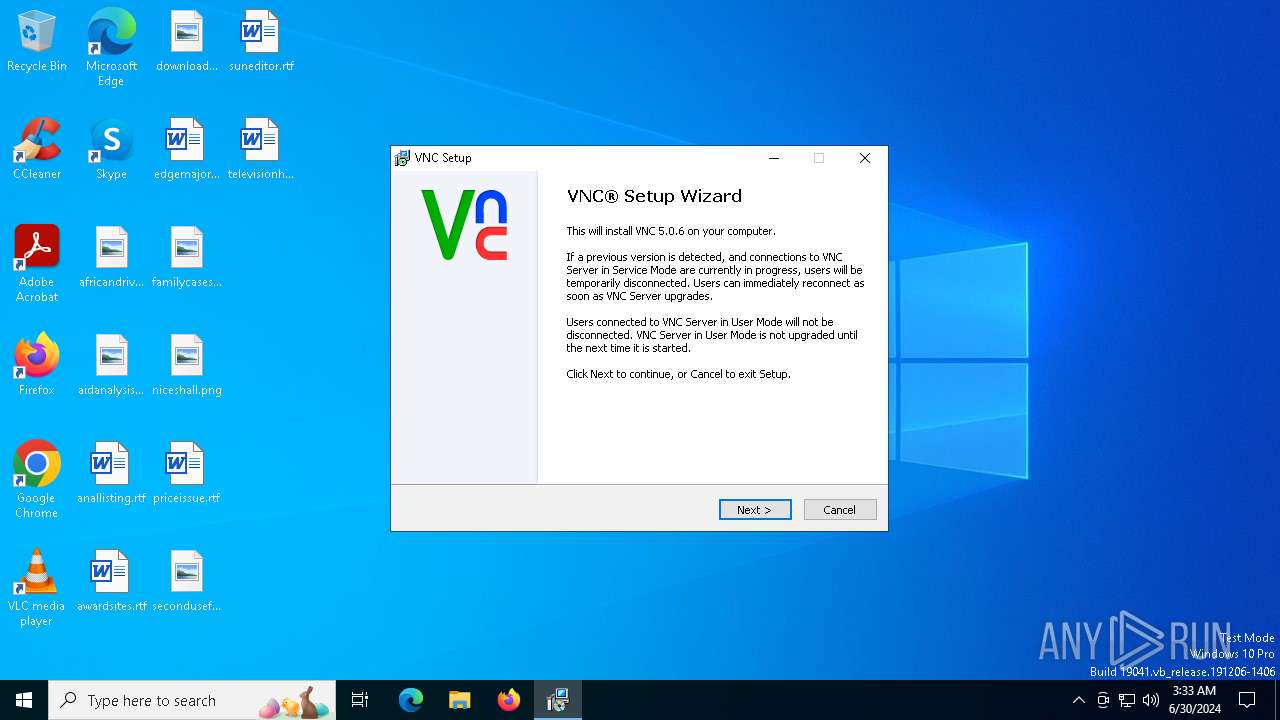
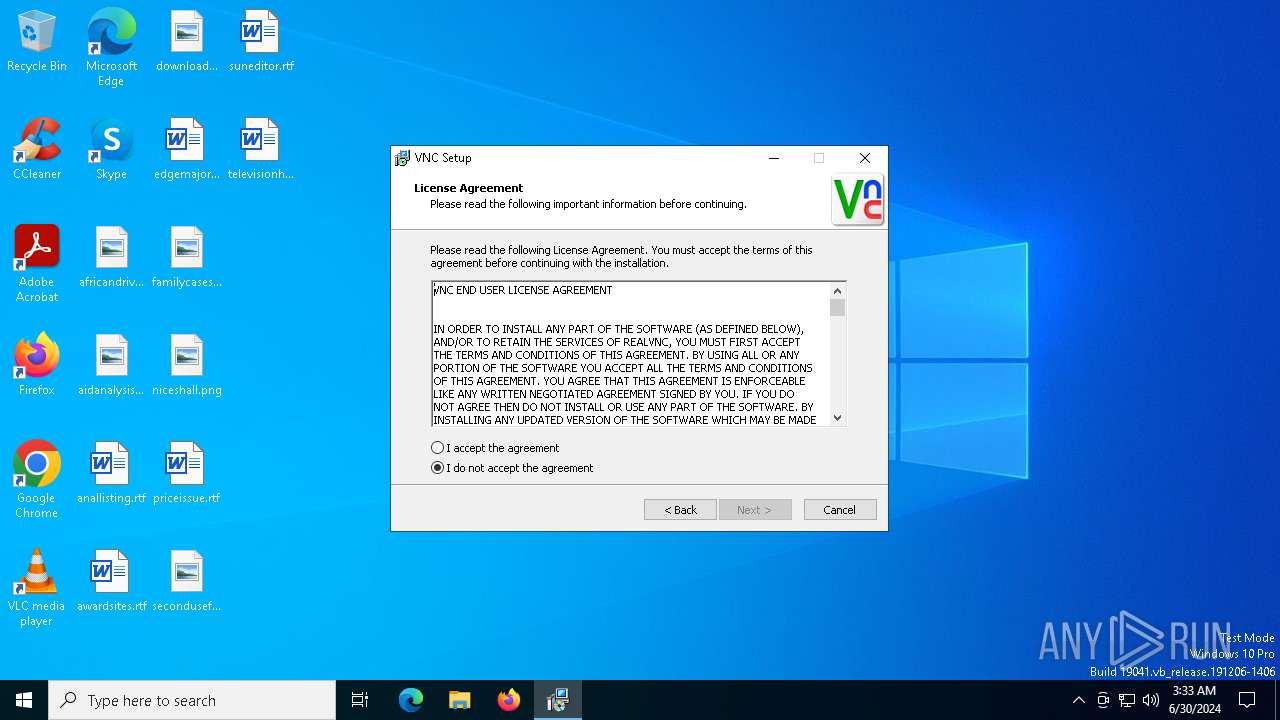
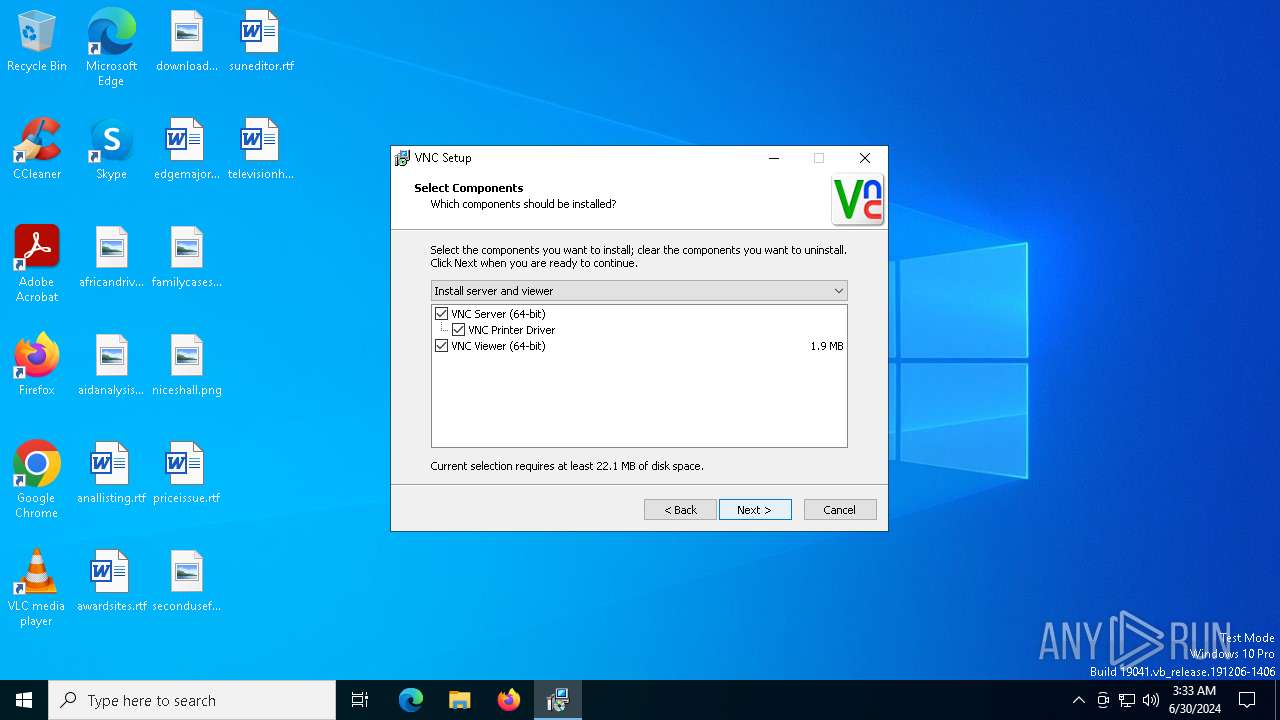
| File name: | VNC-5.0.6-Windows.exe |
| Full analysis: | https://app.any.run/tasks/9324517b-dad6-47b2-b534-7b7ea2ed4af2 |
| Verdict: | Malicious activity |
| Analysis date: | June 30, 2024, 03:33:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A55FDE0C7B8178246C200F80DE36CFBF |
| SHA1: | 91161A1967CCD07C25A16975C672639AC9017C34 |
| SHA256: | 500D6EB4F5FF7D86BDFD2AE20BF05738DB6B1B3C52FEDD354DF27CD3DA178D75 |
| SSDEEP: | 98304:OInpCxa1t0vmFoNtv34IxltirRqbvHKS51pYTN0a08nPmCqkZo8UPrl/2zXqieb4:Ju7o+qC4 |
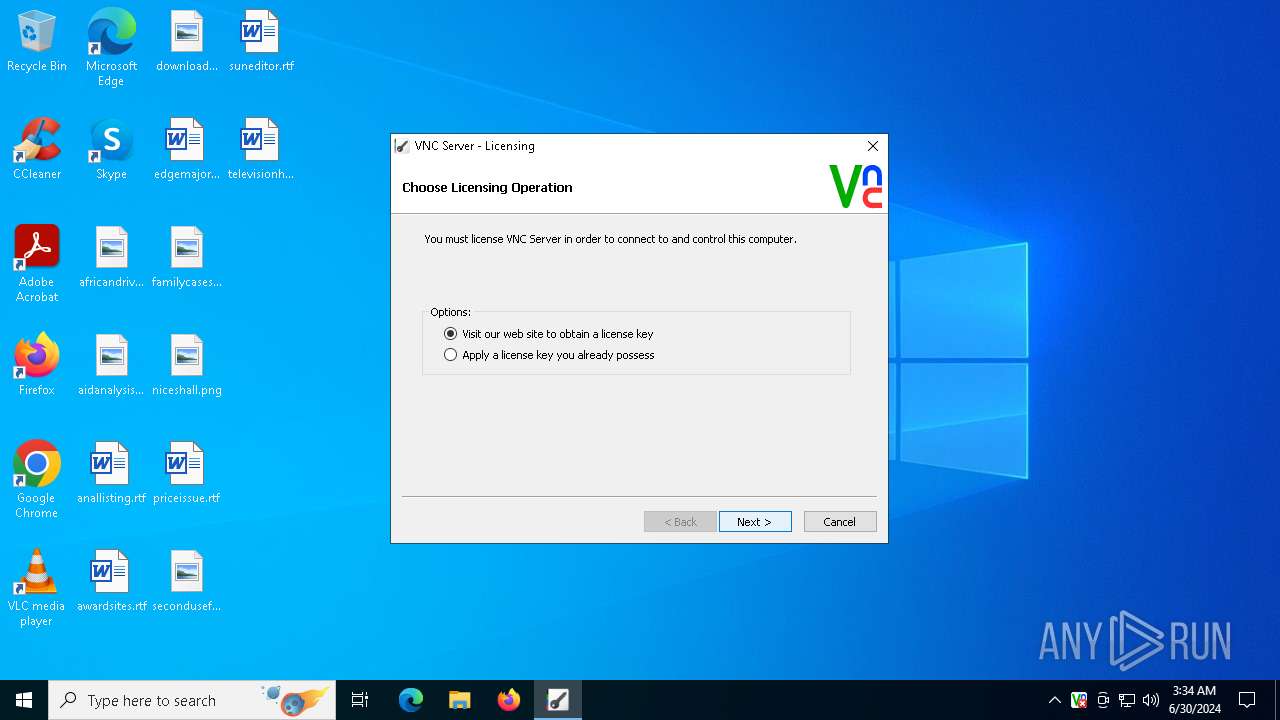
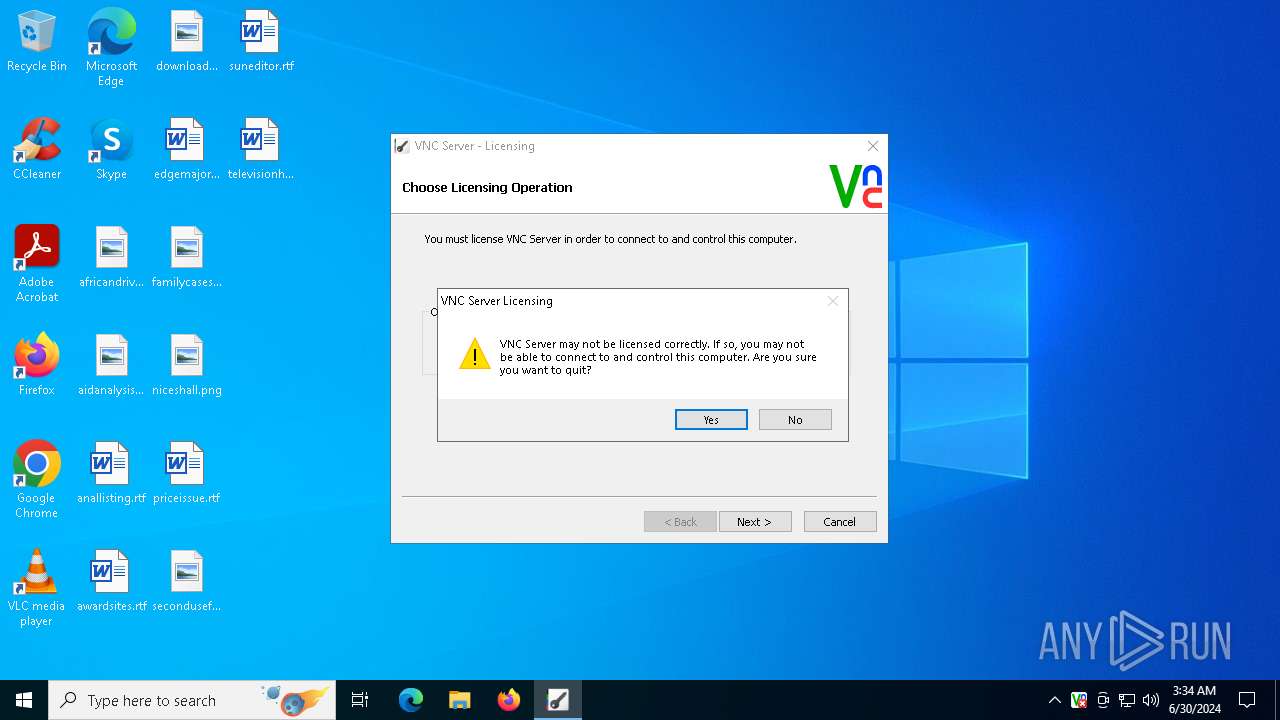
MALICIOUS
Drops the executable file immediately after the start
- VNC-5.0.6-Windows.exe (PID: 1276)
- VNC-5.0.6-Windows.exe (PID: 2060)
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.exe (PID: 4380)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.exe (PID: 2560)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
- printerinst.exe (PID: 5484)
Creates a writable file in the system directory
- printerinst.exe (PID: 5484)
SUSPICIOUS
Executable content was dropped or overwritten
- VNC-5.0.6-Windows.exe (PID: 1276)
- VNC-5.0.6-Windows.exe (PID: 2060)
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.exe (PID: 4380)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
- printerinst.exe (PID: 5484)
- vnc-printer-1_8_0-x86_x64_win32.exe (PID: 2560)
Reads security settings of Internet Explorer
- VNC-5.0.6-Windows.tmp (PID: 3180)
Reads the date of Windows installation
- VNC-5.0.6-Windows.tmp (PID: 3180)
Reads the Windows owner or organization settings
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
Process drops legitimate windows executable
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
- printerinst.exe (PID: 5484)
Searches for installed software
- VNC-5.0.6-Windows.tmp (PID: 884)
Application launched itself
- vncserver.exe (PID: 5864)
- vncserver.exe (PID: 2452)
Executes as Windows Service
- vncserver.exe (PID: 5864)
INFO
Create files in a temporary directory
- VNC-5.0.6-Windows.exe (PID: 2060)
- VNC-5.0.6-Windows.exe (PID: 1276)
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.exe (PID: 4380)
- vnc-printer-1_8_0-x86_x64_win32.exe (PID: 2560)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
Process checks computer location settings
- VNC-5.0.6-Windows.tmp (PID: 3180)
Checks supported languages
- VNC-5.0.6-Windows.exe (PID: 2060)
- VNC-5.0.6-Windows.exe (PID: 1276)
- VNC-5.0.6-Windows.tmp (PID: 3180)
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.exe (PID: 4380)
- vnclicensewiz64.exe (PID: 2764)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.exe (PID: 2560)
- printerinst.exe (PID: 5484)
- vncserver.exe (PID: 2300)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
- vncserver.exe (PID: 4020)
- vncserver.exe (PID: 4104)
- vncserver.exe (PID: 2452)
- vncserver.exe (PID: 8)
- vncserver.exe (PID: 5968)
- vncserver.exe (PID: 2252)
- vncserver.exe (PID: 5864)
- vncserver.exe (PID: 5132)
- vnclicensewiz.exe (PID: 5952)
Reads the computer name
- VNC-5.0.6-Windows.tmp (PID: 3180)
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
- printerinst.exe (PID: 5484)
- vncserver.exe (PID: 2300)
- vncserver.exe (PID: 4020)
- vncserver.exe (PID: 8)
- vncserver.exe (PID: 4104)
- vncserver.exe (PID: 5968)
- vncserver.exe (PID: 2252)
- vncserver.exe (PID: 5864)
- vncserver.exe (PID: 2452)
- vnclicensewiz.exe (PID: 5952)
- vncserver.exe (PID: 5132)
Creates files in the program directory
- VNC-5.0.6-Windows.tmp (PID: 884)
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
Creates a software uninstall entry
- VNC-Viewer-5.0.6-Windows.tmp (PID: 4796)
- vnc-printer-1_8_0-x86_x64_win32.tmp (PID: 5100)
- VNC-5.0.6-Windows.tmp (PID: 884)
Reads the machine GUID from the registry
- vncserver.exe (PID: 2300)
- vncserver.exe (PID: 5864)
- vncserver.exe (PID: 2452)
Reads CPU info
- vncserver.exe (PID: 2452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c40 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | RealVNC Ltd |
| FileDescription: | VNC® Setup |
| FileVersion: | |
| LegalCopyright: | Copyright © 2002-2013 RealVNC Ltd. |
| ProductName: | VNC Server |
| ProductVersion: | 5.0.6 |
Total processes
158
Monitored processes
29
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\Program Files\RealVNC\VNC Server\vncserver.exe" -stop | C:\Program Files\RealVNC\VNC Server\vncserver.exe | — | VNC-5.0.6-Windows.tmp | |||||||||||
User: admin Company: RealVNC Ltd Integrity Level: HIGH Description: VNC® Server Exit code: 0 Version: 5.0.6 (r113416) Modules
| |||||||||||||||
| 884 | "C:\Users\admin\AppData\Local\Temp\is-E0PRM.tmp\VNC-5.0.6-Windows.tmp" /SL5="$170292,6930355,54272,C:\Users\admin\AppData\Local\Temp\VNC-5.0.6-Windows.exe" /SPAWNWND=$502AC /NOTIFYWND=$80040 | C:\Users\admin\AppData\Local\Temp\is-E0PRM.tmp\VNC-5.0.6-Windows.tmp | VNC-5.0.6-Windows.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\AppData\Local\Temp\VNC-5.0.6-Windows.exe" | C:\Users\admin\AppData\Local\Temp\VNC-5.0.6-Windows.exe | explorer.exe | ||||||||||||
User: admin Company: RealVNC Ltd Integrity Level: MEDIUM Description: VNC® Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vncserver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\AppData\Local\Temp\VNC-5.0.6-Windows.exe" /SPAWNWND=$502AC /NOTIFYWND=$80040 | C:\Users\admin\AppData\Local\Temp\VNC-5.0.6-Windows.exe | VNC-5.0.6-Windows.tmp | ||||||||||||
User: admin Company: RealVNC Ltd Integrity Level: HIGH Description: VNC® Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2252 | "C:\Program Files\RealVNC\VNC Server\vncserver.exe" -start -showstatus | C:\Program Files\RealVNC\VNC Server\vncserver.exe | — | VNC-5.0.6-Windows.tmp | |||||||||||
User: admin Company: RealVNC Ltd Integrity Level: HIGH Description: VNC® Server Exit code: 0 Version: 5.0.6 (r113416) Modules
| |||||||||||||||
| 2300 | "C:\Program Files\RealVNC\VNC Server\vncserver.exe" -service -noconsole -generatekeys | C:\Program Files\RealVNC\VNC Server\vncserver.exe | — | VNC-5.0.6-Windows.tmp | |||||||||||
User: admin Company: RealVNC Ltd Integrity Level: HIGH Description: VNC® Server Exit code: 0 Version: 5.0.6 (r113416) Modules
| |||||||||||||||
| 2300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vncserver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2452 | "C:\Program Files\RealVNC\VNC Server\vncserver.exe" -service -noconsole -slave 127.0.0.1::49736 -1062056510 | C:\Program Files\RealVNC\VNC Server\vncserver.exe | — | vncserver.exe | |||||||||||
User: SYSTEM Company: RealVNC Ltd Integrity Level: SYSTEM Description: VNC® Server Version: 5.0.6 (r113416) Modules
| |||||||||||||||
| 2560 | "C:\Program Files\RealVNC\VNC Server\vnc-printer-1_8_0-x86_x64_win32.exe" /DIR="C:\Program Files\RealVNC\VNC Server\Printer Driver" /SP- /VERYSILENT /NORESTART /RESTARTEXITCODE=32123 | C:\Program Files\RealVNC\VNC Server\vnc-printer-1_8_0-x86_x64_win32.exe | VNC-5.0.6-Windows.tmp | ||||||||||||
User: admin Company: RealVNC Ltd. Integrity Level: HIGH Description: VNC® Printer Driver Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
9 293
Read events
9 214
Write events
79
Delete events
0
Modification events
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.4.2 (a) | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\RealVNC\VNC Viewer | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\RealVNC\VNC Viewer\ | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: RealVNC | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | Inno Setup: Deselected Tasks |
Value: desktopicon,quicklaunchicon | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: default | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | DisplayName |
Value: VNC Viewer 5.0.6 | |||
| (PID) Process: | (4796) VNC-Viewer-5.0.6-Windows.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RealVNCViewer_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\RealVNC\VNC Viewer\VNCViewer.exe,0 | |||
Executable files
73
Suspicious files
16
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1276 | VNC-5.0.6-Windows.exe | C:\Users\admin\AppData\Local\Temp\is-S14F2.tmp\VNC-5.0.6-Windows.tmp | executable | |
MD5:C765336F0DCF4EFDCC2101EED67CD30C | SHA256:C5177FDC6031728E10141745CD69EDBC91C92D14411A2DEC6E8E8CAA4F74AB28 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Users\admin\AppData\Local\Temp\is-BD5R2.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Users\admin\AppData\Local\Temp\is-BD5R2.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Program Files\RealVNC\VNC Server\vncserver.exe | executable | |
MD5:A7AA51017D4FB08EFA75F01CCEED482E | SHA256:53A9A2195DC879920775EBC6F8809EC90F86D7B4F288E71B20921FD11B040882 | |||
| 2060 | VNC-5.0.6-Windows.exe | C:\Users\admin\AppData\Local\Temp\is-E0PRM.tmp\VNC-5.0.6-Windows.tmp | executable | |
MD5:C765336F0DCF4EFDCC2101EED67CD30C | SHA256:C5177FDC6031728E10141745CD69EDBC91C92D14411A2DEC6E8E8CAA4F74AB28 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Program Files\RealVNC\VNC Server\is-HJ48V.tmp | executable | |
MD5:6C5281B0D5766586B508A685FB3E620B | SHA256:A969D8EDBCAF8F4252BBB2FCB75DDC24915B2B3B74F3A0B63A5EB596E9F319F4 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Program Files\RealVNC\VNC Server\desktop_dupl.dll | executable | |
MD5:1B932AEE21660AD1BC10362500735818 | SHA256:431896022AD8E3BFF03B4638EDA1CACC29E2091517333ECA1FE513A7D0EE0DA6 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Program Files\RealVNC\VNC Server\unins000.exe | executable | |
MD5:6C5281B0D5766586B508A685FB3E620B | SHA256:A969D8EDBCAF8F4252BBB2FCB75DDC24915B2B3B74F3A0B63A5EB596E9F319F4 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Program Files\RealVNC\VNC Server\saslib.dll | executable | |
MD5:E967D7C16733BADCC1727B64265E52A4 | SHA256:F48629A8BACB778719E27554CD790DABAB7D1940F4B9CFD77ACE1B93BAD0CDC2 | |||
| 884 | VNC-5.0.6-Windows.tmp | C:\Program Files\RealVNC\VNC Server\is-O0RQI.tmp | executable | |
MD5:A7AA51017D4FB08EFA75F01CCEED482E | SHA256:53A9A2195DC879920775EBC6F8809EC90F86D7B4F288E71B20921FD11B040882 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
59
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
2064 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5440 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
2660 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5440 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2480 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2272 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1060 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 20.189.173.6:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
2064 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |