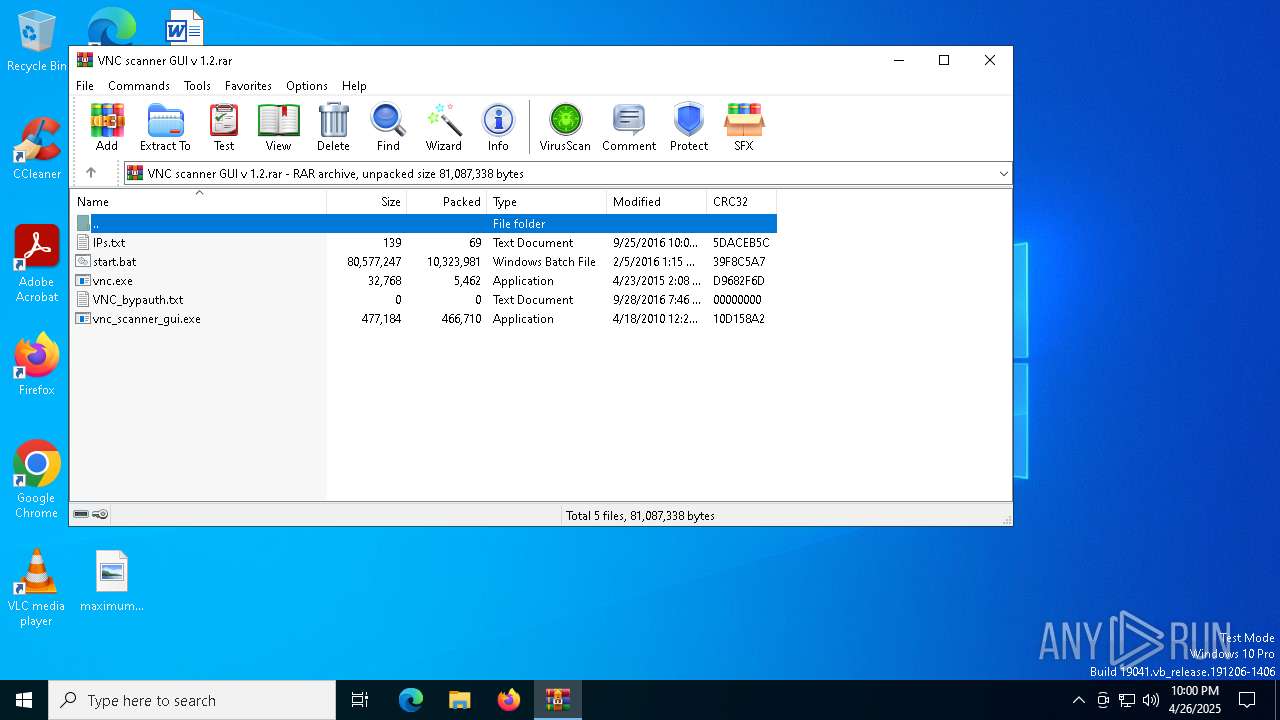
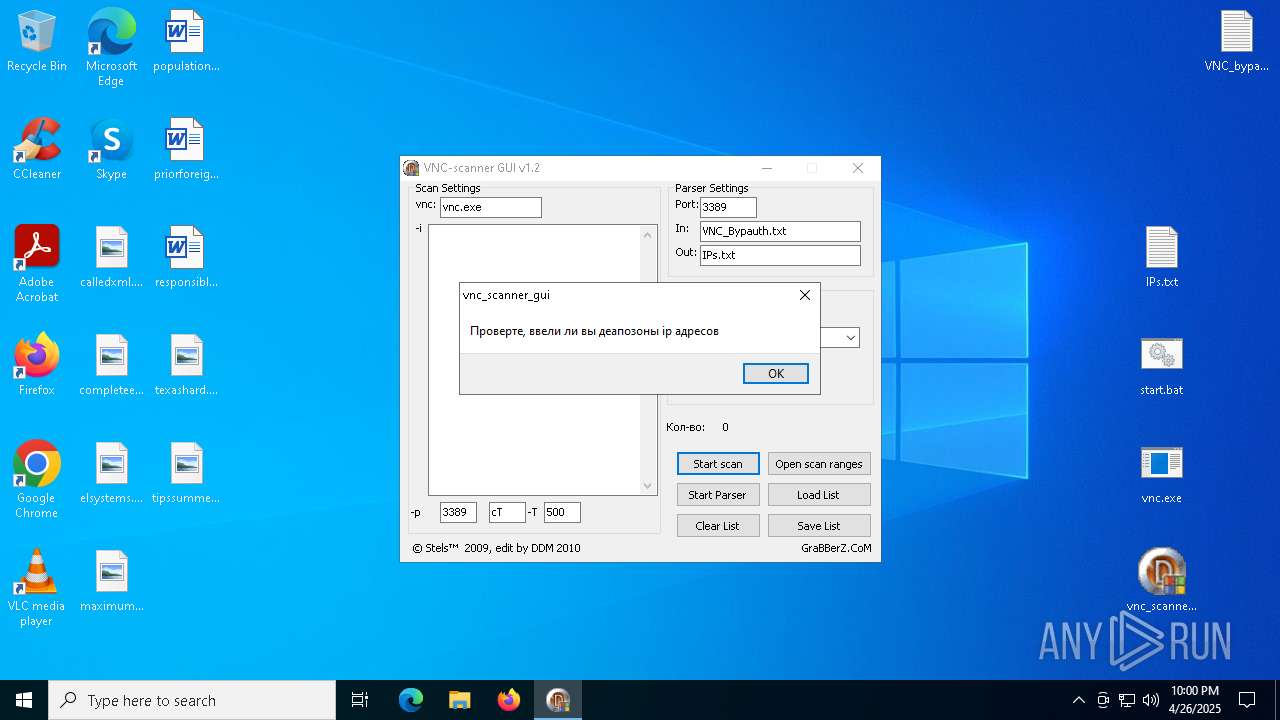
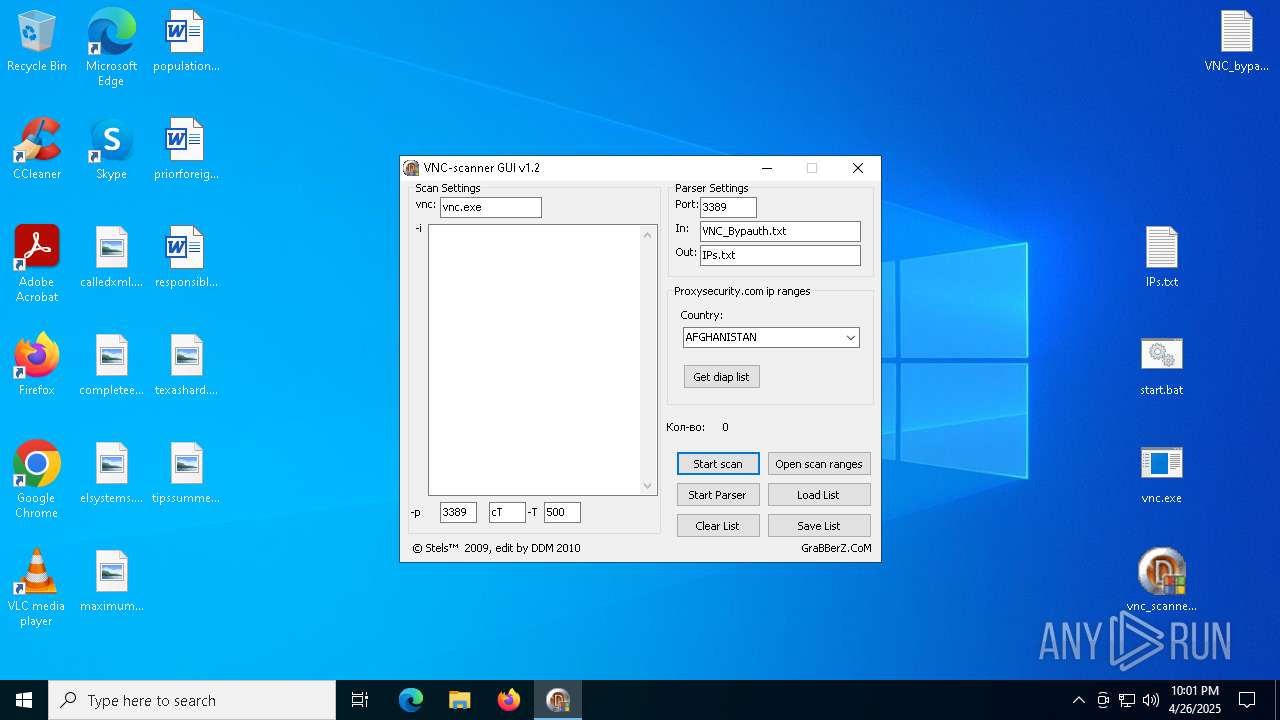
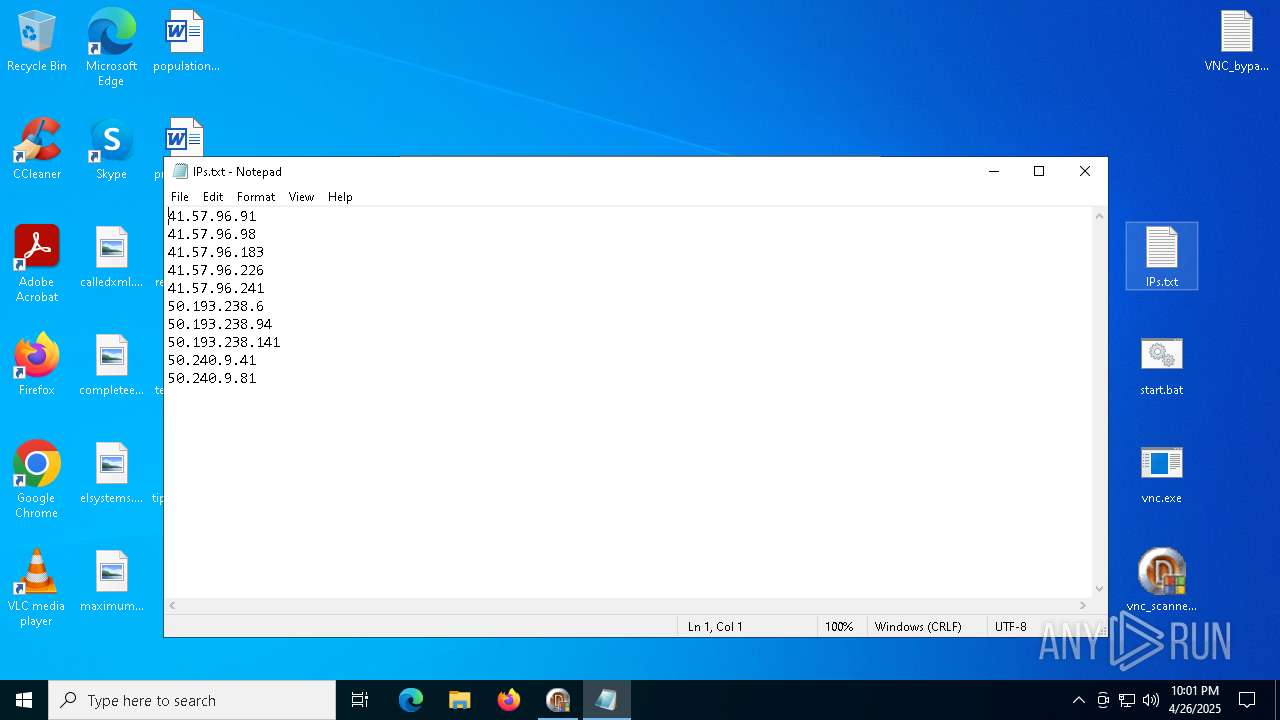
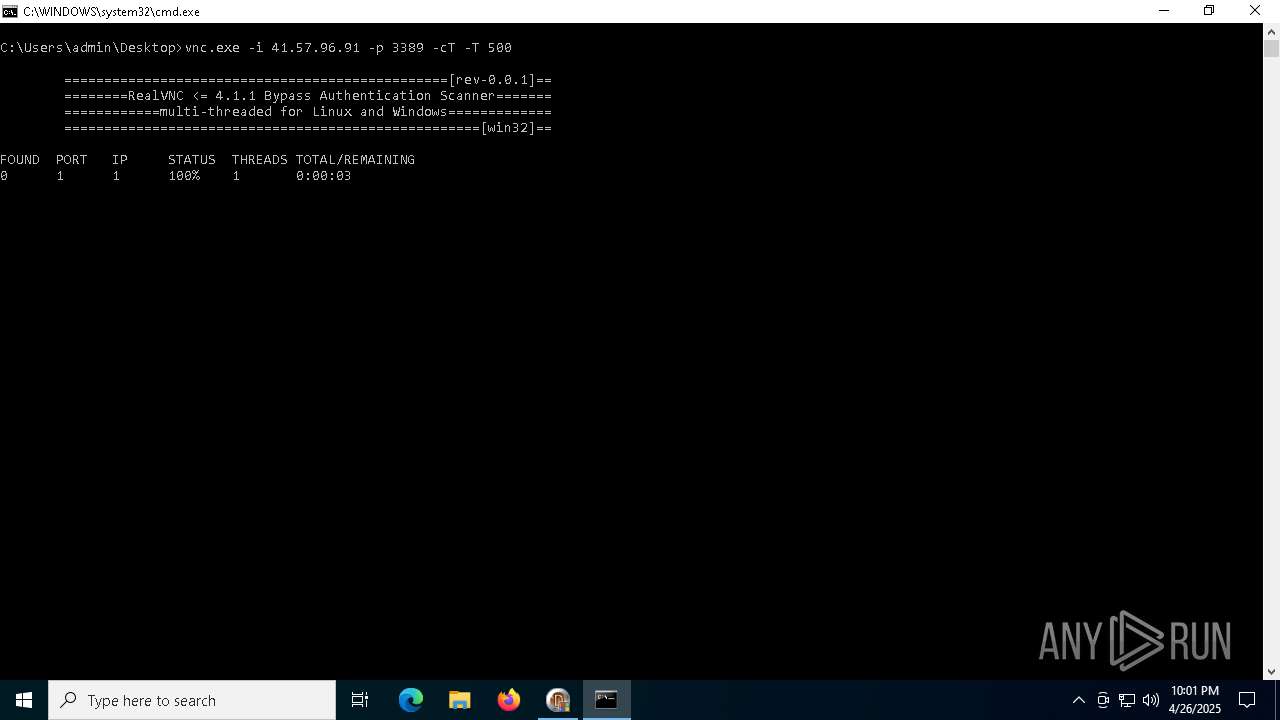
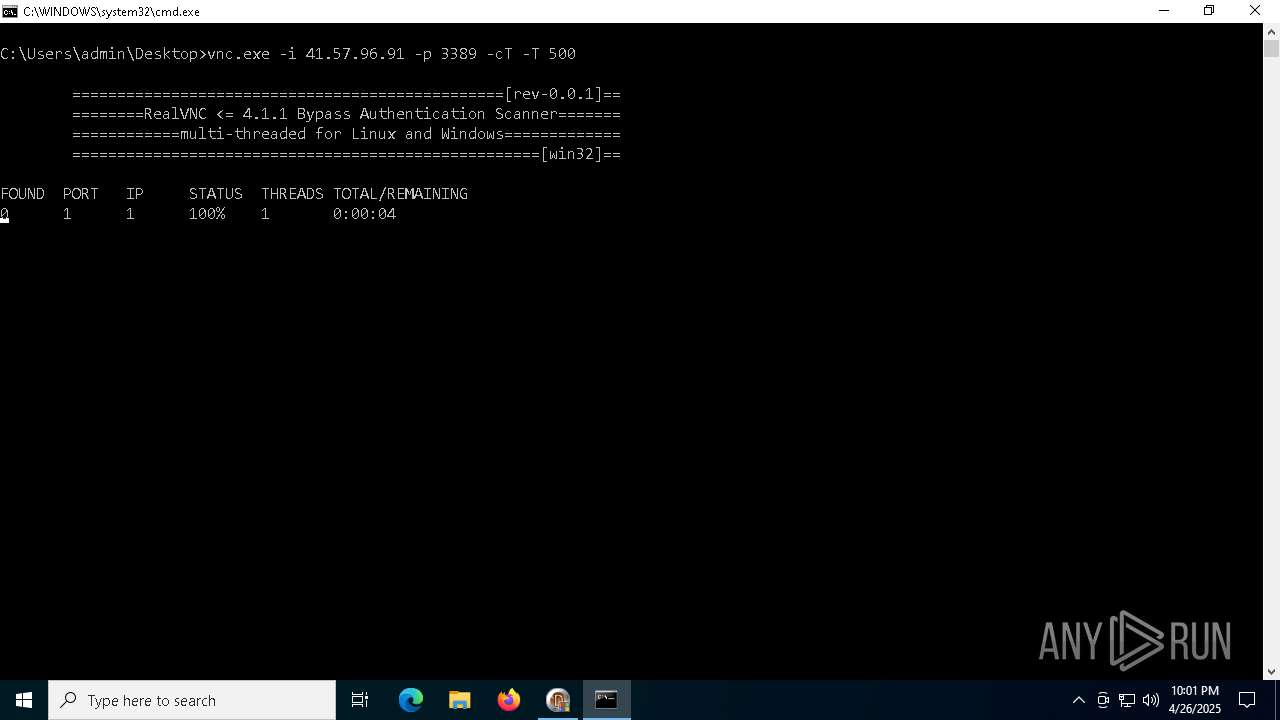
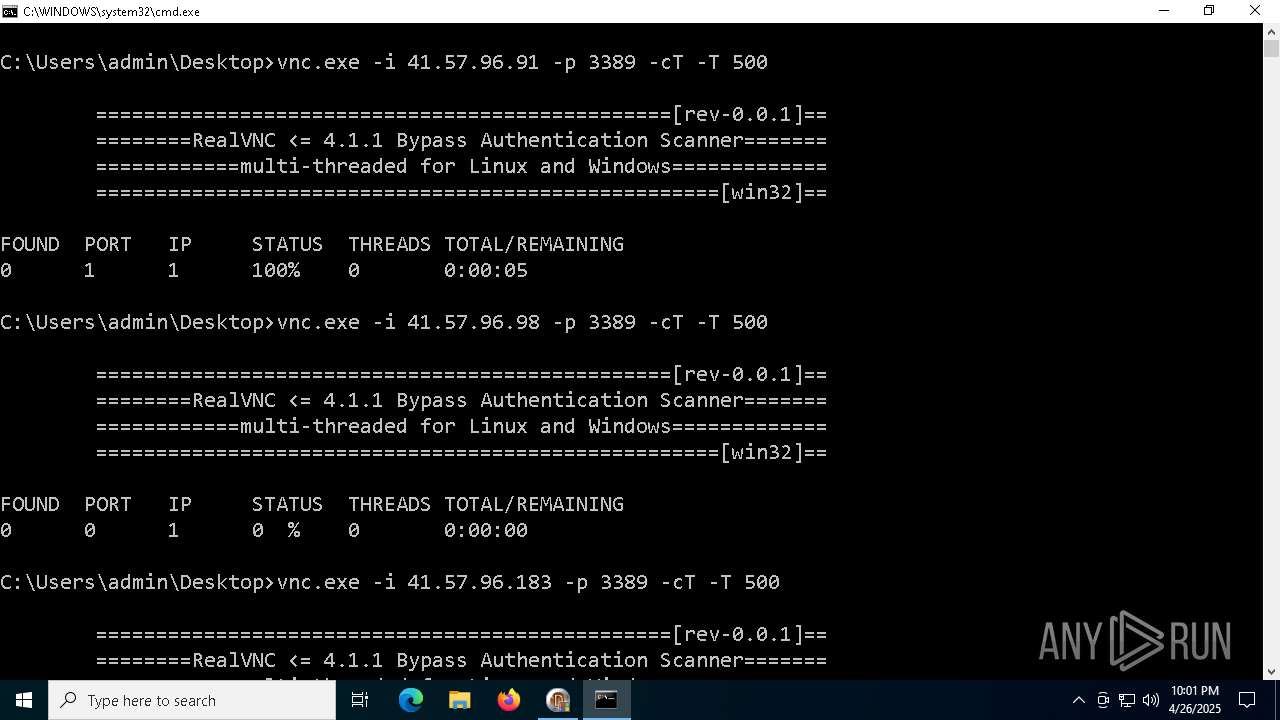
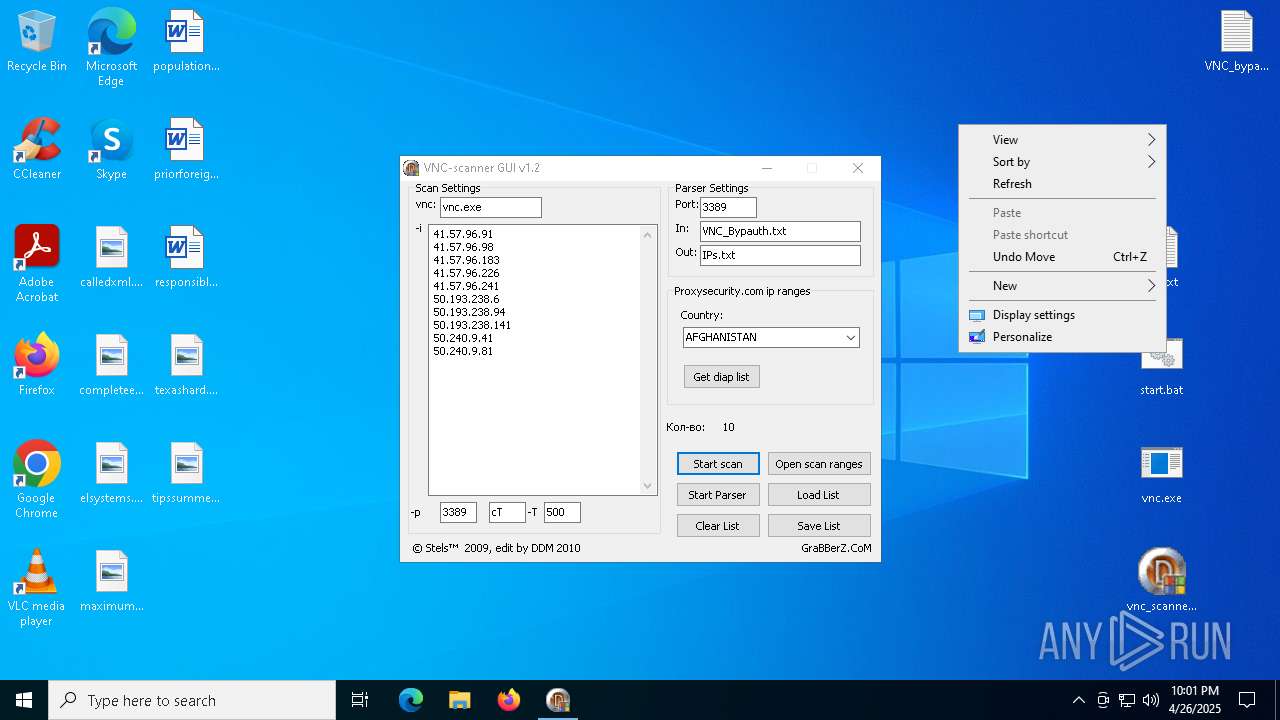
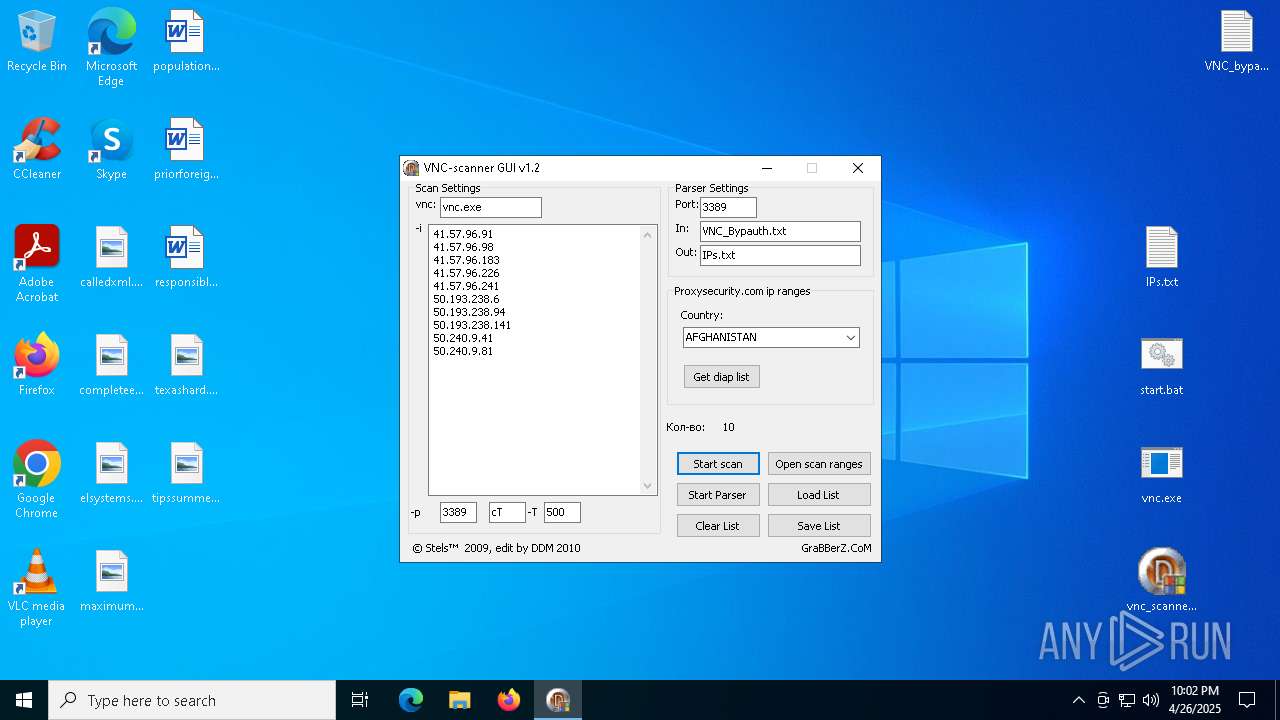
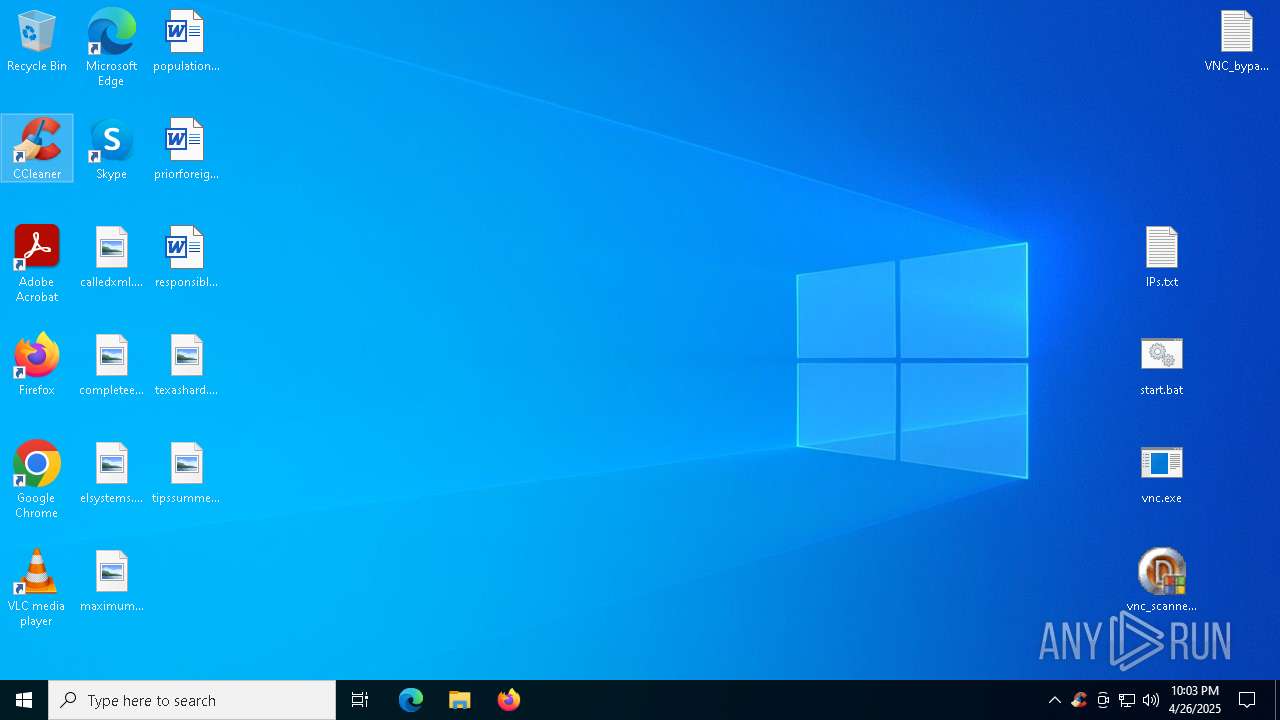
| File name: | VNC scanner GUI v 1.2.rar |
| Full analysis: | https://app.any.run/tasks/239c7b68-a111-480c-9975-38a7b77fd217 |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2025, 21:59:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 06C65EA441088890072741720F1A3587 |
| SHA1: | 0F30A58D3F510DDC78F14D4312EC6F90EE6E61CB |
| SHA256: | 4F2D86771B17DAF80F305C8A49B49F09AB1F5016D0628FD06D6B39BB1745EB1F |
| SSDEEP: | 98304:GdcSG/l3QV54DQihFJRvlx6TpypoY0rc723/k2guzLYuQjQffzYTkO+XJdZL3WcO:X8X/vt86FKr5kaLpFB |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4844)
SUSPICIOUS
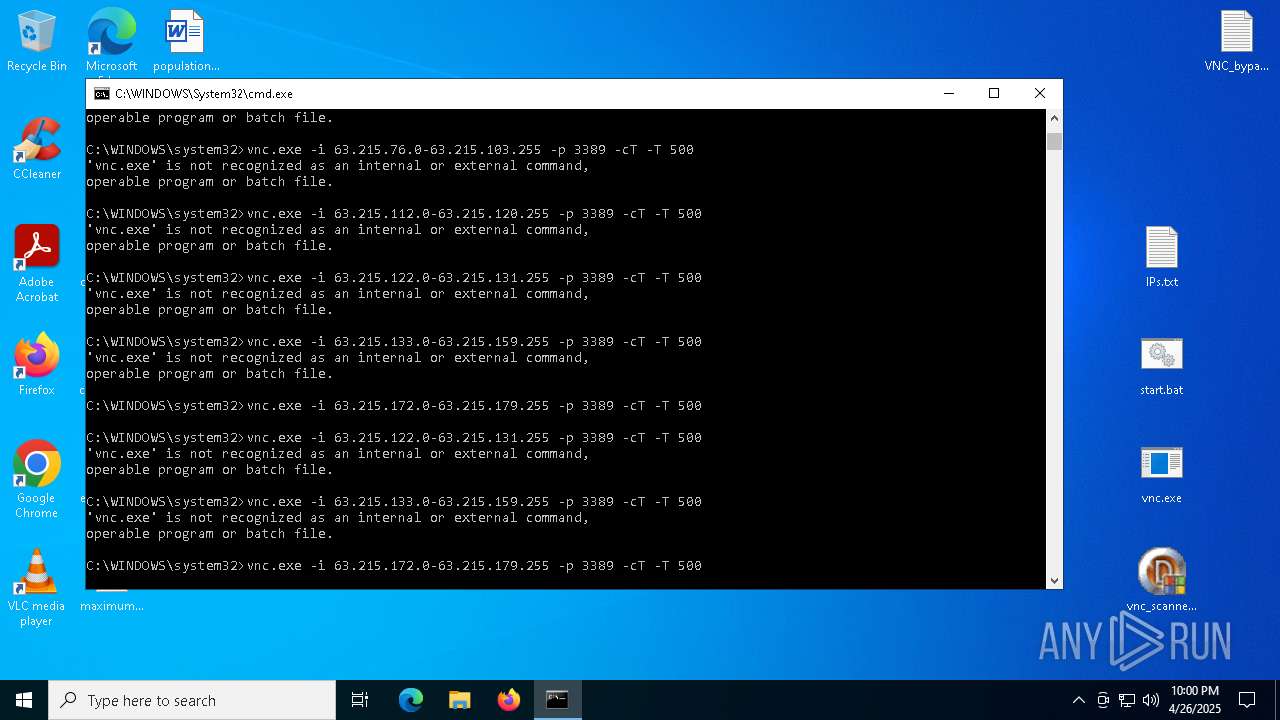
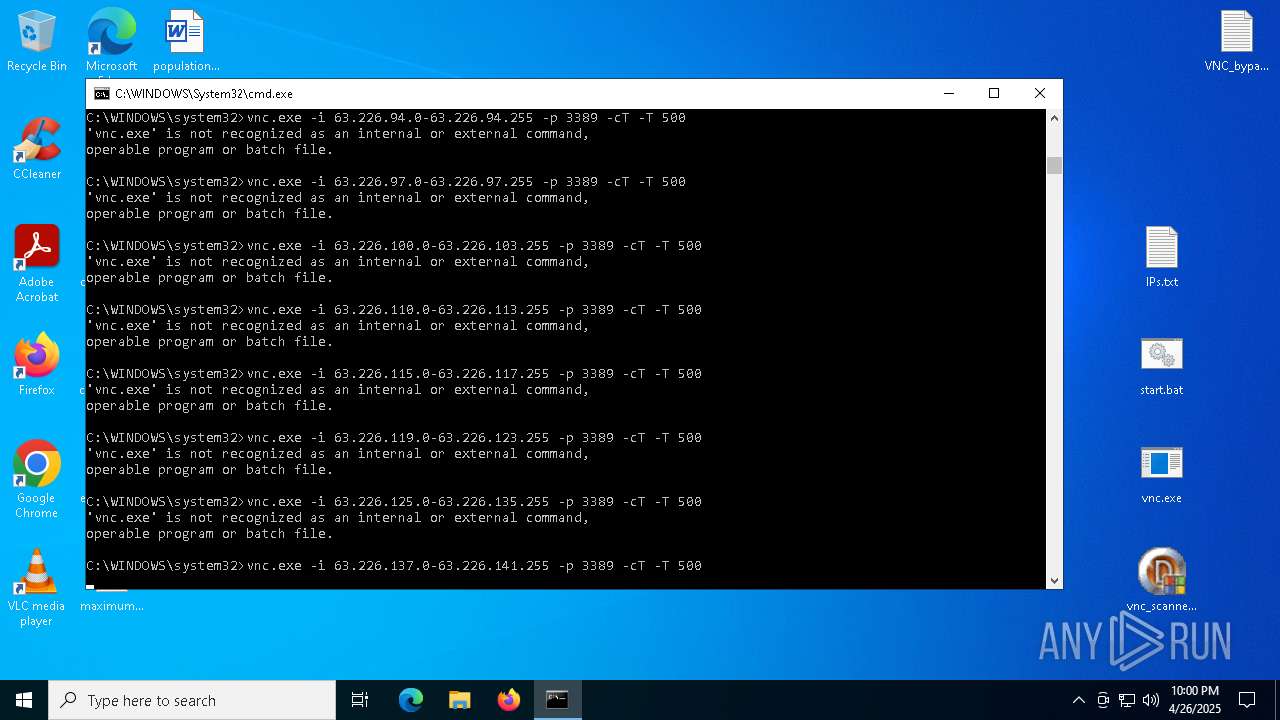
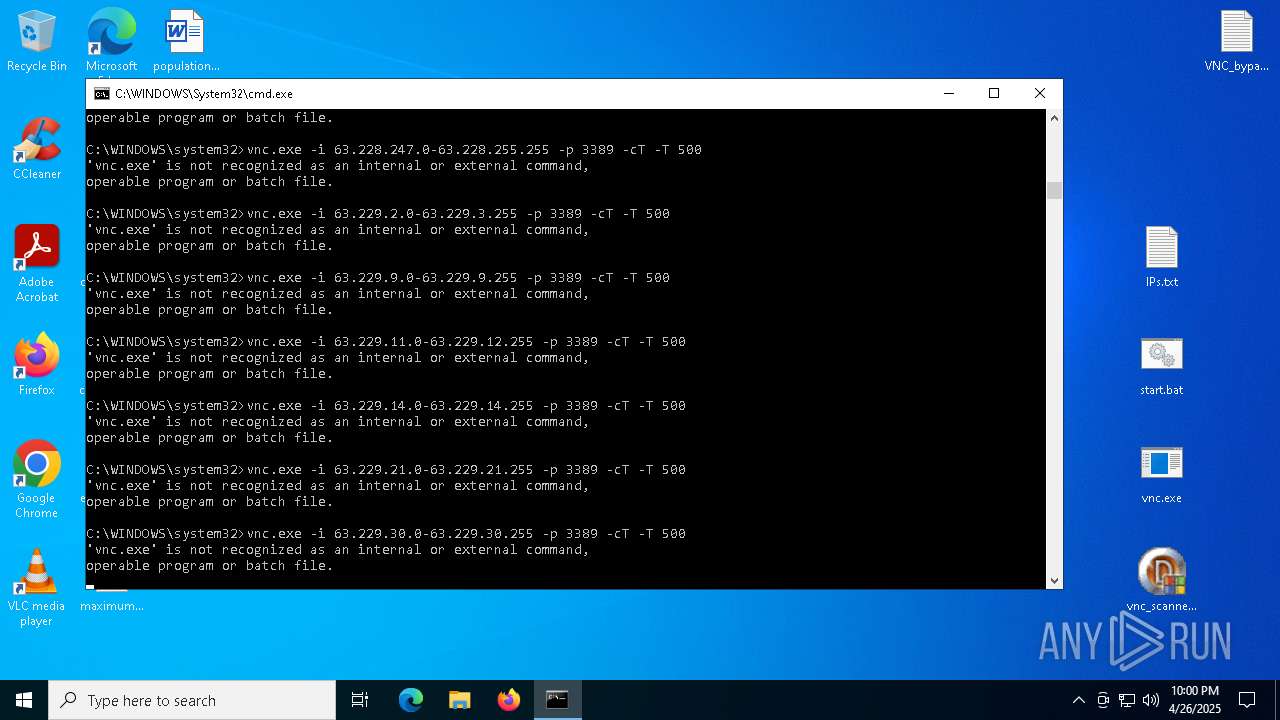
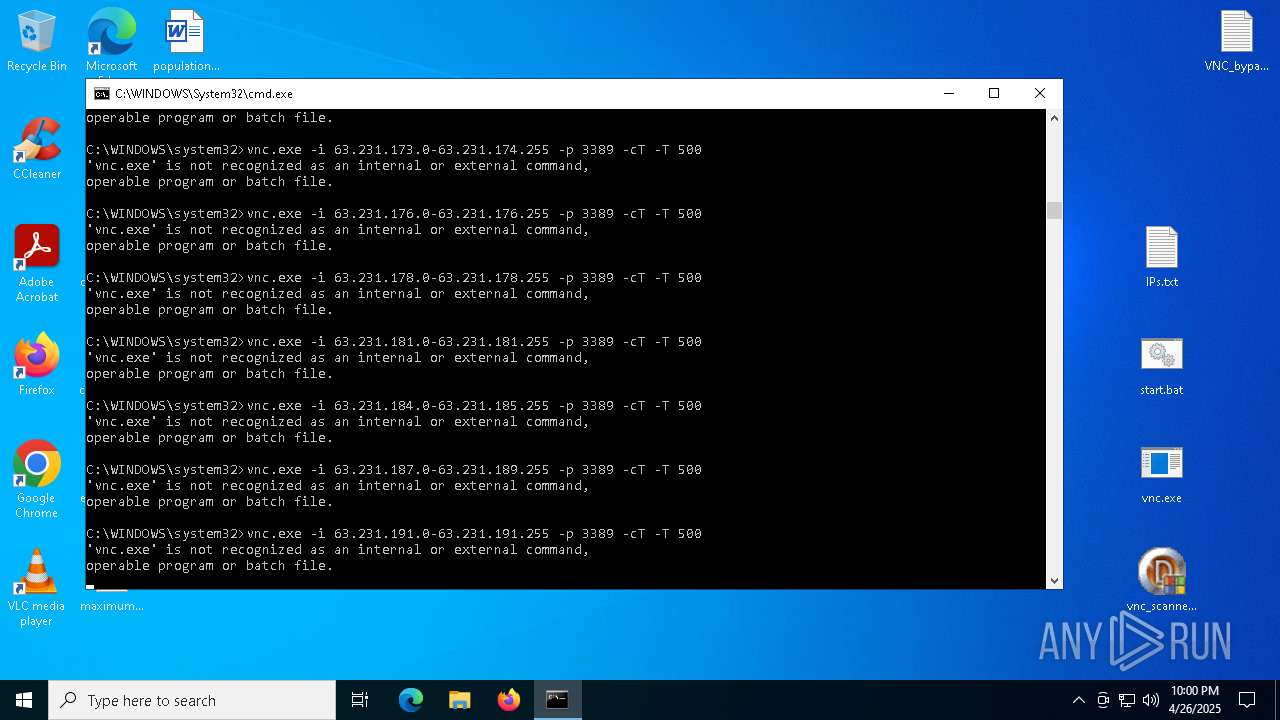
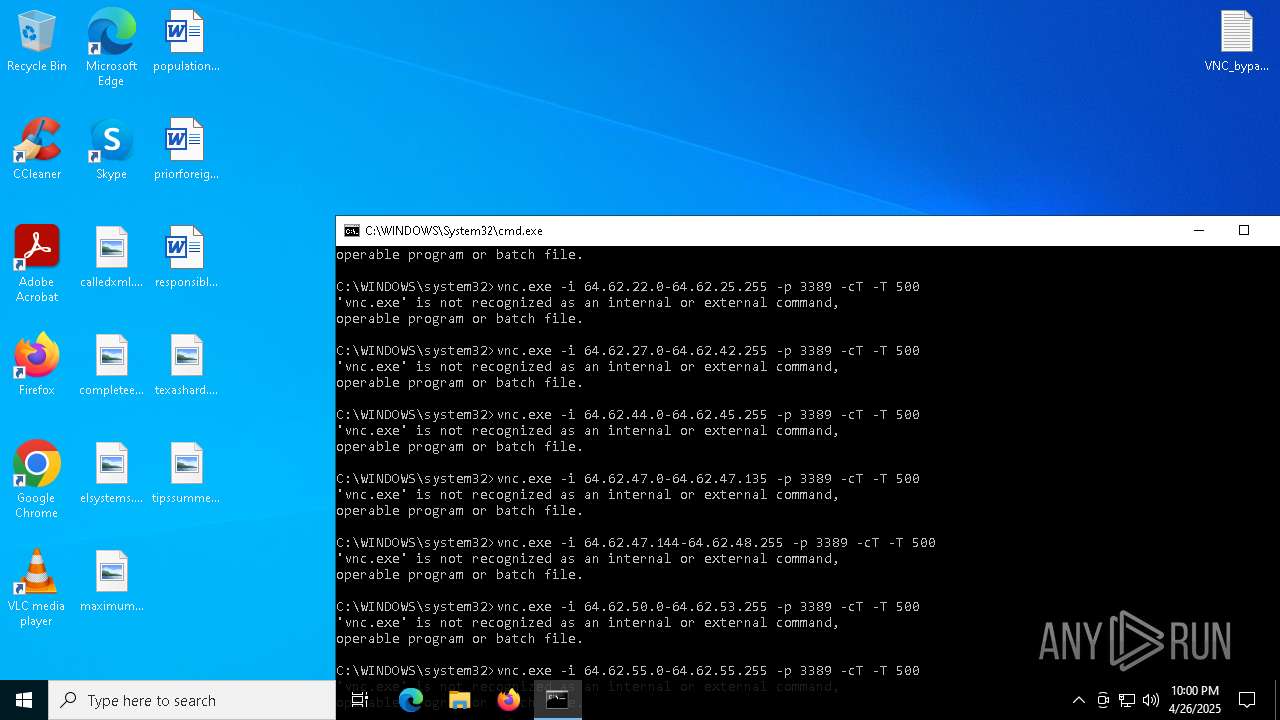
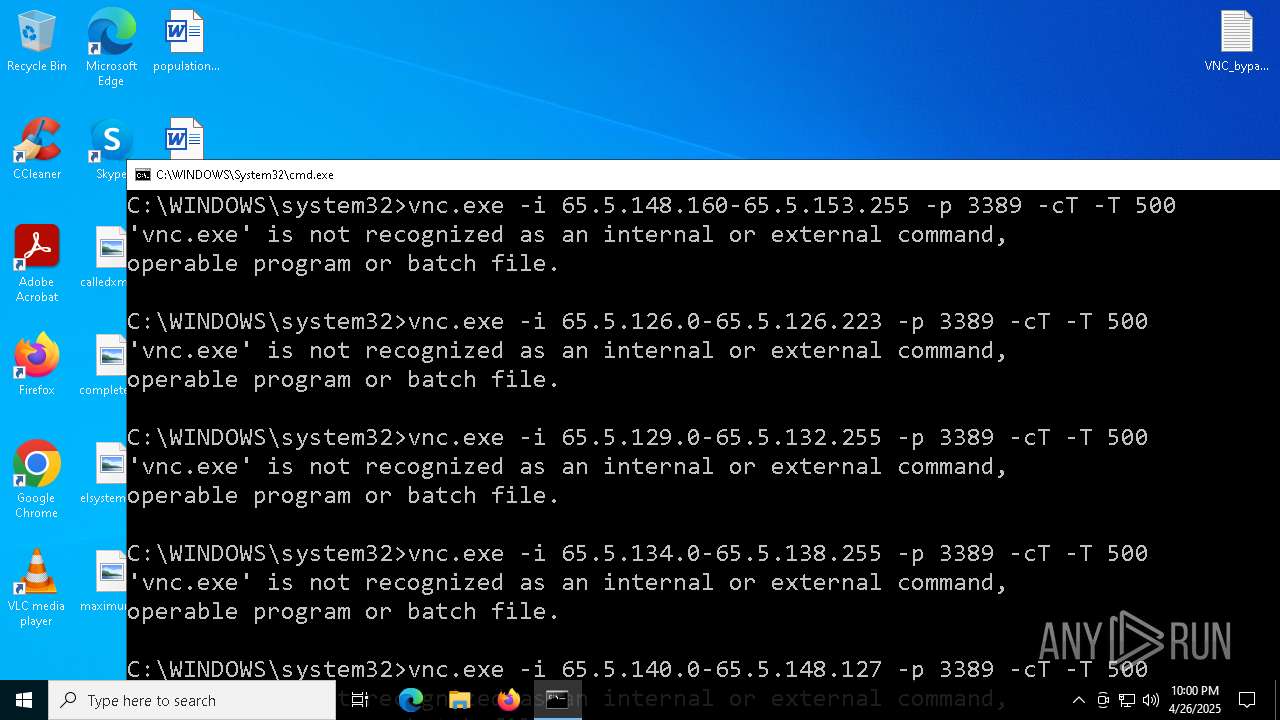
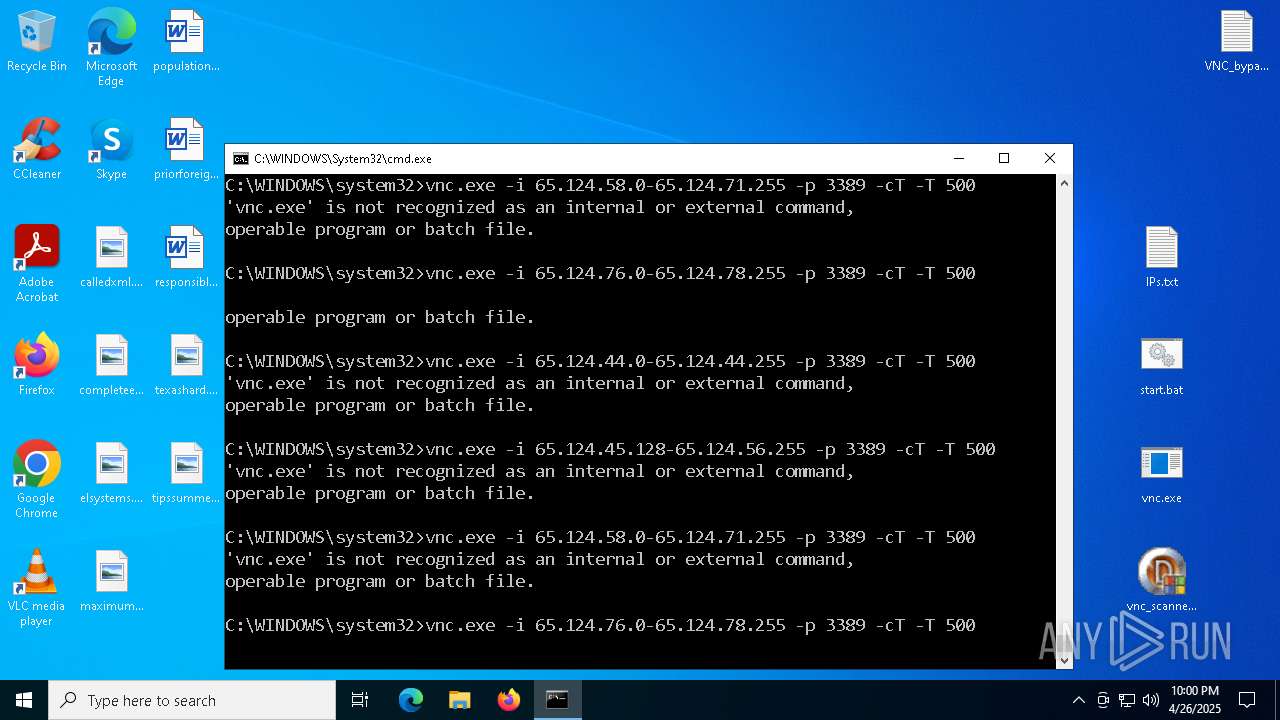
Executing commands from a ".bat" file
- vnc_scanner_gui.exe (PID: 8188)
Starts CMD.EXE for commands execution
- vnc_scanner_gui.exe (PID: 8188)
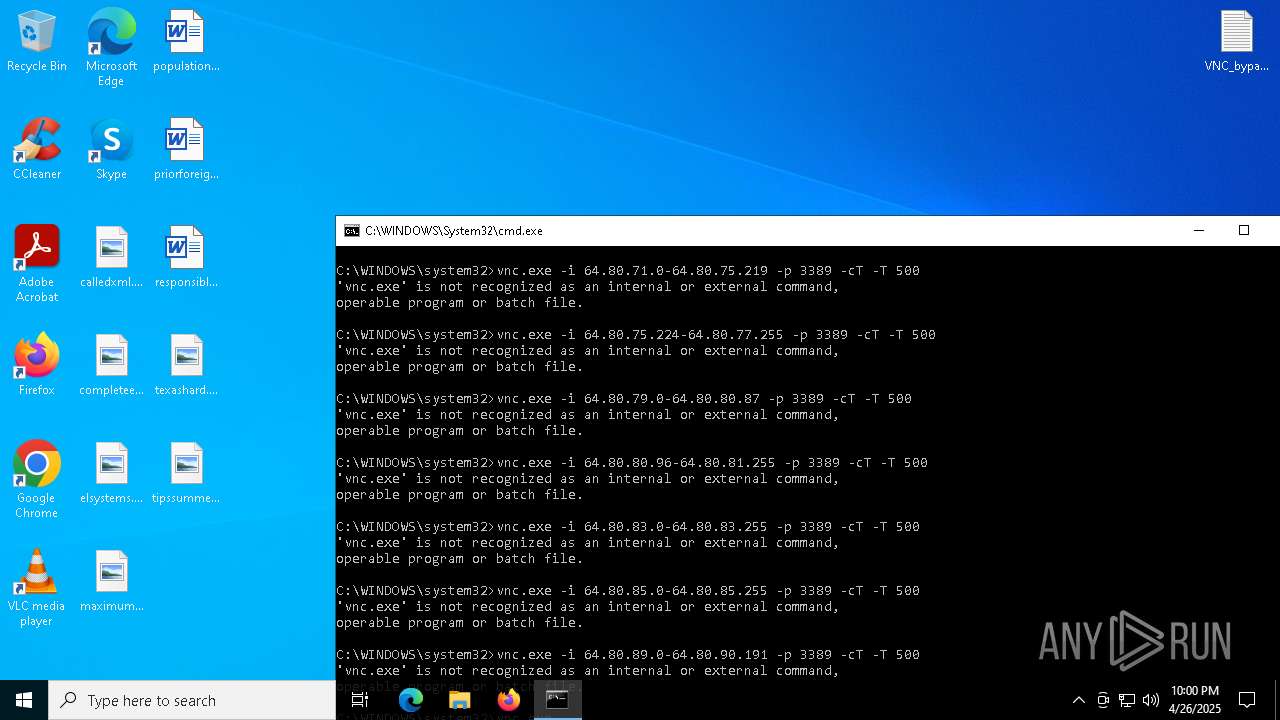
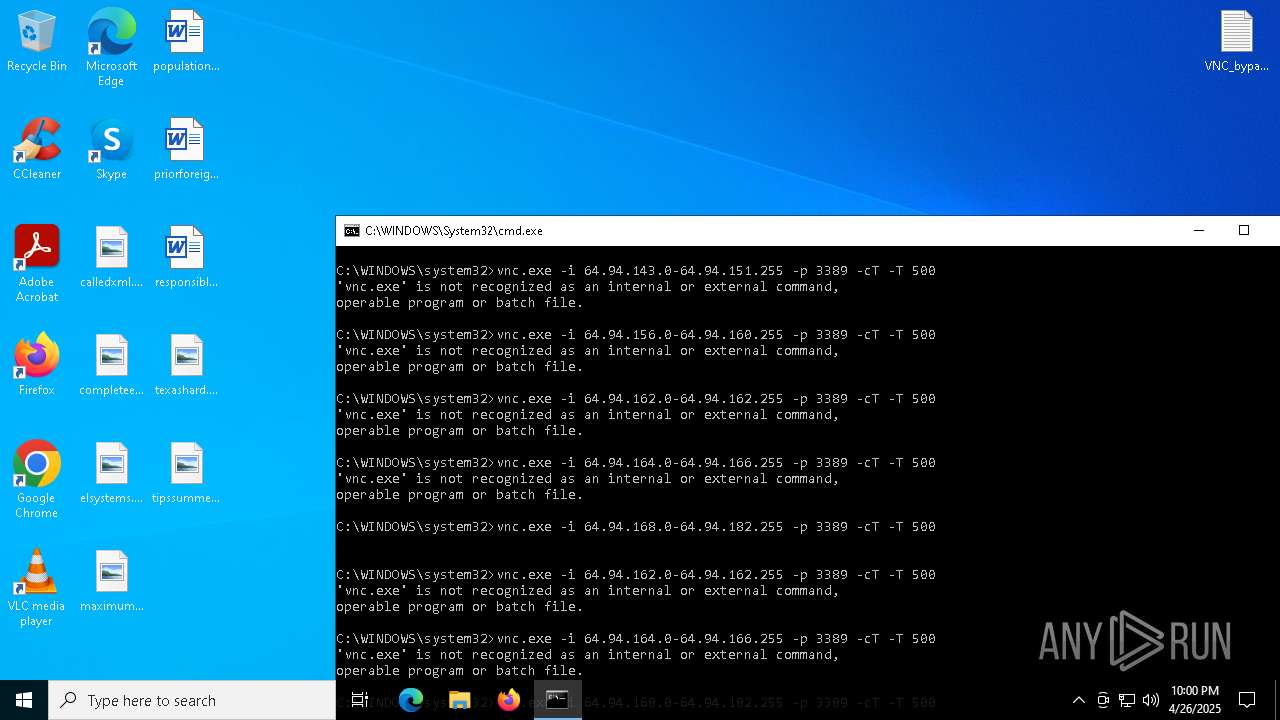
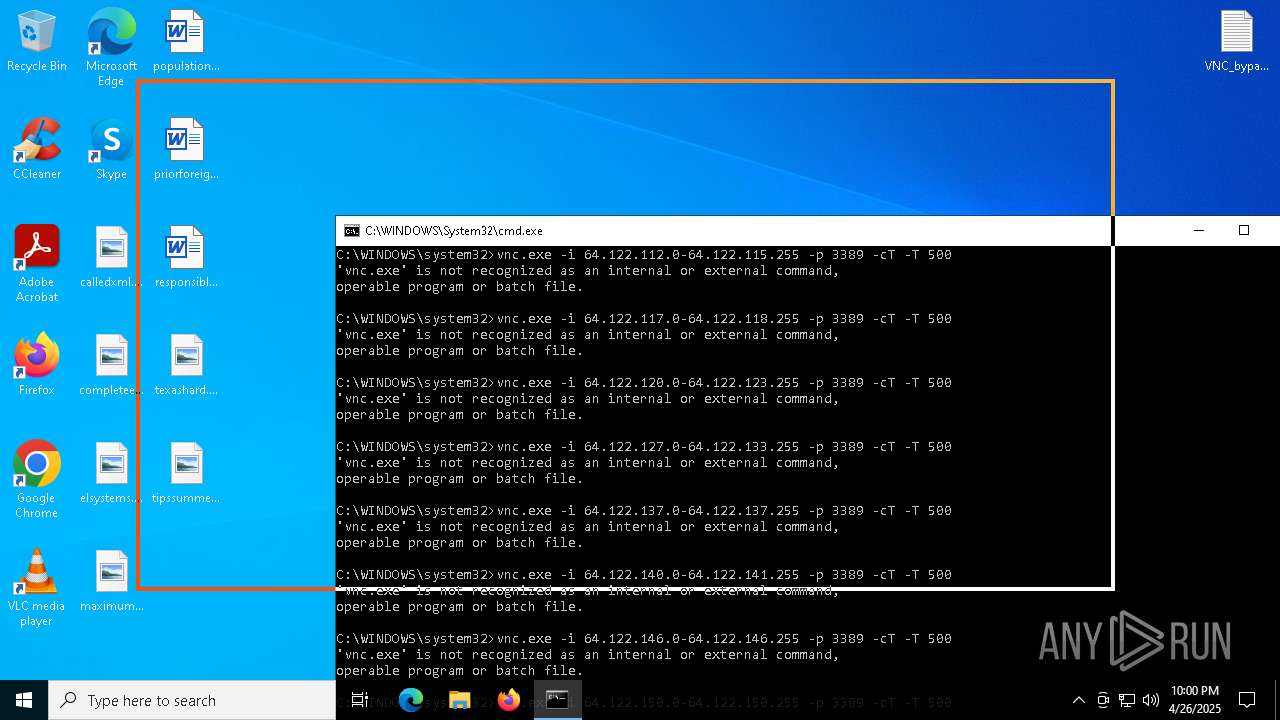
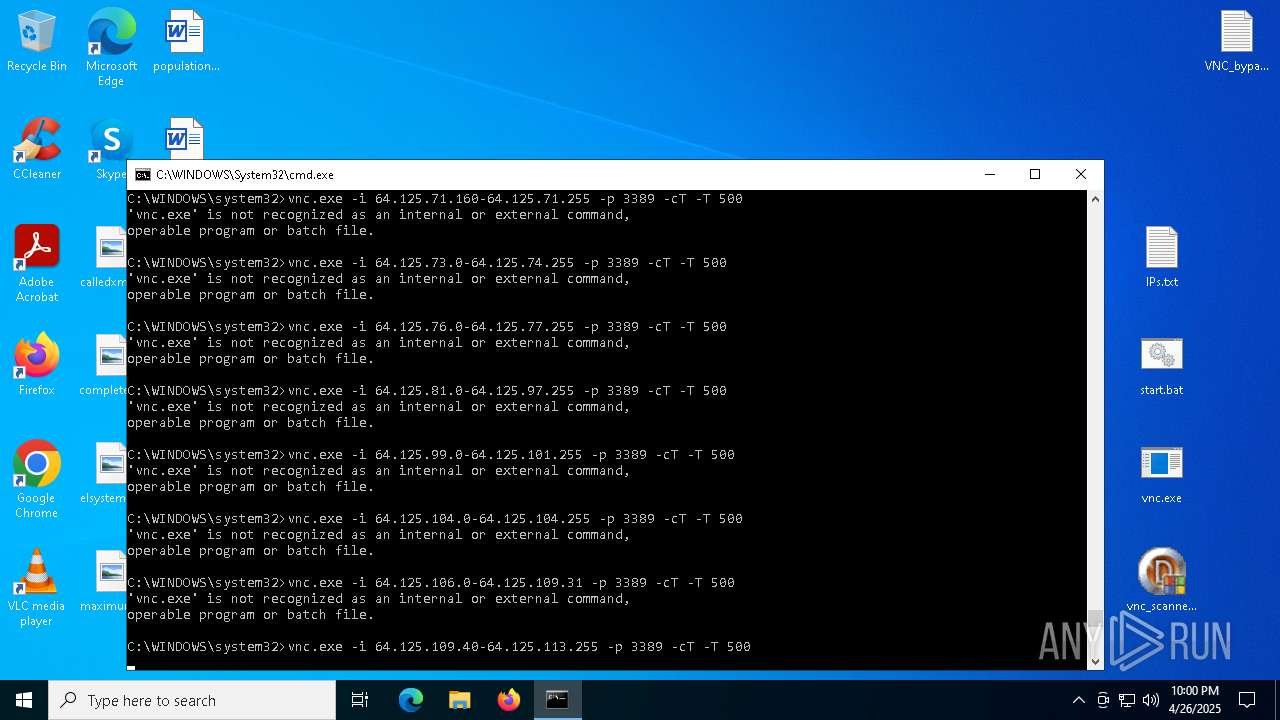
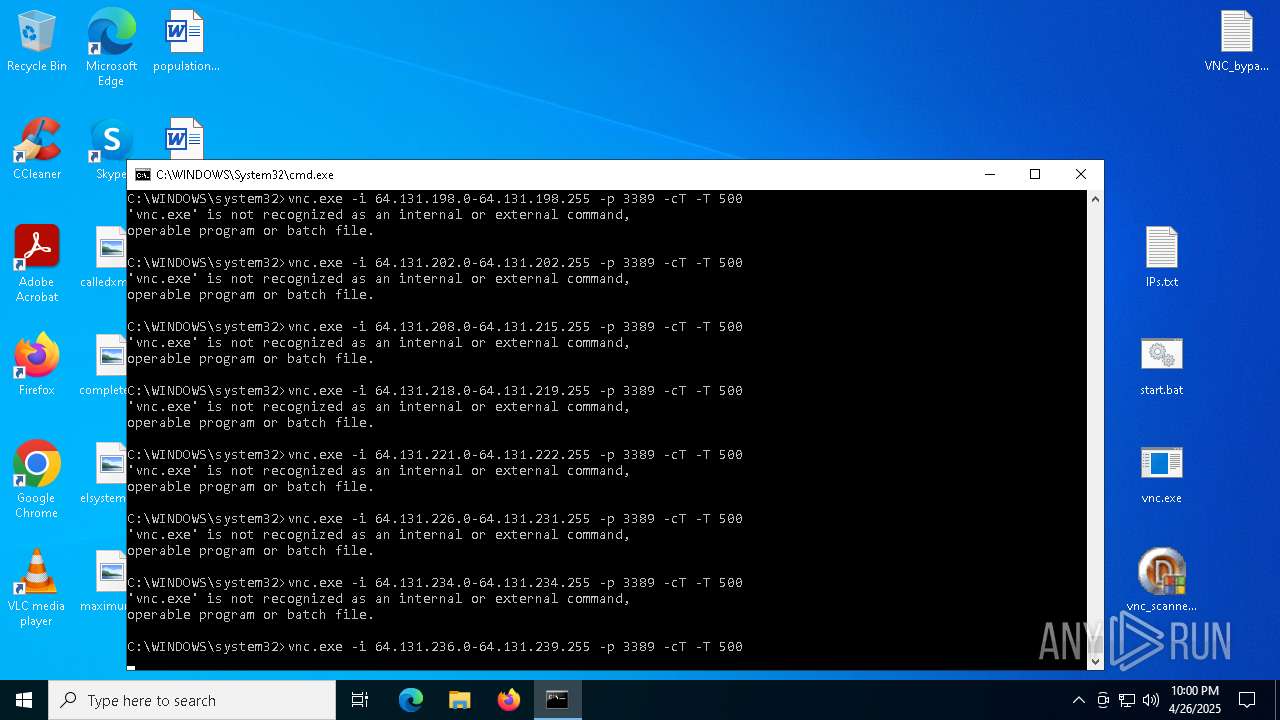
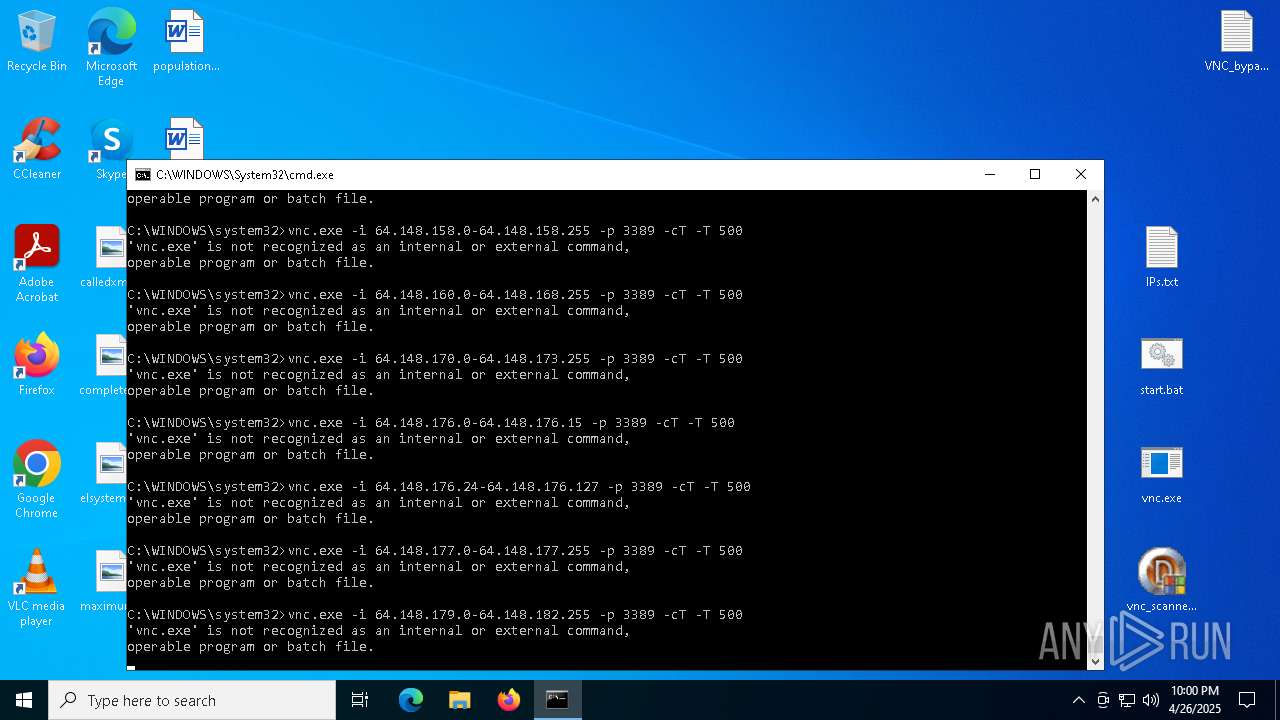
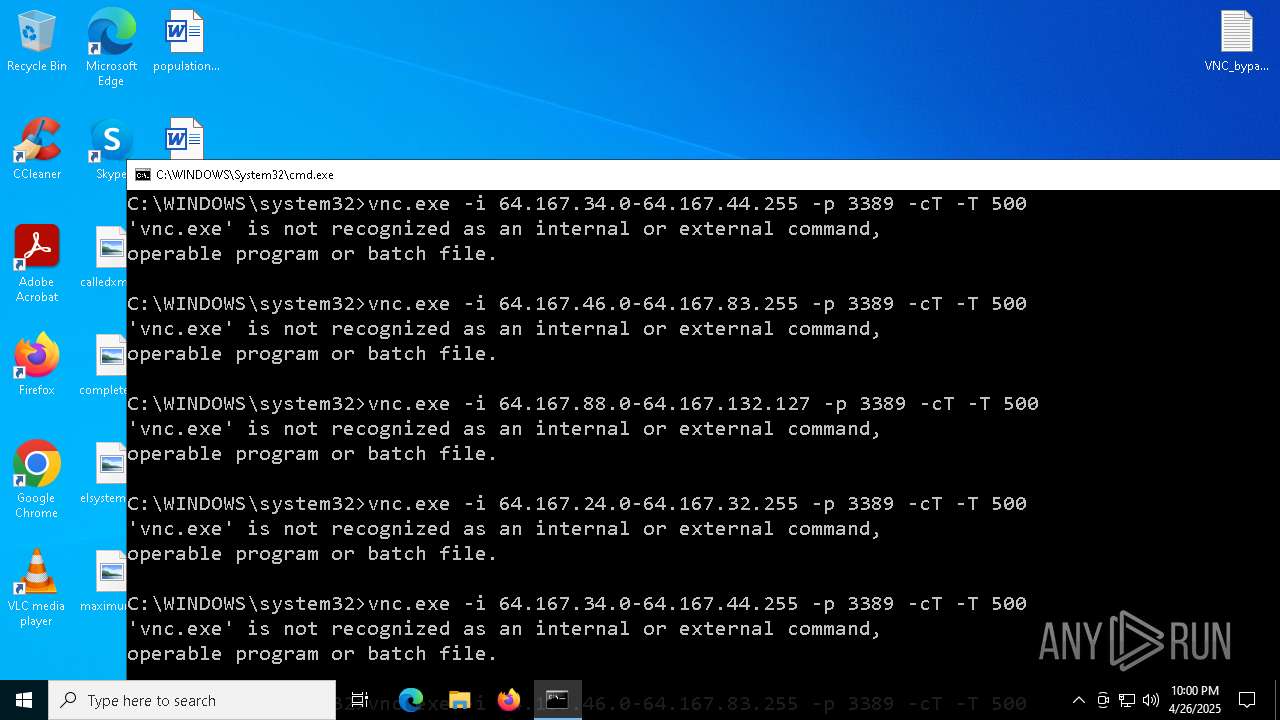
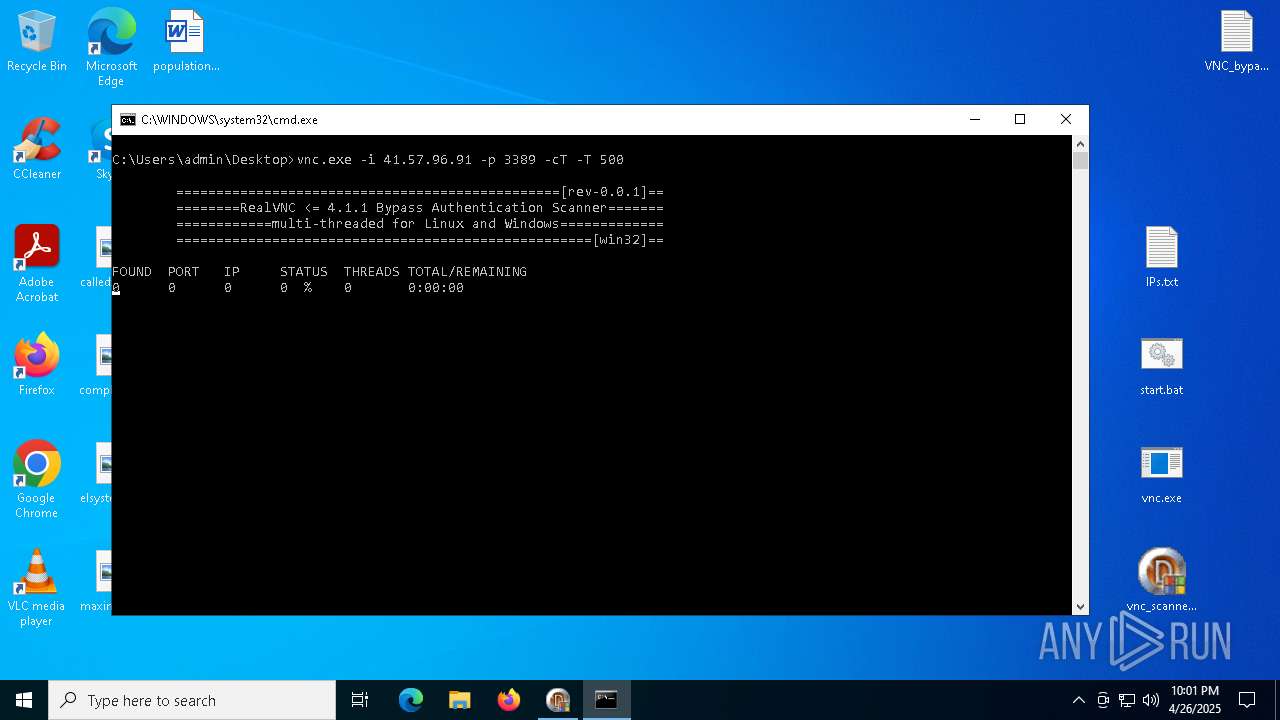
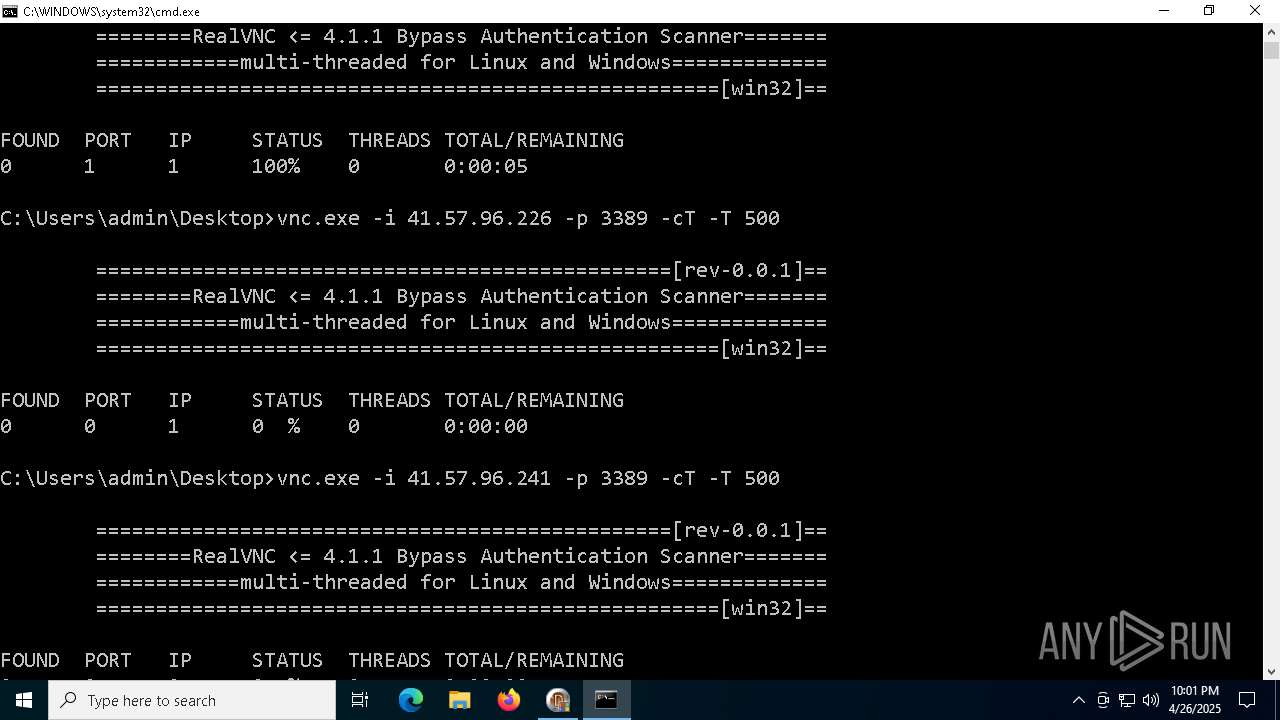
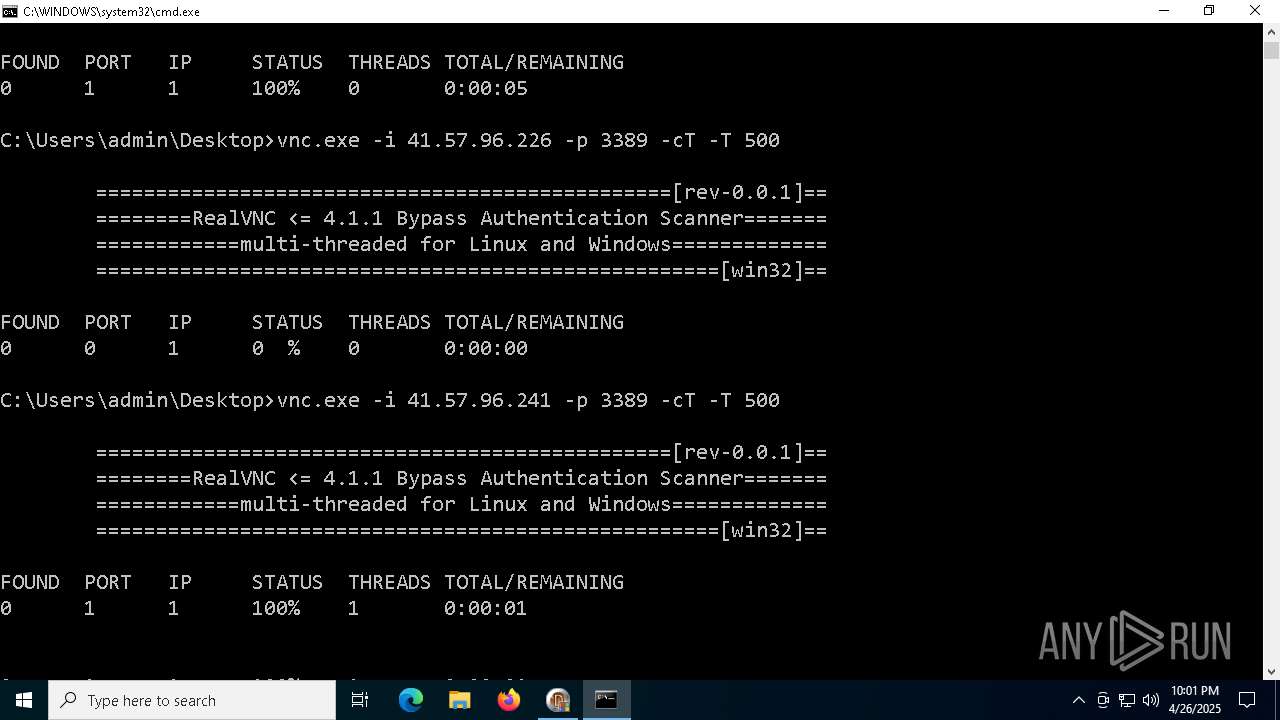
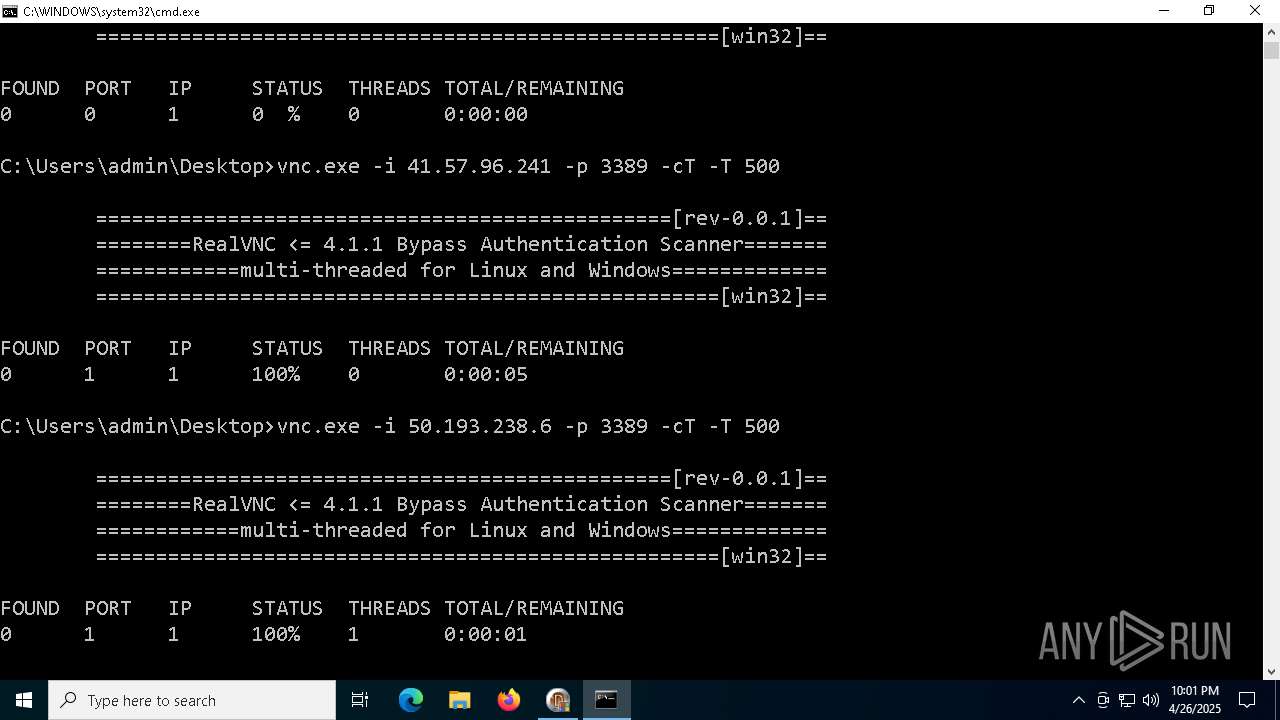
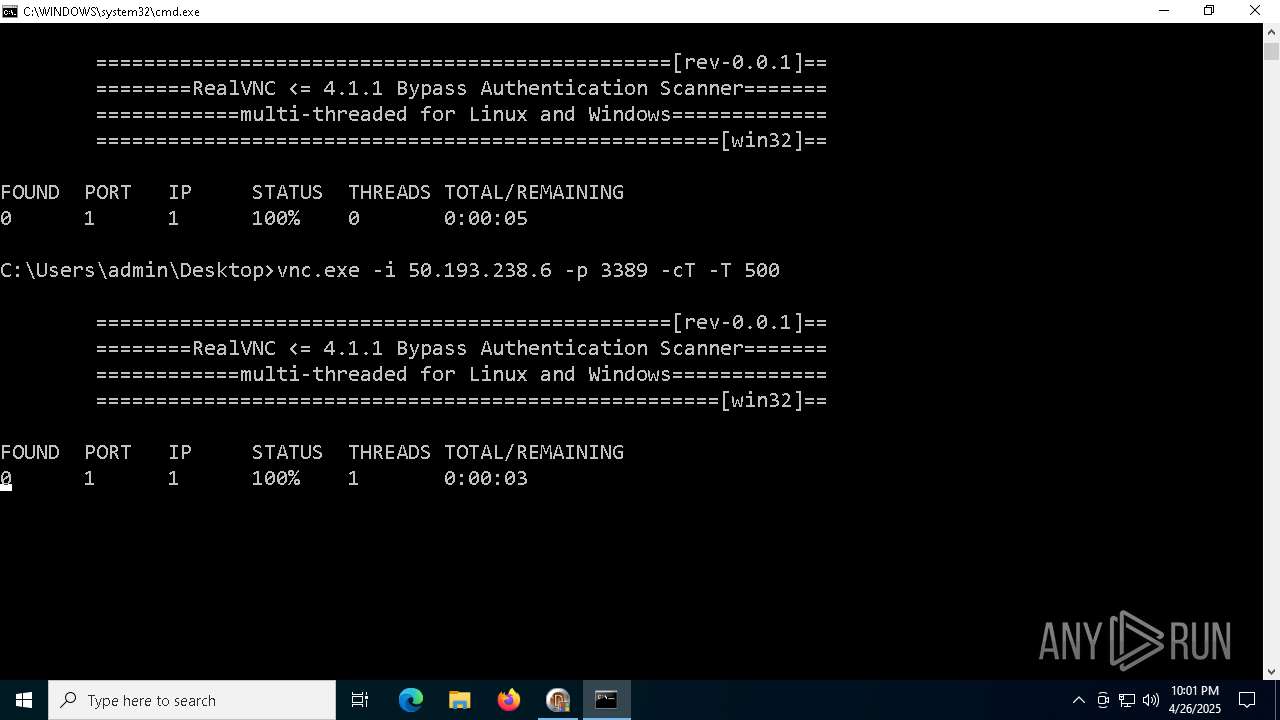
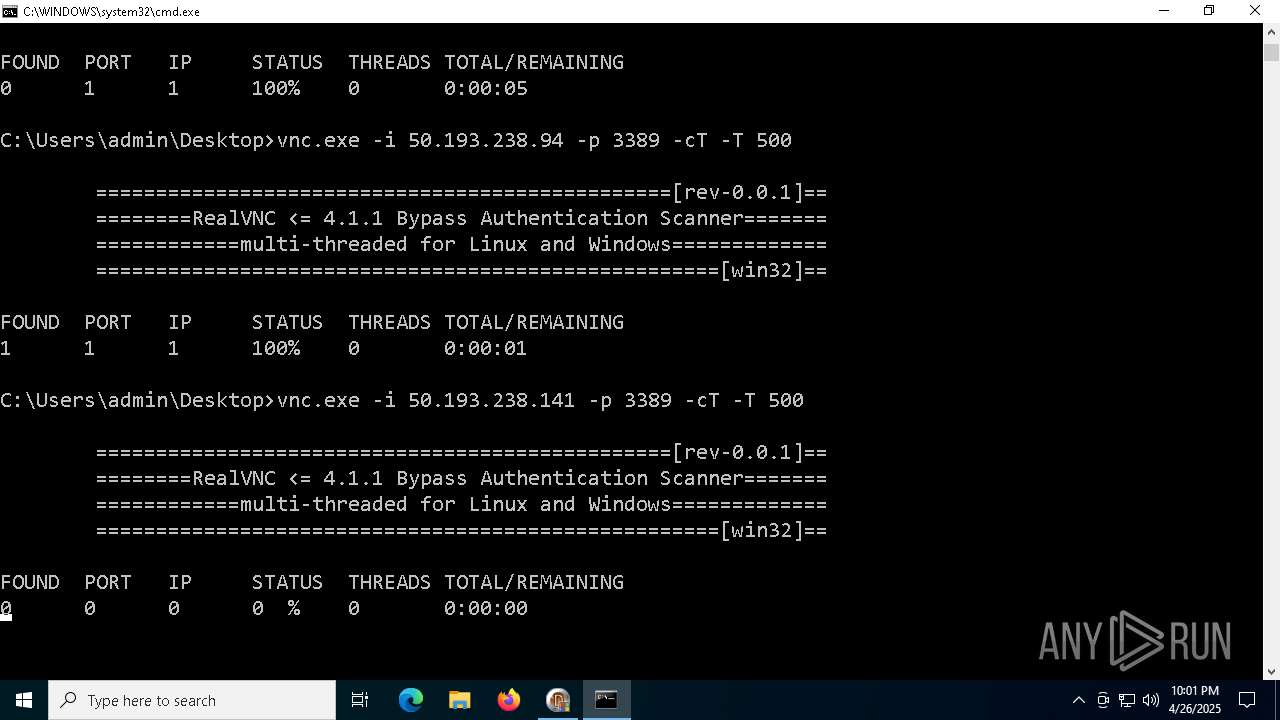
Connects to unusual port
- vnc.exe (PID: 4892)
- vnc.exe (PID: 4988)
- vnc.exe (PID: 7256)
- vnc.exe (PID: 7552)
- vnc.exe (PID: 6640)
- vnc.exe (PID: 7540)
- vnc.exe (PID: 7456)
- vnc.exe (PID: 7368)
- vnc.exe (PID: 7560)
- vnc.exe (PID: 7432)
- vnc.exe (PID: 1228)
- vnc.exe (PID: 7360)
Application launched itself
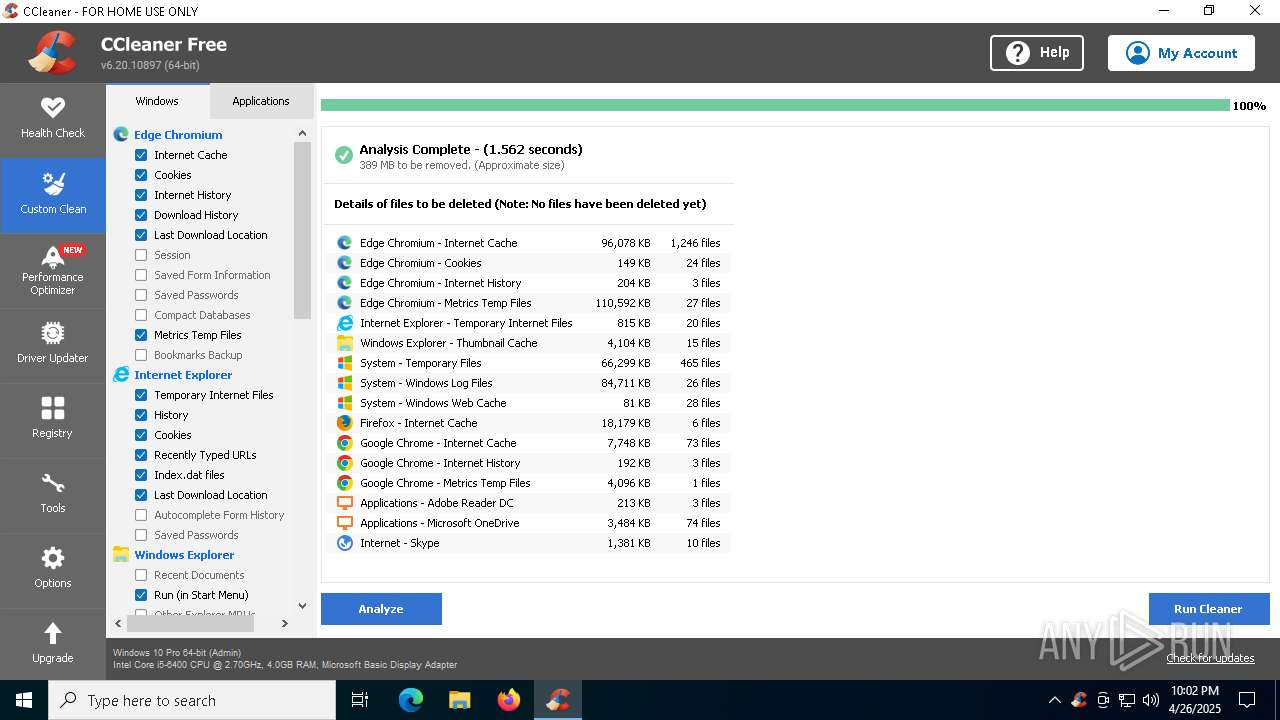
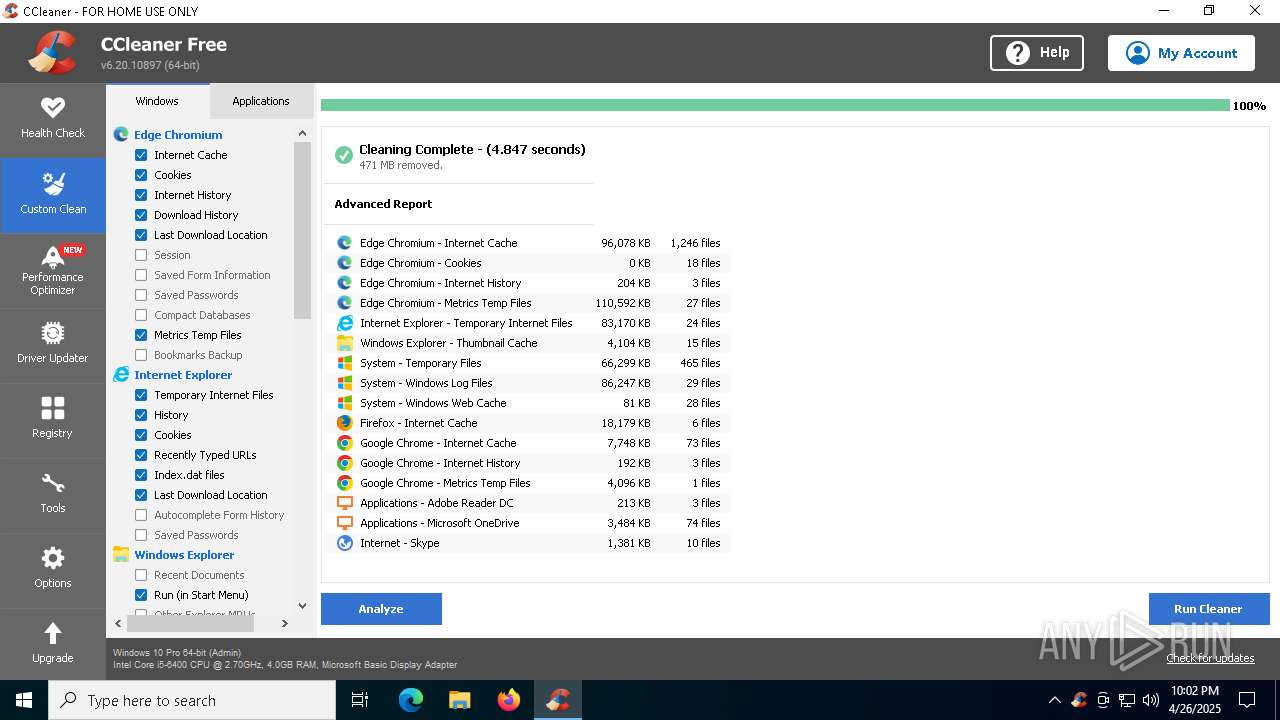
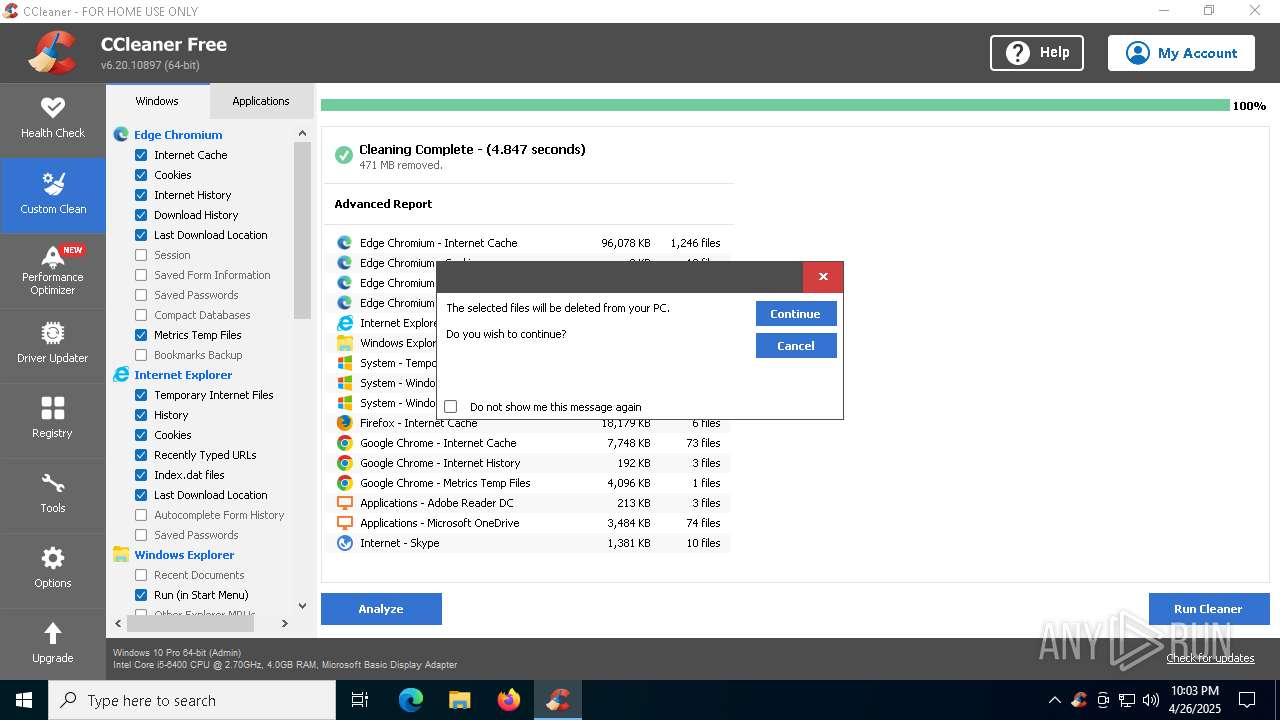
- CCleaner64.exe (PID: 5384)
- CCleaner64.exe (PID: 6752)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 6752)
- CCleaner64.exe (PID: 4212)
- TiWorker.exe (PID: 4304)
Checks for external IP
- CCleaner64.exe (PID: 6752)
Executes as Windows Service
- vds.exe (PID: 4220)
Process drops legitimate windows executable
- TiWorker.exe (PID: 4304)
INFO
Manual execution by a user
- vnc_scanner_gui.exe (PID: 7704)
- cmd.exe (PID: 7828)
- notepad.exe (PID: 6048)
- vnc_scanner_gui.exe (PID: 8188)
- notepad.exe (PID: 7636)
- CCleaner64.exe (PID: 5384)
Checks supported languages
- vnc_scanner_gui.exe (PID: 7704)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4844)
UPX packer has been detected
- vnc_scanner_gui.exe (PID: 8188)
Compiled with Borland Delphi (YARA)
- vnc_scanner_gui.exe (PID: 8188)
- slui.exe (PID: 5968)
- conhost.exe (PID: 5640)
- notepad.exe (PID: 7636)
The sample compiled with english language support
- CCleaner64.exe (PID: 6752)
- CCleaner64.exe (PID: 4212)
- TiWorker.exe (PID: 4304)
Reads the computer name
- vnc_scanner_gui.exe (PID: 7704)
Detects AutoHotkey samples (YARA)
- CCleaner64.exe (PID: 4212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | - |
| UncompressedSize: | - |
| OperatingSystem: | Win32 |
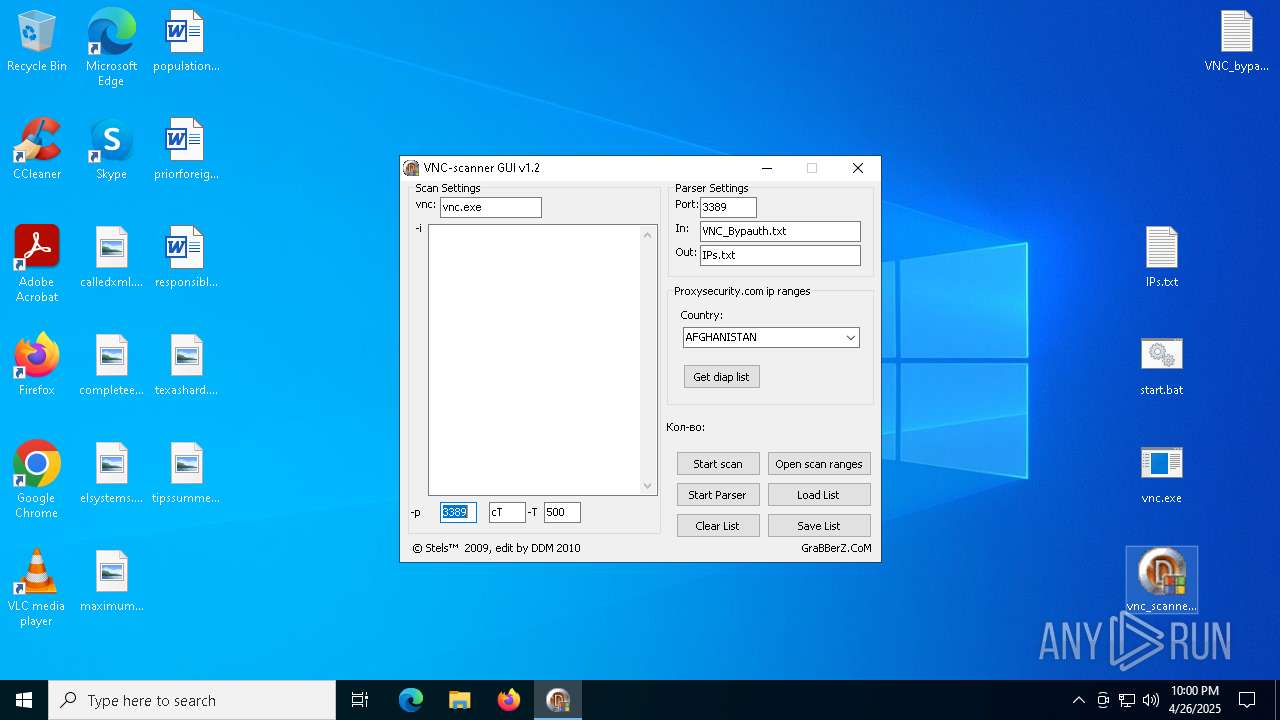
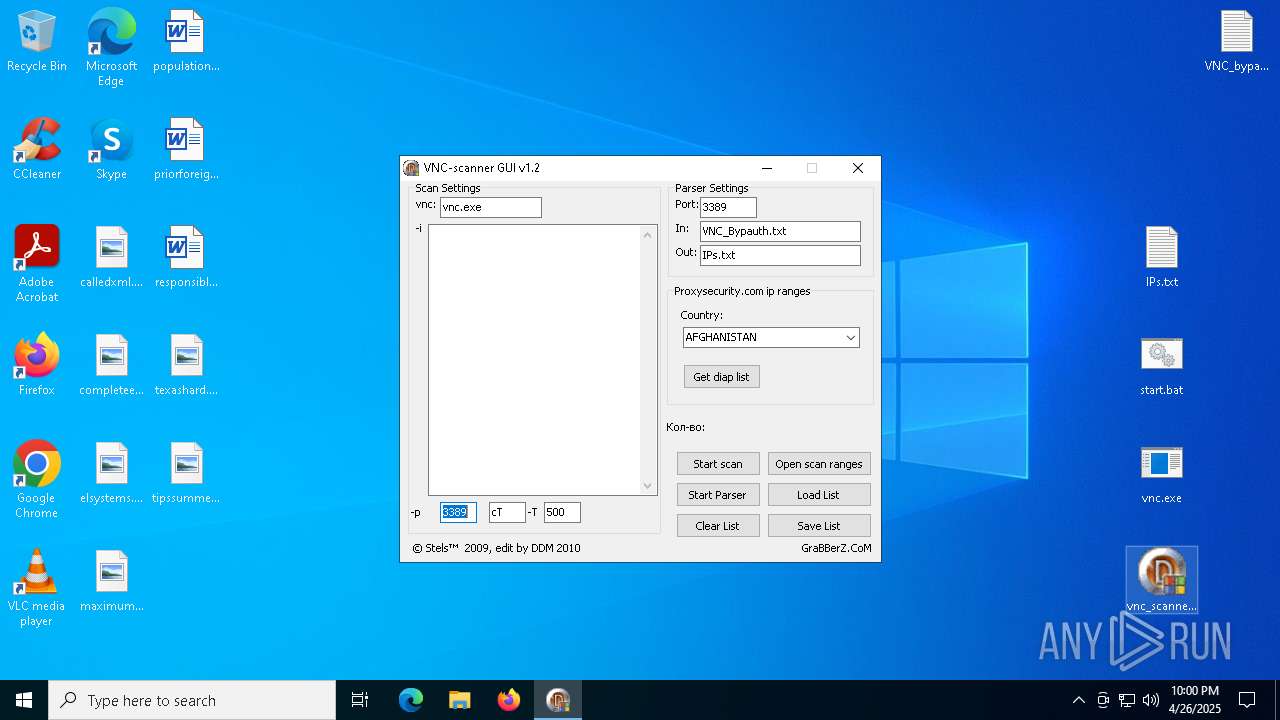
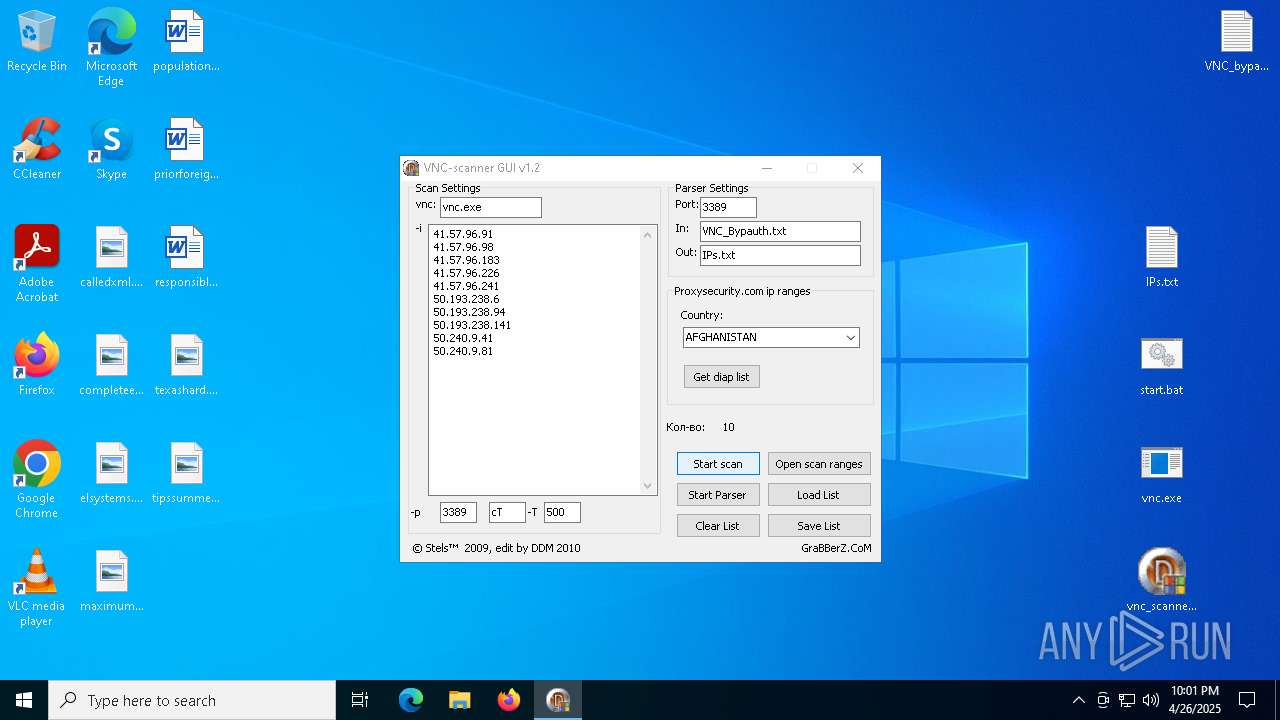
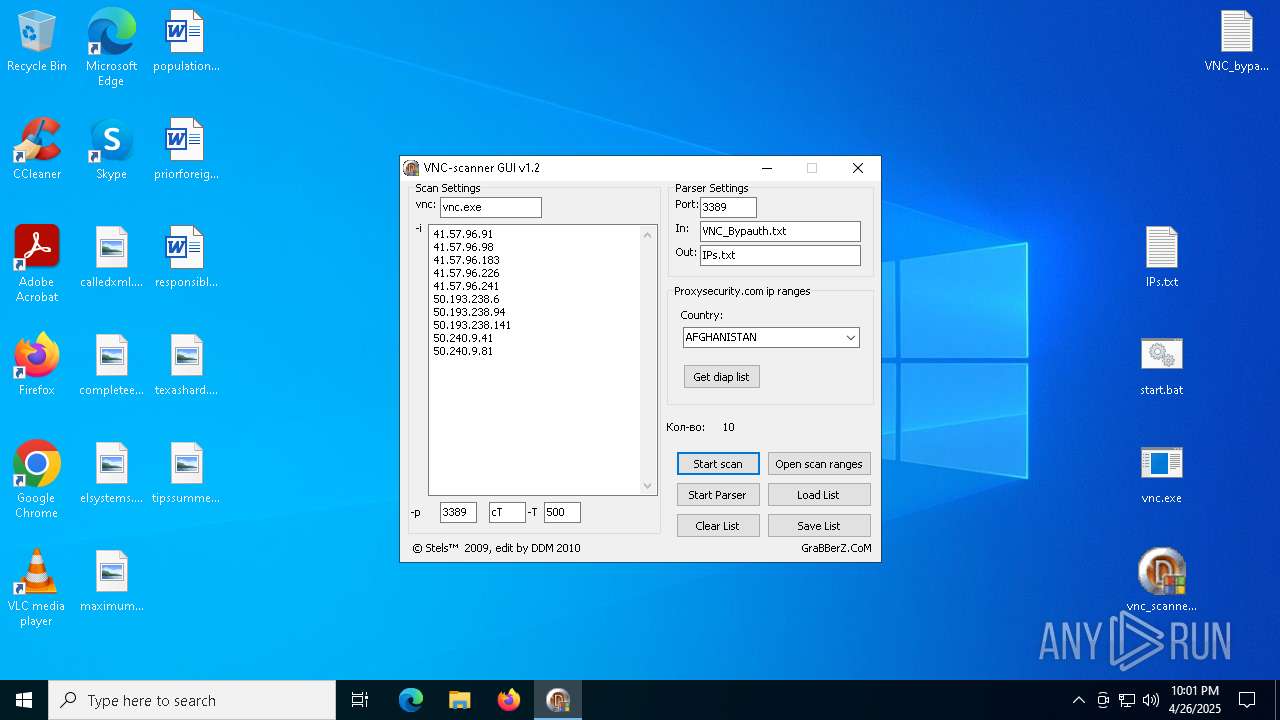
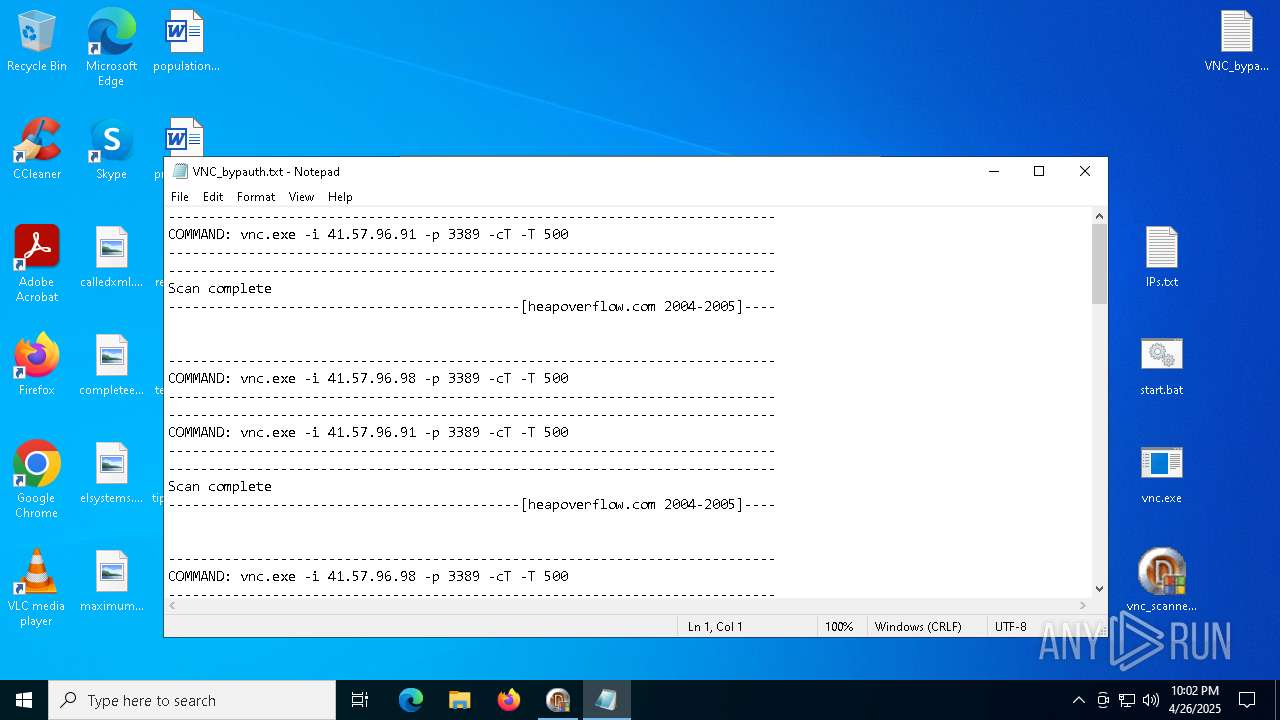
| ArchivedFileName: | VNC_bypauth.txt |
Total processes
188
Monitored processes
33
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
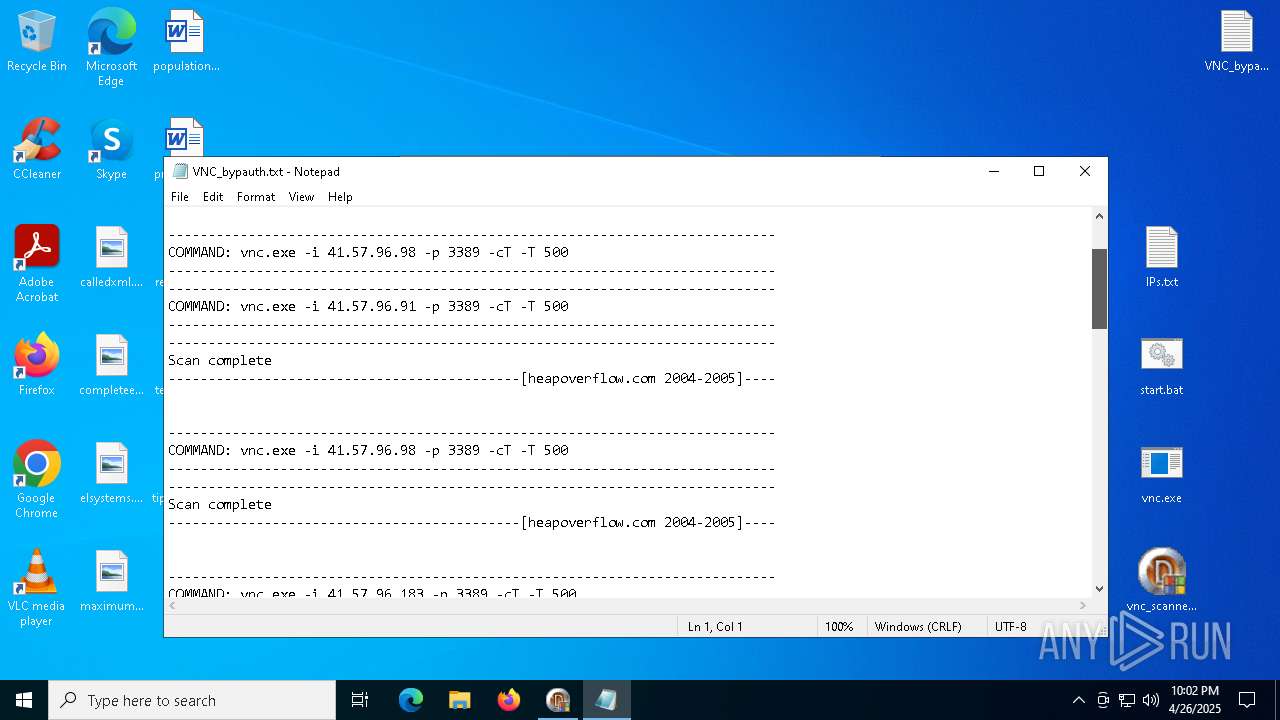
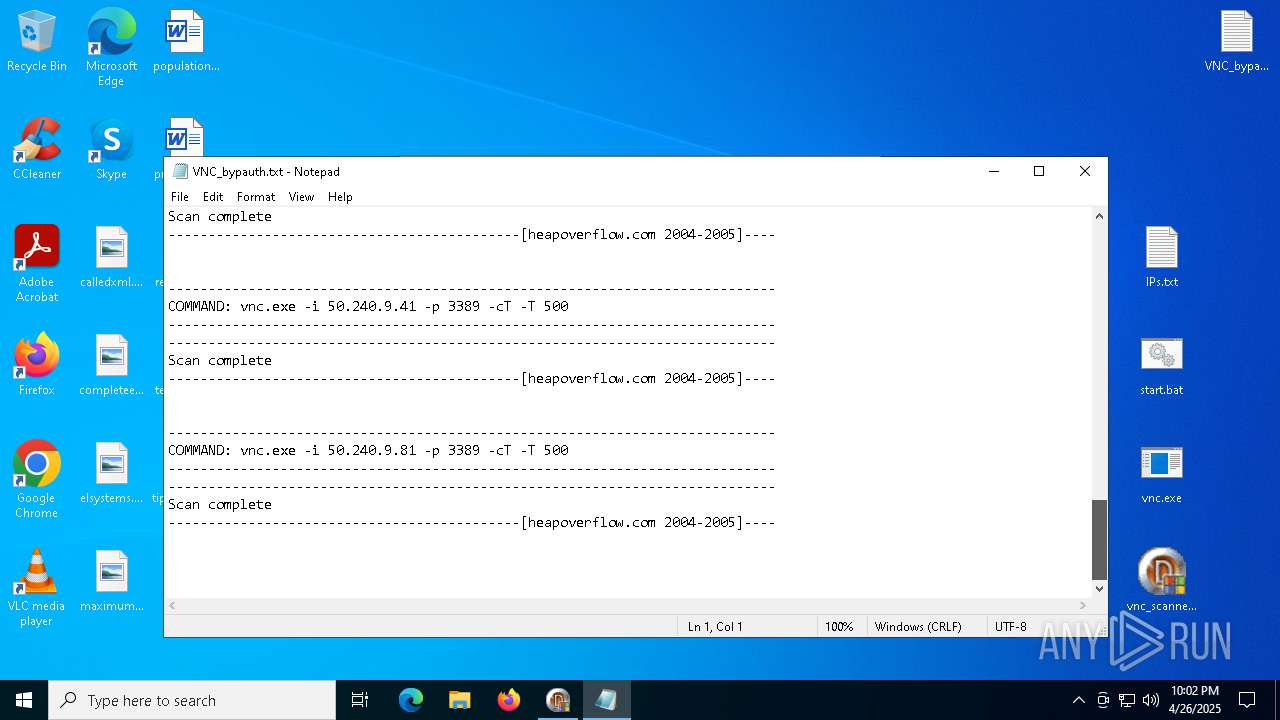
| 1228 | vnc.exe -i 41.57.96.98 -p 3389 -cT -T 500 | C:\Users\admin\Desktop\vnc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 3032 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4212 | "C:\Program Files\CCleaner\CCleaner64.exe" /monitor | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Version: 6.20.0.10897 Modules
| |||||||||||||||
| 4220 | C:\WINDOWS\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4304 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\VNC scanner GUI v 1.2.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4892 | vnc.exe -i 41.57.96.91 -p 3389 -cT -T 500 | C:\Users\admin\Desktop\vnc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4988 | vnc.exe -i 41.57.96.91 -p 3389 -cT -T 500 | C:\Users\admin\Desktop\vnc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5376 | C:\WINDOWS\system32\cmd.exe /c start.bat | C:\Windows\SysWOW64\cmd.exe | — | vnc_scanner_gui.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5384 | "C:\Program Files\CCleaner\CCleaner64.exe" | C:\Program Files\CCleaner\CCleaner64.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
Total events
68 725
Read events
68 501
Write events
144
Delete events
80
Modification events
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\VNC scanner GUI v 1.2.rar | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (4844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
28
Suspicious files
226
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4844.11807\start.bat | — | |
MD5:— | SHA256:— | |||
| 6752 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_17457049396752.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 6752 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E573CDF4C6D731D56A665145182FD759_AFB3BE9383420FBAFF24AD413EEA555E | binary | |
MD5:A9E2FAB5C38F78EB3BE77EA057EF5D3E | SHA256:4AB3C9823851EFEF216B0FE4CD7251B7E7A6BF63A2E5AF6F42A82BDD027580E3 | |||
| 4844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4844.11807\IPs.txt | text | |
MD5:9AECA50A64356F00AED949F159F577F4 | SHA256:AF045E591BB1ADA04EAE57A3922B600E0D79A8B48FFEC626CD4489BC5963299B | |||
| 6752 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:DBFE3DFF93A49B5FD68DDB1042B710D7 | SHA256:87FC40868FF3EA949B4BE5918DF844FEBF851F2BC447EBF4FAEE3DF1C9743C73 | |||
| 6752 | CCleaner64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\info[1].json | binary | |
MD5:9FFABD3D365B1F3AA2594B31BF11731D | SHA256:4AD1FDDB052FBF740EA2DCA19DC0D7508570B4D29FDF696B0309970856F0BE03 | |||
| 6752 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\81242838D18BA7E8D81FCB53A56599A1_36A987CE68EE49AE437422C49EF12A28 | binary | |
MD5:68418C81DE57BA10F1604A7911445100 | SHA256:3EA098F6563CD77FF9EAA5E71A52C4066CFF0F1C49B66FFC18F15E1E3E7A19AE | |||
| 6752 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:05E1820666B02195BBB959A81AE5AFE4 | SHA256:0588A8FAA8FDAC361AC48C11F1AC8CA166C1A411CB5C449827A6CA58077A95E6 | |||
| 6752 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:B99581F5F158E42EEA4E14F62D48DDB4 | SHA256:26330F91A7D427E1AF9DF989760B91A41AD3B8D93EAD1E31C40EFA837E8D11E0 | |||
| 6752 | CCleaner64.exe | — | ||
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
68
DNS requests
47
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7996 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6752 | CCleaner64.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
6752 | CCleaner64.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6752 | CCleaner64.exe | GET | 200 | 2.16.168.113:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
4212 | CCleaner64.exe | GET | 200 | 2.16.168.113:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
6752 | CCleaner64.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAXfj0A2M0oL7zuU%2F%2F2jetU%3D | unknown | — | — | whitelisted |
6752 | CCleaner64.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7540 | vnc.exe | Misc activity | ET SCAN Behavioral Unusually fast Terminal Server Traffic Potential Scan or Infection (Outbound) |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
6752 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |