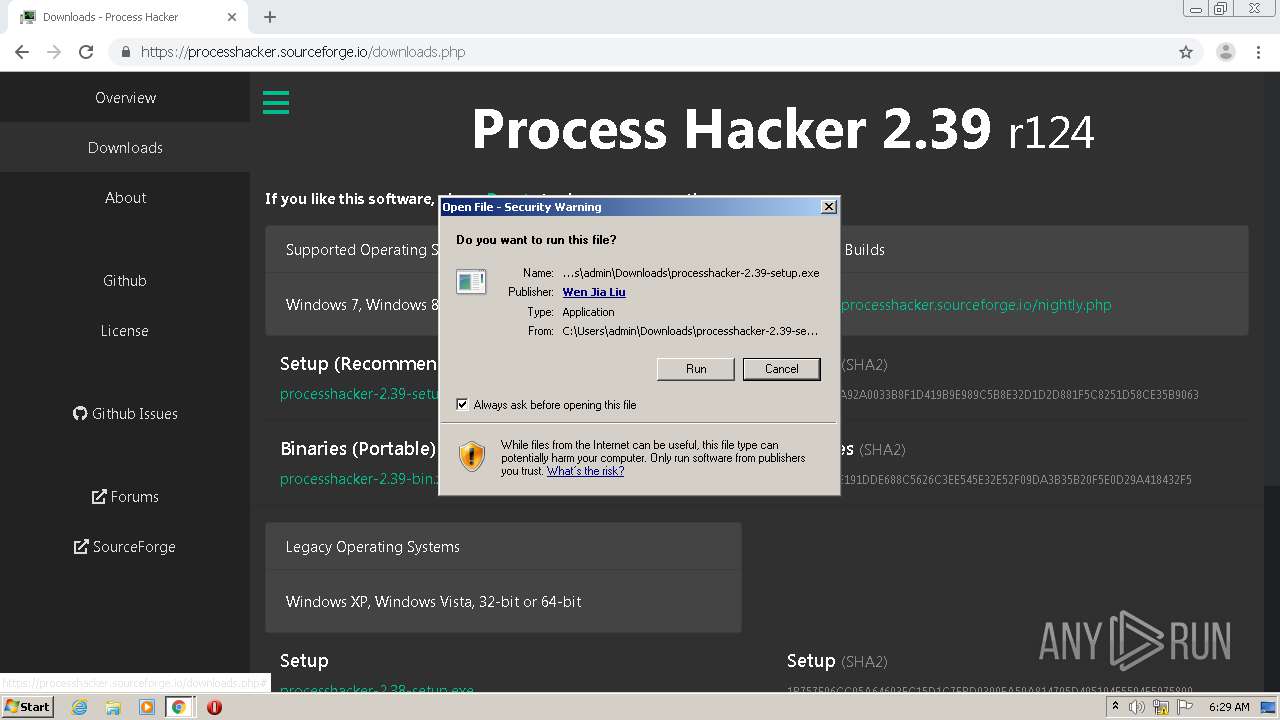
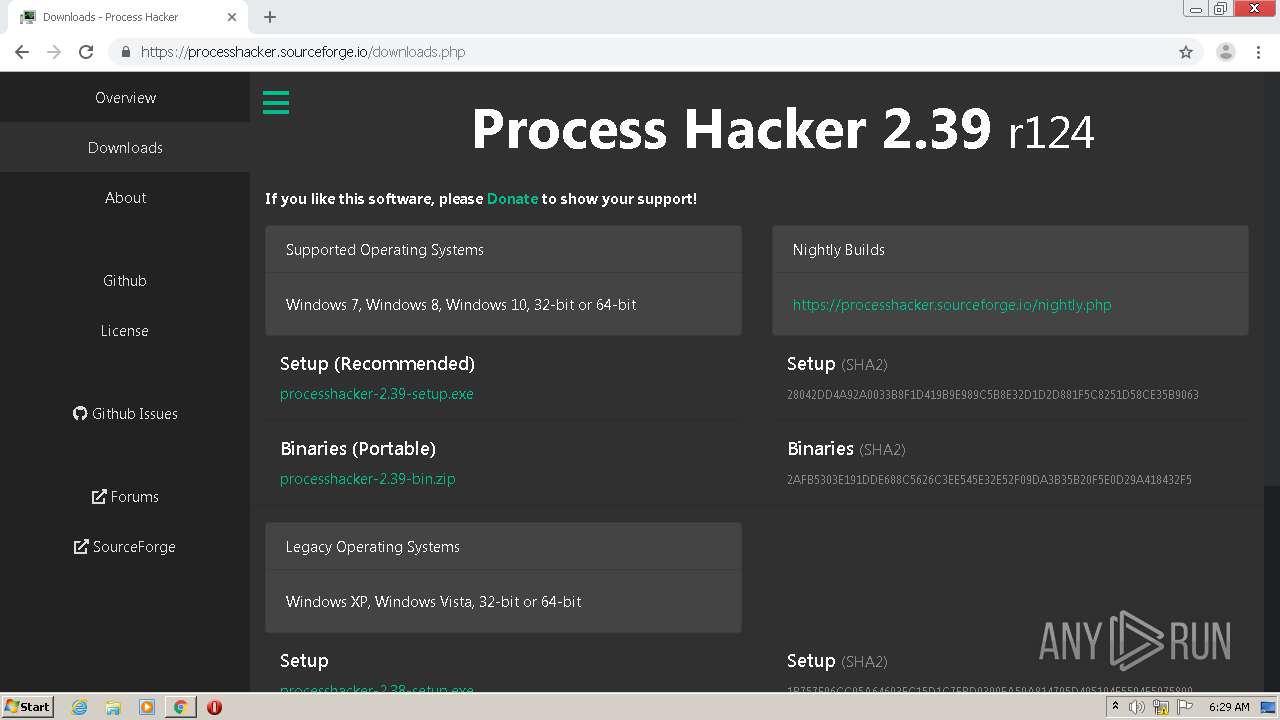
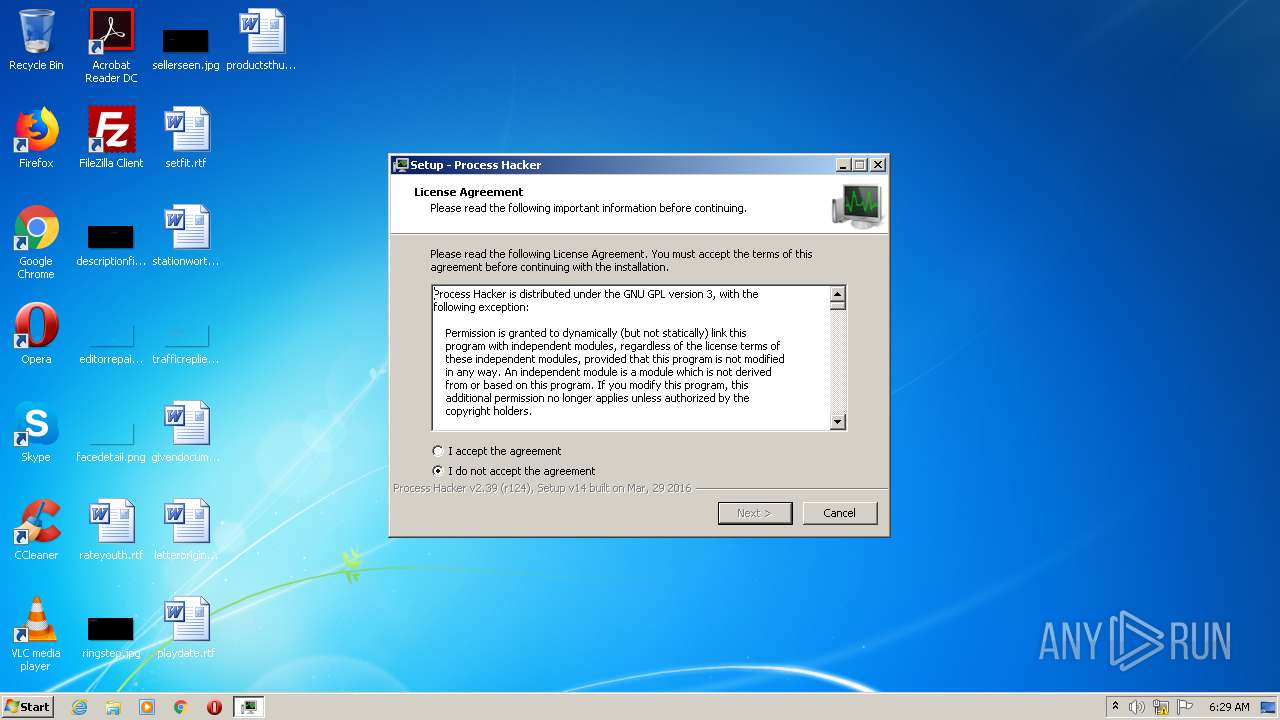
| URL: | https://zeltser.com/malware-sample-sources/ |
| Full analysis: | https://app.any.run/tasks/fea70069-f048-41d1-86e6-3ec48ea6ce56 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 05:26:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6412D77FB75C203080E52407C3409879 |
| SHA1: | 4A520B5E611FE849FAFF062B7E9D0488D4DDBE1C |
| SHA256: | 4F9FC4D5C60B4397C39FFE0B8C33954FCBB25CC6EF5188F1870E1642213D1FA3 |
| SSDEEP: | 3:N8O7GKX3e6N:2O7dneo |
MALICIOUS
Application was dropped or rewritten from another process
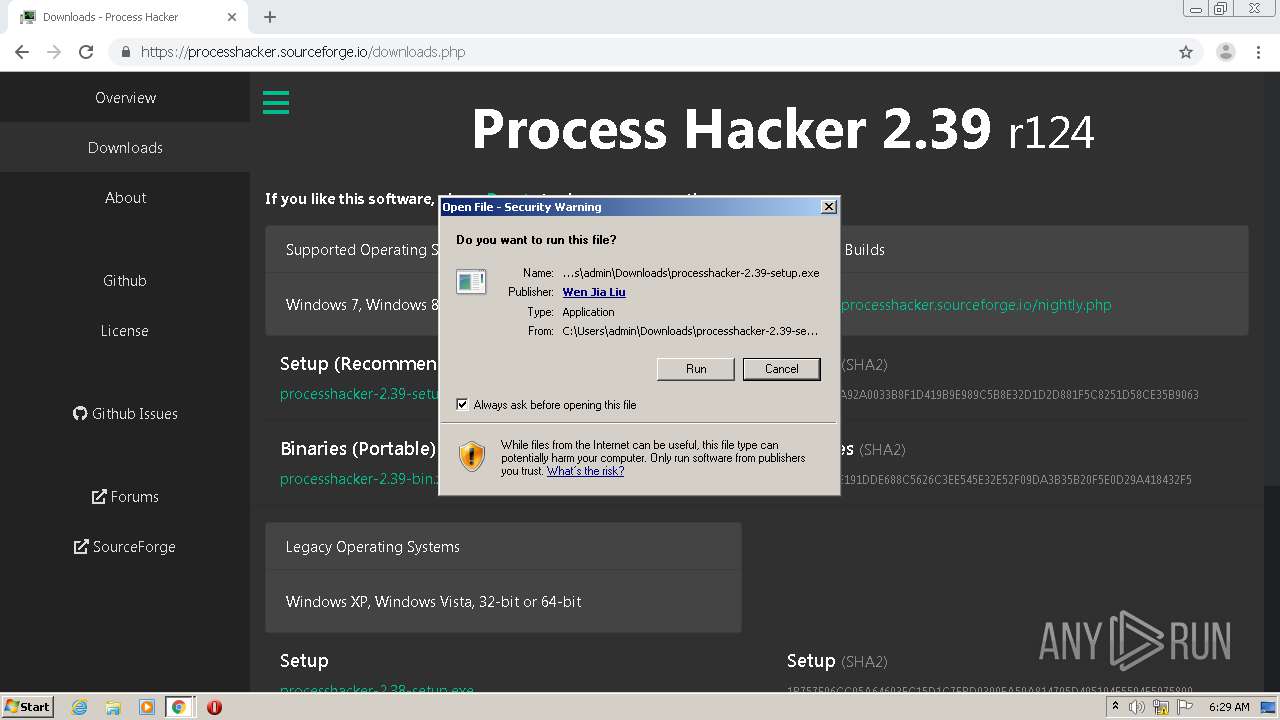
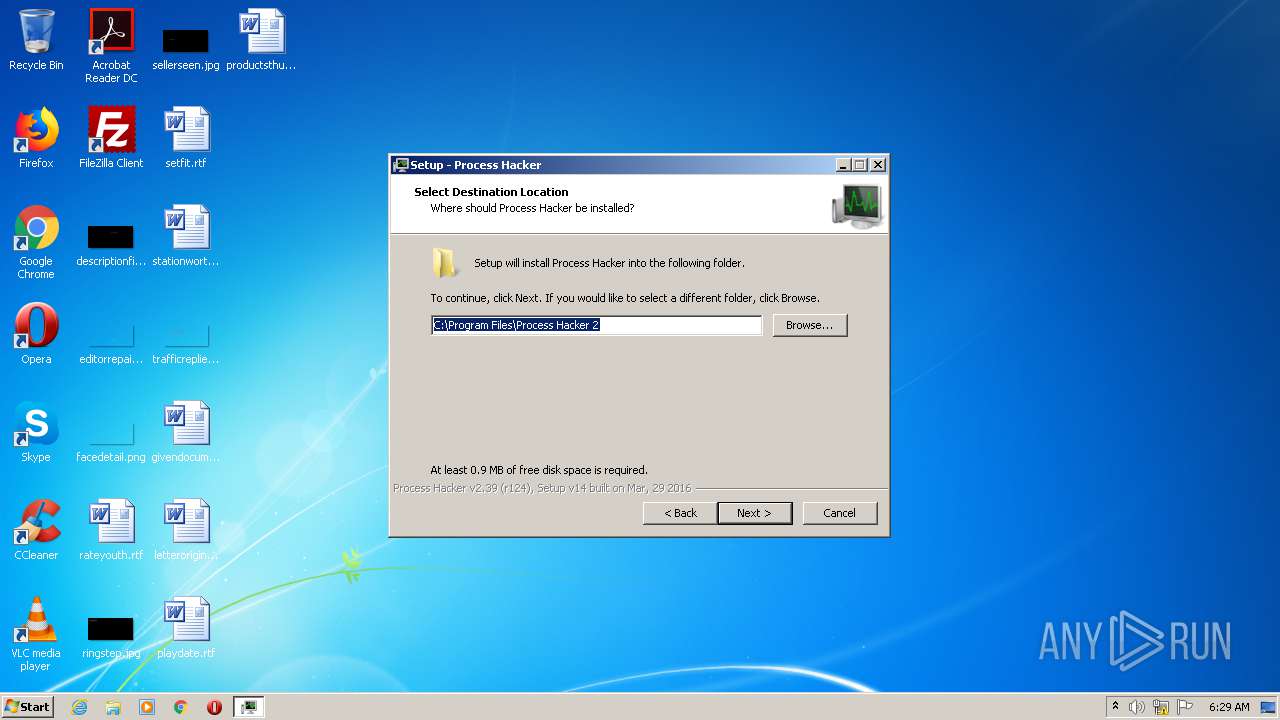
- processhacker-2.39-setup.exe (PID: 3312)
- processhacker-2.39-setup.exe (PID: 2816)
- ProcessHacker.exe (PID: 2656)
- ProcessHacker.exe (PID: 2172)
Loads dropped or rewritten executable
- ProcessHacker.exe (PID: 2656)
Changes settings of System certificates
- ProcessHacker.exe (PID: 2172)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2244)
- processhacker-2.39-setup.exe (PID: 3312)
- chrome.exe (PID: 1456)
- processhacker-2.39-setup.exe (PID: 2816)
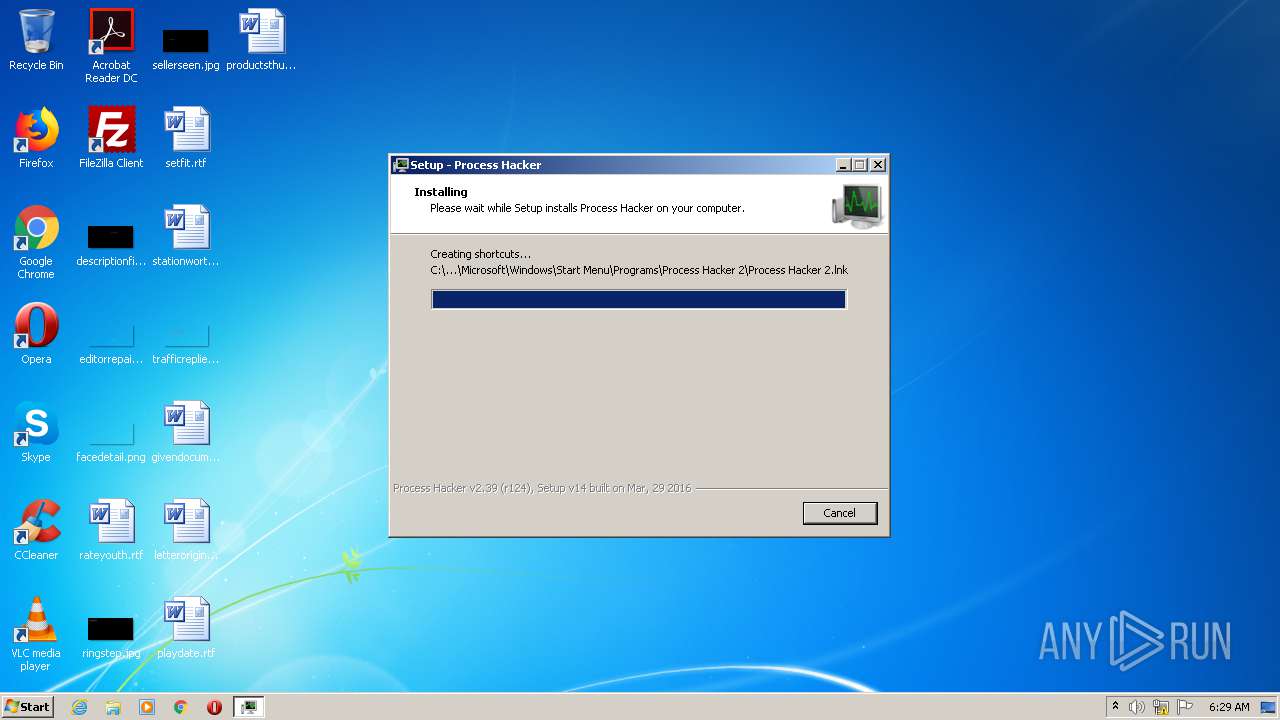
- processhacker-2.39-setup.tmp (PID: 1940)
Uses RUNDLL32.EXE to load library
- chrome.exe (PID: 2244)
Executed via COM
- DllHost.exe (PID: 876)
- DllHost.exe (PID: 3440)
Adds / modifies Windows certificates
- ProcessHacker.exe (PID: 2172)
Creates files in the user directory
- ProcessHacker.exe (PID: 2656)
INFO
Application launched itself
- chrome.exe (PID: 2244)
Reads the hosts file
- chrome.exe (PID: 2244)
- chrome.exe (PID: 1456)
Reads Internet Cache Settings
- chrome.exe (PID: 2244)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2244)
Creates files in the user directory
- chrome.exe (PID: 2244)
Application was dropped or rewritten from another process
- processhacker-2.39-setup.tmp (PID: 1156)
- processhacker-2.39-setup.tmp (PID: 1940)
Loads dropped or rewritten executable
- processhacker-2.39-setup.tmp (PID: 1940)
Creates a software uninstall entry
- processhacker-2.39-setup.tmp (PID: 1940)
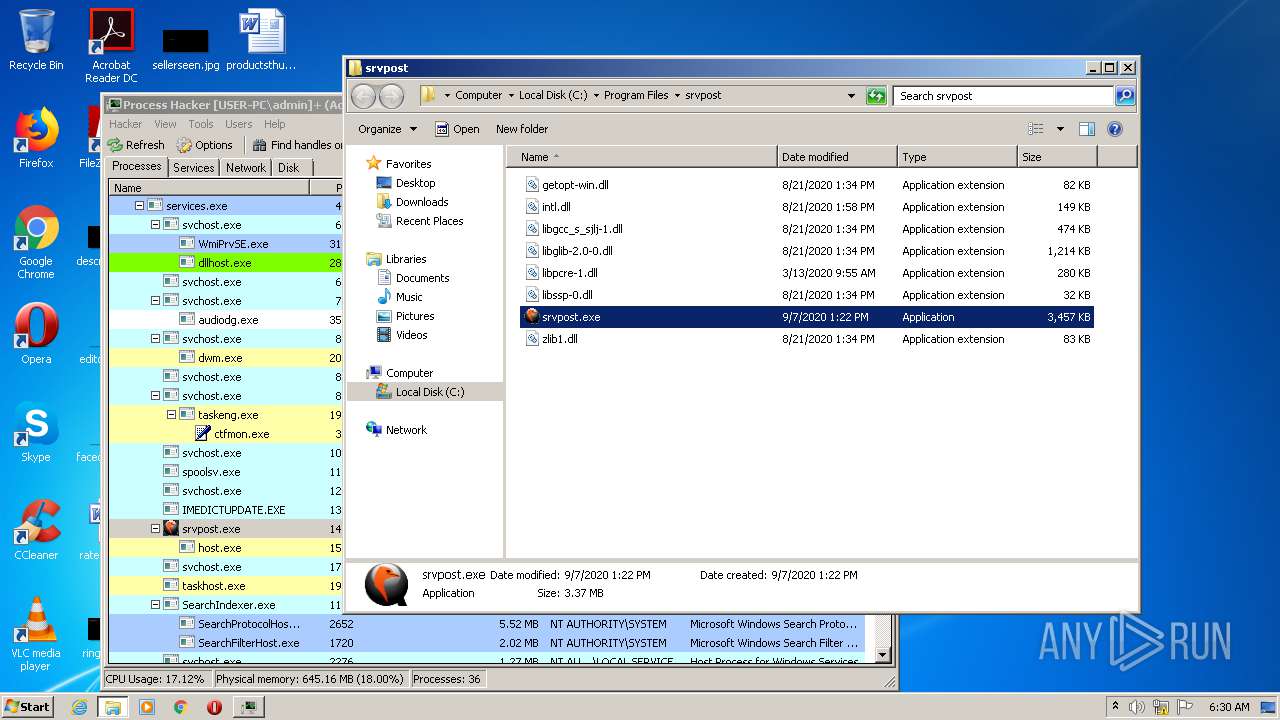
Creates files in the program directory
- processhacker-2.39-setup.tmp (PID: 1940)
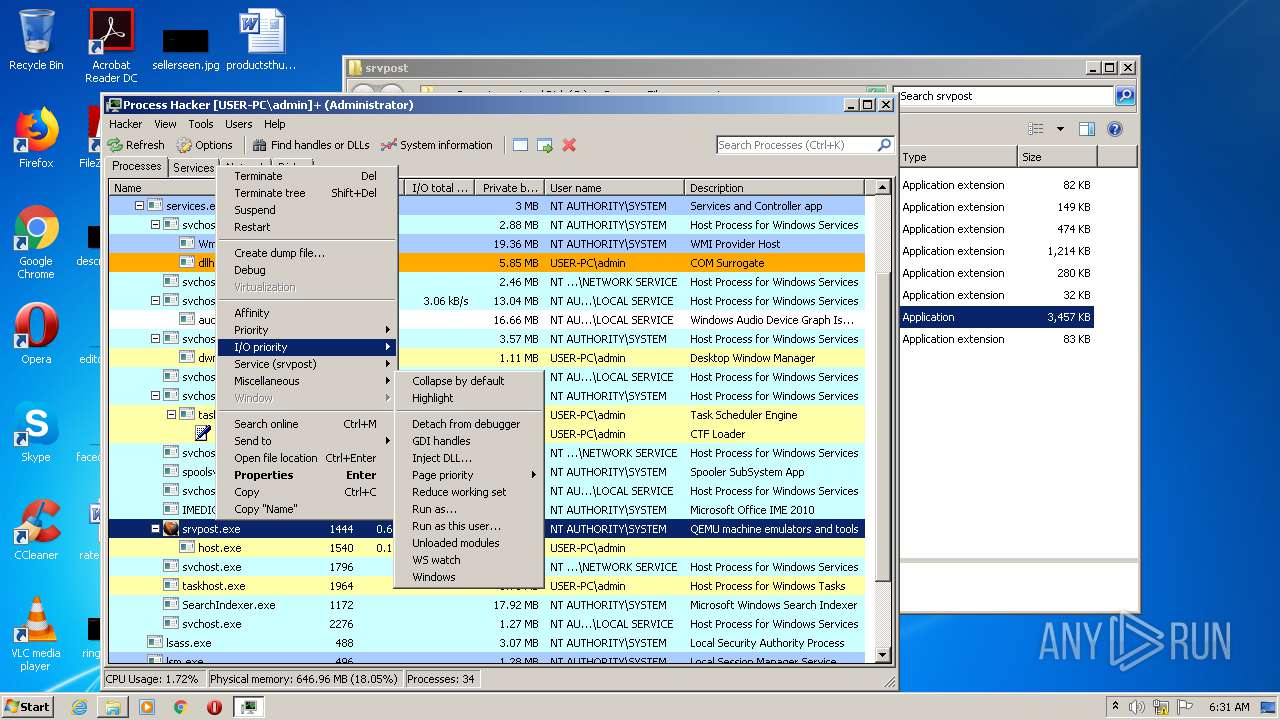
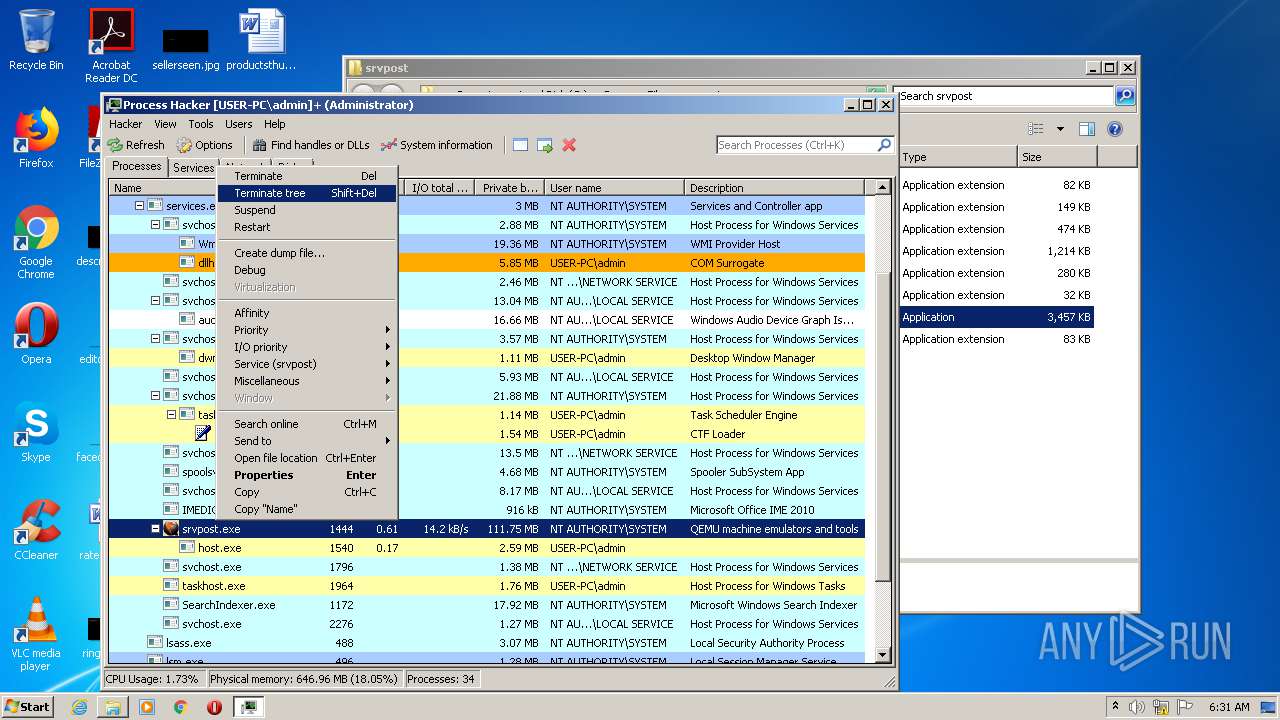
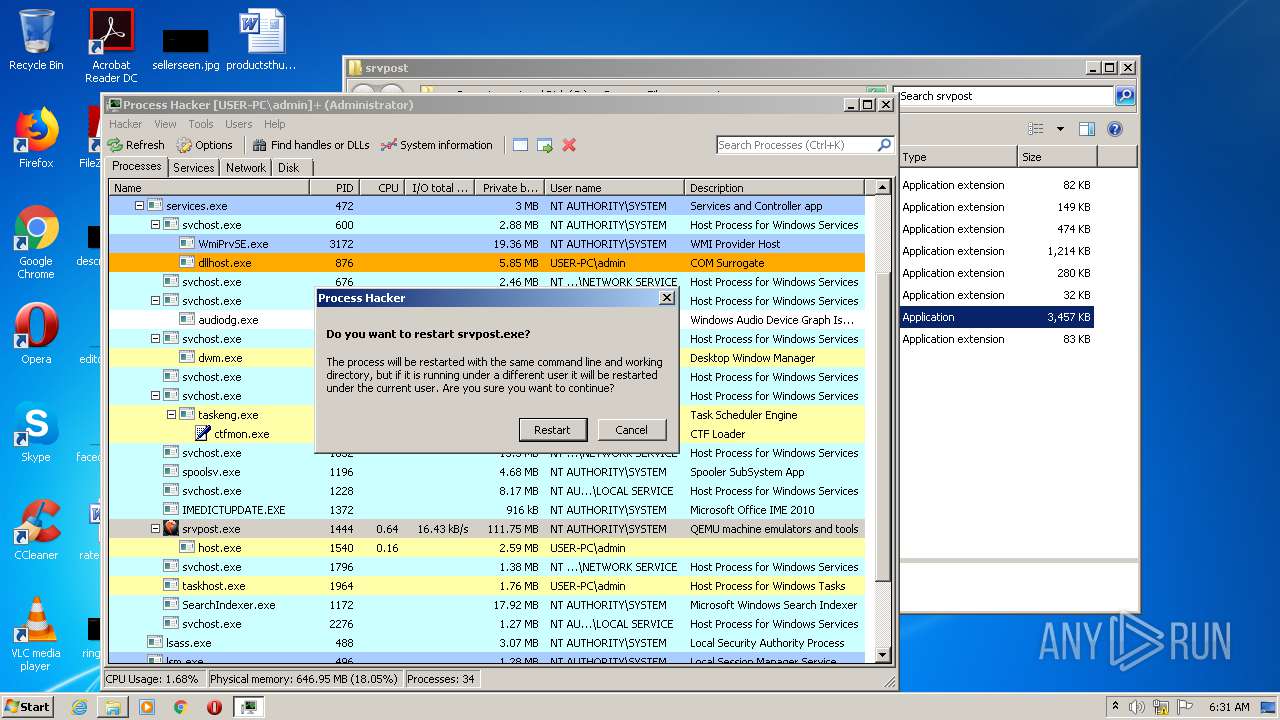
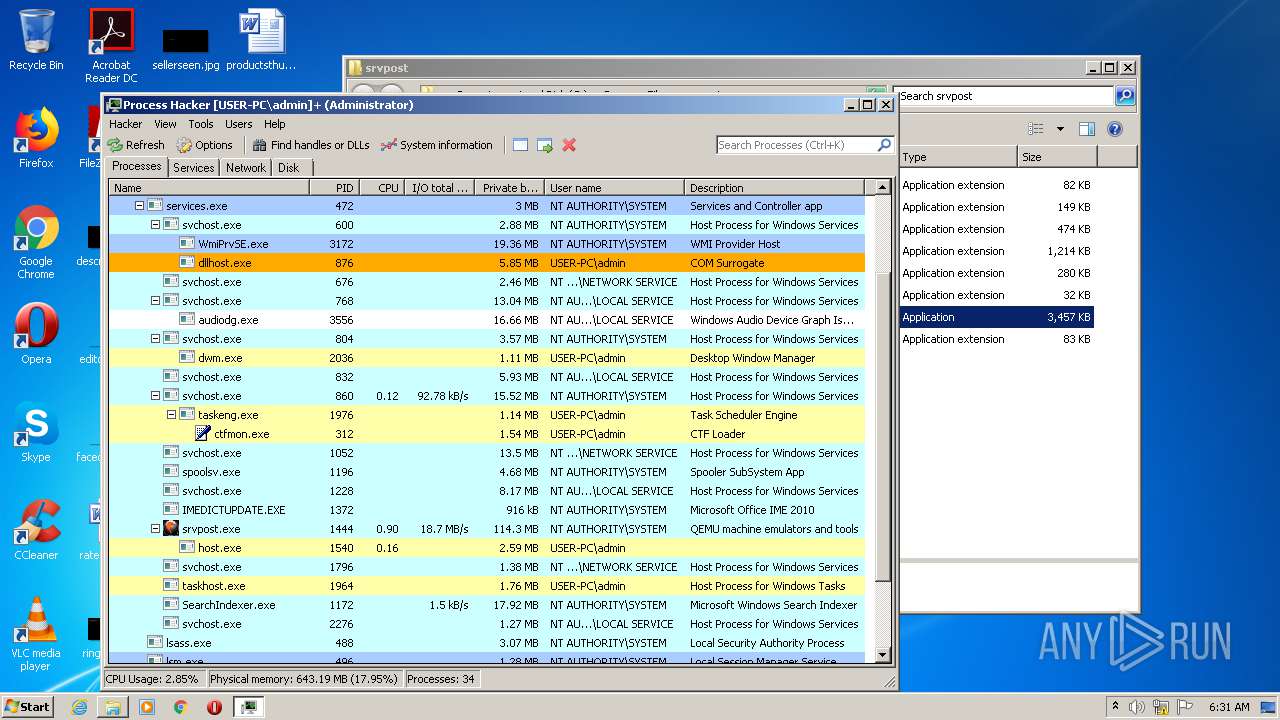
Manual execution by user
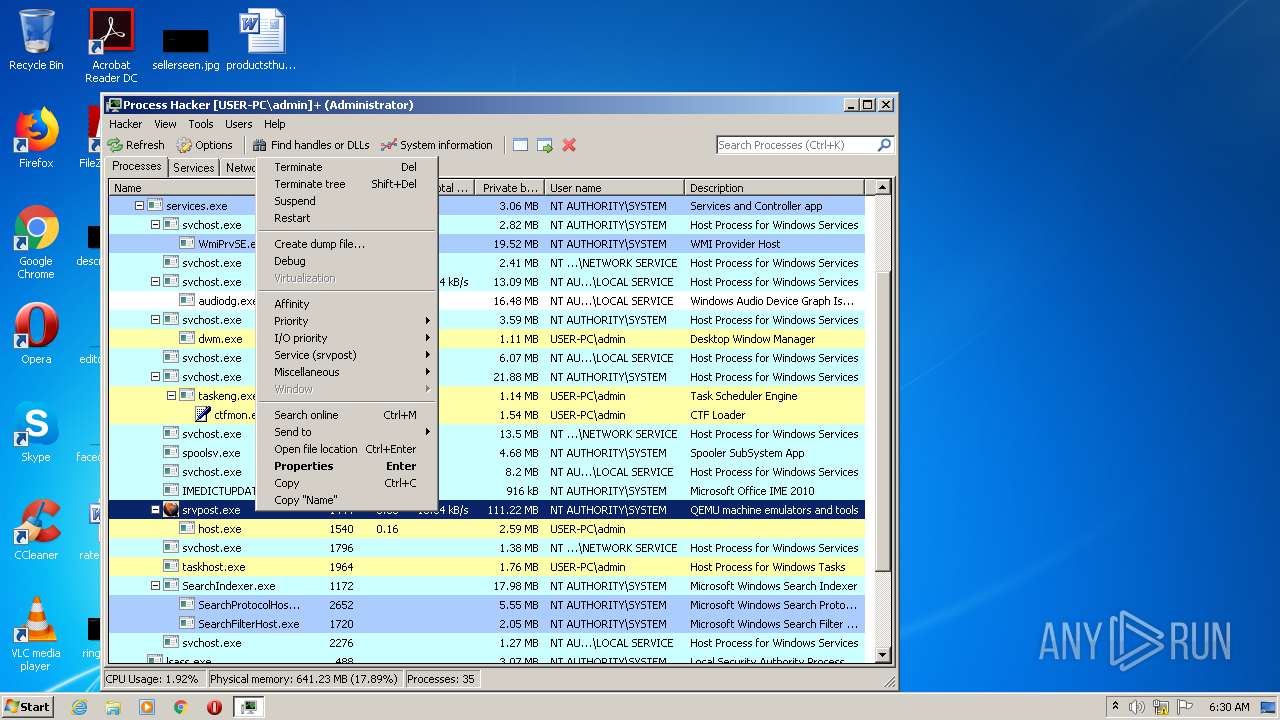
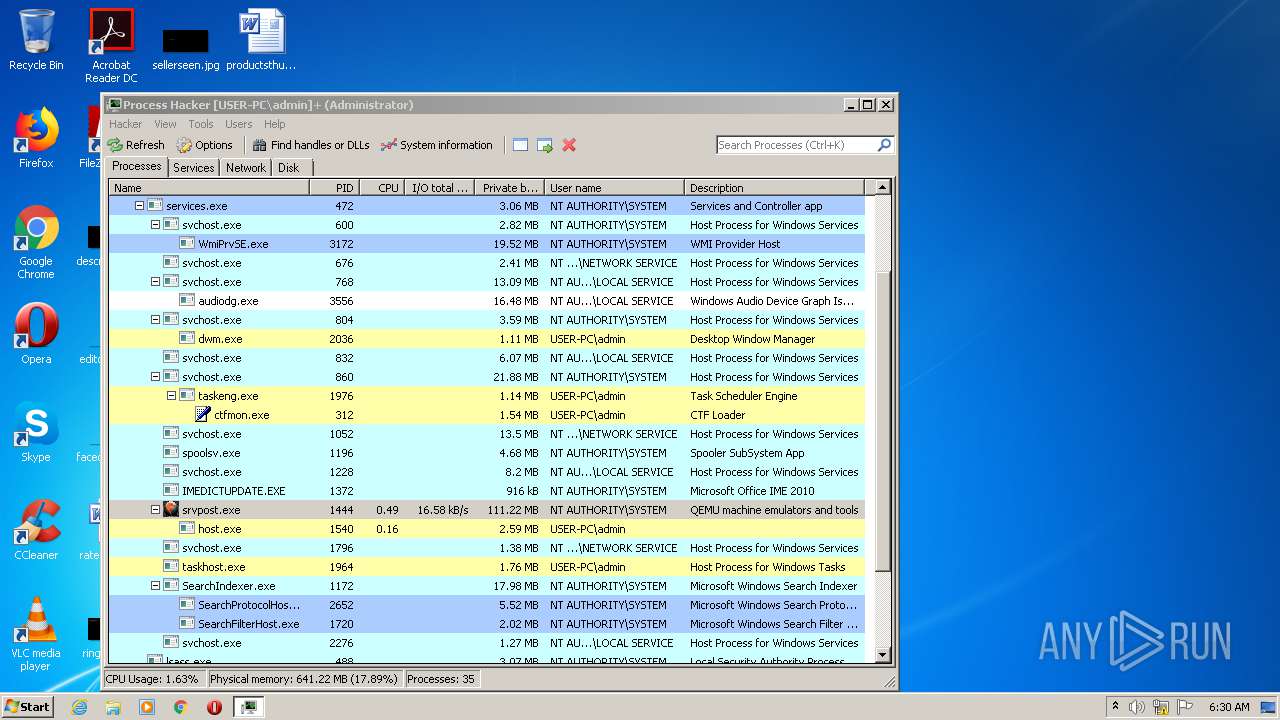
- ProcessHacker.exe (PID: 2172)
- srvpost.exe (PID: 2192)
- srvpost.exe (PID: 1572)
Reads settings of System Certificates
- ProcessHacker.exe (PID: 2172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
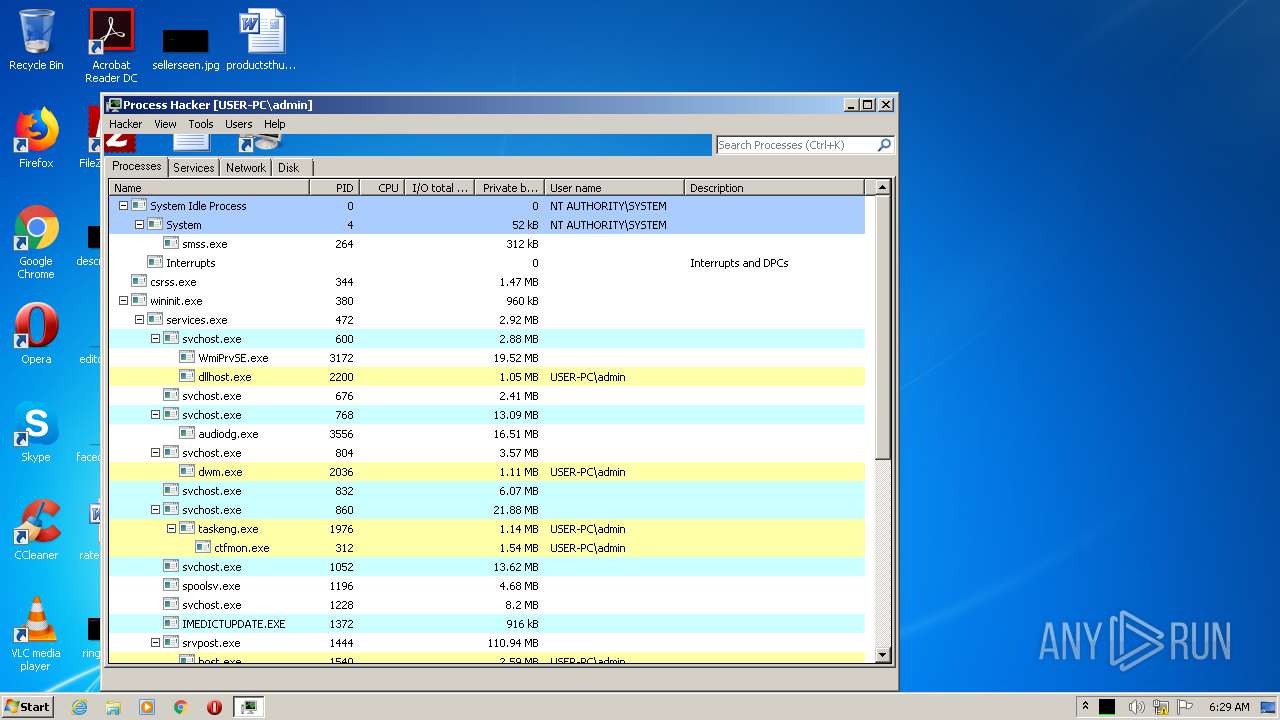
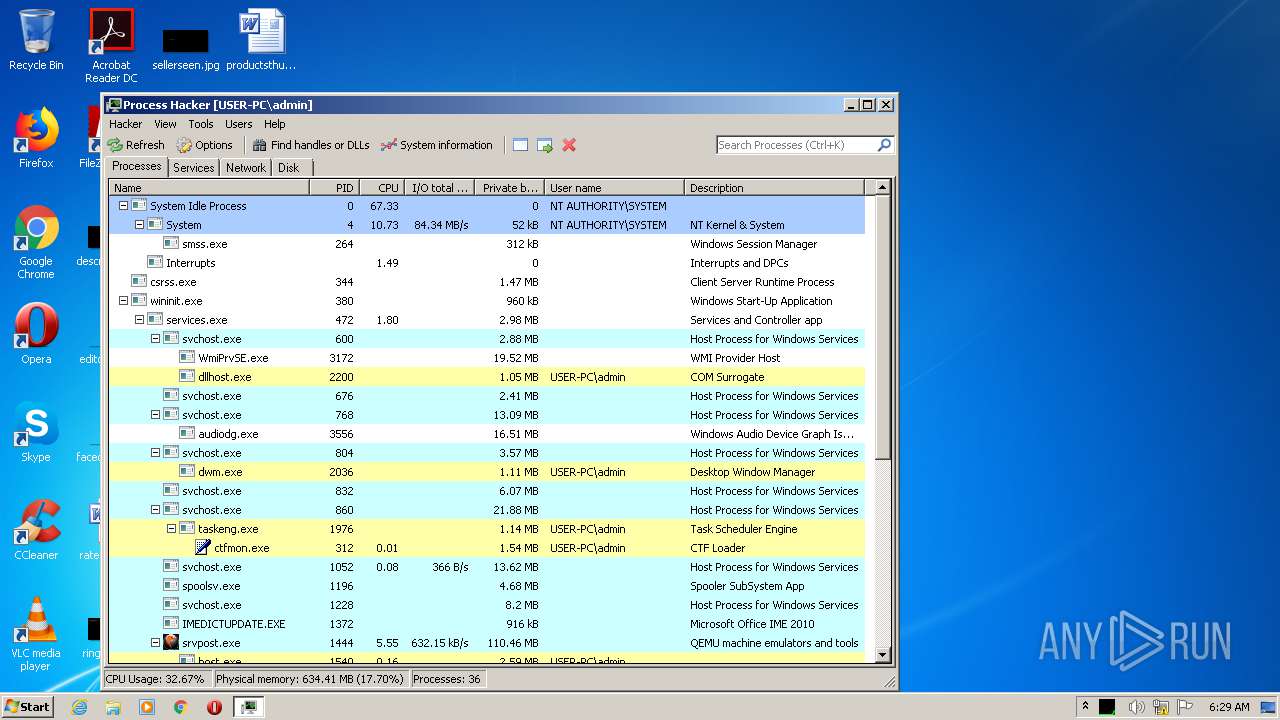
Total processes
116
Monitored processes
62
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18434204476512382608 --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4012 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10191767970045487800 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3028 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14440927450008070576 --renderer-client-id=38 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4192 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 876 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14030803263269476155 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3632 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10228912612317756302 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2152 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1156 | "C:\Users\admin\AppData\Local\Temp\is-16DHO.tmp\processhacker-2.39-setup.tmp" /SL5="$A015A,1874675,150016,C:\Users\admin\Downloads\processhacker-2.39-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-16DHO.tmp\processhacker-2.39-setup.tmp | — | processhacker-2.39-setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11814721602309142517 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=8921078924063944703 --mojo-platform-channel-handle=496 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,5793935398426558615,11382913846107109684,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=17253856853888180696 --mojo-platform-channel-handle=1628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 376
Read events
2 065
Write events
277
Delete events
34
Modification events
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2244-13245917185997375 |
Value: 259 | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3228-13245745346152343 |
Value: 0 | |||
| (PID) Process: | (2244) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
23
Suspicious files
331
Text files
294
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F741702-8C4.pma | — | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF19b1a3.TMP | — | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\82787b51-69de-426b-b89b-8f2db8768149.tmp | — | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000046.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT~RF19b24e.TMP | text | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | text | |
MD5:— | SHA256:— | |||
| 2244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old~RF19b2eb.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
180
DNS requests
101
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
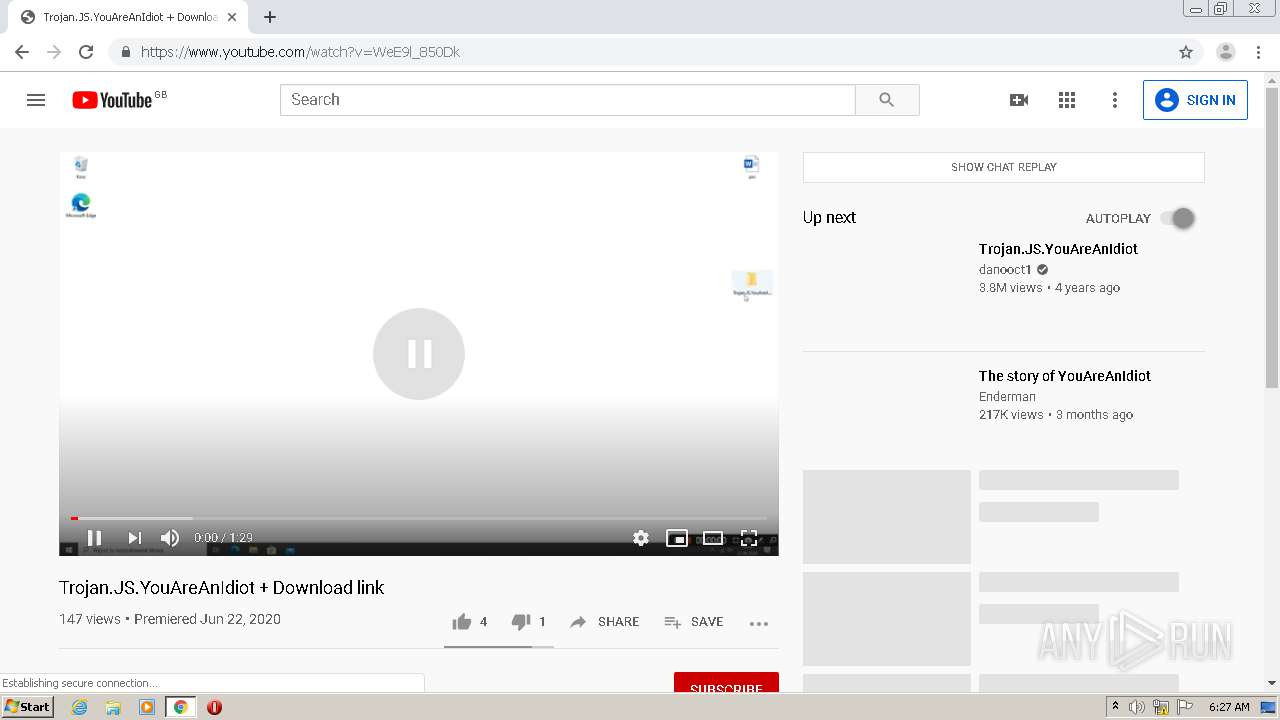
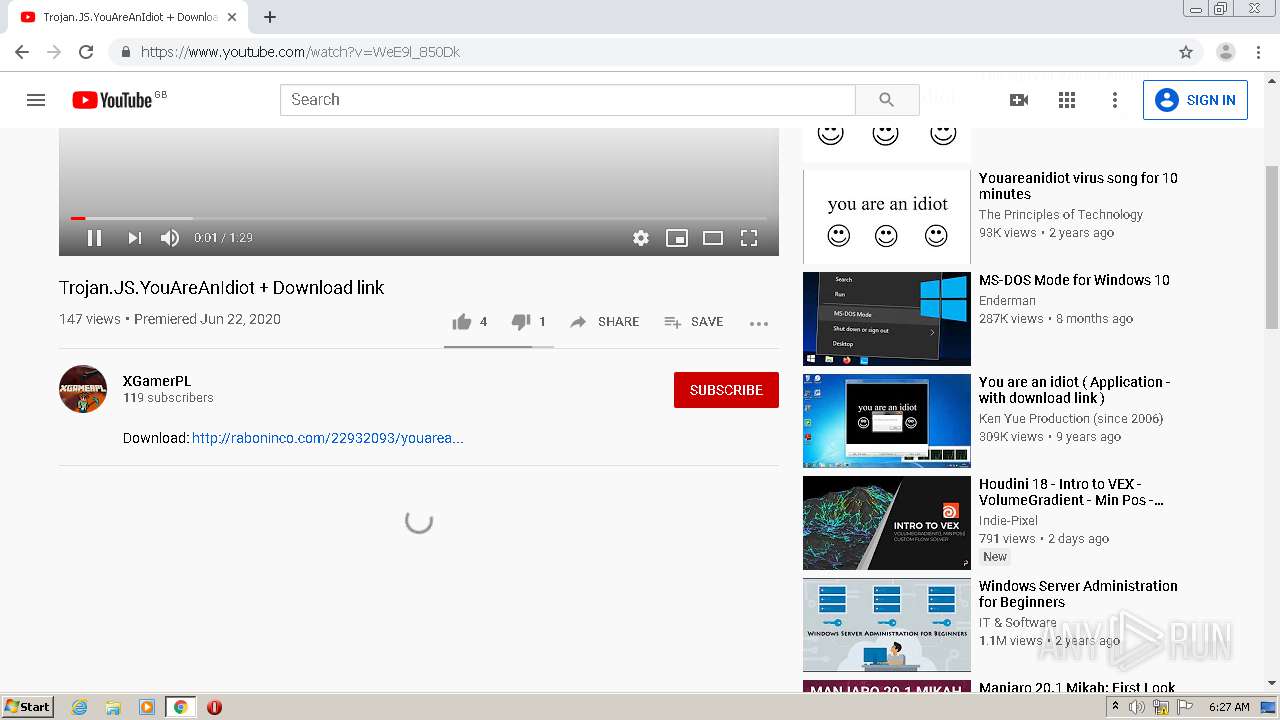
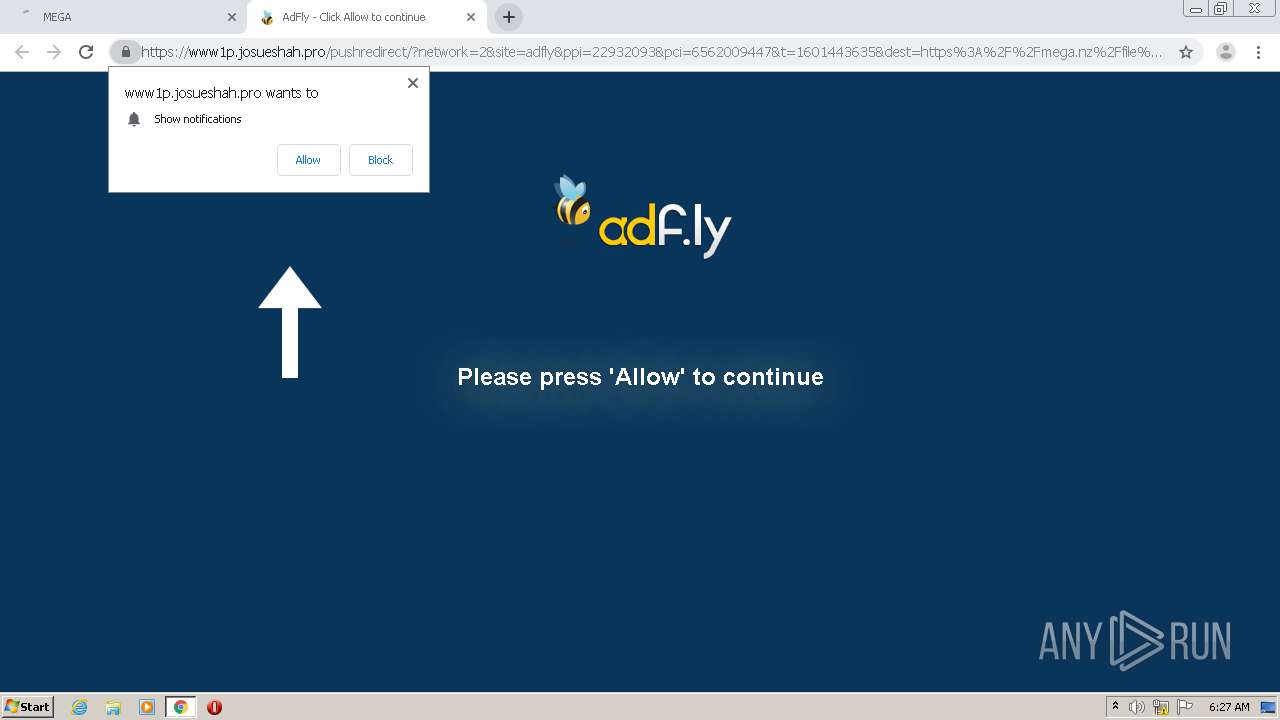
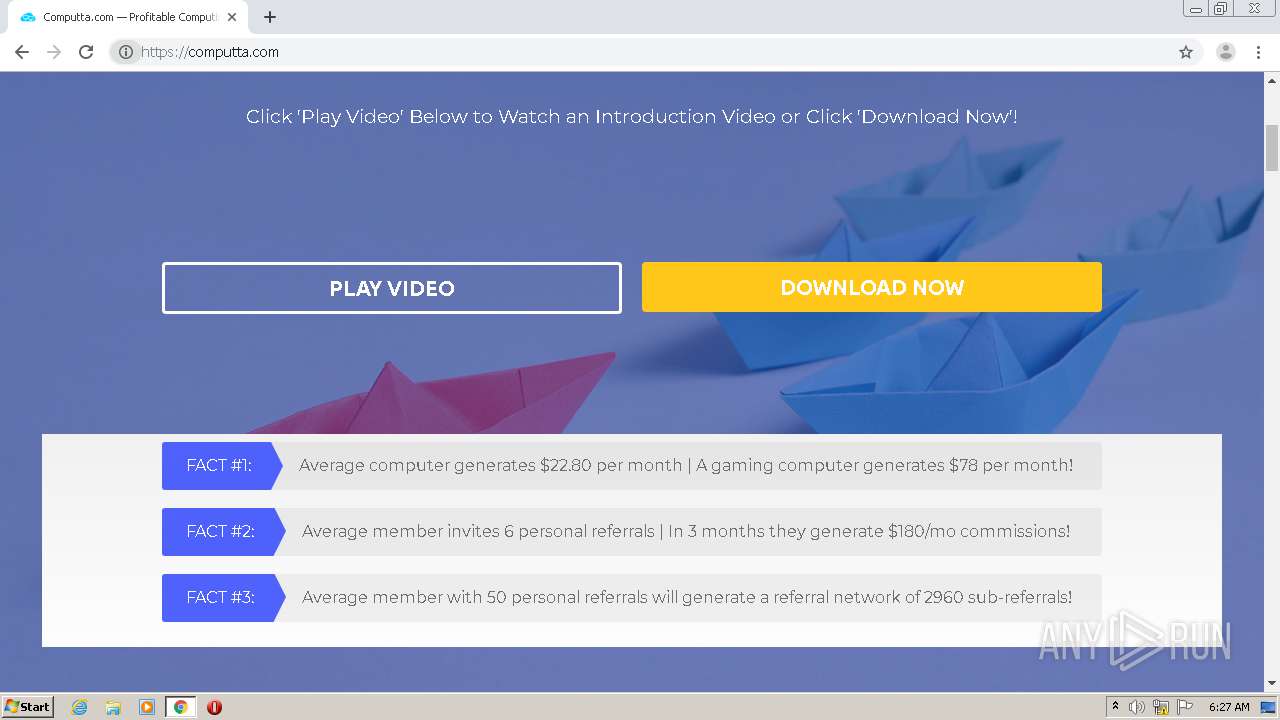
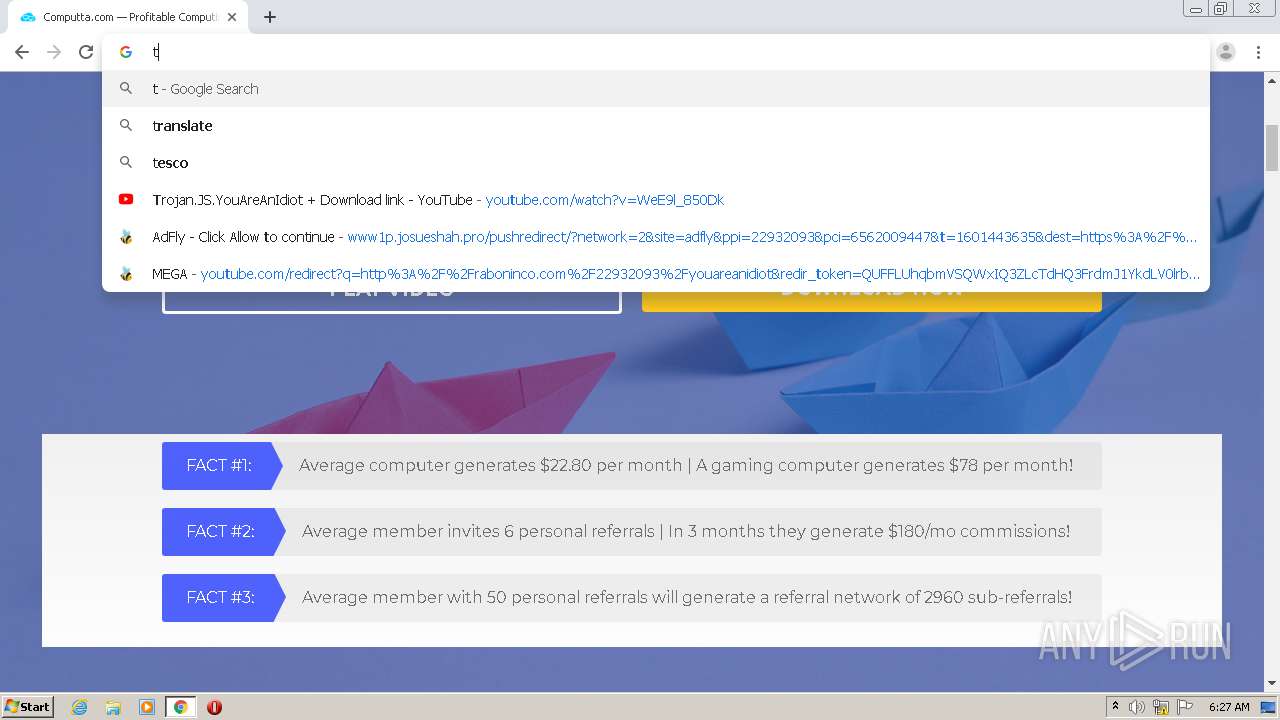
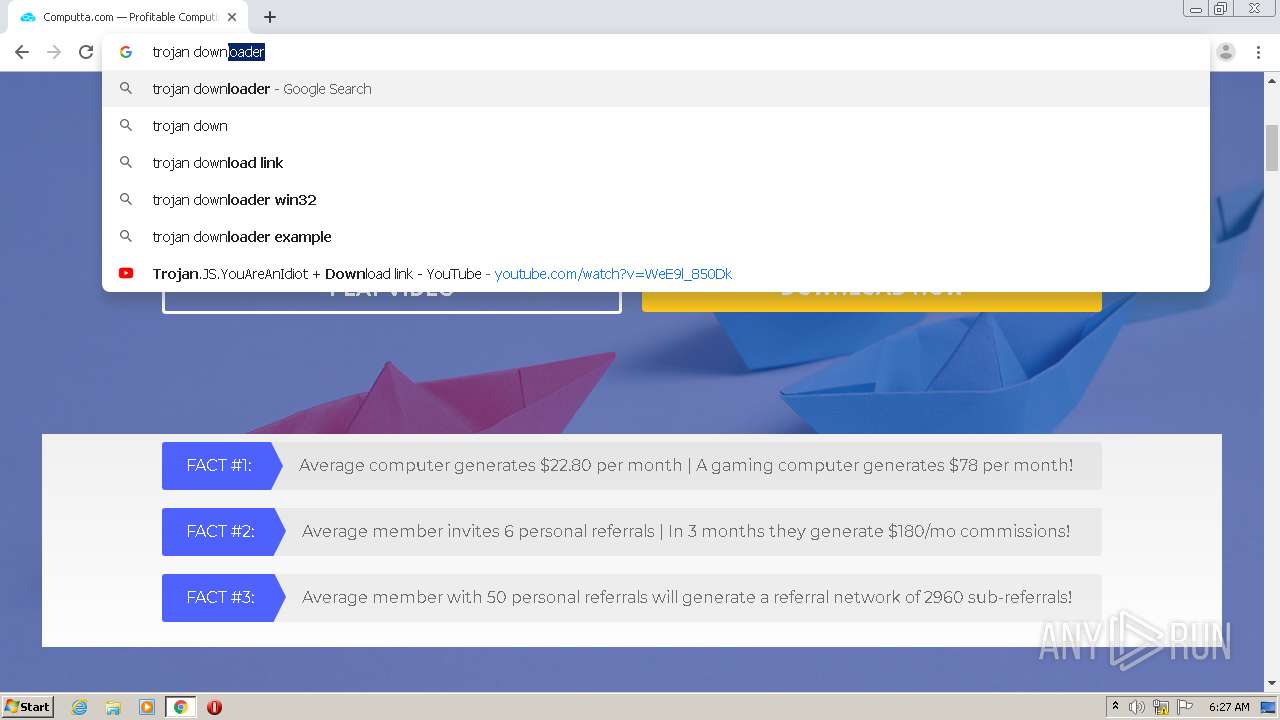
1456 | chrome.exe | GET | 301 | 172.67.145.201:80 | http://raboninco.com/22932093/youareanidiot | US | — | — | whitelisted |
1456 | chrome.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
1456 | chrome.exe | GET | 200 | 172.64.105.28:80 | http://cdn.atharori.net/static/js/b64.js | US | text | 1.07 Kb | shared |
1456 | chrome.exe | GET | 200 | 172.64.105.28:80 | http://cdn.atharori.net/static/js/main.js | US | text | 667 b | shared |
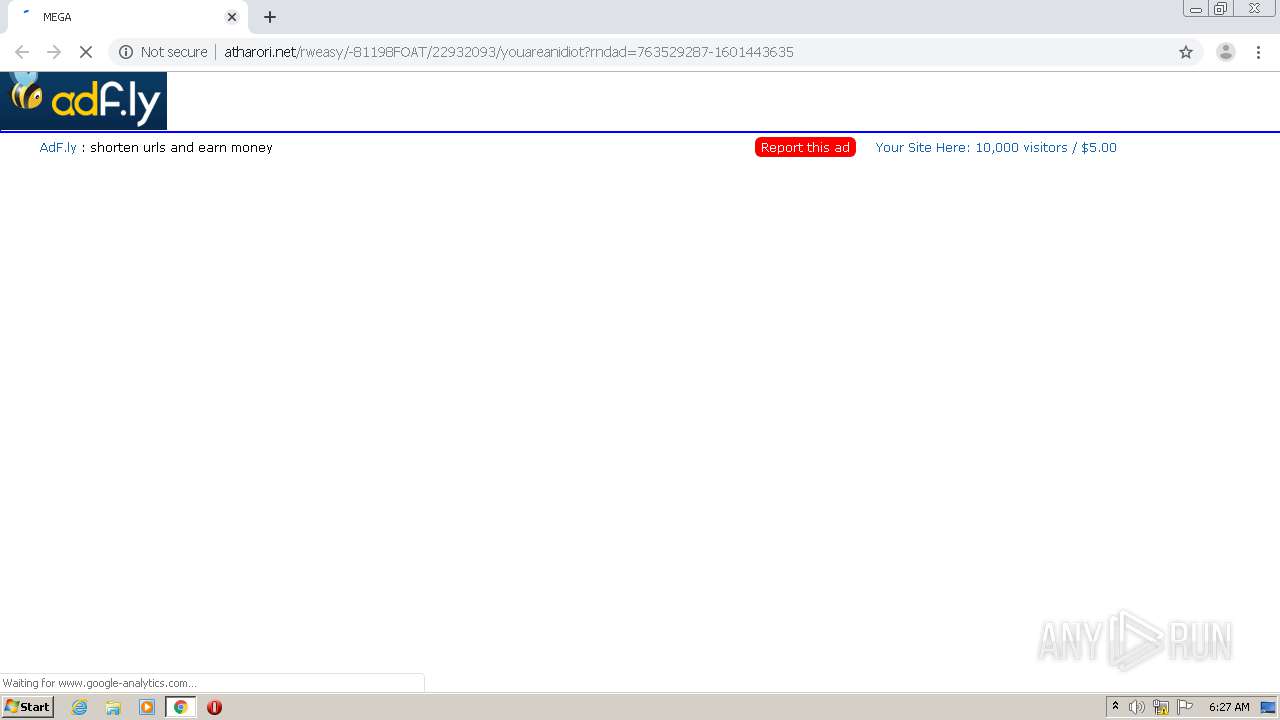
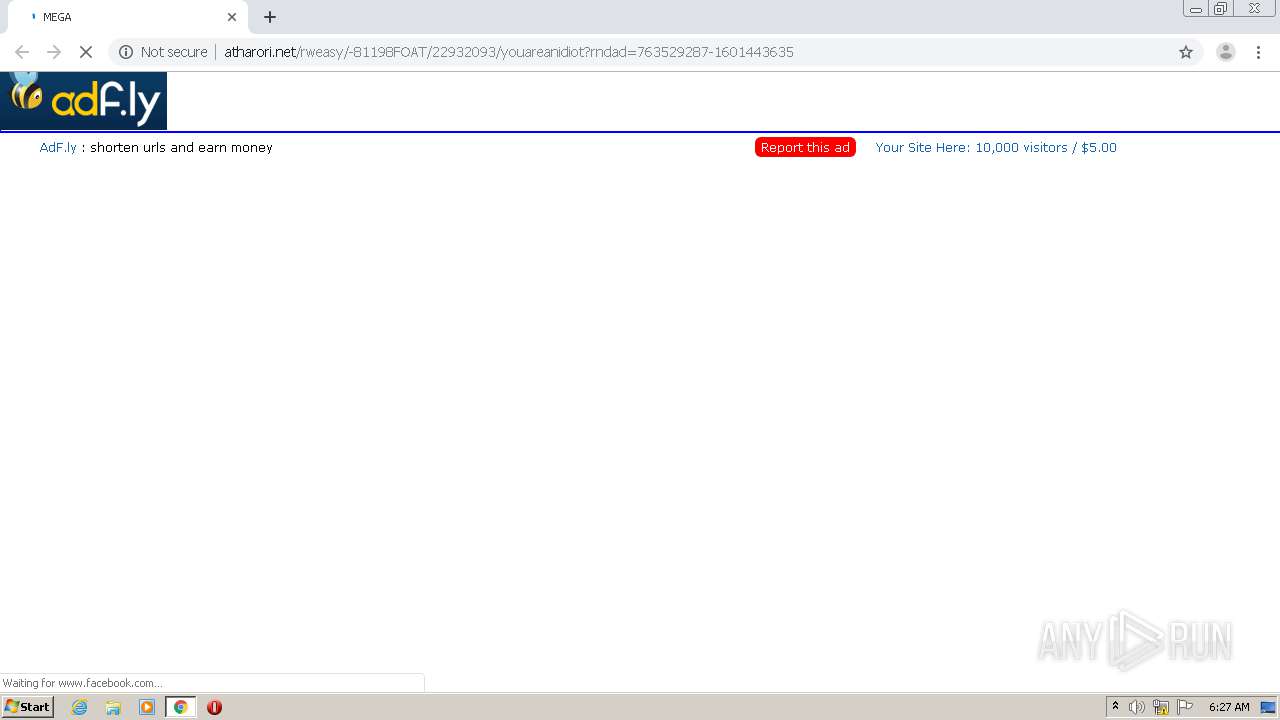
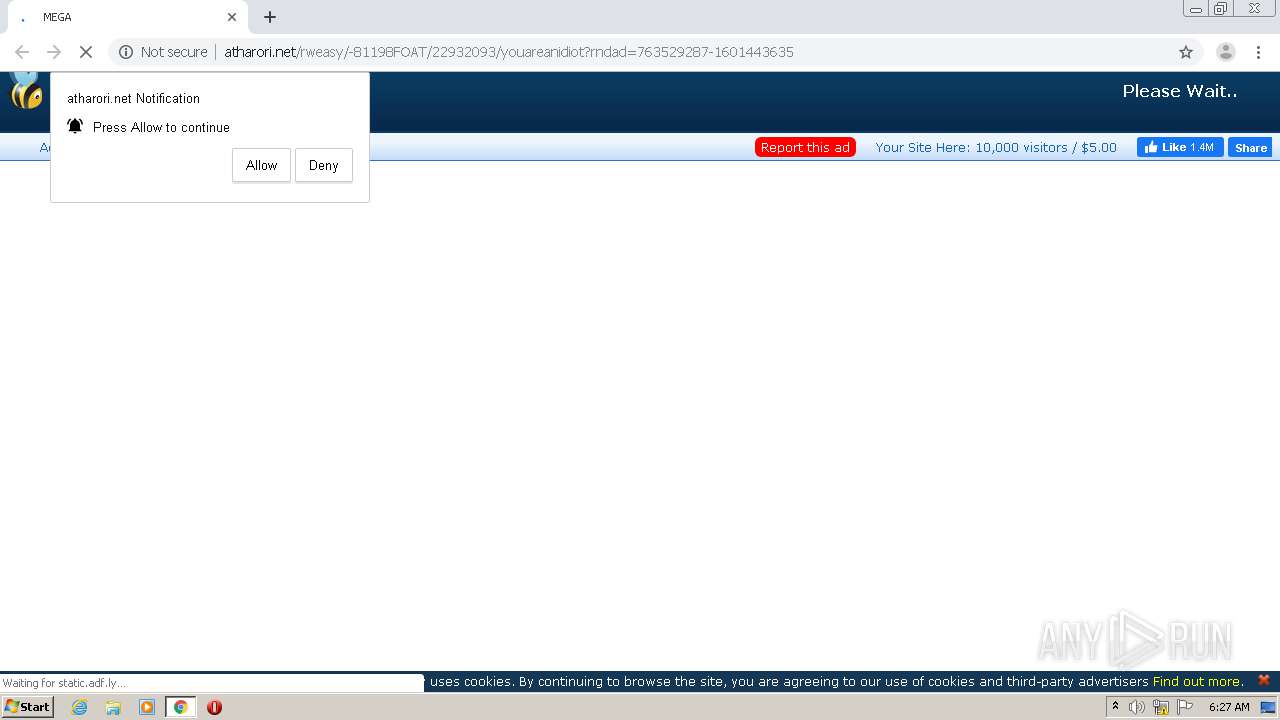
1456 | chrome.exe | GET | 200 | 172.64.105.28:80 | http://atharori.net/rweasy/-81198FOAT/22932093/youareanidiot?rndad=763529287-1601443635 | US | html | 5.90 Kb | shared |
1456 | chrome.exe | GET | 200 | 172.64.105.28:80 | http://cdn.atharori.net/static/js/view111.js | US | text | 28.1 Kb | shared |
1456 | chrome.exe | GET | 200 | 172.64.105.28:80 | http://cdn.atharori.net/static/css/adfly_7.css | US | text | 869 b | shared |
1456 | chrome.exe | GET | 304 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
1456 | chrome.exe | GET | 304 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
1456 | chrome.exe | GET | 200 | 143.204.101.151:80 | http://d1nmxiiewlx627.cloudfront.net/?ixmnd=709056 | US | compressed | 36.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1456 | chrome.exe | 138.197.15.59:443 | zeltser.com | Digital Ocean, Inc. | US | unknown |
1456 | chrome.exe | 151.139.128.14:80 | crl.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
1456 | chrome.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
1456 | chrome.exe | 172.217.16.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1456 | chrome.exe | 172.217.23.110:443 | clients1.google.com | Google Inc. | US | whitelisted |
1456 | chrome.exe | 172.217.23.132:443 | www.google.com | Google Inc. | US | whitelisted |
1456 | chrome.exe | 142.250.74.206:443 | ogs.google.com | Google Inc. | US | whitelisted |
1456 | chrome.exe | 216.58.205.238:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
1456 | chrome.exe | 216.58.212.142:443 | play.google.com | Google Inc. | US | whitelisted |
1456 | chrome.exe | 172.217.16.130:443 | adservice.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zeltser.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
crl.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
cdn.zeltser.com |
| whitelisted |
s.w.org |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1456 | chrome.exe | Attempted User Privilege Gain | AV POLICY Observed Suspicious JScript serving Adware Inbound |
1456 | chrome.exe | Attempted User Privilege Gain | AV POLICY Observed Suspicious JScript serving Adware Inbound |