| URL: | https://pixeldra.in/api/download/lZnJtk |
| Full analysis: | https://app.any.run/tasks/b6170d07-4021-410e-9da2-8b144a9a4e59 |
| Verdict: | Malicious activity |
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 31, 2019, 01:52:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 71CC618D2BED7A9C1034B07FBB4C2AB5 |
| SHA1: | 6CCC5DB8A7BE13FB5EBC6F60F40591891F0D7B2C |
| SHA256: | 4F9A5FB75EBD249A2A7104B8B14711B433A6A6185D0EB835A4A61FB34B4E749D |
| SSDEEP: | 3:N8Ici2AEki:2IEAu |
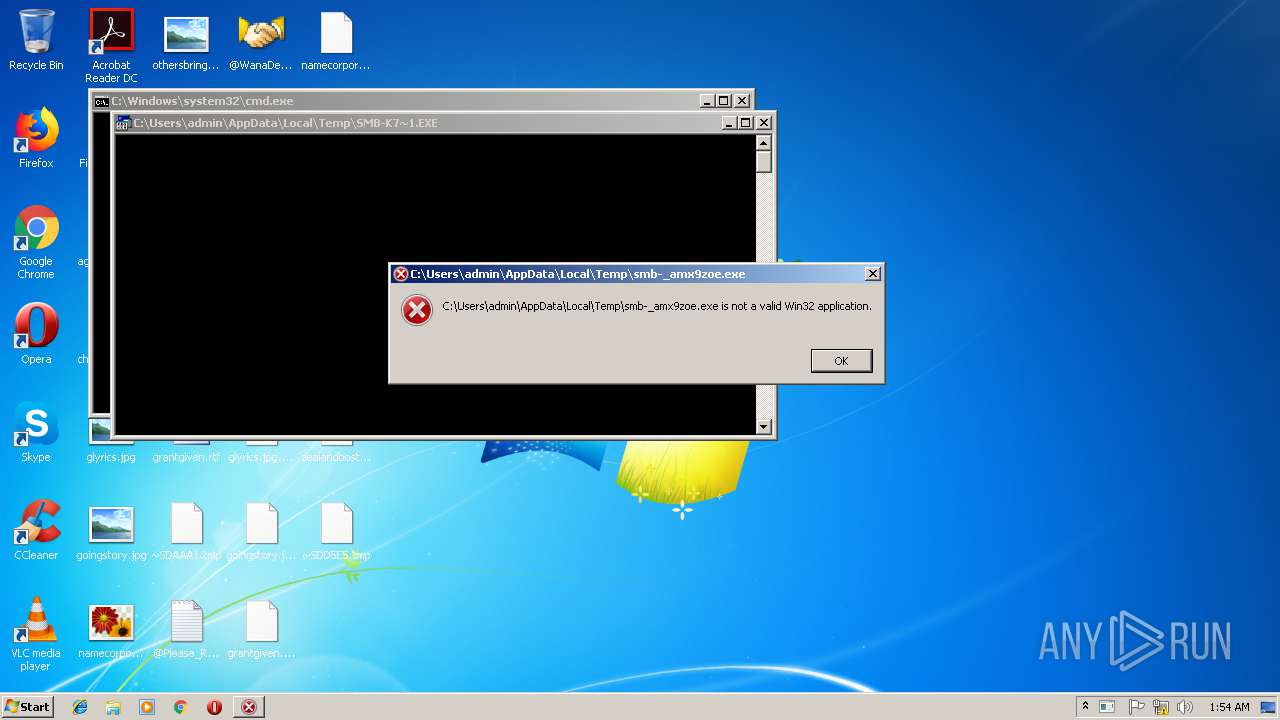
MALICIOUS
Application was dropped or rewritten from another process
- cf8533849ee5e82023ad7adbdbd6543cb6db596c53048b1a0c00b3643a72db30.exe (PID: 2568)
- 32f24601153be0885f11d62e0a8a2f0280a2034fc981d8184180c5d3b1b9e8cf.exe (PID: 3364)
- mssecsvc.exe (PID: 2756)
- mssecsvc.exe (PID: 2452)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
- tasksche.exe (PID: 3252)
- 8200755cbedd6f15eecd8207eba534709a01957b172d7a051b9cc4769ddbf233.exe (PID: 3820)
- 02ca4397da55b3175aaa1ad2c99981e792f66151.exe (PID: 2444)
- taskdl.exe (PID: 3212)
- 4c1dc737915d76b7ce579abddaba74ead6fdb5b519a1ea45308b8c49b950655c (1).exe (PID: 3092)
- grandcab.exe (PID: 312)
- NsCpuCNMiner32.exe (PID: 3956)
- 86e0eac8c5ce70c4b839ef18af5231b5f92e292b81e440193cdbdc7ed108049f.exe (PID: 2532)
WANNACRY was detected
- mssecsvc.exe (PID: 2452)
- mssecsvc.exe (PID: 2756)
Actions looks like stealing of personal data
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
Dropped file may contain instructions of ransomware
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
Connects to CnC server
- 8200755cbedd6f15eecd8207eba534709a01957b172d7a051b9cc4769ddbf233.exe (PID: 3820)
Writes file to Word startup folder
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
GandCrab keys found
- grandcab.exe (PID: 312)
Modifies files in Chrome extension folder
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
Looks like application has launched a miner
- 02ca4397da55b3175aaa1ad2c99981e792f66151.exe (PID: 2444)
- cmd.exe (PID: 3020)
Changes the autorun value in the registry
- reg.exe (PID: 2868)
Low-level write access rights to disk partition
- 4c1dc737915d76b7ce579abddaba74ead6fdb5b519a1ea45308b8c49b950655c (1).exe (PID: 3092)
SUSPICIOUS
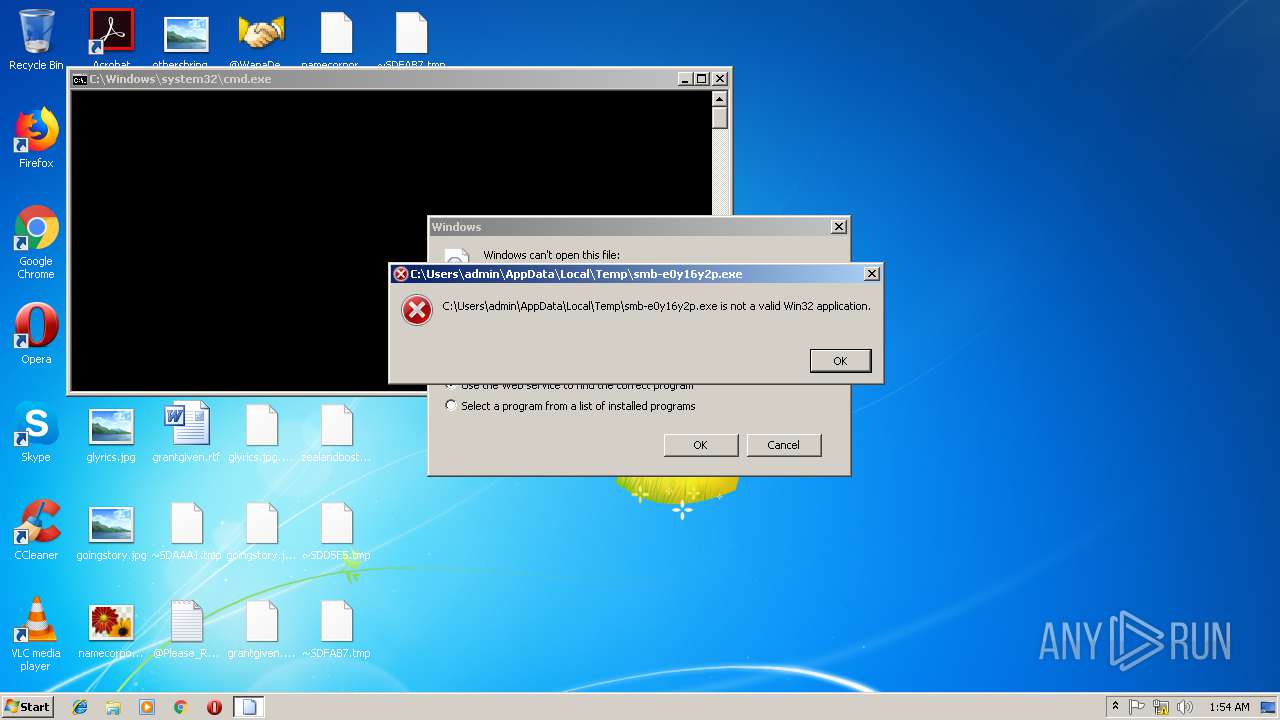
Executable content was dropped or overwritten
- HorridReap.exe (PID: 2488)
- cf8533849ee5e82023ad7adbdbd6543cb6db596c53048b1a0c00b3643a72db30.exe (PID: 2568)
- mssecsvc.exe (PID: 2452)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
- 02ca4397da55b3175aaa1ad2c99981e792f66151.exe (PID: 2444)
Uses ATTRIB.EXE to modify file attributes
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
Uses ICACLS.EXE to modify access control list
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
Changes tracing settings of the file or console
- 32f24601153be0885f11d62e0a8a2f0280a2034fc981d8184180c5d3b1b9e8cf.exe (PID: 3364)
Creates files in the Windows directory
- mssecsvc.exe (PID: 2756)
- mssecsvc.exe (PID: 2452)
Creates files in the user directory
- mssecsvc.exe (PID: 2452)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
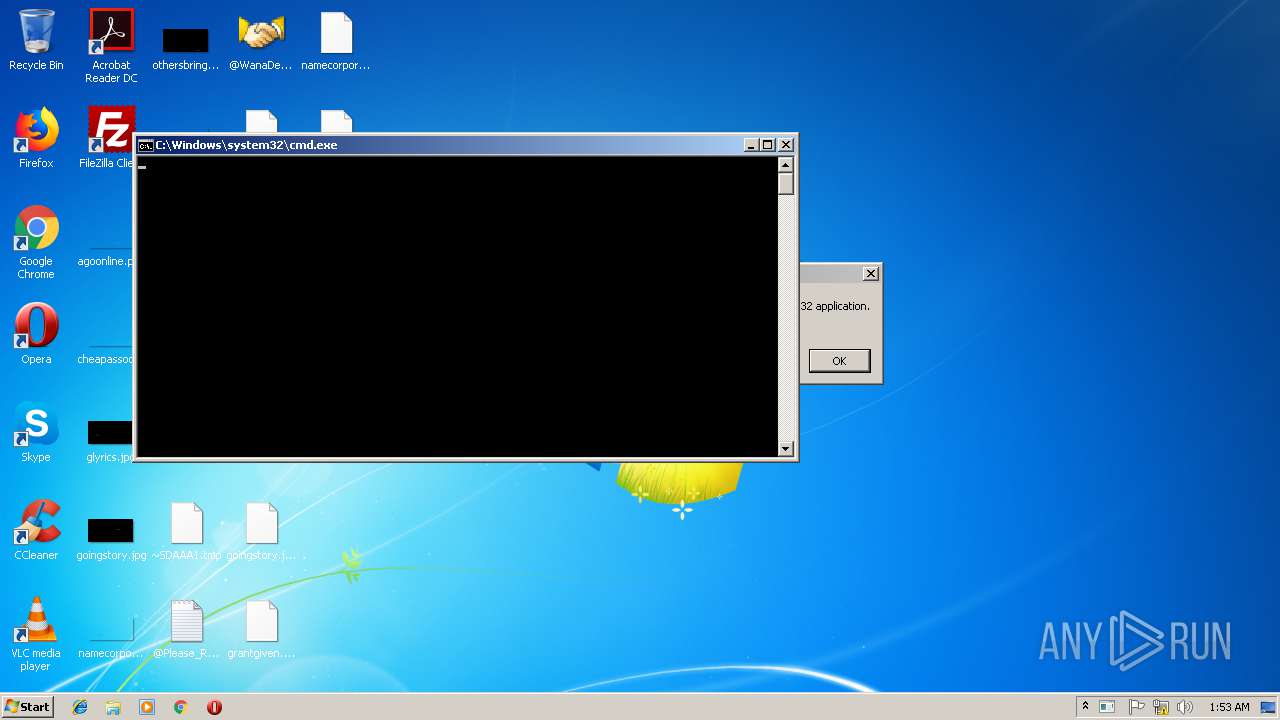
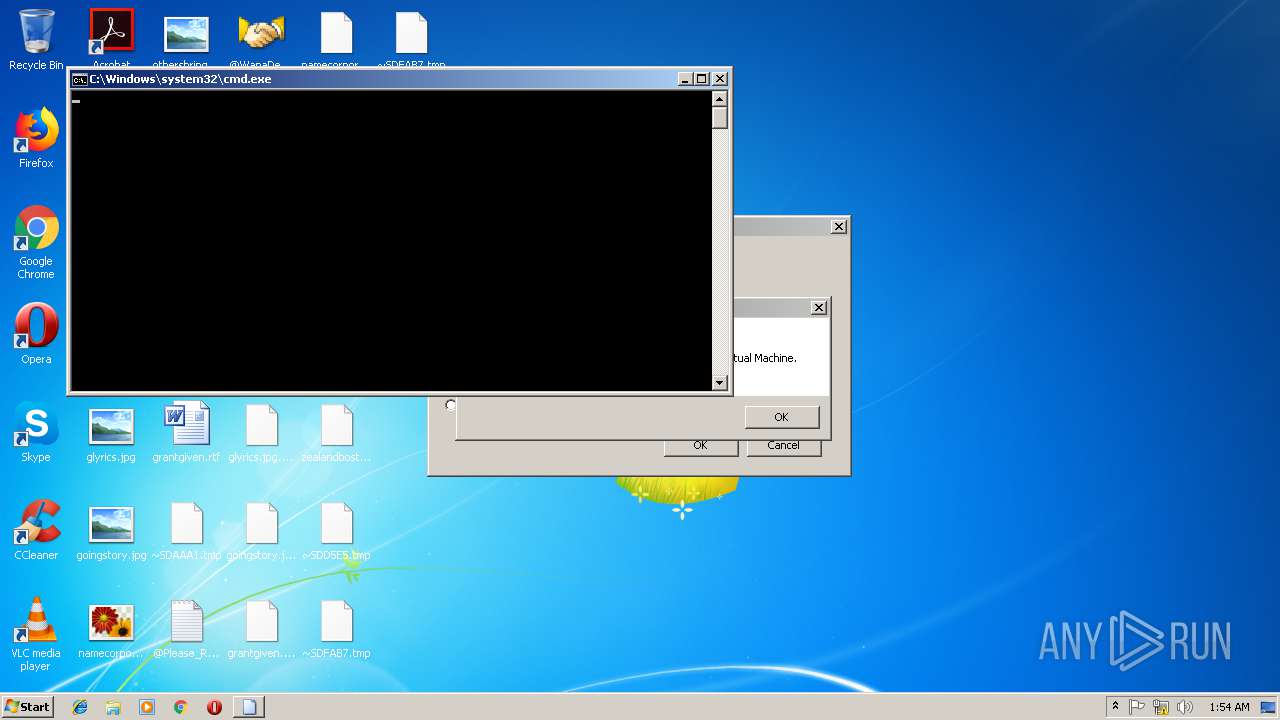
Starts CMD.EXE for commands execution
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
- 8200755cbedd6f15eecd8207eba534709a01957b172d7a051b9cc4769ddbf233.exe (PID: 3820)
- 02ca4397da55b3175aaa1ad2c99981e792f66151.exe (PID: 2444)
Creates files like Ransomware instruction
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
Executes scripts
- cmd.exe (PID: 3768)
Starts SC.EXE for service management
- cmd.exe (PID: 2504)
- cmd.exe (PID: 3968)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1044)
- cmd.exe (PID: 2784)
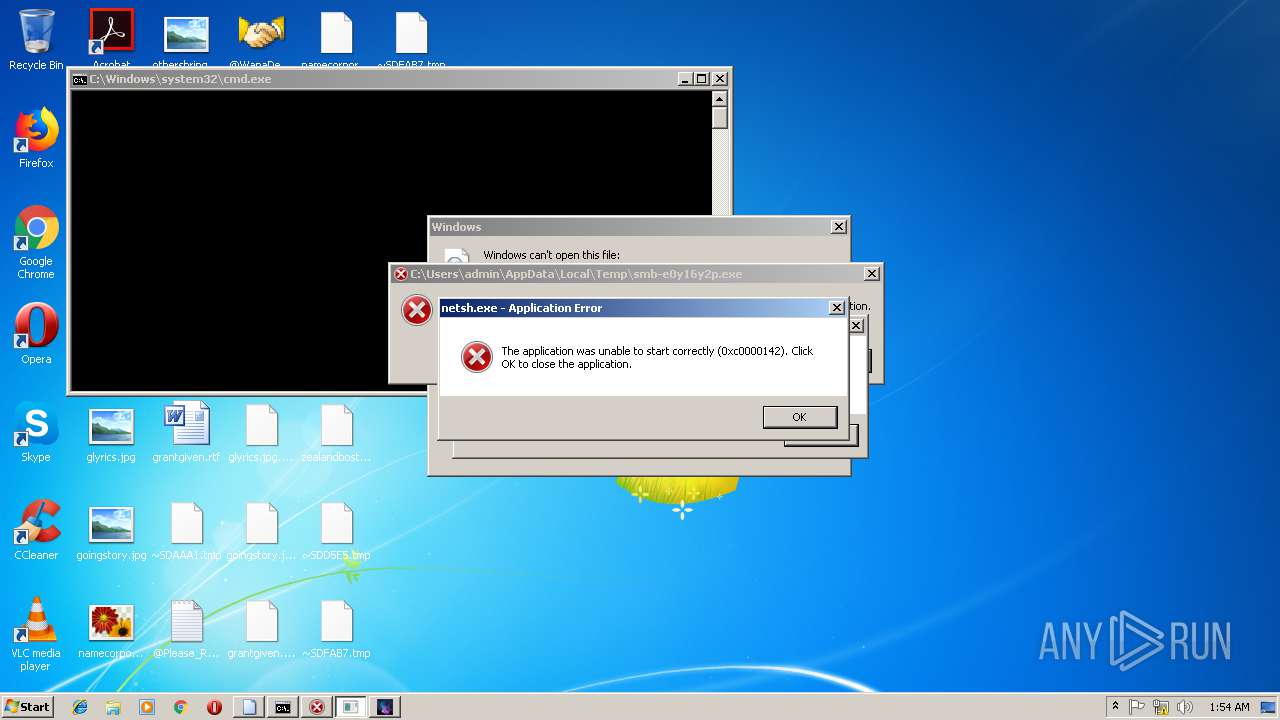
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 2600)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 3268)
- cmd.exe (PID: 3172)
Executes application which crashes
- HorridReap.exe (PID: 2488)
Uses RUNDLL32.EXE to load library
- HorridReap.exe (PID: 2488)
Dropped object may contain URLs of mainers pools
- cmd.exe (PID: 3216)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3032)
Low-level read access rights to disk partition
- 4c1dc737915d76b7ce579abddaba74ead6fdb5b519a1ea45308b8c49b950655c (1).exe (PID: 3092)
Creates files in the program directory
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
INFO
Application launched itself
- chrome.exe (PID: 2996)
Reads settings of System Certificates
- chrome.exe (PID: 2996)
Reads Internet Cache Settings
- chrome.exe (PID: 2996)
Dropped object may contain TOR URL's
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
- HorridReap.exe (PID: 2488)
Creates files in the user directory
- chrome.exe (PID: 2996)
Dropped object may contain URL to Tor Browser
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
Dropped object may contain Bitcoin addresses
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe (PID: 3728)
- HorridReap.exe (PID: 2488)
Application was crashed
- grandcab.exe (PID: 312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
104
Monitored processes
49
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Users\admin\AppData\Local\Temp\grandcab.exe" | C:\Users\admin\AppData\Local\Temp\grandcab.exe | HorridReap.exe | ||||||||||||
User: admin Company: HWorks Integrity Level: HIGH Description: Safemode Mentions Coms Exit code: 0 Version: 5.3.38.4 Modules
| |||||||||||||||
| 340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=896,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=33FF2C0AC3CCF2B4F5A9F9DE1C426F58 --mojo-platform-channel-handle=988 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 932 | attrib +h . | C:\Windows\system32\attrib.exe | — | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | C:\Windows\system32\cmd.exe /c taskkill /f /im mmc.exe | C:\Windows\system32\cmd.exe | — | 8200755cbedd6f15eecd8207eba534709a01957b172d7a051b9cc4769ddbf233.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1620 | netsh ipsec static add filteraction name=block action=block | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1820 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | HorridReap.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | icacls . /grant Everyone:F /T /C /Q | C:\Windows\system32\icacls.exe | — | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "C:\Users\admin\AppData\Local\Temp\02ca4397da55b3175aaa1ad2c99981e792f66151.exe" | C:\Users\admin\AppData\Local\Temp\02ca4397da55b3175aaa1ad2c99981e792f66151.exe | HorridReap.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2452 | "C:\Users\admin\AppData\Local\Temp\mssecsvc.exe" | C:\Users\admin\AppData\Local\Temp\mssecsvc.exe | HorridReap.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Disk Defragmenter Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2488 | "C:\Users\admin\Downloads\HorridReap.exe" | C:\Users\admin\Downloads\HorridReap.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 494
Read events
1 136
Write events
355
Delete events
3
Modification events
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2996-13193373152926000 |
Value: 259 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2996-13193373152926000 |
Value: 259 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
95
Suspicious files
354
Text files
141
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\74802bb0-60c3-48cc-b75f-0942b928756a.tmp | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\6a57f39b-135f-41da-8cbf-96098558724a.tmp | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\aad43214-8d78-48c4-b0f6-45c3bd96bed0.tmp | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\Downloads\e182e731-583a-4ca6-960e-21f103a4c341.tmp | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\Downloads\Unconfirmed 422674.crdownload | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Translate Ranker Model~RF199754.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
310
DNS requests
19
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3820 | 8200755cbedd6f15eecd8207eba534709a01957b172d7a051b9cc4769ddbf233.exe | GET | 200 | 66.42.108.166:80 | http://08.super5566.com/install/start | US | — | — | malicious |
2444 | 02ca4397da55b3175aaa1ad2c99981e792f66151.exe | GET | 404 | 37.1.216.8:80 | http://hrtests.ru/test.html?1 | DE | html | 1.22 Kb | malicious |
2444 | 02ca4397da55b3175aaa1ad2c99981e792f66151.exe | GET | 404 | 37.1.216.8:80 | http://jobtests.ru/test.html?7 | DE | html | 1.22 Kb | malicious |
2444 | 02ca4397da55b3175aaa1ad2c99981e792f66151.exe | GET | 404 | 37.1.216.8:80 | http://testpsy.ru/test.html?3 | DE | html | 1.22 Kb | malicious |
2444 | 02ca4397da55b3175aaa1ad2c99981e792f66151.exe | GET | 404 | 37.1.216.8:80 | http://profetest.ru/test.html?2 | DE | html | 1.22 Kb | malicious |
2444 | 02ca4397da55b3175aaa1ad2c99981e792f66151.exe | GET | 404 | 37.1.216.8:80 | http://qptest.ru/test.html?5 | DE | html | 1.22 Kb | malicious |
2444 | 02ca4397da55b3175aaa1ad2c99981e792f66151.exe | GET | 404 | 37.1.216.8:80 | http://pstests.ru/test.html?4 | DE | html | 1.22 Kb | malicious |
2756 | mssecsvc.exe | GET | 200 | 104.17.38.137:80 | http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/ | US | html | 607 b | malicious |
2452 | mssecsvc.exe | GET | 200 | 104.17.38.137:80 | http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/ | US | html | 607 b | malicious |
2444 | 02ca4397da55b3175aaa1ad2c99981e792f66151.exe | GET | 200 | 89.111.178.201:80 | http://iqtesti.ru/test.html?8 | RU | html | 2.01 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2996 | chrome.exe | 23.175.0.142:443 | pixeldra.in | Puppet, Inc. | US | unknown |
2996 | chrome.exe | 216.58.210.14:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2996 | chrome.exe | 216.58.206.14:443 | clients4.google.com | Google Inc. | US | whitelisted |
3364 | 32f24601153be0885f11d62e0a8a2f0280a2034fc981d8184180c5d3b1b9e8cf.exe | 98.143.148.47:80 | www.ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com | QuadraNet, Inc | US | unknown |
2756 | mssecsvc.exe | 104.17.38.137:80 | www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com | Cloudflare Inc | US | shared |
2452 | mssecsvc.exe | 104.17.38.137:80 | www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com | Cloudflare Inc | US | shared |
2756 | mssecsvc.exe | 149.187.219.165:445 | — | — | GB | unknown |
2996 | chrome.exe | 172.217.22.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2756 | mssecsvc.exe | 57.53.225.2:445 | — | Societe Internationale de Telecommunications Aeronautiques | BE | unknown |
2756 | mssecsvc.exe | 16.2.10.41:445 | — | Hewlett-Packard Company | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
pixeldra.in |
| suspicious |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
clients4.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com |
| unknown |
www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com |
| malicious |
stafftest.ru |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | A Network Trojan was detected | ET TROJAN Possible WannaCry DNS Lookup 2 |
1056 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Possible WannaCry killswitch URL pattern |
1056 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Possible WannaCry killswitch URL pattern |
2452 | mssecsvc.exe | A Network Trojan was detected | ET TROJAN W32/WannaCry.Ransomware Killswitch Domain HTTP Request 1 |
2452 | mssecsvc.exe | A Network Trojan was detected | ET TROJAN W32/WannaCry.Ransomware Killswitch Domain HTTP Request 2 |
2452 | mssecsvc.exe | A Network Trojan was detected | ET TROJAN W32/WannaCry.Ransomware Killswitch Domain HTTP Request 4 |
2452 | mssecsvc.exe | A Network Trojan was detected | ET TROJAN W32/WannaCry.Ransomware Killswitch Domain HTTP Request 5 |
2756 | mssecsvc.exe | A Network Trojan was detected | ET TROJAN W32/WannaCry.Ransomware Killswitch Domain HTTP Request 1 |
2756 | mssecsvc.exe | A Network Trojan was detected | ET TROJAN W32/WannaCry.Ransomware Killswitch Domain HTTP Request 2 |
2756 | mssecsvc.exe | A Network Trojan was detected | ET TROJAN W32/WannaCry.Ransomware Killswitch Domain HTTP Request 4 |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
8200755cbedd6f15eecd8207eba534709a01957b172d7a051b9cc4769ddbf233.exe | LD: scripts\main.lua: L(083): Startup
|