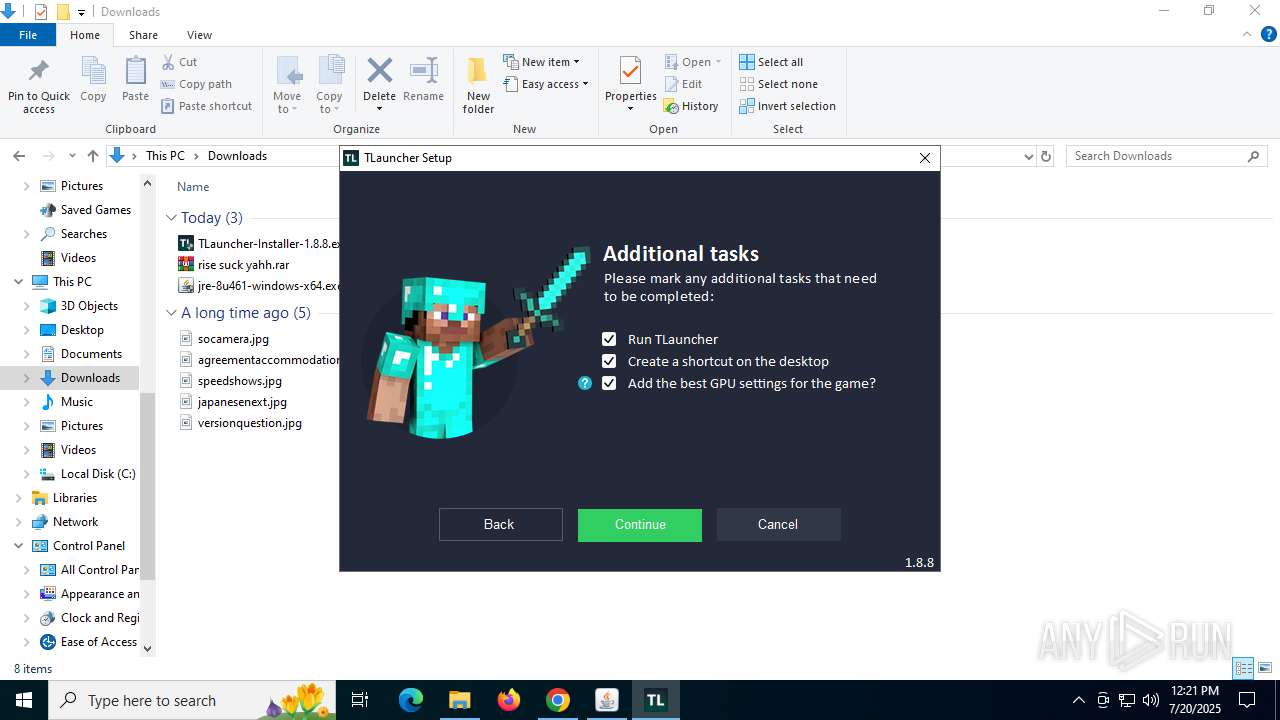
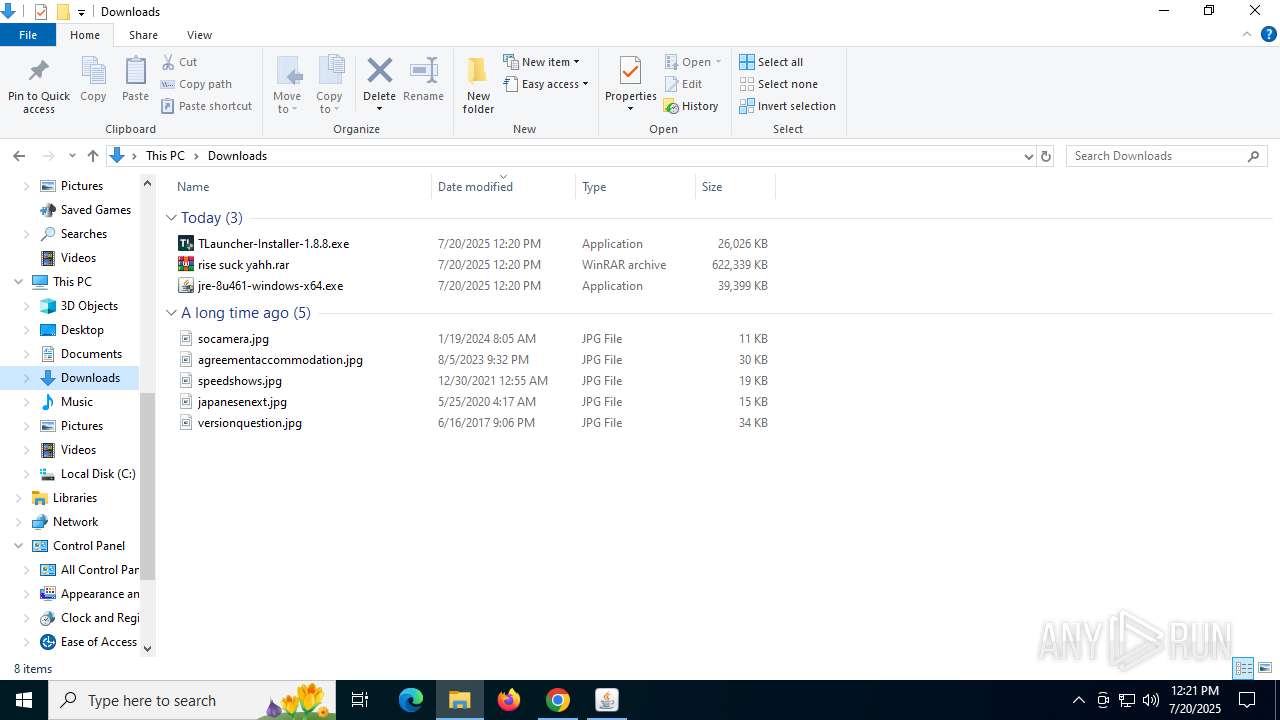
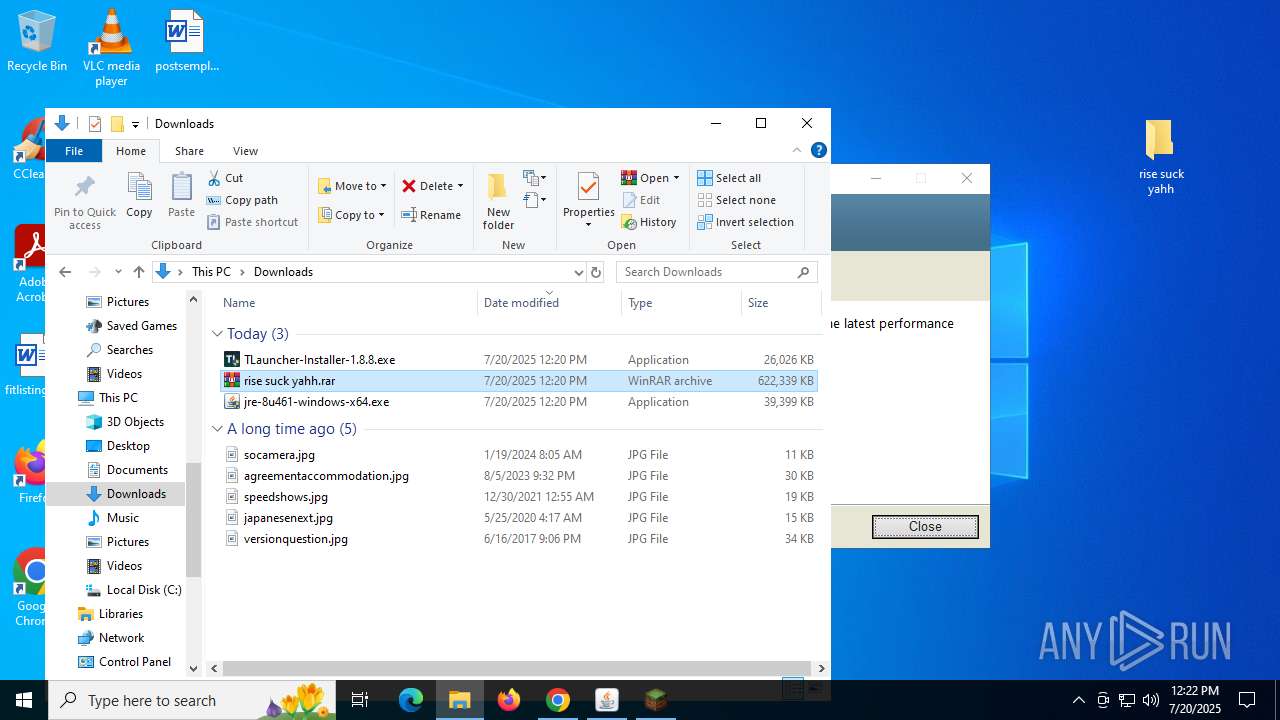
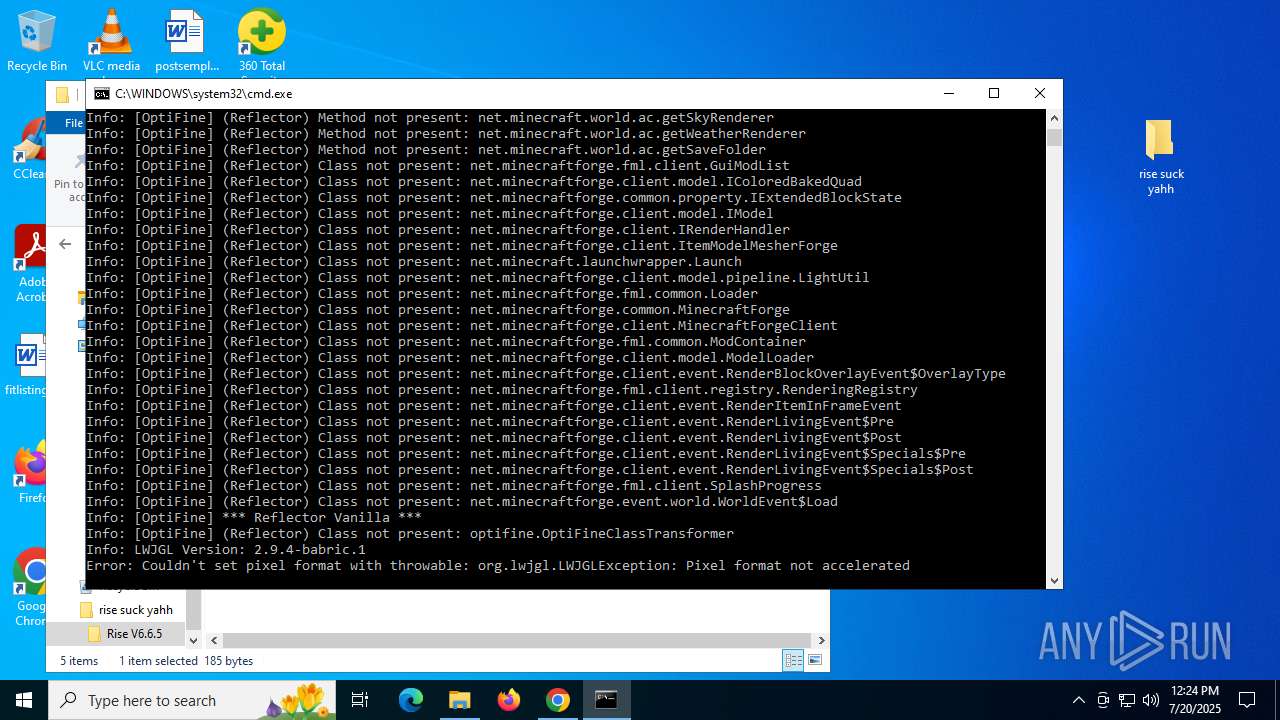
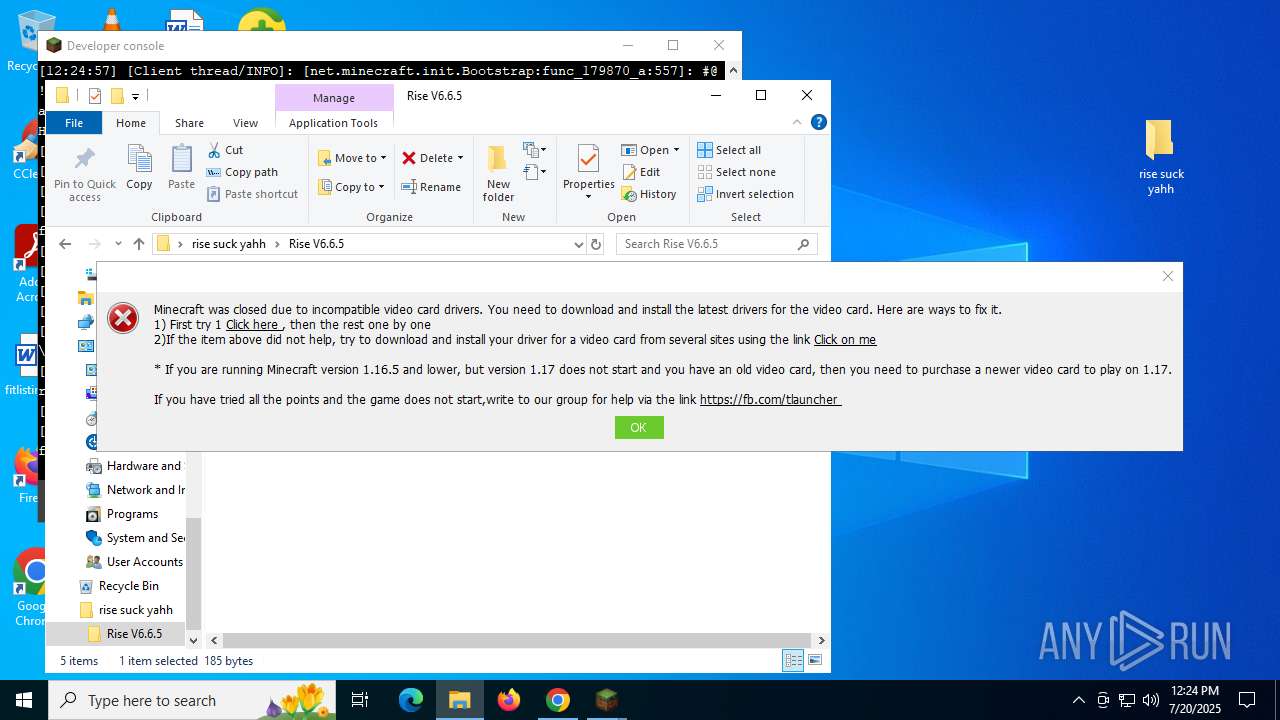
| URL: | https://drive.google.com/file/d/1_wU0nKw7_E21-bmk61SEJ7O3ayoZNIQz/view?pli=1 |
| Full analysis: | https://app.any.run/tasks/f4987026-9dc8-4f4d-9a21-94f1356ea2ab |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | July 20, 2025, 12:19:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D8D95489465FE27B89B31CAEF86BB8FE |
| SHA1: | 812A4A3C02A91D83089D64E9DDB3D2EE4322A147 |
| SHA256: | 4FCECF0C7F1D99CDC75527F34E740F2022956E45A83F5881183F32EDED09D199 |
| SSDEEP: | 3:N8PMMtZJuloASBsnIoObMck4mI3M5:2ABUsnjObdk4S5 |
MALICIOUS
Actions looks like stealing of personal data
- irsetup.exe (PID: 7132)
- 360TS_Setup.exe (PID: 8404)
- PowerSaver.exe (PID: 8568)
- regsvr32.exe (PID: 7476)
- WscReg.exe (PID: 8812)
- csrss.exe (PID: 608)
- WscReg.exe (PID: 8800)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 7712)
- csrss.exe (PID: 524)
- QHActiveDefense.exe (PID: 3048)
- QHSafeTray.exe (PID: 5264)
- regsvr32.exe (PID: 8536)
- QHSafeTray.exe (PID: 1244)
- PopWndLog.exe (PID: 7488)
- QHSafeTray.exe (PID: 2536)
- PopWndLog.exe (PID: 7528)
- KB931125-rootsupd.exe (PID: 188)
- regsvr32.exe (PID: 8980)
- regsvr32.exe (PID: 5904)
- WscReg.exe (PID: 7428)
- WscReg.exe (PID: 2876)
Changes the autorun value in the registry
- 360TS_Setup.exe (PID: 8404)
- QHActiveDefense.exe (PID: 7712)
- KB931125-rootsupd.exe (PID: 188)
Registers / Runs the DLL via REGSVR32.EXE
- 360TS_Setup.exe (PID: 8404)
- QHSafeTray.exe (PID: 1244)
- QHActiveDefense.exe (PID: 7712)
Executing a file with an untrusted certificate
- PowerSaver.exe (PID: 8568)
- EaInstHelper64.exe (PID: 2848)
- QHWatchdog.exe (PID: 8128)
- KB931125-rootsupd.exe (PID: 188)
- QHWatchdog.exe (PID: 4860)
- javaw.exe (PID: 3576)
Application was injected by another process
- explorer.exe (PID: 4772)
Runs injected code in another process
- QHSafeTray.exe (PID: 1244)
SUSPICIOUS
Reads security settings of Internet Explorer
- jre-8u461-windows-x64.exe (PID: 8132)
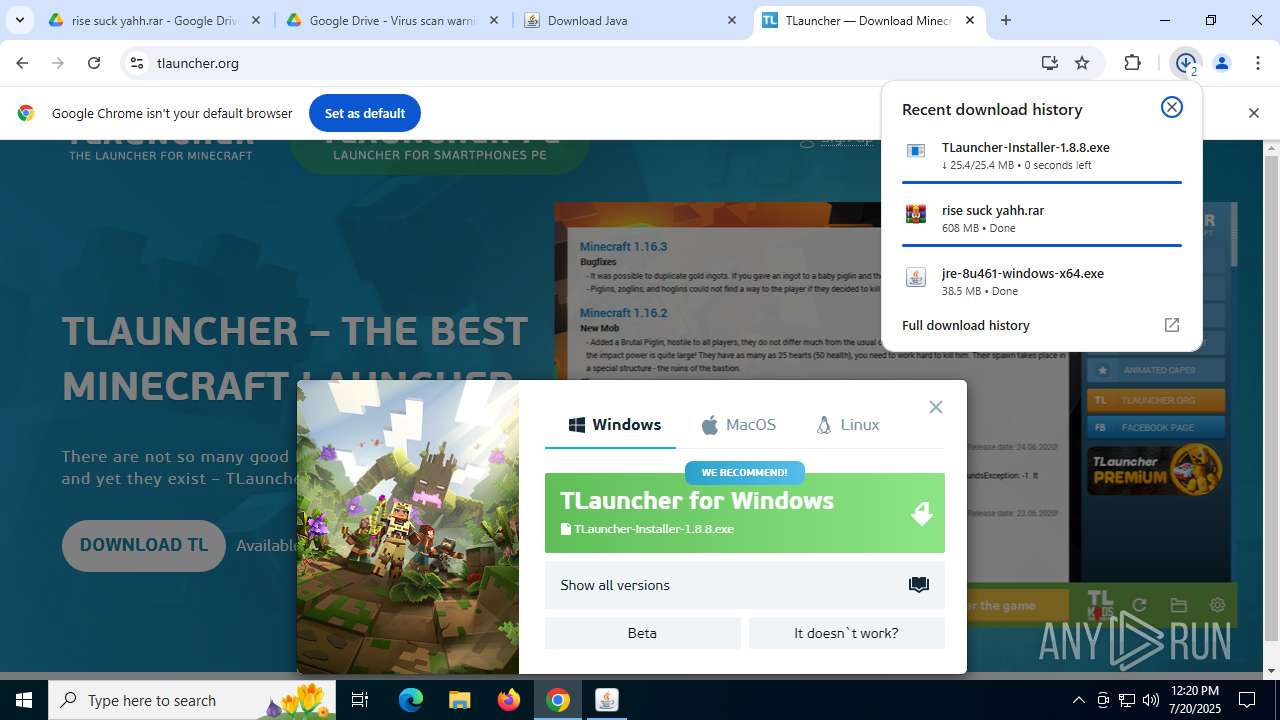
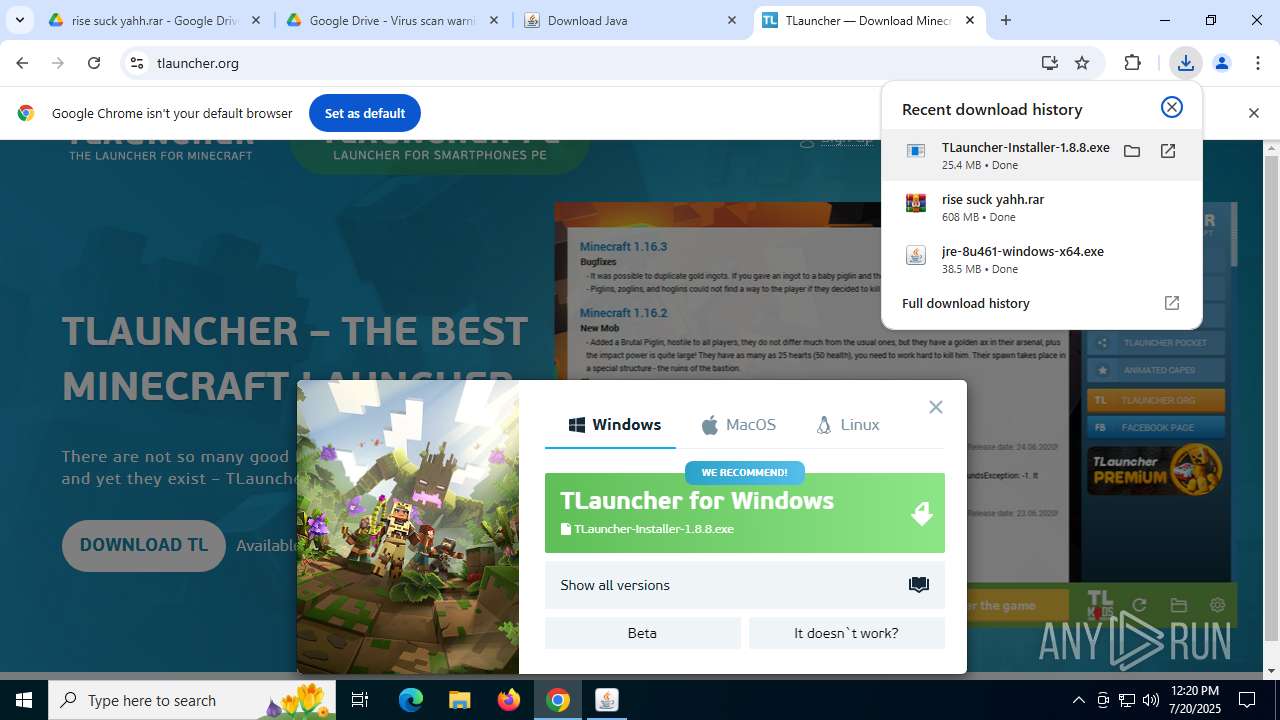
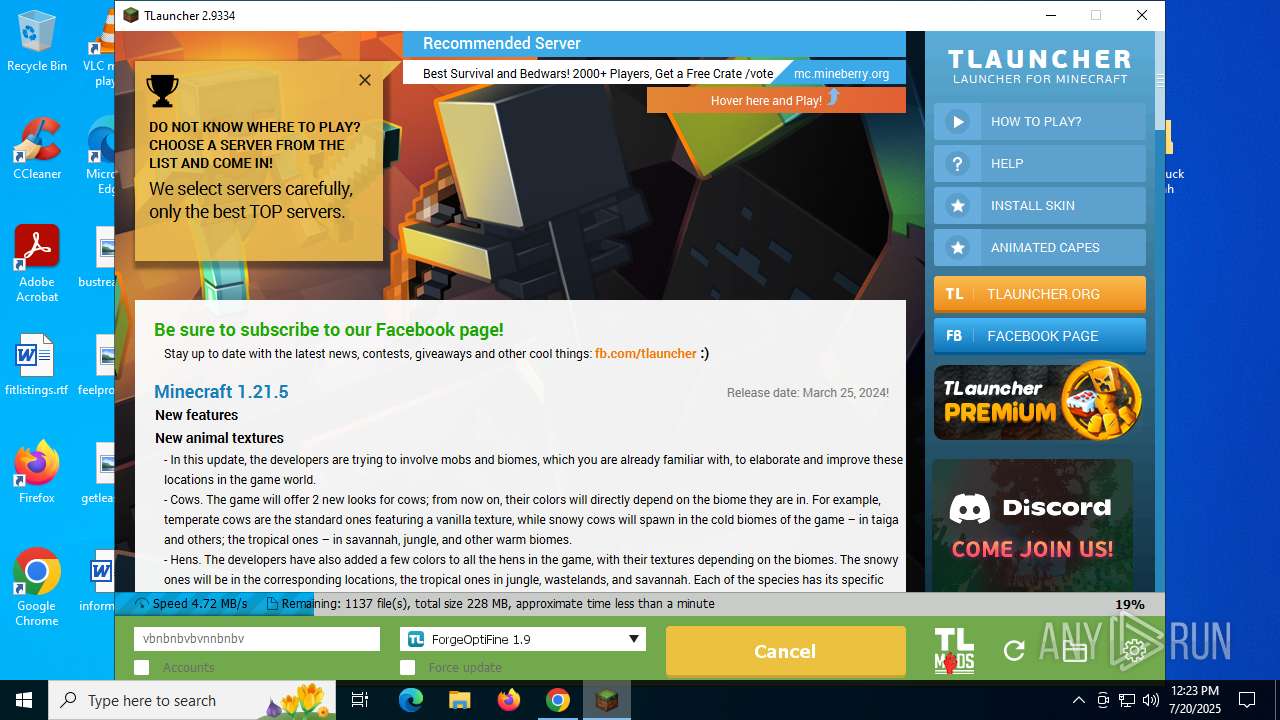
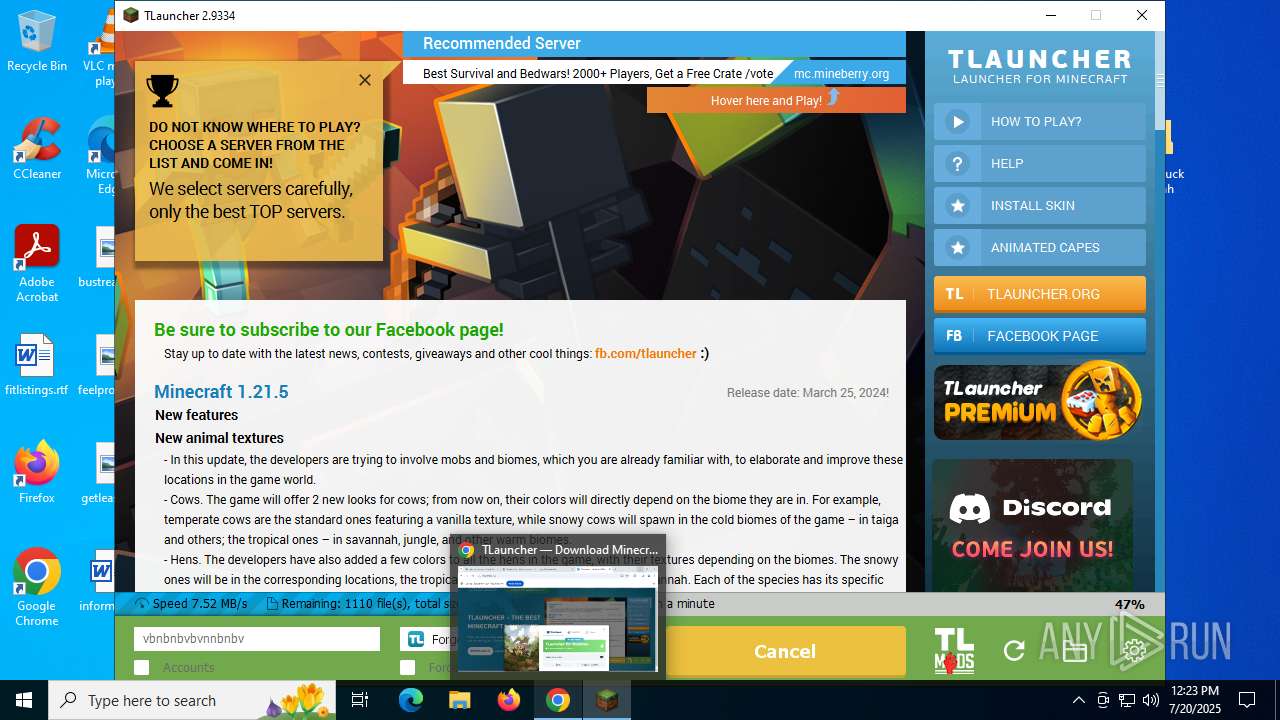
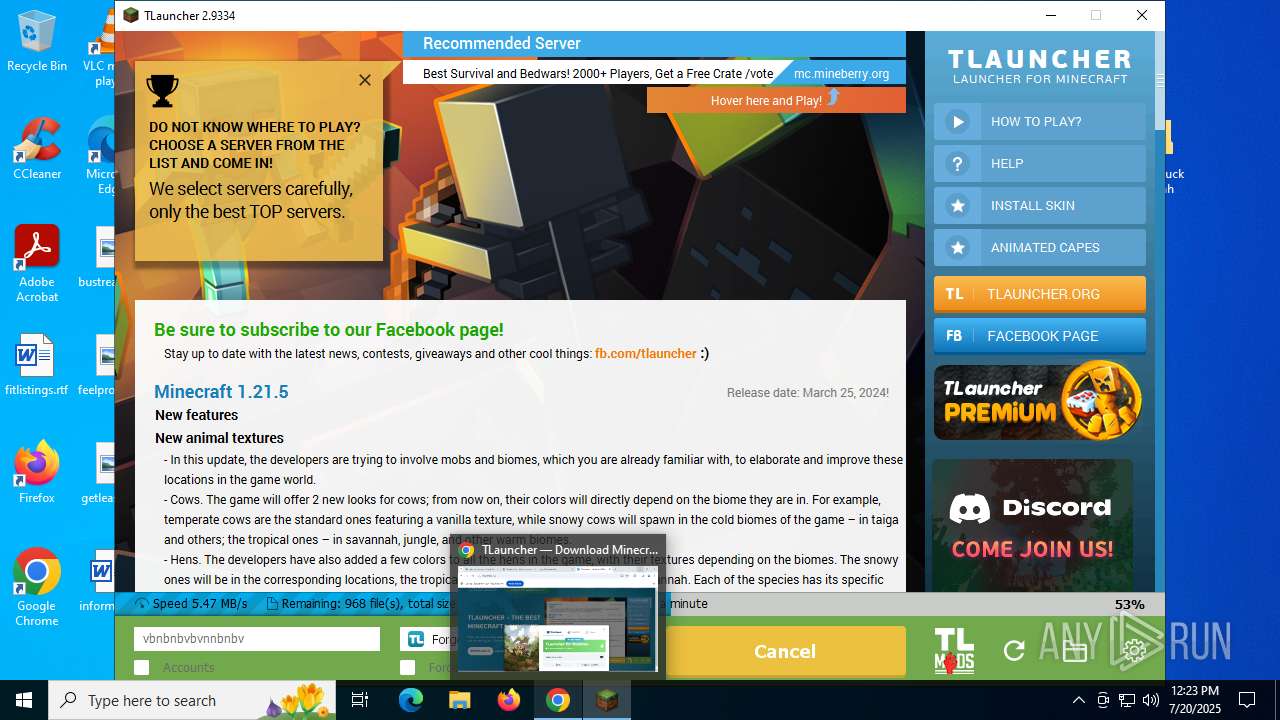
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- irsetup.exe (PID: 7132)
- BrowserInstaller.exe (PID: 4820)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- installer.exe (PID: 4512)
- jp2launcher.exe (PID: 7988)
- javaw.exe (PID: 3148)
- jp2launcher.exe (PID: 3704)
- 360TS_Setup.exe (PID: 8404)
- java.exe (PID: 8952)
- QHSafeTray.exe (PID: 1244)
- PopWndLog.exe (PID: 7488)
- PopWndLog.exe (PID: 7528)
- QHActiveDefense.exe (PID: 7712)
Reads Microsoft Outlook installation path
- jre-8u461-windows-x64.exe (PID: 8132)
- irsetup.exe (PID: 7132)
Reads Internet Explorer settings
- jre-8u461-windows-x64.exe (PID: 8132)
- irsetup.exe (PID: 7132)
Checks for Java to be installed
- jre-8u461-windows-x64.exe (PID: 8132)
- irsetup.exe (PID: 7132)
- msiexec.exe (PID: 7360)
- msiexec.exe (PID: 4580)
- installer.exe (PID: 4512)
- ssvagent.exe (PID: 2312)
- TLauncher.exe (PID: 2384)
- jp2launcher.exe (PID: 7988)
- jp2launcher.exe (PID: 3704)
- msiexec.exe (PID: 8352)
- javaw.exe (PID: 8640)
Executable content was dropped or overwritten
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- irsetup.exe (PID: 7132)
- BrowserInstaller.exe (PID: 4820)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- installer.exe (PID: 4512)
- 360TS_Setup.exe (PID: 1660)
- 360TS_Setup.exe (PID: 8404)
- javaw.exe (PID: 3148)
- java.exe (PID: 8952)
- jre-8u461-windows-x64.exe (PID: 8132)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 3048)
- KB931125-rootsupd.exe (PID: 188)
- QHActiveDefense.exe (PID: 7712)
- javaw.exe (PID: 3576)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4580)
Application launched itself
- msiexec.exe (PID: 4580)
- QHSafeTray.exe (PID: 1244)
- PopWndLog.exe (PID: 7488)
Creates file in the systems drive root
- explorer.exe (PID: 4772)
- 360TS_Setup.exe (PID: 8404)
There is functionality for taking screenshot (YARA)
- jre-8u461-windows-x64.exe (PID: 8132)
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- 360TS_Setup.exe (PID: 1660)
- 360TS_Setup.exe (PID: 8404)
Process drops legitimate windows executable
- msiexec.exe (PID: 4580)
- javaw.exe (PID: 3148)
- WinRAR.exe (PID: 8236)
- 360TS_Setup.exe (PID: 8404)
- java.exe (PID: 8952)
- KB931125-rootsupd.exe (PID: 188)
Reads Mozilla Firefox installation path
- MSIB6B1.tmp (PID: 1332)
- installer.exe (PID: 4512)
The process drops C-runtime libraries
- msiexec.exe (PID: 4580)
- javaw.exe (PID: 3148)
- java.exe (PID: 8952)
Potential Corporate Privacy Violation
- 360-installer-bro.exe (PID: 1480)
Process requests binary or script from the Internet
- 360-installer-bro.exe (PID: 1480)
- 360TS_Setup.exe (PID: 8404)
- java.exe (PID: 8952)
Creates a software uninstall entry
- irsetup.exe (PID: 7132)
- 360TS_Setup.exe (PID: 8404)
Creates/Modifies COM task schedule object
- ssvagent.exe (PID: 2312)
- dxdiag.exe (PID: 5248)
- installer.exe (PID: 4512)
- regsvr32.exe (PID: 7476)
Starts itself from another location
- 360TS_Setup.exe (PID: 1660)
The process verifies whether the antivirus software is installed
- 360TS_Setup.exe (PID: 8404)
- csrss.exe (PID: 608)
- PowerSaver.exe (PID: 8568)
- regsvr32.exe (PID: 7476)
- WscReg.exe (PID: 8812)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 3048)
- WscReg.exe (PID: 8800)
- QHActiveDefense.exe (PID: 7712)
- csrss.exe (PID: 524)
- QHWatchdog.exe (PID: 8128)
- explorer.exe (PID: 4772)
- QHSafeTray.exe (PID: 5264)
- regsvr32.exe (PID: 8536)
- QHSafeTray.exe (PID: 1244)
- PopWndLog.exe (PID: 7488)
- QHSafeTray.exe (PID: 2536)
- PopWndLog.exe (PID: 7528)
- KB931125-rootsupd.exe (PID: 188)
- regsvr32.exe (PID: 5904)
- WscReg.exe (PID: 7428)
- WscReg.exe (PID: 2876)
- javaw.exe (PID: 3576)
- java.exe (PID: 8088)
- regsvr32.exe (PID: 8980)
Drops 7-zip archiver for unpacking
- 360TS_Setup.exe (PID: 8404)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 8236)
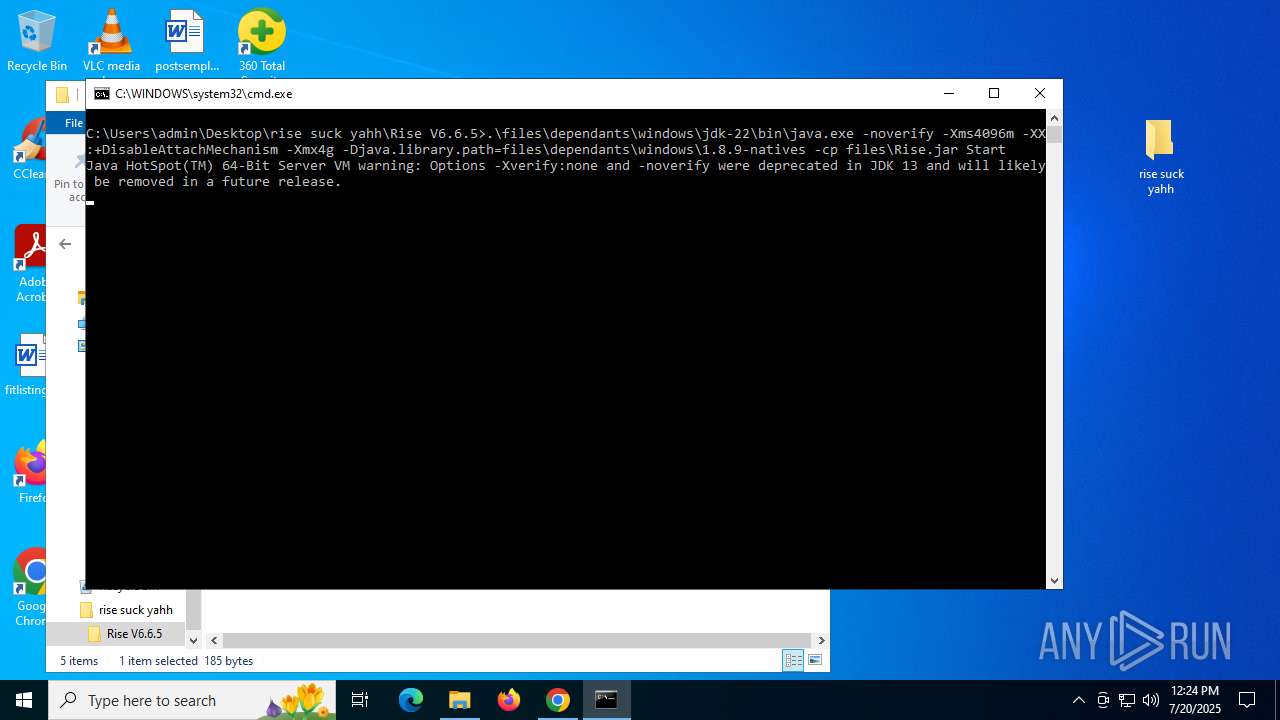
Starts CMD.EXE for commands execution
- java.exe (PID: 8952)
- explorer.exe (PID: 4772)
Starts application with an unusual extension
- cmd.exe (PID: 3396)
- cmd.exe (PID: 432)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 8764)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 3396)
Uses WMIC.EXE to obtain quick Fix Engineering (patches) data
- cmd.exe (PID: 8764)
Drops a system driver (possible attempt to evade defenses)
- 360TS_Setup.exe (PID: 8404)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 3048)
- QHActiveDefense.exe (PID: 7712)
Creates files in the driver directory
- 360TS_Setup.exe (PID: 8404)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 3048)
- QHActiveDefense.exe (PID: 7712)
Adds/modifies Windows certificates
- PowerSaver.exe (PID: 8568)
- updroots.exe (PID: 7224)
- updroots.exe (PID: 5028)
- updroots.exe (PID: 6320)
- QHActiveDefense.exe (PID: 7712)
- 360TS_Setup.exe (PID: 8404)
Creates or modifies Windows services
- 360TS_Setup.exe (PID: 8404)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 3048)
- QHActiveDefense.exe (PID: 7712)
- QHSafeTray.exe (PID: 1244)
Executes as Windows Service
- WscReg.exe (PID: 8800)
- QHActiveDefense.exe (PID: 7712)
- WscReg.exe (PID: 2876)
Zapya greyware has been detected
- QHActiveDefense.exe (PID: 7712)
Searches for installed software
- QHSafeTray.exe (PID: 1244)
Starts a Microsoft application from unusual location
- updroots.exe (PID: 5028)
- updroots.exe (PID: 6320)
- updroots.exe (PID: 7224)
- updroots.exe (PID: 8644)
Executing commands from ".cmd" file
- explorer.exe (PID: 4772)
INFO
Reads the computer name
- jre-8u461-windows-x64.exe (PID: 2076)
- jre-8u461-windows-x64.exe (PID: 8132)
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- irsetup.exe (PID: 7132)
- msiexec.exe (PID: 4580)
- msiexec.exe (PID: 7360)
- MSIB6B1.tmp (PID: 1332)
- BrowserInstaller.exe (PID: 4820)
- 360-installer-bro.exe (PID: 1480)
- irsetup.exe (PID: 7424)
- installer.exe (PID: 4512)
- javaw.exe (PID: 3148)
- javaws.exe (PID: 7644)
- jp2launcher.exe (PID: 7988)
- javaws.exe (PID: 6220)
- jp2launcher.exe (PID: 3704)
- 360TS_Setup.exe (PID: 1660)
- msiexec.exe (PID: 8352)
- 360TS_Setup.exe (PID: 8404)
- javaw.exe (PID: 8640)
- msiexec.exe (PID: 8556)
- javaw.exe (PID: 8736)
- java.exe (PID: 8952)
- msiexec.exe (PID: 7532)
- javaw.exe (PID: 7956)
- msiexec.exe (PID: 5288)
- WscReg.exe (PID: 8812)
- WscReg.exe (PID: 8800)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 7712)
- QHActiveDefense.exe (PID: 3048)
- QHSafeTray.exe (PID: 1244)
- PopWndLog.exe (PID: 7488)
- QHSafeTray.exe (PID: 5264)
- QHSafeTray.exe (PID: 2536)
- PopWndLog.exe (PID: 7528)
- WscReg.exe (PID: 7428)
- WscReg.exe (PID: 2876)
- javaw.exe (PID: 3576)
- java.exe (PID: 8088)
Create files in a temporary directory
- jre-8u461-windows-x64.exe (PID: 2076)
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- irsetup.exe (PID: 7132)
- MSIB6B1.tmp (PID: 1332)
- BrowserInstaller.exe (PID: 4820)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- javaw.exe (PID: 6224)
- javaw.exe (PID: 3148)
- jp2launcher.exe (PID: 7988)
- jp2launcher.exe (PID: 3704)
- 360TS_Setup.exe (PID: 1660)
- 360TS_Setup.exe (PID: 8404)
- java.exe (PID: 8952)
- javaw.exe (PID: 7956)
- KB931125-rootsupd.exe (PID: 188)
- javaw.exe (PID: 3576)
- java.exe (PID: 8088)
Creates files or folders in the user directory
- jre-8u461-windows-x64.exe (PID: 8132)
- msiexec.exe (PID: 4580)
- irsetup.exe (PID: 7132)
- explorer.exe (PID: 4772)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- javaw.exe (PID: 3148)
- 360TS_Setup.exe (PID: 8404)
- java.exe (PID: 8952)
- dxdiag.exe (PID: 5248)
- QHSafeTray.exe (PID: 1244)
- javaw.exe (PID: 3576)
Reads the software policy settings
- jre-8u461-windows-x64.exe (PID: 8132)
- irsetup.exe (PID: 7132)
- msiexec.exe (PID: 4580)
- irsetup.exe (PID: 7424)
- 360TS_Setup.exe (PID: 8404)
- slui.exe (PID: 7080)
- dxdiag.exe (PID: 5248)
- QHActiveDefense.exe (PID: 7712)
Java executable
- jre-8u461-windows-x64.exe (PID: 8132)
- jre-8u461-windows-x64.exe (PID: 8008)
- jre-8u461-windows-x64.exe (PID: 2076)
- MSIB6B1.tmp (PID: 1332)
- installer.exe (PID: 4512)
The sample compiled with english language support
- chrome.exe (PID: 4724)
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- irsetup.exe (PID: 7132)
- msiexec.exe (PID: 4580)
- BrowserInstaller.exe (PID: 4820)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- installer.exe (PID: 4512)
- 360TS_Setup.exe (PID: 8404)
- javaw.exe (PID: 3148)
- WinRAR.exe (PID: 8236)
- java.exe (PID: 8952)
- jre-8u461-windows-x64.exe (PID: 8132)
- QHActiveDefense.exe (PID: 3048)
- javaw.exe (PID: 3576)
- KB931125-rootsupd.exe (PID: 188)
Executable content was dropped or overwritten
- chrome.exe (PID: 4724)
- msiexec.exe (PID: 4580)
- WinRAR.exe (PID: 8236)
Application launched itself
- chrome.exe (PID: 4724)
Checks supported languages
- jre-8u461-windows-x64.exe (PID: 8132)
- jre-8u461-windows-x64.exe (PID: 2076)
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- irsetup.exe (PID: 7132)
- msiexec.exe (PID: 4580)
- msiexec.exe (PID: 7360)
- MSIB6B1.tmp (PID: 1332)
- jaureg.exe (PID: 7996)
- BrowserInstaller.exe (PID: 4820)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- installer.exe (PID: 4512)
- javaw.exe (PID: 6224)
- TLauncher.exe (PID: 2384)
- javaw.exe (PID: 3148)
- javaws.exe (PID: 7644)
- jp2launcher.exe (PID: 7988)
- javaws.exe (PID: 6220)
- jp2launcher.exe (PID: 3704)
- 360TS_Setup.exe (PID: 1660)
- msiexec.exe (PID: 8352)
- 360TS_Setup.exe (PID: 8404)
- msiexec.exe (PID: 8556)
- javaw.exe (PID: 8640)
- java.exe (PID: 8952)
- javaw.exe (PID: 8736)
- chcp.com (PID: 8296)
- chcp.com (PID: 5556)
- chcp.com (PID: 7016)
- ssvagent.exe (PID: 2312)
- chcp.com (PID: 8840)
- msiexec.exe (PID: 5288)
- msiexec.exe (PID: 7532)
- javaw.exe (PID: 7956)
- PowerSaver.exe (PID: 8568)
- WscReg.exe (PID: 8812)
- WscReg.exe (PID: 8800)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 3048)
- QHActiveDefense.exe (PID: 7712)
- QHWatchdog.exe (PID: 8128)
- PopWndLog.exe (PID: 7488)
- QHSafeTray.exe (PID: 1244)
- QHSafeTray.exe (PID: 5264)
- PopWndLog.exe (PID: 7528)
- QHSafeTray.exe (PID: 2536)
- QHWatchdog.exe (PID: 4860)
- updroots.exe (PID: 5028)
- updroots.exe (PID: 7224)
- KB931125-rootsupd.exe (PID: 188)
- updroots.exe (PID: 8644)
- WscReg.exe (PID: 2876)
- WscReg.exe (PID: 7428)
- java.exe (PID: 8088)
- javaw.exe (PID: 3576)
- updroots.exe (PID: 6320)
Checks proxy server information
- jre-8u461-windows-x64.exe (PID: 8132)
- irsetup.exe (PID: 7132)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- jp2launcher.exe (PID: 7988)
- jp2launcher.exe (PID: 3704)
- 360TS_Setup.exe (PID: 8404)
- slui.exe (PID: 7080)
- QHSafeTray.exe (PID: 1244)
Reads Environment values
- jre-8u461-windows-x64.exe (PID: 8132)
- QHSafeTray.exe (PID: 1244)
- QHActiveDefense.exe (PID: 7712)
Reads the machine GUID from the registry
- jre-8u461-windows-x64.exe (PID: 8132)
- msiexec.exe (PID: 4580)
- irsetup.exe (PID: 7132)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- javaw.exe (PID: 3148)
- 360TS_Setup.exe (PID: 8404)
- java.exe (PID: 8952)
- QHActiveDefense.exe (PID: 7712)
- QHSafeTray.exe (PID: 1244)
- javaw.exe (PID: 3576)
- java.exe (PID: 8088)
The sample compiled with portuguese language support
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- BrowserInstaller.exe (PID: 4820)
- irsetup.exe (PID: 7132)
Process checks computer location settings
- TLauncher-Installer-1.8.8.exe (PID: 7344)
- BrowserInstaller.exe (PID: 4820)
- irsetup.exe (PID: 7132)
- irsetup.exe (PID: 7424)
- 360-installer-bro.exe (PID: 1480)
- 360TS_Setup.exe (PID: 8404)
- java.exe (PID: 8952)
- QHSafeTray.exe (PID: 1244)
- java.exe (PID: 8088)
Starts application with an unusual extension
- msiexec.exe (PID: 4580)
Reads CPU info
- msiexec.exe (PID: 4580)
- java.exe (PID: 8952)
- 360TS_Setup.exe (PID: 8404)
- QHActiveDefense.exe (PID: 7712)
- java.exe (PID: 8088)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- WMIC.exe (PID: 8228)
- dxdiag.exe (PID: 5248)
- WMIC.exe (PID: 8524)
Creates files in the program directory
- irsetup.exe (PID: 7132)
- installer.exe (PID: 4512)
- javaw.exe (PID: 6224)
- javaw.exe (PID: 3148)
- 360TS_Setup.exe (PID: 1660)
- 360TS_Setup.exe (PID: 8404)
- QHActiveDefense.exe (PID: 7712)
- PopWndLog.exe (PID: 7488)
- QHSafeTray.exe (PID: 1244)
- PopWndLog.exe (PID: 7528)
- WscReg.exe (PID: 7428)
Disables trace logs
- 360-installer-bro.exe (PID: 1480)
- 360TS_Setup.exe (PID: 8404)
- QHActiveDefense.exe (PID: 7712)
- QHSafeTray.exe (PID: 1244)
- QHSafeTray.exe (PID: 5264)
- QHSafeTray.exe (PID: 2536)
Creates a software uninstall entry
- msiexec.exe (PID: 4580)
Application based on Java
- javaw.exe (PID: 3148)
JAVA mutex has been found
- jp2launcher.exe (PID: 7988)
- jp2launcher.exe (PID: 3704)
- msiexec.exe (PID: 8556)
- msiexec.exe (PID: 5288)
The sample compiled with chinese language support
- 360TS_Setup.exe (PID: 1660)
- 360TS_Setup.exe (PID: 8404)
- EaInstHelper64.exe (PID: 2848)
- QHActiveDefense.exe (PID: 7712)
Manual execution by a user
- WinRAR.exe (PID: 8236)
- cmd.exe (PID: 4024)
Reads Microsoft Office registry keys
- explorer.exe (PID: 4772)
The sample compiled with turkish language support
- 360TS_Setup.exe (PID: 8404)
Changes the display of characters in the console
- cmd.exe (PID: 3396)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 432)
- cmd.exe (PID: 8764)
The sample compiled with russian language support
- 360TS_Setup.exe (PID: 8404)
Launching a file from a Registry key
- 360TS_Setup.exe (PID: 8404)
- QHActiveDefense.exe (PID: 7712)
- KB931125-rootsupd.exe (PID: 188)
Process checks whether UAC notifications are on
- 360TS_Setup.exe (PID: 8404)
- QHActiveDefense.exe (PID: 7712)
- QHSafeTray.exe (PID: 1244)
Reads the time zone
- javaw.exe (PID: 3576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
277
Monitored processes
129
Malicious processes
38
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files (x86)\360\Total Security\modules\KB931125-rootsupd.exe" | C:\Program Files (x86)\360\Total Security\modules\KB931125-rootsupd.exe | 360TS_Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 432 | cmd.exe /C chcp 437 & set processor | C:\Windows\System32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 608 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1244 | /showtrayicon | C:\Program Files (x86)\360\Total Security\safemon\QHSafeTray.exe | QHActiveDefense.exe | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: HIGH Description: 360 Total Security Version: 10,0,0,1860 Modules
| |||||||||||||||
| 1300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3076,i,12574307751575925639,2611191096748367988,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3104 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=3604,i,12574307751575925639,2611191096748367988,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6996 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1332 | "C:\WINDOWS\Installer\MSIB6B1.tmp" INSTALLDIR="C:\Program Files\Java\jre1.8.0_271\\" ProductCode={26A24AE4-039D-4CA4-87B4-2F64180271F0} /s BASEIMAGECHECKSUMSHA256= | C:\Windows\Installer\MSIB6B1.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\AppData\Local\Temp\360-installer-bro.exe" /s | C:\Users\admin\AppData\Local\Temp\360-installer-bro.exe | irsetup.exe | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: HIGH Description: 360 Total Security Online Installer Exit code: 1 Version: 6, 6, 0, 1060 Modules
| |||||||||||||||
| 1660 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
156 140
Read events
123 700
Write events
15 640
Delete events
16 800
Modification events
| (PID) Process: | (4724) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4724) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4724) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4724) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000080244 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4724) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4724) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (8132) jre-8u461-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
| (PID) Process: | (8132) jre-8u461-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8132) jre-8u461-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
2 222
Suspicious files
3 428
Text files
2 542
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF18d404.TMP | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF18d423.TMP | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF18d423.TMP | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF18d423.TMP | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF18d423.TMP | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF18d443.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
112
TCP/UDP connections
415
DNS requests
262
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2348 | chrome.exe | GET | 200 | 142.250.184.206:80 | http://clients2.google.com/time/1/current?cup2key=8:Q6aO3ehVJX3oSwFheDPl-Hj5YIENaHKtBQ24XQGbNEw&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3872 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7296 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7296 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8132 | jre-8u461-windows-x64.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
5468 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7132 | irsetup.exe | GET | 200 | 104.20.7.182:80 | http://dl2.tlauncher.org/ | unknown | — | — | malicious |
7132 | irsetup.exe | GET | 200 | 104.20.7.182:80 | http://dl2.tlauncher.org/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4172 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2348 | chrome.exe | 142.250.186.106:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
2348 | chrome.exe | 142.250.184.206:443 | clients2.google.com | GOOGLE | US | whitelisted |
2348 | chrome.exe | 142.250.184.206:80 | clients2.google.com | GOOGLE | US | whitelisted |
2348 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2348 | chrome.exe | 142.250.185.163:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
drive.google.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ogads-pa.clients6.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
1480 | 360-installer-bro.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
1480 | 360-installer-bro.exe | Misc activity | ET INFO Packed Executable Download |
3148 | javaw.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
8952 | java.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 21.0.x Detected |