| File name: | WPinternals 2.8.zip |
| Full analysis: | https://app.any.run/tasks/2371bda8-d76c-4bad-947c-0fc48e86af88 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 15:11:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8CD6D8B48947C5974E0AC015C87A3096 |
| SHA1: | 78B8F73F8FE6172C656AC0841E34DD93F652E87D |
| SHA256: | 4F9E9D387FEE6AD9ED6F0D6AFEDFA36E34ECEBB930BA82B45D89FE99377679D5 |
| SSDEEP: | 24576:ihG/kEvnrj522c9UBeNpKq6KMLLugEKBOD7sg:nRPI2cespKqiubFt |
MALICIOUS
Application was dropped or rewritten from another process
- WPinternals.exe (PID: 2220)
- WPinternals.exe (PID: 3164)
SUSPICIOUS
Reads the Internet Settings
- WPinternals.exe (PID: 3164)
INFO
Checks supported languages
- WPinternals.exe (PID: 3164)
Reads the computer name
- WPinternals.exe (PID: 3164)
The process checks LSA protection
- WPinternals.exe (PID: 3164)
- wisptis.exe (PID: 3896)
Reads the machine GUID from the registry
- WPinternals.exe (PID: 3164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1048)
Manual execution by a user
- WPinternals.exe (PID: 2220)
- notepad.exe (PID: 4088)
- WPinternals.exe (PID: 3164)
Creates files in the program directory
- WPinternals.exe (PID: 3164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
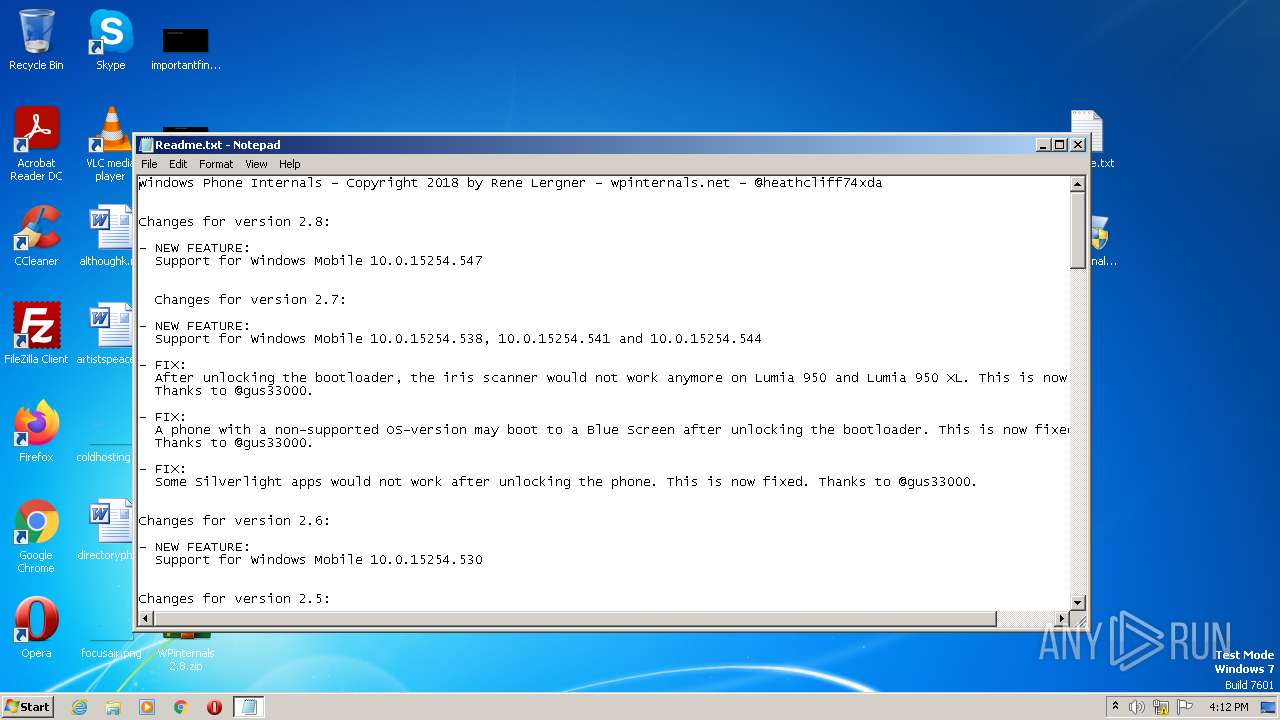
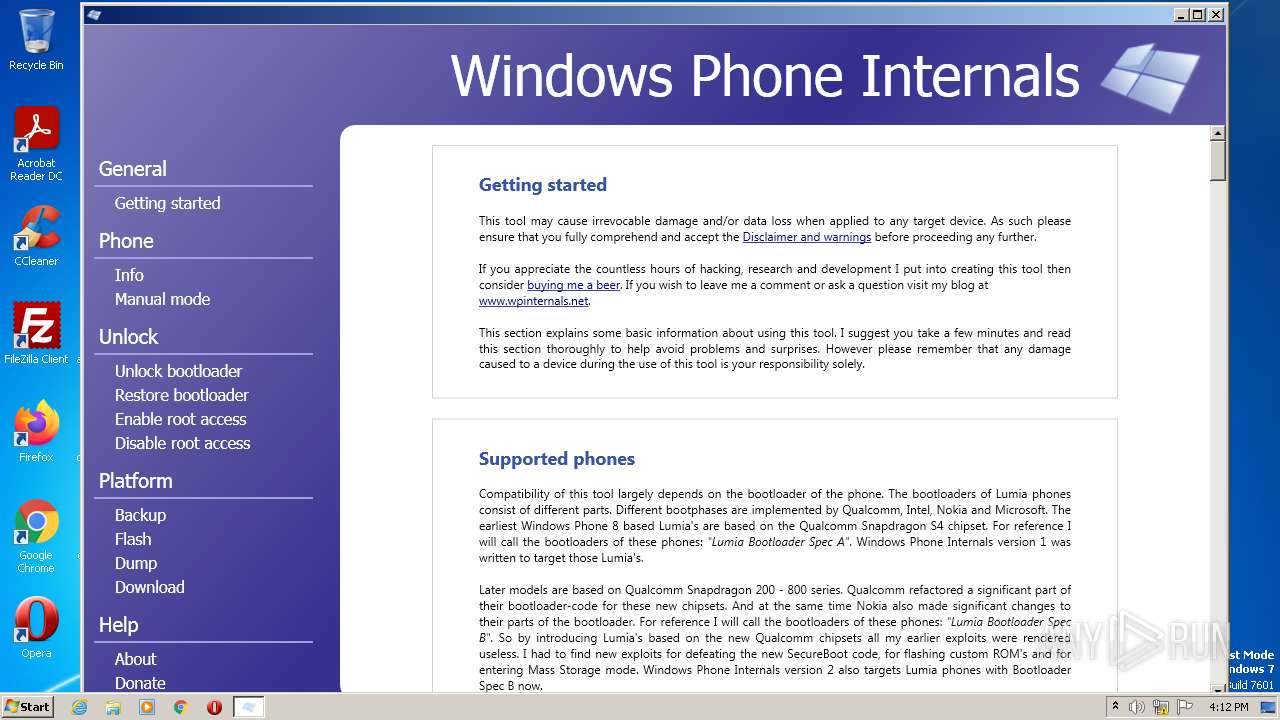
| ZipFileName: | Readme.txt |
|---|---|
| ZipUncompressedSize: | 8621 |
| ZipCompressedSize: | 2950 |
| ZipCRC: | 0xd18a08c2 |
| ZipModifyDate: | 2019:01:11 22:22:20 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\WPinternals 2.8.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
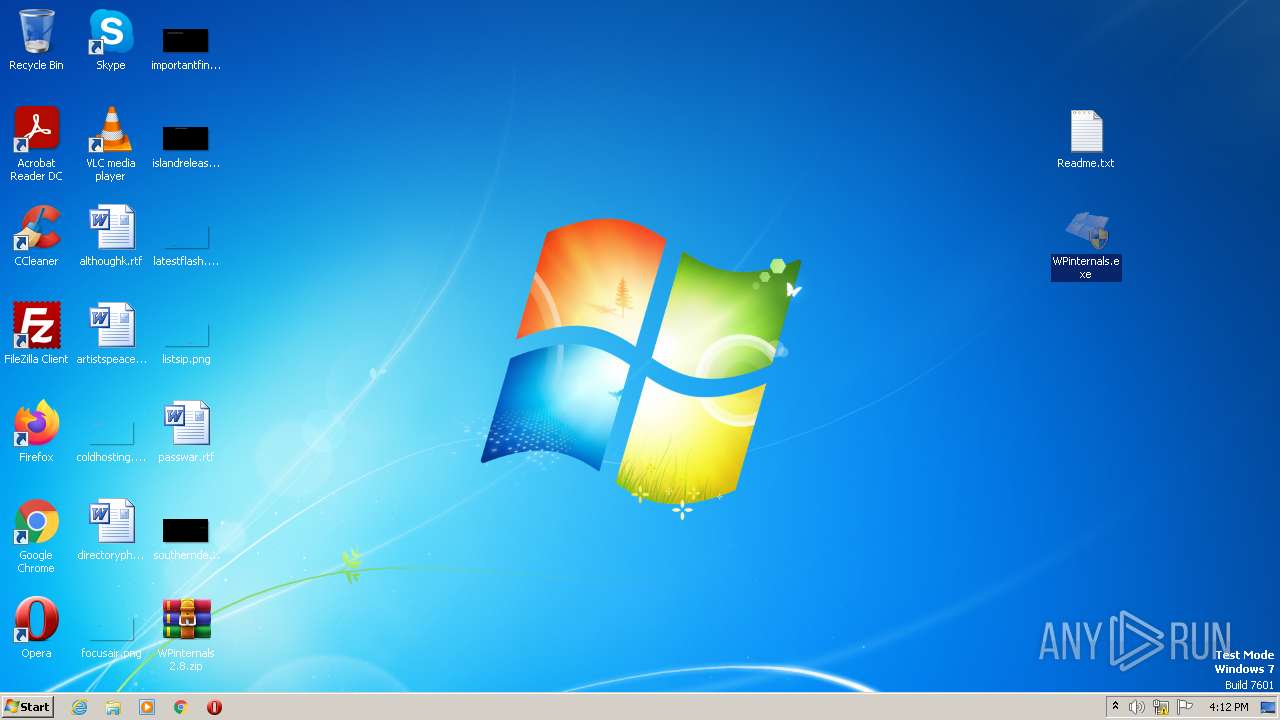
| 2220 | "C:\Users\admin\Desktop\WPinternals.exe" | C:\Users\admin\Desktop\WPinternals.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WPinternals Exit code: 3221226540 Version: 2.8.6950.39616 Modules
| |||||||||||||||
| 3164 | "C:\Users\admin\Desktop\WPinternals.exe" | C:\Users\admin\Desktop\WPinternals.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: WPinternals Exit code: 0 Version: 2.8.6950.39616 Modules
| |||||||||||||||
| 3516 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | — | WPinternals.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3896 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | — | WPinternals.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 24 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4088 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Readme.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 438
Read events
2 378
Write events
60
Delete events
0
Modification events
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1048.41101\WPinternals.exe | executable | |
MD5:— | SHA256:— | |||
| 1048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1048.41101\Readme.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report