| download: | electrum-3.1.3.exe |
| Full analysis: | https://app.any.run/tasks/27b31c9b-ba7d-4e56-ae4e-bdde1a511e0f |
| Verdict: | Malicious activity |
| Analysis date: | June 30, 2018, 00:27:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A569212983A81B9B7F8DF8F0157BF737 |
| SHA1: | 3E5E7280328F87A751D8083608CF47AB325A4EEC |
| SHA256: | 4F2E0B548E1A8E7B8CC37B55EF4FDC663F93D20008F5B7948ED8CFAFBCE9B4C9 |
| SSDEEP: | 393216:DtjPxKXkIDAwspzl0WmMHPi7g8/A3+v6s+ruhaZ5HGlsPUNhm8Nnwx2ayXmx5gAl:1wXql07MH6R/A3+ys+tyNhrW2LQg17Ej |
MALICIOUS
Loads dropped or rewritten executable
- electrum-3.1.3.exe (PID: 1952)
SUSPICIOUS
Application launched itself
- electrum-3.1.3.exe (PID: 3240)
Creates files in the user directory
- electrum-3.1.3.exe (PID: 1952)
Connects to unusual port
- electrum-3.1.3.exe (PID: 1952)
Executable content was dropped or overwritten
- electrum-3.1.3.exe (PID: 3240)
INFO
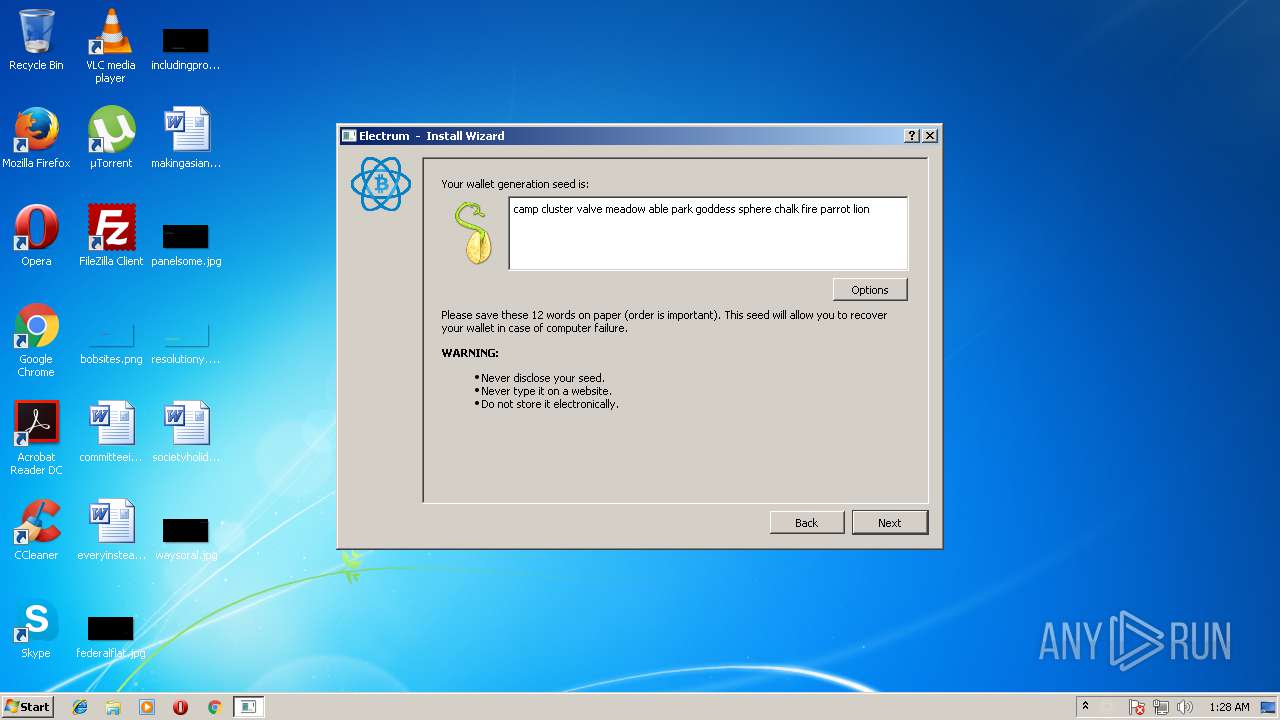
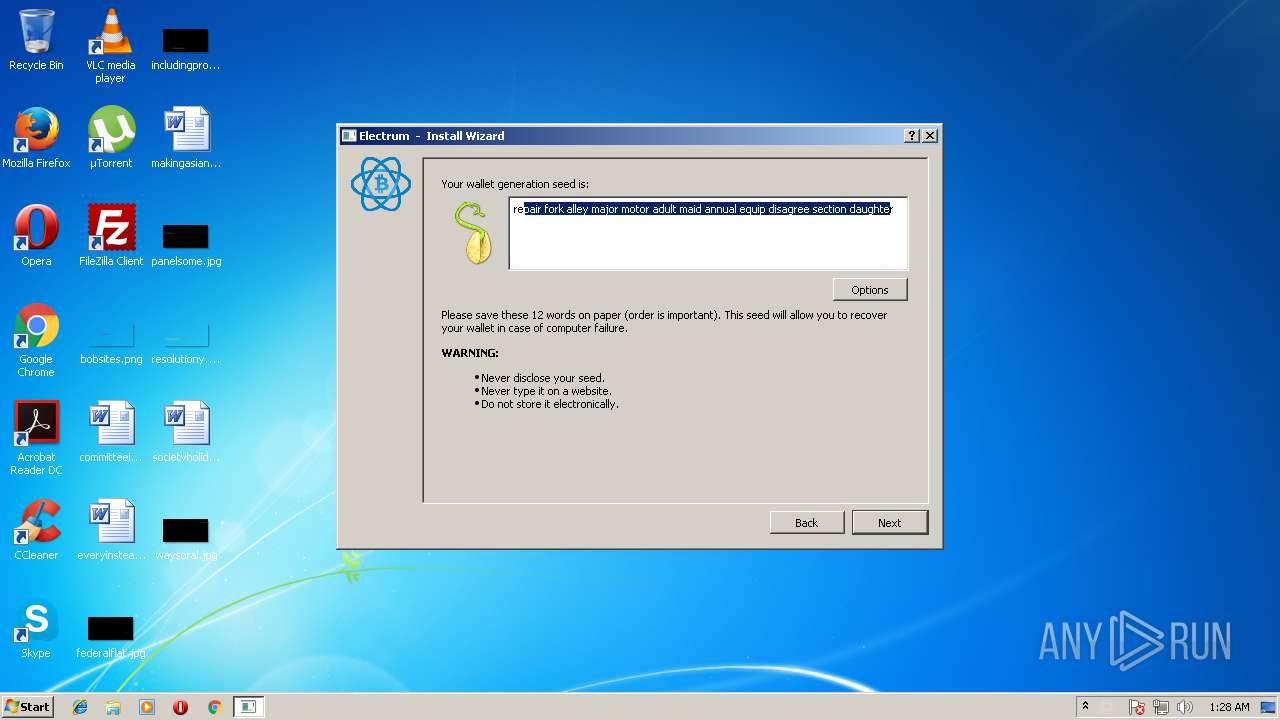
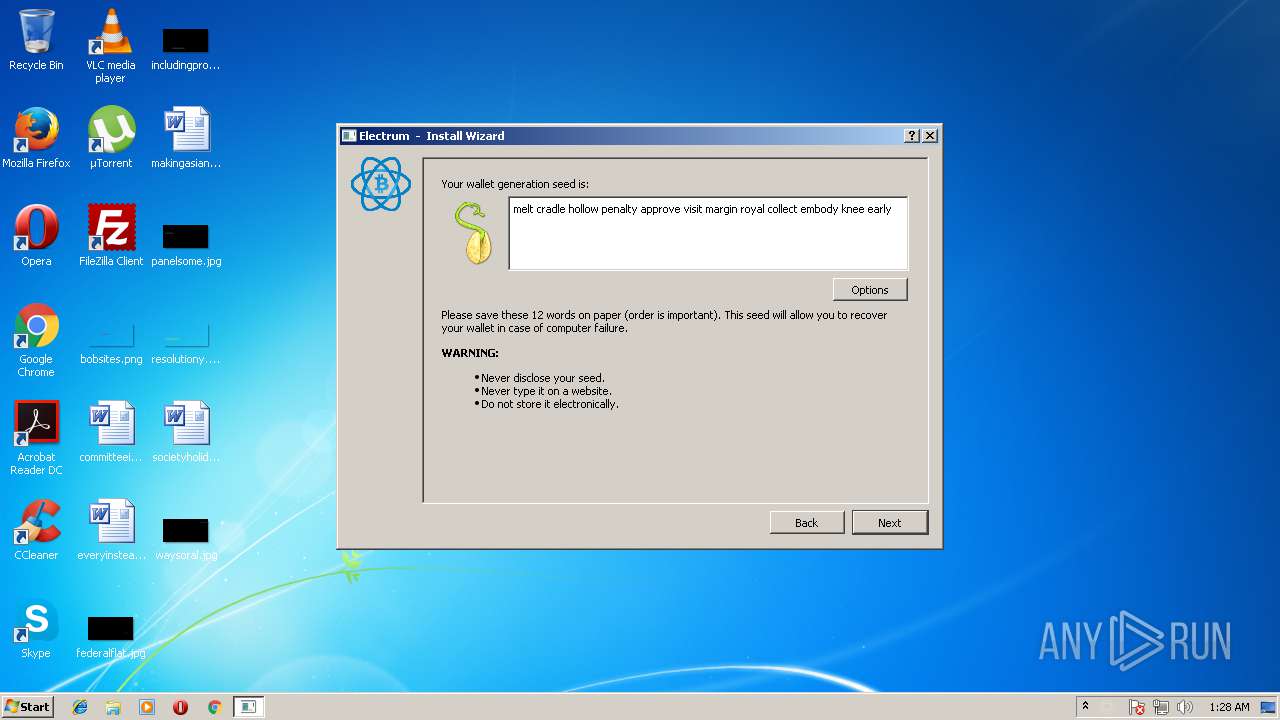
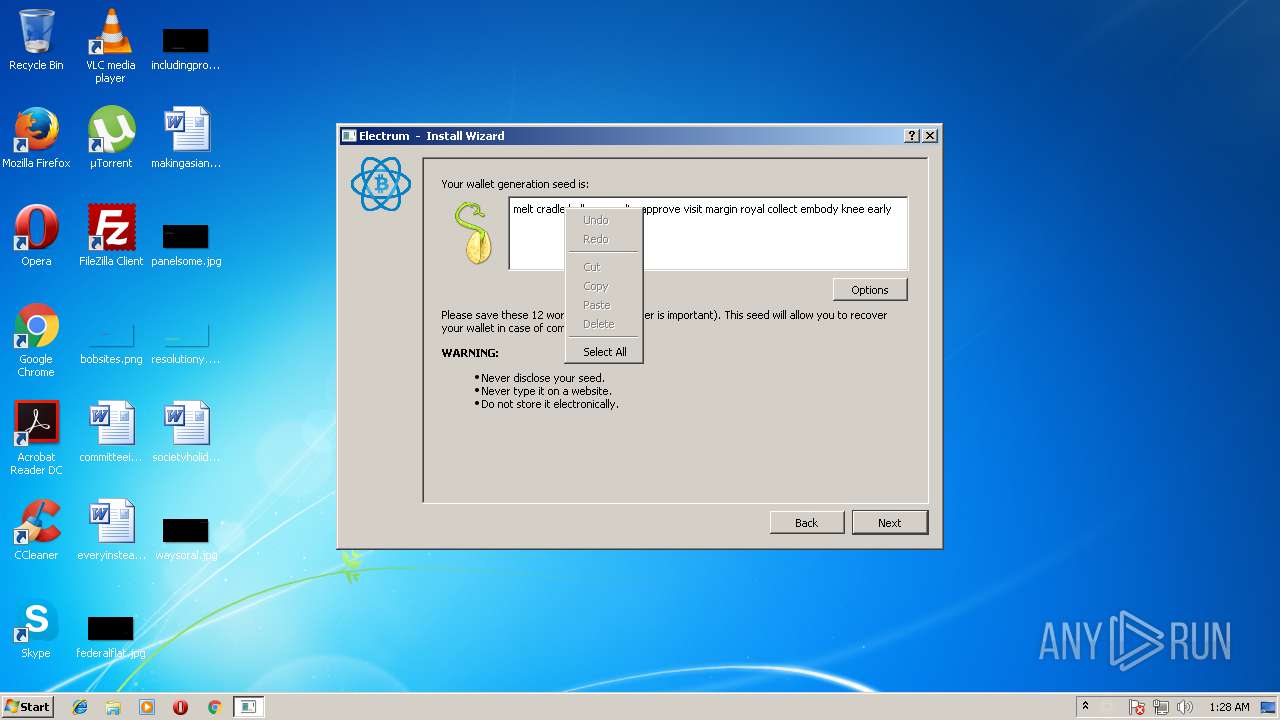
Dropped object may contain Bitcoin addresses
- electrum-3.1.3.exe (PID: 1952)
- electrum-3.1.3.exe (PID: 3240)
Dropped object may contain TOR URL's
- electrum-3.1.3.exe (PID: 3240)
Reads settings of System Certificates
- electrum-3.1.3.exe (PID: 1952)
Dropped object may contain URL's
- electrum-3.1.3.exe (PID: 3240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:07:31 17:20:53+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 125440 |
| InitializedDataSize: | 107520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7873 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 31-Jul-2017 15:20:53 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 31-Jul-2017 15:20:53 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001E9D4 | 0x0001EA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65368 |
.rdata | 0x00020000 | 0x0000B0C2 | 0x0000B200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.08353 |
.data | 0x0002C000 | 0x0000E680 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.93069 |
.gfids | 0x0003B000 | 0x000000B8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.82553 |
.rsrc | 0x0003C000 | 0x0000D000 | 0x0000CE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.159 |
.reloc | 0x00049000 | 0x000017B8 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.63681 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
0 | 2.90294 | 146 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
1 | 1.734 | 296 | UNKNOWN | UNKNOWN | RT_ICON |
2 | 1.15935 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 4.17452 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 2.65167 | 744 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 2.47831 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 3.52336 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 2.66811 | 1640 | UNKNOWN | UNKNOWN | RT_ICON |
8 | 2.80722 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
9 | 3.20642 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
Imports
KERNEL32.dll |
USER32.dll |
WS2_32.dll |
Total processes
34
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
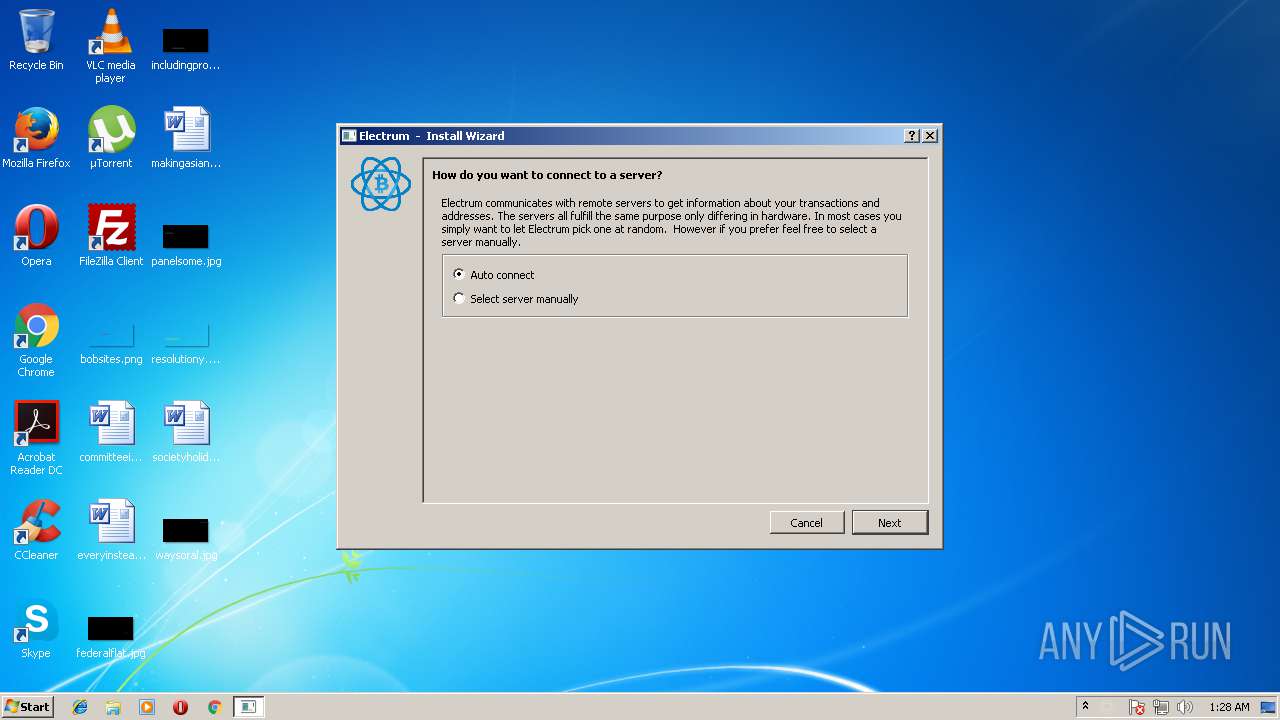
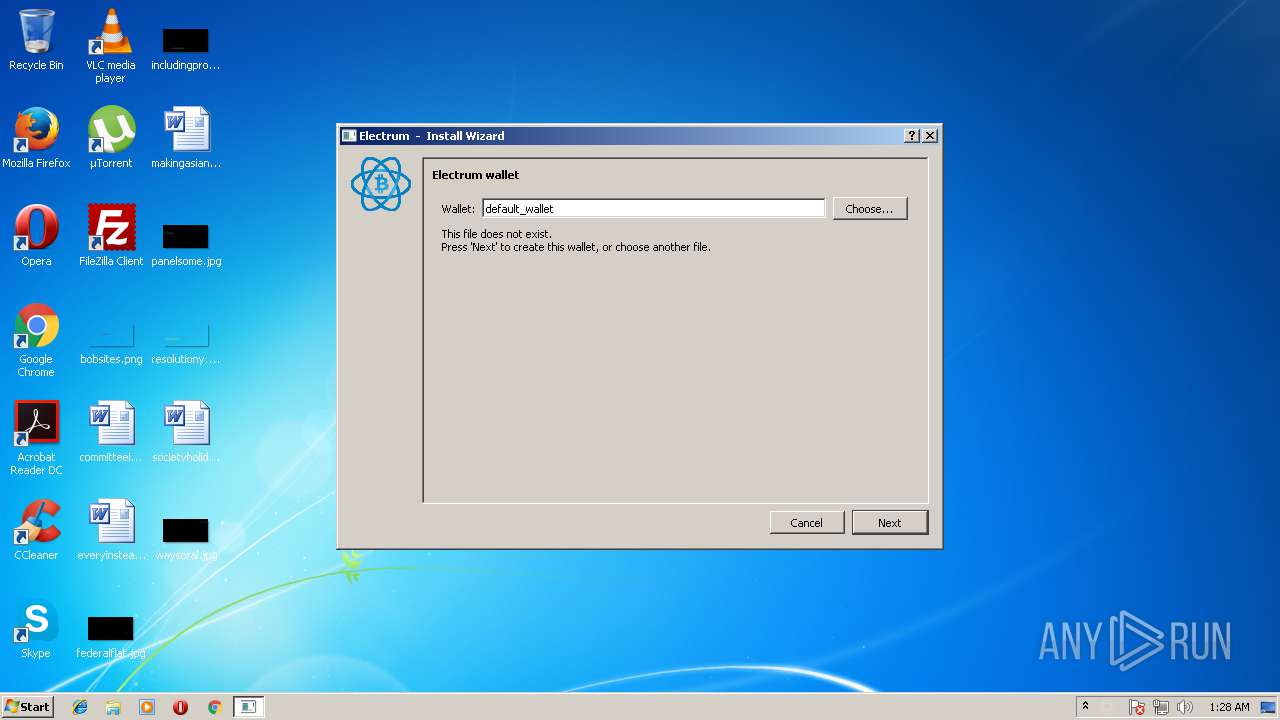
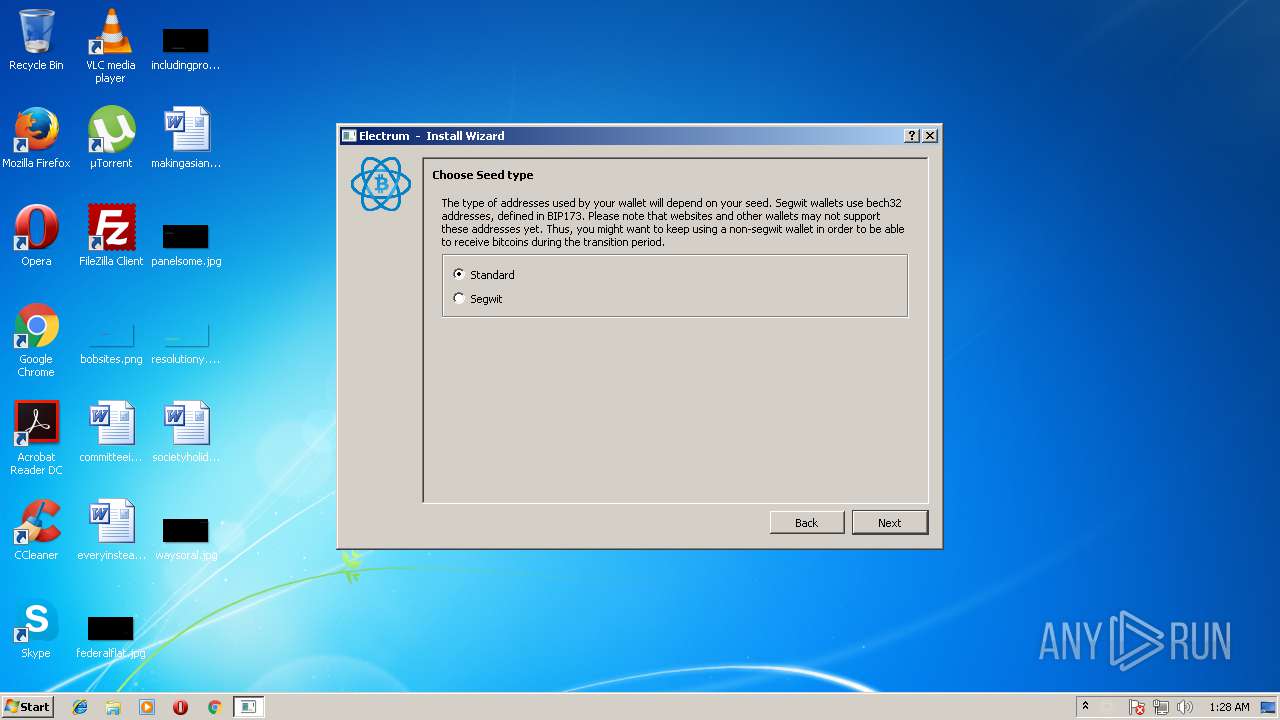
| 1952 | "C:\Users\admin\AppData\Local\Temp\electrum-3.1.3.exe" | C:\Users\admin\AppData\Local\Temp\electrum-3.1.3.exe | electrum-3.1.3.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3240 | "C:\Users\admin\AppData\Local\Temp\electrum-3.1.3.exe" | C:\Users\admin\AppData\Local\Temp\electrum-3.1.3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
248
Read events
247
Write events
1
Delete events
0
Modification events
| (PID) Process: | (1952) electrum-3.1.3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: electrum-3.1.3.exe | |||
Executable files
80
Suspicious files
36
Text files
155
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_aesni.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_arc2.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_blowfish.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_aes.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_cast.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_chacha20.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_ctr.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_cfb.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_Salsa20.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
| 3240 | electrum-3.1.3.exe | C:\Users\admin\AppData\Local\Temp\_MEI32402\Cryptodome\Cipher\_raw_cbc.cp35-win32.pyd | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
36
DNS requests
22
Threats
23
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1952 | electrum-3.1.3.exe | 79.11.31.76:50002 | electrumx.soon.it | Telecom Italia | IT | unknown |
1952 | electrum-3.1.3.exe | 88.202.202.221:50002 | electrum.villocq.com | Gigaclear PLC | GB | unknown |
1952 | electrum-3.1.3.exe | 50.35.67.146:50002 | orannis.com | Frontier Communications of America, Inc. | US | malicious |
1952 | electrum-3.1.3.exe | 212.56.108.81:50002 | electrum.poorcoding.com | British Telecommunications PLC | GB | unknown |
1952 | electrum-3.1.3.exe | 194.71.109.91:50002 | e.keff.org | Scaling Networks AB | SE | unknown |
1952 | electrum-3.1.3.exe | 109.61.102.5:50002 | electrumx.nmdps.net | Dravanet Co Ltd. | HU | unknown |
1952 | electrum-3.1.3.exe | 45.77.138.212:50002 | songbird.bauerj.eu | — | US | unknown |
1952 | electrum-3.1.3.exe | 220.233.178.199:50002 | electrum-server.ninja | Exetel Pty Ltd | AU | suspicious |
1952 | electrum-3.1.3.exe | 144.217.204.104:50002 | electrum.cutie.ga | OVH SAS | CA | unknown |
1952 | electrum-3.1.3.exe | 141.0.148.11:50002 | aspinall.io | Hyperoptic Ltd | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
electrum.poorcoding.com |
| unknown |
e.keff.org |
| unknown |
electrumx.nmdps.net |
| unknown |
hsmiths4fyqlw5xw.onion |
| unknown |
songbird.bauerj.eu |
| unknown |
de.hamster.science |
| unknown |
arihancckjge66iv.onion |
| unknown |
electrum-server.ninja |
| suspicious |
electrum.cutie.ga |
| malicious |
aspinall.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
1052 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
1052 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
1952 | electrum-3.1.3.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
1952 | electrum-3.1.3.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
1952 | electrum-3.1.3.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
1952 | electrum-3.1.3.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
1952 | electrum-3.1.3.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
1952 | electrum-3.1.3.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
Process | Message |
|---|---|
electrum-3.1.3.exe | QWindowsEGLStaticContext::create: Failed to load and resolve libEG² |
electrum-3.1.3.exe | QWindowsEGLStaticContext::create: Failed to load and resolve libEGL functions
|
electrum-3.1.3.exe | Failed to load opengl32sw.dll (The specified module could not be found.)
|
electrum-3.1.3.exe | Failed to load and resolve WGL/OpenGL functions
|