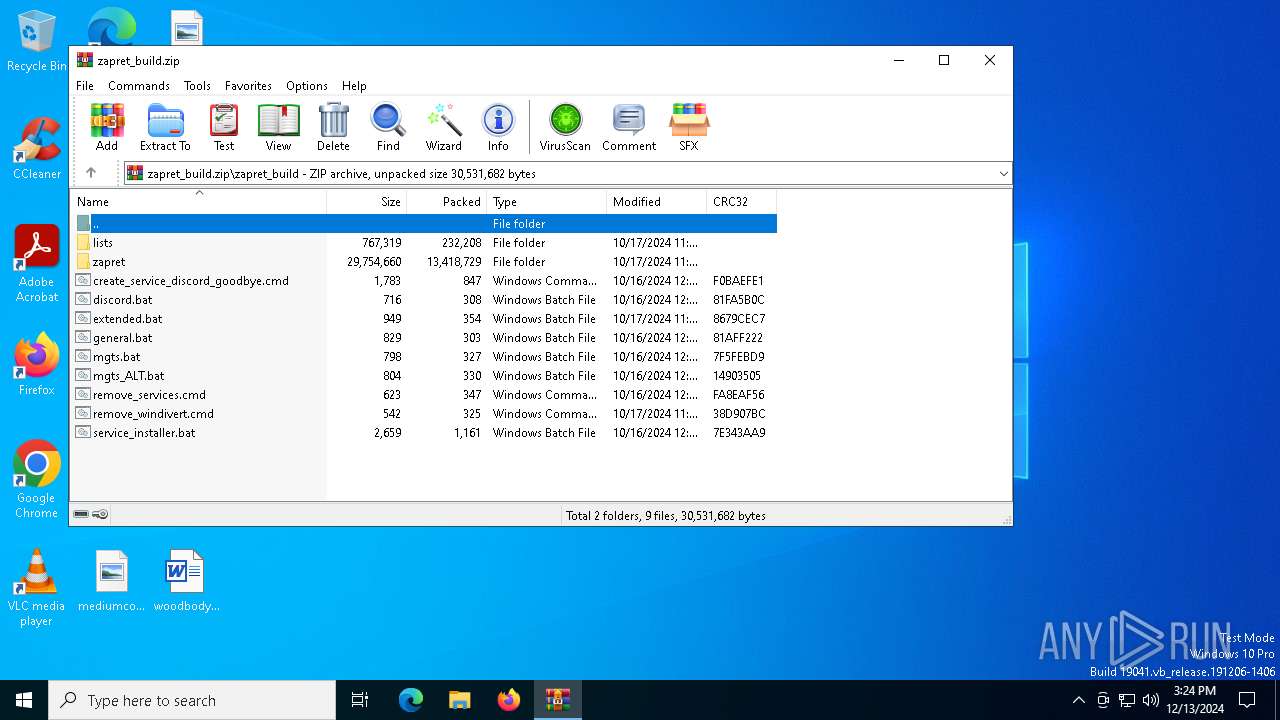
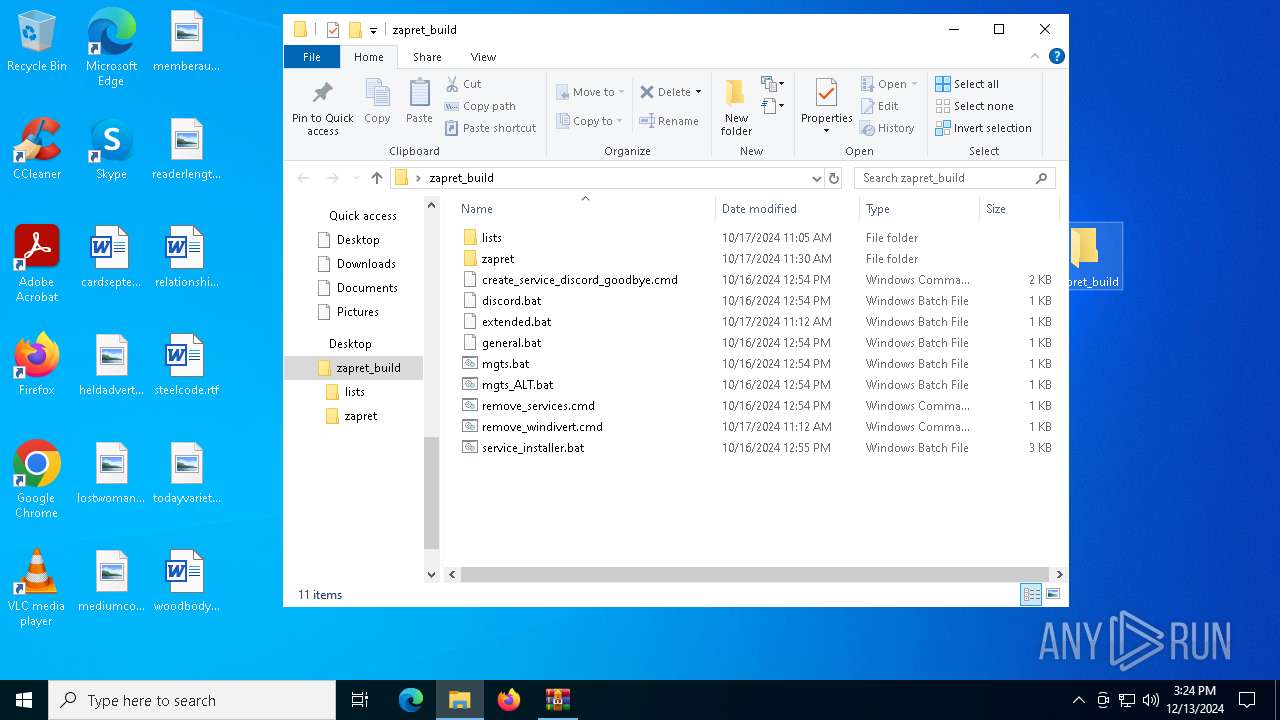
| File name: | zapret_build.zip |
| Full analysis: | https://app.any.run/tasks/513f3710-f1b2-4095-adfc-f5ad9a887540 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 15:24:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | E9CAF5D3B51C2E7AA2FD6B9E84362A0C |
| SHA1: | 932FC5785D1D49050B9DFE0323F99815A5ED69C0 |
| SHA256: | 4FC3E517B7855FDC966FDFCA0431317D5B4A22D46C757045B5070112B39F4FF4 |
| SSDEEP: | 98304:H6UYPkxljOp5lZ3BVJh/8fiuhpeFEP6th02KcUD6etsfNZPZQ2+i+4sHSXGRpljv:OPbSkdiDOYZnTUOKTPqZad4cMp |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6536)
Detects Cygwin installation
- WinRAR.exe (PID: 6536)
Starts NET.EXE for service management
- cmd.exe (PID: 2972)
- net.exe (PID: 5748)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6536)
Starts SC.EXE for service management
- cmd.exe (PID: 2972)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6536)
The process uses the downloaded file
- WinRAR.exe (PID: 6536)
- cmd.exe (PID: 4596)
Manual execution by a user
- cmd.exe (PID: 6856)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 4596)
- cmd.exe (PID: 6372)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6536)
UPX packer has been detected
- winws.exe (PID: 7000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:17 16:12:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | zapret_build/ |
Total processes
144
Monitored processes
24
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2972 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\zapret_build\create_service_discord_goodbye.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3260 | "C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\winws.exe" --wf-raw="@lists\rules.txt" --filter-udp=443 --hostlist="lists\list-general.txt" --dpi-desync=fake --dpi-desync-udplen-increment=10 --dpi-desync-repeats=6 --dpi-desync-udplen-pattern=0xDEADBEEF --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin" --new --filter-udp=50000-65535 --dpi-desync=fake,tamper --dpi-desync-any-protocol --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin" --new --filter-tcp=80 --dpi-desync=split --dpi-desync-ttl=4 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="lists\list-general.txt" --dpi-desync=fake,split2 --dpi-desync-ttl=2 --dpi-desync-split-pos=1 --dpi-desync=fake,disorder2 --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig | C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3420 | sc description "zapret" "zapret DPI bypass software" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | "C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\winws.exe" --wf-raw="@lists\rules.txt" --filter-udp=443 --hostlist="lists\list-general.txt" --dpi-desync=fake --dpi-desync-udplen-increment=10 --dpi-desync-repeats=6 --dpi-desync-udplen-pattern=0xDEADBEEF --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin" --new --filter-udp=50000-65535 --dpi-desync=fake,tamper --dpi-desync-any-protocol --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin" --new --filter-tcp=80 --dpi-desync=split --dpi-desync-ttl=4 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="lists\list-general.txt" --dpi-desync=fake,split2 --dpi-desync-ttl=2 --dpi-desync-split-pos=1 --dpi-desync=fake,disorder2 --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig | C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4076 | C:\WINDOWS\system32\net1 stop "zapret" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4516 | "C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\winws.exe" --wf-raw="@lists\rules.txt" --filter-udp=443 --hostlist="lists\list-general.txt" --dpi-desync=fake --dpi-desync-udplen-increment=10 --dpi-desync-repeats=6 --dpi-desync-udplen-pattern=0xDEADBEEF --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin" --new --filter-udp=50000-65535 --dpi-desync=fake,tamper --dpi-desync-any-protocol --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin" --new --filter-tcp=80 --dpi-desync=split --dpi-desync-ttl=4 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="lists\list-general.txt" --dpi-desync=fake,split2 --dpi-desync-ttl=2 --dpi-desync-split-pos=1 --dpi-desync=fake,disorder2 --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig | C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\winws.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4596 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\zapret_build\mgts.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
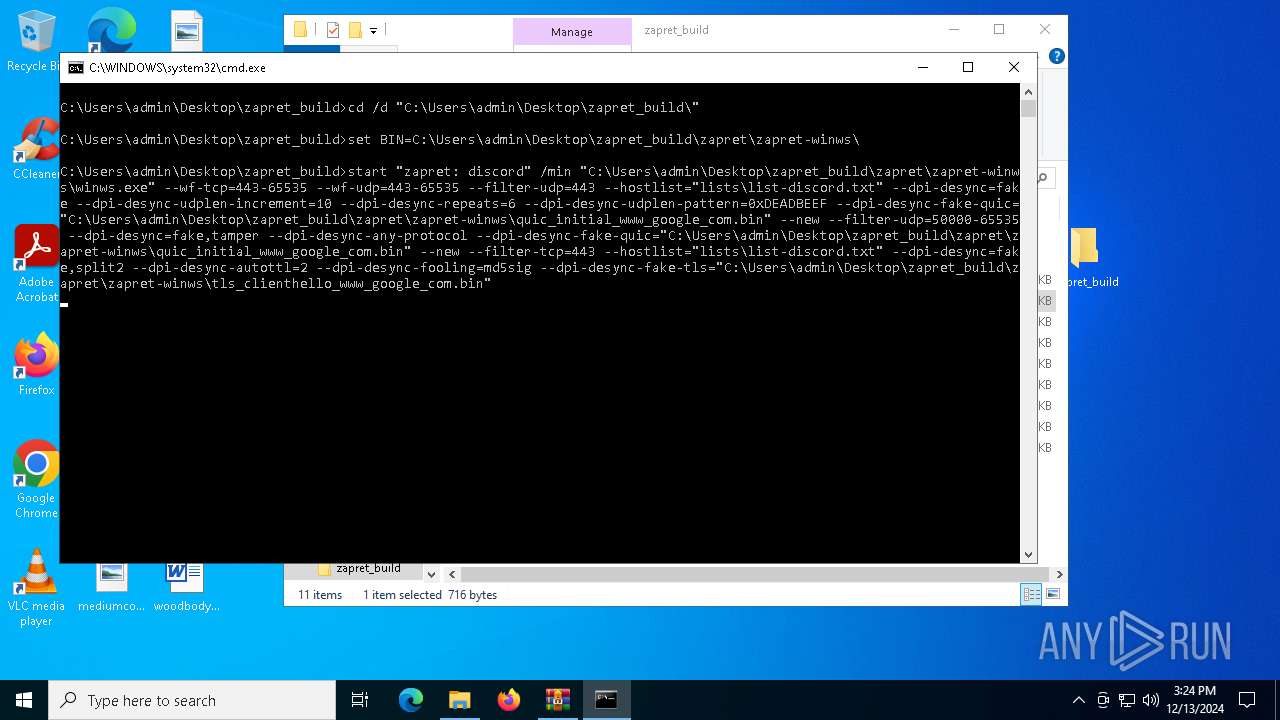
| 4672 | sc create "zapret" binPath="\"C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\winws.exe\" --wf-raw=\"@C:\Users\admin\Desktop\zapret_build\lists\rules.txt\" --filter-udp=443 --hostlist=\"C:\Users\admin\Desktop\zapret_build\lists\list-discord.txt\" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic=\"C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin\" --new --filter-udp=50000-65535 --dpi-desync=fake --dpi-desync-any-protocol --dpi-desync-cutoff=d3 --dpi-desync-repeats=6 --dpi-desync-fake-quic=\"C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\quic_initial_www_google_com.bin\" --new --filter-tcp=443 --hostlist=\"C:\Users\admin\Desktop\zapret_build\lists\list-discord.txt\" --dpi-desync=fake,split --dpi-desync-autottl=2 --dpi-desync-repeats=6 --dpi-desync-fooling=badseq --dpi-desync-fake-tls=\"C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\tls_clienthello_www_google_com.bin\"" DisplayName="zapret DPI bypass: Discord (GoodbyeDPI)" start=auto depend="GoodbyeDPI" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | sc delete "zapret" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | sc start "zapret" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 868
Read events
2 856
Write events
12
Delete events
0
Modification events
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret_build.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7000) winws.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\System\WinDivert |
| Operation: | write | Name: | EventMessageFile |
Value: C:\Users\admin\Desktop\zapret_build\zapret\zapret-winws\WinDivert64.sys | |||
| (PID) Process: | (7000) winws.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\System\WinDivert |
| Operation: | write | Name: | TypesSupported |
Value: 7 | |||
Executable files
143
Suspicious files
190
Text files
73
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\discord.bat | text | |
MD5:16C7BB99BA93AC058F3EC4188D8D4A8D | SHA256:7373867722E2618B809FCED190D15188DA926DC20C64DC24ED231DFBA5B40FC0 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\create_service_discord_goodbye.cmd | text | |
MD5:7BFDCECD62053A57AD095E1D35527354 | SHA256:C58D6DA183C32BD012303A98D60434F059C7A211E31CA07210F25D1BDA8039FD | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\lists\list-discord.txt | text | |
MD5:C3BFC48C92E5BF637073300BF7FA2D89 | SHA256:DD108096CE5D89CF94273BED34D3280F1B72DED285917E628EEF53EEB2A53032 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\extended.bat | text | |
MD5:BC9D08055ADC8A6FB747C81A75D7B443 | SHA256:212EAA0C00A3C54E77AFF45D65B71175CF8CC4E4EED843159D12027AC9928205 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\lists\list-youtube.txt | text | |
MD5:A33C3A6C0469EC472A25CC3CDF91FFE5 | SHA256:079E524C8B19DCF75C8ACF1B7A2C266B1F967D1FDDCA2E422183A0BBA73A0EFB | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\lists\list-general.txt | text | |
MD5:A03D2C9945CD2C801C3CE17519513BE9 | SHA256:0D1ABA287A4DBE47A4F077E527C34FACC459DFA715CD89E990C8C5FC4C9C672F | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\mgts.bat | text | |
MD5:D21A15E45CA079CFAAE968D3DCE549BA | SHA256:8D4AE506F99B5187157DE99FB2979B9224670AB7D20727AC4BFEC8F4D6B9C863 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\general.bat | text | |
MD5:12FF6B5E3CD58C225DE766DD4F6E350D | SHA256:739E4478D46FD81ECA9C51C843C0DD321E41B440DC252BCBE941840838AF386D | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\zapret\blockcheck\cygwin\bin\basename.exe | executable | |
MD5:88910994D984FE1EC33239D4AA91CCEF | SHA256:1D36AF5EF59CF397DE184E23B4C9A32C2FBD4D0AA8E33309578E400976E42244 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.27568\zapret_build\zapret\blockcheck\cygwin\bin\awk | text | |
MD5:11E6D956542C3DCBD393F274F1090297 | SHA256:96B5687E64A6B4B5692CB9344F0D4B239C549FD88BC5599C2E3560D6E3E81F4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
34
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4 | System | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4 | System | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
132 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
132 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 92.123.104.43:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.138:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 23.48.23.138:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |