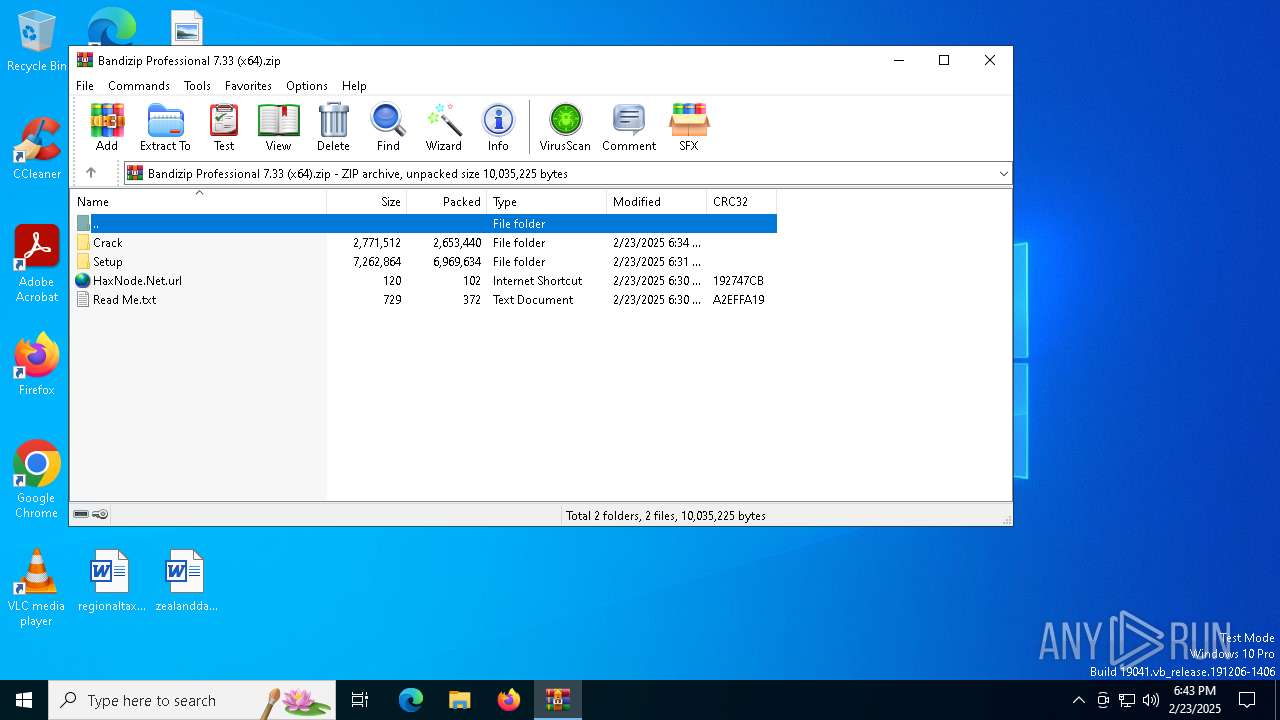
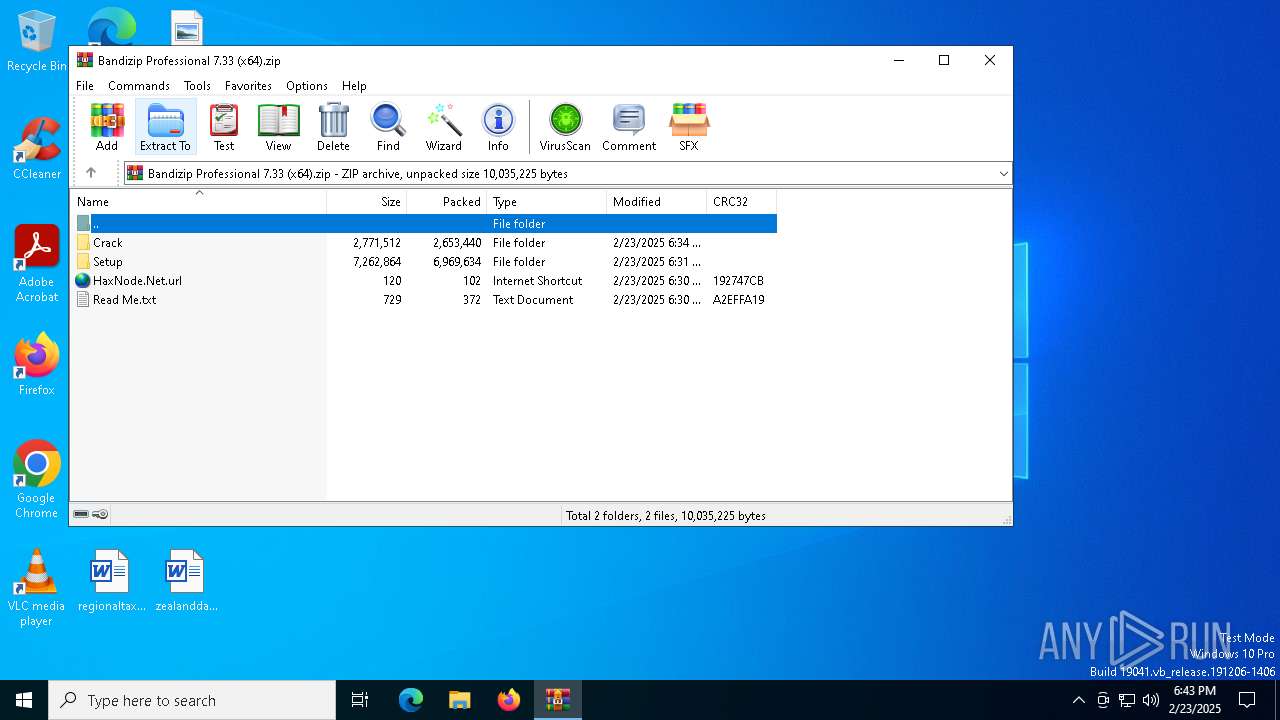
| File name: | Bandizip Professional 7.33 (x64).zip |
| Full analysis: | https://app.any.run/tasks/e57c6188-c93e-4617-a612-9914d8764f3d |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2025, 18:43:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | F2FE6D74F52BA39C6656B91E232D5A3E |
| SHA1: | D4E386F071316E9E3C78BADF9C08744F5B10CD00 |
| SHA256: | 4F15E8FC35D6DB63A5759BD8A904135A9DA5CC7079CB726EDC13FE2291B89A33 |
| SSDEEP: | 98304:VjHQrrFe6ToREw+qcfMlpFgAbpGp5ReagpqLqOYkmvDFqdrTQ34ChLFAkoVbenqB:W49egR/HbzgQtt+rhJ |
MALICIOUS
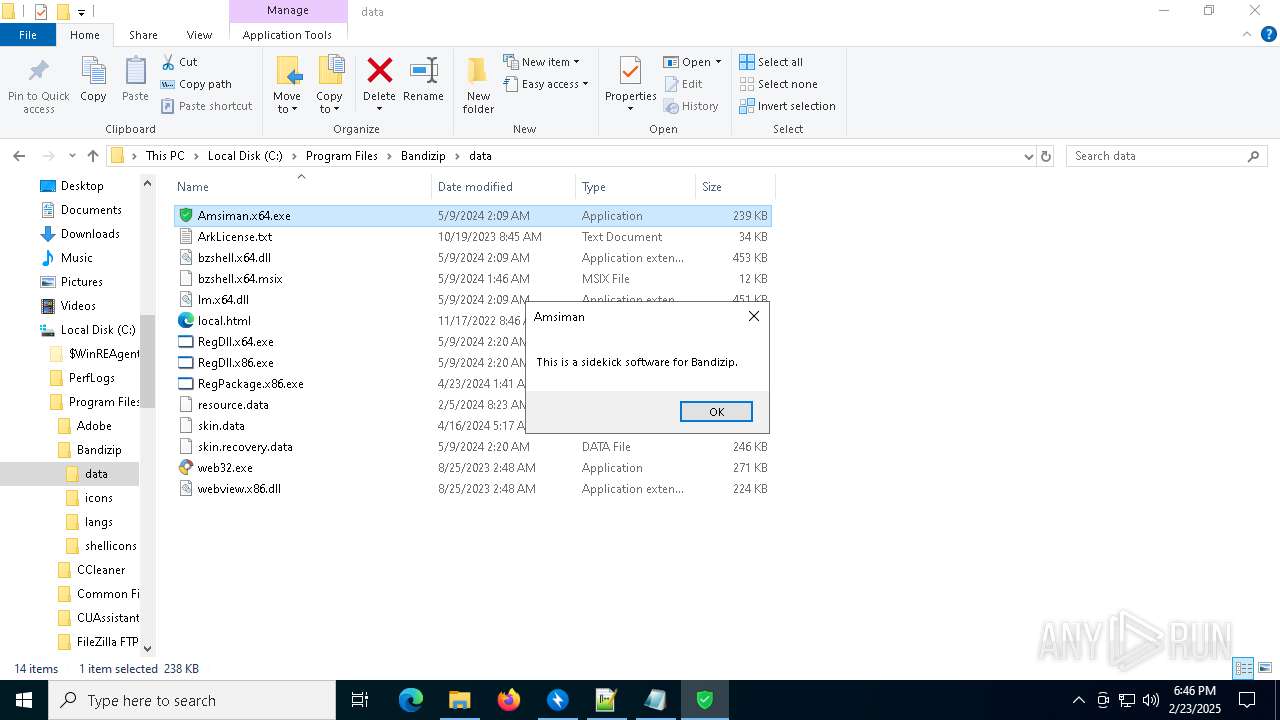
Executing a file with an untrusted certificate
- Setup.exe (PID: 3224)
- Setup.exe (PID: 2728)
- Bandizip.exe (PID: 1576)
- RegDll.x86.exe (PID: 1344)
- RegDll.x86.exe (PID: 4052)
- RegDll.x86.exe (PID: 2512)
- RegDll.x86.exe (PID: 5540)
- RegDll.x64.exe (PID: 5872)
- RegDll.x64.exe (PID: 5748)
- RegDll.x64.exe (PID: 4528)
- Bandizip.exe (PID: 4540)
- RegDll.x64.exe (PID: 4984)
- Bandizip.exe (PID: 6344)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- Bandizip.exe (PID: 536)
- RegPackage.x86.exe (PID: 7104)
- Bandizip.exe (PID: 3524)
- web32.exe (PID: 776)
- web32.exe (PID: 5568)
- RegDll.x86.exe (PID: 4932)
- RegPackage.x86.exe (PID: 2164)
- Amsiman.x64.exe (PID: 4912)
Generic archive extractor
- WinRAR.exe (PID: 6372)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6372)
- Setup.exe (PID: 2728)
- Bandizip.exe (PID: 6344)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- Bandizip.exe (PID: 536)
- Bandizip.exe (PID: 3524)
Checks Windows Trust Settings
- Setup.exe (PID: 2728)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- Bandizip.exe (PID: 536)
- Bandizip.exe (PID: 3524)
Executable content was dropped or overwritten
- Setup.exe (PID: 2728)
- dllhost.exe (PID: 1596)
Creates/Modifies COM task schedule object
- RegDll.x86.exe (PID: 5540)
- RegDll.x64.exe (PID: 5872)
Changes Internet Explorer settings (feature browser emulation)
- RegDll.x86.exe (PID: 1344)
- RegDll.x86.exe (PID: 2512)
- RegDll.x86.exe (PID: 4052)
Creates a software uninstall entry
- Setup.exe (PID: 2728)
Reads the date of Windows installation
- RegDll.x64.exe (PID: 4528)
- Bandizip.exe (PID: 6344)
Reads Internet Explorer settings
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
Reads Microsoft Outlook installation path
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
Application launched itself
- Bandizip.exe (PID: 6344)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6372)
Local mutex for internet shortcut management
- WinRAR.exe (PID: 6372)
The sample compiled with english language support
- WinRAR.exe (PID: 6372)
Checks supported languages
- Setup.exe (PID: 2728)
- Bandizip.exe (PID: 1576)
- RegDll.x86.exe (PID: 2512)
- RegDll.x86.exe (PID: 1344)
- RegDll.x86.exe (PID: 4052)
- RegDll.x86.exe (PID: 5540)
- RegDll.x64.exe (PID: 5872)
- RegDll.x64.exe (PID: 4528)
- RegDll.x64.exe (PID: 4984)
- Bandizip.exe (PID: 4540)
- Bandizip.exe (PID: 6344)
- RegDll.x64.exe (PID: 5748)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- Bandizip.exe (PID: 536)
- RegPackage.x86.exe (PID: 7104)
- Bandizip.exe (PID: 3524)
- web32.exe (PID: 776)
- web32.exe (PID: 5568)
- RegPackage.x86.exe (PID: 2164)
- RegDll.x86.exe (PID: 4932)
- Amsiman.x64.exe (PID: 4912)
Manual execution by a user
- Setup.exe (PID: 3224)
- Setup.exe (PID: 2728)
- Bandizip.exe (PID: 6344)
- RegDll.x64.exe (PID: 4528)
- Bandizip.exe (PID: 3524)
- notepad++.exe (PID: 5748)
- notepad.exe (PID: 4384)
- web32.exe (PID: 776)
- web32.exe (PID: 5568)
- RegDll.x86.exe (PID: 4932)
- RegPackage.x86.exe (PID: 2164)
- Amsiman.x64.exe (PID: 4912)
Checks proxy server information
- Setup.exe (PID: 2728)
- Bandizip.exe (PID: 6344)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- Bandizip.exe (PID: 536)
- Bandizip.exe (PID: 3524)
Reads the computer name
- Setup.exe (PID: 2728)
- RegDll.x64.exe (PID: 4528)
- Bandizip.exe (PID: 6344)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- RegPackage.x86.exe (PID: 7104)
- Bandizip.exe (PID: 536)
- Bandizip.exe (PID: 3524)
- RegDll.x86.exe (PID: 4932)
- RegPackage.x86.exe (PID: 2164)
- Amsiman.x64.exe (PID: 4912)
Reads the machine GUID from the registry
- Setup.exe (PID: 2728)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- Bandizip.exe (PID: 536)
- Bandizip.exe (PID: 3524)
Reads the software policy settings
- Setup.exe (PID: 2728)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
- Bandizip.exe (PID: 536)
- Bandizip.exe (PID: 3524)
Creates files or folders in the user directory
- Setup.exe (PID: 2728)
- RegDll.x64.exe (PID: 4528)
- Updater.exe (PID: 5432)
- web32.exe (PID: 6896)
Creates files in the program directory
- Setup.exe (PID: 2728)
The sample compiled with korean language support
- Setup.exe (PID: 2728)
Process checks computer location settings
- RegDll.x64.exe (PID: 4528)
- Bandizip.exe (PID: 6344)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 1596)
- notepad.exe (PID: 4384)
Create files in a temporary directory
- Bandizip.exe (PID: 3524)
UPX packer has been detected
- Bandizip.exe (PID: 3524)
Mpress packer has been detected
- Bandizip.exe (PID: 3524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:23 21:34:50 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Crack/ |
Total processes
154
Monitored processes
28
Malicious processes
8
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\Bandizip\Bandizip.exe" | C:\Program Files\Bandizip\Bandizip.exe | Bandizip.exe | ||||||||||||
User: admin Company: Bandisoft International Inc. Integrity Level: MEDIUM Description: Bandizip Exit code: 0 Version: 7.33.0.1 Modules
| |||||||||||||||
| 776 | "C:\Program Files\Bandizip\data\web32.exe" | C:\Program Files\Bandizip\data\web32.exe | — | explorer.exe | |||||||||||
User: admin Company: Bandisoft.com Integrity Level: MEDIUM Description: Web32 web control process Exit code: 2 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Bandizip\data\RegDll.x86.exe" /regieemulation Bandizip.exe | C:\Program Files\Bandizip\data\RegDll.x86.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Bandizip\Bandizip.exe" /regmandatoryadmin | C:\Program Files\Bandizip\Bandizip.exe | — | Setup.exe | |||||||||||
User: admin Company: Bandisoft International Inc. Integrity Level: HIGH Description: Bandizip Exit code: 0 Version: 7.33.0.1 Modules
| |||||||||||||||
| 1596 | C:\WINDOWS\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2164 | "C:\Program Files\Bandizip\data\RegPackage.x86.exe" | C:\Program Files\Bandizip\data\RegPackage.x86.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 286326785 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Bandizip\data\RegDll.x86.exe" /regieemulation Updater.exe | C:\Program Files\Bandizip\data\RegDll.x86.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
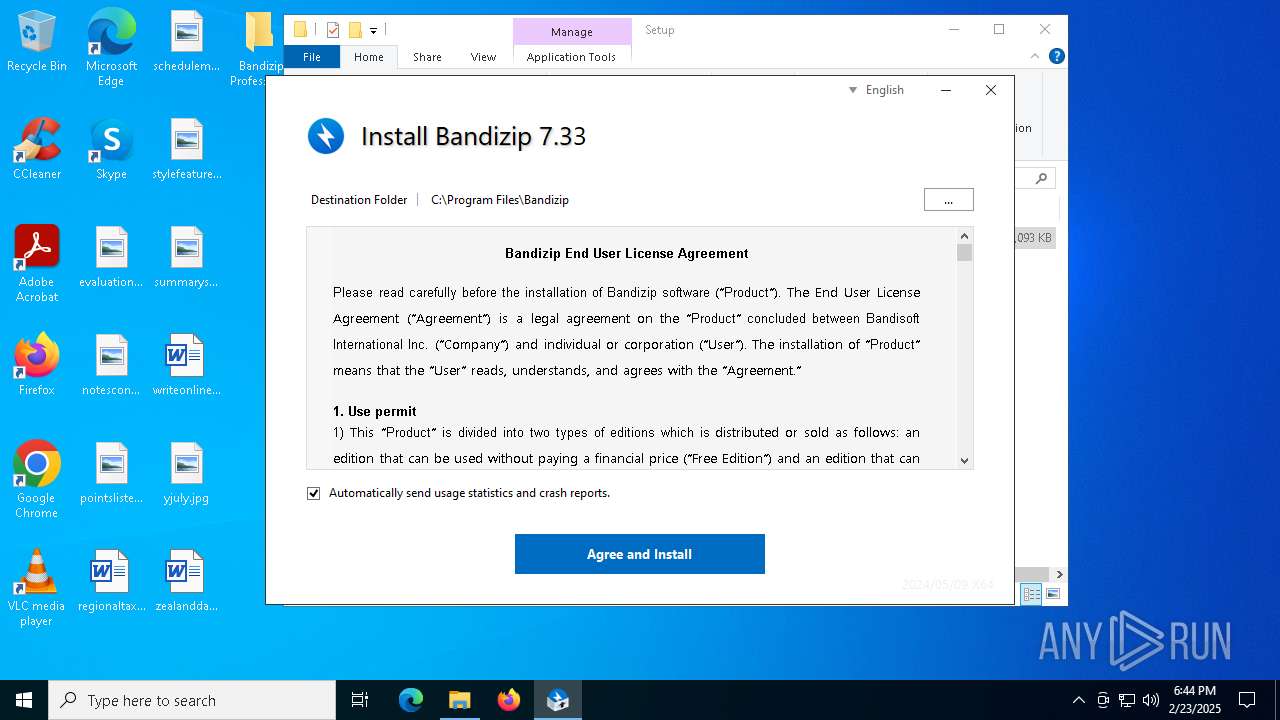
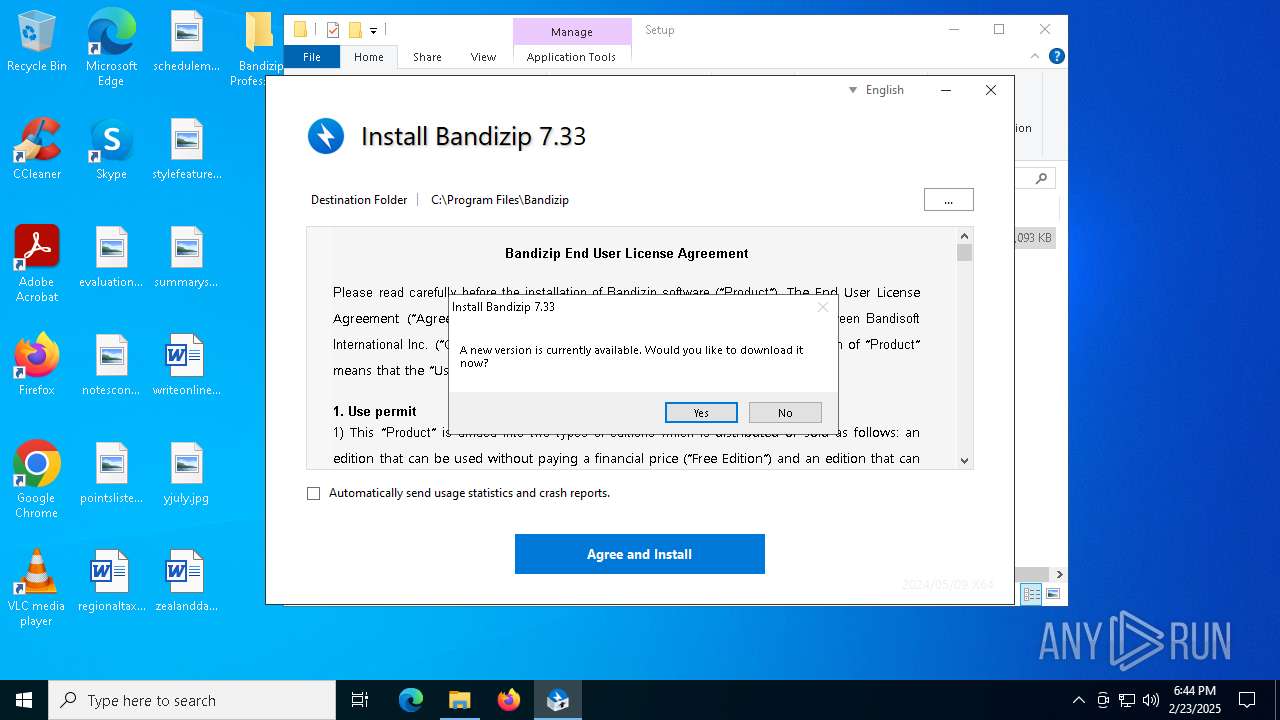
| 2728 | "C:\Users\admin\Desktop\Bandizip Professional 7.33 (x64)\Setup\Setup.exe" | C:\Users\admin\Desktop\Bandizip Professional 7.33 (x64)\Setup\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Bandisoft Integrity Level: HIGH Description: Bandizip 7.33 0 Setup Exit code: 0 Version: 7.33 Modules
| |||||||||||||||
| 3224 | "C:\Users\admin\Desktop\Bandizip Professional 7.33 (x64)\Setup\Setup.exe" | C:\Users\admin\Desktop\Bandizip Professional 7.33 (x64)\Setup\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Bandisoft Integrity Level: MEDIUM Description: Bandizip 7.33 0 Setup Exit code: 3221226540 Version: 7.33 Modules
| |||||||||||||||
| 3524 | "C:\Program Files\Bandizip\Bandizip.exe" | C:\Program Files\Bandizip\Bandizip.exe | explorer.exe | ||||||||||||
User: admin Company: Bandisoft International Inc. Integrity Level: MEDIUM Description: Bandizip Version: 7.33.0.1 Modules
| |||||||||||||||
Total events
13 830
Read events
12 139
Write events
1 676
Delete events
15
Modification events
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Bandizip Professional 7.33 (x64).zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
25
Suspicious files
61
Text files
49
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2728 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\035E52AEDA0CBD41F7A1EE1F14E33688 | binary | |
MD5:9477BE617479F833549DA6322F9486BA | SHA256:CA27232C373DFEE29E8FBA8E2E7DA136B876FEDC3ED560920193CC5472C471CE | |||
| 2728 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:4397A42ACEAB0D7C183C811795082D83 | SHA256:256C2C355905E5A0D894F0963DADFE49AA6D30F88B9FBCBAC96038B3D3A702F0 | |||
| 6372 | WinRAR.exe | C:\Users\admin\Desktop\Bandizip Professional 7.33 (x64)\Setup\Setup.exe | executable | |
MD5:E30461839158144FF5AC897D2E7A96C1 | SHA256:E20BD0A77802EFE4274FDDB7198977AF6B0FE01845B4E1776052881B267B1AA5 | |||
| 2728 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\035E52AEDA0CBD41F7A1EE1F14E33688 | binary | |
MD5:5E29D4CE2A2E4954697BA3E4B6712DC3 | SHA256:668CA1875E8D96DA93428A487323012E551C0F07EA026A532DE29BAD45A97C00 | |||
| 2728 | Setup.exe | C:\Program Files\Bandizip\bdzshl.x64.dll | executable | |
MD5:BB6D82190A9566941C475CE2171D25B5 | SHA256:5FAE9E9F6D6D8BA6300DD4306666AFD2796AF39F52F2C7BD33DA8772E584898A | |||
| 6372 | WinRAR.exe | C:\Users\admin\Desktop\Bandizip Professional 7.33 (x64)\Read Me.txt | text | |
MD5:27F7E9FE736B1D8EFB645A6B4166CFB0 | SHA256:71C9D8EB468EB555BA692249F55FFB37B96EE5BFDFCAA07C90BF790C8D04C22A | |||
| 2728 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:0CB76E0439CD88EB91C9CFC1F779060C | SHA256:D1444AB750204141AF3D4BD1086A41752384DB8E9983DF0689B5B451E8804D44 | |||
| 2728 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:7367C4E9FA9D5B89CC2072FD24581695 | SHA256:864CBAF6F6681E069018624BCCE17775059172B9CCC5A06328652DD640698D64 | |||
| 2728 | Setup.exe | C:\Program Files\Bandizip\data\skin.data | compressed | |
MD5:5C8D06D3E7EF6A547951610FDEA0C2EB | SHA256:FF7472D2D2C9B6567A4ADB03DEAECBB75BC1B6EC07D95AF122780DD51D4FA4AC | |||
| 2728 | Setup.exe | C:\Program Files\Bandizip\ark.x86.dll | executable | |
MD5:722FF103F4C2509FD12B374EE490BB7C | SHA256:845DB7FBE66A86665A772A6D723808A18D9723F8C1516810857EA07A68B68A73 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
48
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6600 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2728 | Setup.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
2728 | Setup.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
2728 | Setup.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEHby99qPBsQR44pGbdwfRPc%3D | unknown | — | — | whitelisted |
5432 | Updater.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
5432 | Updater.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5564 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2324 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|