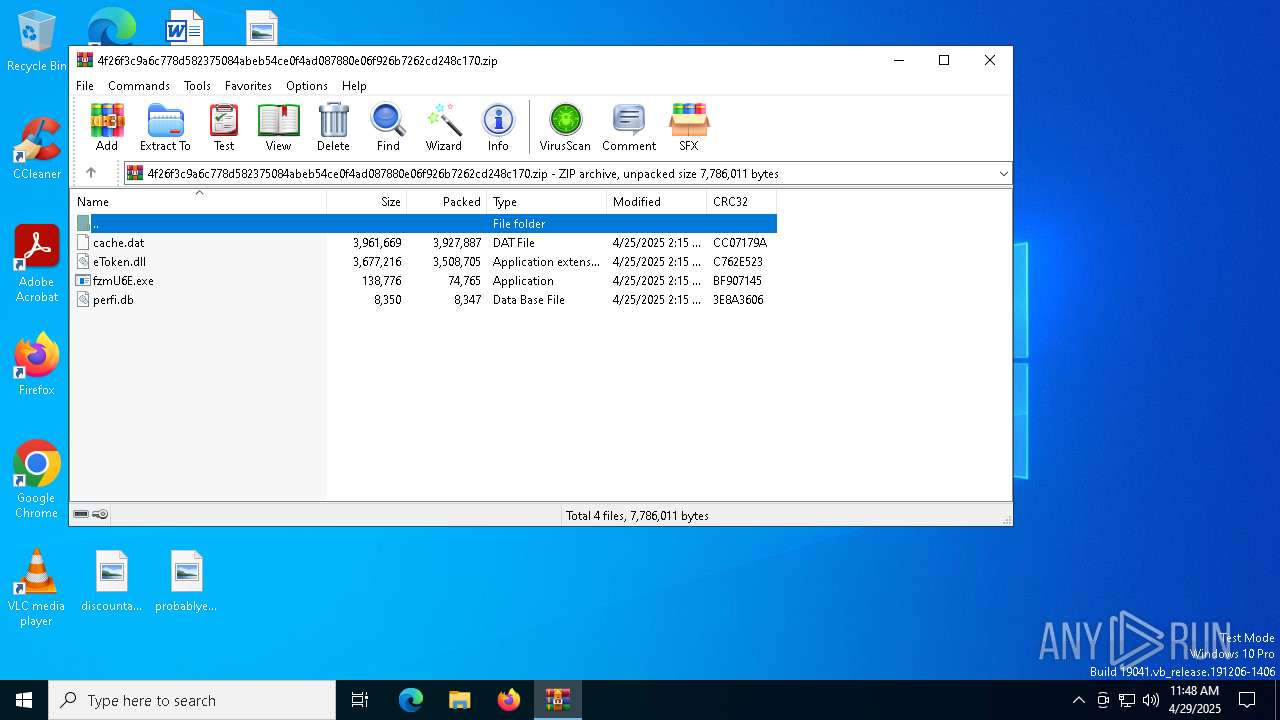
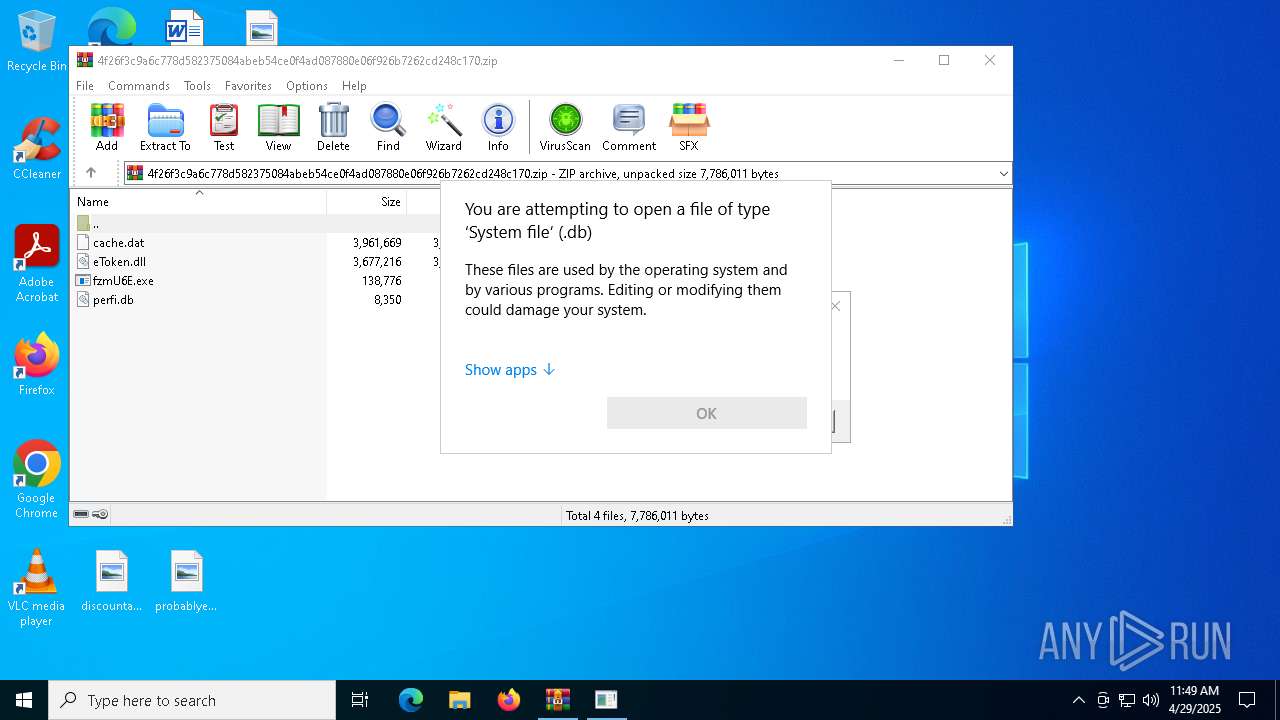
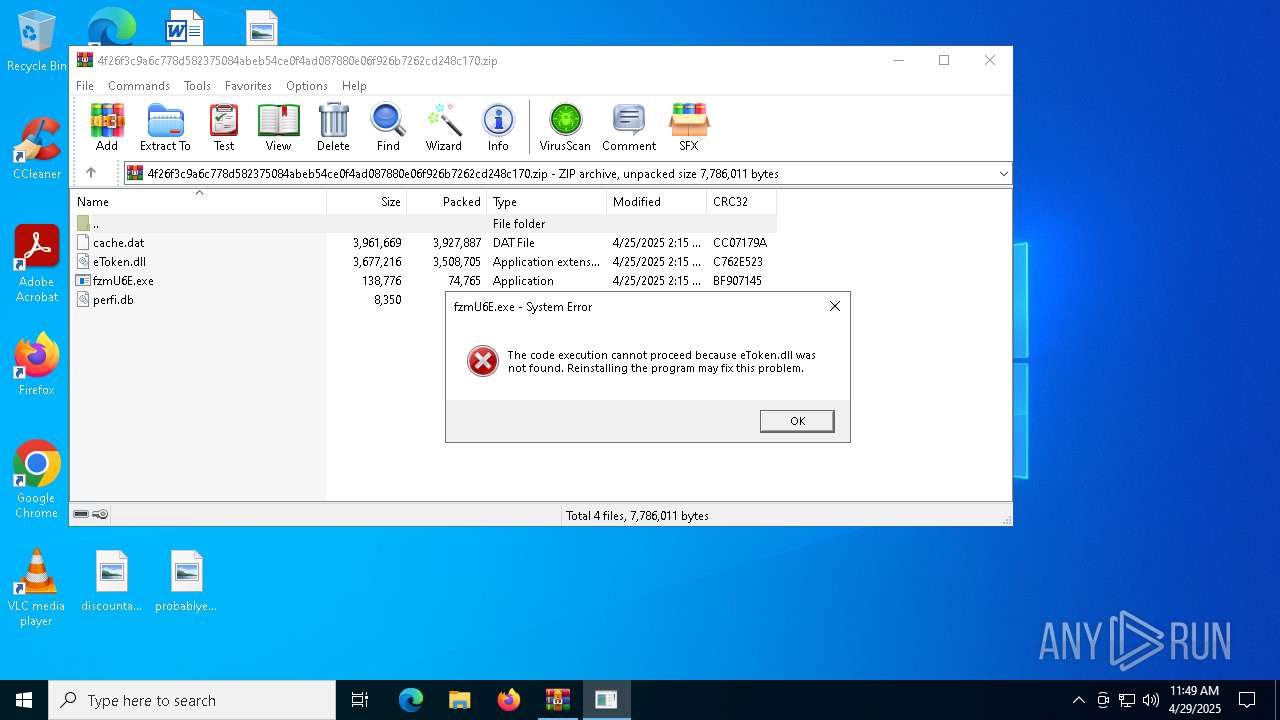
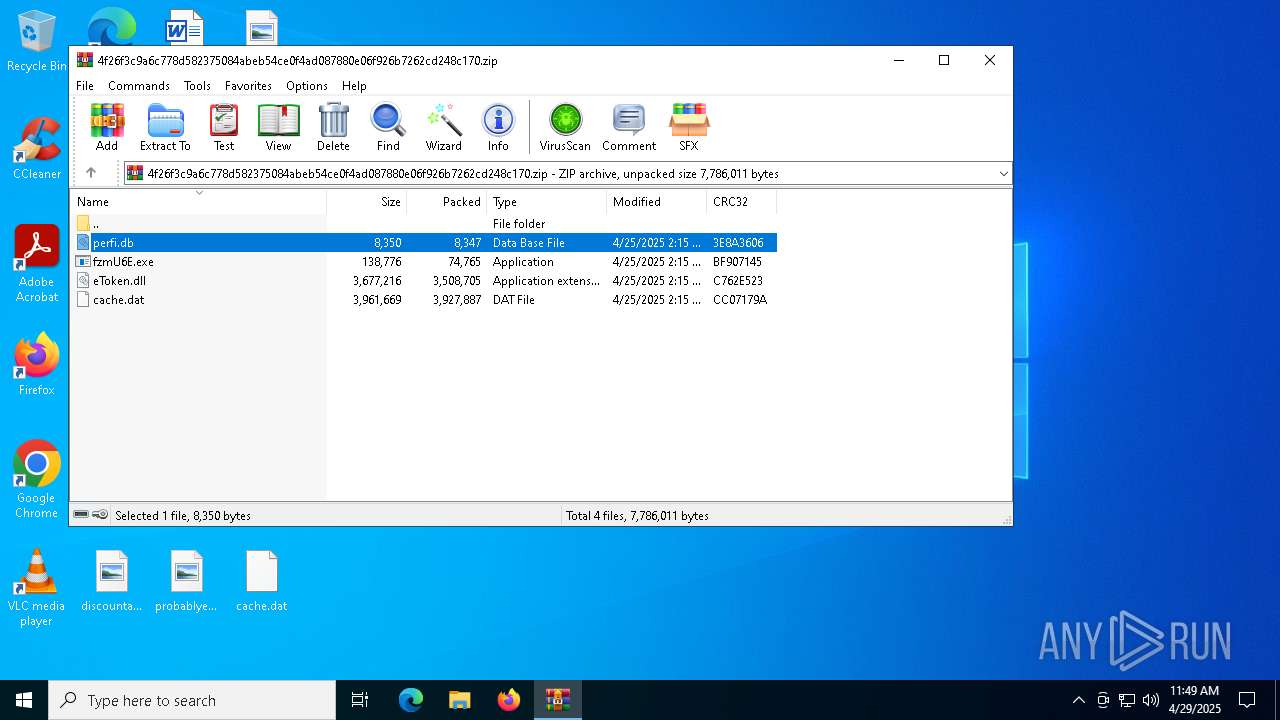
| File name: | 4f26f3c9a6c778d582375084abeb54ce0f4ad087880e06f926b7262cd248c170 |
| Full analysis: | https://app.any.run/tasks/10726324-8ccb-4bd6-91e1-7241dcf7001f |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 11:48:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1E3B123805539AFA541E7002F491CFAB |
| SHA1: | 4022BB5A8D08C370F0C468EFFEF3DC601C11D6F1 |
| SHA256: | 4F26F3C9A6C778D582375084ABEB54CE0F4AD087880E06F926B7262CD248C170 |
| SSDEEP: | 98304:m/FSlpVg3RPzncP4Obfkc6ManA2WnCOzgx59mvqmwydEjtJPX/PdNImaRd2s3+mX:uv0+4vKQk+awKLCDH |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7684)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7684)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7684)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7684)
INFO
Manual execution by a user
- fzmU6E.exe (PID: 7876)
- fzmU6E.exe (PID: 7828)
- OpenWith.exe (PID: 7984)
- OpenWith.exe (PID: 7920)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7920)
- OpenWith.exe (PID: 7984)
Checks supported languages
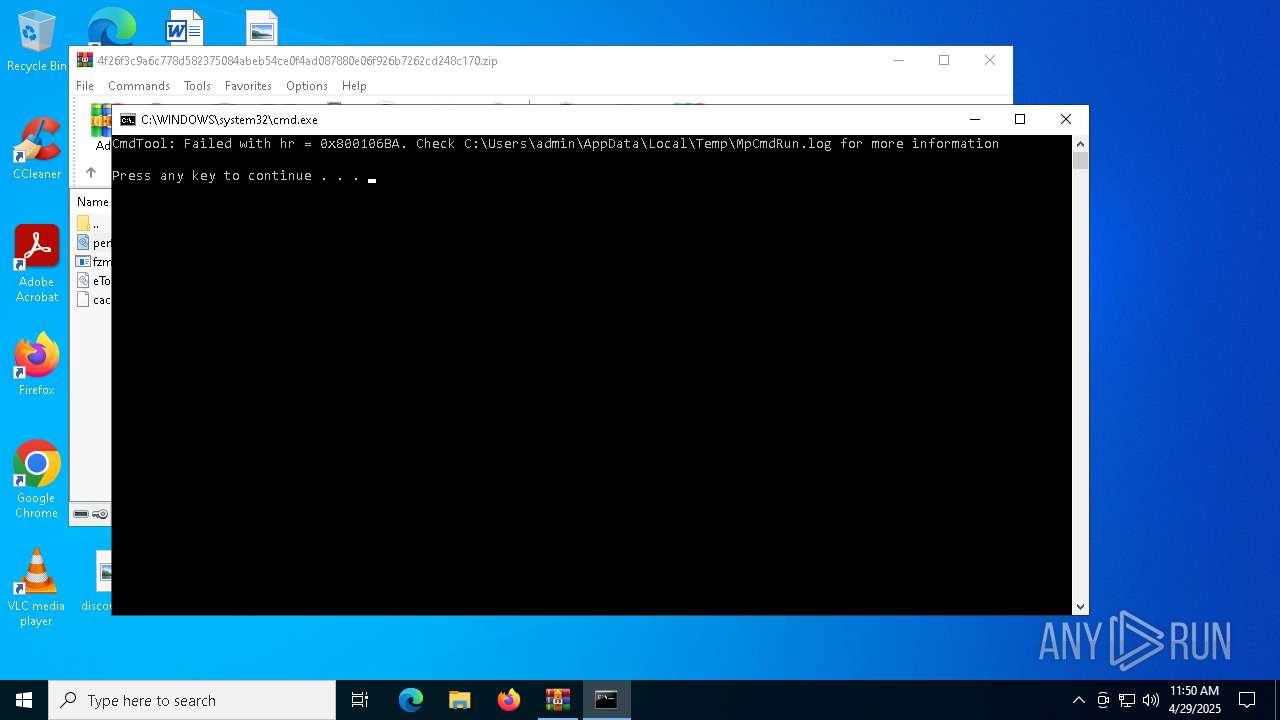
- MpCmdRun.exe (PID: 1228)
The sample compiled with english language support
- WinRAR.exe (PID: 7684)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7684)
Create files in a temporary directory
- MpCmdRun.exe (PID: 1228)
Reads the computer name
- MpCmdRun.exe (PID: 1228)
Checks proxy server information
- slui.exe (PID: 6404)
Reads the software policy settings
- slui.exe (PID: 6404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:25 10:15:22 |
| ZipCRC: | 0xcc07179a |
| ZipCompressedSize: | 3927887 |
| ZipUncompressedSize: | 3961669 |
| ZipFileName: | cache.dat |
Total processes
133
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
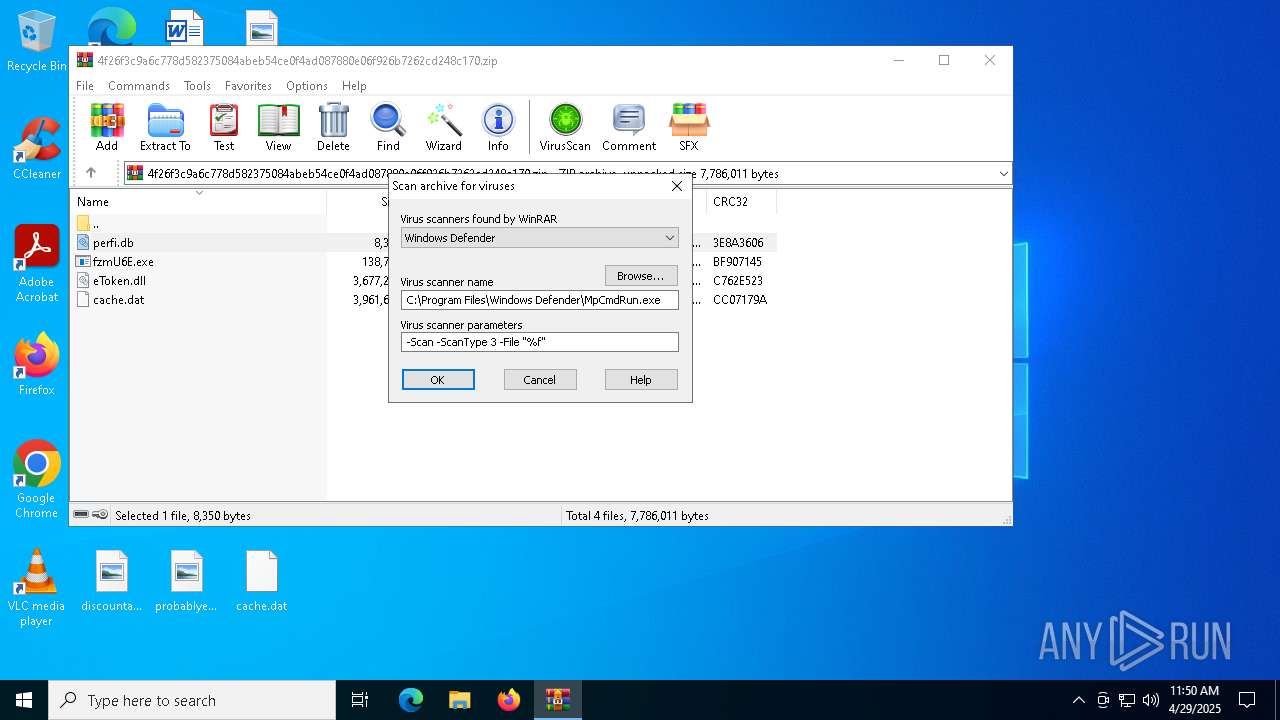
| 1228 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7684.25713" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7684.25713\Rar$Scan110185.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6404 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7684 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\4f26f3c9a6c778d582375084abeb54ce0f4ad087880e06f926b7262cd248c170.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7828 | "C:\Users\admin\Desktop\fzmU6E.exe" | C:\Users\admin\Desktop\fzmU6E.exe | — | explorer.exe | |||||||||||
User: admin Company: Thales Integrity Level: MEDIUM Description: eToken readers management tool Exit code: 3221226540 Version: 10,9,3283,0 Modules
| |||||||||||||||
| 7876 | "C:\Users\admin\Desktop\fzmU6E.exe" | C:\Users\admin\Desktop\fzmU6E.exe | explorer.exe | ||||||||||||
User: admin Company: Thales Integrity Level: HIGH Description: eToken readers management tool Exit code: 3221225781 Version: 10,9,3283,0 Modules
| |||||||||||||||
| 7920 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\perfi.db | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7984 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\cache.dat | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 157
Read events
6 144
Write events
13
Delete events
0
Modification events
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\4f26f3c9a6c778d582375084abeb54ce0f4ad087880e06f926b7262cd248c170.zip | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7920) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.db\OpenWithProgids |
| Operation: | write | Name: | dbfile |
Value: | |||
| (PID) Process: | (7684) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
Executable files
2
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7684.25713\4f26f3c9a6c778d582375084abeb54ce0f4ad087880e06f926b7262cd248c170.zip\cache.dat | image | |
MD5:599FA79EA859421BCED546351C426885 | SHA256:802AD8A2D573CE7B8CE6B901B7C7B6B516FD54E9C2B3D819F30967BC1D03A8FA | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7684.25713\4f26f3c9a6c778d582375084abeb54ce0f4ad087880e06f926b7262cd248c170.zip\fzmU6E.exe | executable | |
MD5:DF76205EAF175184567FC44A83019B20 | SHA256:A6123E13E12A1A1D4C4A4EB034769BFE8E229C3A9877E0DD173B422E700A26AC | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7684.25713\4f26f3c9a6c778d582375084abeb54ce0f4ad087880e06f926b7262cd248c170.zip\eToken.dll | executable | |
MD5:017B78A8D034F17FD265B321BC7A2CFC | SHA256:773F1E61850A7E5BB8315DD5643E19E239BCDD0D539901C1B5DA31E20052F866 | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7684.25713\Rar$Scan110185.bat | text | |
MD5:7A32A819D08A50F243E171C6164316C5 | SHA256:1572C232AE0C14E4E0C3D1EFD838CB919C421FF3C02870D4C8A201E114F5FBEB | |||
| 7684 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7684.25713\4f26f3c9a6c778d582375084abeb54ce0f4ad087880e06f926b7262cd248c170.zip\perfi.db | binary | |
MD5:D7B985D13484016E8540280DE8662054 | SHA256:B84C2D03219681A9AAC19915D1D63616C1D59BAD246A2D658223F0E99C345E7E | |||
| 1228 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:15DC6BCAD88238EF82B239B79A5DAB89 | SHA256:9D4E6033E2CCA77CA9A627A22657ECA2F3D40A393EEE5F7A67D88658D47FD863 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
50
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |