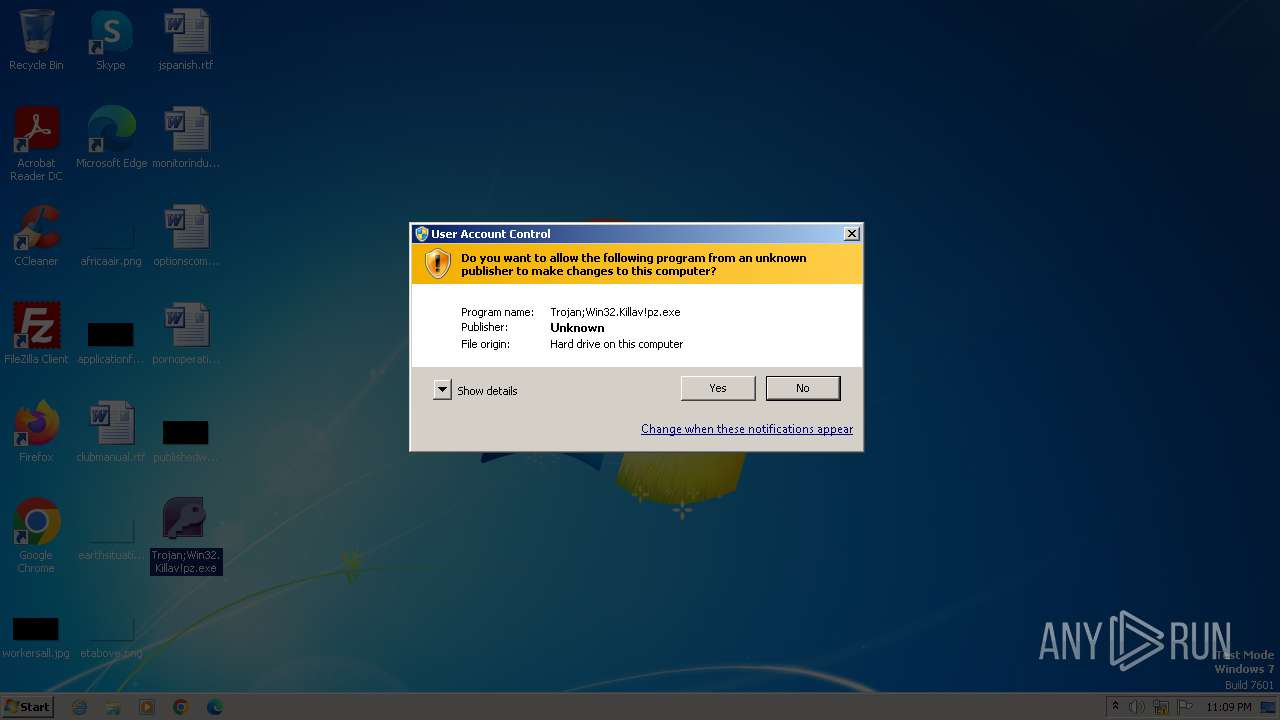
| File name: | Trojan;Win32.Killav!pz.exe |
| Full analysis: | https://app.any.run/tasks/a9da6ce7-146a-4253-b91a-e72ef0363571 |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2024, 22:08:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1E2EF7CE30D20DACEFCA0A4A931DF2F5 |
| SHA1: | A7C617CD2919057038DF5F36940E06C2BF3CCBB7 |
| SHA256: | 4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE |
| SSDEEP: | 24576:5E0wz/KDpKFlPAIrCZXbfAUpxOsz5MG3lB1vwFApP1:5E0wz/KDpKFlPAIrCZXbfAUpxOsz5MG3 |
MALICIOUS
Drops the executable file immediately after the start
- Trojan;Win32.Killav!pz.exe (PID: 3972)
- gegcazmfdfb.exe (PID: 4036)
- gegcazmfdfb.exe (PID: 2236)
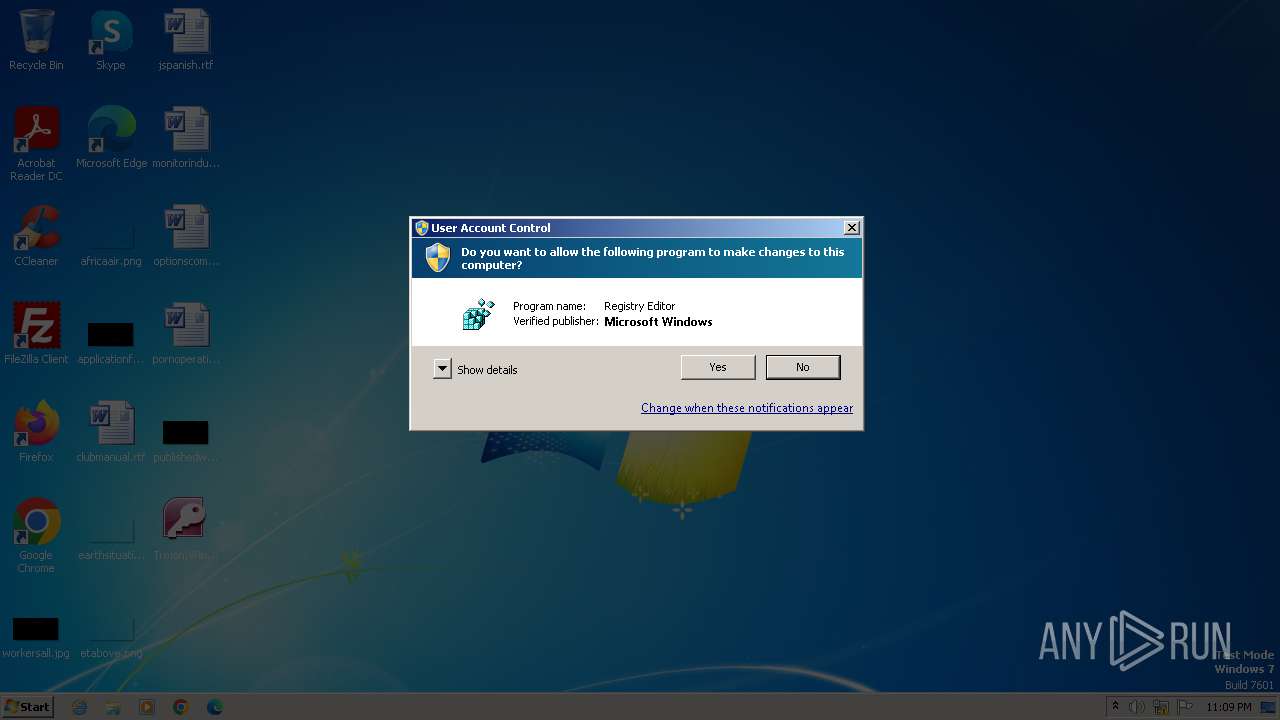
UAC/LUA settings modification
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4072)
- ccors.exe (PID: 4064)
- regedit.exe (PID: 2240)
- gegcazmfdfb.exe (PID: 2236)
- ccors.exe (PID: 2380)
- ccors.exe (PID: 2372)
- gegcazmfdfb.exe (PID: 3816)
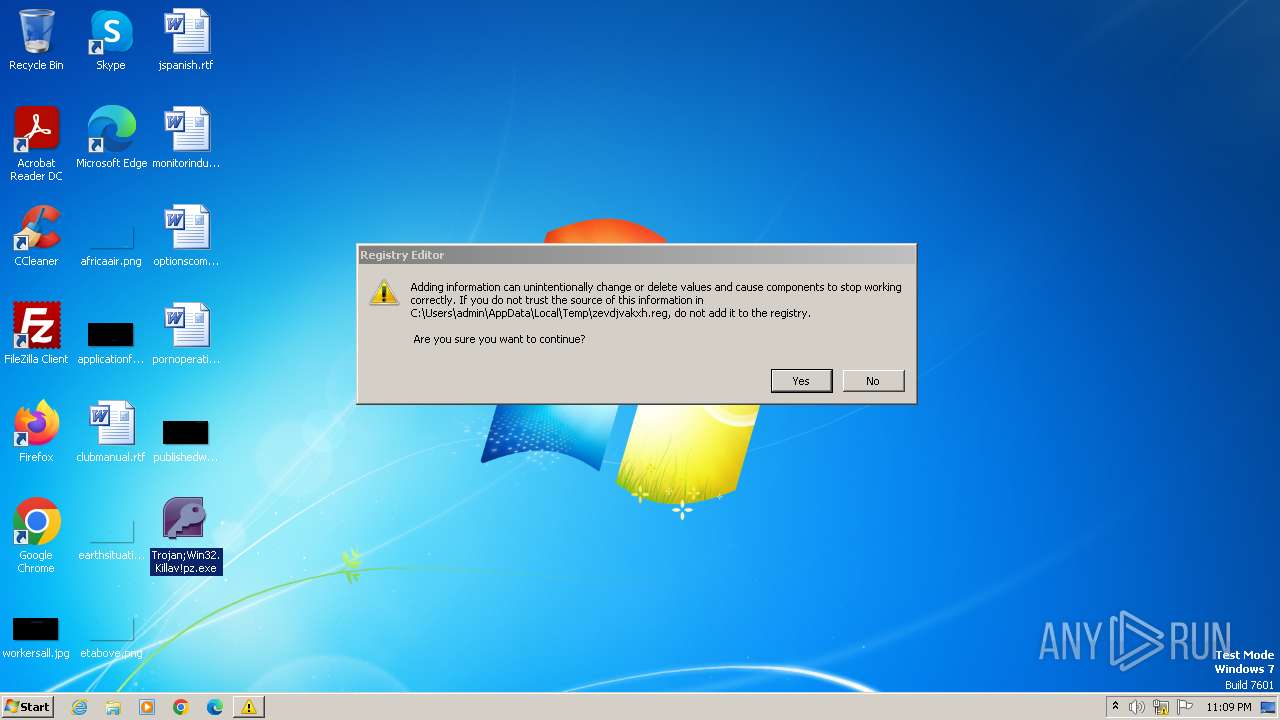
Changes the login/logoff helper path in the registry
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4072)
- ccors.exe (PID: 4064)
- gegcazmfdfb.exe (PID: 2236)
- ccors.exe (PID: 2372)
- ccors.exe (PID: 2380)
- gegcazmfdfb.exe (PID: 3816)
Changes the autorun value in the registry
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- gegcazmfdfb.exe (PID: 2236)
- ccors.exe (PID: 2380)
- ccors.exe (PID: 2372)
- gegcazmfdfb.exe (PID: 3816)
Changes appearance of the Explorer extensions
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4072)
- ccors.exe (PID: 4064)
- gegcazmfdfb.exe (PID: 2236)
- ccors.exe (PID: 2372)
- ccors.exe (PID: 2380)
Creates a writable file in the system directory
- ccors.exe (PID: 4064)
- gegcazmfdfb.exe (PID: 2236)
- ccors.exe (PID: 2372)
Modify registry editing tools (regedit)
- ccors.exe (PID: 2380)
- ccors.exe (PID: 2372)
- gegcazmfdfb.exe (PID: 3816)
Deletes the SafeBoot registry key
- ccors.exe (PID: 2372)
SUSPICIOUS
Reads the Internet Settings
- Trojan;Win32.Killav!pz.exe (PID: 3972)
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4064)
- sipnotify.exe (PID: 1624)
- csunebrmkfqykqyhevlng.exe (PID: 2172)
- gsqfslxoizgksuydw.exe (PID: 2156)
- gegcazmfdfb.exe (PID: 2236)
Executable content was dropped or overwritten
- Trojan;Win32.Killav!pz.exe (PID: 3972)
- gegcazmfdfb.exe (PID: 4036)
- gegcazmfdfb.exe (PID: 2236)
Reads security settings of Internet Explorer
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4064)
- Trojan;Win32.Killav!pz.exe (PID: 3972)
- gsqfslxoizgksuydw.exe (PID: 2156)
- csunebrmkfqykqyhevlng.exe (PID: 2172)
- gegcazmfdfb.exe (PID: 2236)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1624)
- ctfmon.exe (PID: 1572)
Reads settings of System Certificates
- sipnotify.exe (PID: 1624)
Checks for external IP
- ccors.exe (PID: 2372)
Potential Corporate Privacy Violation
- ccors.exe (PID: 2372)
INFO
Checks supported languages
- Trojan;Win32.Killav!pz.exe (PID: 3972)
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- Trojan;Win32.Killav!pz.exe (PID: 2064)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
- gsqfslxoizgksuydw.exe (PID: 2156)
- csunebrmkfqykqyhevlng.exe (PID: 2172)
- gegcazmfdfb.exe (PID: 2236)
- gegcazmfdfb.exe (PID: 2248)
- ccors.exe (PID: 2372)
- ccors.exe (PID: 2380)
- wmpnscfg.exe (PID: 2524)
- wmpnscfg.exe (PID: 2552)
- gegcazmfdfb.exe (PID: 3816)
Reads the computer name
- Trojan;Win32.Killav!pz.exe (PID: 3972)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- Trojan;Win32.Killav!pz.exe (PID: 2064)
- gegcazmfdfb.exe (PID: 4036)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
- gsqfslxoizgksuydw.exe (PID: 2156)
- csunebrmkfqykqyhevlng.exe (PID: 2172)
- gegcazmfdfb.exe (PID: 2236)
- gegcazmfdfb.exe (PID: 2248)
- ccors.exe (PID: 2372)
- ccors.exe (PID: 2380)
- wmpnscfg.exe (PID: 2552)
- wmpnscfg.exe (PID: 2524)
- gegcazmfdfb.exe (PID: 3816)
Create files in a temporary directory
- Trojan;Win32.Killav!pz.exe (PID: 3972)
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 2372)
Process checks whether UAC notifications are on
- gegcazmfdfb.exe (PID: 4036)
- ccors.exe (PID: 4072)
- ccors.exe (PID: 4064)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
- gegcazmfdfb.exe (PID: 2236)
- ccors.exe (PID: 2372)
- ccors.exe (PID: 2380)
- gegcazmfdfb.exe (PID: 3816)
Creates files or folders in the user directory
- ccors.exe (PID: 4064)
- ccors.exe (PID: 2372)
Manual execution by a user
- Trojan;Win32.Killav!pz.exe (PID: 2064)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
- gsqfslxoizgksuydw.exe (PID: 2156)
- csunebrmkfqykqyhevlng.exe (PID: 2172)
- wmpnscfg.exe (PID: 2524)
- wmpnscfg.exe (PID: 2552)
- chrome.exe (PID: 2680)
- chrome.exe (PID: 1992)
- chrome.exe (PID: 3616)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1624)
Creates files in the program directory
- ccors.exe (PID: 2372)
Application launched itself
- chrome.exe (PID: 3616)
- chrome.exe (PID: 1992)
- chrome.exe (PID: 2680)
Reads the software policy settings
- sipnotify.exe (PID: 1624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:05:02 04:16:24+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 36864 |
| InitializedDataSize: | 520192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x58c2 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
142
Monitored processes
61
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3748 --field-trial-handle=1176,i,10029379725846061609,14993735828118751854,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1236 --field-trial-handle=1176,i,10029379725846061609,14993735828118751854,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3724 --field-trial-handle=1176,i,10029379725846061609,14993735828118751854,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1572 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1624 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1756 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\zevdjvakxh.reg" | C:\Windows\regedit.exe | — | ccors.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2292 --field-trial-handle=1172,i,1989018271147064909,3340332412587015337,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\Trojan;Win32.Killav!pz.exe" | C:\Users\admin\Desktop\Trojan;Win32.Killav!pz.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
Total events
30 852
Read events
29 829
Write events
964
Delete events
59
Modification events
| (PID) Process: | (3972) Trojan;Win32.Killav!pz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3972) Trojan;Win32.Killav!pz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3972) Trojan;Win32.Killav!pz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3972) Trojan;Win32.Killav!pz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4036) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (4036) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: Explorer.exe | |||
| (PID) Process: | (4036) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | acqvyhj |
Value: pcbrfzmezrzenqvbvj.exe | |||
| (PID) Process: | (4036) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | pshnrbem |
Value: pcbrfzmezrzenqvbvj.exe . | |||
| (PID) Process: | (4036) gegcazmfdfb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | zevdjvakxh |
Value: pcbrfzmezrzenqvbvj.exe | |||
| (PID) Process: | (4036) gegcazmfdfb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | uasbivbmalm |
Value: aoofupdwsluakoubwlz.exe . | |||
Executable files
29
Suspicious files
308
Text files
107
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | Trojan;Win32.Killav!pz.exe | C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe | executable | |
MD5:645E4A8AE0488DB9034CAAEA0DD15D38 | SHA256:97258CA05CD7A15E174ED2036E1161CA9BCF5A1ABF4A99FC07F6F11EA60E3B8C | |||
| 4036 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\csunebrmkfqykqyhevlng.exe | executable | |
MD5:1E2EF7CE30D20DACEFCA0A4A931DF2F5 | SHA256:4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE | |||
| 4036 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\ncdvlhwqnhryjovdzpef.exe | executable | |
MD5:1E2EF7CE30D20DACEFCA0A4A931DF2F5 | SHA256:4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE | |||
| 4036 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\pcbrfzmezrzenqvbvj.exe | executable | |
MD5:1E2EF7CE30D20DACEFCA0A4A931DF2F5 | SHA256:4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE | |||
| 4064 | ccors.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\System32\mkuvuzxagjcsmaqhmljtutywz.ibr | binary | |
MD5:62723B93C8D28011F89E24B0D484BA0E | SHA256:4F110F9B1869BB566FB96791FA9D15122207C502B81C815416225768F3CAA81B | |||
| 4036 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\aoofupdwsluakoubwlz.exe | executable | |
MD5:1E2EF7CE30D20DACEFCA0A4A931DF2F5 | SHA256:4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE | |||
| 4036 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\tknhzxokjfranudnlduxrj.exe | executable | |
MD5:1E2EF7CE30D20DACEFCA0A4A931DF2F5 | SHA256:4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE | |||
| 2236 | gegcazmfdfb.exe | C:\Windows\system32\zkhvhzkatjpszadh.exe | executable | |
MD5:1E2EF7CE30D20DACEFCA0A4A931DF2F5 | SHA256:4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE | |||
| 2236 | gegcazmfdfb.exe | C:\Windows\system32\aoofupdwsluakoubwlz.exe | executable | |
MD5:1E2EF7CE30D20DACEFCA0A4A931DF2F5 | SHA256:4F87BCDC60EF981FD2582D5B5AE86AEDEF224DF5D8599CF4835224C8D30201EE | |||
| 4064 | ccors.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\mkuvuzxagjcsmaqhmljtutywz.ibr | binary | |
MD5:62723B93C8D28011F89E24B0D484BA0E | SHA256:4F110F9B1869BB566FB96791FA9D15122207C502B81C815416225768F3CAA81B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
90
DNS requests
91
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2372 | ccors.exe | GET | 301 | 104.27.207.92:80 | http://www.whatismyip.com/ | unknown | — | — | unknown |
1624 | sipnotify.exe | HEAD | 200 | 104.96.141.237:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133627073926870000 | unknown | — | — | unknown |
2372 | ccors.exe | GET | 301 | 188.114.97.3:80 | http://www.showmyipaddress.com/ | unknown | — | — | unknown |
2372 | ccors.exe | GET | — | 104.27.207.92:80 | http://www.whatismyip.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1092 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1432 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
1624 | sipnotify.exe | 104.96.141.237:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | AT | unknown |
2372 | ccors.exe | 104.27.207.92:80 | www.whatismyip.com | CLOUDFLARENET | US | unknown |
2372 | ccors.exe | 49.13.77.253:80 | www.whatismyip.ca | Hetzner Online GmbH | DE | unknown |
2680 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2848 | chrome.exe | 142.250.186.35:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |
www.whatismyip.com |
| shared |
www.whatismyip.ca |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| unknown |
encrypted-tbn0.gstatic.com |
| whitelisted |
whatismyip.everdot.org |
| unknown |
lh5.googleusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2372 | ccors.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2372 | ccors.exe | Attempted Information Leak | ET POLICY IP Check Domain (whatismyip in HTTP Host) |
2372 | ccors.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2372 | ccors.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (showmyipaddress .com in HTTP Host) |
2372 | ccors.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2372 | ccors.exe | Attempted Information Leak | ET POLICY IP Check Domain (whatismyip in HTTP Host) |