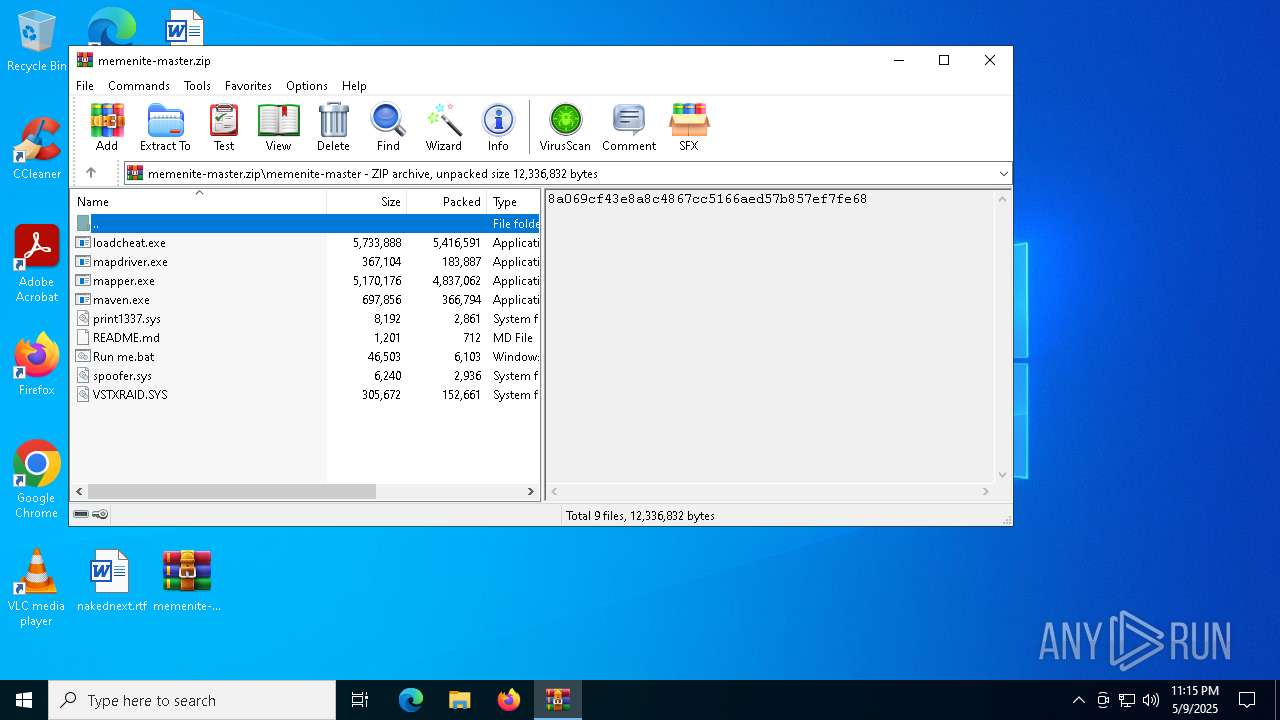
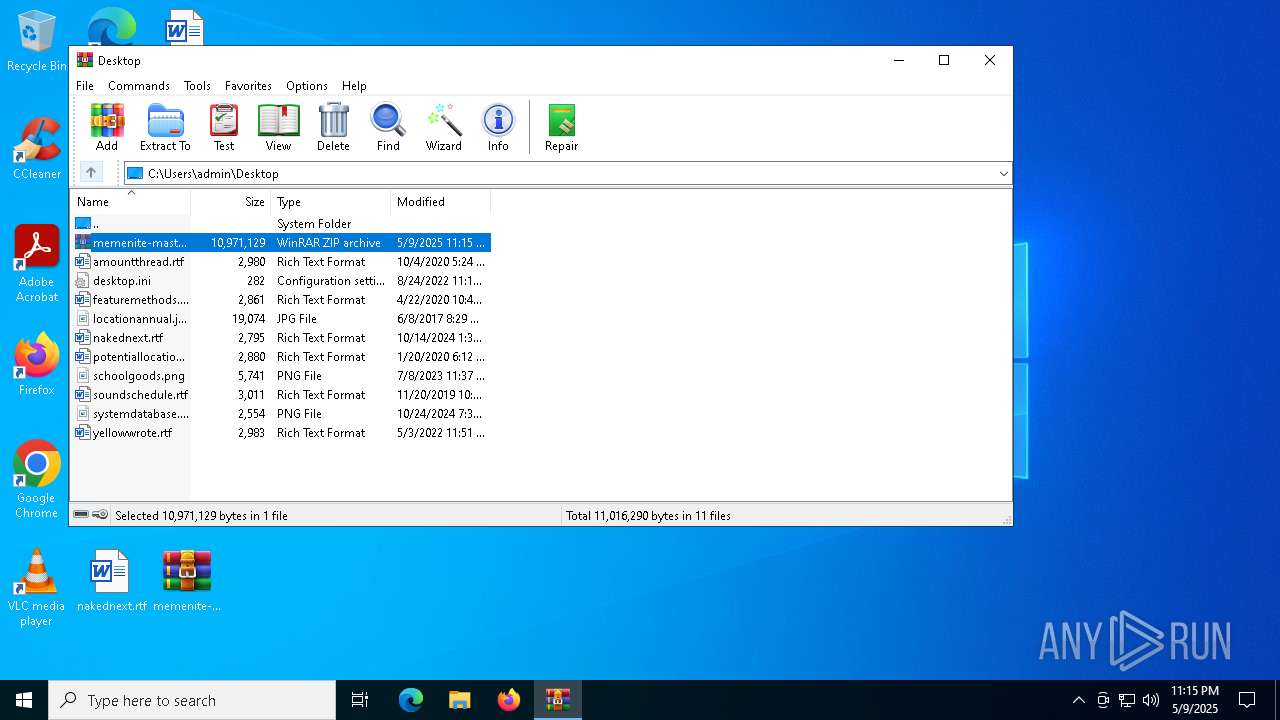
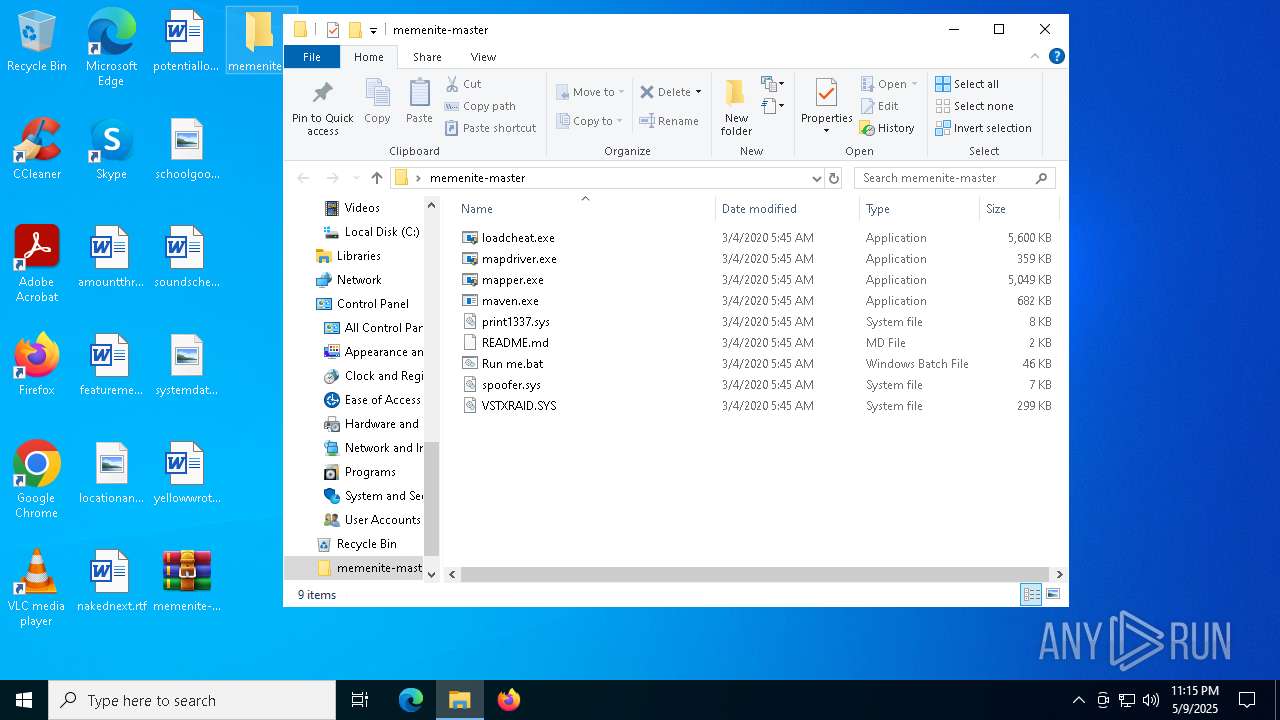
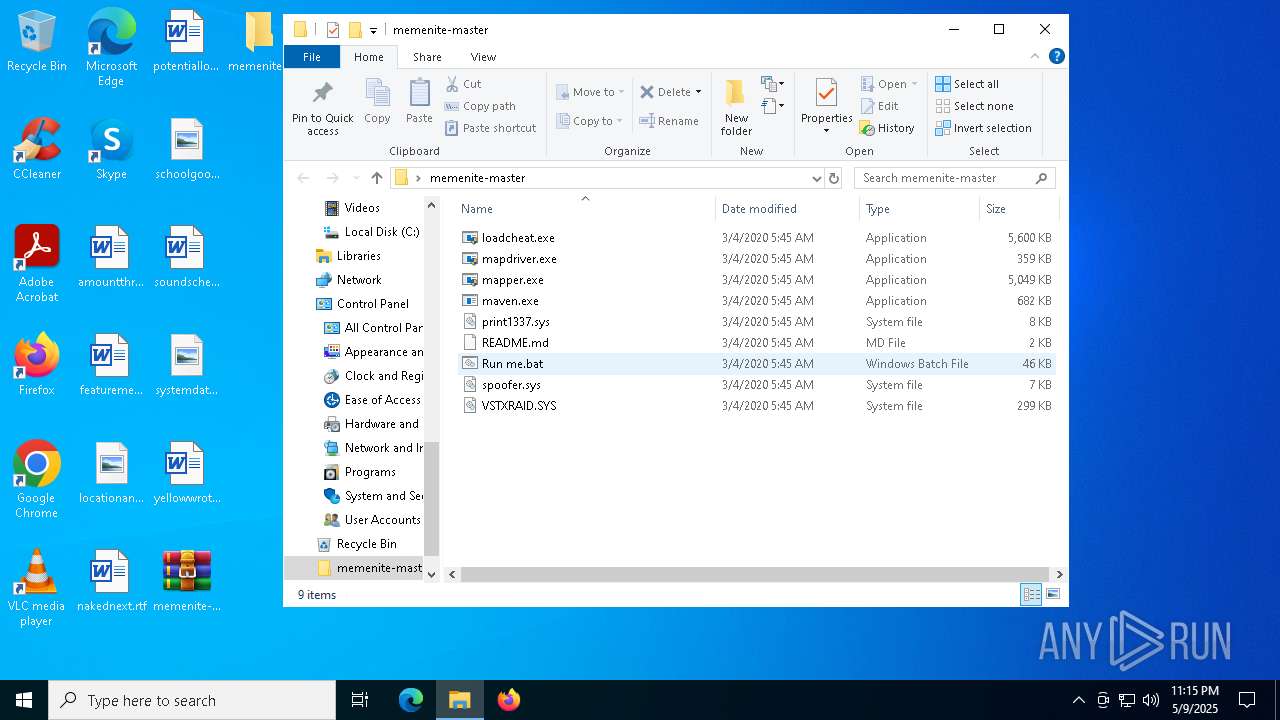
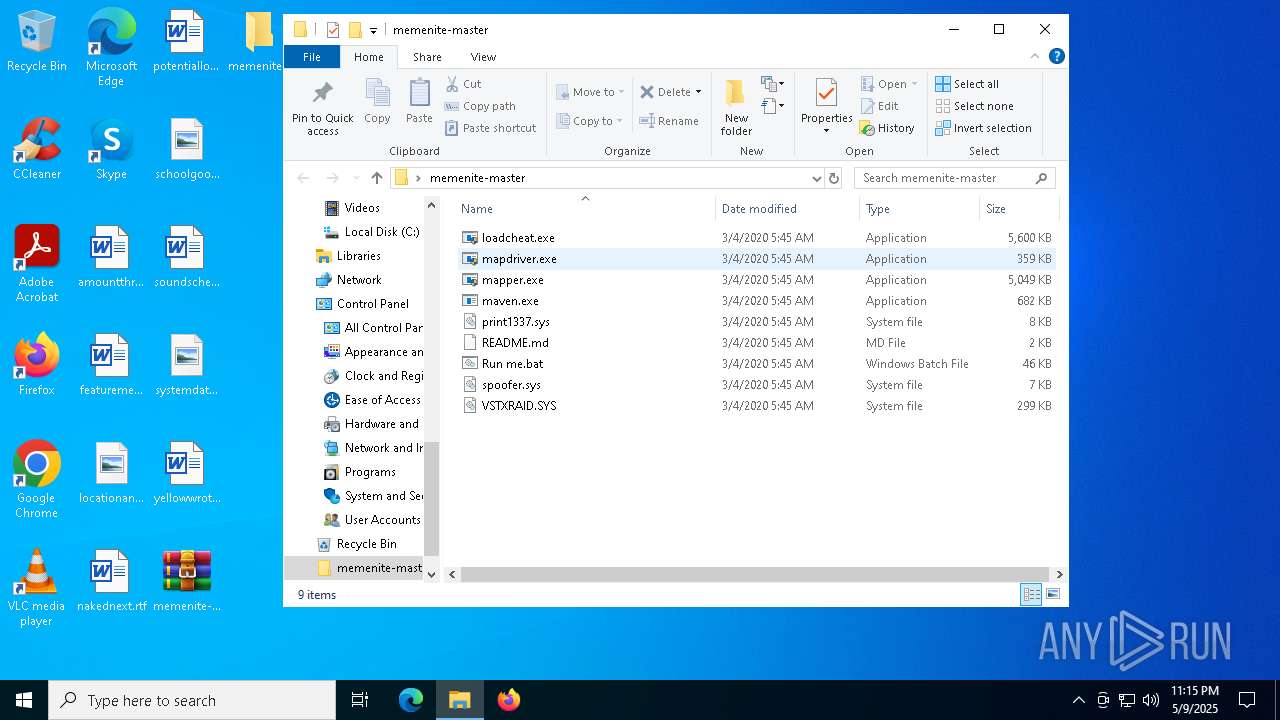
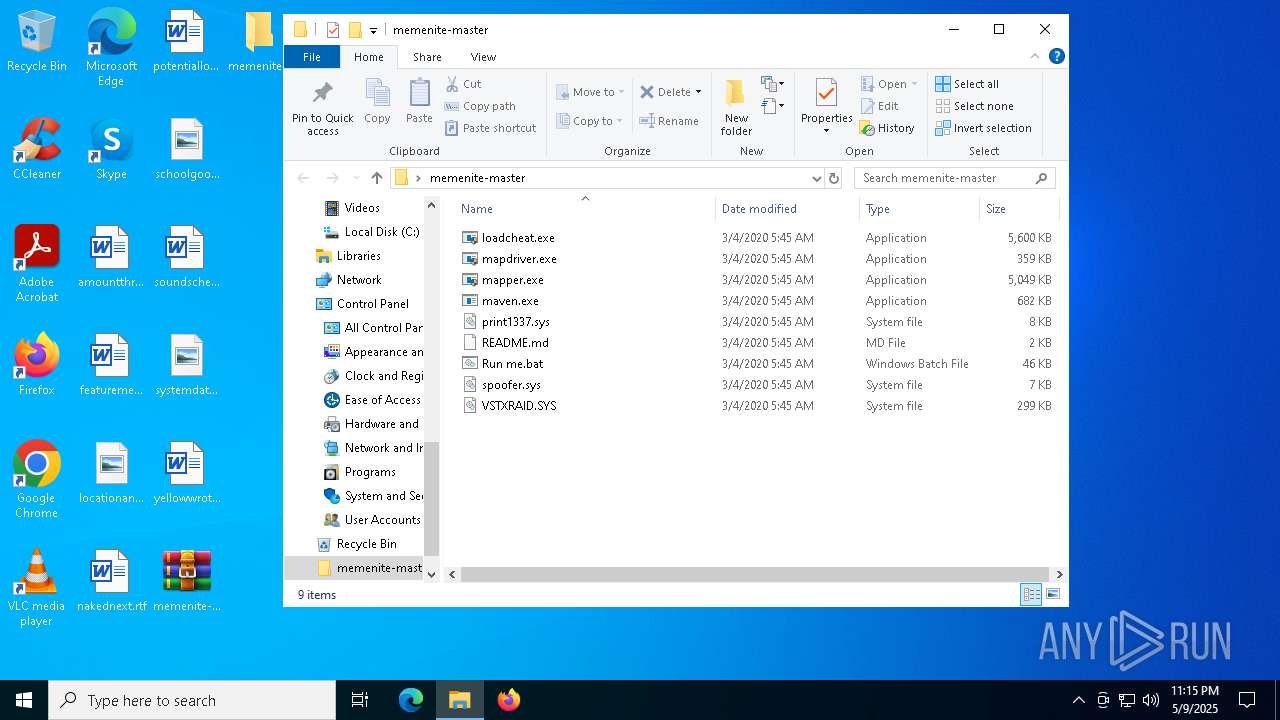
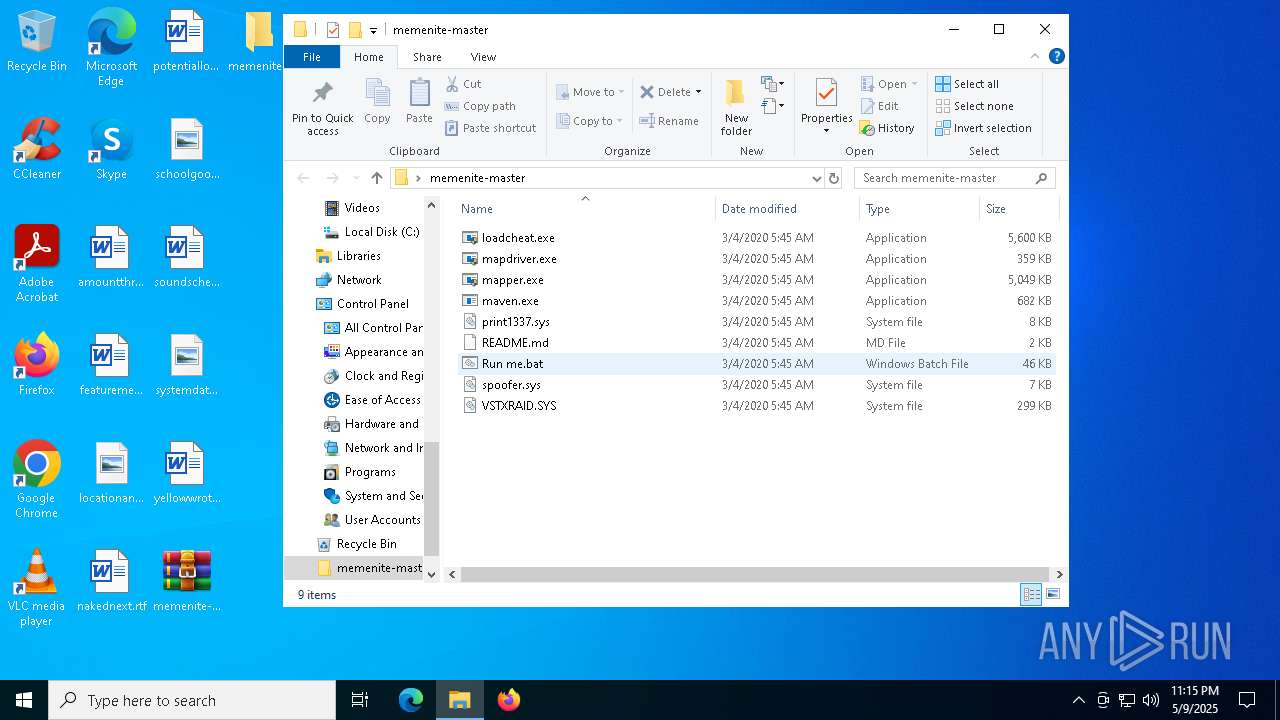
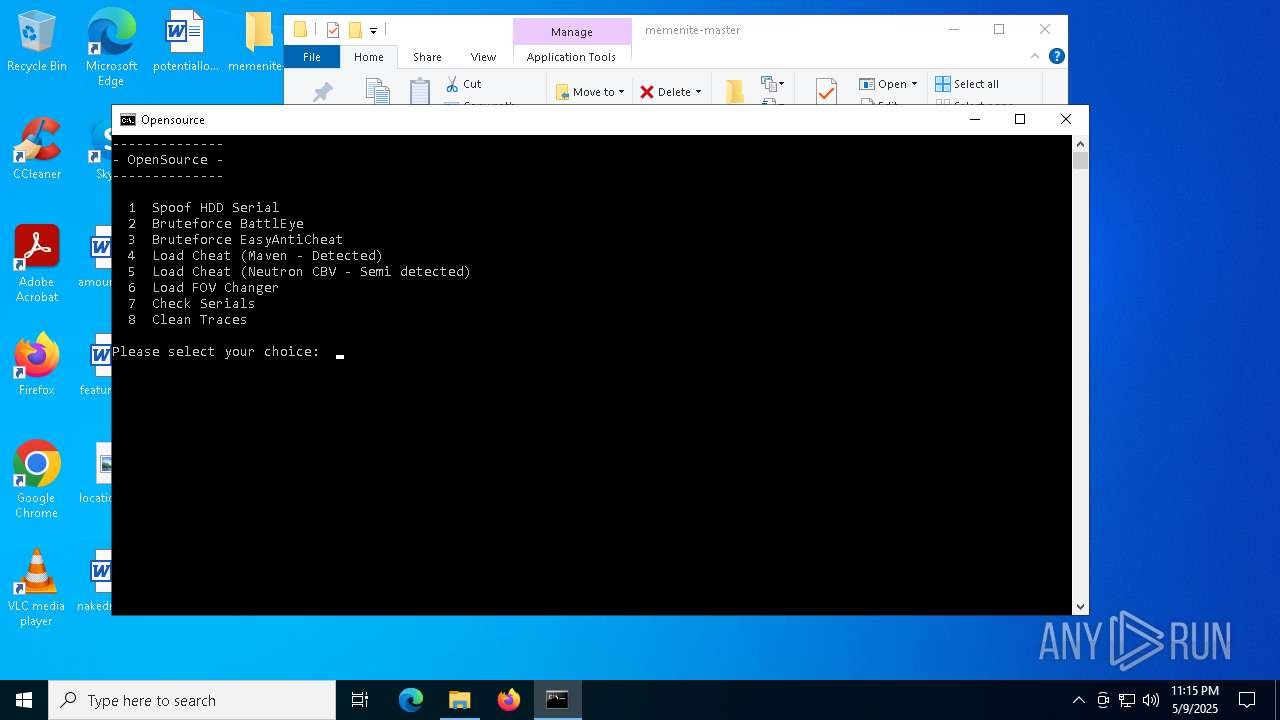
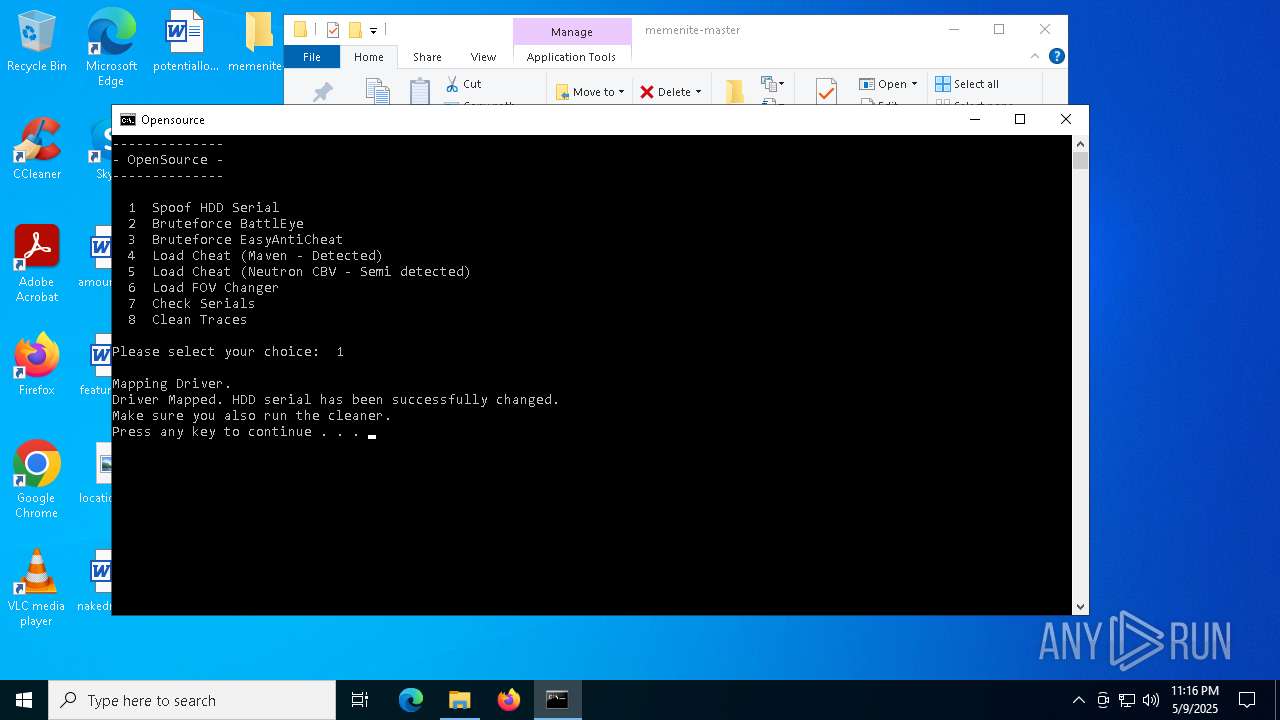
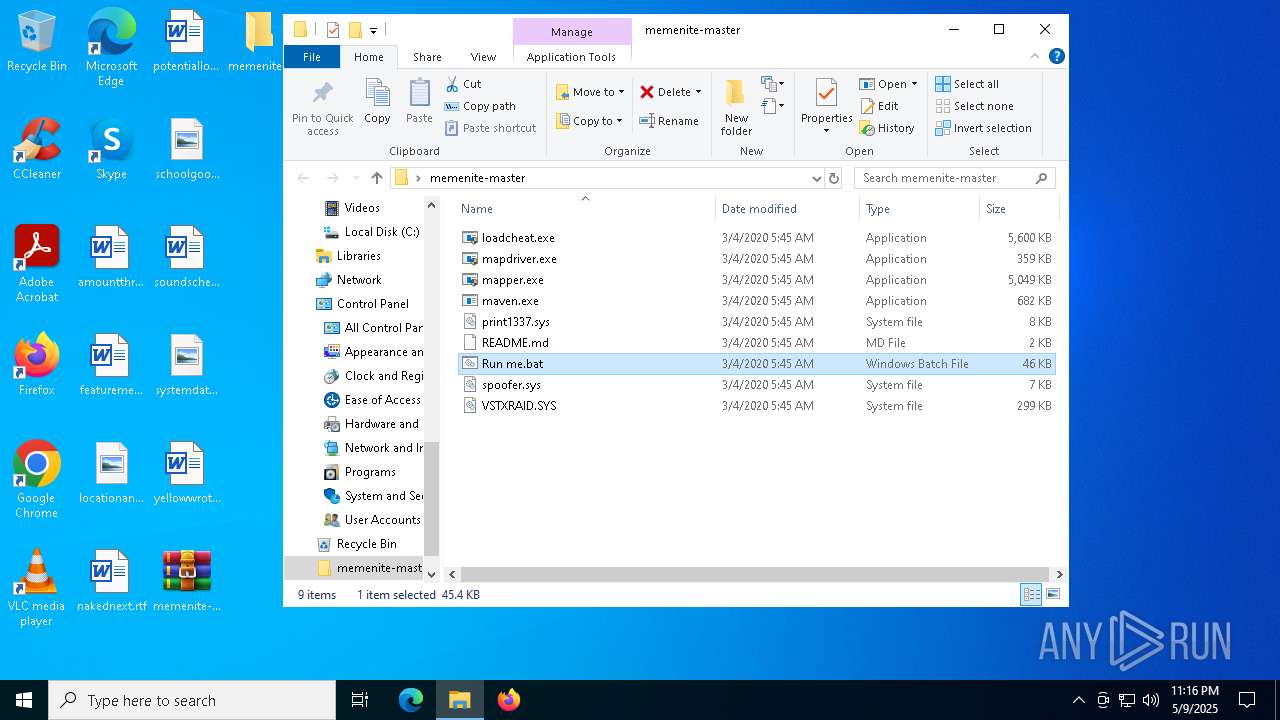
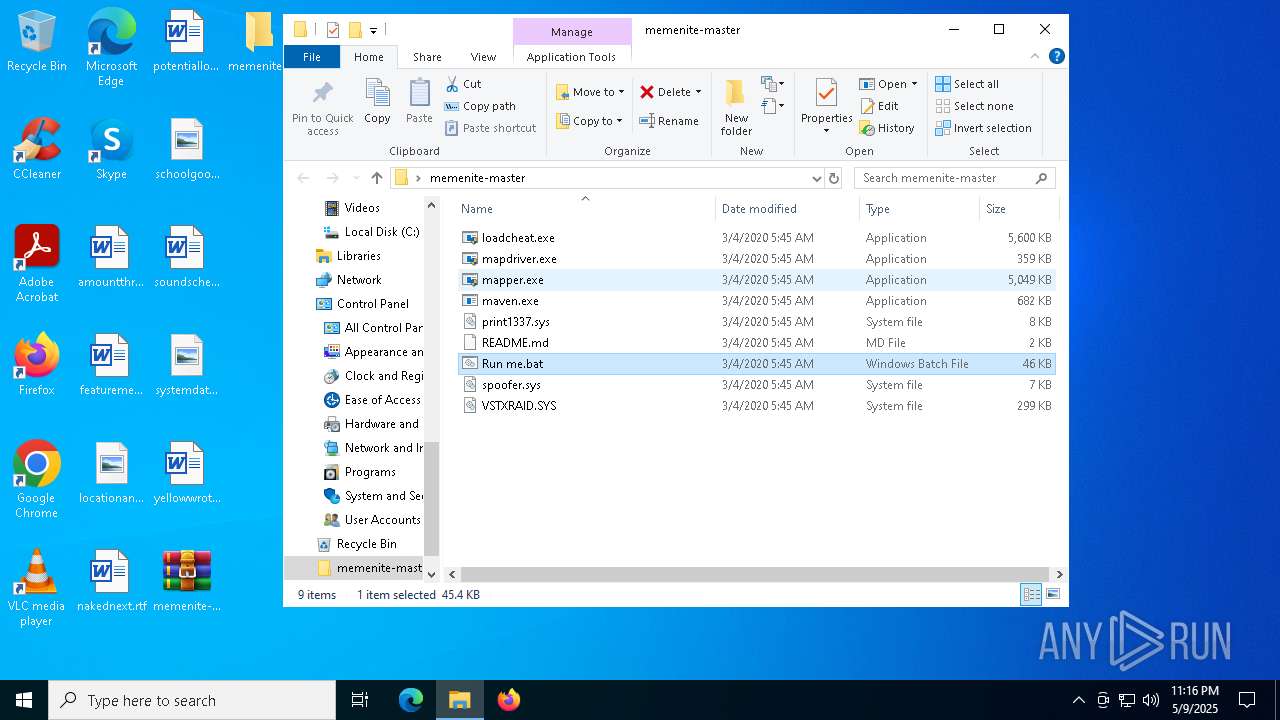
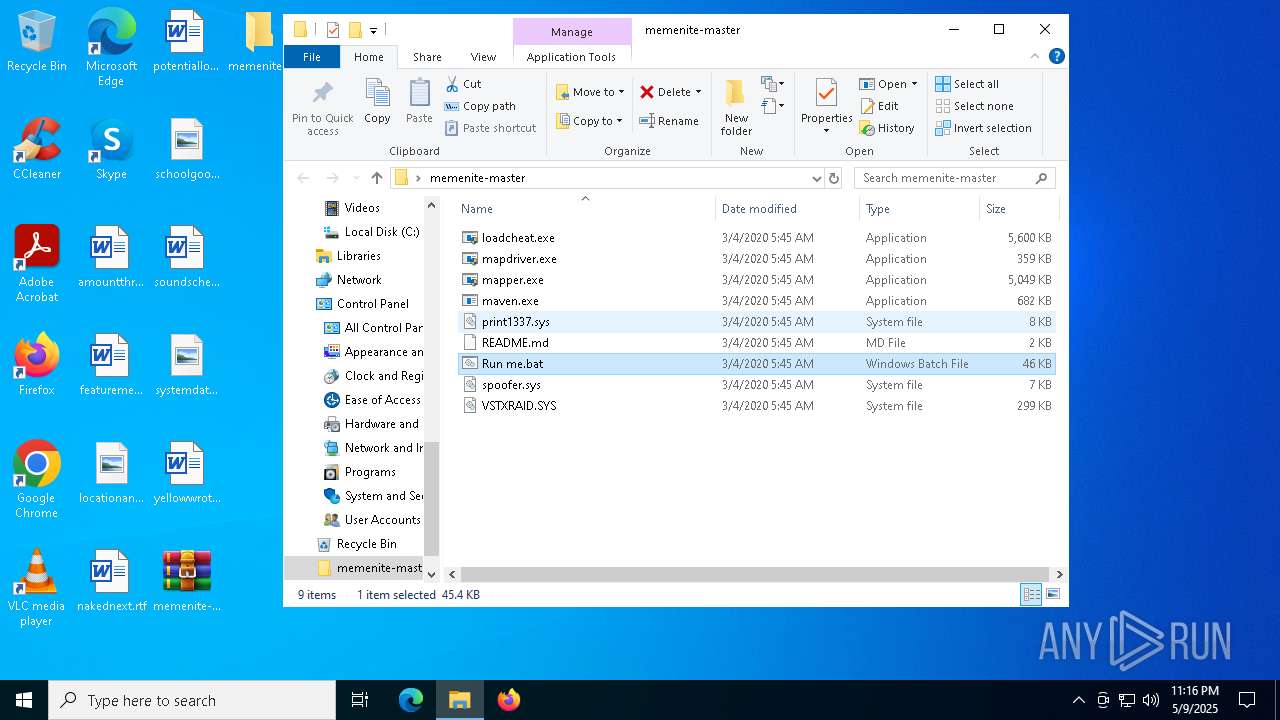
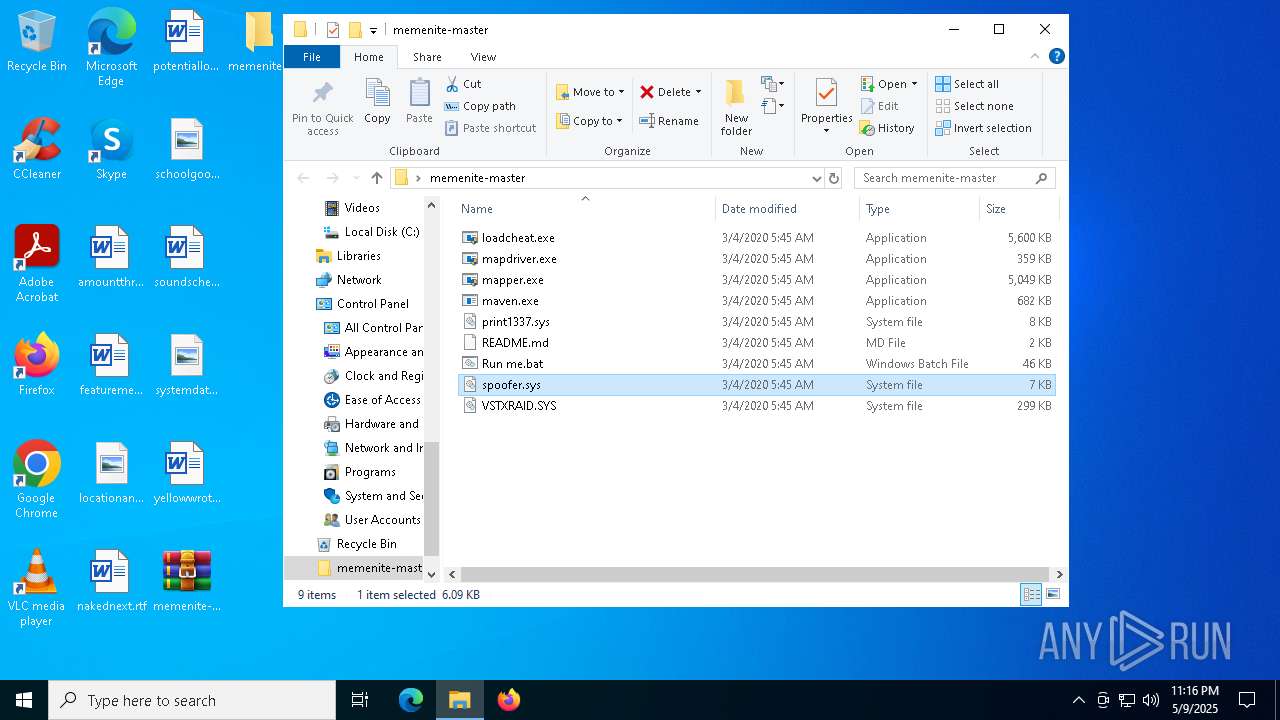
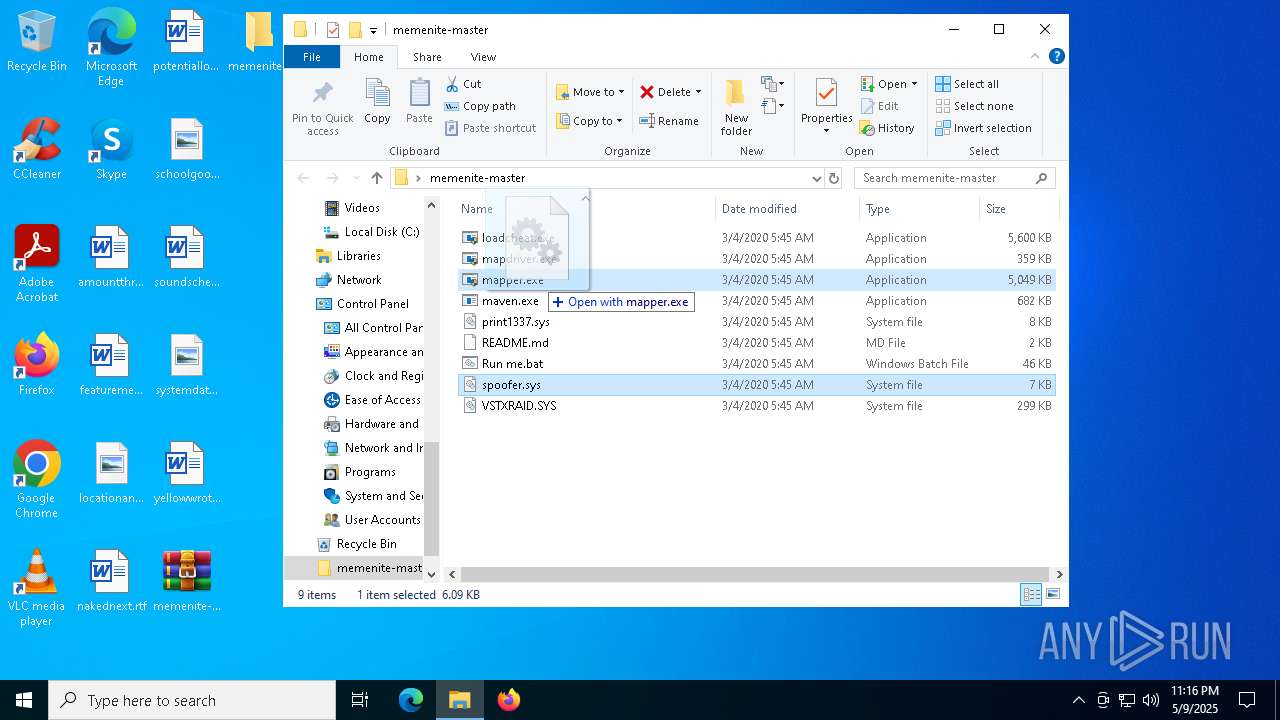
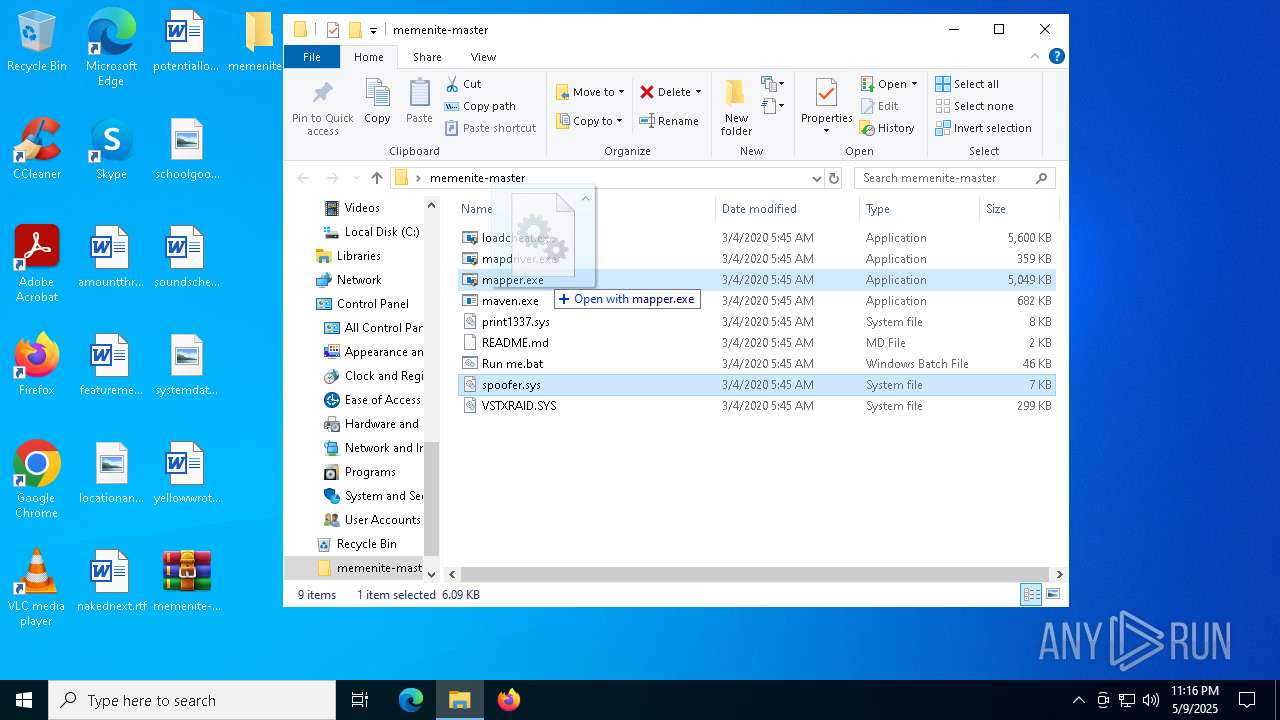
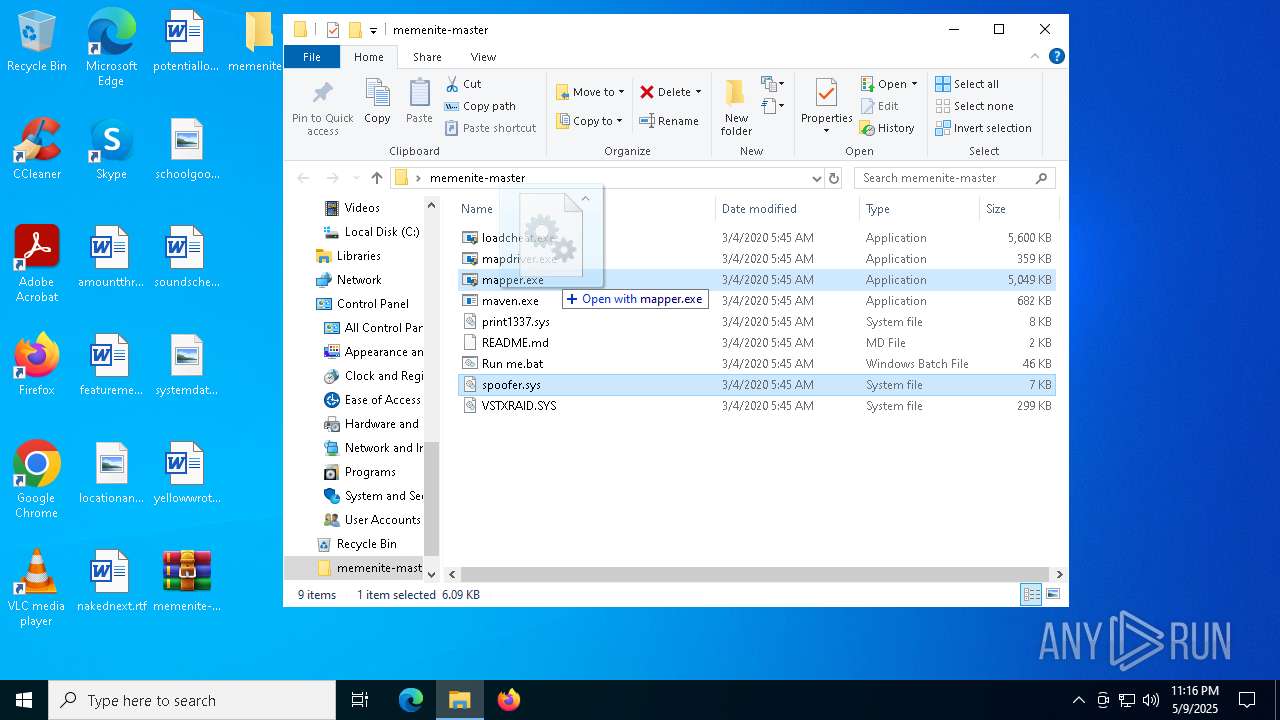
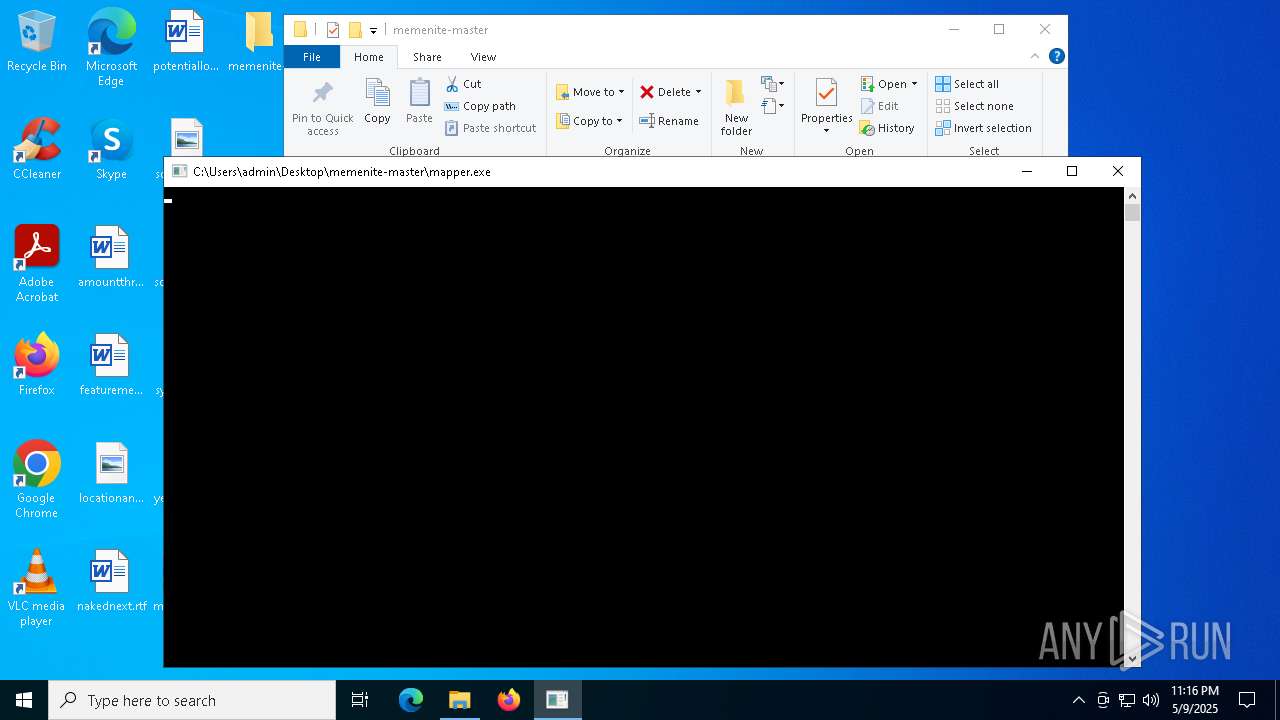
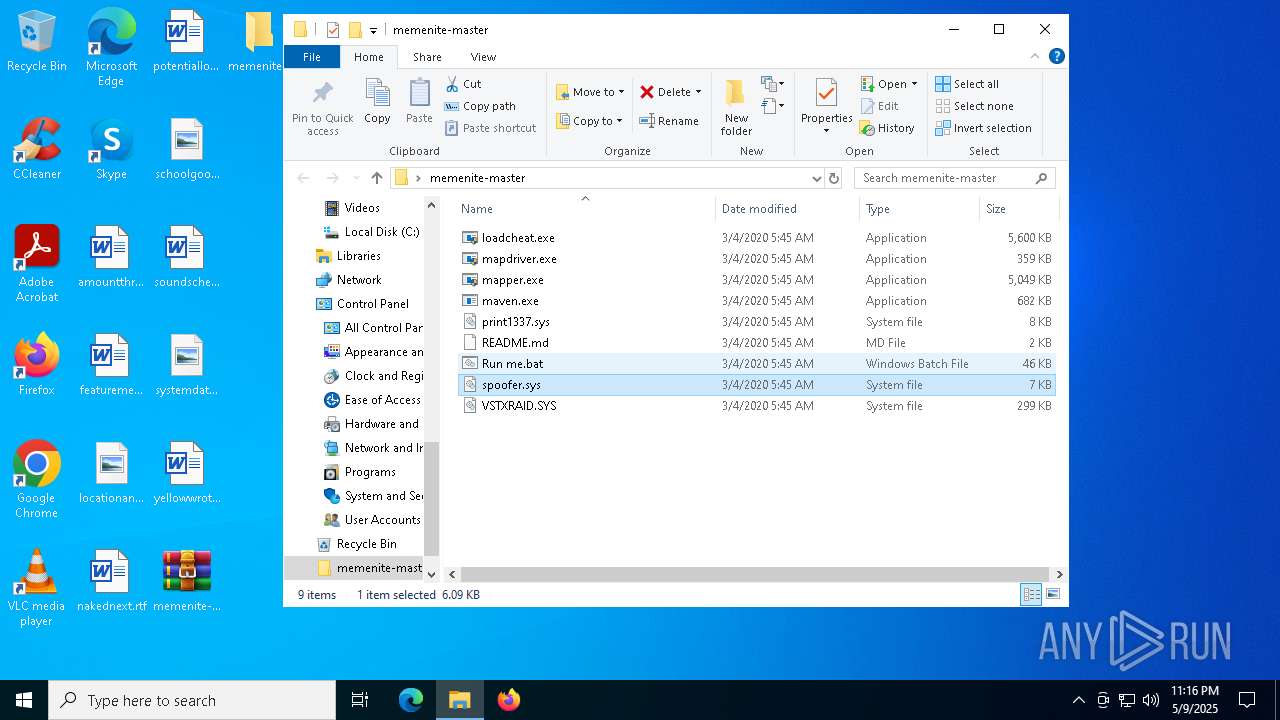
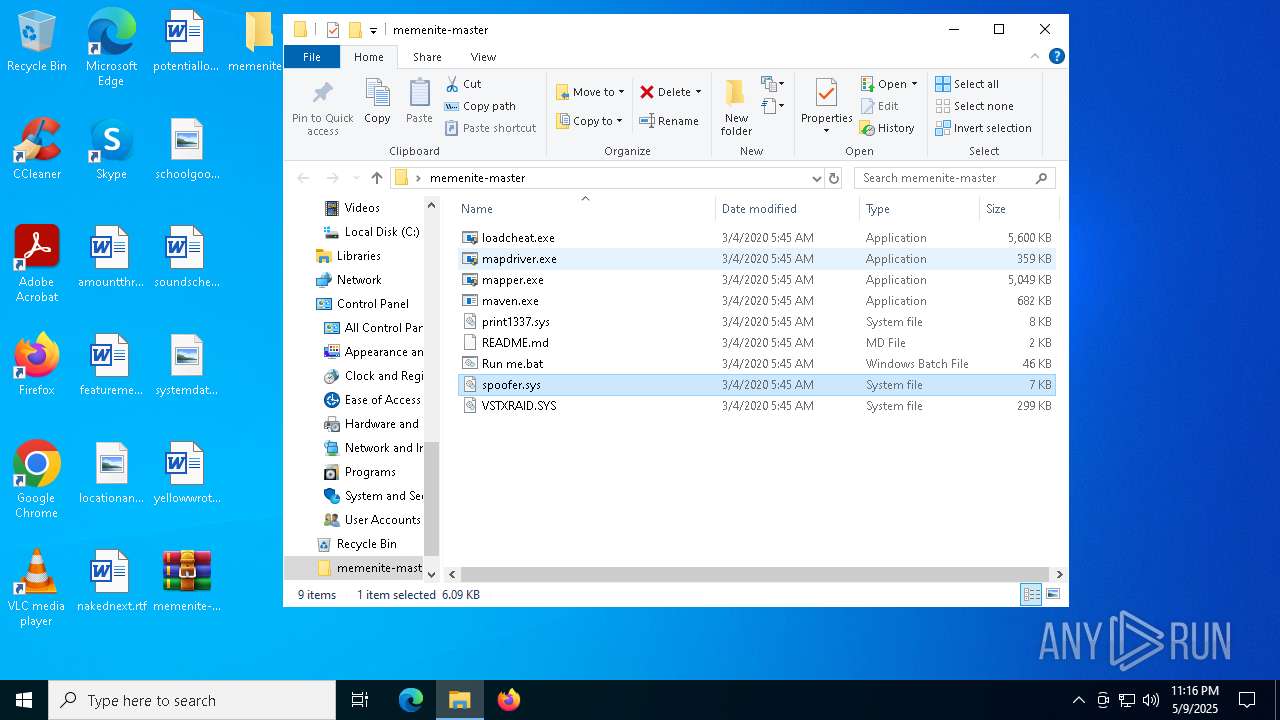
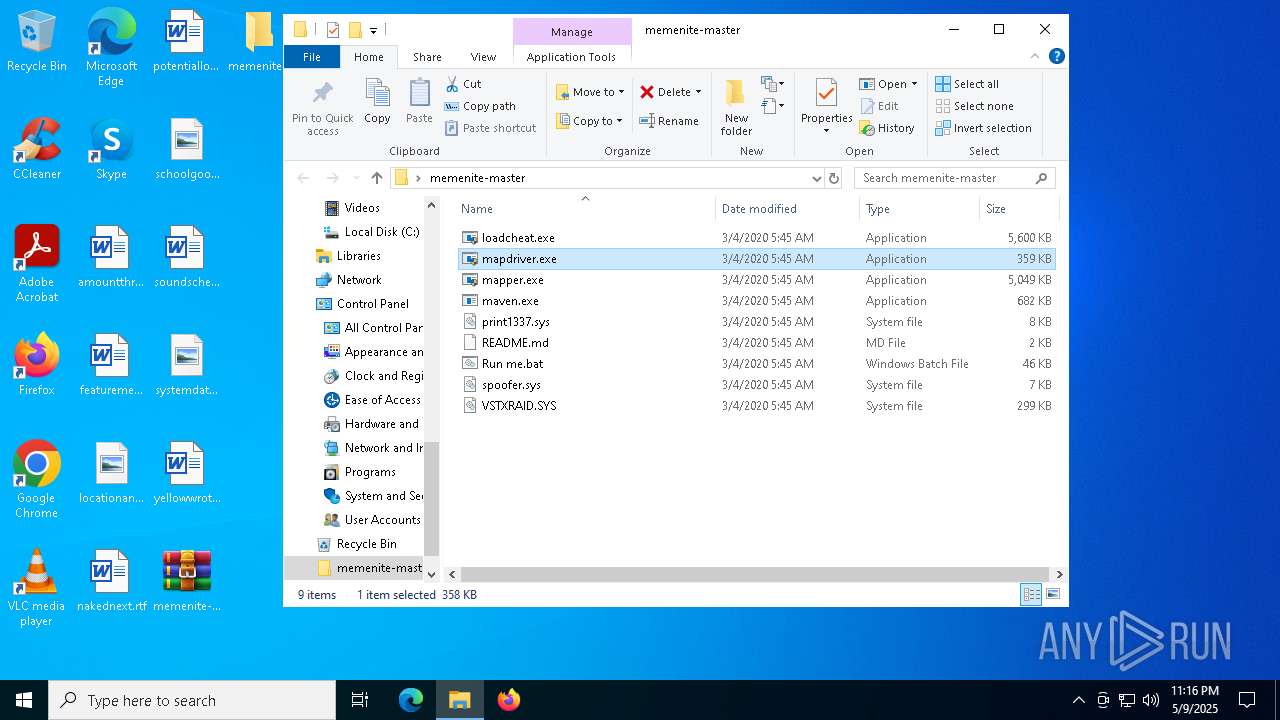
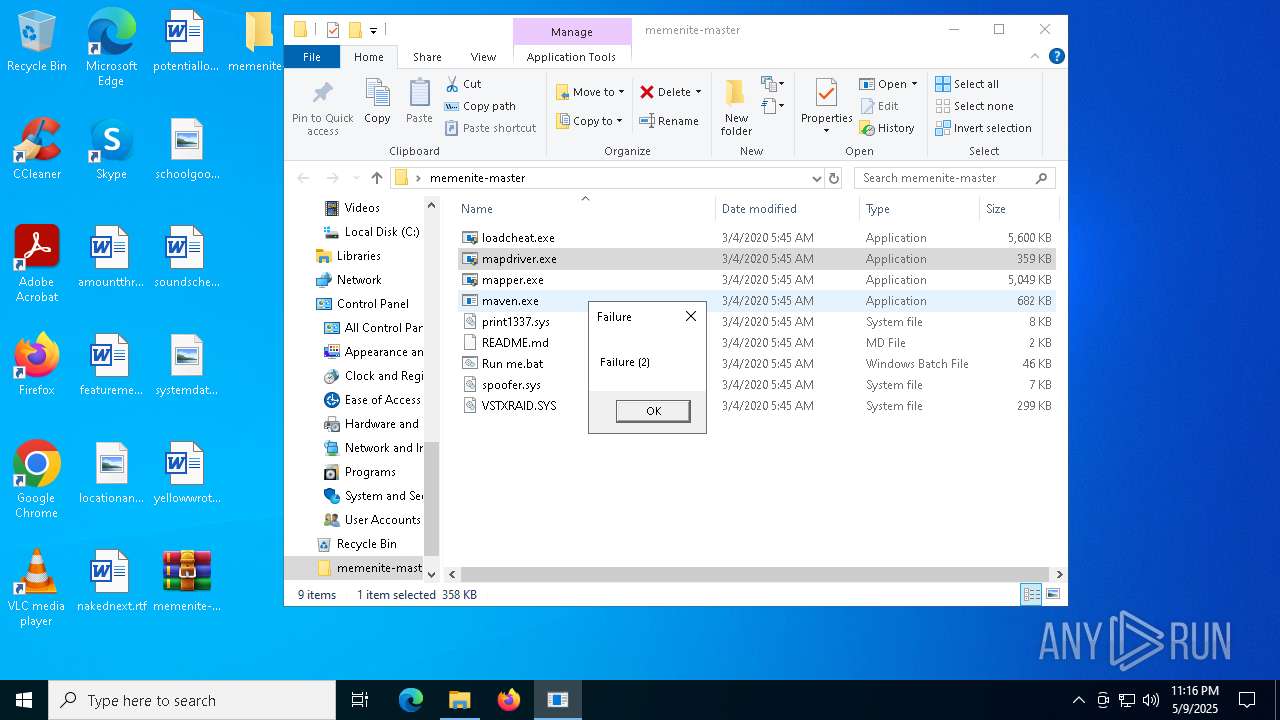
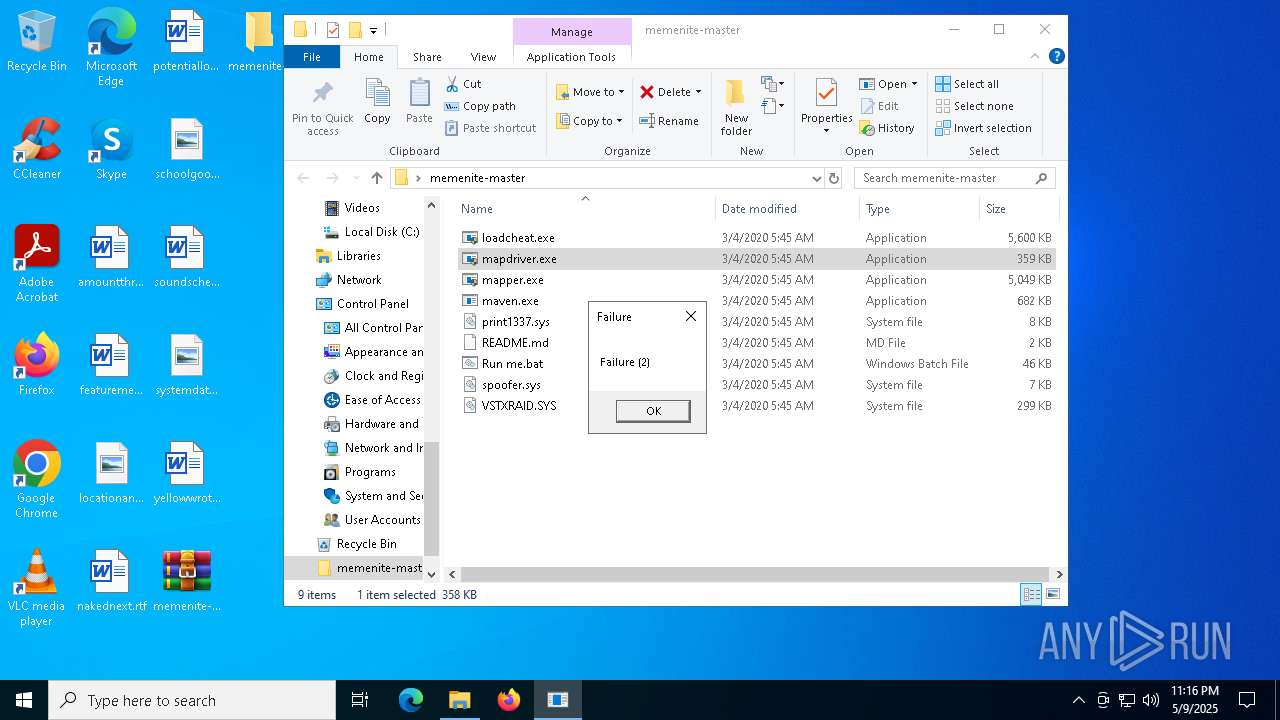
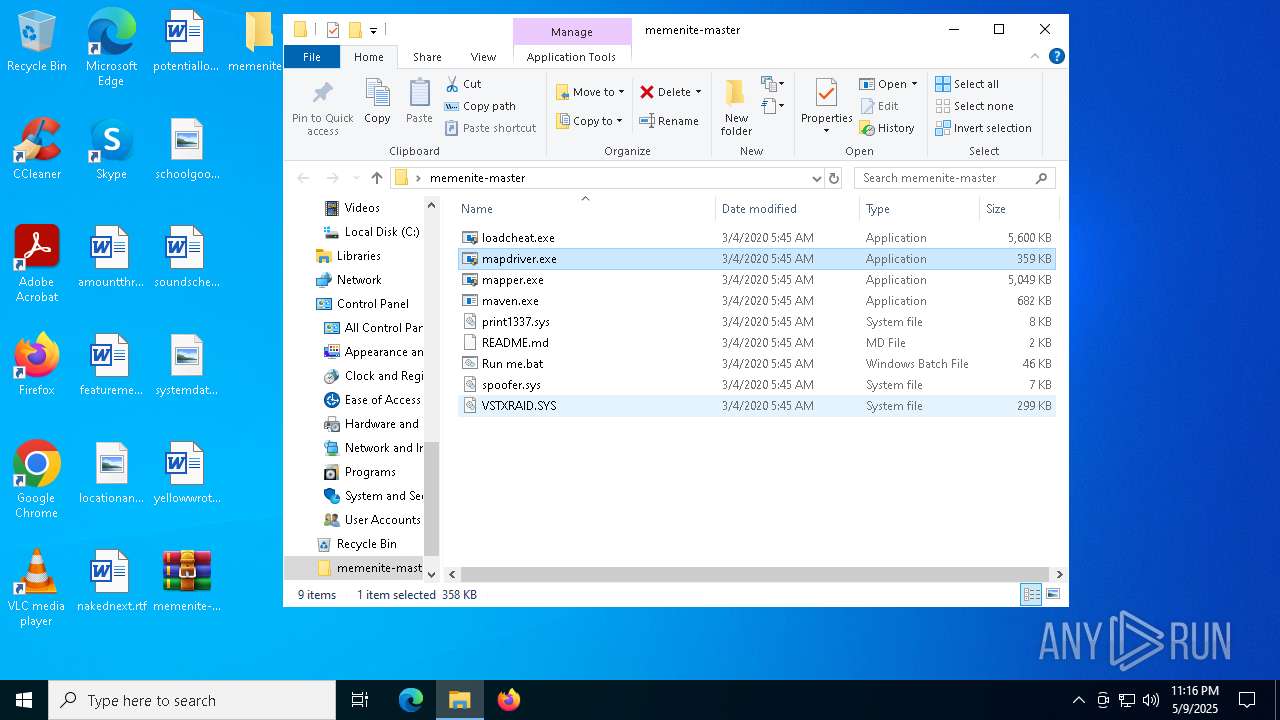
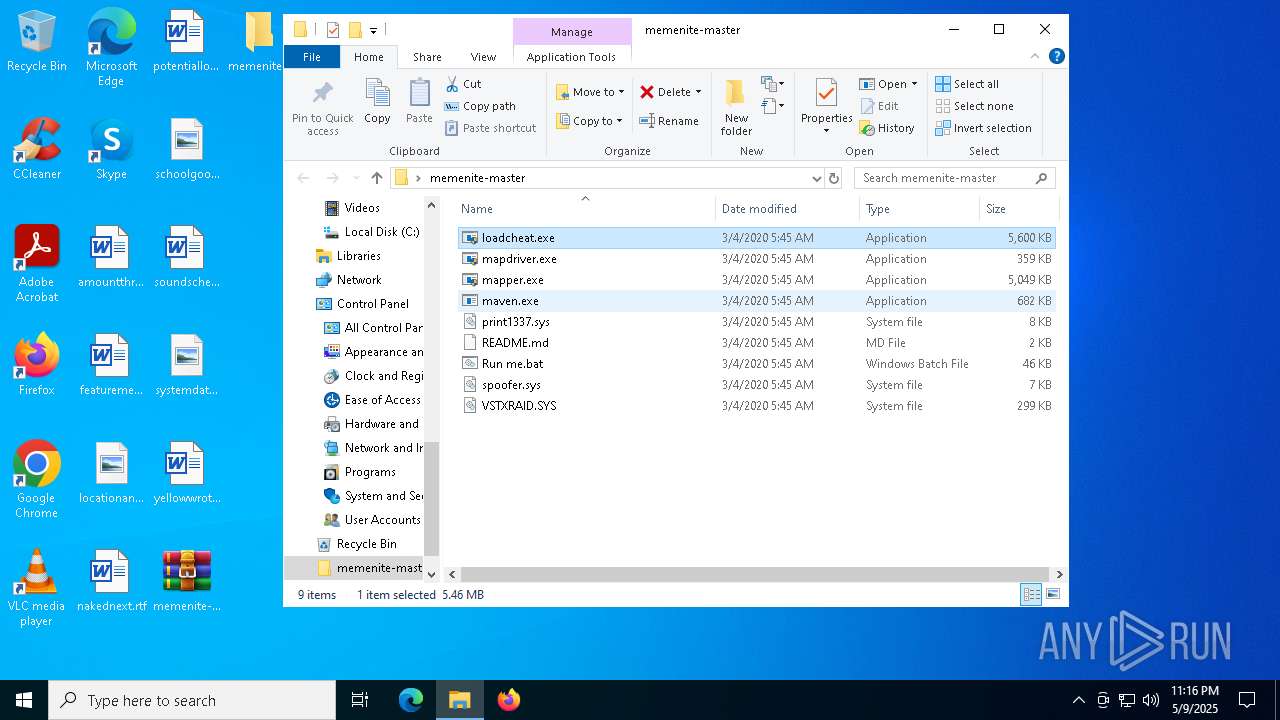
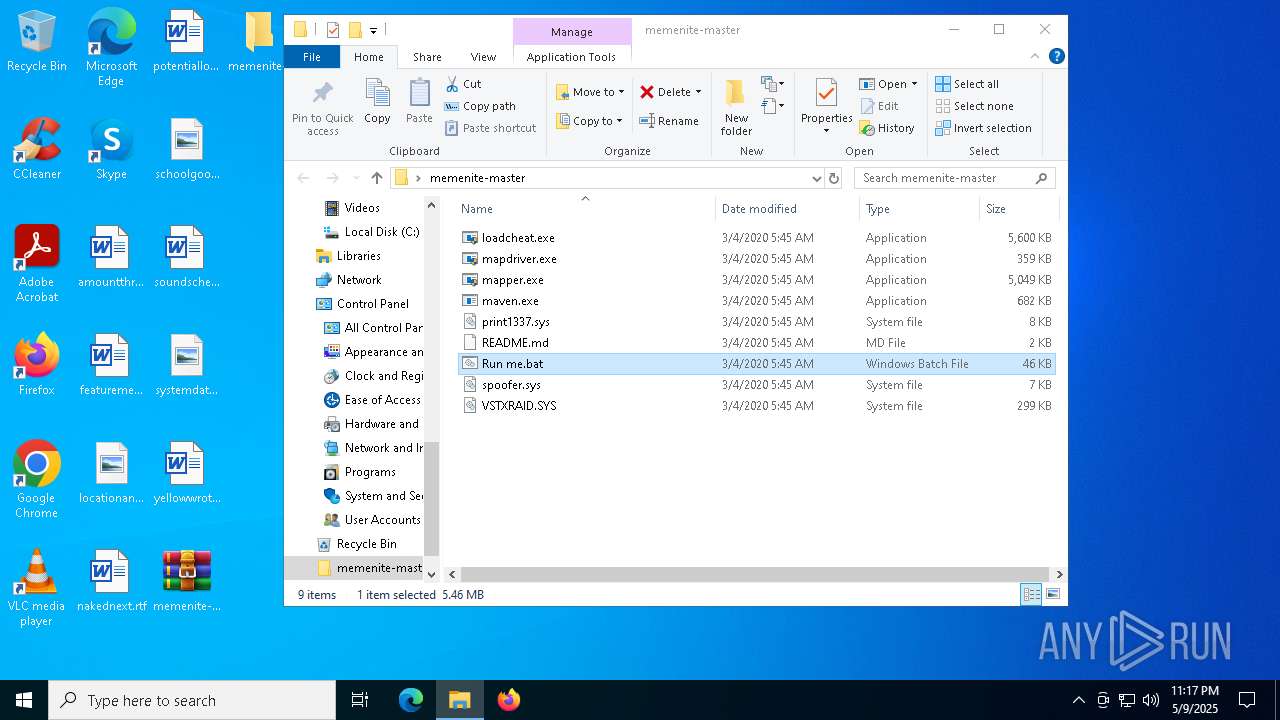
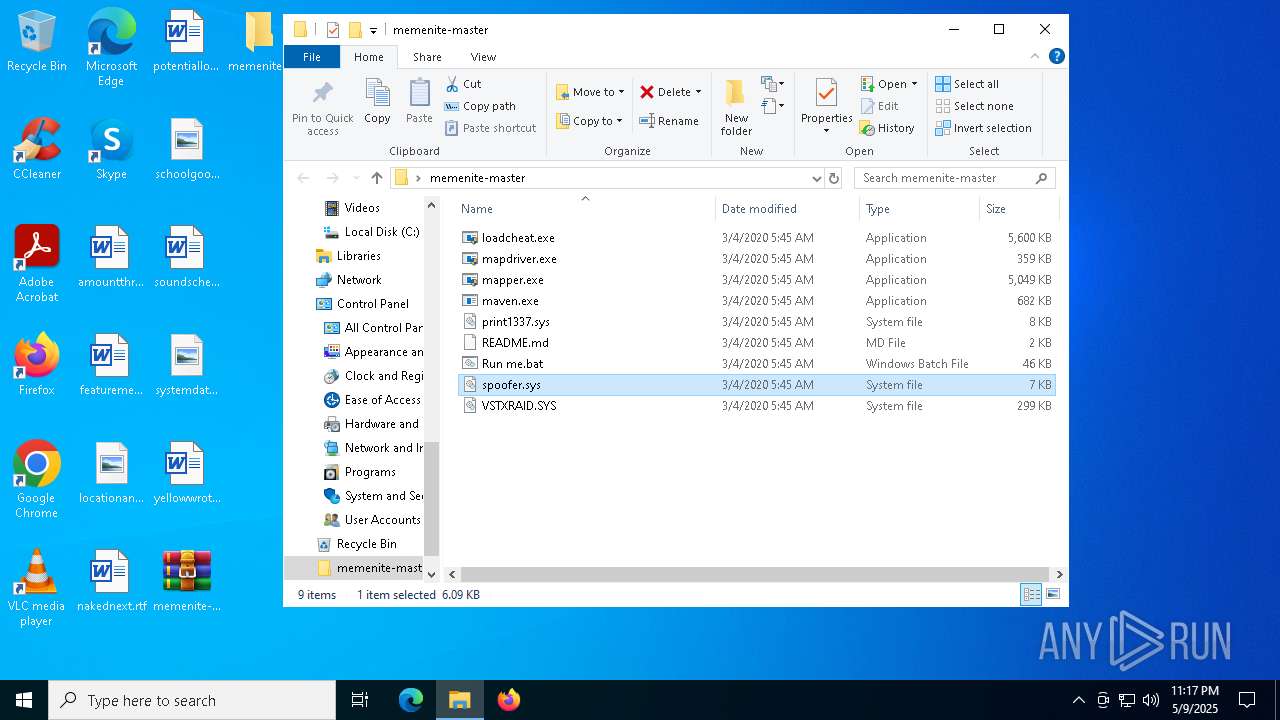
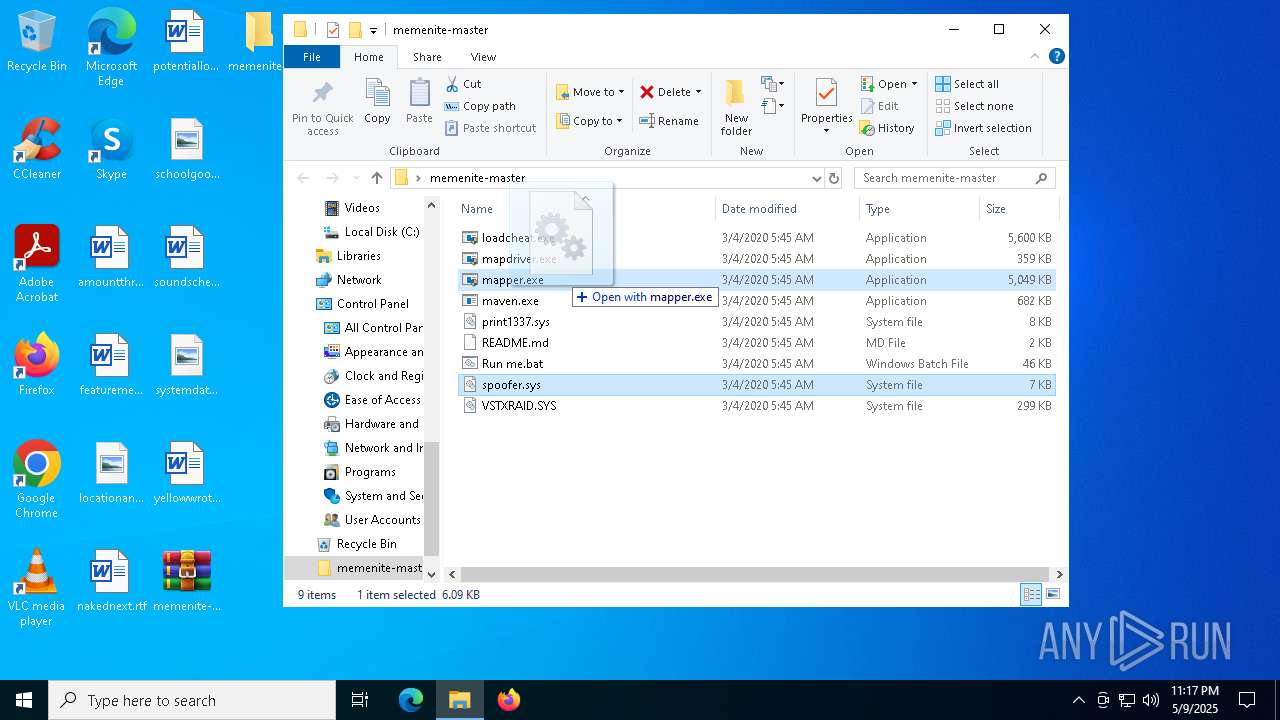
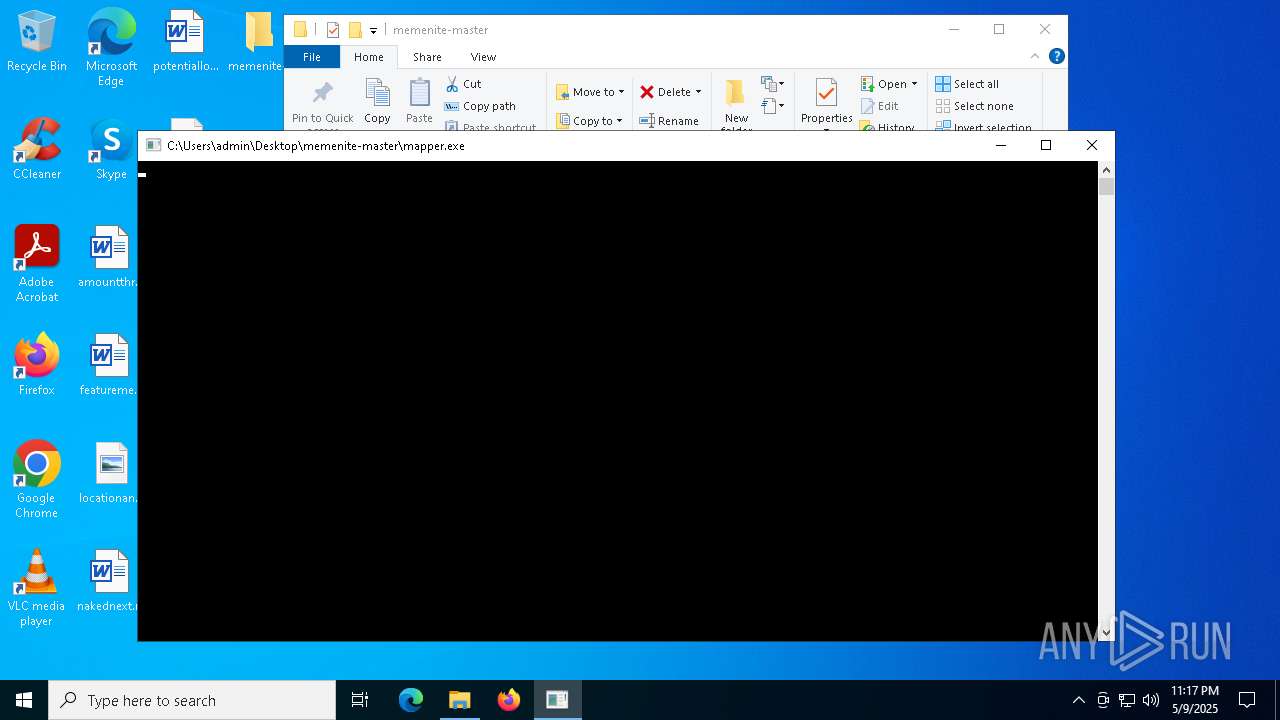
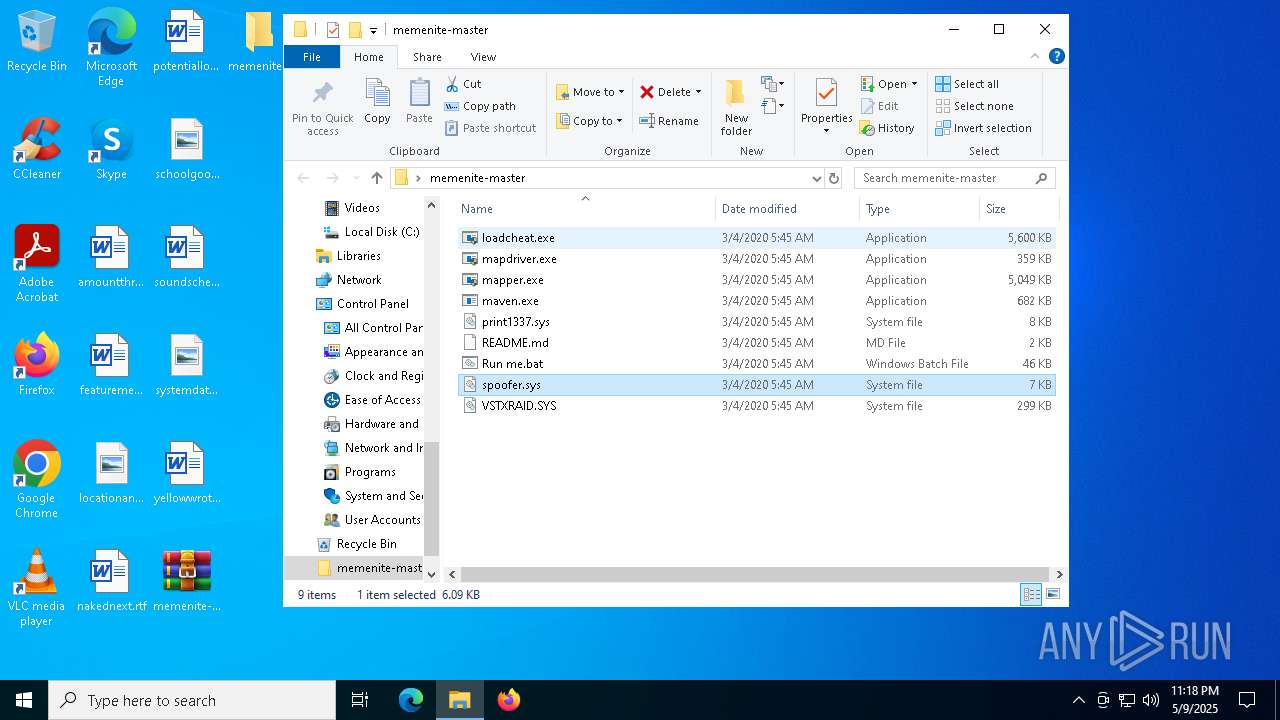
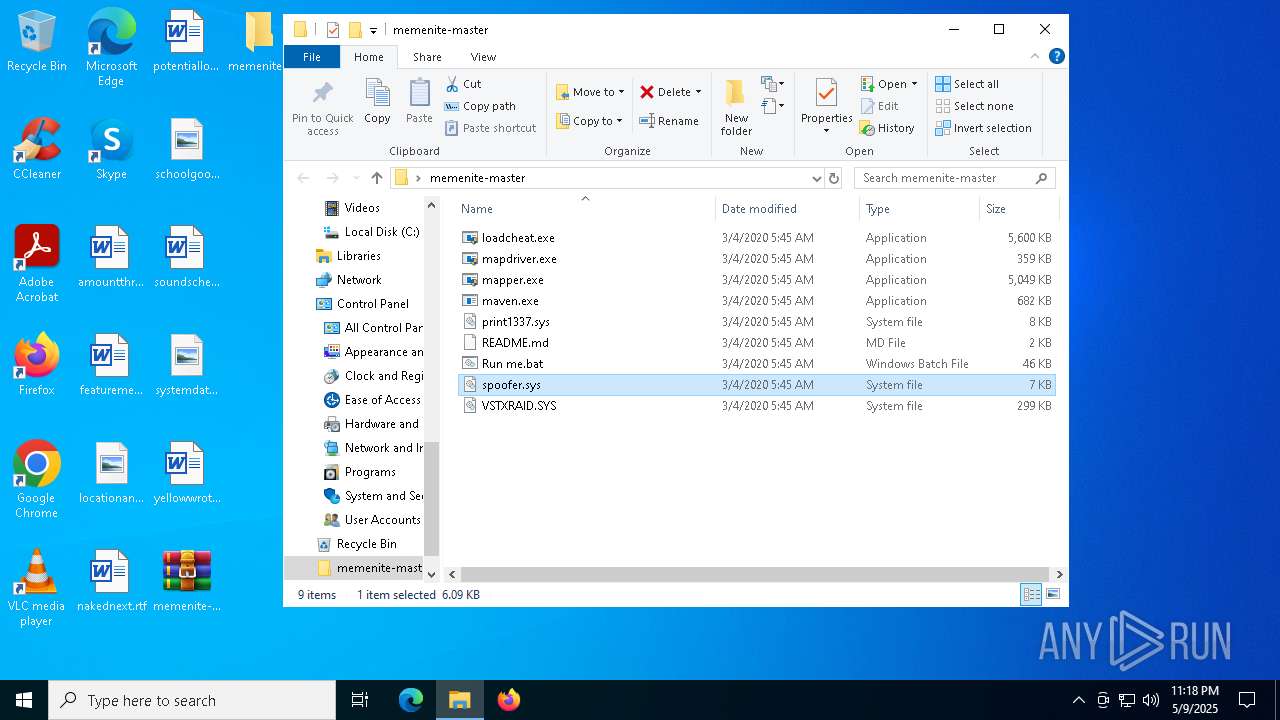
| File name: | memenite-master.zip |
| Full analysis: | https://app.any.run/tasks/961987c2-9efc-4207-b814-dcb7d7e05d7f |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 23:15:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 6F58E964634CE4DC1C189E1324EF415A |
| SHA1: | CF08D595ED35EEFD2FBD1955301066697F85BF33 |
| SHA256: | 4F98137A7D8CEA117FE163661D28F4A4F8CBDC93187BC21456BC9B9446E18015 |
| SSDEEP: | 196608:2vAIDVEz/Bb6g5N1nFv3CLJUM2HBpQVBX64ZEcY2cEy3eagDn9nAhg5/kuTZhRDZ:IAImz/dR5N1FvS+M2HBpqZER2cleagDH |
MALICIOUS
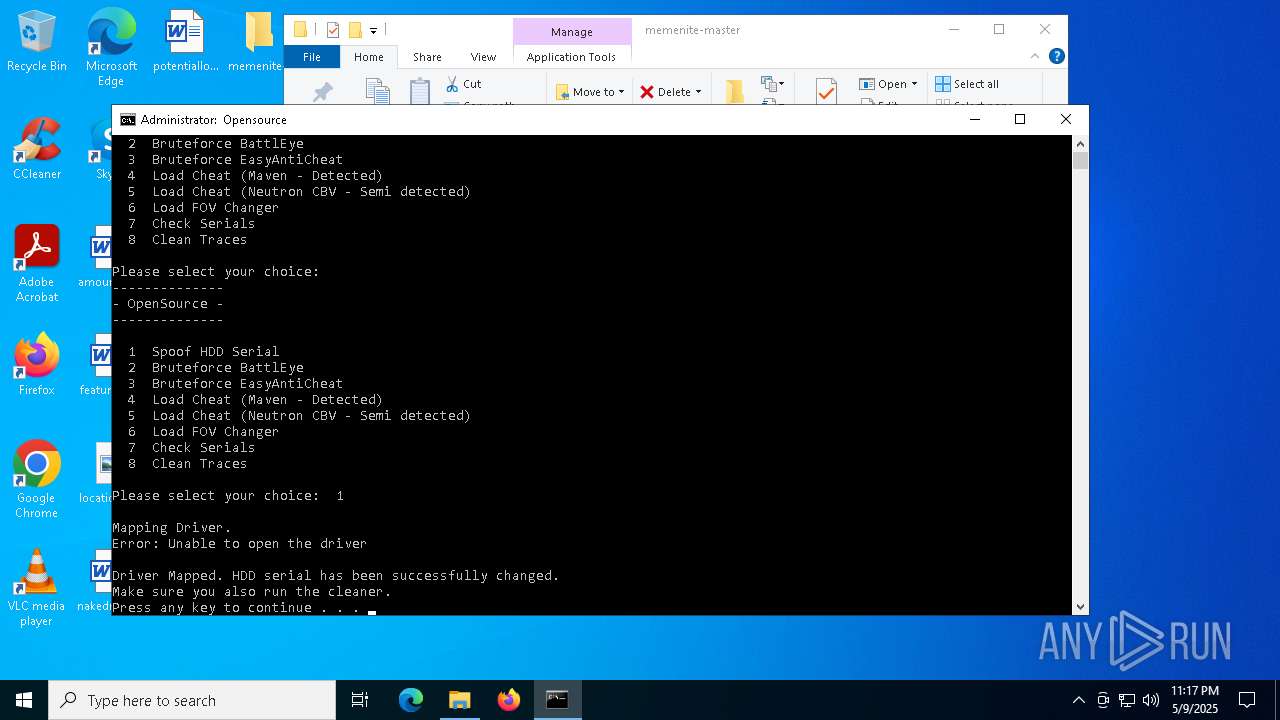
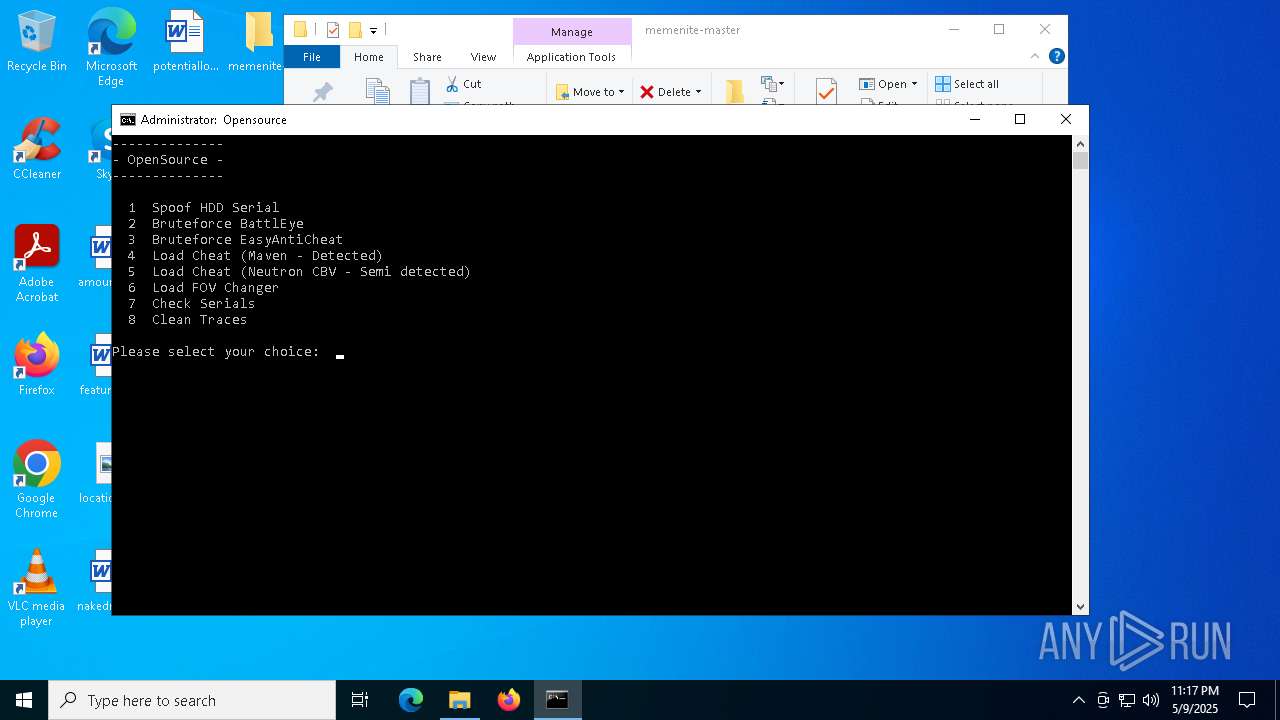
Vulnerable driver has been detected
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5048)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7152)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 1244)
- mapper.exe (PID: 2284)
- mapper.exe (PID: 1168)
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5048)
- mapper.exe (PID: 2104)
Application launched itself
- cmd.exe (PID: 1272)
- cmd.exe (PID: 6584)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1272)
- loadcheat.exe (PID: 5048)
- cmd.exe (PID: 6584)
Executing commands from a ".bat" file
- cmd.exe (PID: 1272)
- cmd.exe (PID: 6584)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5984)
- cmd.exe (PID: 2416)
- cmd.exe (PID: 6576)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 3008)
Executable content was dropped or overwritten
- mapper.exe (PID: 2284)
- mapper.exe (PID: 1168)
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5048)
- mapper.exe (PID: 2104)
Creates files in the driver directory
- mapper.exe (PID: 2284)
- mapper.exe (PID: 1168)
- mapper.exe (PID: 2104)
Creates or modifies Windows services
- mapper.exe (PID: 2284)
- mapper.exe (PID: 1168)
- mapper.exe (PID: 2104)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6392)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 2100)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 208)
Starts SC.EXE for service management
- cmd.exe (PID: 3240)
- cmd.exe (PID: 5188)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 5640)
Stops a currently running service
- sc.exe (PID: 6148)
- sc.exe (PID: 3800)
- sc.exe (PID: 5116)
- sc.exe (PID: 2096)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 6584)
Uses WMIC.EXE to obtain memory chip information
- cmd.exe (PID: 6584)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 6584)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7152)
- WinRAR.exe (PID: 1244)
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5048)
Manual execution by a user
- cmd.exe (PID: 1272)
- WinRAR.exe (PID: 1244)
- mapper.exe (PID: 4696)
- mapper.exe (PID: 1168)
- mapdriver.exe (PID: 6156)
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5988)
- loadcheat.exe (PID: 5048)
- cmd.exe (PID: 6584)
- mapper.exe (PID: 2104)
- mapper.exe (PID: 1328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1244)
Checks supported languages
- mapper.exe (PID: 2284)
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5048)
- mapper.exe (PID: 6456)
- mapper.exe (PID: 2104)
- mapper.exe (PID: 1168)
Reads the computer name
- mapper.exe (PID: 2284)
- mapper.exe (PID: 1168)
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5048)
- mapper.exe (PID: 2104)
Reads the software policy settings
- slui.exe (PID: 2852)
- slui.exe (PID: 3140)
Create files in a temporary directory
- mapdriver.exe (PID: 6252)
- loadcheat.exe (PID: 5048)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4212)
- WMIC.exe (PID: 4220)
- WMIC.exe (PID: 4284)
Checks proxy server information
- slui.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:03:03 21:45:52 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | memenite-master/ |
Total processes
198
Monitored processes
65
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /c taskkill /f /im EpicGamesLauncher.exe | C:\Windows\System32\cmd.exe | — | loadcheat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
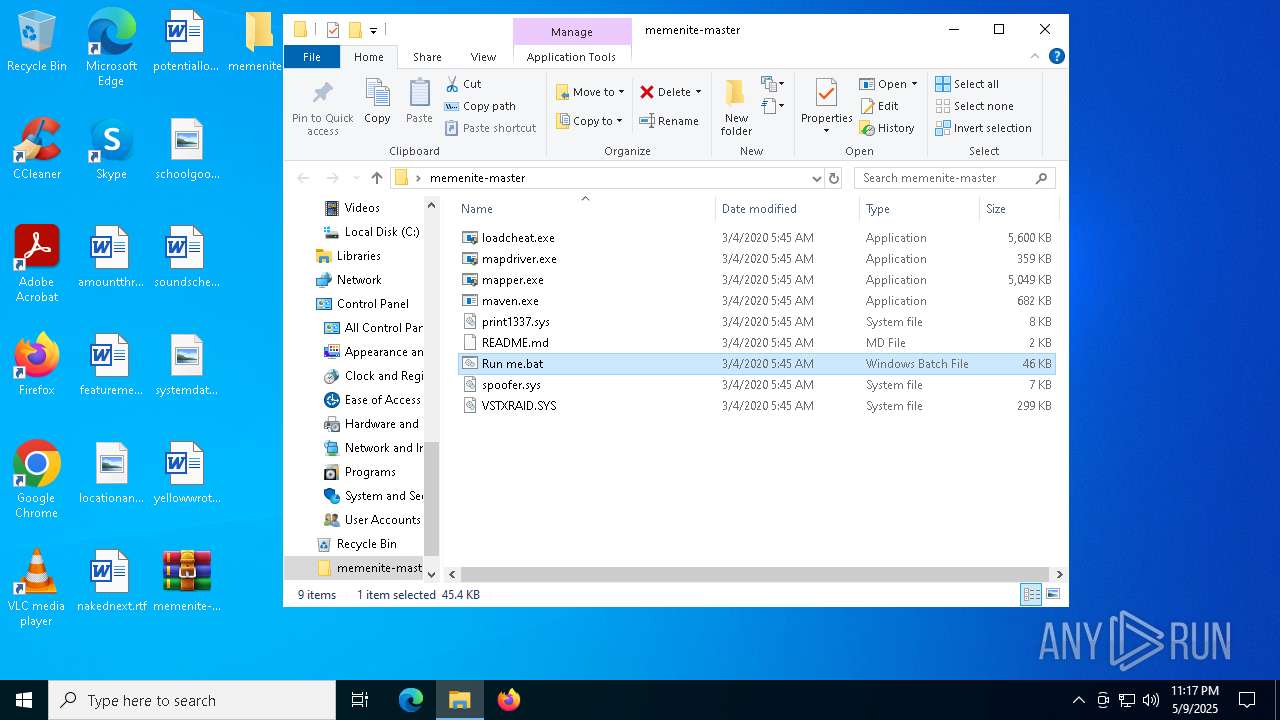
| 616 | findstr /b /c:":menu_" "C:\Users\admin\Desktop\memenite-master\Run me.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | findstr /b /c:":menu_" "C:\Users\admin\Desktop\memenite-master\Run me.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\Users\admin\Desktop\memenite-master\mapper.exe spoofer.sys | C:\Users\admin\Desktop\memenite-master\mapper.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1052 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\Desktop\memenite-master\mapper.exe" C:\Users\admin\Desktop\memenite-master\spoofer.sys | C:\Users\admin\Desktop\memenite-master\mapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
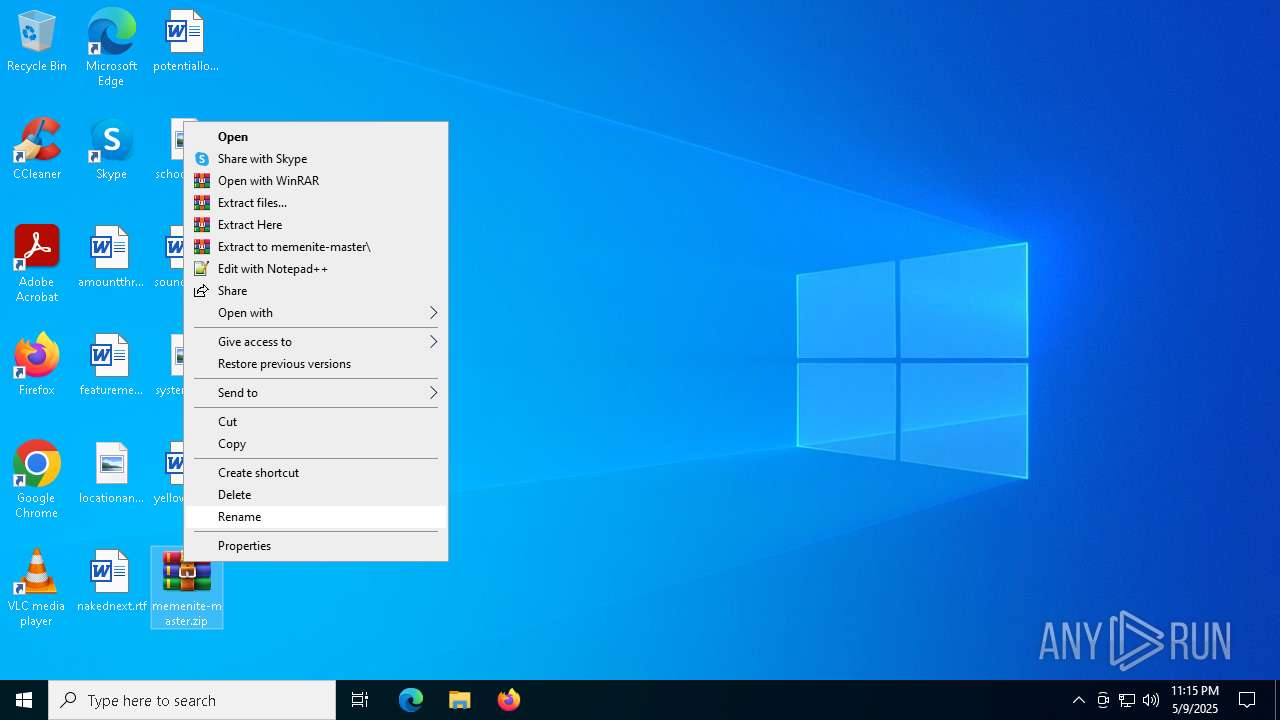
| 1244 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\memenite-master.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
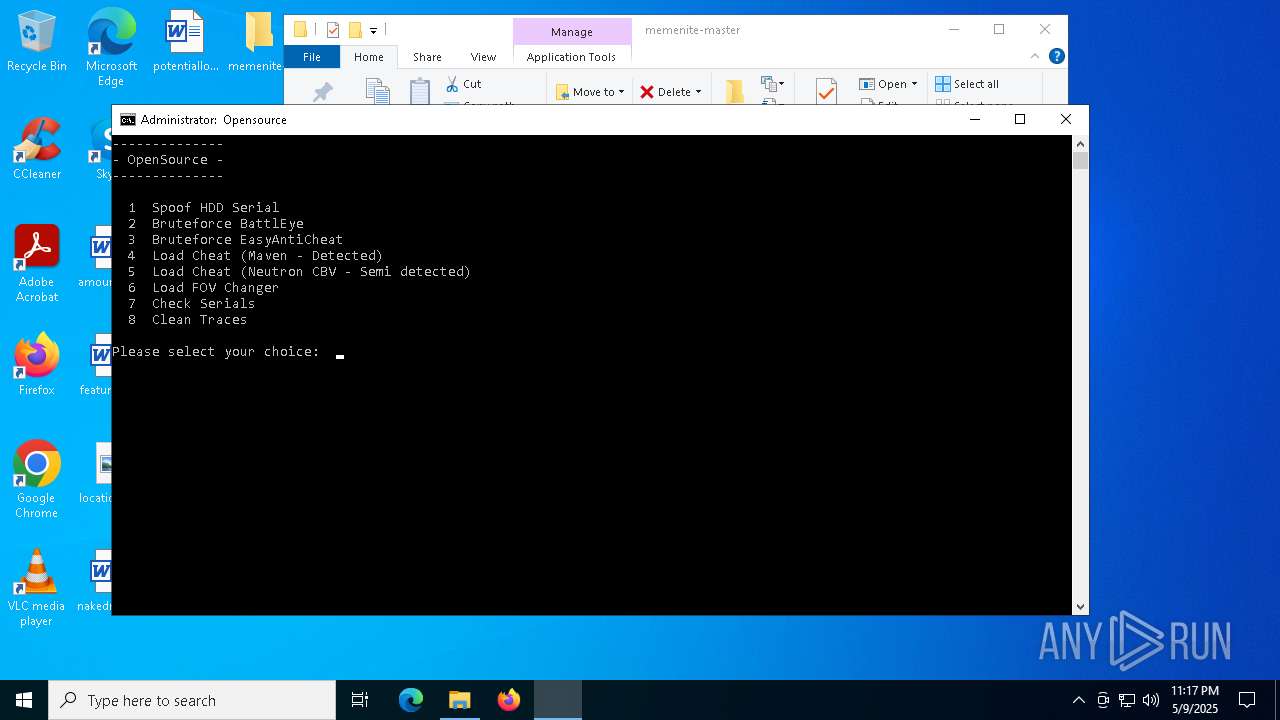
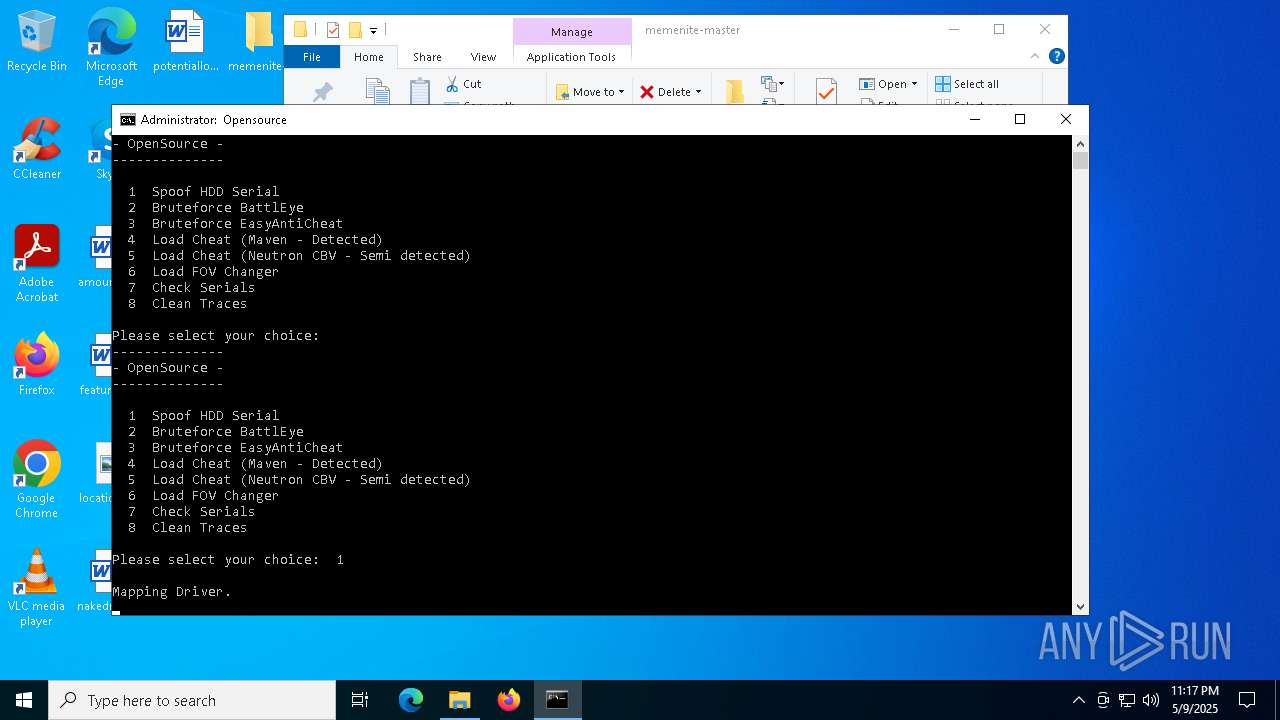
| 1272 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\memenite-master\Run me.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Users\admin\Desktop\memenite-master\mapper.exe" C:\Users\admin\Desktop\memenite-master\spoofer.sys | C:\Users\admin\Desktop\memenite-master\mapper.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
6 157
Read events
6 115
Write events
39
Delete events
3
Modification events
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\memenite-master.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Comment |
| Operation: | write | Name: | LeftBorder |
Value: 472 | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
12
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\mapper.exe | executable | |
MD5:8D68BF555643D03CC0A254199581D2A0 | SHA256:9B2AA35E6EEF2F49691BBD69DDAF23D88005F3F6E3F4CFFDF9BFC0DCCEFDCE25 | |||
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\mapdriver.exe | executable | |
MD5:8C564C612E0C026FB381A1EDC06E3677 | SHA256:8164305213E548256184AAF8830875FC7020F2C595AACCCAB5C13F70621AB844 | |||
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\loadcheat.exe | executable | |
MD5:9A9CE1911EFEA388A090B14FCD5B616E | SHA256:5F18528D89F0FAD6830FEB611772D9E918298125504FC913277D6614D2DD75EF | |||
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\spoofer.sys | executable | |
MD5:96756DEAFF1B2667883D4A21E43F4F65 | SHA256:1992C044963F5C77AA7B5462E2BB69A37C66BC0E13032524FB1663C0314FD420 | |||
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\maven.exe | executable | |
MD5:A142523FC1BF32FF9903C9043B713405 | SHA256:39A661E3346E929415C230034557F890696F312188FC5F2F7A269B251D1FCD27 | |||
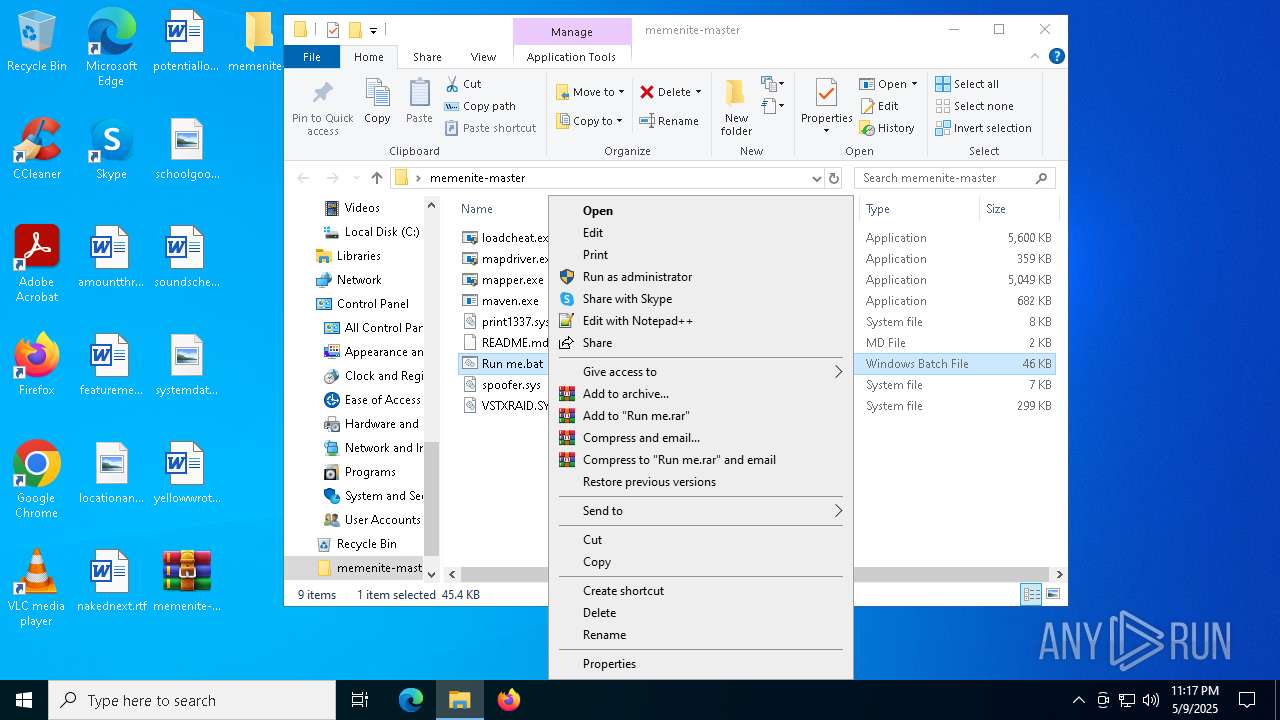
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\Run me.bat | text | |
MD5:4C3F1F1A63102A7B6F8167A95D2DC975 | SHA256:2249ECF66BAECE44E152EEDD9C2E10C9593FDEDB22265B1246D096DD323D522B | |||
| 2104 | mapper.exe | C:\Windows\System32\drivers\L3APD.sys | executable | |
MD5:C599F45FD550301593675B711CEC0794 | SHA256:E446BE684F7FC7FC674DFDCEEB49838087DAD15A282DD047EF15B13F581549D7 | |||
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\VSTXRAID.SYS | executable | |
MD5:A6CEC1A878536F3D5C82CFDF6E4CFCB9 | SHA256:A569744957E492042994C6F1312C8F4EC2F20A559BD8938A6A09C15230DEBBDC | |||
| 2284 | mapper.exe | C:\Windows\System32\drivers\L3APD.sys | executable | |
MD5:C599F45FD550301593675B711CEC0794 | SHA256:E446BE684F7FC7FC674DFDCEEB49838087DAD15A282DD047EF15B13F581549D7 | |||
| 1244 | WinRAR.exe | C:\Users\admin\Desktop\memenite-master\print1337.sys | executable | |
MD5:570FA1DE0B1B346A8270C0B2C26DF3E4 | SHA256:957D5F4CB7204F32D99BAF241C95111C9C0AFC0DDF0698B7A395081C3CDA5A2C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1072 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1072 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1072 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |