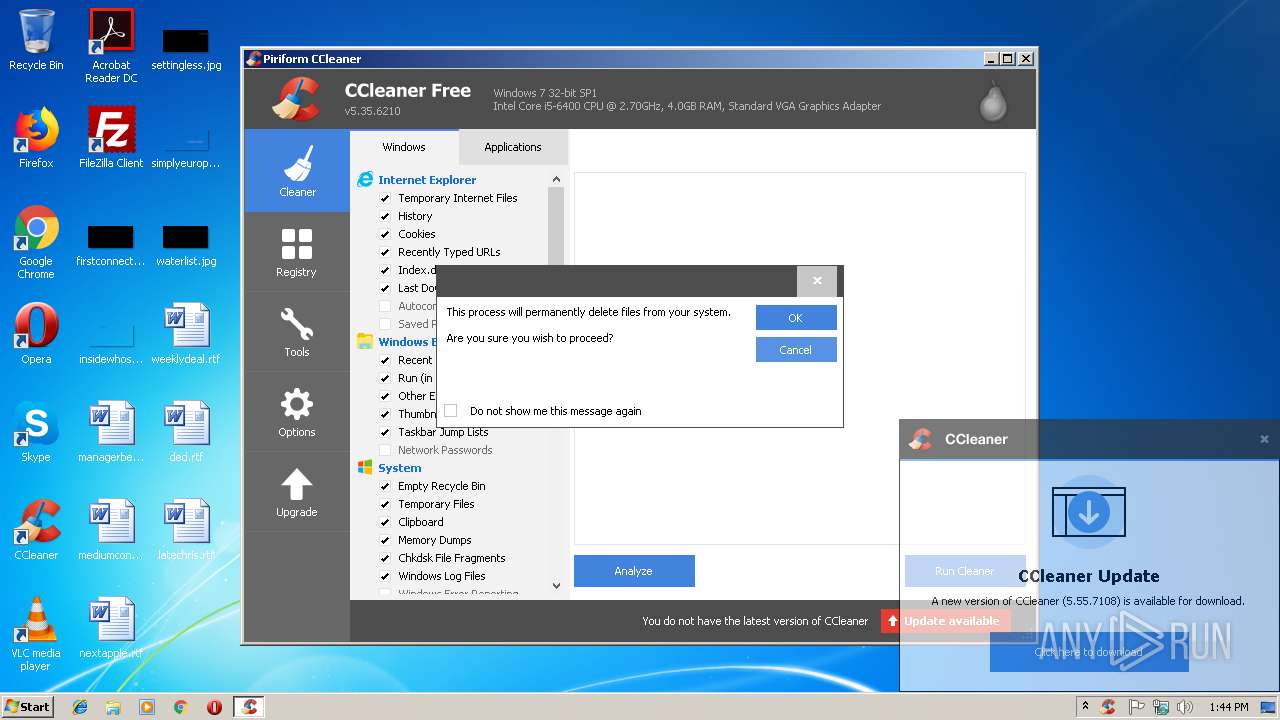
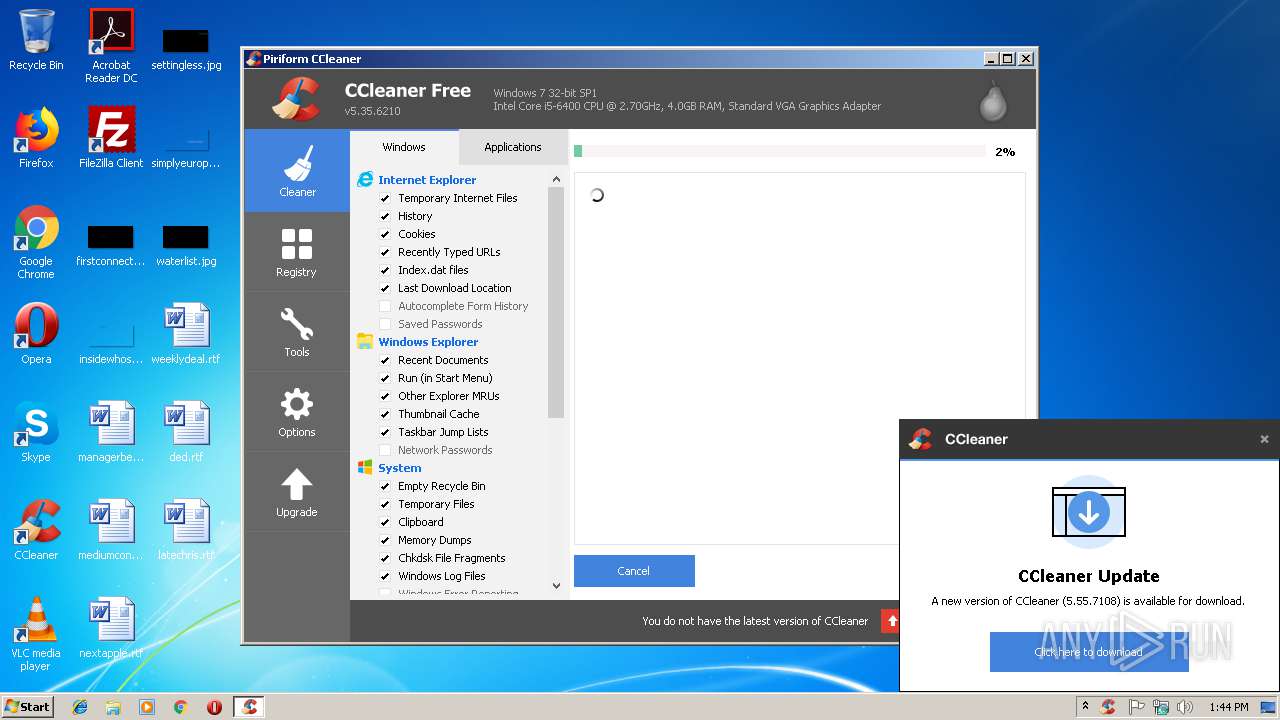
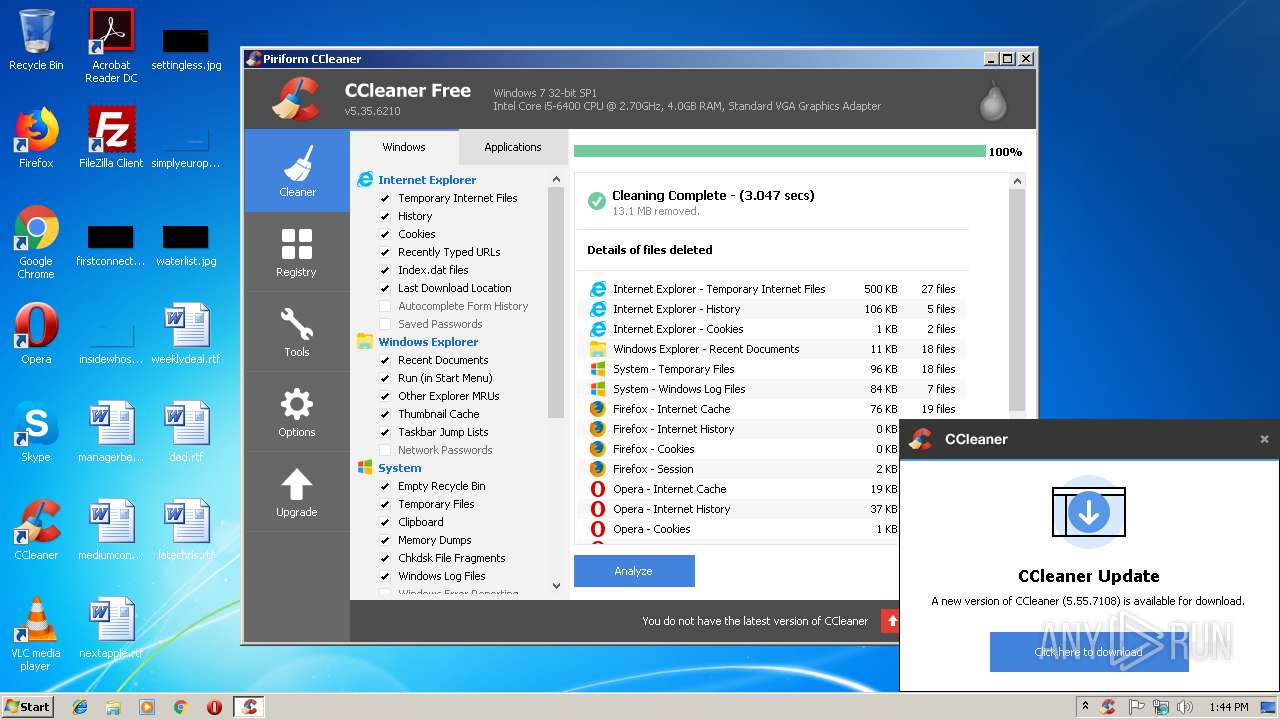
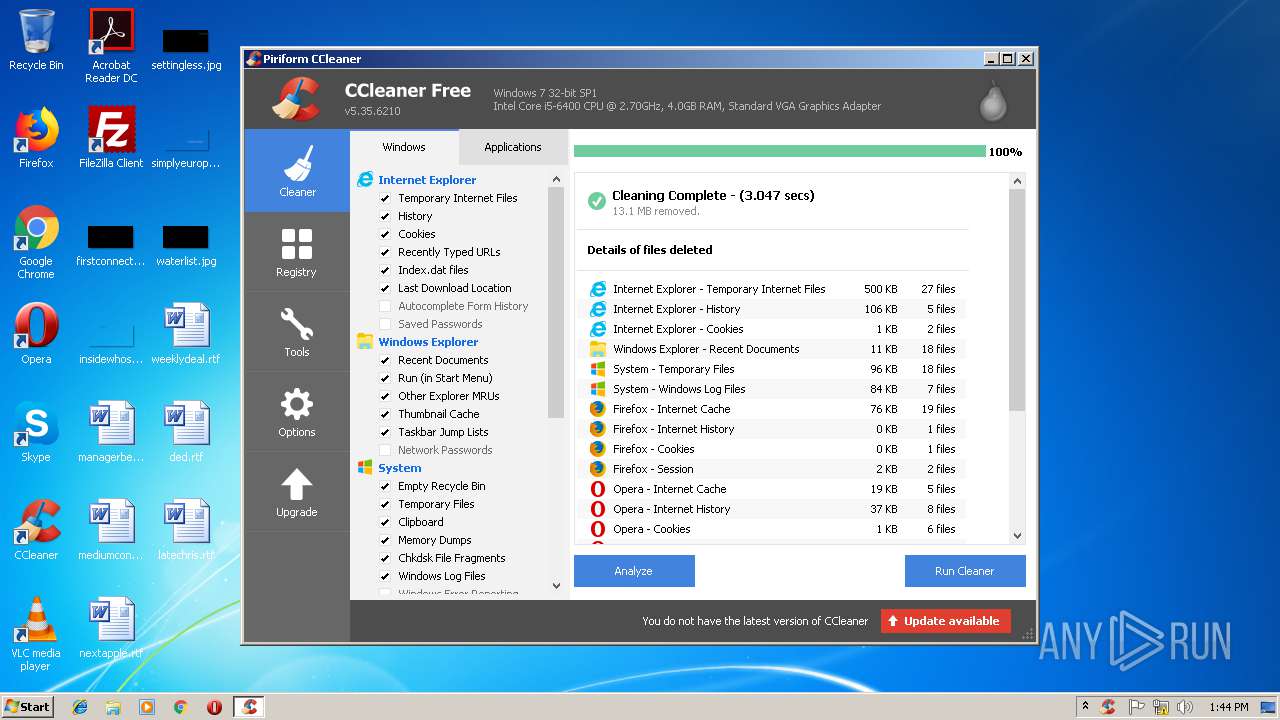
| File name: | 3.exe |
| Full analysis: | https://app.any.run/tasks/2aa79186-d1cc-42f2-b50b-b360b5d14877 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 13:43:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 28BBCE9643FE16BA8AA219D67B06F91D |
| SHA1: | B6AC3A2DEADA8DB7F7CED7A32FC2E9468C0B6266 |
| SHA256: | 4F0B66034A053A747C9BE93D97D4E53E0BCEA2CF92994BD46F4427C9F79B5B3B |
| SSDEEP: | 3072:9liUPXC8k1nJrX+fNTBf+N8SxWvXcEiH+k:9zBkLL2NTBGCemJnk |
MALICIOUS
Actions looks like stealing of personal data
- CCleaner.exe (PID: 2908)
- CCleaner.exe (PID: 3364)
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 3364)
- CCleaner.exe (PID: 2728)
Changes the autorun value in the registry
- CCleaner.exe (PID: 3364)
SUSPICIOUS
Reads internet explorer settings
- CCleaner.exe (PID: 2908)
- CCleaner.exe (PID: 3364)
Executable content was dropped or overwritten
- 3.exe (PID: 2860)
Creates files in the user directory
- 3.exe (PID: 2860)
- CCleaner.exe (PID: 2908)
Starts CMD.EXE for commands execution
- 3.exe (PID: 2860)
Reads the cookies of Google Chrome
- CCleaner.exe (PID: 2908)
Application launched itself
- CCleaner.exe (PID: 2908)
Reads the cookies of Mozilla Firefox
- CCleaner.exe (PID: 2908)
Low-level read access rights to disk partition
- CCleaner.exe (PID: 2908)
Reads Internet Cache Settings
- CCleaner.exe (PID: 2908)
Removes files from Windows directory
- CCleaner.exe (PID: 2908)
INFO
Reads settings of System Certificates
- CCleaner.exe (PID: 2908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 21:18:00+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 67584 |
| InitializedDataSize: | 52224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Feb-2018 20:18:00 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 01-Feb-2018 20:18:00 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.code | 0x00001000 | 0x000037F0 | 0x00003800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.61236 |
.text | 0x00005000 | 0x0000CFA2 | 0x0000D000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.58582 |
.rdata | 0x00012000 | 0x000033A0 | 0x00003400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.11024 |
.data | 0x00016000 | 0x00001724 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.93674 |
.rsrc | 0x00018000 | 0x00008510 | 0x00008600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.97091 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.92322 | 611 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
213E4B4F54AE4F4186D0C15C492CD3CC79BA41D2 | 7.99393 | 32533 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
3D1F5A1768FF03094B7205C1F656F770 | 4.54659 | 26 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
7581988FF961F569E508D38D15734EBACD17187B | 2.58496 | 6 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
7EA50BB2E6EED45D1812A9C4223909DE | 3.88418 | 20 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
C58CFDC25974411E881FF4BAA34E8B07 | 5.91376 | 71 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
DBC1F5D2E2 | 0 | 1 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
COMCTL32.DLL |
GDI32.DLL |
KERNEL32.dll |
MSVCRT.dll |
OLE32.DLL |
SHELL32.DLL |
SHLWAPI.DLL |
USER32.DLL |
WINMM.DLL |
Total processes
39
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2644 | TIMEOUT /T 1 /NOBREAK | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2728 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 2860 | "C:\Users\admin\AppData\Local\Temp\3.exe" | C:\Users\admin\AppData\Local\Temp\3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 3364 | "C:\Program Files\CCleaner\CCleaner.exe" /monitor | C:\Program Files\CCleaner\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 3992 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\E2D2.tmp\E2D3.tmp\E2D4.bat C:\Users\admin\AppData\Local\Temp\3.exe" | C:\Windows\system32\cmd.exe | — | 3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
999
Read events
739
Write events
225
Delete events
35
Modification events
| (PID) Process: | (2860) 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2860) 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2908) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | WipeFreeSpaceDrives |
Value: C:\ | |||
| (PID) Process: | (2908) CCleaner.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3364) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | Monitoring |
Value: 1 | |||
| (PID) Process: | (3364) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CCleaner Monitoring |
Value: "C:\Program Files\CCleaner\CCleaner.exe" /MONITOR | |||
| (PID) Process: | (3364) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | SystemMonitoring |
Value: 1 | |||
| (PID) Process: | (2908) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | CookiesToSave |
Value: *.piriform.com|facebook.com|google.com | |||
| (PID) Process: | (2908) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | RunICS |
Value: 0 | |||
| (PID) Process: | (2908) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | delete value | Name: | AutoICS |
Value: 1 | |||
Executable files
1
Suspicious files
32
Text files
2
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\webappsstore.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IFM8WBRQ6LYGGAQWIHGR.temp | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\TY7BTB0XTCZ21FSFDHWJ.temp | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FP2BSGGW2D10V13Q4W9P.temp | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019031420190315\index.dat | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\16ec093b8f51508f.automaticDestinations-ms | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | — | |
MD5:— | SHA256:— | |||
| 2908 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\7e4dca80246863e3.automaticDestinations-ms | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2908 | CCleaner.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/auto?a=0&p=cc&v=5.35.6210&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2908 | CCleaner.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
2908 | CCleaner.exe | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
2908 | CCleaner.exe | 151.101.2.202:443 | www.ccleaner.com | Fastly | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.piriform.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |