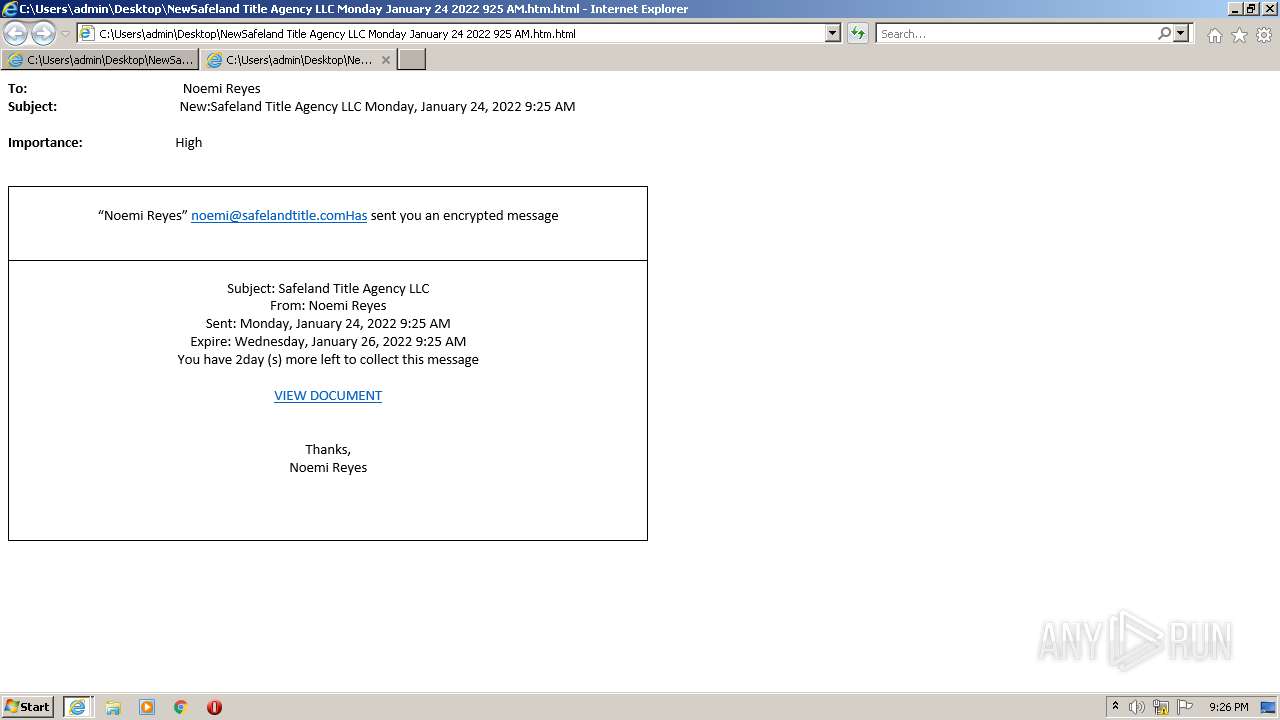
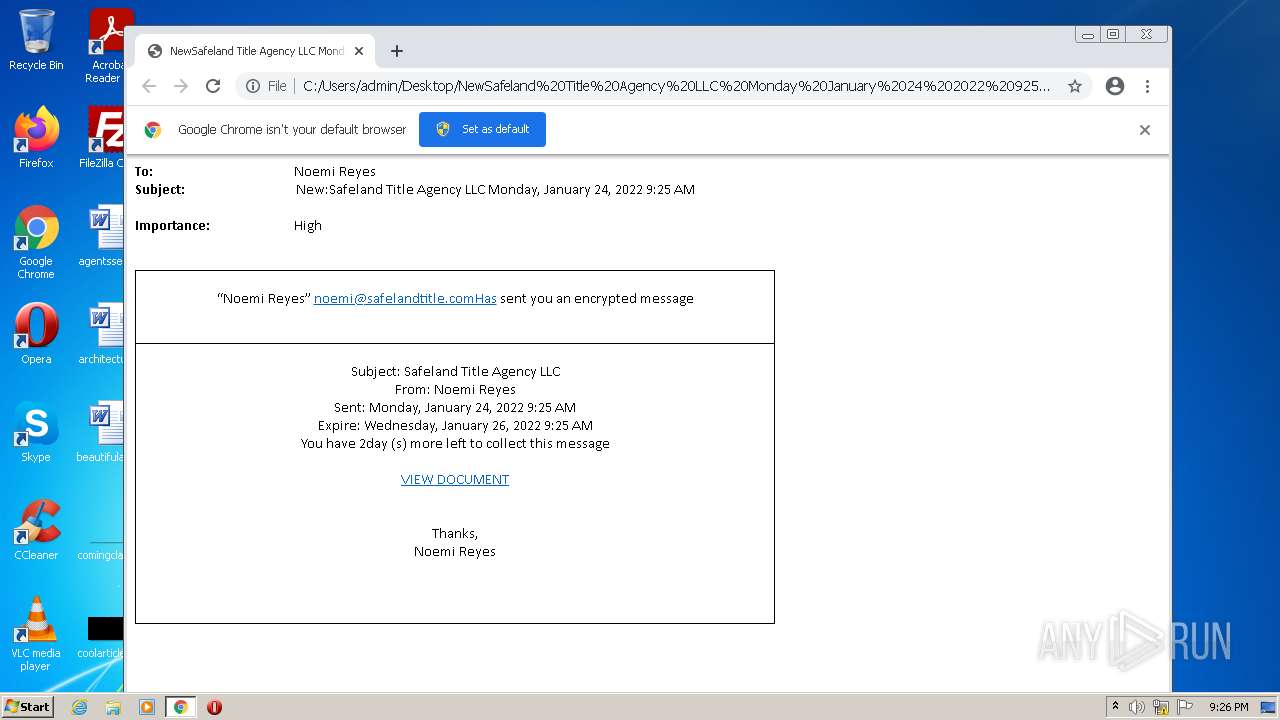
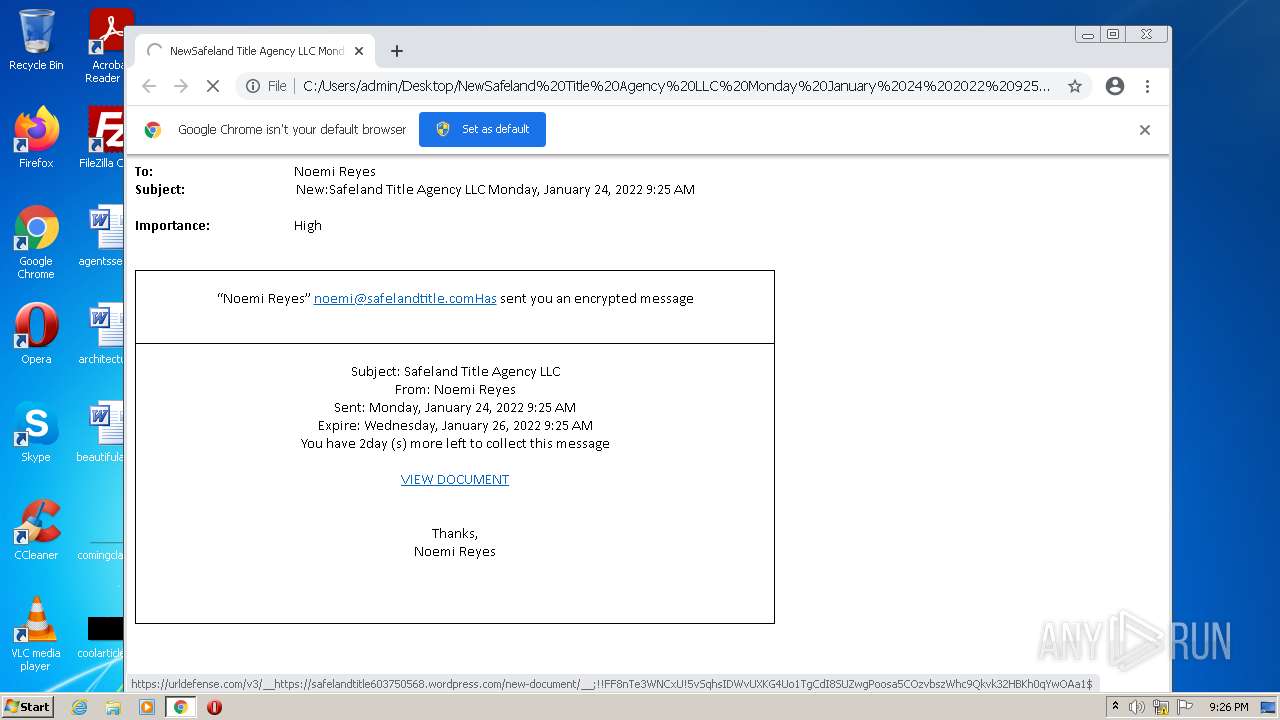
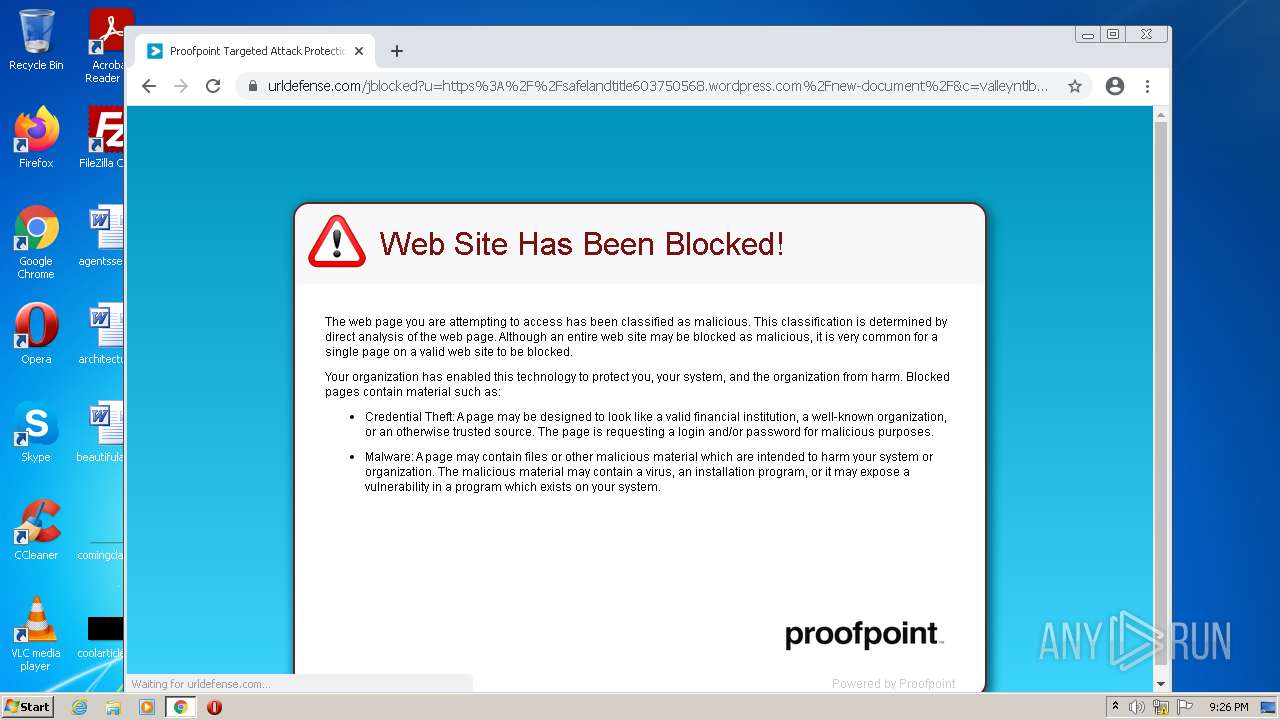
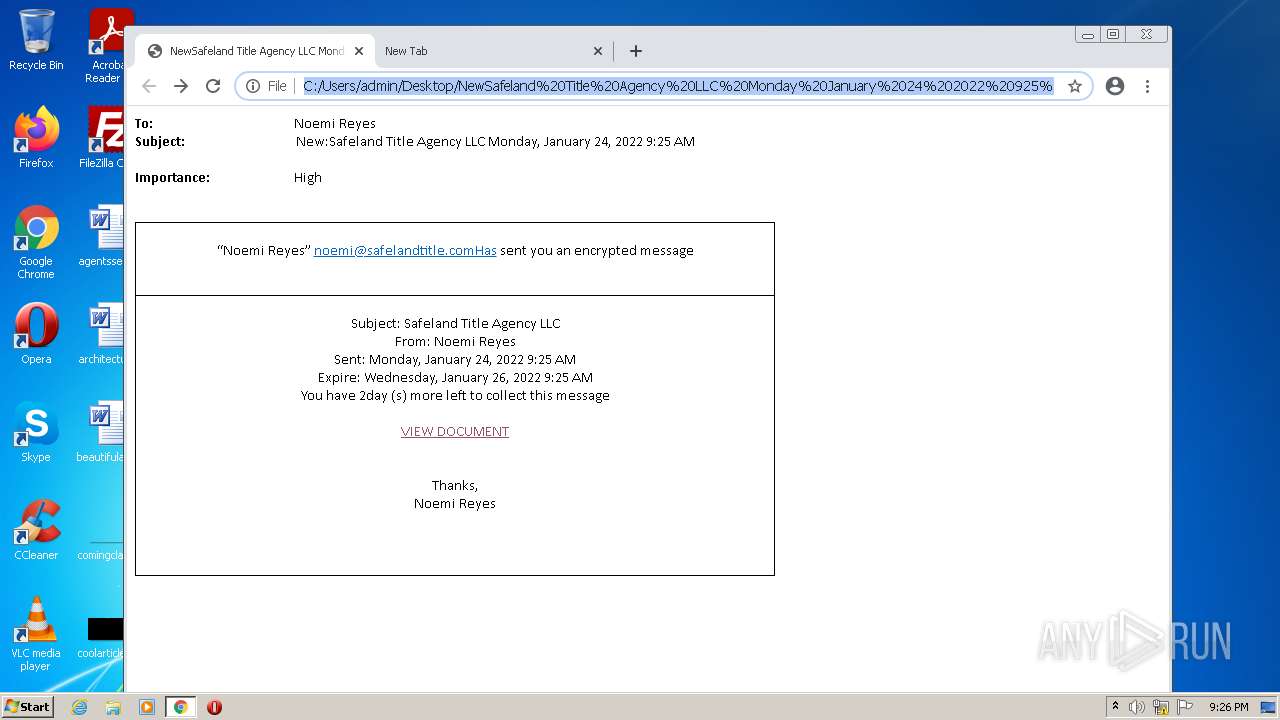
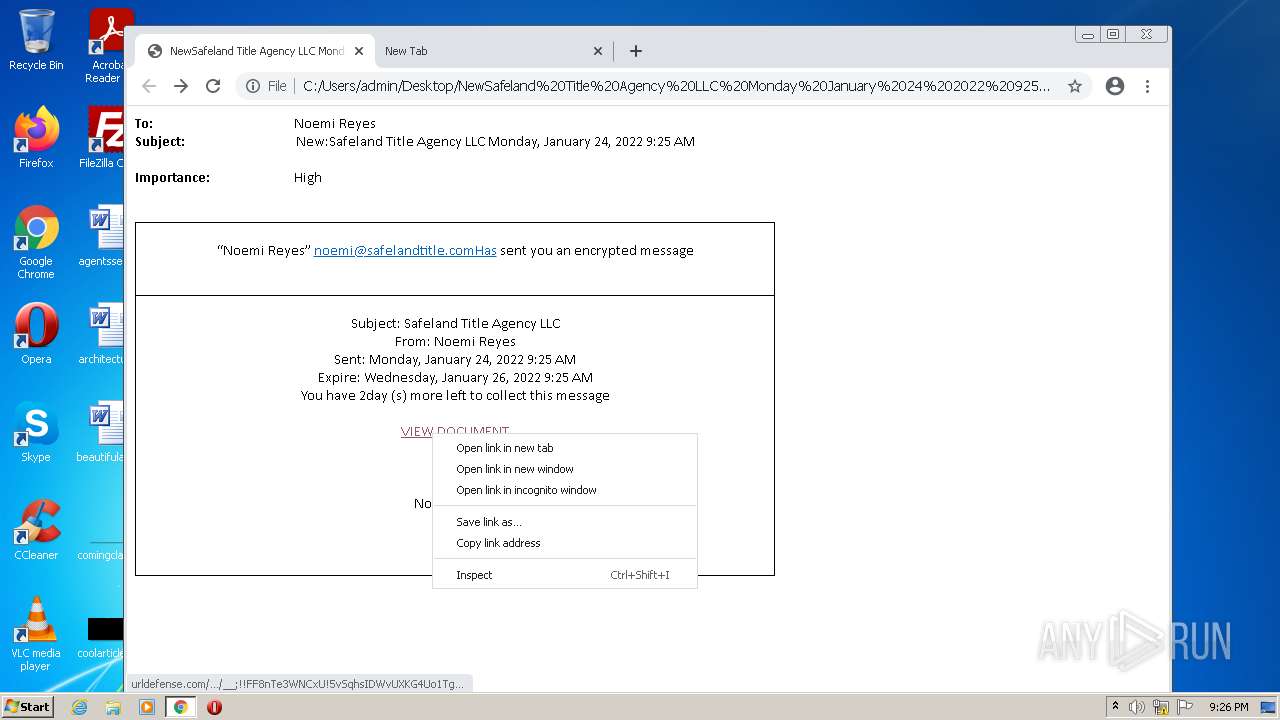
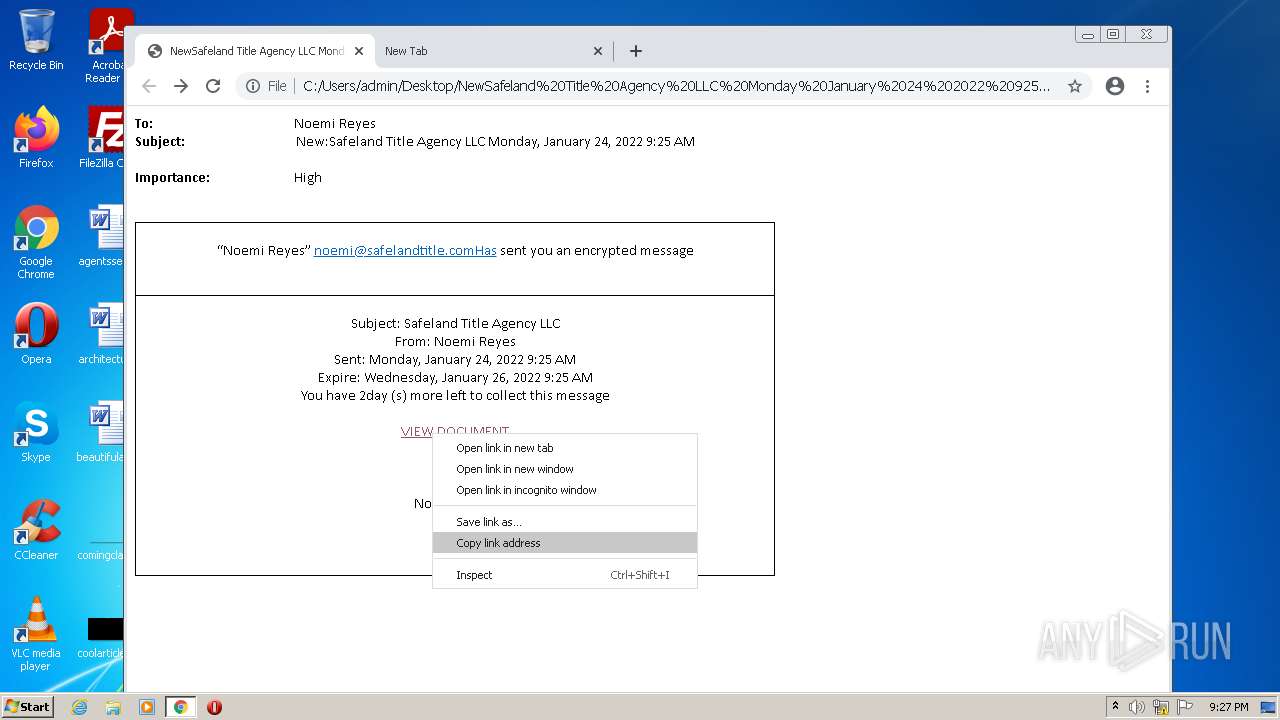
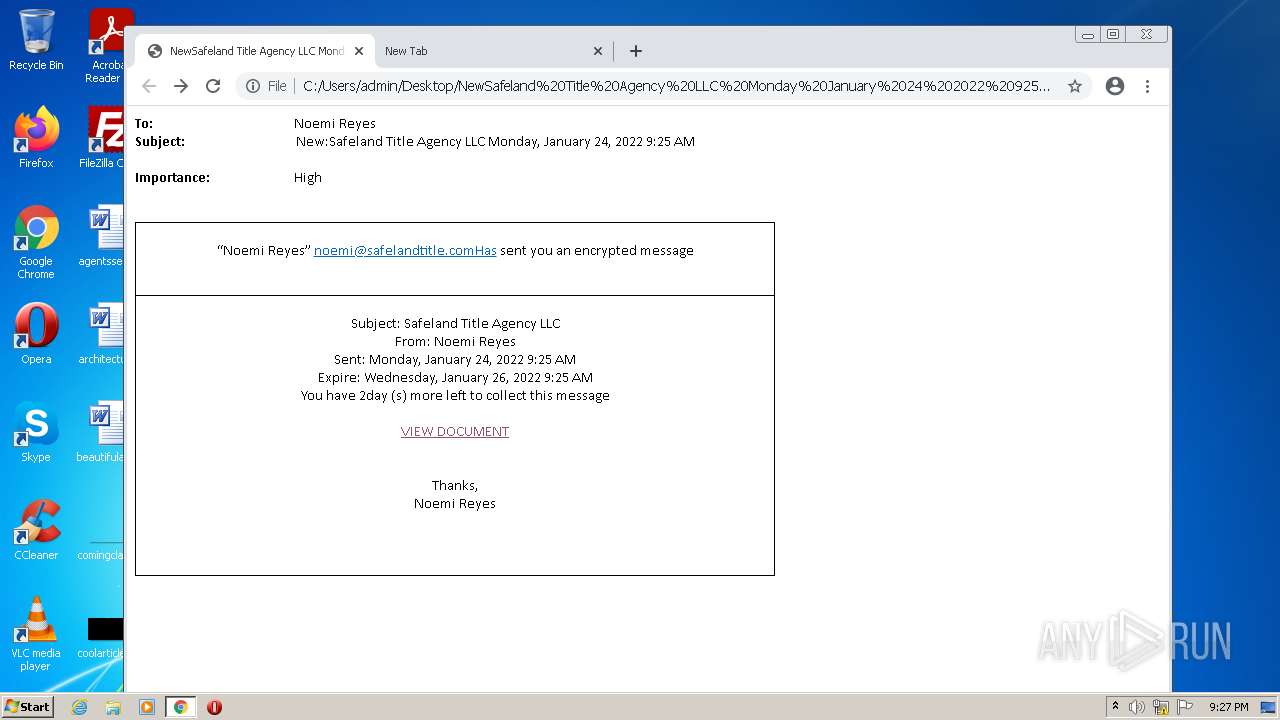
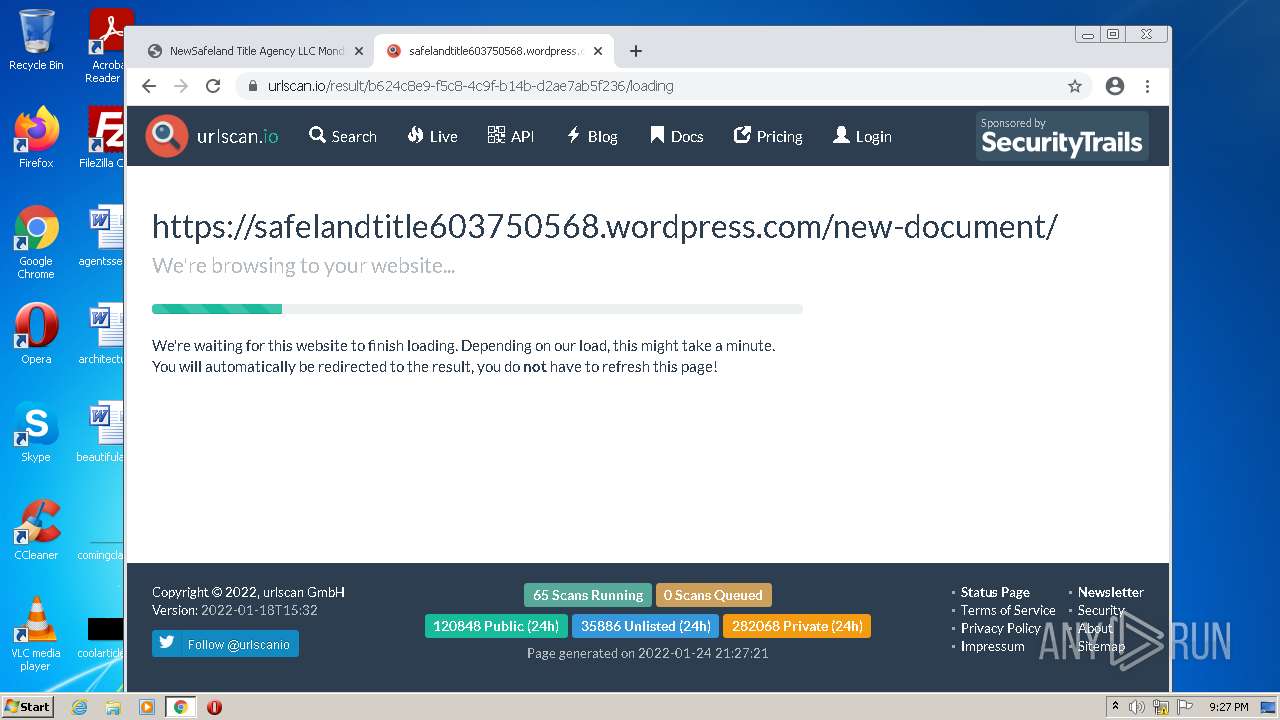
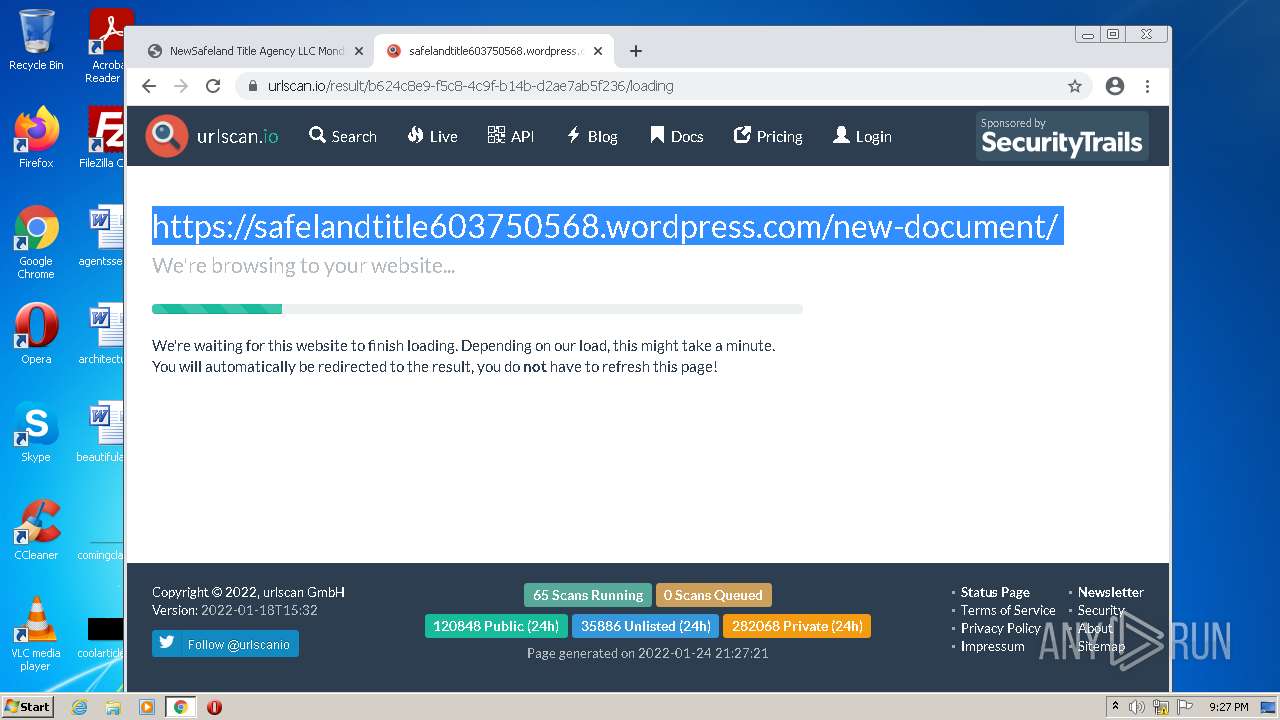
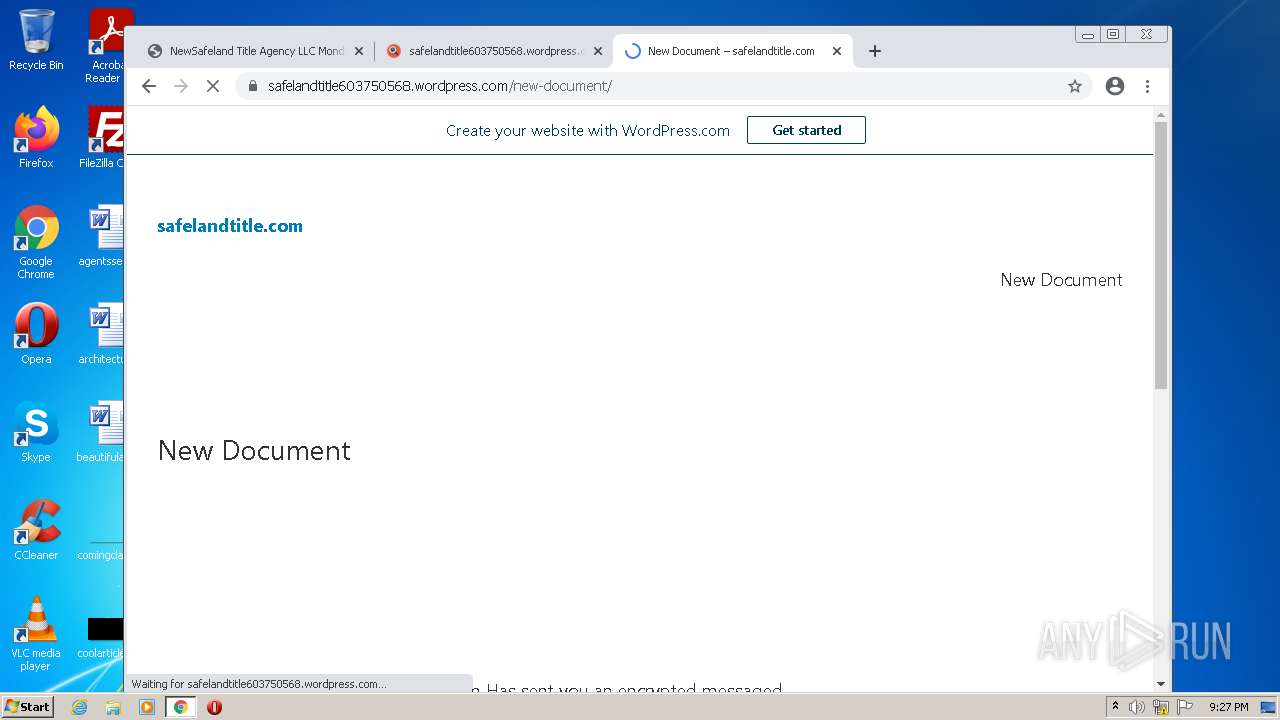
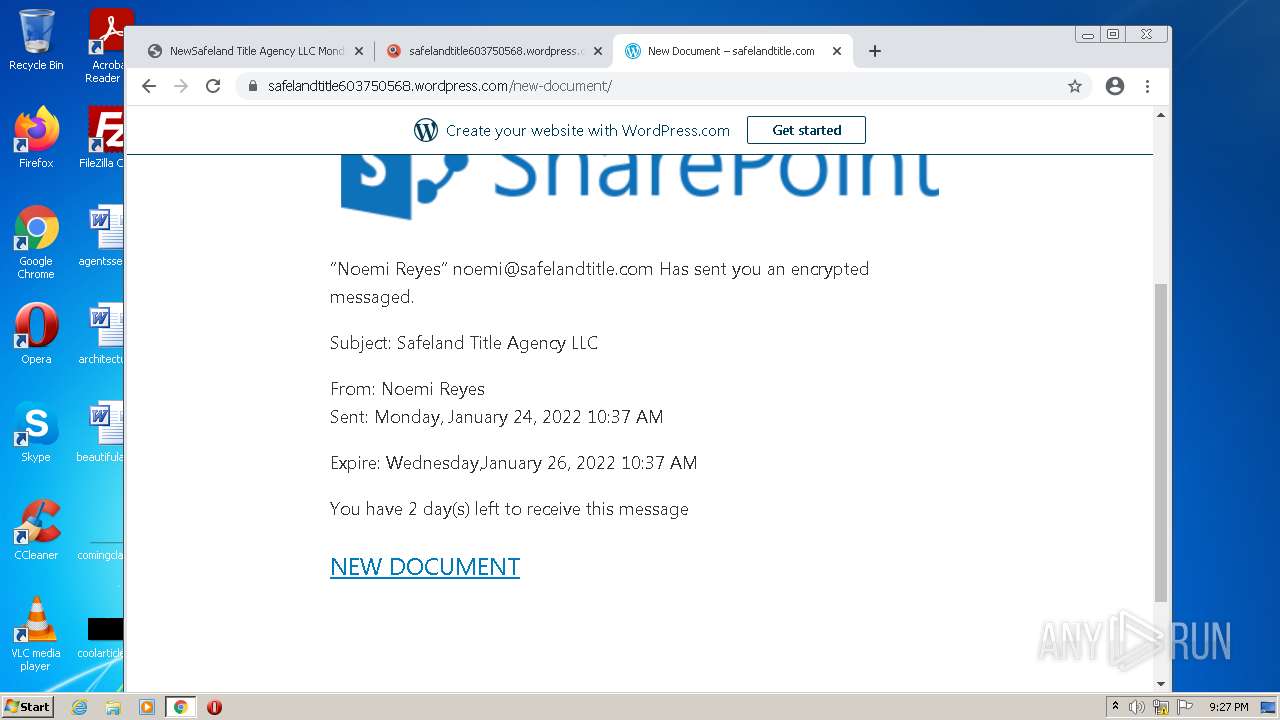
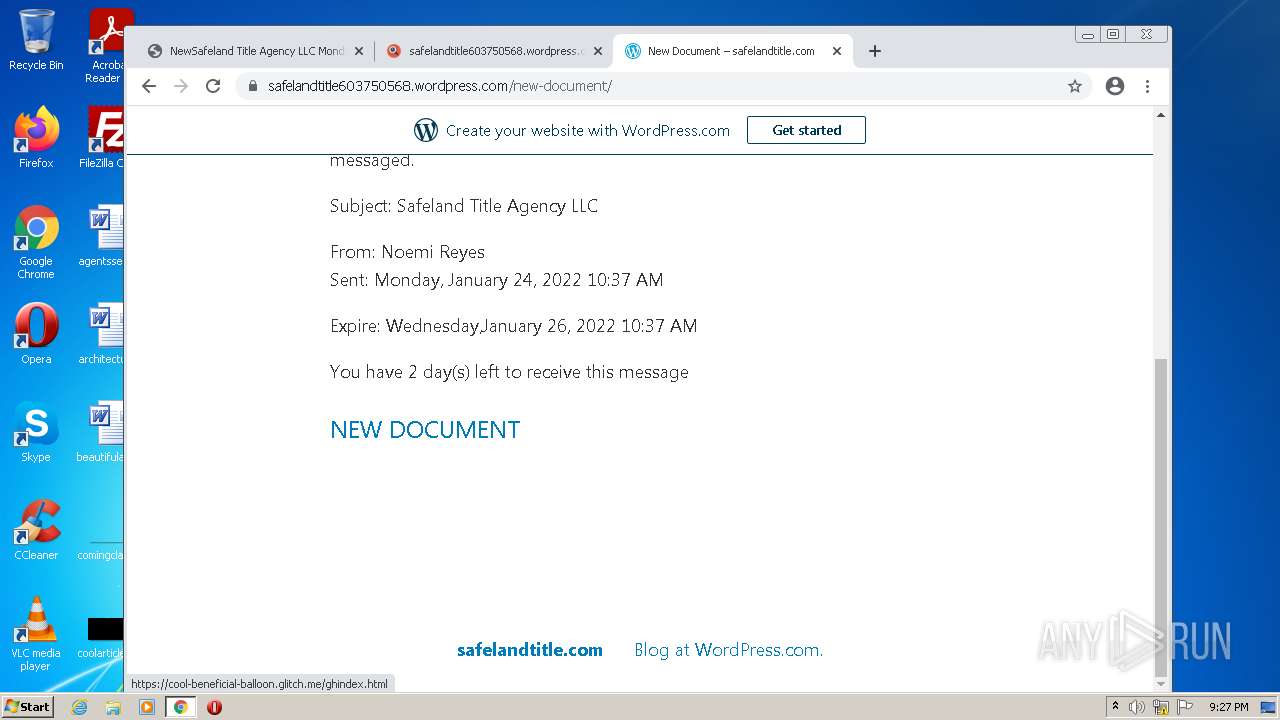
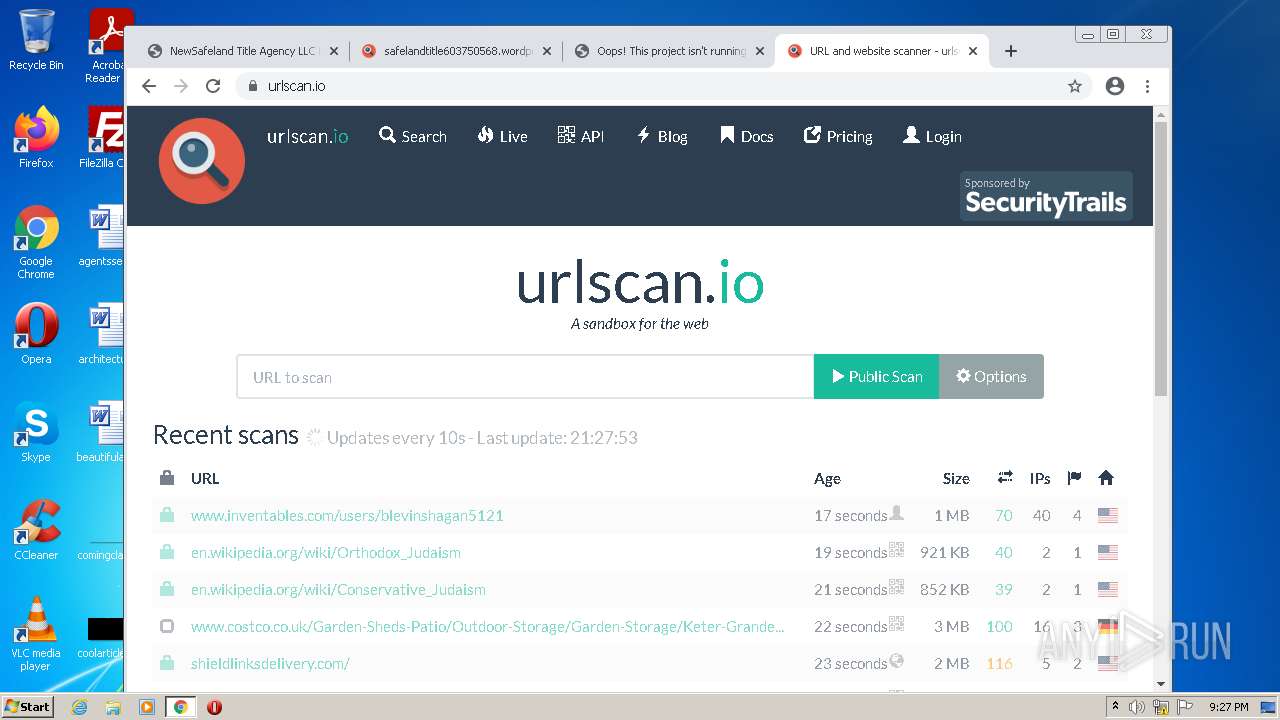
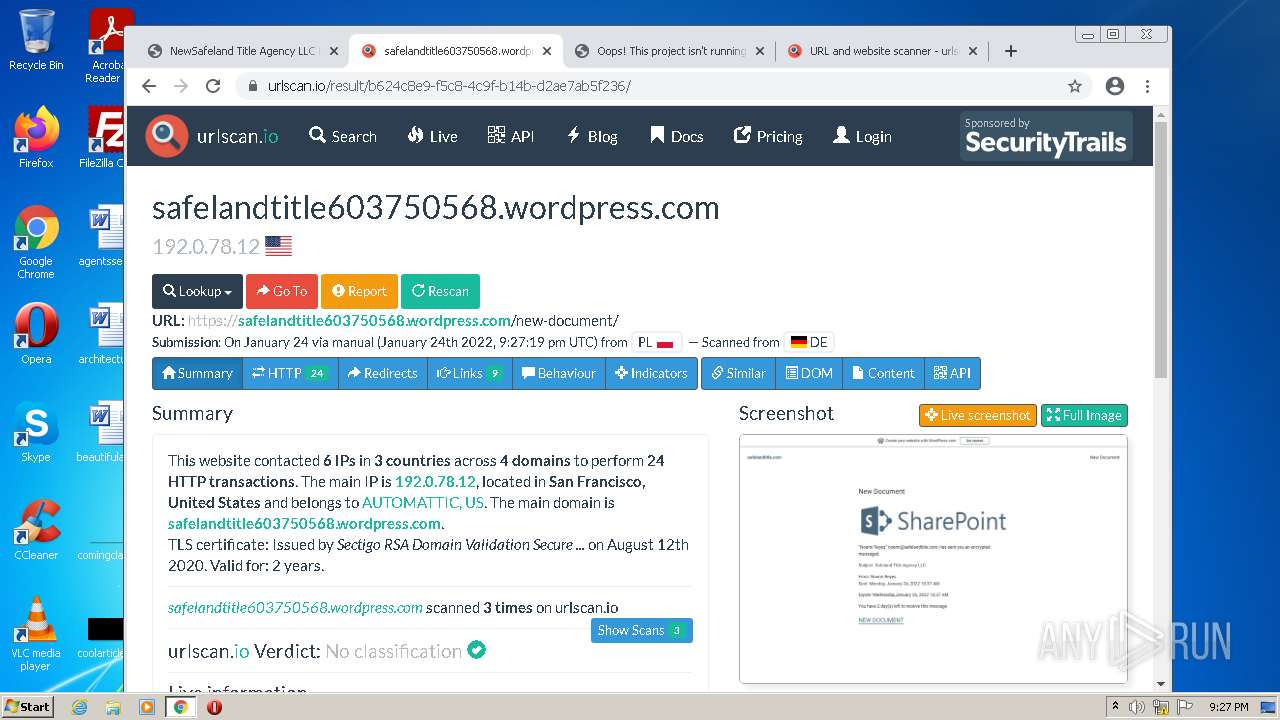
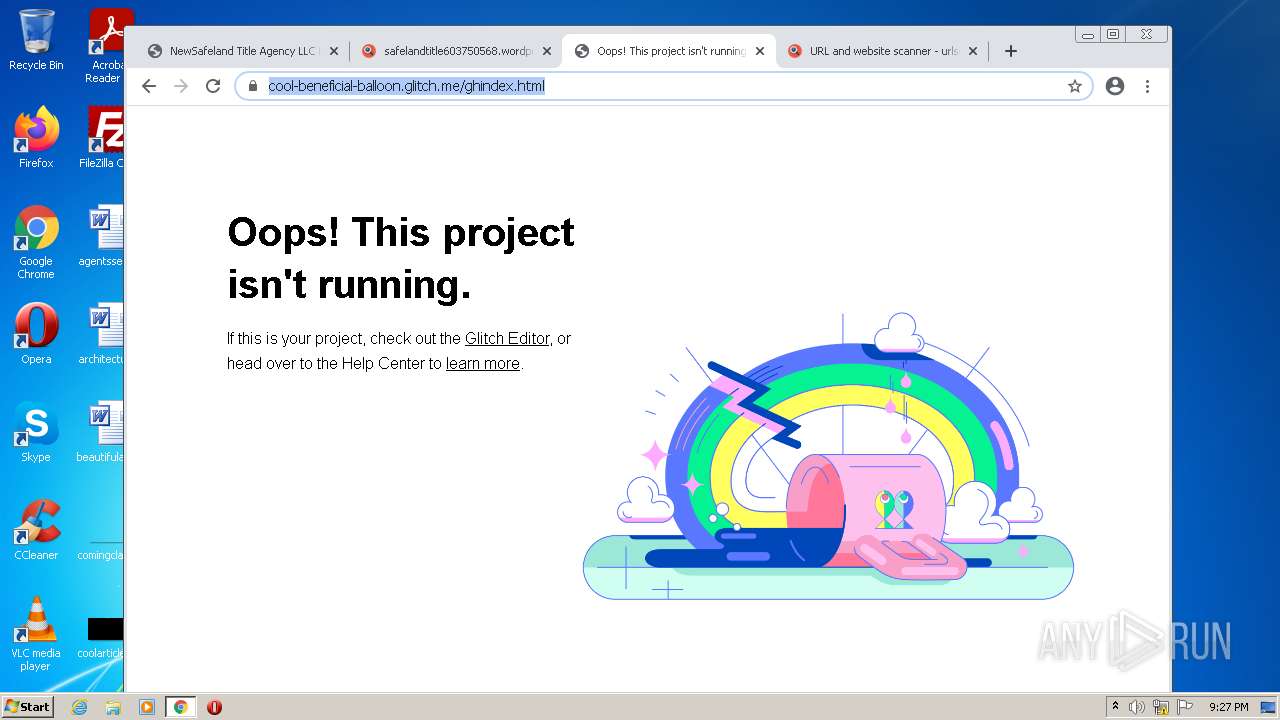
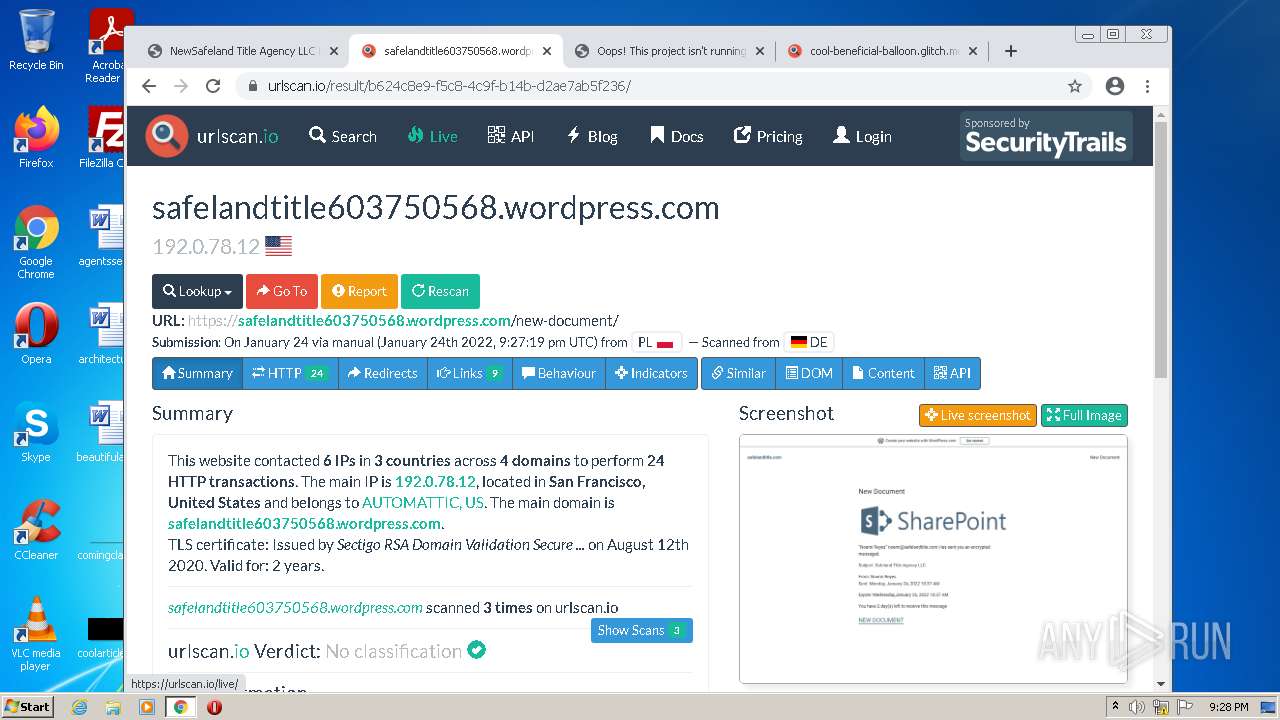
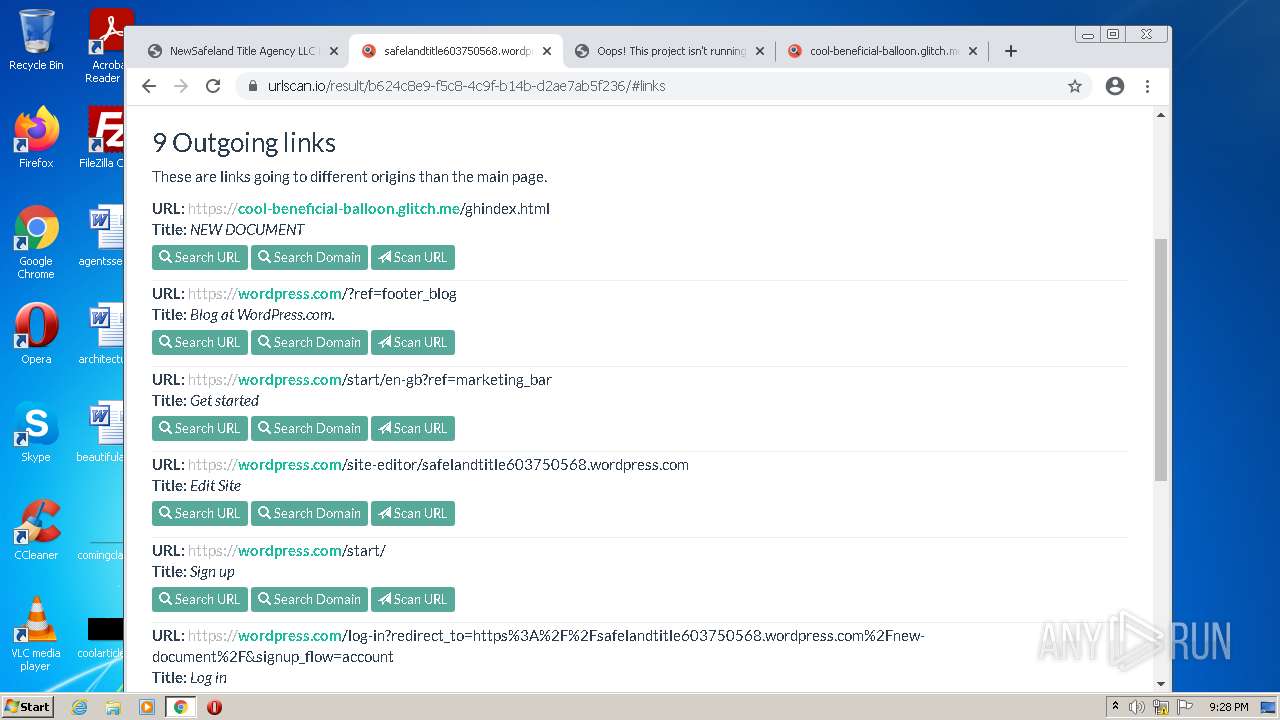
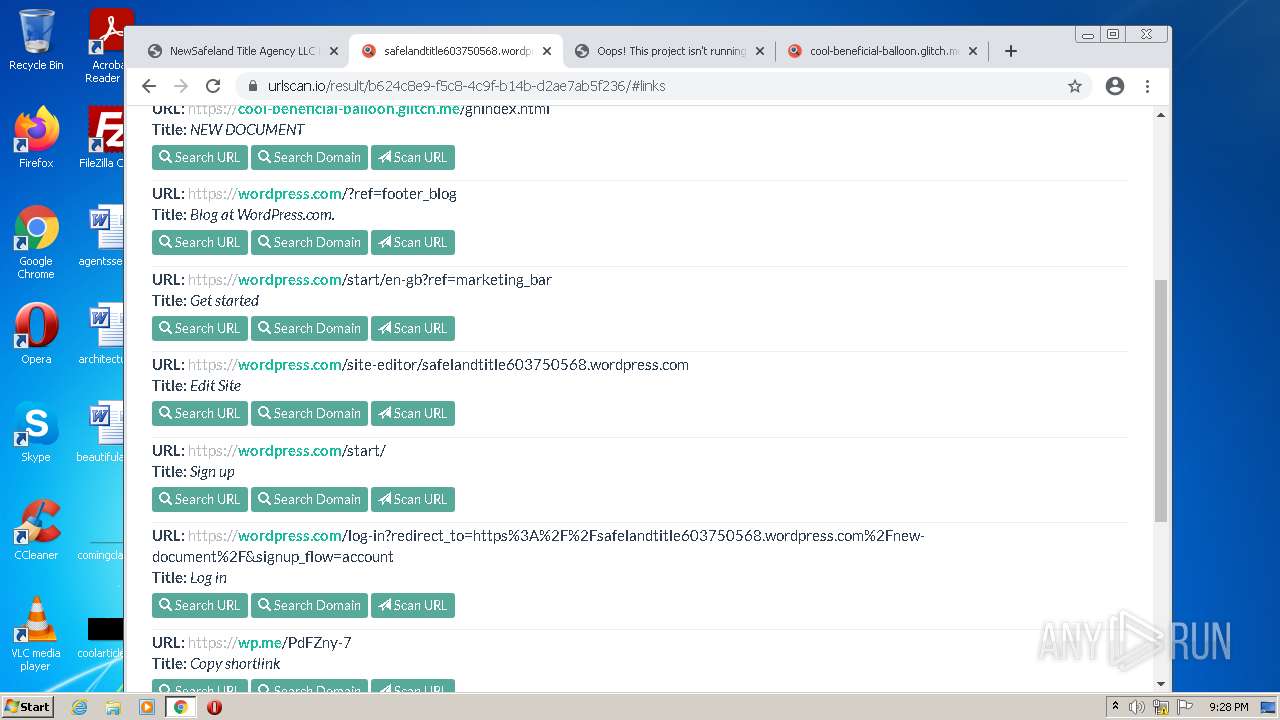
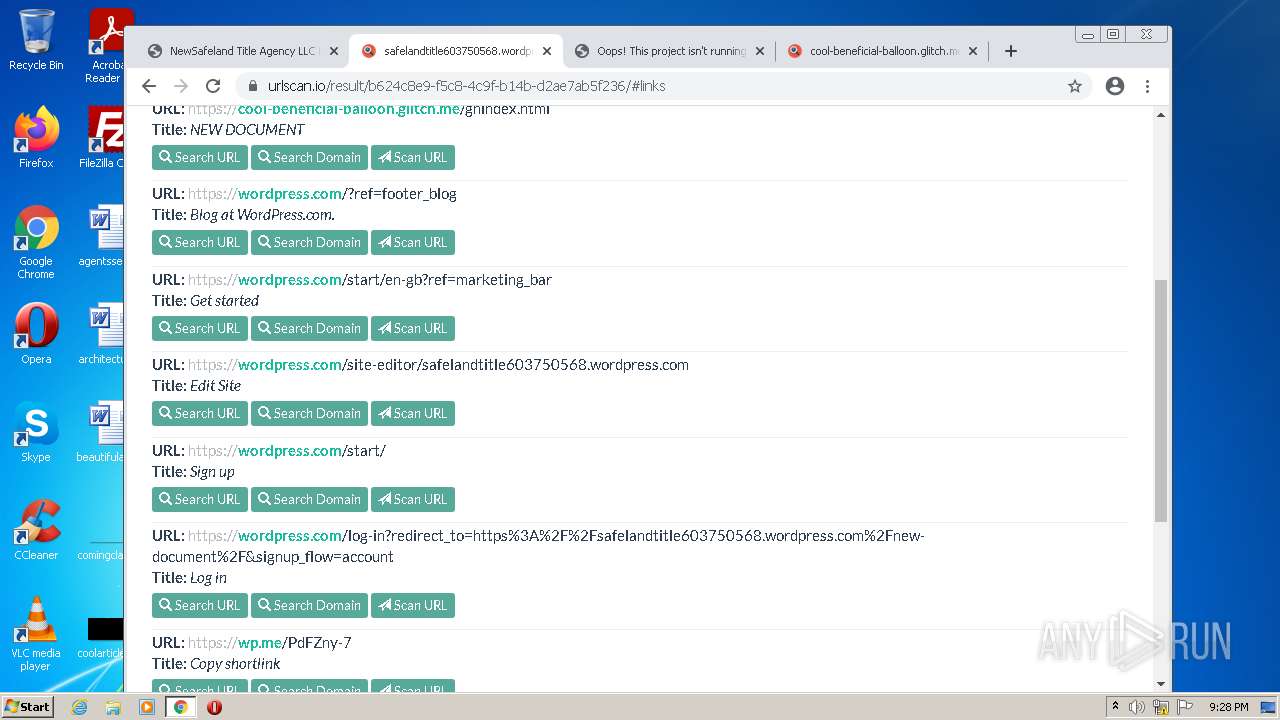
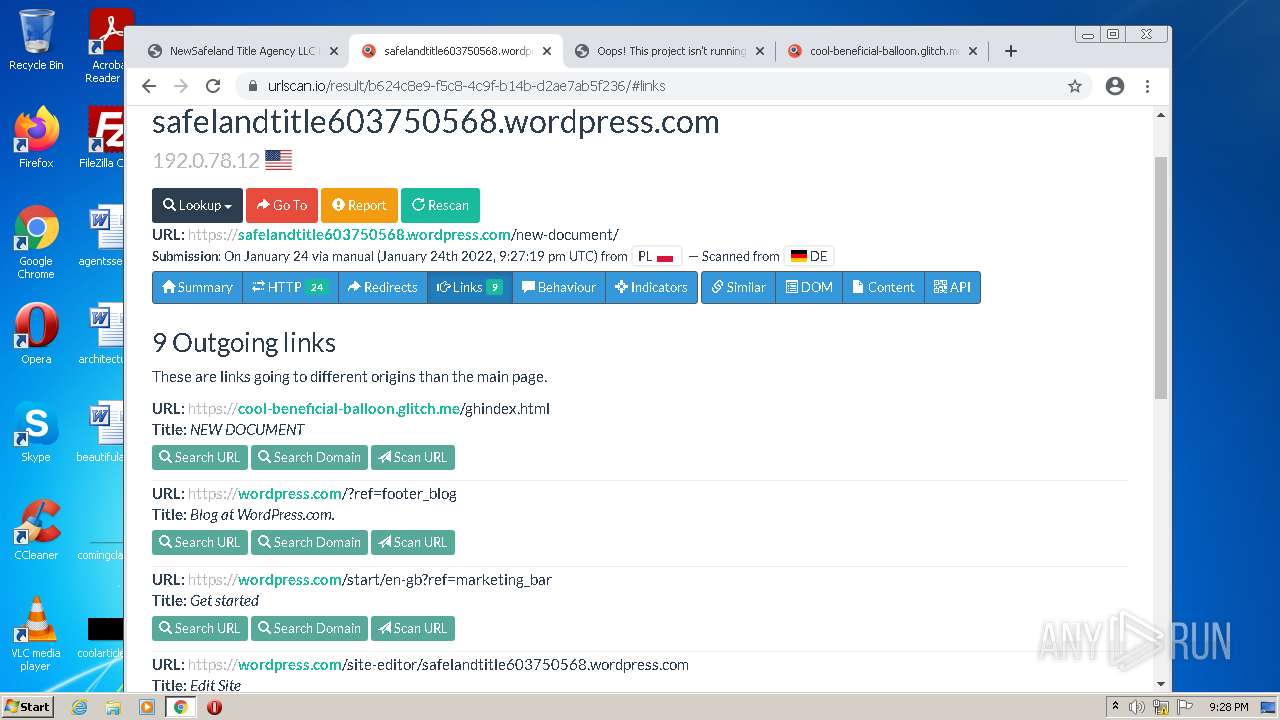
| File name: | NewSafeland Title Agency LLC Monday January 24 2022 925 AM.htm |
| Full analysis: | https://app.any.run/tasks/1fa1d999-9acd-4d18-83c3-24d74129cd8a |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 21:26:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Non-ISO extended-ASCII text, with CRLF, CR line terminators |
| MD5: | FF81675395513F00D2F901142BA488AA |
| SHA1: | B2485ADB3352BC140FDE38059573F2CCA1787432 |
| SHA256: | 502713D87259C486B965060E95D3006E45BA8156F49C2BF57E5119E2A231F6AB |
| SSDEEP: | 192:IX8TeoFH8IniRcLGPUvm1ETK5o50NSZE+D4r43anRY5zgkkS+UGYNs9o/QzHL6SS:IX8TKXyxoPMGvYgOp/s0PFi5BW |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3116)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3236)
- iexplore.exe (PID: 2348)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2572)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 3116)
Executable content was dropped or overwritten
- chrome.exe (PID: 3116)
INFO
Reads the computer name
- iexplore.exe (PID: 2196)
- iexplore.exe (PID: 3236)
- iexplore.exe (PID: 2348)
- iexplore.exe (PID: 3316)
- chrome.exe (PID: 2572)
- chrome.exe (PID: 2200)
- chrome.exe (PID: 3512)
- chrome.exe (PID: 3824)
- chrome.exe (PID: 700)
- chrome.exe (PID: 3104)
- chrome.exe (PID: 2508)
- chrome.exe (PID: 472)
- chrome.exe (PID: 2356)
Changes internet zones settings
- iexplore.exe (PID: 2196)
Checks supported languages
- iexplore.exe (PID: 2196)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 2348)
- chrome.exe (PID: 2572)
- chrome.exe (PID: 2200)
- chrome.exe (PID: 2772)
- chrome.exe (PID: 3824)
- iexplore.exe (PID: 3236)
- chrome.exe (PID: 4000)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 3512)
- chrome.exe (PID: 1432)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 700)
- chrome.exe (PID: 2052)
- chrome.exe (PID: 580)
- chrome.exe (PID: 1888)
- chrome.exe (PID: 2232)
- chrome.exe (PID: 3956)
- chrome.exe (PID: 2160)
- chrome.exe (PID: 3104)
- chrome.exe (PID: 4020)
- chrome.exe (PID: 2992)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 128)
- chrome.exe (PID: 2508)
- chrome.exe (PID: 1232)
- chrome.exe (PID: 472)
- chrome.exe (PID: 2376)
- chrome.exe (PID: 3100)
- chrome.exe (PID: 1620)
- chrome.exe (PID: 2932)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 2356)
- chrome.exe (PID: 3652)
- chrome.exe (PID: 2224)
- chrome.exe (PID: 304)
- chrome.exe (PID: 3364)
- chrome.exe (PID: 2532)
- chrome.exe (PID: 3344)
- chrome.exe (PID: 576)
- chrome.exe (PID: 3876)
- chrome.exe (PID: 3696)
- chrome.exe (PID: 2788)
- chrome.exe (PID: 2348)
- chrome.exe (PID: 3124)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 3768)
- chrome.exe (PID: 3116)
- chrome.exe (PID: 3948)
Application launched itself
- iexplore.exe (PID: 2196)
- iexplore.exe (PID: 3236)
- chrome.exe (PID: 2572)
Reads internet explorer settings
- iexplore.exe (PID: 3236)
- iexplore.exe (PID: 2348)
Manual execution by user
- chrome.exe (PID: 2572)
Reads the date of Windows installation
- iexplore.exe (PID: 2196)
- chrome.exe (PID: 472)
Reads the hosts file
- chrome.exe (PID: 2572)
- chrome.exe (PID: 2200)
Reads settings of System Certificates
- chrome.exe (PID: 2200)
- iexplore.exe (PID: 2196)
Checks Windows Trust Settings
- iexplore.exe (PID: 2196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Originator: | Microsoft Word 15 |
|---|---|
| Generator: | Microsoft Word 15 |
| ProgID: | Word.Document |
| ContentType: | text/html; charset=windows-1252 |
Total processes
90
Monitored processes
51
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3220 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1636 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 472 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3236 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3384 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2924 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1160 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3472 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2044 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1680 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,3232859079724927651,11007784367420244271,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2784 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
26 929
Read events
26 653
Write events
267
Delete events
9
Modification events
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 161162096 | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937449 | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 461327096 | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937449 | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
178
Text files
184
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2572 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EF198D-A0C.pma | — | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFFBF12611CC8144EE.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{473E4816-7D5C-11EC-A45D-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF3E9852F2539E7058.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{473E4815-7D5C-11EC-A45D-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFDB73A20FDDA2944E.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF3AD8D151A584D229.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{473E4813-7D5C-11EC-A45D-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4FEB0B5905F23A65.TMP | gmc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
62
DNS requests
47
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | — | — | whitelisted |
2196 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 5.78 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 9.90 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 7.10 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 43.6 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | fli | 21.1 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 88.7 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | binary | 9.90 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 720 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2200 | chrome.exe | 216.58.212.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 142.250.185.78:443 | clients2.google.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 142.250.186.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
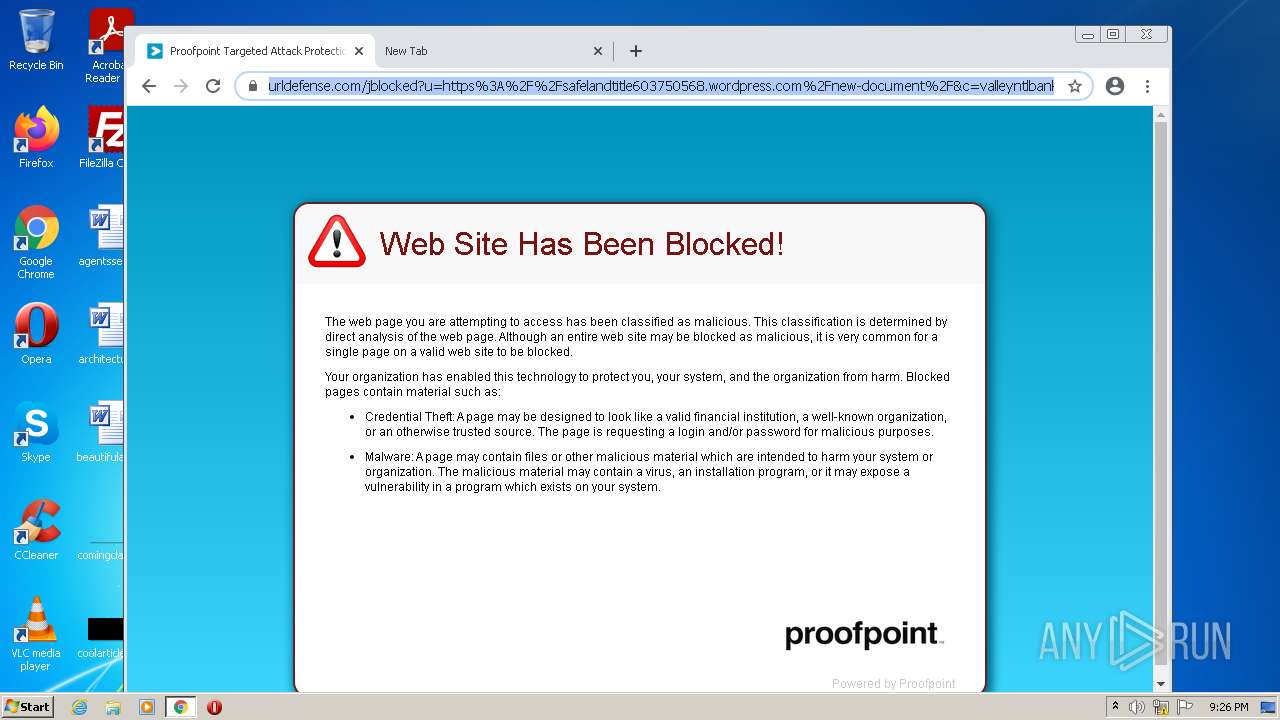
2200 | chrome.exe | 52.204.90.22:443 | urldefense.com | Amazon.com, Inc. | US | suspicious |
2200 | chrome.exe | 142.250.185.99:443 | update.googleapis.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 142.250.184.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
2200 | chrome.exe | 142.250.186.100:443 | www.google.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 142.250.185.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 142.250.184.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
urldefense.com |
| shared |
update.googleapis.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Suspicious Glitch Hosted DNS Request - Possible Phishing Landing |
2200 | chrome.exe | Misc activity | ET INFO Suspicious Glitch Hosted TLS SNI Request - Possible Phishing Landing |
2200 | chrome.exe | Misc activity | ET INFO Suspicious Glitch Hosted TLS SNI Request - Possible Phishing Landing |