| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/e8d6387c-381b-46d3-9151-ce3c58ec9a1a |
| Verdict: | Malicious activity |
| Analysis date: | November 05, 2023, 11:24:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 240BDB7AF8CAE7C1129099DB2E72FCA0 |
| SHA1: | FD8A3D2901020CB7552596DC28E4ACD82B4BAAA1 |
| SHA256: | 501CA30174426B8E1ADDD980955C9BA6C4368AB6B4E20B85271AD81390148AFC |
| SSDEEP: | 98304:6TdWSXLMXwMSTeJy4JXN8JNiL8NDklbe+5WPv7wZVqmJwXxtl1B8ZzI0c59RA1r5:bsVx10G29F |
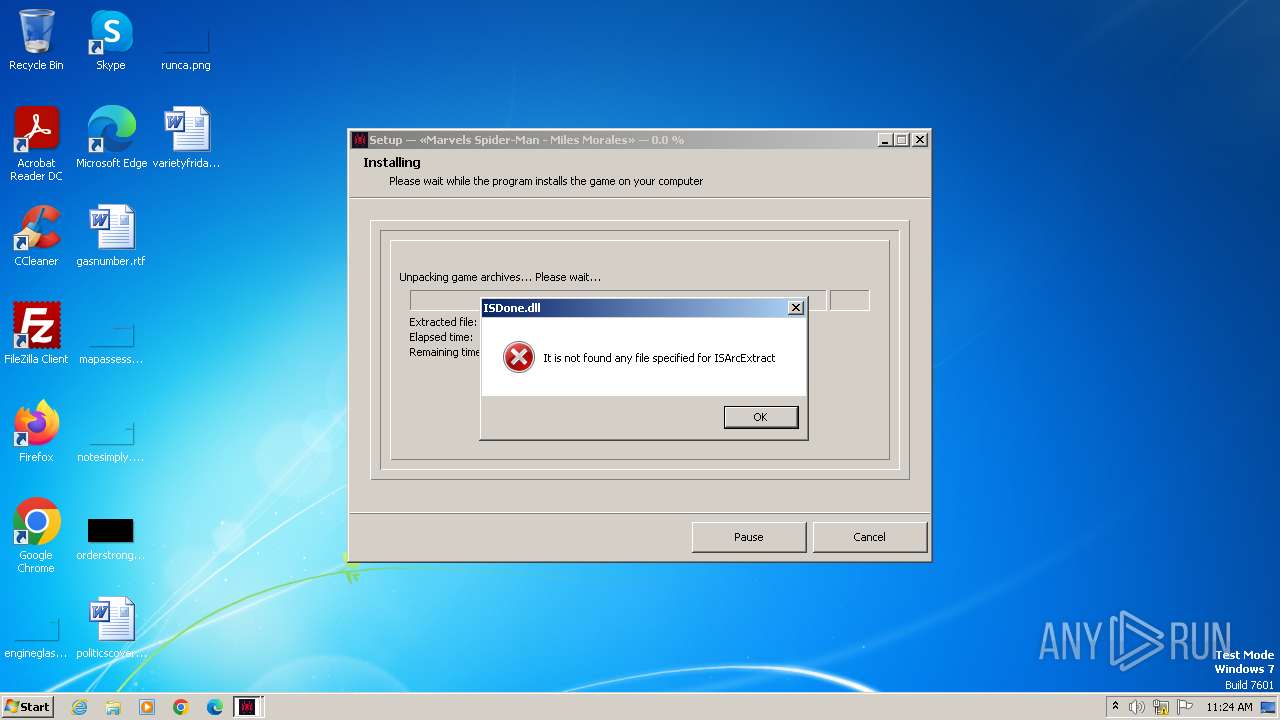
MALICIOUS
Drops the executable file immediately after the start
- Setup.exe (PID: 3480)
- _iu14D2N.tmp (PID: 3660)
- unins000.exe (PID: 3652)
- Setup.tmp (PID: 3500)
SUSPICIOUS
Process drops legitimate windows executable
- Setup.tmp (PID: 3500)
- _iu14D2N.tmp (PID: 3660)
Starts application with an unusual extension
- unins000.exe (PID: 3652)
Reads the Windows owner or organization settings
- _iu14D2N.tmp (PID: 3660)
- Setup.tmp (PID: 3500)
Starts itself from another location
- unins000.exe (PID: 3652)
Drops 7-zip archiver for unpacking
- Setup.tmp (PID: 3500)
INFO
Checks supported languages
- Setup.tmp (PID: 3500)
- Setup.exe (PID: 3480)
- unins000.exe (PID: 3652)
- _iu14D2N.tmp (PID: 3660)
Reads the computer name
- Setup.tmp (PID: 3500)
Create files in a temporary directory
- unins000.exe (PID: 3652)
- Setup.tmp (PID: 3500)
- Setup.exe (PID: 3480)
- _iu14D2N.tmp (PID: 3660)
Reads the machine GUID from the registry
- Setup.tmp (PID: 3500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:10:02 07:04:04+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 86016 |
| InitializedDataSize: | 116736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16478 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | dixen18 |
| FileDescription: | MSMR-MM Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | MSMR-MM |
| ProductVersion: |
Total processes
42
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3216 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: dixen18 Integrity Level: MEDIUM Description: MSMR-MM Setup Exit code: 3221226540 Version: Modules
| |||||||||||||||
| 3480 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: dixen18 Integrity Level: HIGH Description: MSMR-MM Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3500 | "C:\Users\admin\AppData\Local\Temp\is-I0V5R.tmp\Setup.tmp" /SL5="$80134,4118480,203776,C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-I0V5R.tmp\Setup.tmp | — | Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3652 | "C:\Games\MSMR-MM\Uninstall\unins000.exe" /Silent | C:\Games\MSMR-MM\Uninstall\unins000.exe | — | Setup.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3660 | "C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp" /SECONDPHASE="C:\Games\MSMR-MM\Uninstall\unins000.exe" /FIRSTPHASEWND=$50170 /Silent | C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp | — | unins000.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
155
Read events
145
Write events
0
Delete events
10
Modification events
| (PID) Process: | (3660) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MSMR-MM_is1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3660) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Insomniac Games\Marvel's Spider-Man Miles Morales |
| Operation: | delete value | Name: | englishVO |
Value: 0 | |||
| (PID) Process: | (3660) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Insomniac Games\Marvel's Spider-Man Miles Morales |
| Operation: | delete value | Name: | TextLanguage |
Value: 14 | |||
| (PID) Process: | (3660) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Insomniac Games\Marvel's Spider-Man Miles Morales |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3660) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete value | Name: | C:\Games\MSMR-MM\MilesMorales.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (3660) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3500) Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3500) Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 6555869F4BF17984F6C6AC8697EE71770CDE7B5B547E9169264E9E6A875FA64E | |||
| (PID) Process: | (3500) Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: AC0D0000B846469ADA0FDA01 | |||
| (PID) Process: | (3500) Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
19
Suspicious files
1
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3480 | Setup.exe | C:\Users\admin\AppData\Local\Temp\is-I0V5R.tmp\Setup.tmp | executable | |
MD5:DD2DBE8B2EC560D07560679CB0CFF87E | SHA256:5D4FFCB88DC7CD190A0C2EC1CD9163578917C0181174BD08C46F6424D519D771 | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\CLS-srep.dll | executable | |
MD5:9E1E200472D66356A4AE5D597B01DABC | SHA256:87DF573AC240E09EA4941E169FB2D15D5316A1B0E053446B8144E04B1154F061 | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\image.bmp | image | |
MD5:BFDEF6D84B98E5773CE1F7358AD11786 | SHA256:B9967BC7ACE2E130DBF05A2A3CF33428583E40DD0DB5954619FD52D141DCBE12 | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\english.ini | text | |
MD5:B031BEE9106D82782B43BDF5D4AD79B0 | SHA256:E1B6F4DC9BA12E110B33D370E8F06F176228059C42754BE5DA7B92AB939FF38E | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\unarc.dll | executable | |
MD5:2CED17F02B24372C166FAAF7DA2DFFB3 | SHA256:89952411324163A635942DB33DD0087508E20D112E1E75403DC1D5E852927DD7 | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\QIcon.ico | image | |
MD5:C51102DACF0506D628911D37D8AEA2C9 | SHA256:5F8D6210FEBCA3B6780249912872CF3E9CB0D9B5E7A59A88F80F68392BB34789 | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\WinTB.dll | executable | |
MD5:348F5C9651B979191373EBA950D0EDC3 | SHA256:6922915886745D1B59320DEE9A87311AADD57F924FFB73CAC1D27573E75BCECC | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\arc.ini | text | |
MD5:49C4CD5C133D6DC2FD1480E6590139CD | SHA256:C7366208066F5AD1BA4CD319A09C2DC7CB47F1A113C9719901B68E98291B5421 | |||
| 3500 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HLQMP.tmp\facompress_mt.dll | executable | |
MD5:002508839634E56D43E4FD56E3DF2757 | SHA256:7EEB2C50920E30544E2F180B0C39488501372A8F8BD8393BCB095353E9114CDE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |