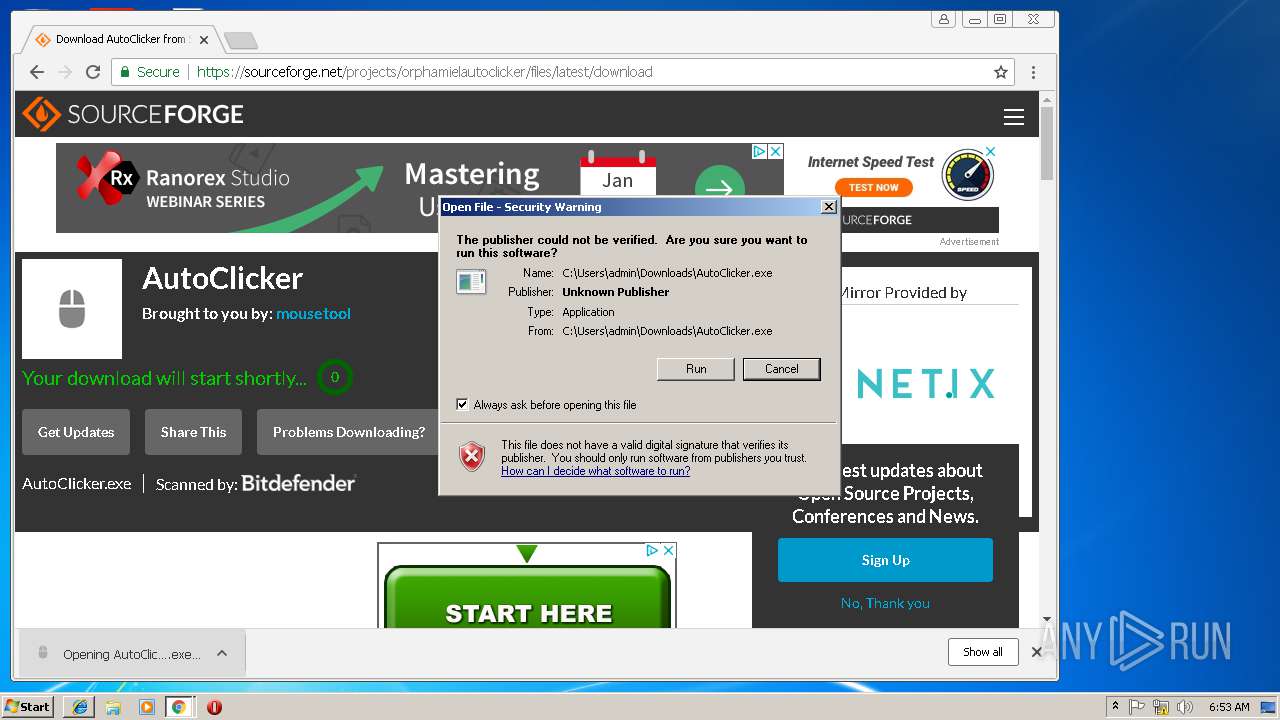
| URL: | https://downloads.sourceforge.net:443/project/orphamielautoclicker/AutoClicker.exe?r=https%3A%2F%2Fsourceforge.net%2Fprojects%2Forphamielautoclicker%2F&ts=1548042747&use_mirror=superb-dca2 |
| Full analysis: | https://app.any.run/tasks/1a6f7411-fb17-4bf9-97b6-a50a022dfe9c |
| Verdict: | Malicious activity |
| Analysis date: | January 21, 2019, 06:50:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 65E8A7B53997C6EC3F1D4AC1565BE488 |
| SHA1: | 85F5F53EBC146B0AE0BB115E338F6581099C04CE |
| SHA256: | 4F9CEFB123E1E79515C3CC5176AE1B8AC2E0DB9596A61C4EC092E286B730B4EA |
| SSDEEP: | 3:N8SE4LVSuLA4vtbBhOAX/jmJMGOtdcR8AWCXjC2SuLAgpMALhOAX2RWO7TiUaRsb:2SBnnbBhOmGOtq1zC2nIkhODniUa+TX |
MALICIOUS
Application was dropped or rewritten from another process
- AutoClicker.exe (PID: 2812)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3424)
INFO
Application launched itself
- iexplore.exe (PID: 2848)
- chrome.exe (PID: 3424)
Reads settings of System Certificates
- iexplore.exe (PID: 2848)
- chrome.exe (PID: 3424)
Changes settings of System certificates
- iexplore.exe (PID: 2848)
- chrome.exe (PID: 3424)
Changes internet zones settings
- iexplore.exe (PID: 2848)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2848)
Reads internet explorer settings
- iexplore.exe (PID: 3140)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3140)
Creates files in the user directory
- iexplore.exe (PID: 3140)
Reads Internet Cache Settings
- iexplore.exe (PID: 3140)
- chrome.exe (PID: 3424)
- iexplore.exe (PID: 3960)
- iexplore.exe (PID: 2960)
- iexplore.exe (PID: 3840)
- iexplore.exe (PID: 3932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=06854AB975B25280757038C990F0BCCF --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=06854AB975B25280757038C990F0BCCF --renderer-client-id=6 --mojo-platform-channel-handle=3548 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=B8982569F1EBCE4C06BFCC58ACAD3EFF --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=B8982569F1EBCE4C06BFCC58ACAD3EFF --renderer-client-id=13 --mojo-platform-channel-handle=2196 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=BE9C03D97ACE2644A276E6D1D04BFF73 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=BE9C03D97ACE2644A276E6D1D04BFF73 --renderer-client-id=7 --mojo-platform-channel-handle=3788 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=803E5F456626DE71C850310AD1F6DE91 --mojo-platform-channel-handle=524 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2612 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=77A24D767418FBDCD825E50AA6F392FF --mojo-platform-channel-handle=992 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=24F3AFCF83F33BB05F1240E199F340B8 --mojo-platform-channel-handle=4660 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=1045B5D7A72911C08C99D5674E5F38E5 --mojo-platform-channel-handle=3828 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
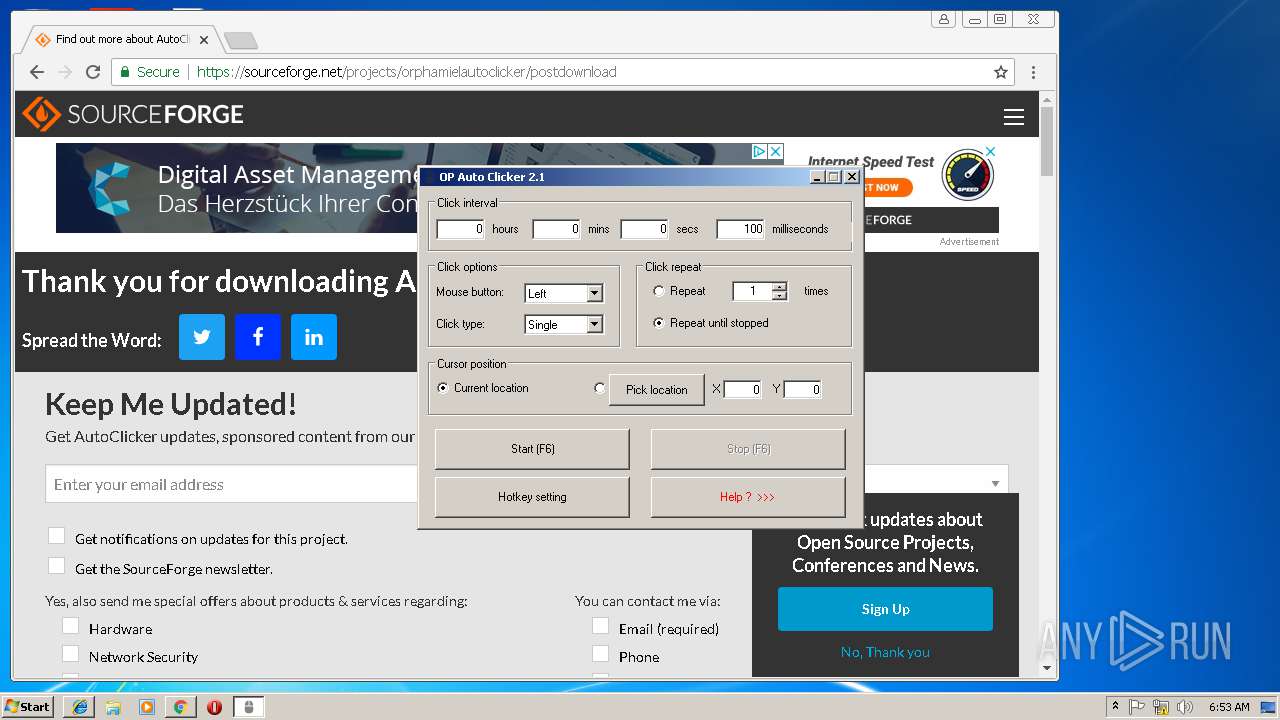
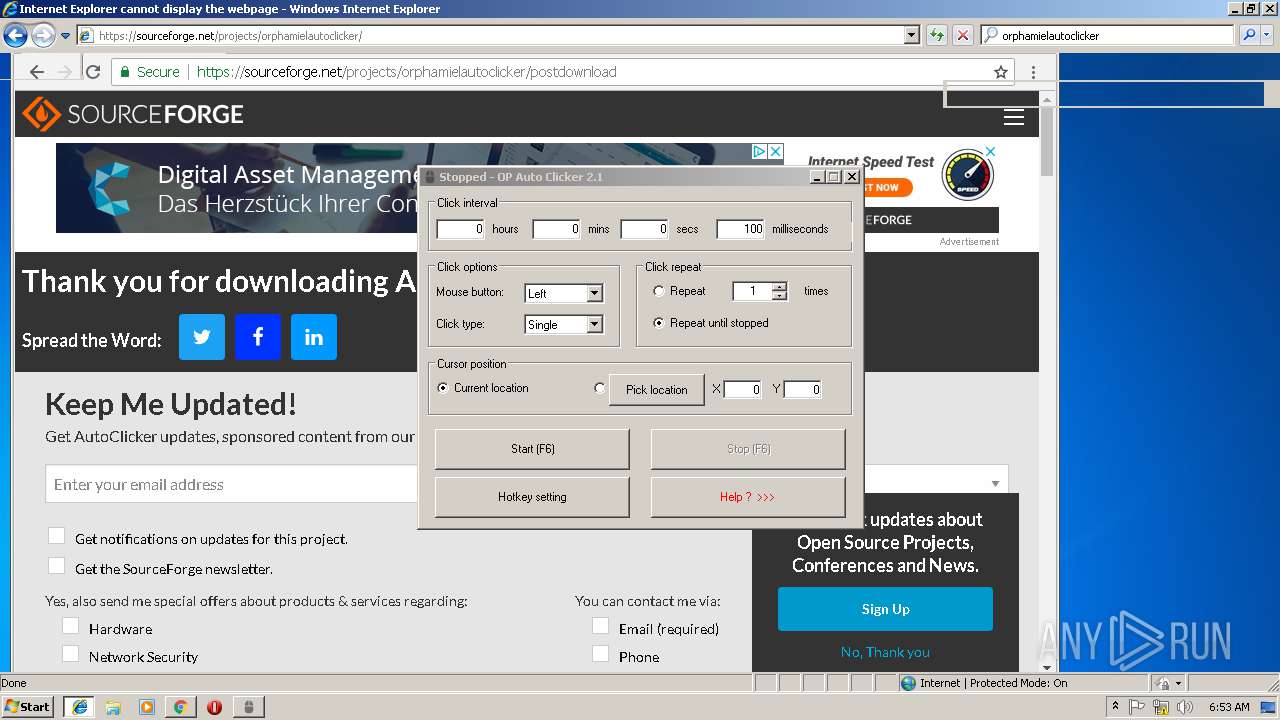
| 2812 | "C:\Users\admin\Downloads\AutoClicker.exe" | C:\Users\admin\Downloads\AutoClicker.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: OP Auto Clicker Exit code: 0 Version: 2.1 Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=924,3211385136632648544,11136466125251988613,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=4024E827D2B50DB47E35416A3366013B --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4024E827D2B50DB47E35416A3366013B --renderer-client-id=9 --mojo-platform-channel-handle=4468 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 817
Read events
1 565
Write events
245
Delete events
7
Modification events
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {EA77488F-1D48-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070100010015000600330003000802 | |||
Executable files
2
Suspicious files
107
Text files
180
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\dnserror[1] | html | |
MD5:68E03ED57EC741A4AFBBCD11FAB1BDBE | SHA256:1FF3334C3EB27033F8F37029FD72F648EDD4551FCE85FC1F5159FEAEA1439630 | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[3].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\down[1] | image | |
MD5:555E83CE7F5D280D7454AF334571FB25 | SHA256:70F316A5492848BB8242D49539468830B353DDAA850964DB4E60A6D2D7DB4880 | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\httpErrorPagesScripts[1] | text | |
MD5:E7CA76A3C9EE0564471671D500E3F0F3 | SHA256:58268CA71A28973B756A48BBD7C9DC2F6B87B62AE343E582CE067C725275B63C | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\errorPageStrings[1] | text | |
MD5:1A0563F7FB85A678771450B131ED66FD | SHA256:EB5678DE9D8F29CA6893D4E6CA79BD5AB4F312813820FE4997B009A2B1A1654C | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\favcenter[1] | image | |
MD5:25D76EE5FB5B890F2CC022D94A42FE19 | SHA256:07D07A467E4988D3C377ACD6DC9E53ABCA6B64E8FBF70F6BE19D795A1619289B | |||
| 3140 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\background_gradient[1] | image | |
MD5:20F0110ED5E4E0D5384A496E4880139B | SHA256:1471693BE91E53C2640FE7BAEECBC624530B088444222D93F2815DFCE1865D5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
63
TCP/UDP connections
244
DNS requests
141
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3140 | iexplore.exe | GET | 301 | 204.79.197.200:80 | http://bing.com/ | US | — | — | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/sa/simg/hpc26.png | US | image | 3.50 Kb | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/ | US | html | 20.8 Kb | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/az/hprichbg/rb/DivingEmperors_ROW1484400372_1920x1080.jpg | US | image | 339 Kb | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/az/hprichbg/rb/DivingEmperors_ROW1484400372_1920x1080.jpg | US | image | 339 Kb | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rb/5m/cj,nj/3e6a7d75/9a358300.js?bu=ErMe0R78Hf8d5ASNHo8e3R6RHpgeoB7JHscevB6xHdUc2By0HQ | US | text | 4.95 Kb | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/notifications/render?bnptrigger=%7B%22PartnerId%22%3A%22HomePage%22%2C%22IID%22%3A%22SERP.2000%22%2C%22Attributes%22%3A%7B%22RawRequestURL%22%3A%22%2F%22%7D%7D&IG=1622CBF563184A708335C4D7D419E30B&IID=SERP.2000 | US | html | 3.51 Kb | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/2Y/1H/cj,nj/5983aa50/f8c6dd44.js | US | text | 773 b | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/3Z/H/cj,nj/285f1e47/746833cb.js | US | text | 395 b | whitelisted |
3140 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/2Y/1X/cj,nj/4c7364c5/40e1b425.js | US | text | 816 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2848 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
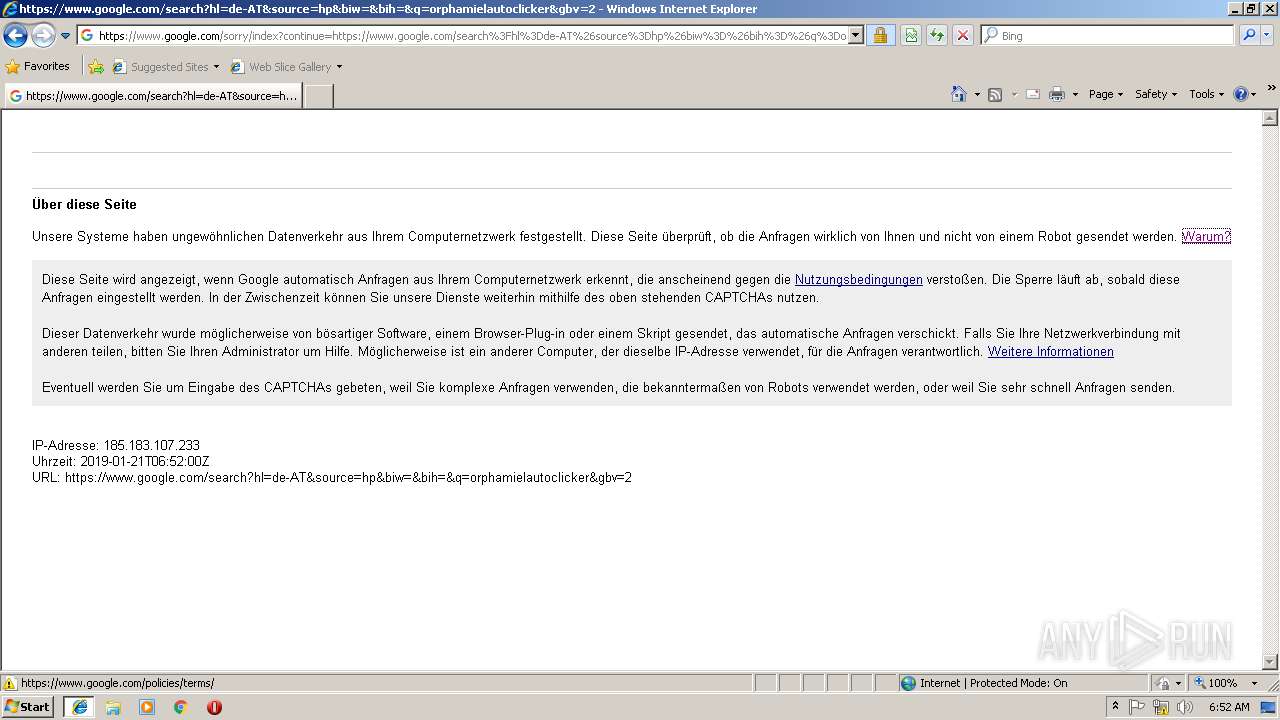
3140 | iexplore.exe | 216.105.38.13:443 | downloads.sourceforge.net | American Internet Services, LLC. | US | malicious |
3140 | iexplore.exe | 216.58.210.14:80 | — | Google Inc. | US | whitelisted |
3140 | iexplore.exe | 172.217.18.100:80 | www.google.com | Google Inc. | US | whitelisted |
3140 | iexplore.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
2848 | iexplore.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
3140 | iexplore.exe | 216.58.206.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3140 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3140 | iexplore.exe | 2.16.186.88:80 | a4.bing.com | Akamai International B.V. | — | whitelisted |
3140 | iexplore.exe | 52.231.32.10:80 | e8a053f43fd56a0c4c4760a07d5cce7b.clo.footprintdns.com | Microsoft Corporation | KR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
downloads.sourceforge.net |
| whitelisted |
www.google.com |
| malicious |
www.gstatic.com |
| whitelisted |
bing.com |
| whitelisted |
login.live.com |
| whitelisted |
a4.bing.com |
| whitelisted |
02d69ed4c227d80b4de541d1e86cdf66.clo.footprintdns.com |
| unknown |
d1661d77dfdd42a891df2300fa5edeb8.clo.footprintdns.com |
| suspicious |
e8a053f43fd56a0c4c4760a07d5cce7b.clo.footprintdns.com |
| unknown |