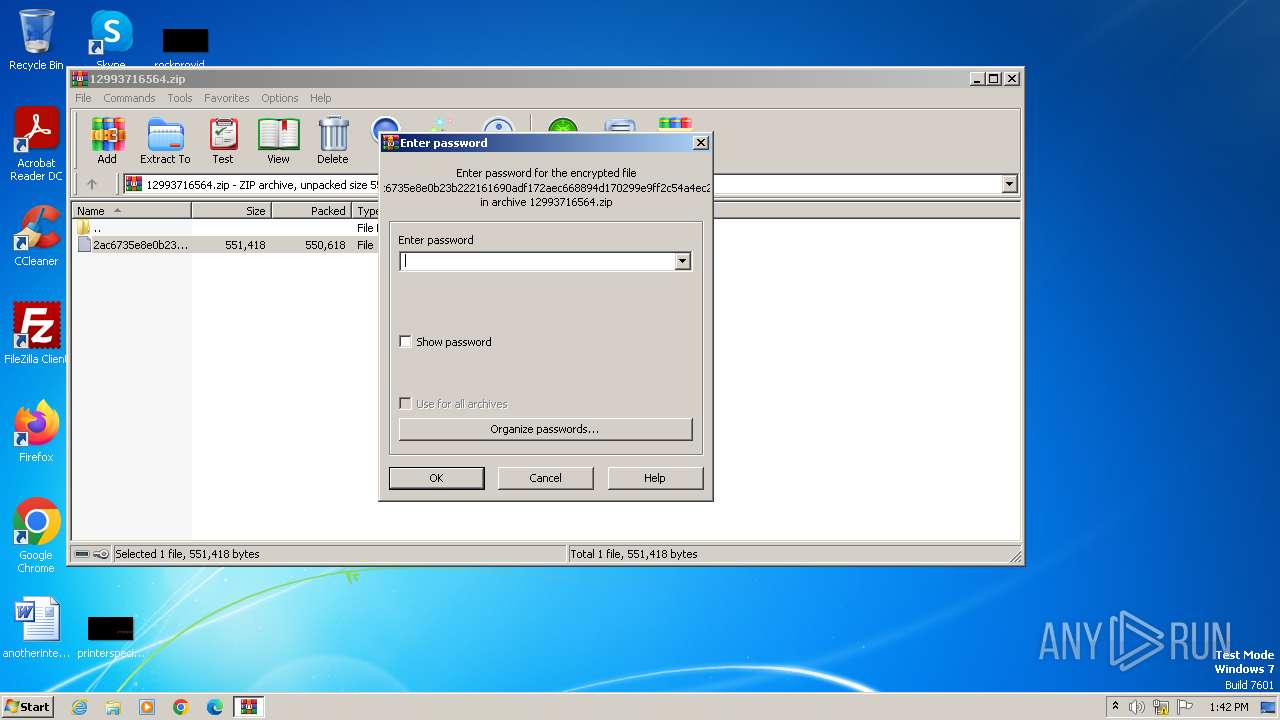
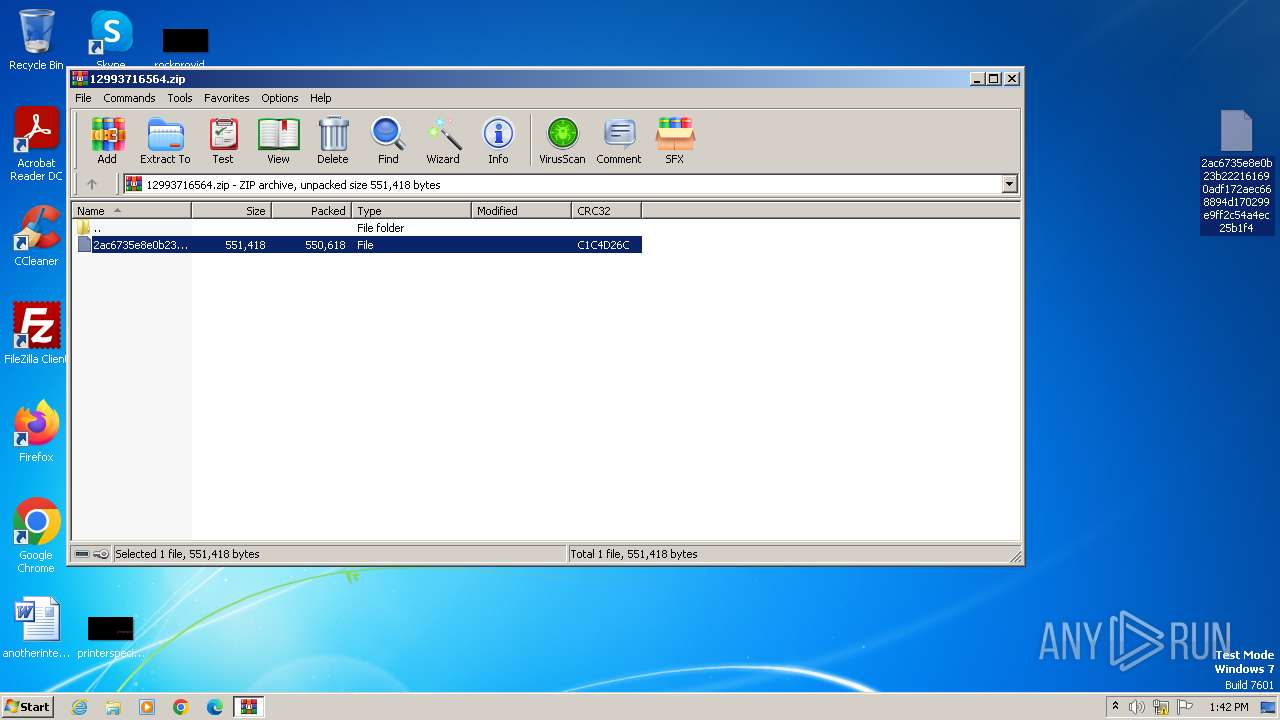
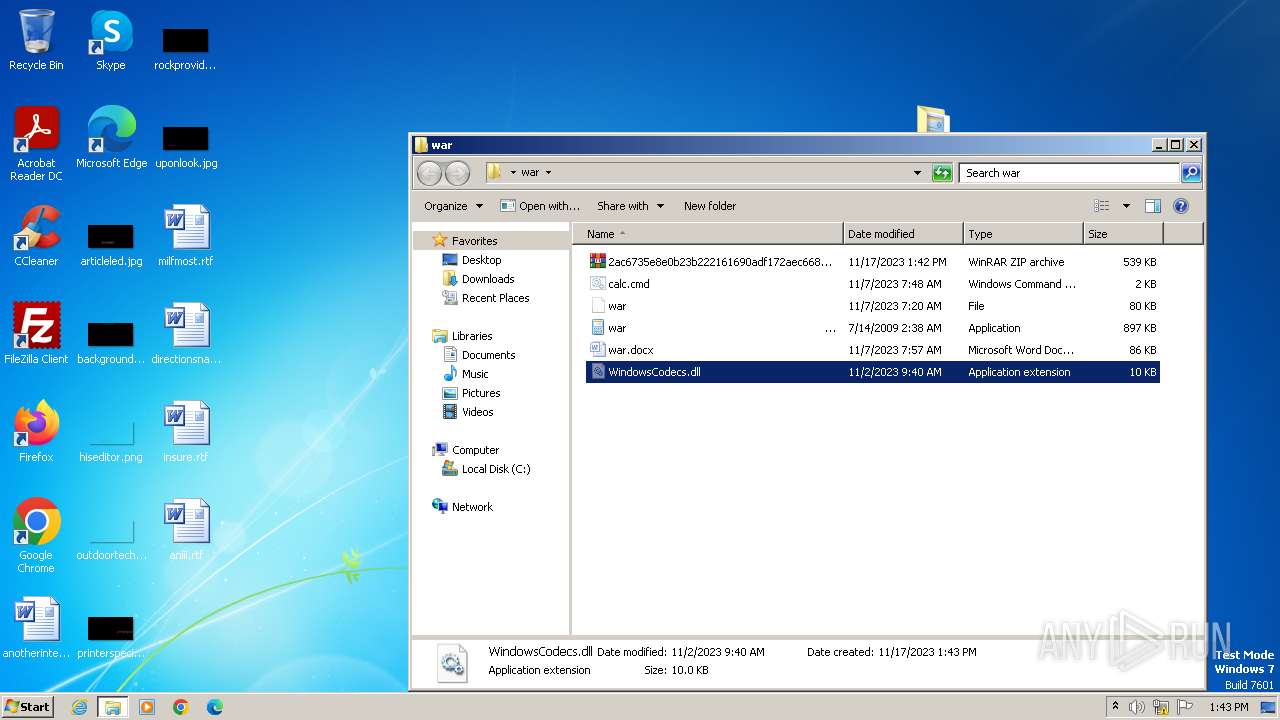
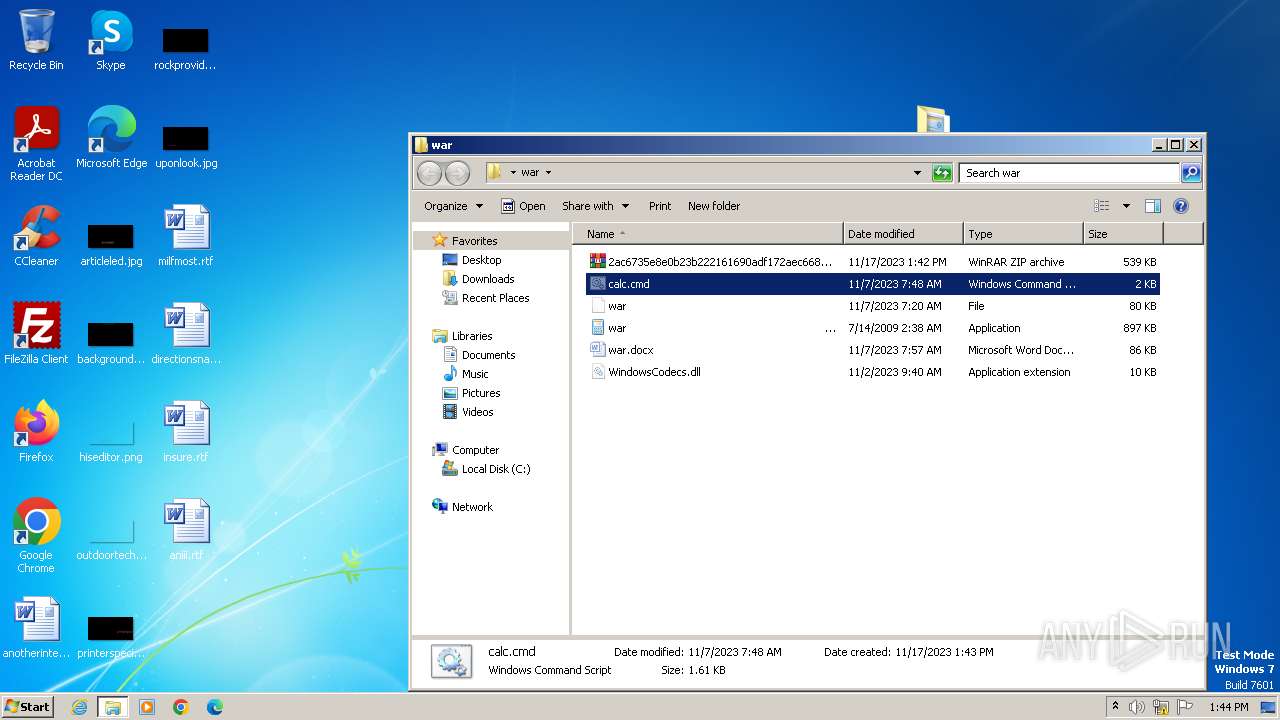
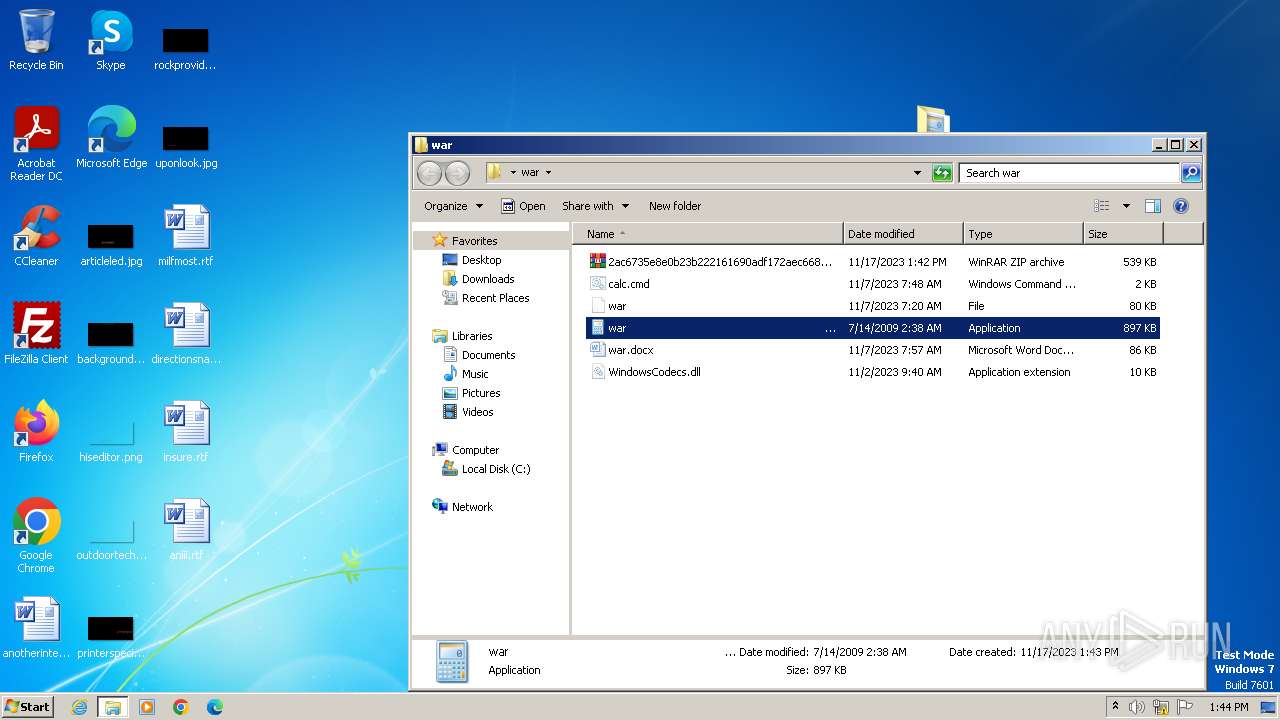
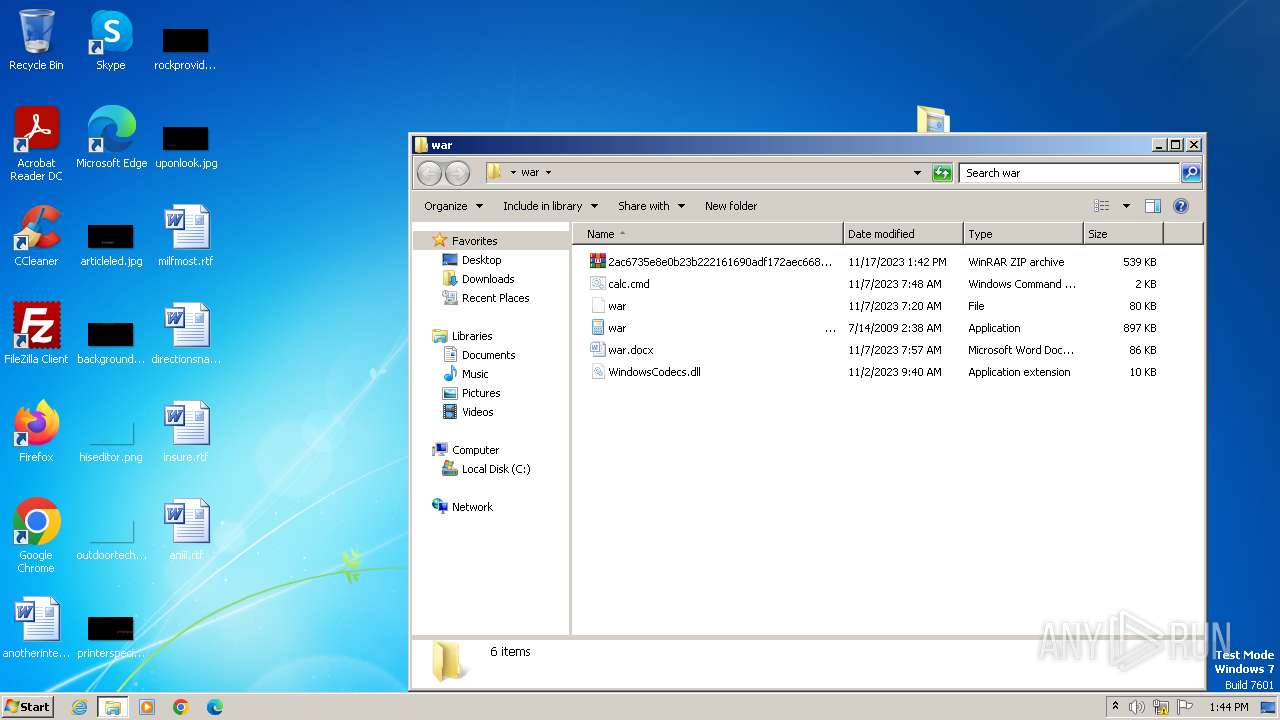
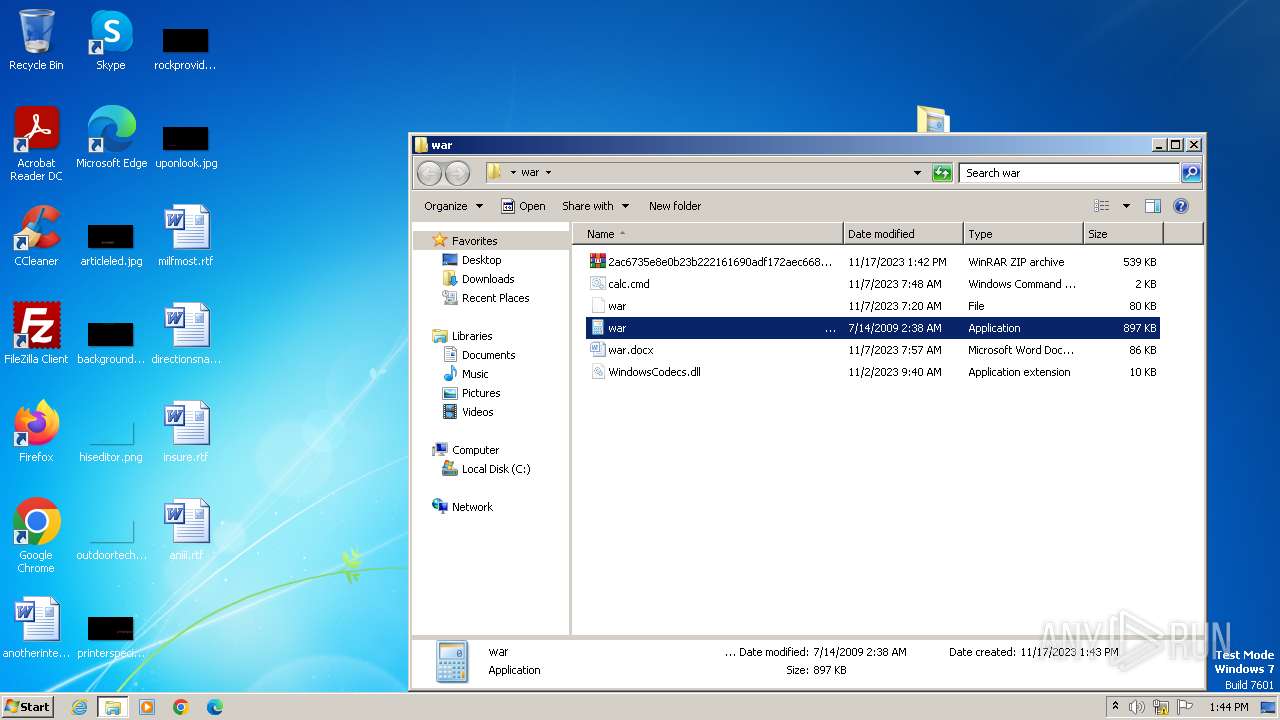
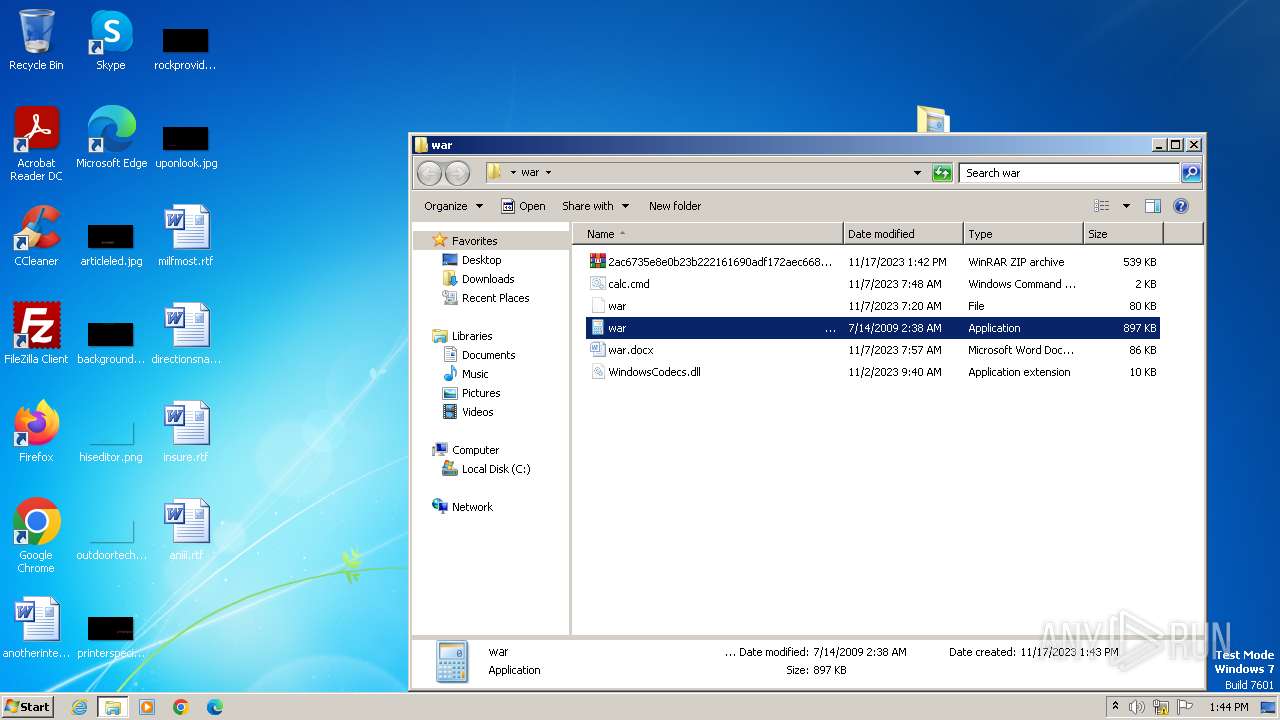
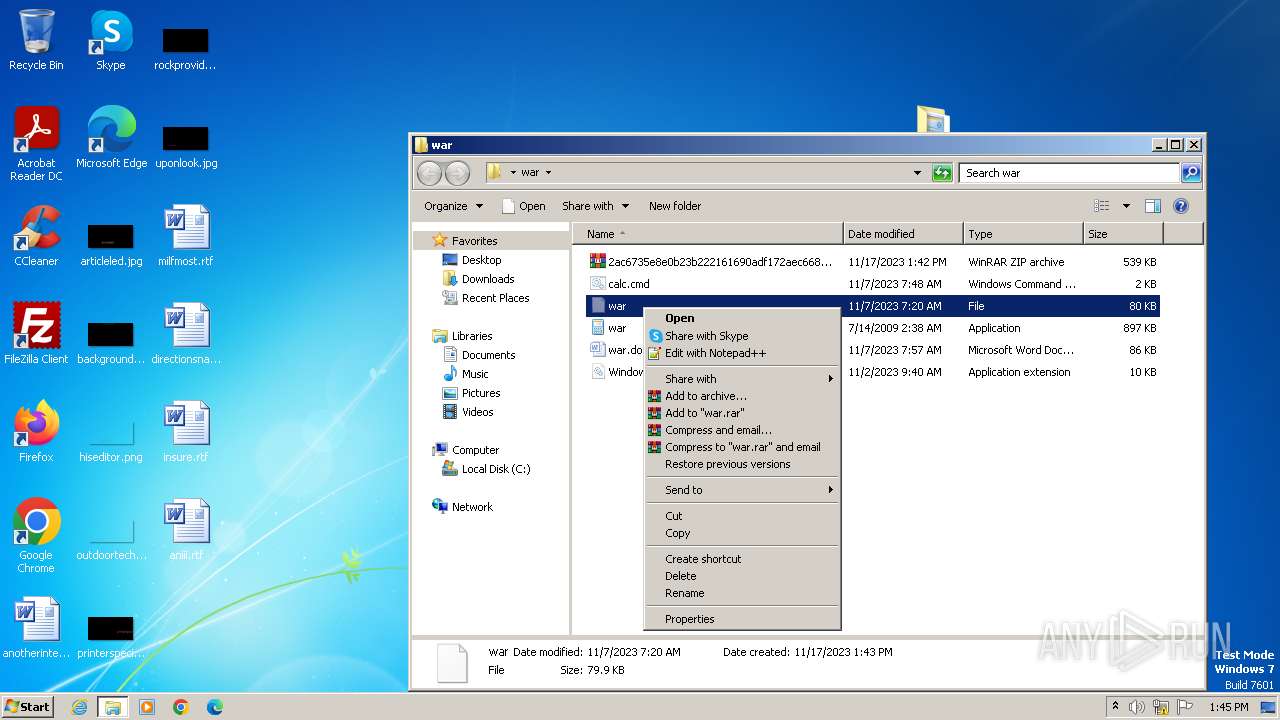
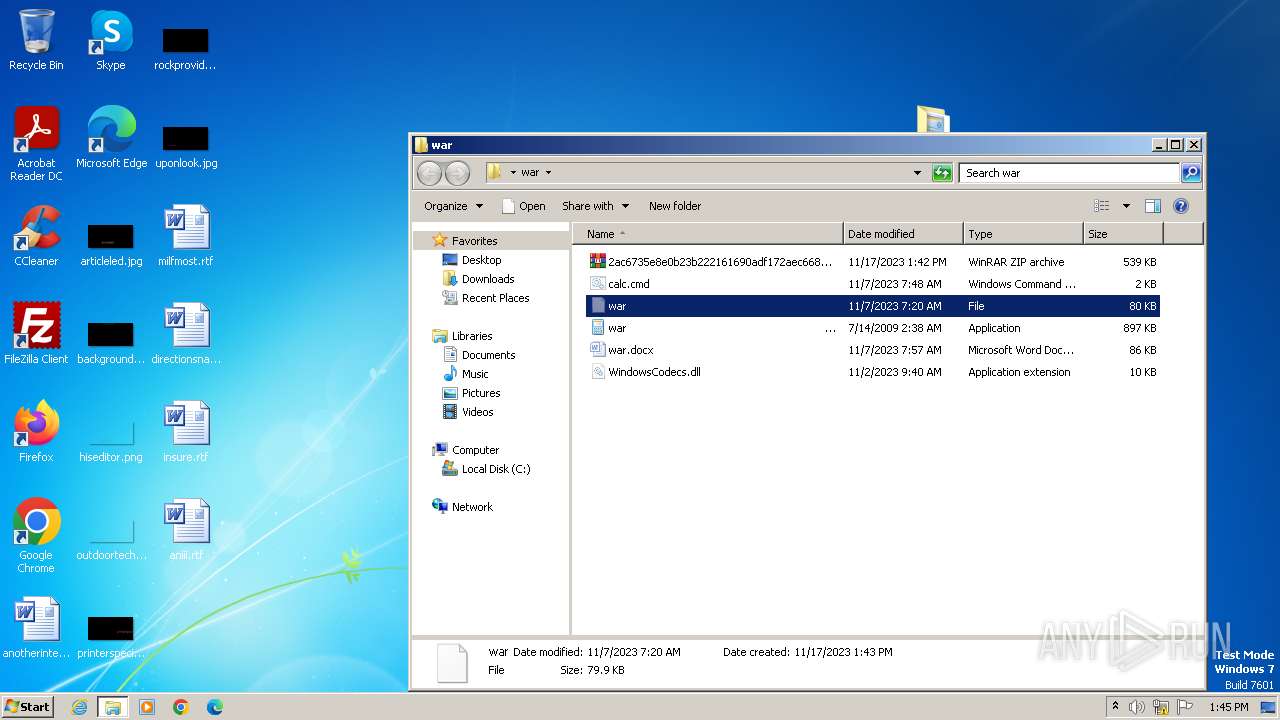
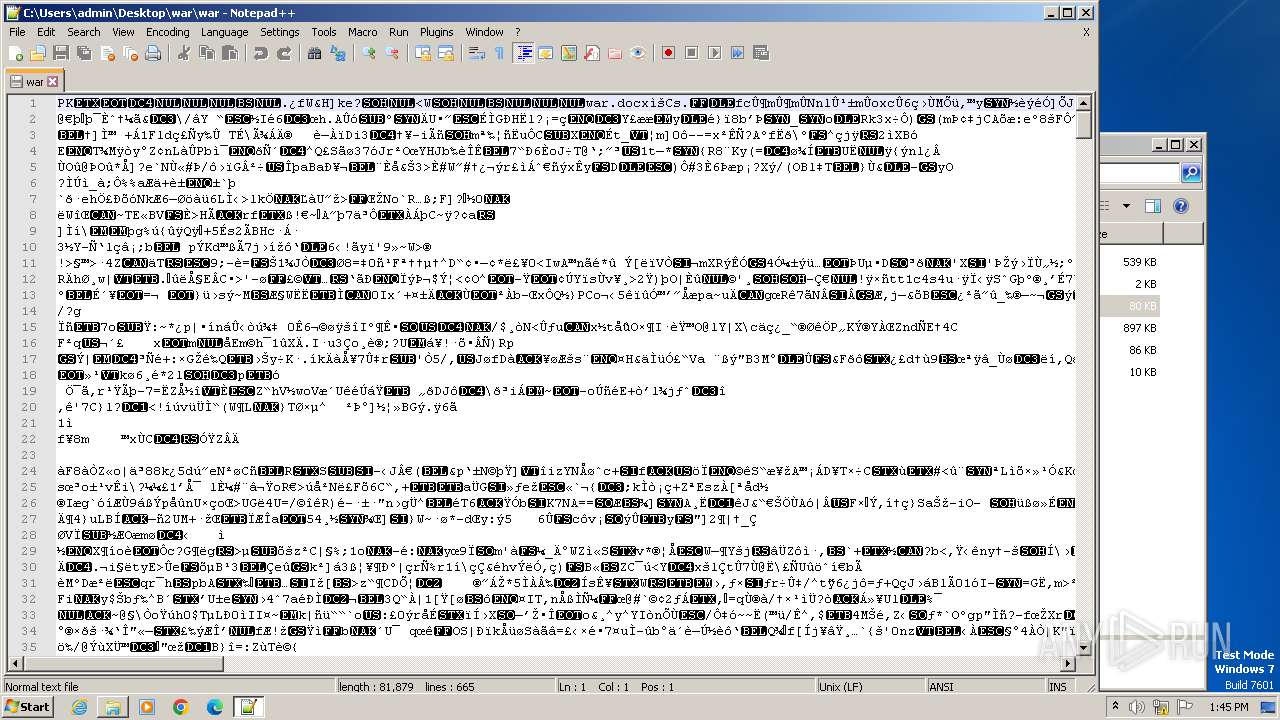
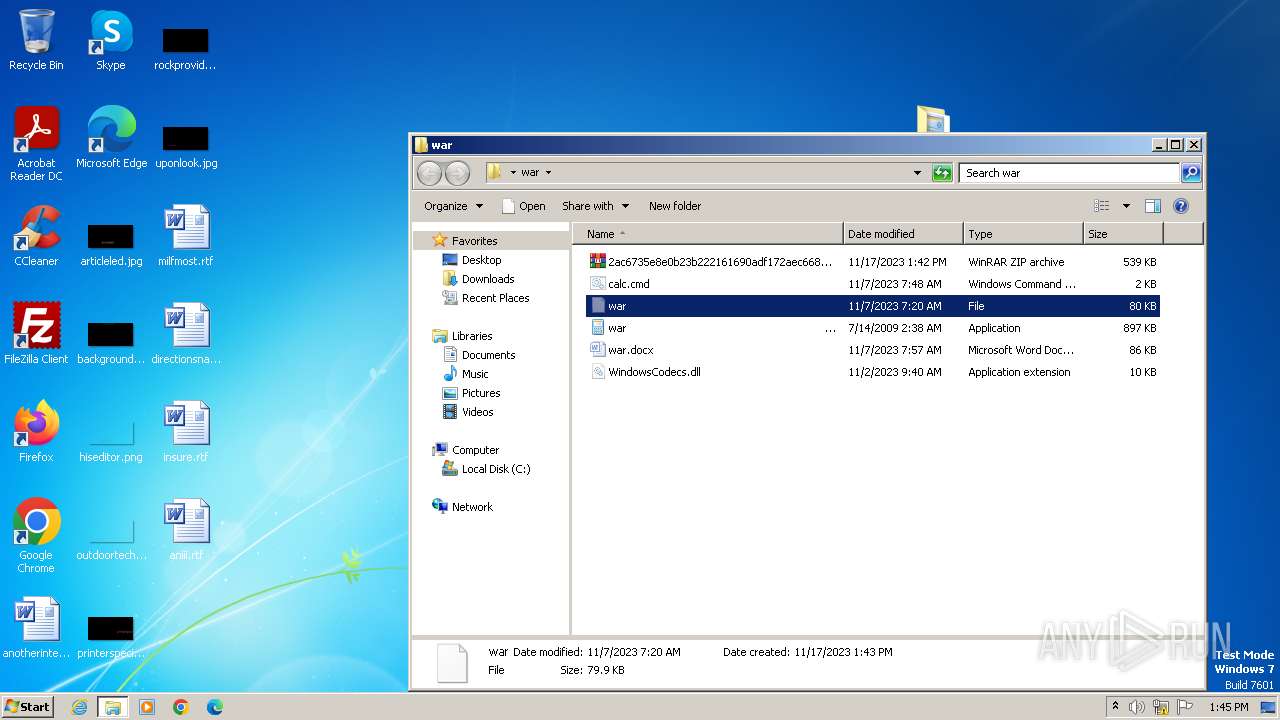
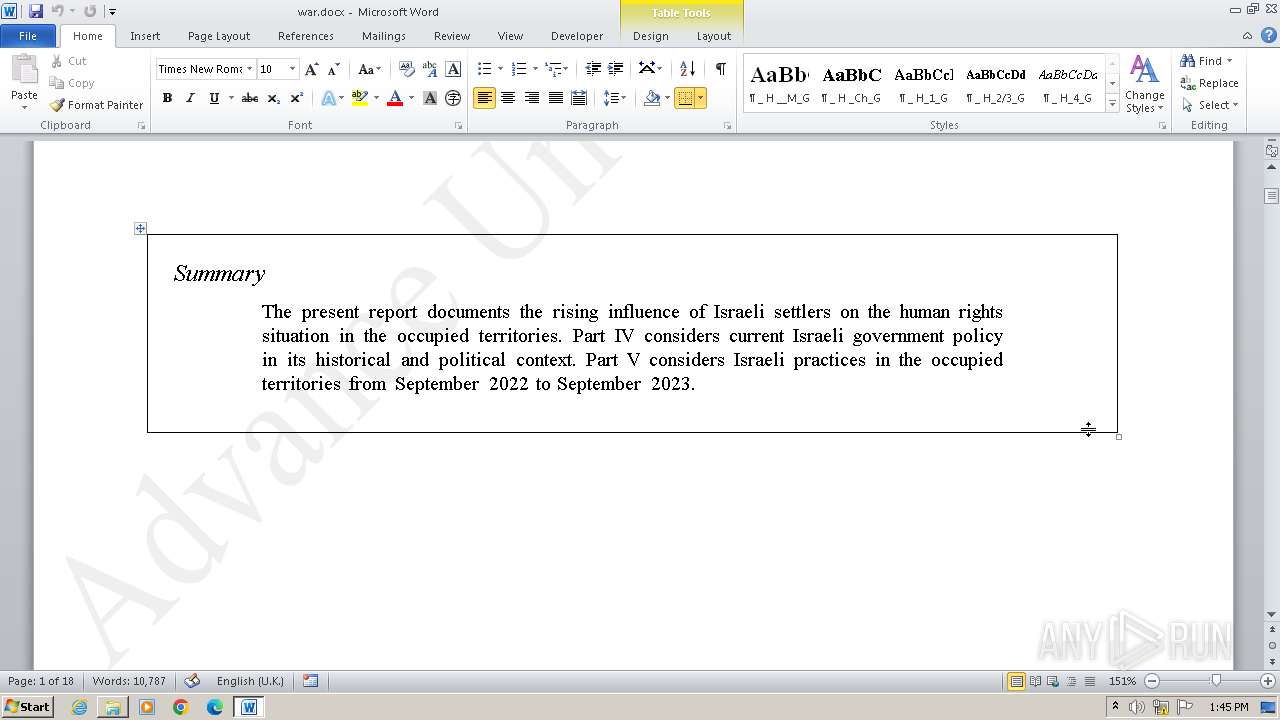
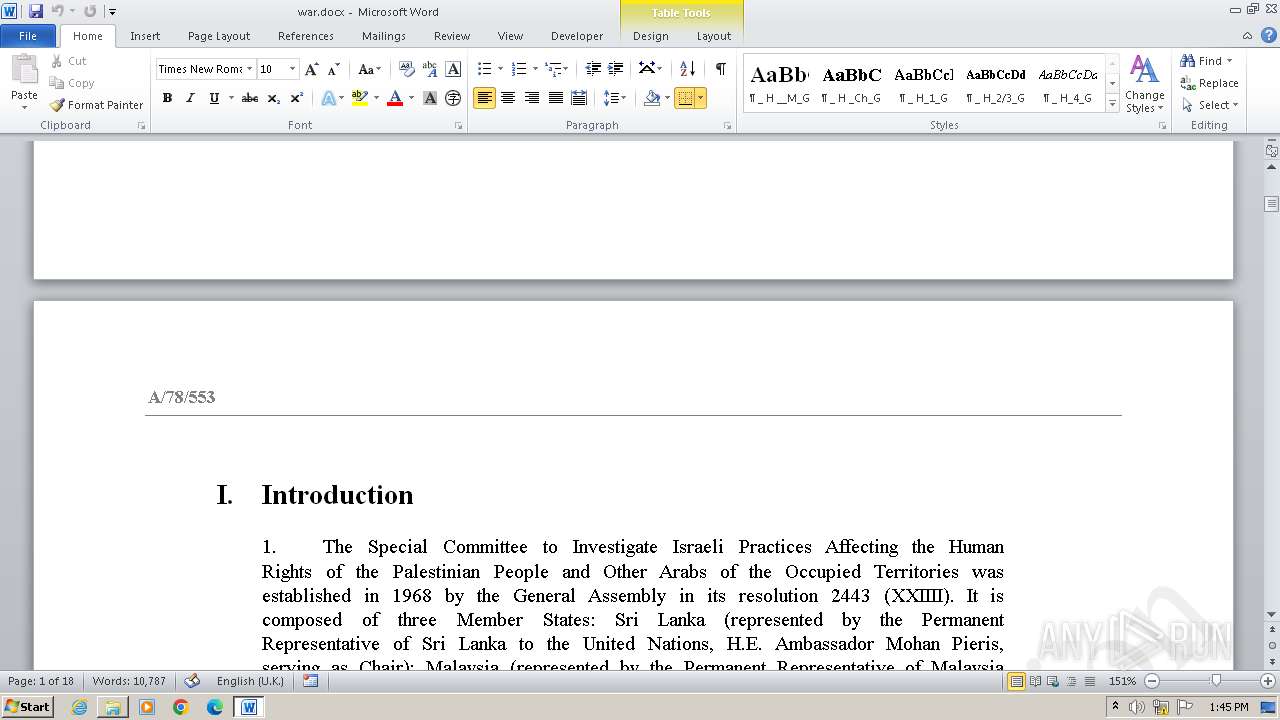
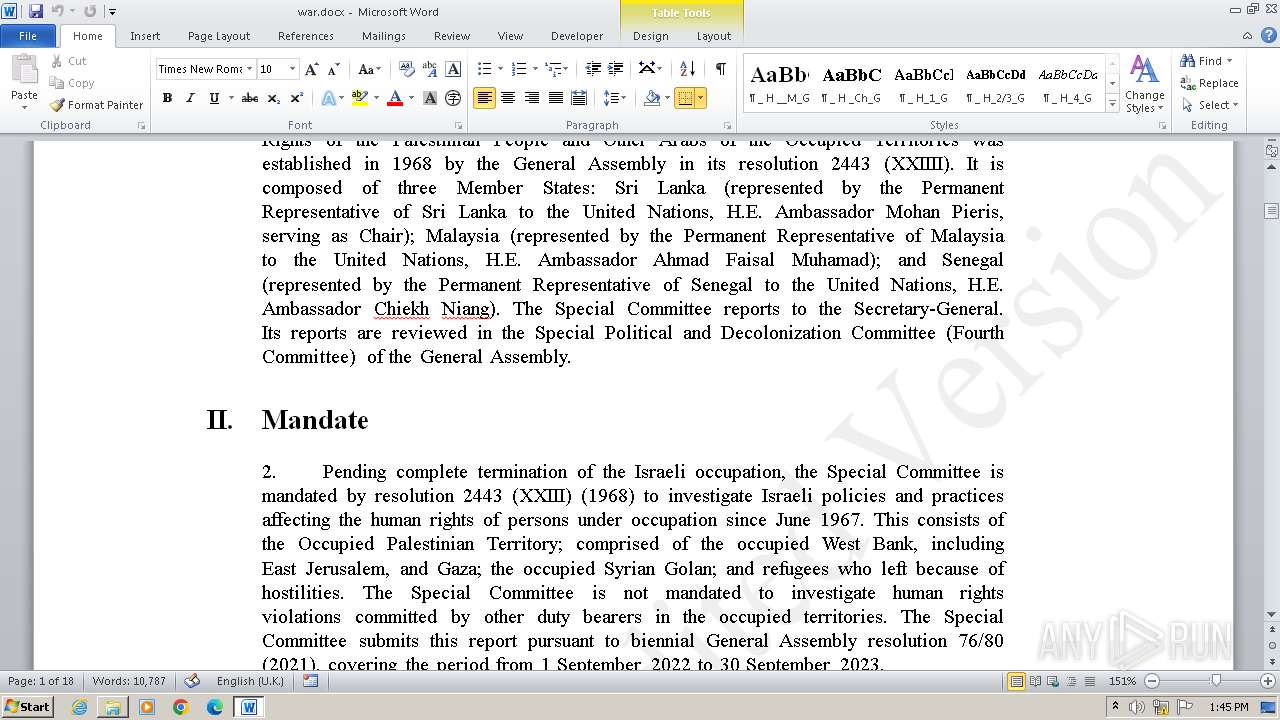
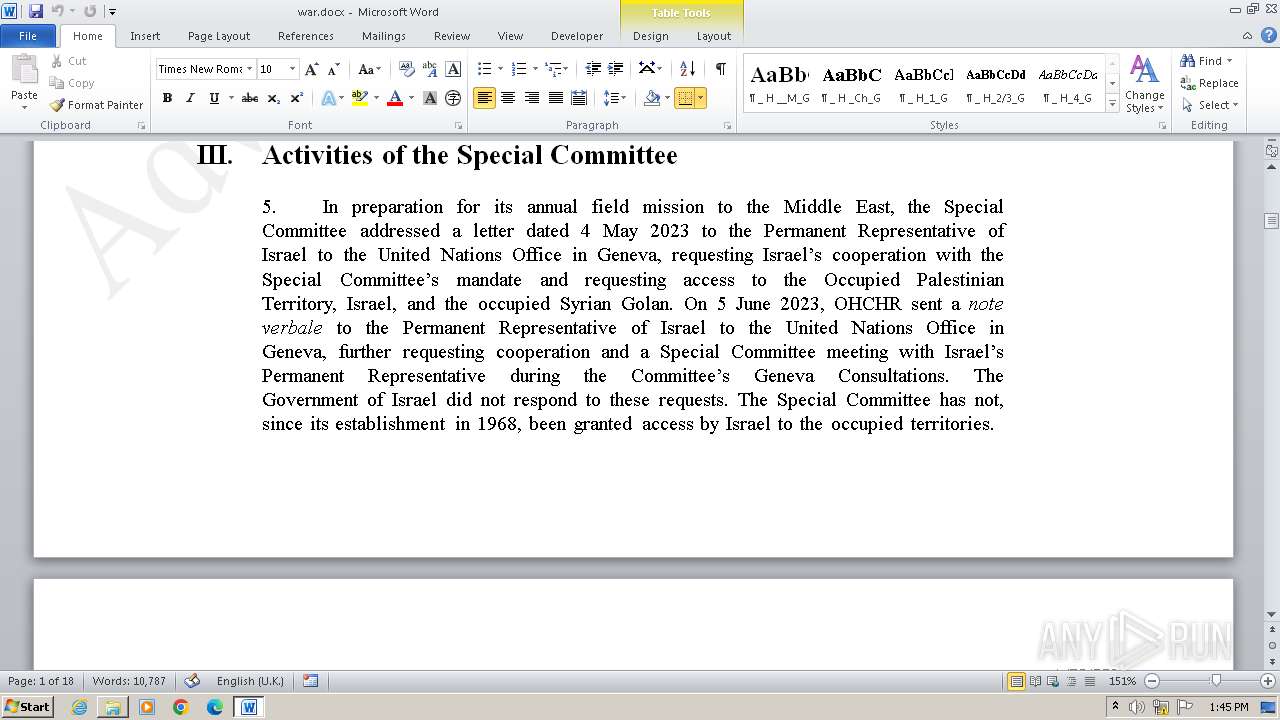
| File name: | 12993716564.zip |
| Full analysis: | https://app.any.run/tasks/800a5abb-a0a6-4d95-9d9e-15716100c9b5 |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2023, 13:42:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8E16006218C42723F651751D1167AC43 |
| SHA1: | 133D9F558F4C020AA7C3F6C756E68B35D46C9AF8 |
| SHA256: | 4F37078A27873D3C71C1F60E8D9FE9957AF70AC6B7565DEE284B02A3AD6B5F34 |
| SSDEEP: | 24576:LIbAGzQcSdMo229gPJmcae0Gqr5jDVGSn7zevkR2QGLYxdWZE4D84RD:LIbAGzQcSdMd29gPJmcae0Gqr1VGSn7I |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3880)
Starts application with an unusual extension
- cmd.exe (PID: 2636)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 284)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2328)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2636)
Reads the Internet Settings
- wscript.exe (PID: 2328)
- cmd.exe (PID: 284)
The process executes VB scripts
- cmd.exe (PID: 284)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2328)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 284)
Executing commands from a ".bat" file
- wscript.exe (PID: 2328)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3880)
- WinRAR.exe (PID: 1944)
- cmd.exe (PID: 284)
- notepad++.exe (PID: 1032)
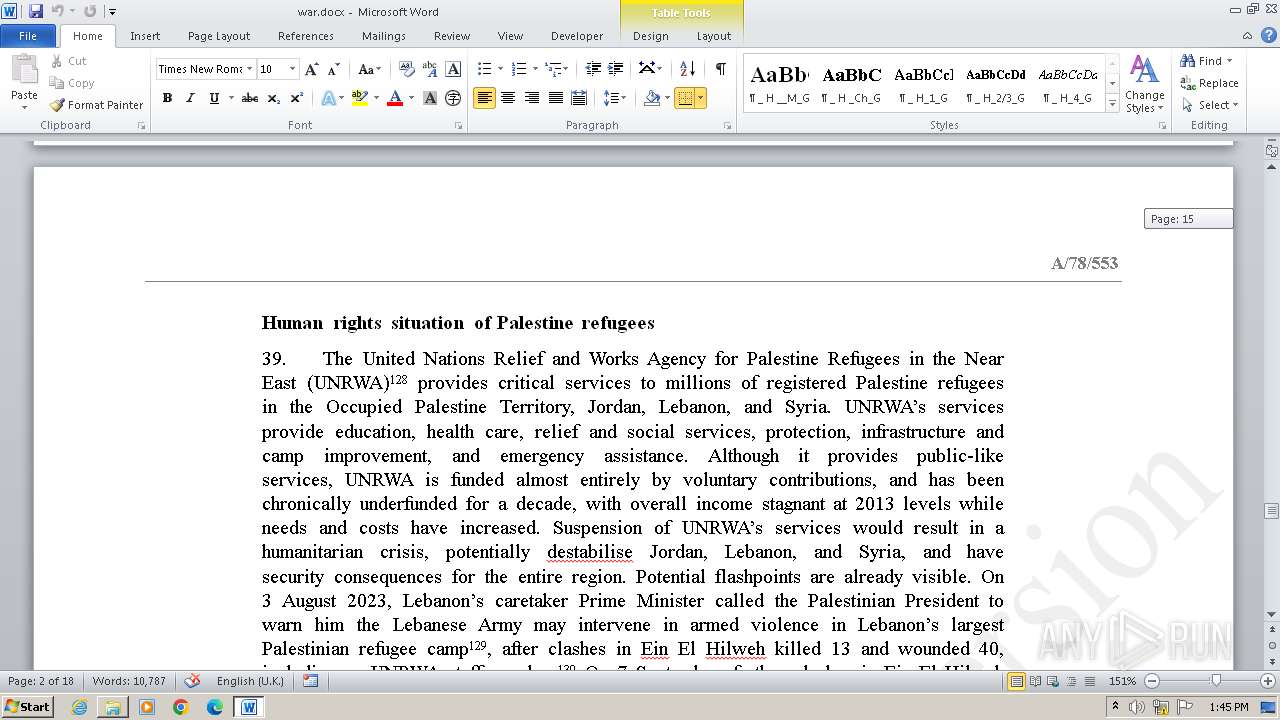
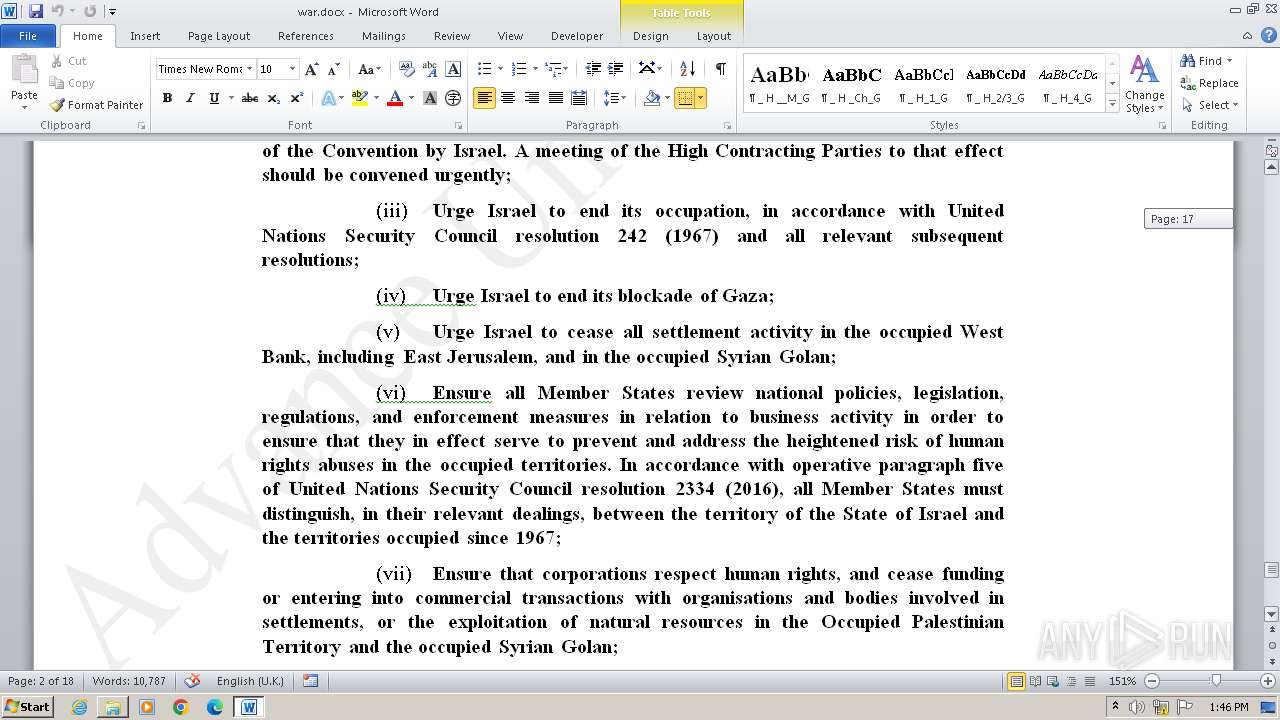
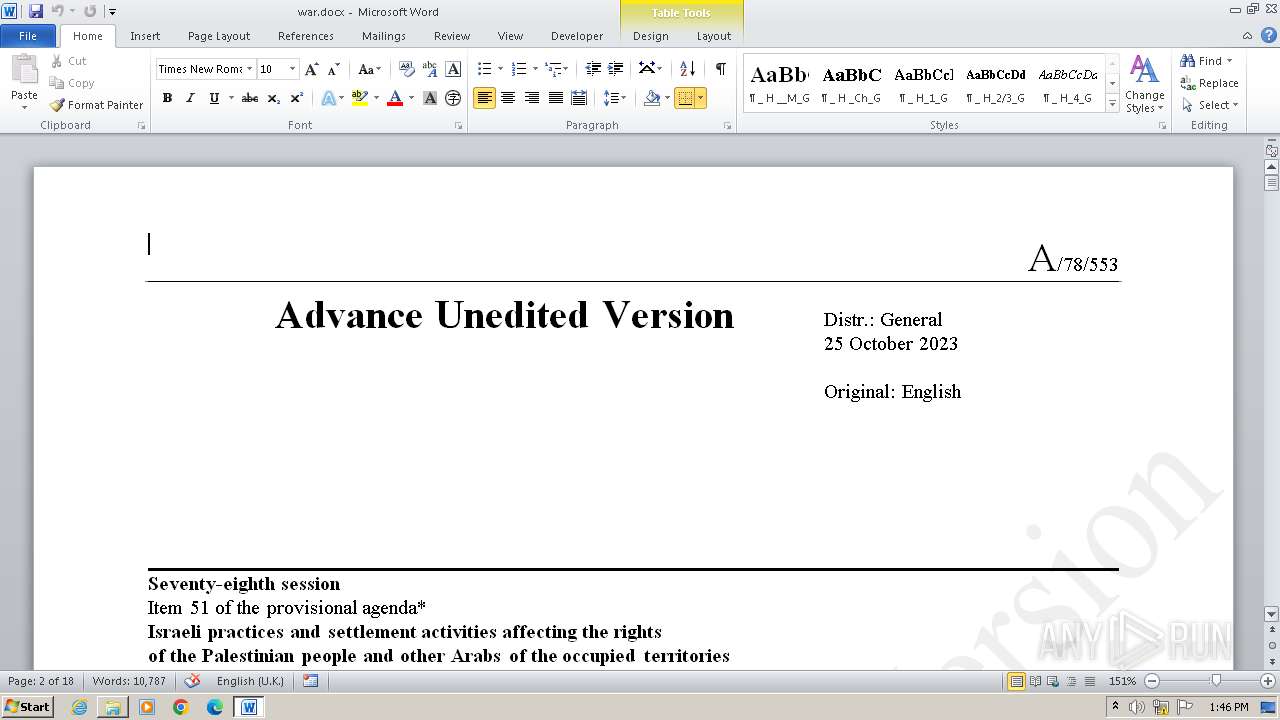
- WINWORD.EXE (PID: 3708)
- wmpnscfg.exe (PID: 2880)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3880)
Checks supported languages
- wmpnscfg.exe (PID: 2880)
- chcp.com (PID: 2532)
Creates files in the program directory
- cmd.exe (PID: 284)
Reads the computer name
- wmpnscfg.exe (PID: 2880)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xc1c4d26c |
| ZipCompressedSize: | 550618 |
| ZipUncompressedSize: | 551418 |
| ZipFileName: | 2ac6735e8e0b23b222161690adf172aec668894d170299e9ff2c54a4ec25b1f4 |
Total processes
66
Monitored processes
14
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | attrib -h -r /s | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\war\calc.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\war\war" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\war\war.zip" C:\Users\admin\Desktop\war\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 10 Version: 5.91.0 Modules
| |||||||||||||||
| 2328 | "C:\Windows\System32\WScript.exe" "C:\ProgramData\6a98168f-f14f-4014-8b28-8329b0118936.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2532 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | taskkill /F /IM "war .EXE" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2636 | C:\Windows\system32\cmd.exe /c ""C:\ProgramData\6a98168f-f14f-4014-8b28-8329b0118936.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2688 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\war\war.docx" | C:\program files\microsoft office\Office14\WINWORD.EXE | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2880 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
28 828
Read events
18 481
Write events
10 015
Delete events
332
Modification events
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
3
Suspicious files
18
Text files
13
Unknown types
0
Dropped files
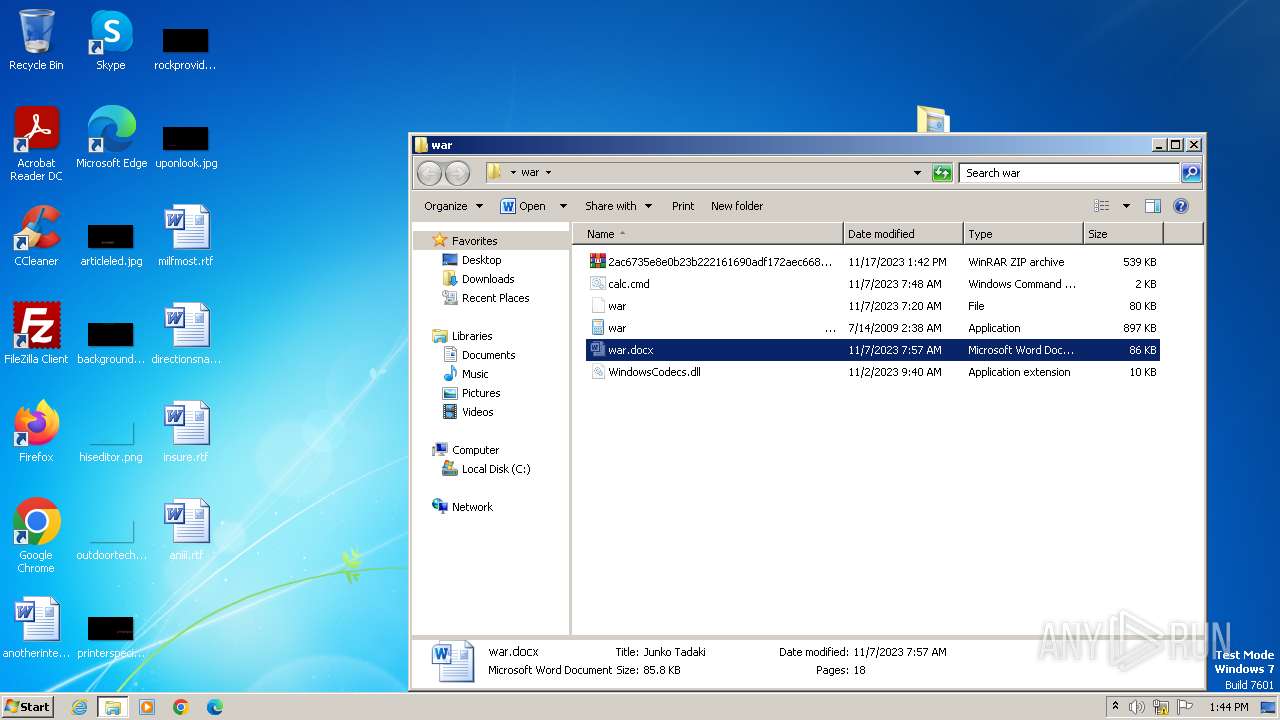
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB486.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{49A05F7F-567D-4E12-912A-791E47FFCA19}.tmp | binary | |
MD5:0F4C51A4EFD78D6758C89681C48582FA | SHA256:B7A6713E12B1D6B08A5DC0600C529D07DA2D48DF57914496C42383D1BB7AB9B2 | |||
| 2688 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR85A1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
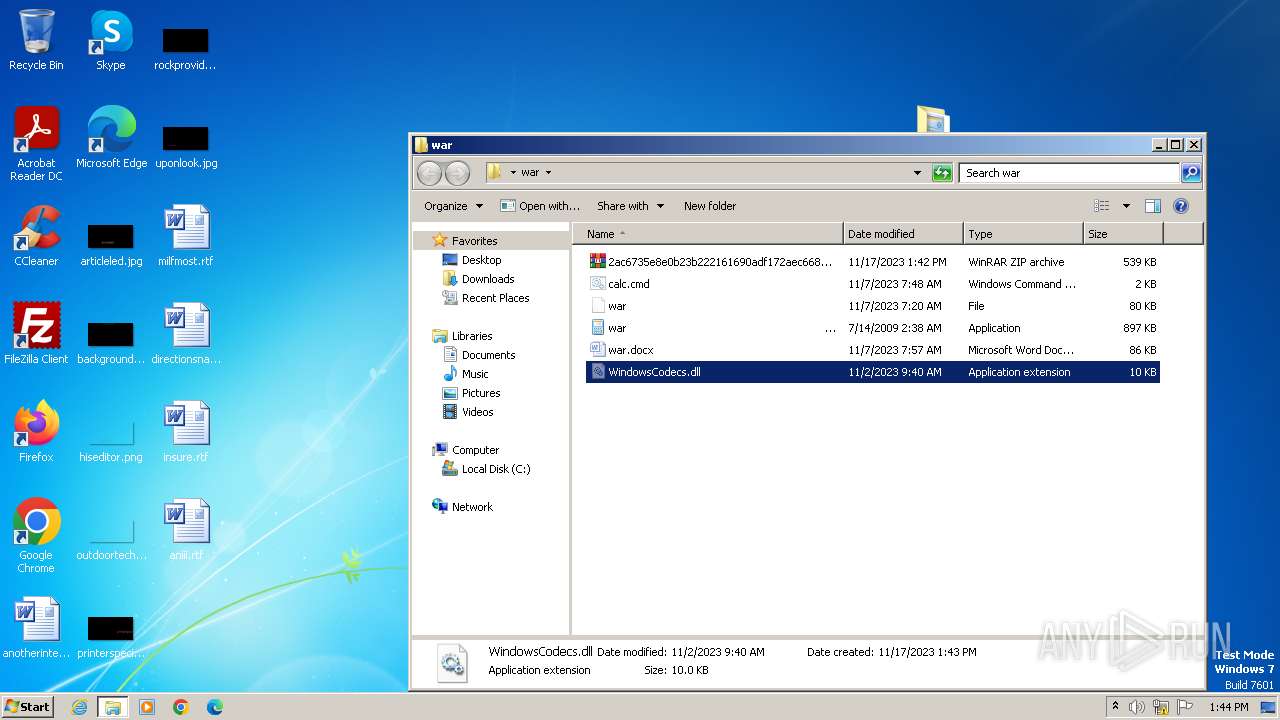
| 3880 | WinRAR.exe | C:\Users\admin\Desktop\war\WindowsCodecs.dll | executable | |
MD5:C7B906017453F3CE54DA40A98C1A55AB | SHA256:47074A6D033966D07E4587705401533AD6C5FA2B11303C520A37999337D1A1EB | |||
| 3880 | WinRAR.exe | C:\Users\admin\Desktop\war\calc.cmd | text | |
MD5:FE2A3F3CC663EB4A9D985D9F8E0E3A7D | SHA256:103ADB71848A31021692F5BA2EF1691EB29F3DED81B86954753F2F2FBEDA08A7 | |||
| 3708 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
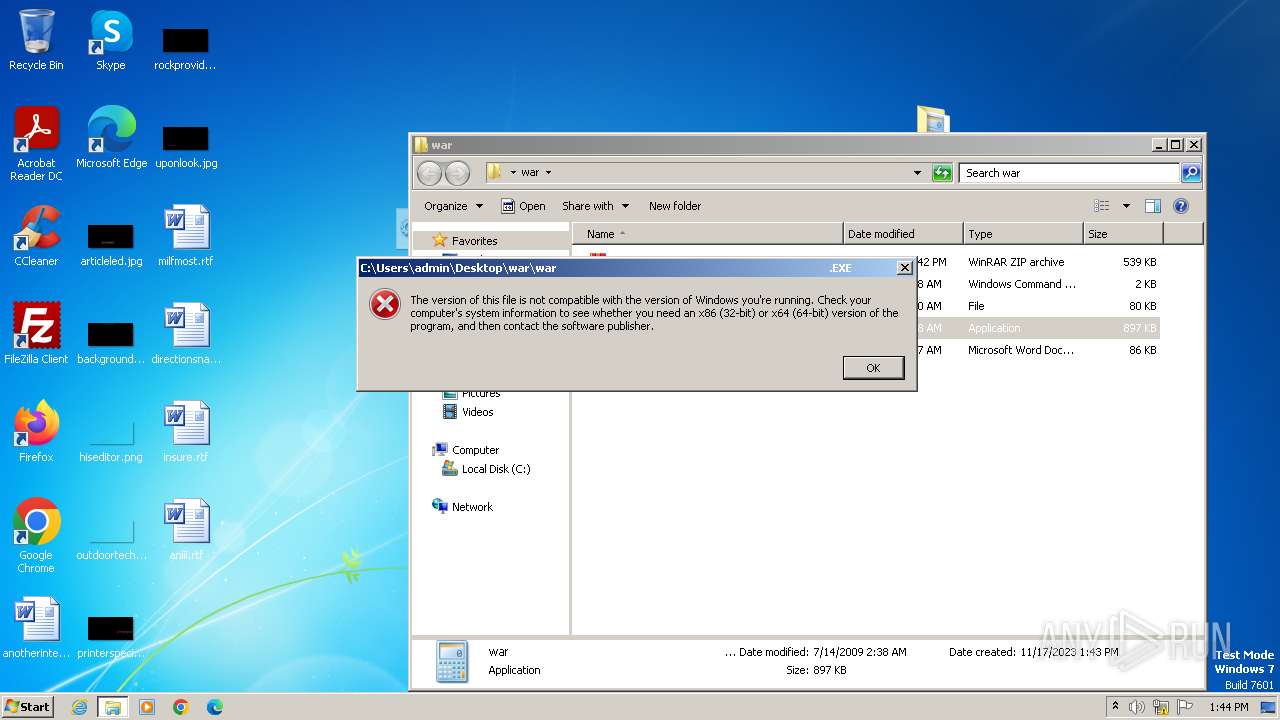
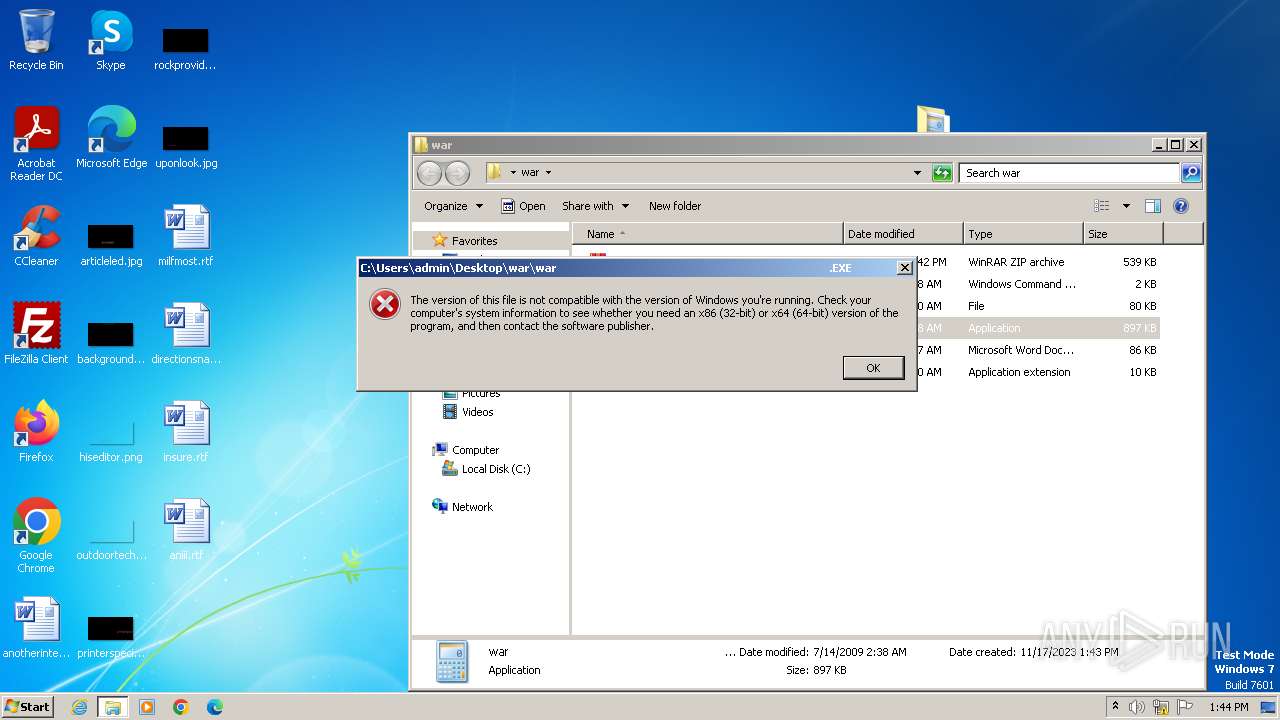
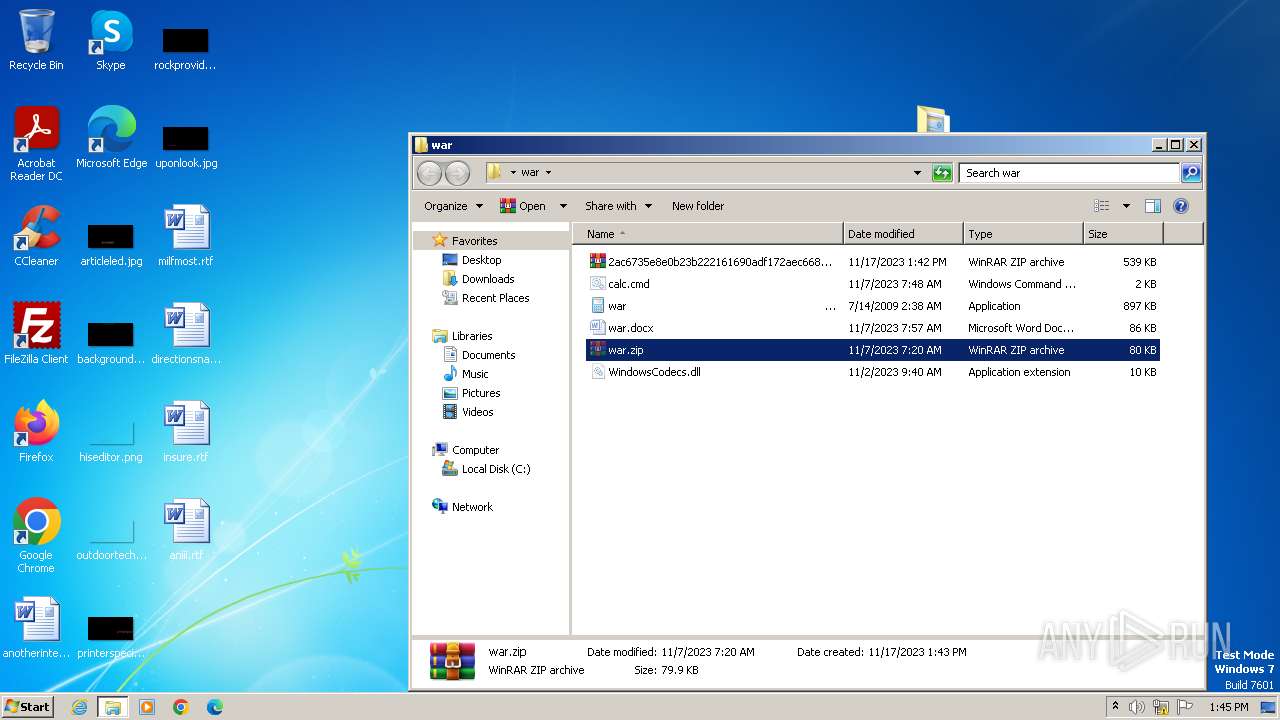
| 3880 | WinRAR.exe | C:\Users\admin\Desktop\war\war .EXE | executable | |
MD5:10E4A1D2132CCB5C6759F038CDB6F3C9 | SHA256:C6A91CBA00BF87CDB064C49ADAAC82255CBEC6FDD48FD21F9B3B96ABF019916B | |||
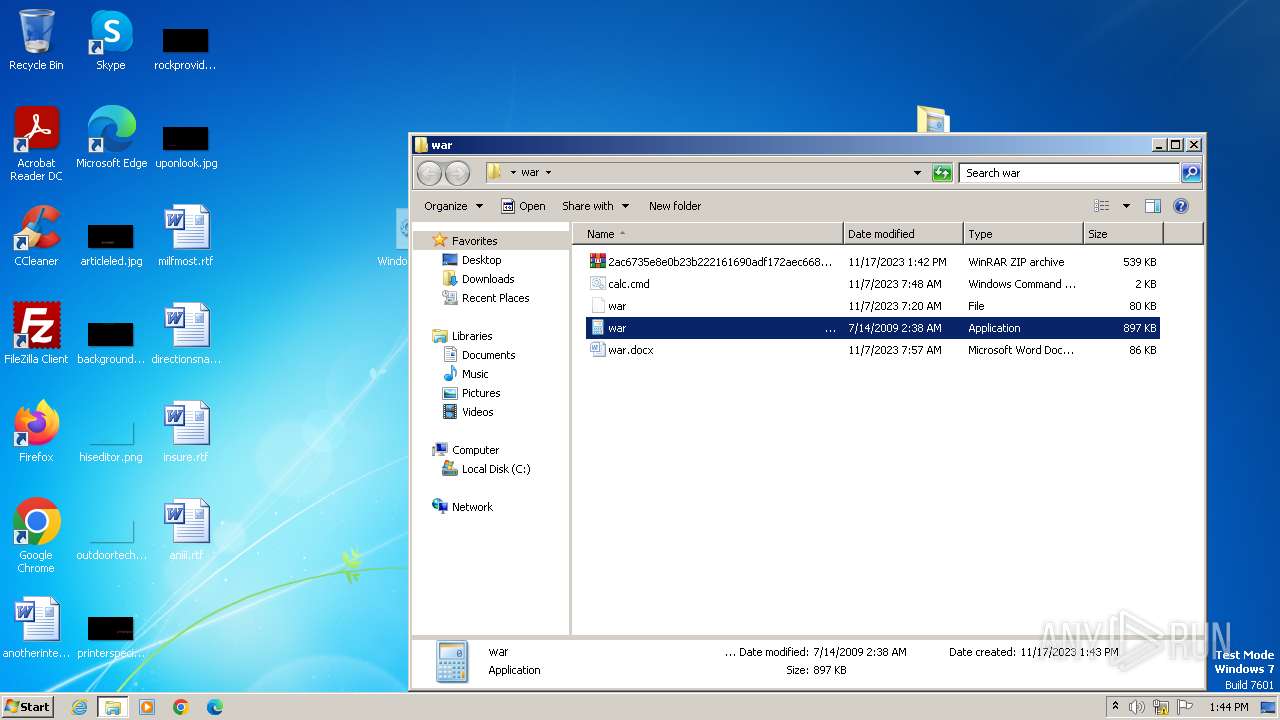
| 3880 | WinRAR.exe | C:\Users\admin\Desktop\war\war | compressed | |
MD5:B66CB10E6ADC64FAF3269E0AF489ED38 | SHA256:8CC664FF412FC80485D0AF61FB0617F818D37776E5A06B799F74FE0179B31768 | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3372.4200\2ac6735e8e0b23b222161690adf172aec668894d170299e9ff2c54a4ec25b1f4 | compressed | |
MD5:C6AA26343C8E716EA0304EEB26C93BED | SHA256:2AC6735E8E0B23B222161690ADF172AEC668894D170299E9FF2C54A4EC25B1F4 | |||
| 3708 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{2C266A23-AA88-4D64-A88F-B622A4ADFDC4}.tmp | image | |
MD5:CFC4A3ADB4546CFC67568096ED48192C | SHA256:FEF806D4DF0E2BCDF56A5ABBDADD05EC2590A140176616D2A29A6D89AA70C5F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2688 | WINWORD.EXE | GET | 200 | 52.109.32.97:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={019C826E-445A-4649-A5B0-0BF08FCC4EEE}&build=14.0.6023 | unknown | xml | 1.96 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2688 | WINWORD.EXE | 52.109.32.97:80 | office14client.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
2688 | WINWORD.EXE | 52.109.124.67:443 | rr.office.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
office14client.microsoft.com |
| whitelisted |
rr.office.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|