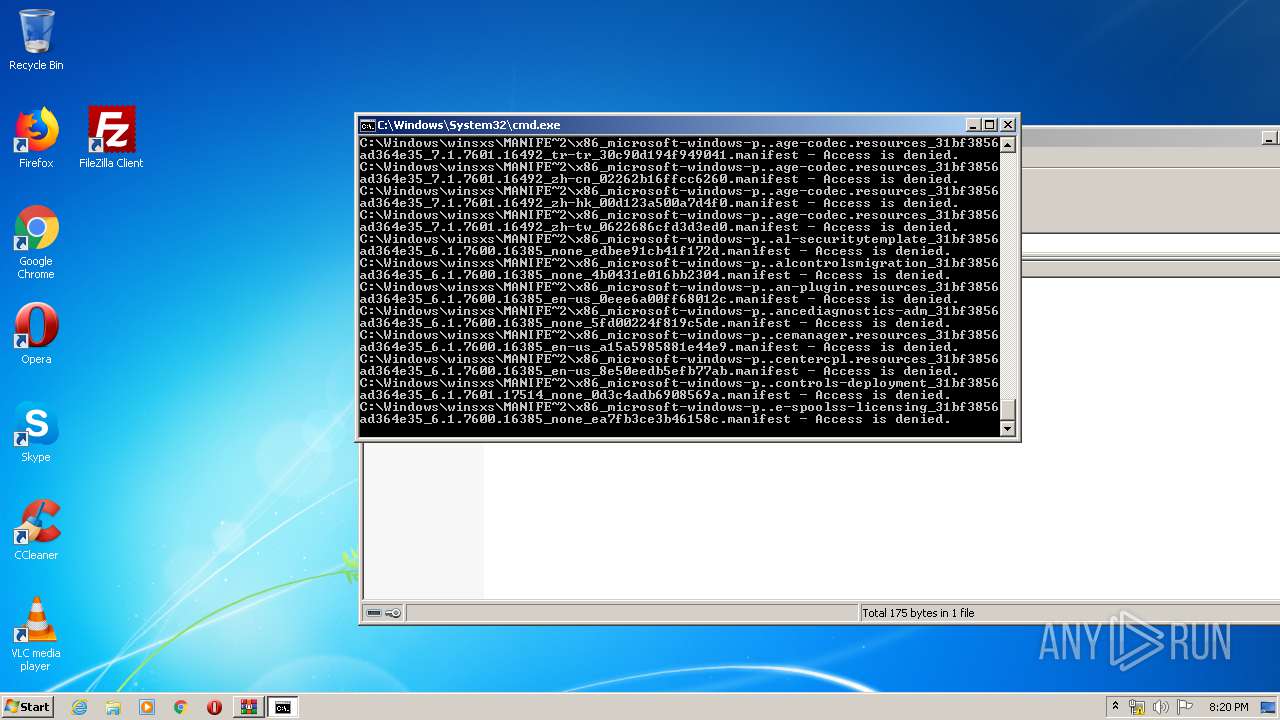
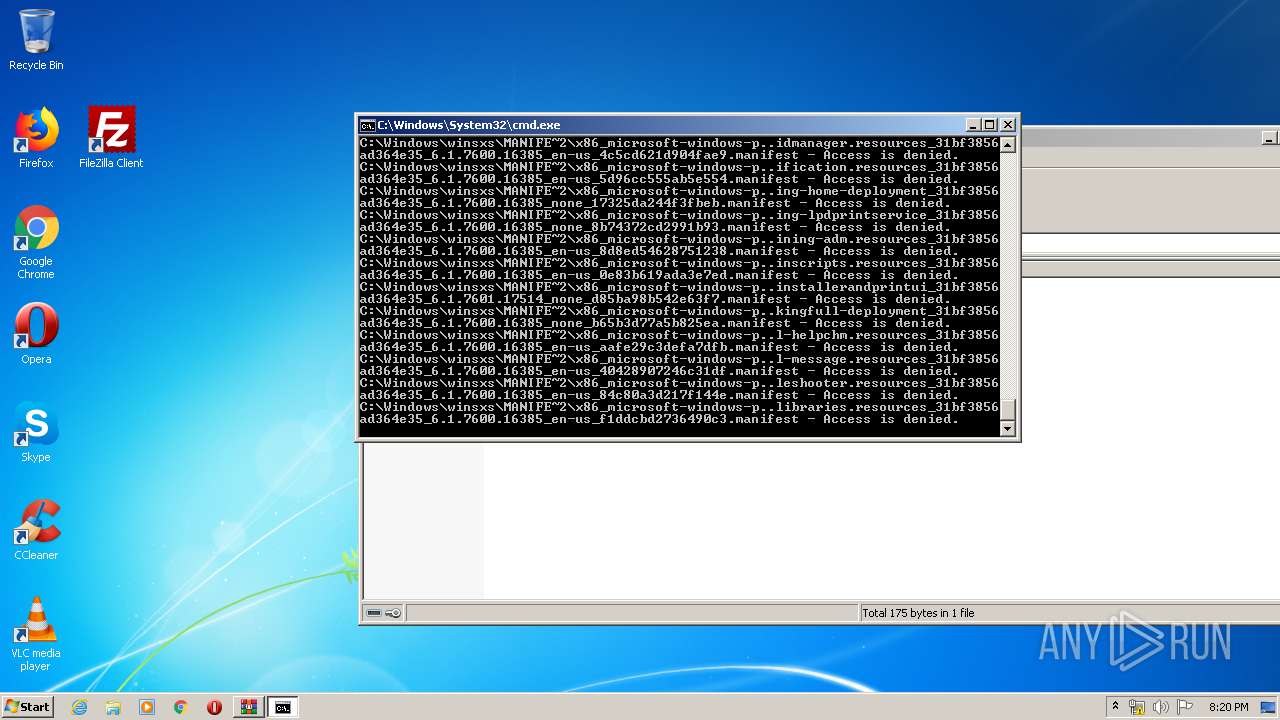
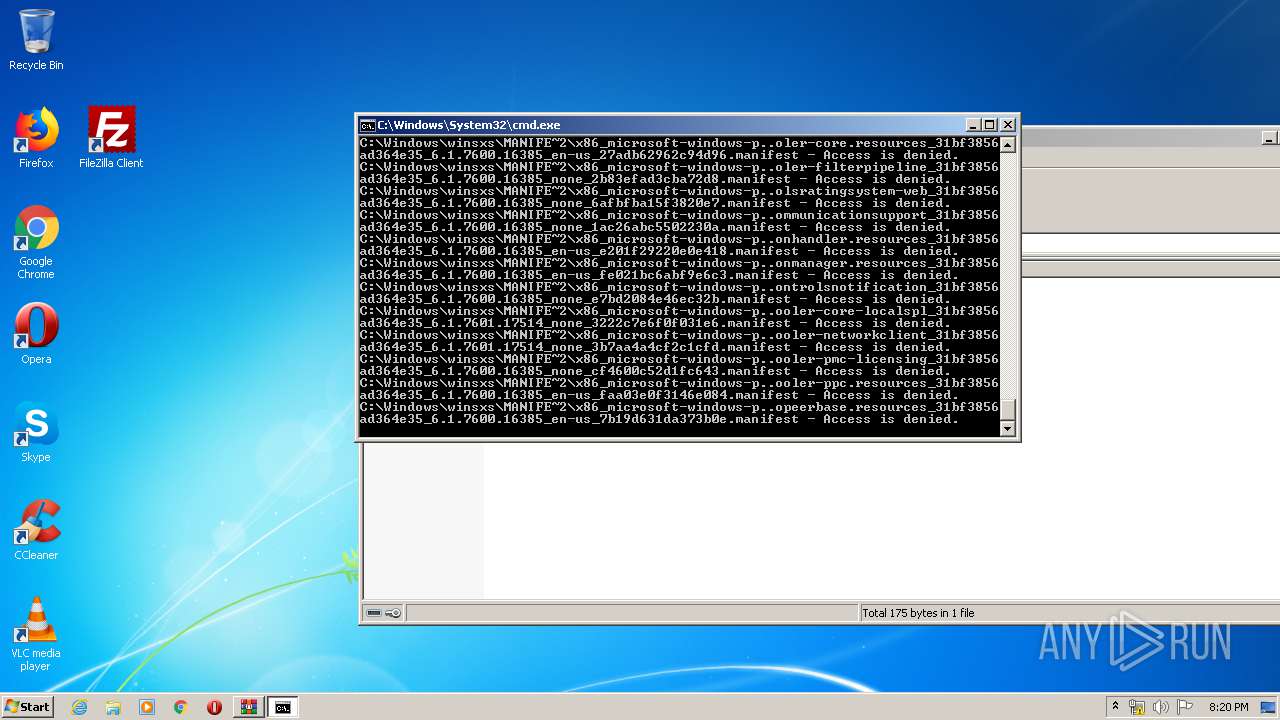
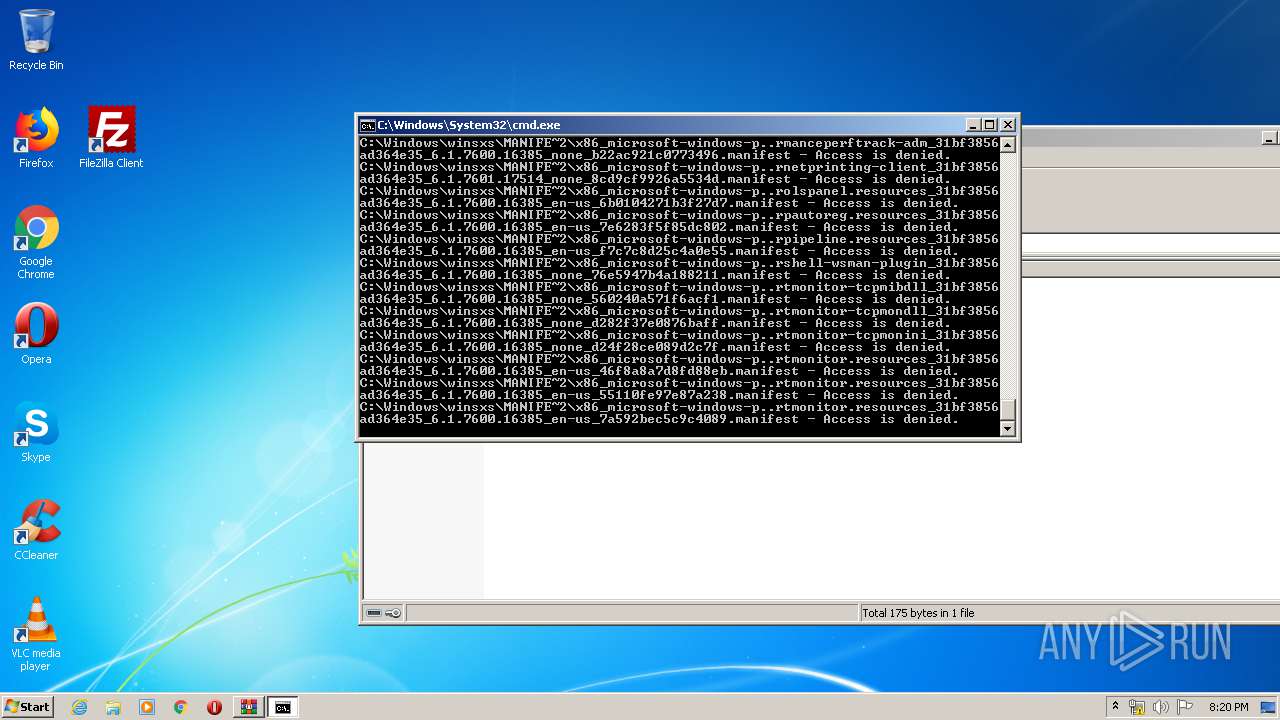
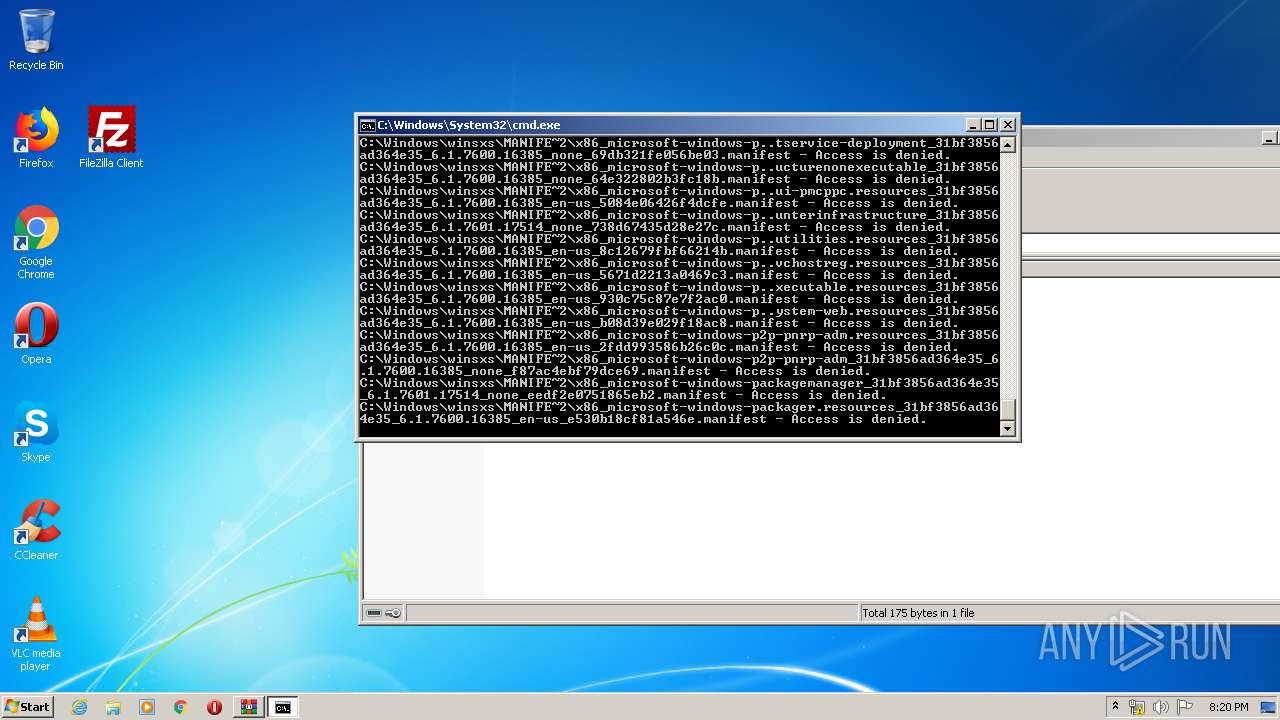
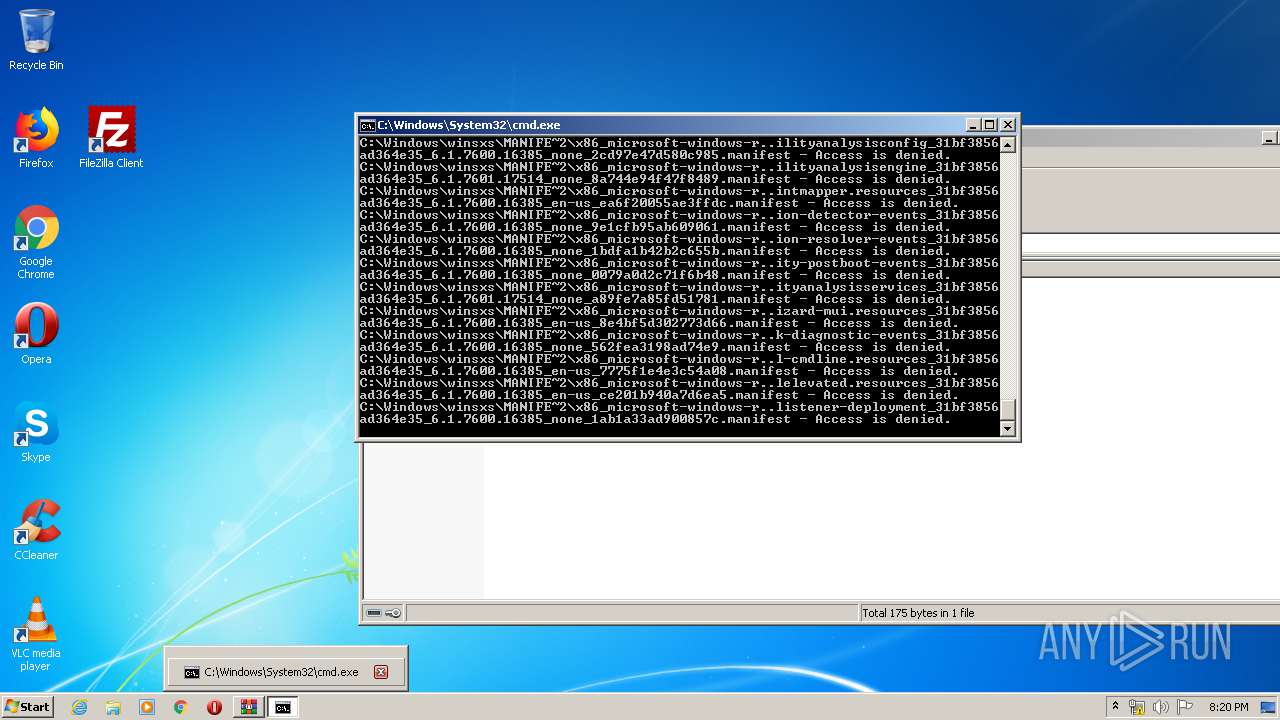
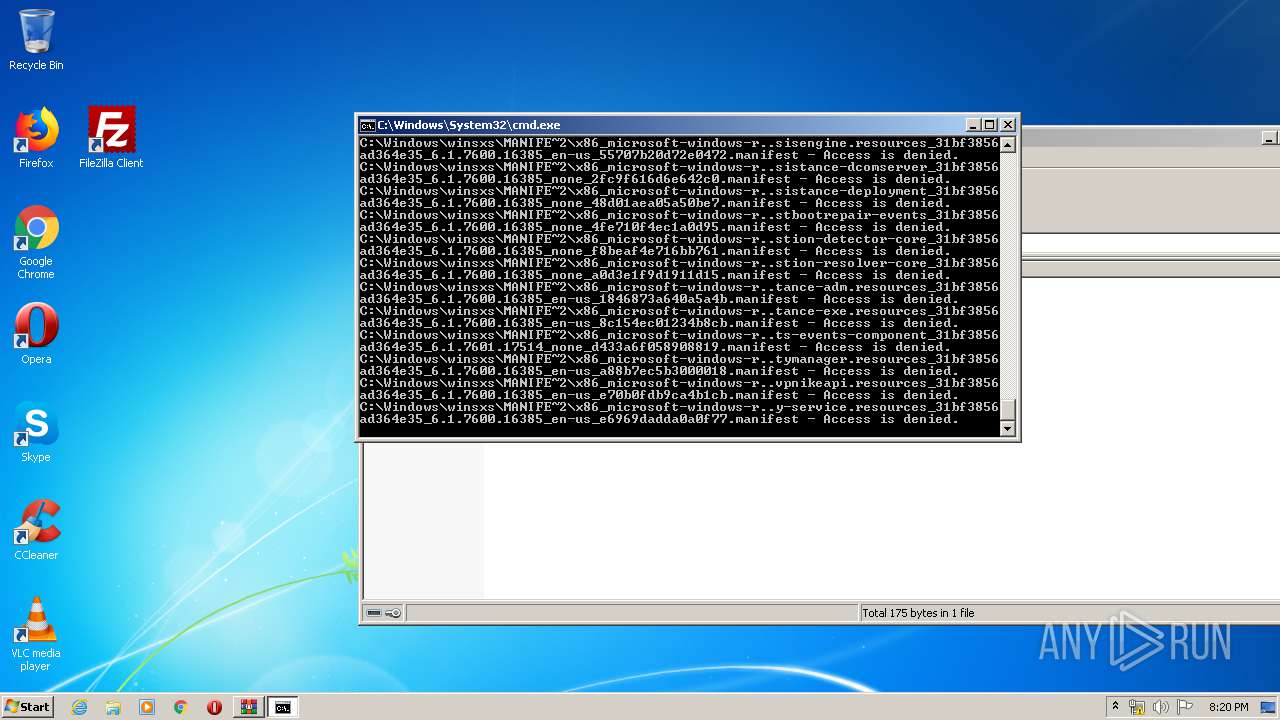
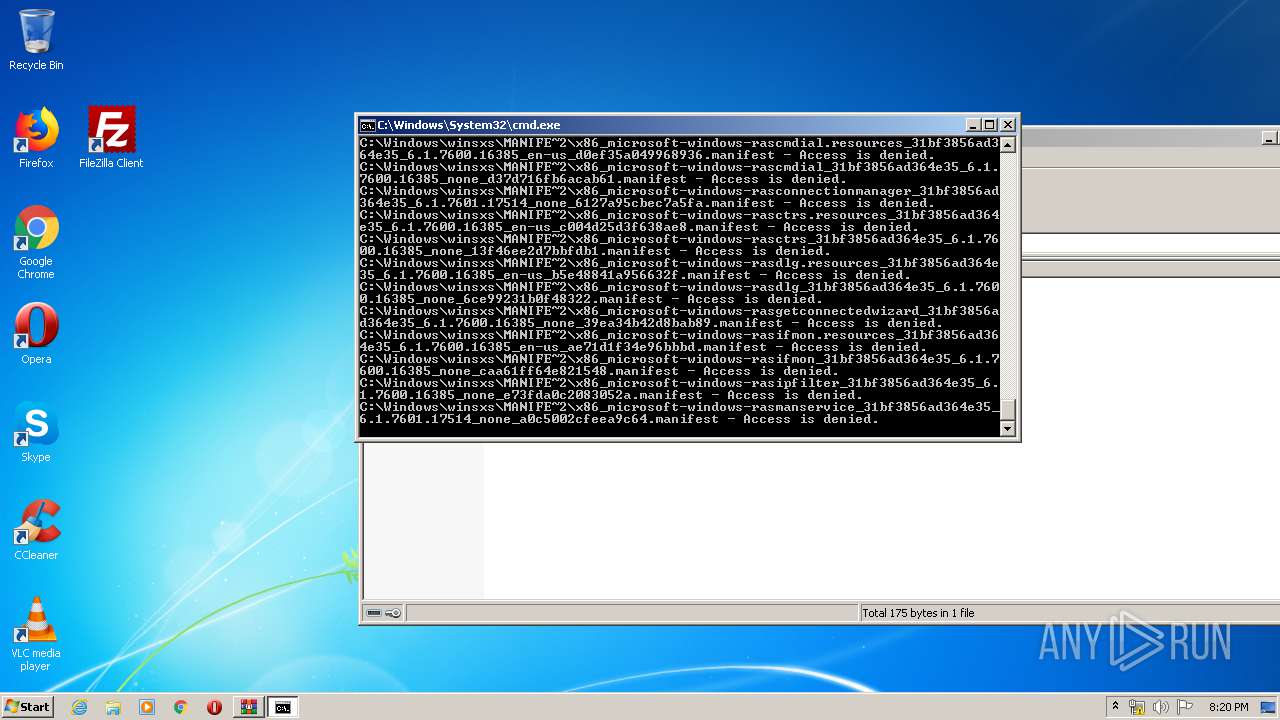
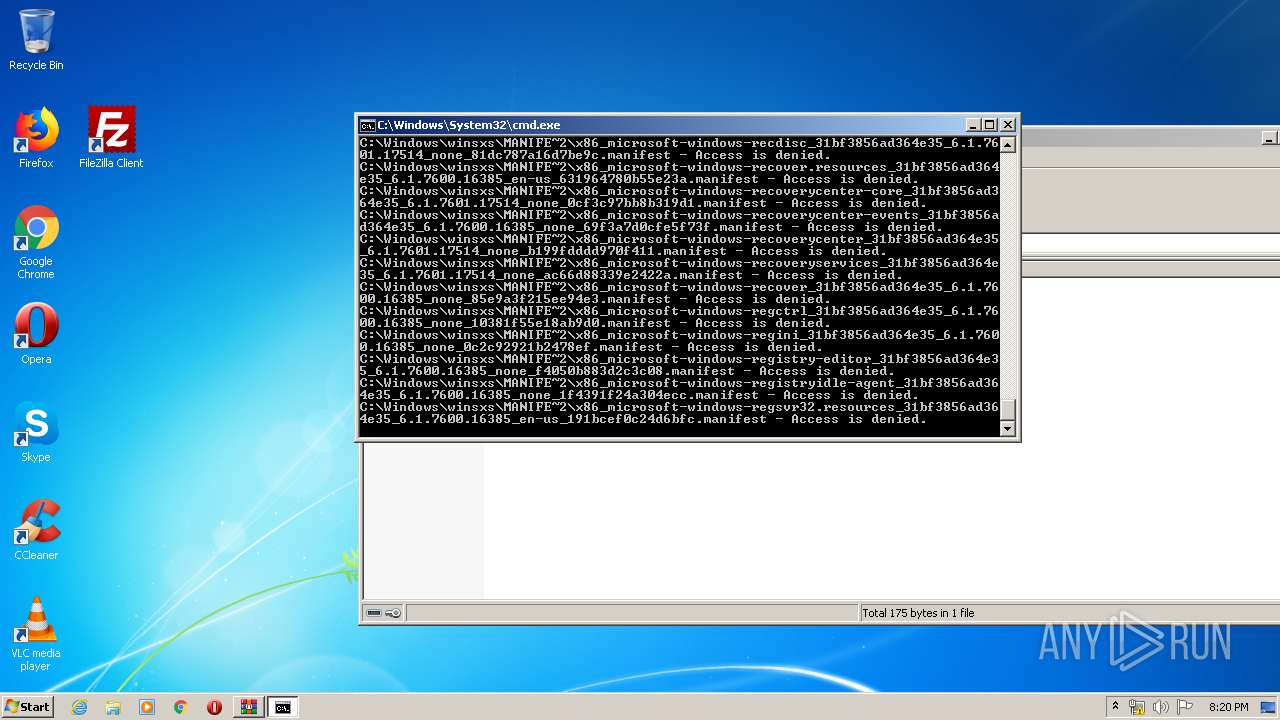
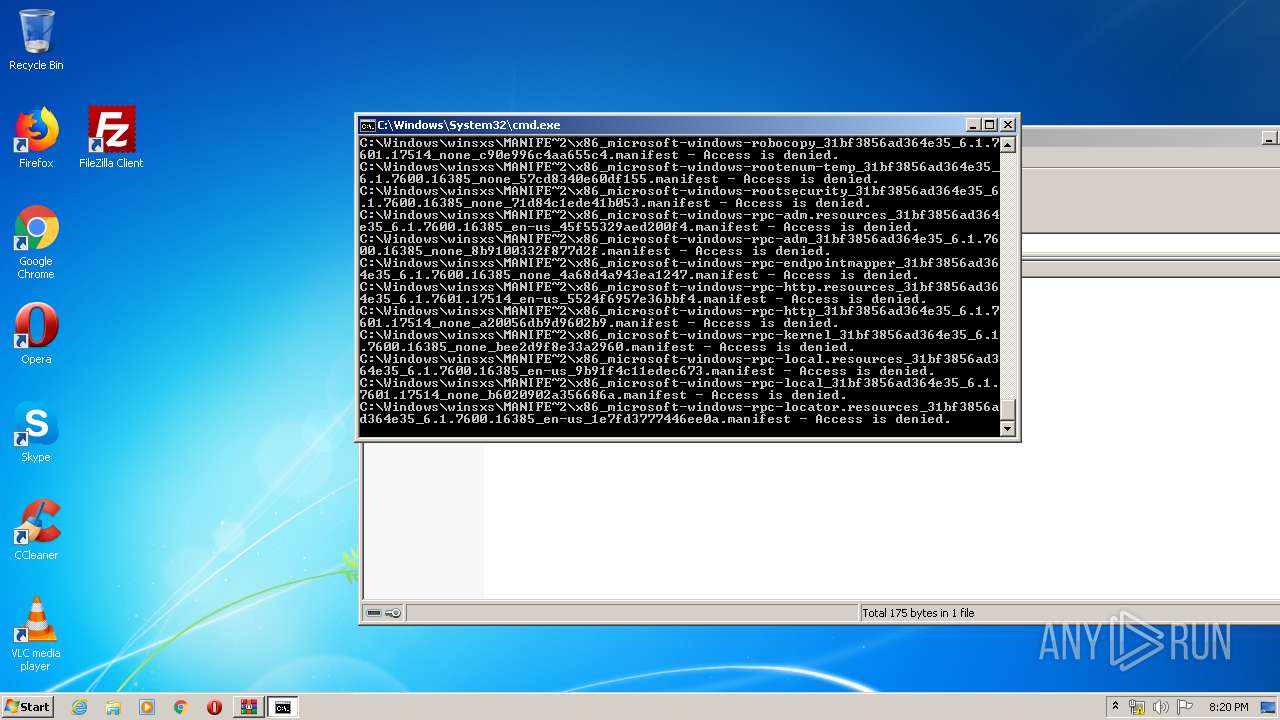
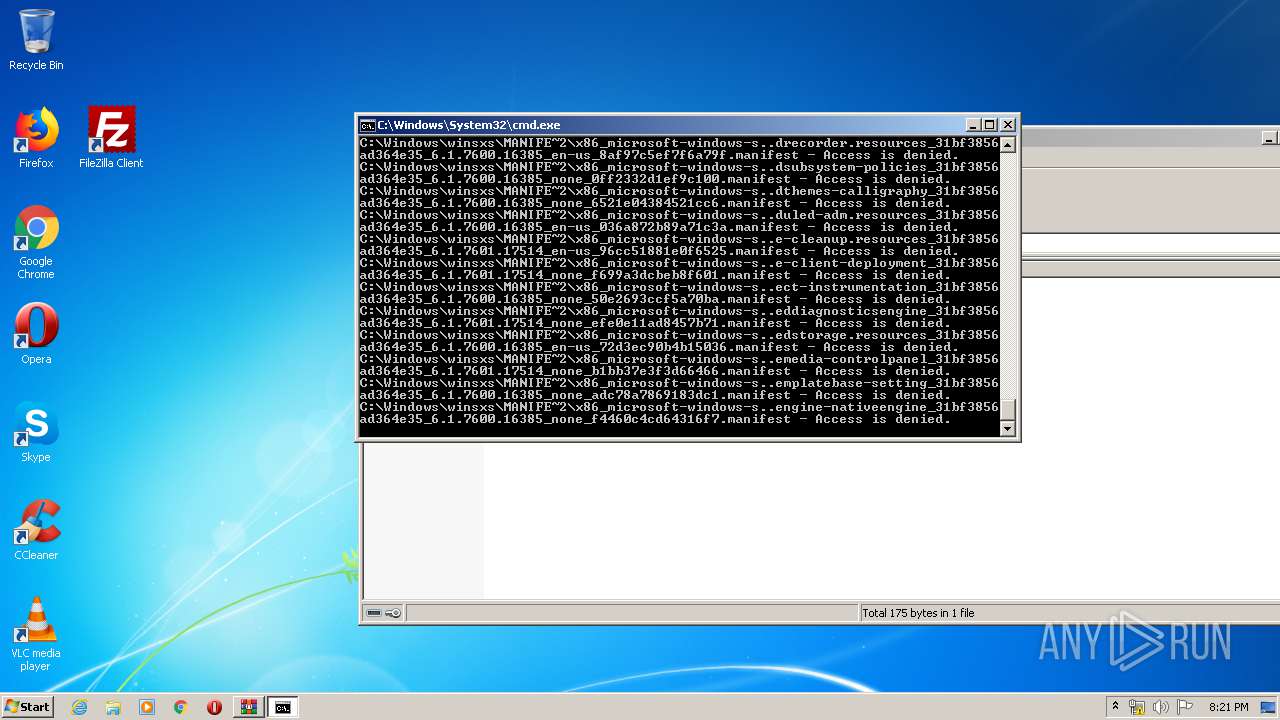
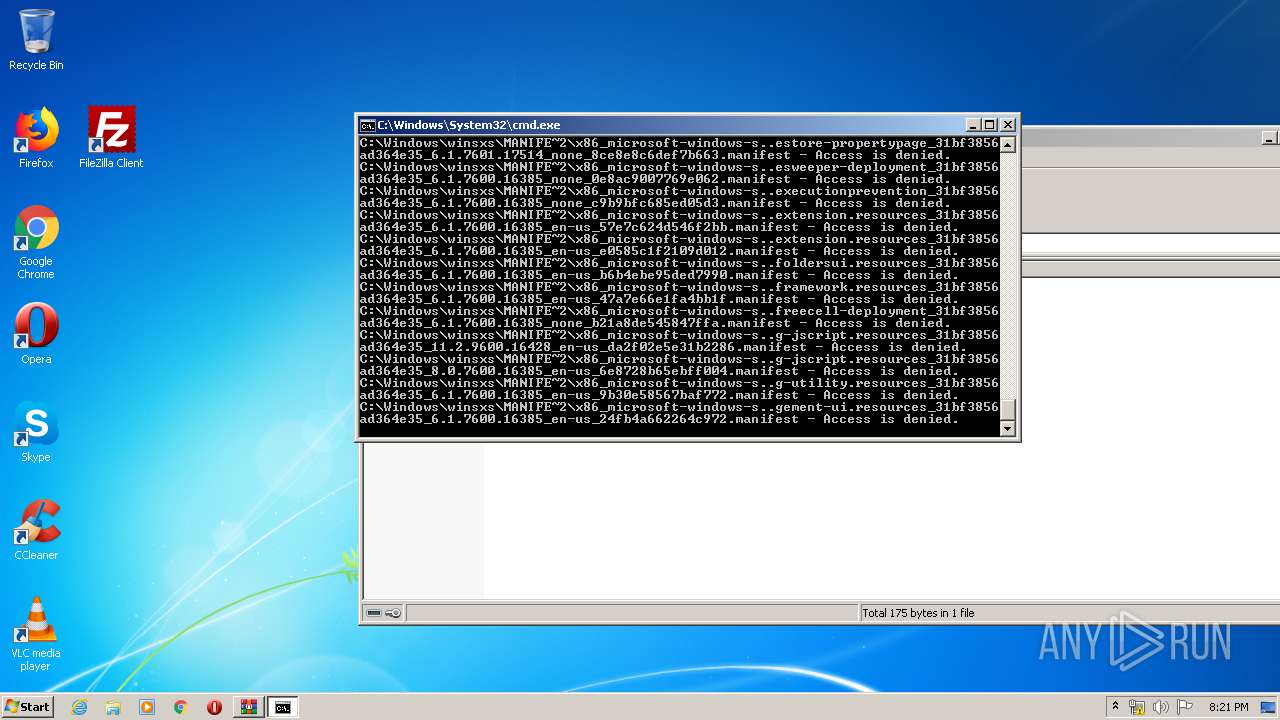
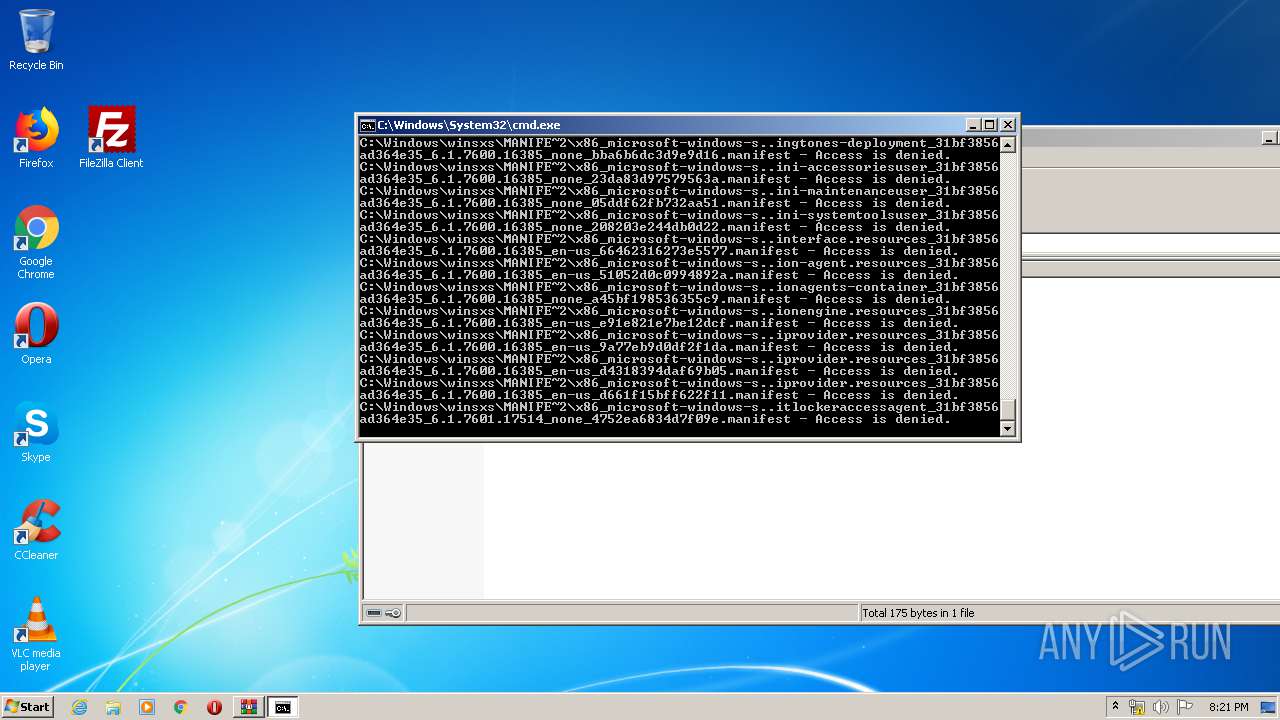
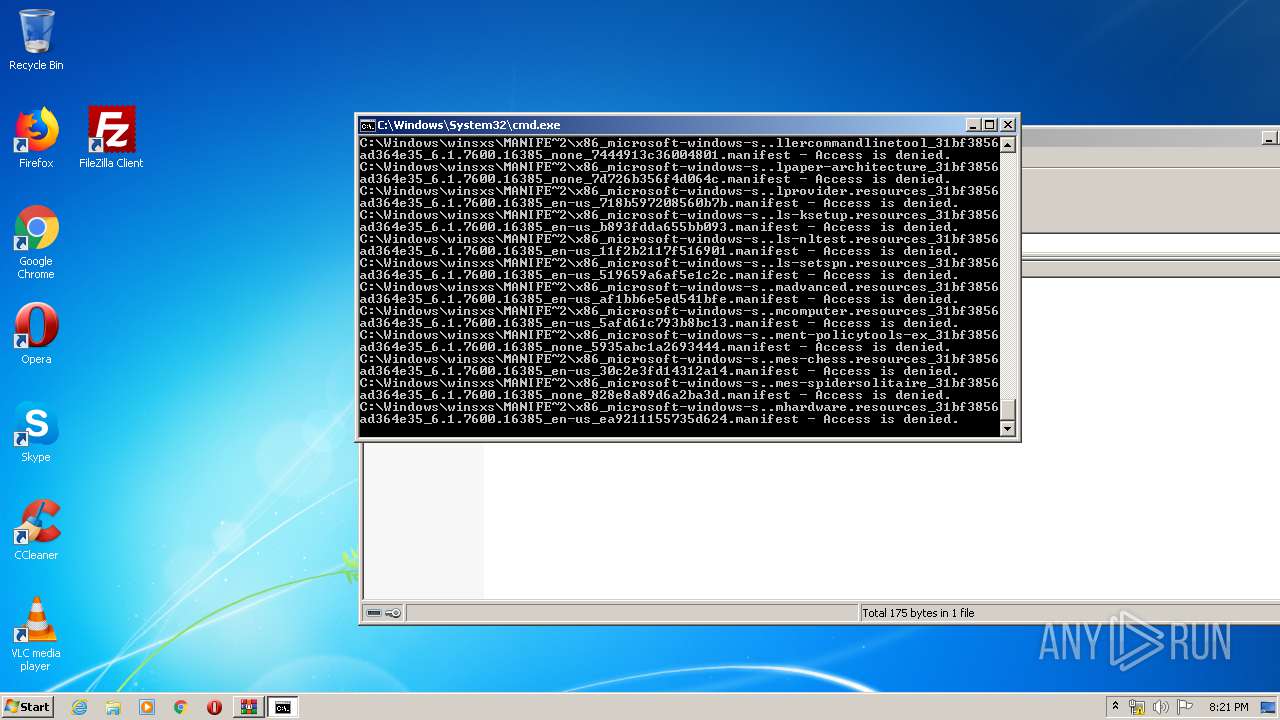
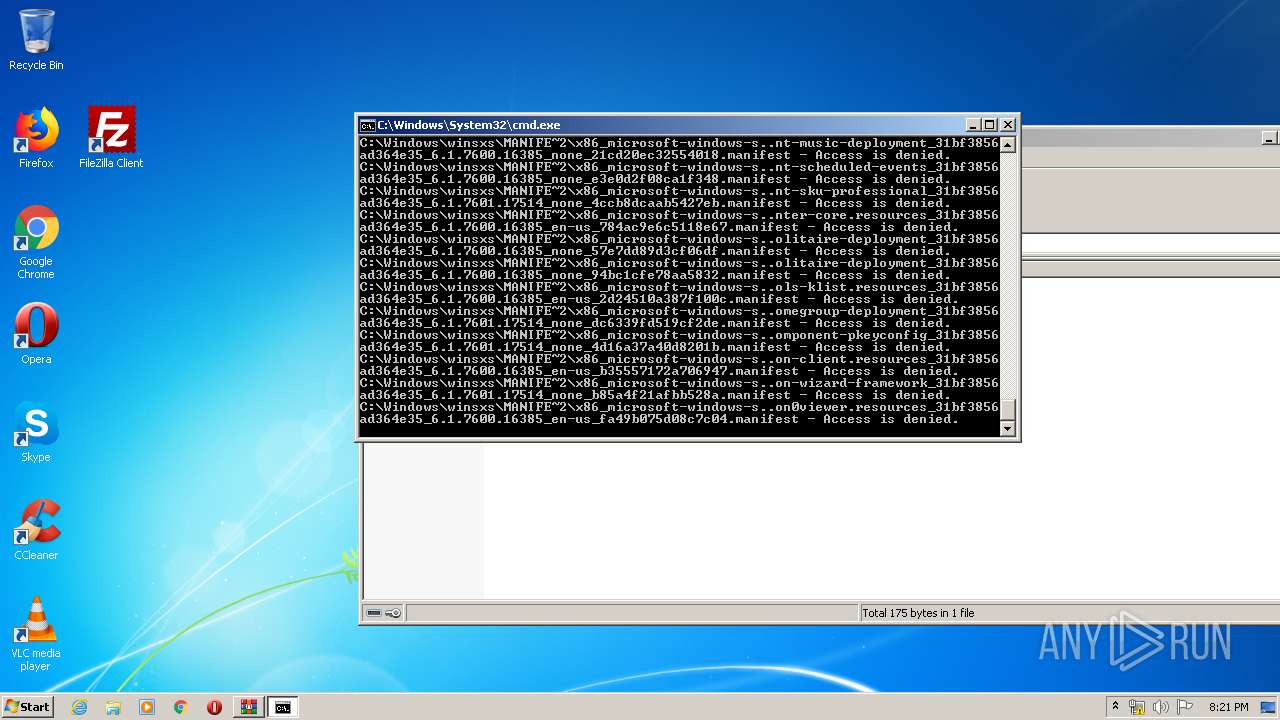
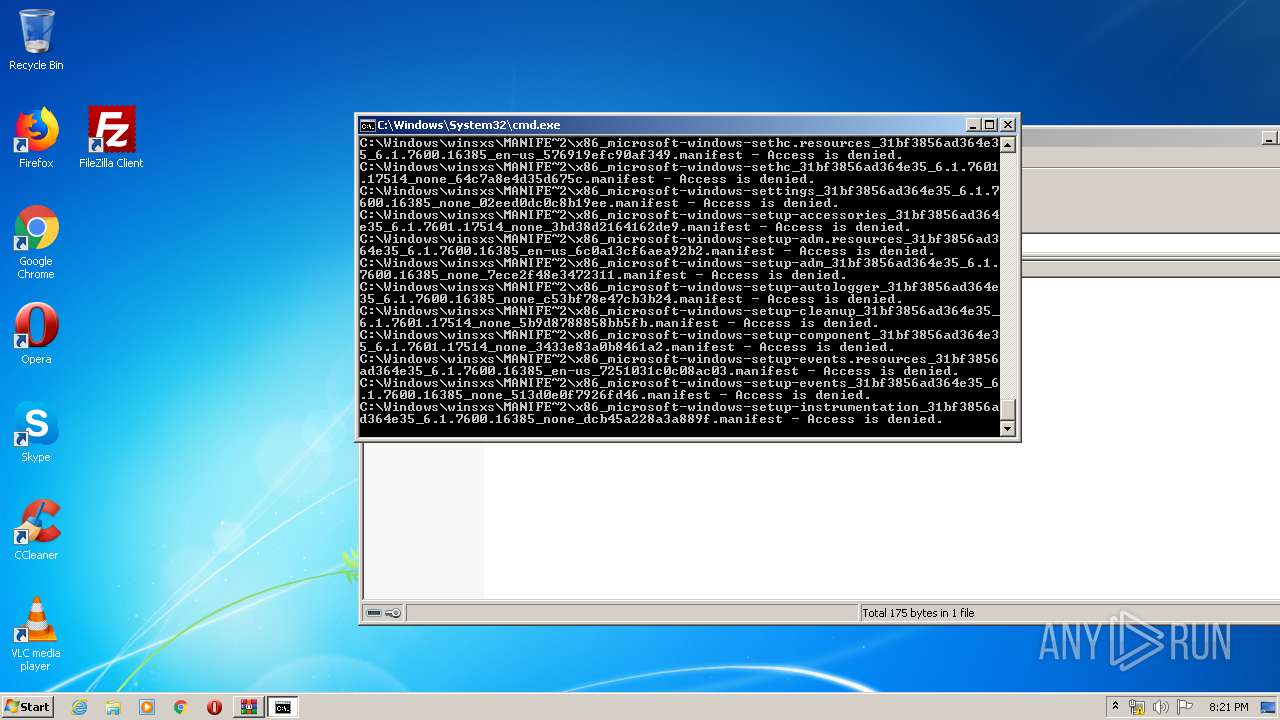
Tries to delete the host file
- cmd.exe (PID: 3228)
SUSPICIOUS
Executed as Windows Service
- SearchIndexer.exe (PID: 1332)
- SearchIndexer.exe (PID: 3380)
Creates files in the program directory
- SearchIndexer.exe (PID: 1332)
- SearchIndexer.exe (PID: 3380)
Creates files in the Windows directory
- SearchIndexer.exe (PID: 3380)
Removes files from Windows directory
- cmd.exe (PID: 3228)
INFO
Manual execution by user
- cmd.exe (PID: 3228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:03:30 19:13:21 |
| ZipCRC: | 0x187cfbee |
| ZipCompressedSize: | 134 |
| ZipUncompressedSize: | 175 |
| ZipFileName: | break.bat |
Total processes
50
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\WinDie V2.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1332 | C:\Windows\system32\SearchIndexer.exe /Embedding | C:\Windows\system32\SearchIndexer.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2564 | timeout 5 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2852 | "C:\Windows\system32\SearchFilterHost.exe" 0 520 524 532 65536 528 | C:\Windows\system32\SearchFilterHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Filter Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3228 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\break.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3356 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe1_ Global\UsGthrCtrlFltPipeMssGthrPipe1 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3380 | C:\Windows\system32\SearchIndexer.exe /Embedding | C:\Windows\system32\SearchIndexer.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3732 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 493
Read events
1 852
Write events
1 434
Delete events
207
Modification events
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\WinDie V2.zip | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (604) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (1332) SearchIndexer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Search\Tracing\EventThrottleState |
| Operation: | delete value | Name: | 000003f5 |
Value: 01000000EAD2EB8E040C00000200000000000000 | |||
Executable files
0
Suspicious files
19
Text files
2
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa604.16185\break.bat | — | |
MD5:— | SHA256:— | |||
| 1332 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Windows.edb | — | |
MD5:— | SHA256:— | |||
| 1332 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\tmp.edb | — | |
MD5:— | SHA256:— | |||
| 3380 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\MSStmp.log | — | |
MD5:— | SHA256:— | |||
| 3380 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\MSS.log | — | |
MD5:— | SHA256:— | |||
| 3380 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Windows.edb | — | |
MD5:— | SHA256:— | |||
| 3380 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\MSS.chk | binary | |
MD5:— | SHA256:— | |||
| 3380 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Projects\SystemIndex\PropMap\CiPT0000.002 | binary | |
MD5:— | SHA256:— | |||
| 1332 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\MSS.chk | binary | |
MD5:— | SHA256:— | |||
| 3380 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Projects\SystemIndex\PropMap\CiPT0000.001 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report