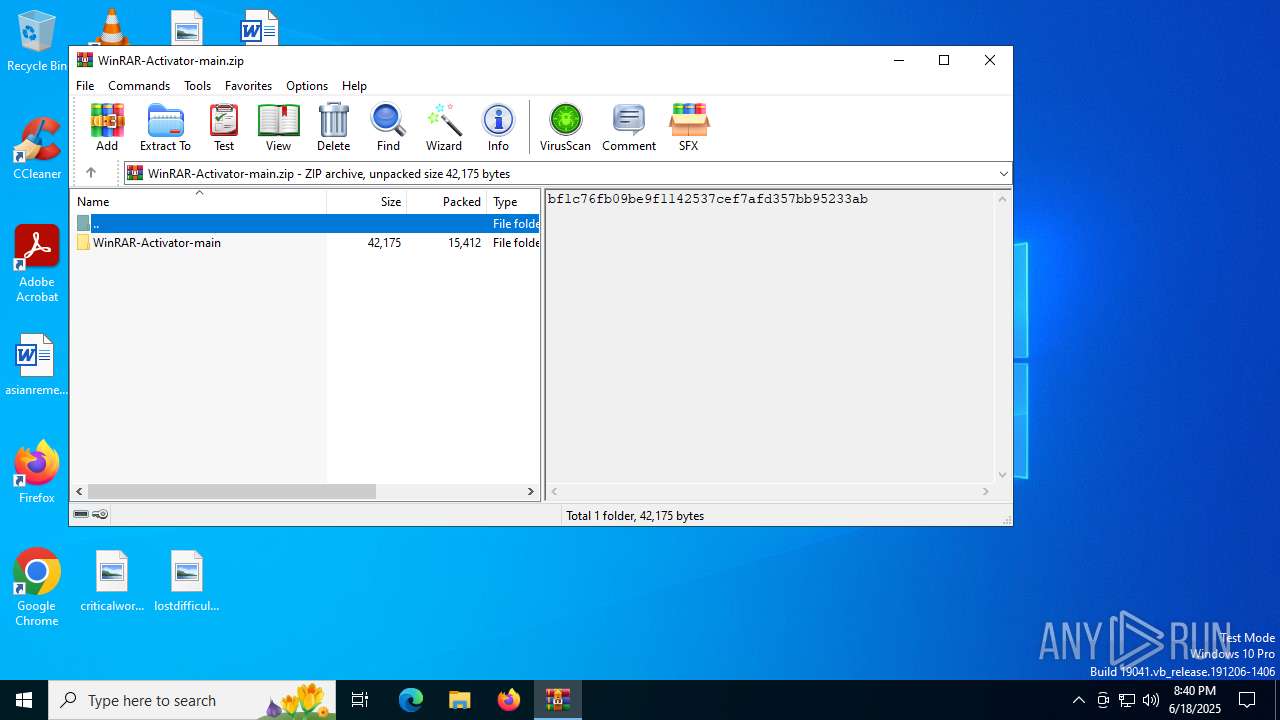
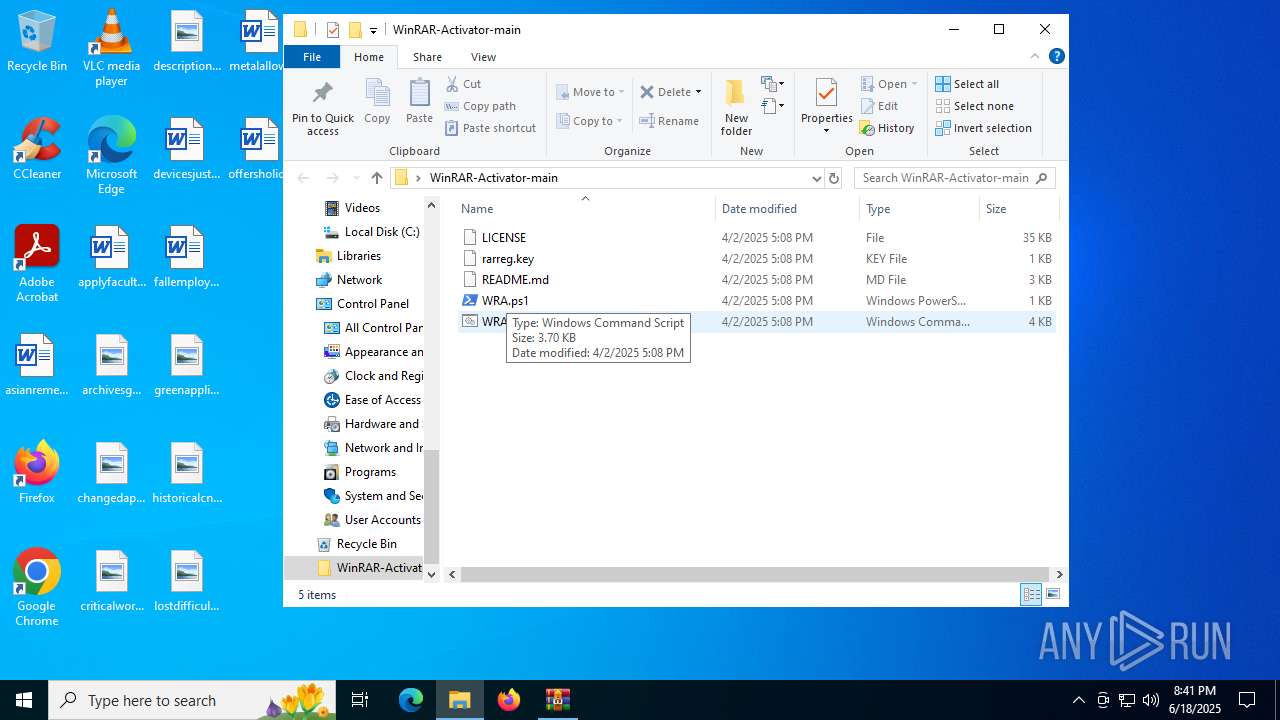
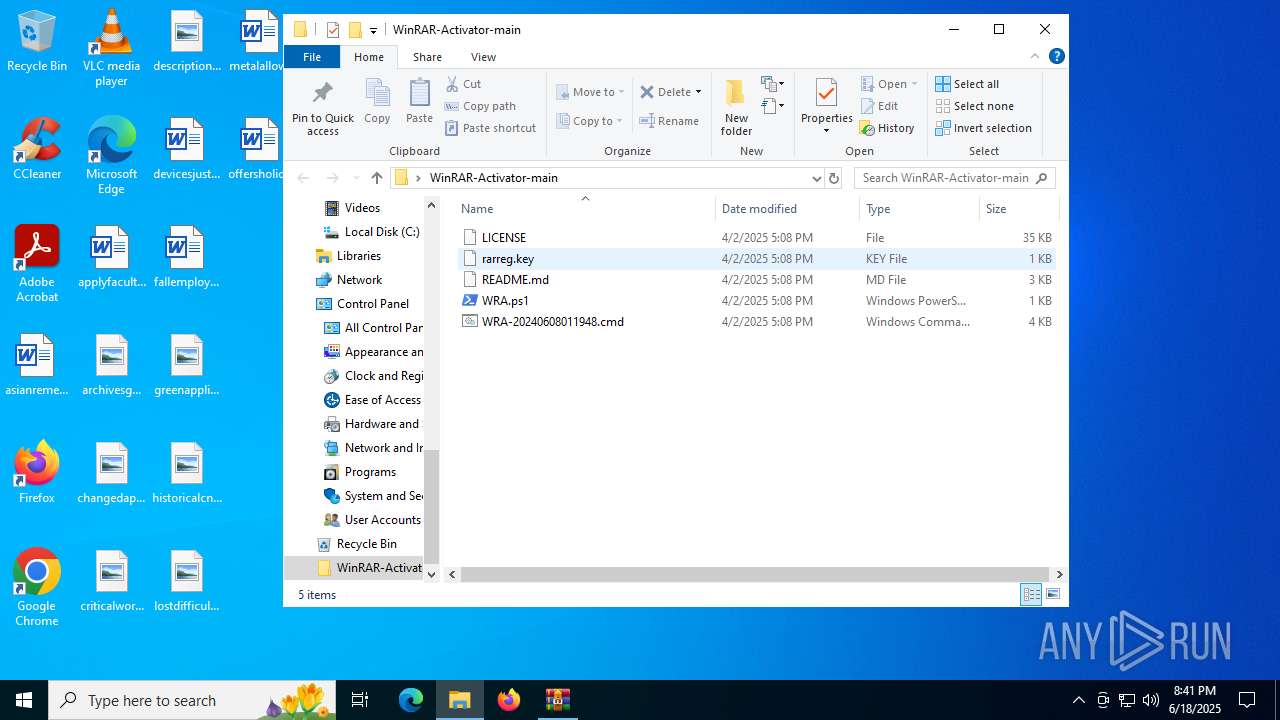
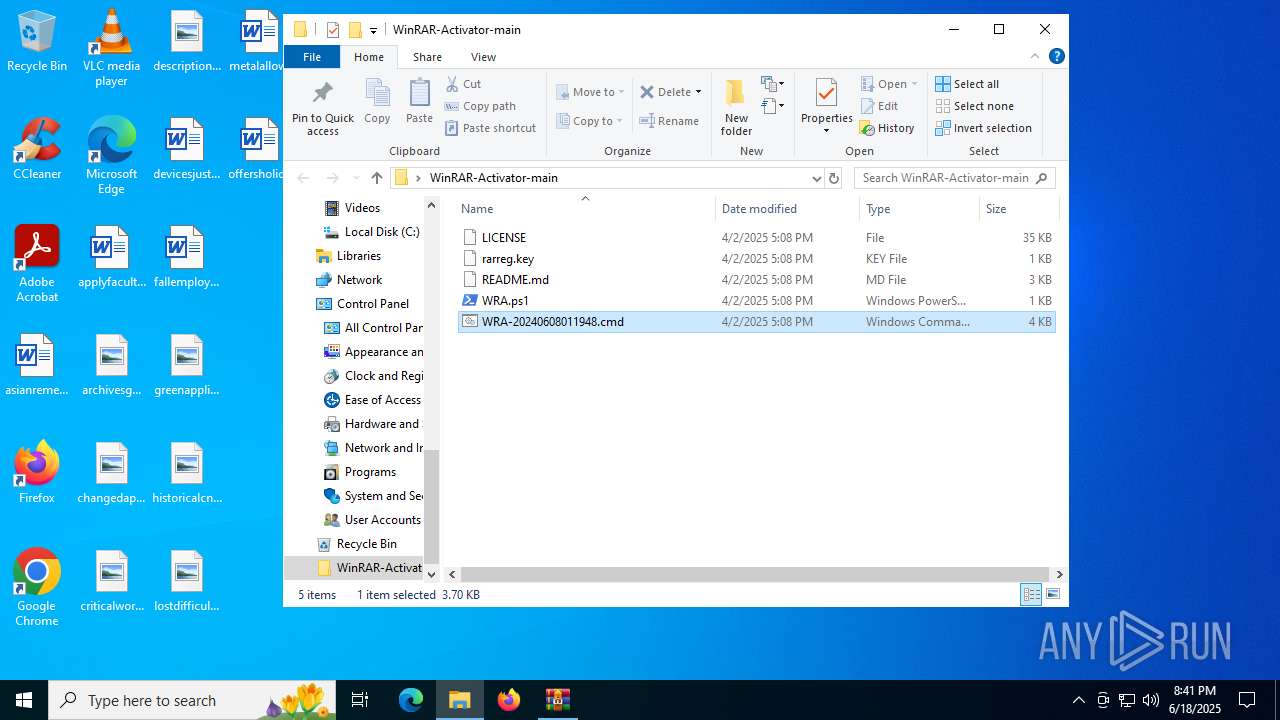
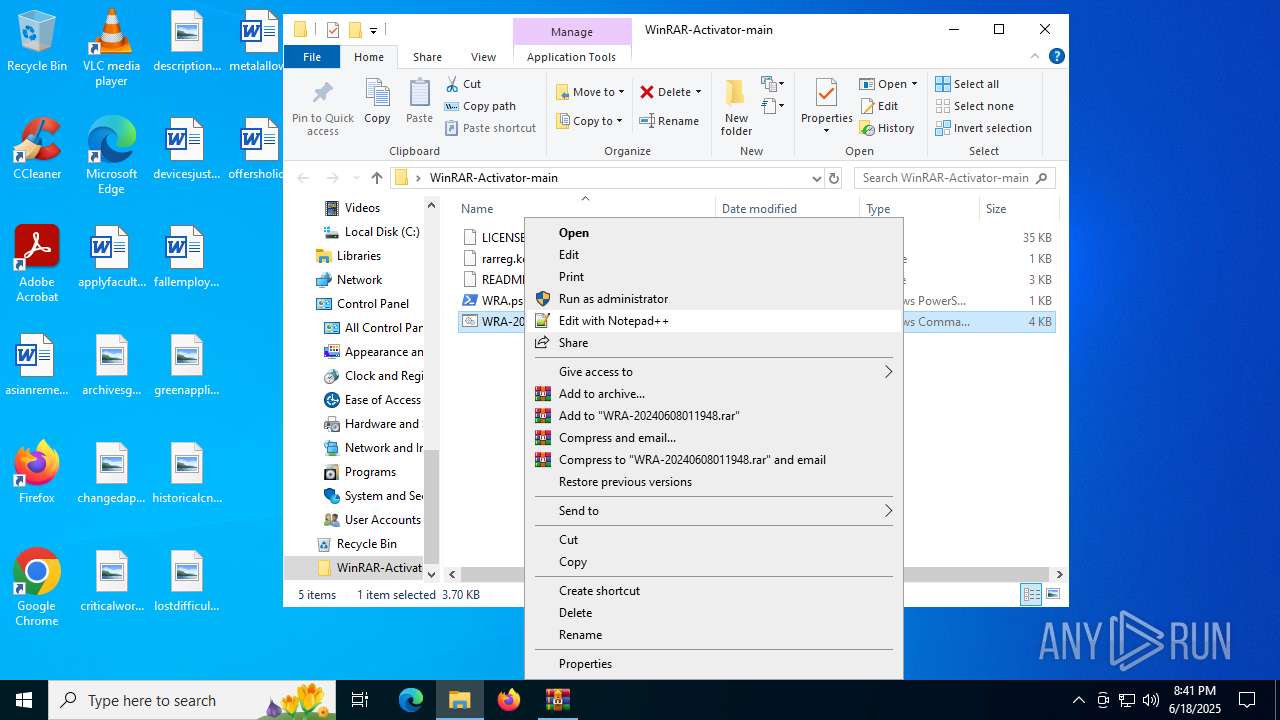
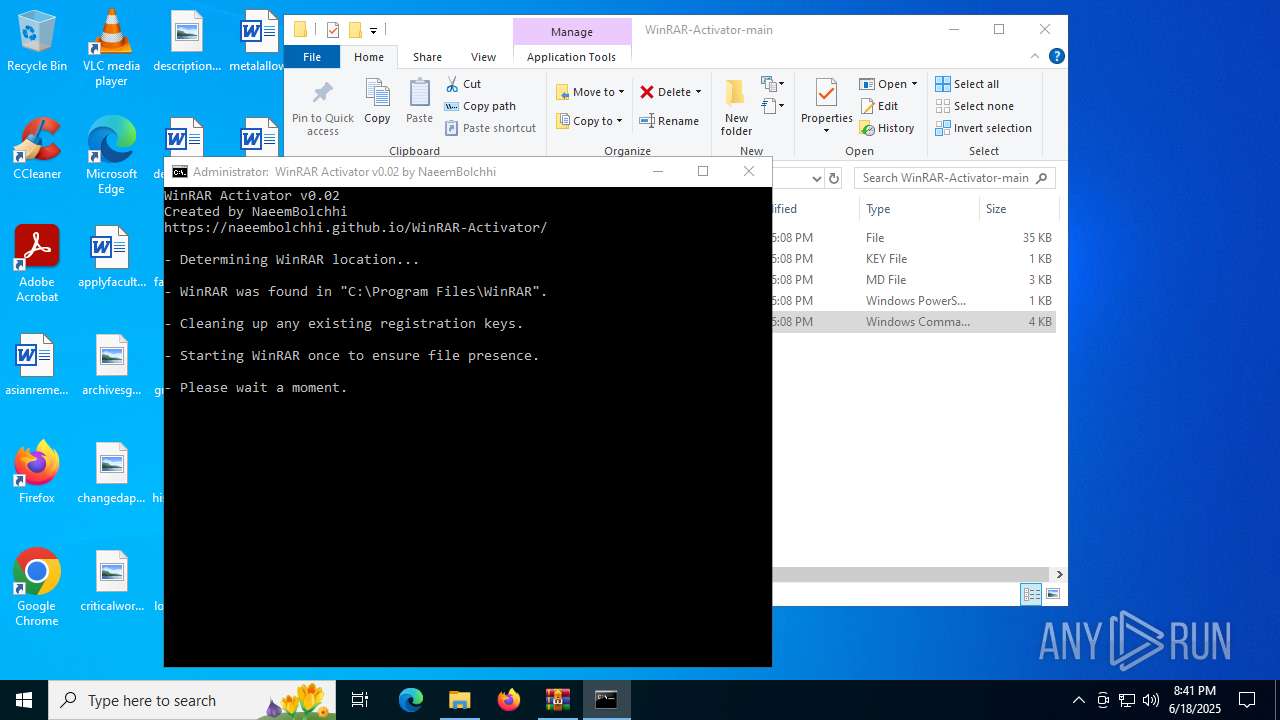
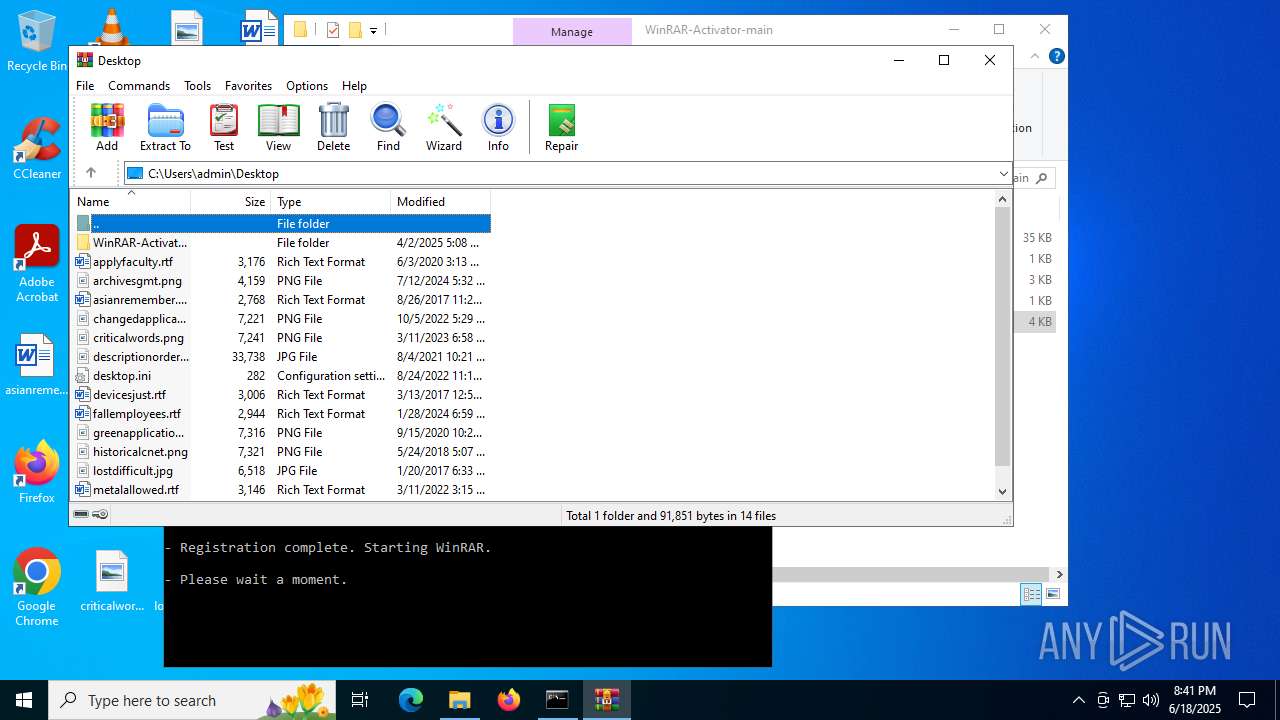
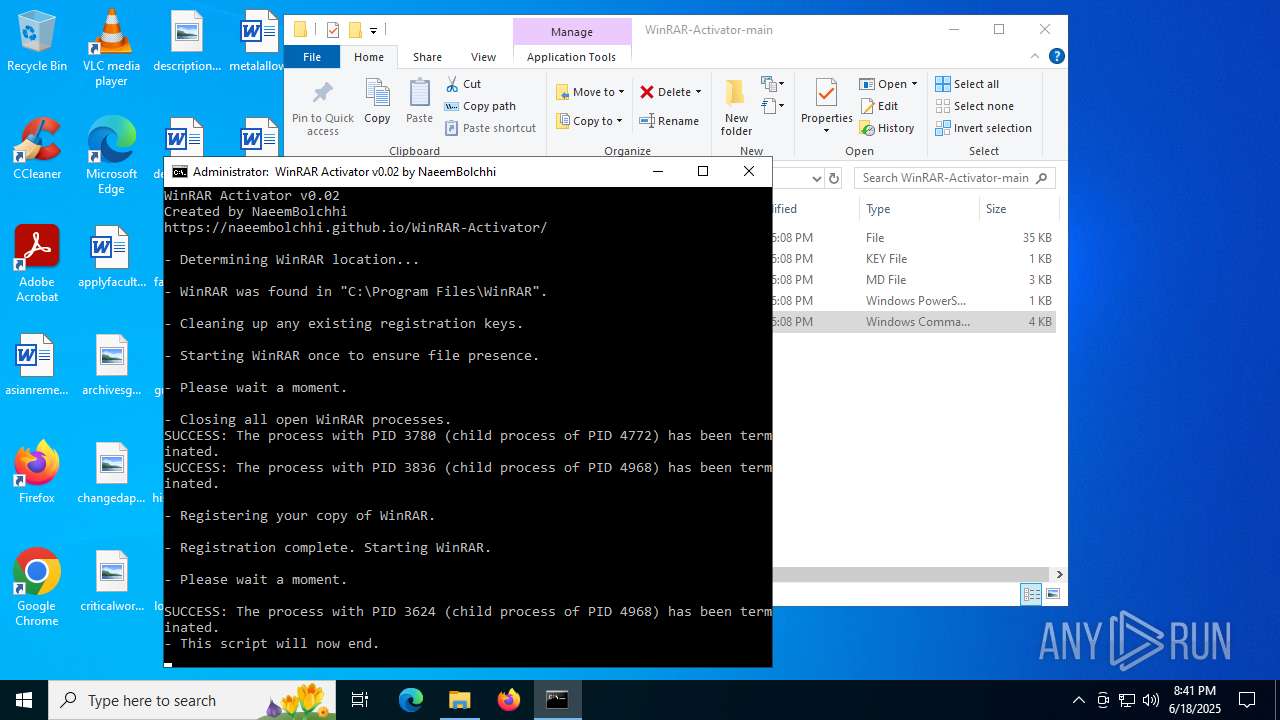
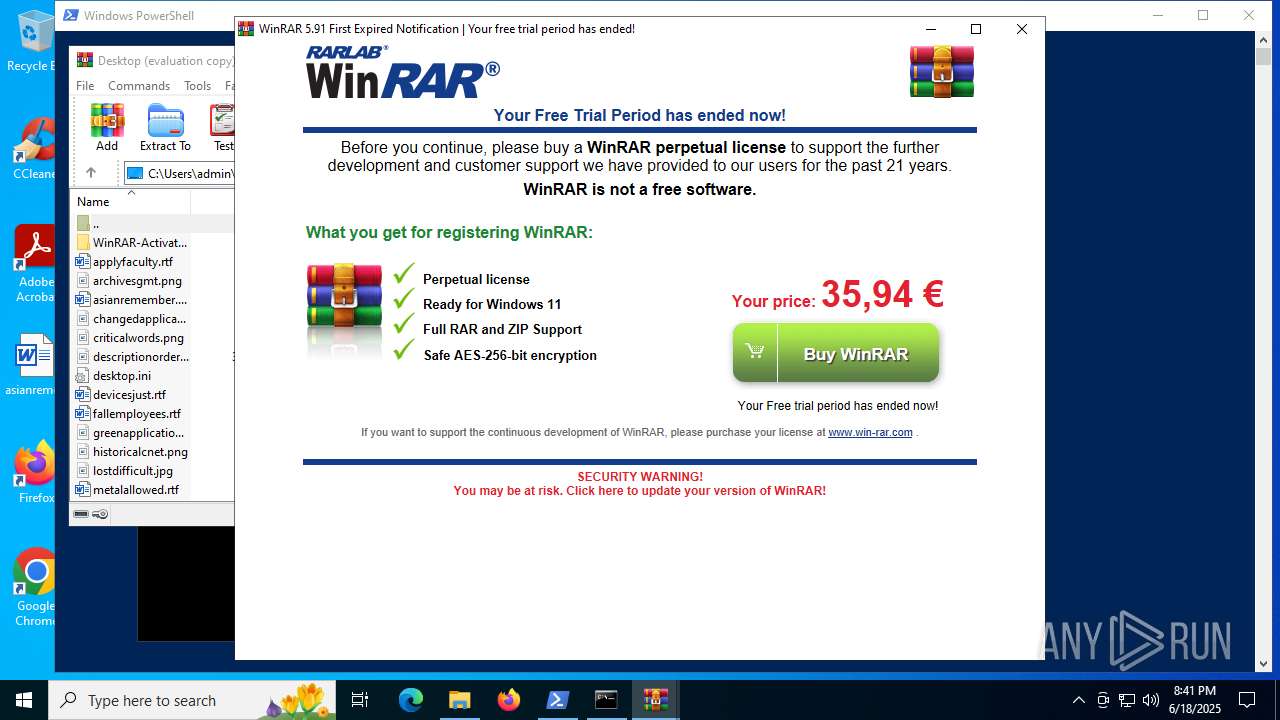
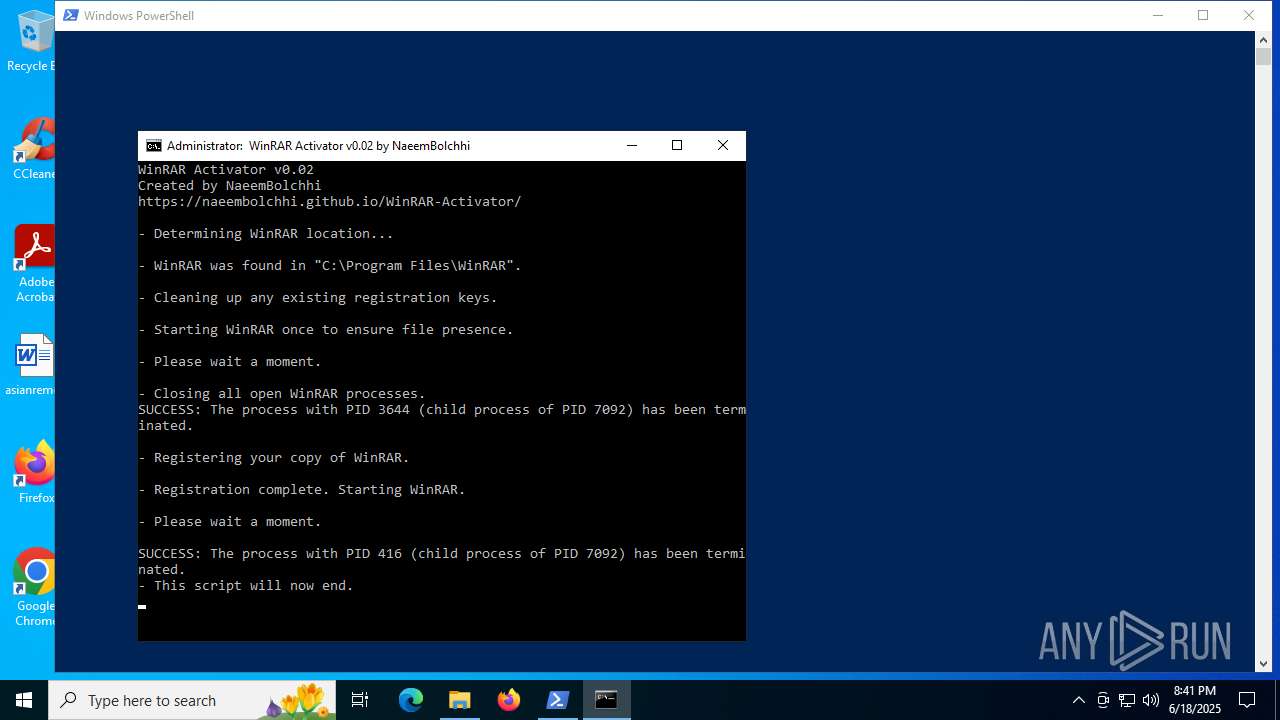
| File name: | WinRAR-Activator-main.zip |
| Full analysis: | https://app.any.run/tasks/a3114bf1-35bc-49f8-bd9d-c1f50cfacf32 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2025, 20:40:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 05D031AE577D8E4D707E90E7FC388AC6 |
| SHA1: | 33B1FA0975619A8626AF5D99CBDDE9F01169FDFE |
| SHA256: | 4F041E2AE9FC60A28CA8A3887A182000C9F671900351DED9818EE85C7D8B8041 |
| SSDEEP: | 384:WvaUISEGbW2QqA/N92gHkZIWUZtbFXbC87ArkmzvMSM:8ISEGM/zEZIWUZtbFXbpo1z6 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3780)
Bypass execution policy to execute commands
- powershell.exe (PID: 1688)
SUSPICIOUS
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 3836)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4968)
- cmd.exe (PID: 7092)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3836)
- WinRAR.exe (PID: 3644)
Reads Internet Explorer settings
- WinRAR.exe (PID: 3836)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4968)
- cmd.exe (PID: 7092)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1688)
Executing commands from ".cmd" file
- powershell.exe (PID: 1688)
- wscript.exe (PID: 6344)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1688)
- wscript.exe (PID: 6344)
The process executes VB scripts
- cmd.exe (PID: 3048)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6344)
INFO
Manual execution by a user
- cmd.exe (PID: 4968)
- powershell.exe (PID: 1688)
Starts MODE.COM to configure console settings
- mode.com (PID: 6180)
- mode.com (PID: 5908)
Checks supported languages
- mode.com (PID: 6180)
- mode.com (PID: 5908)
Reads the software policy settings
- WinRAR.exe (PID: 3836)
Checks proxy server information
- WinRAR.exe (PID: 3836)
- powershell.exe (PID: 1688)
- WinRAR.exe (PID: 3644)
Creates files in the program directory
- cmd.exe (PID: 4968)
- cmd.exe (PID: 7092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:02 10:08:36 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | WinRAR-Activator-main/ |
Total processes
168
Monitored processes
34
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Program Files\WinRAR\WinRAR.exe" | C:\Program Files\WinRAR\WinRAR.exe | — | cmd.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
| 1100 | NET FILE | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\WinRAR-Activator-main\WRA.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2032 | C:\WINDOWS\system32\net1 FILE | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | taskkill /f /im WinRAR.exe /t | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2292 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2388 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2808 | taskkill /f /im WinRAR.exe /t | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 450
Read events
17 429
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WinRAR-Activator-main.zip | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Misc |
| Operation: | write | Name: | RemShown |
Value: 1 | |||
Executable files
0
Suspicious files
5
Text files
23
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3780.7471\WinRAR-Activator-main\WRA.ps1 | text | |
MD5:0FEDCC2251EE025DD89566E0F9E35542 | SHA256:570C19342B79E3808F587B2D68759314E44E08617549C05E5AFB4292B757642F | |||
| 3780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3780.7471\WinRAR-Activator-main\WRA-20240608011948.cmd | text | |
MD5:9DB87924850D471E71D588DCAFE89642 | SHA256:888EF31D2130D5A8FE0FCD1894CB2DB0FDB333591E185B7ED690EFF16BDAD877 | |||
| 3836 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\4TDOFY41.htm | html | |
MD5:13CADD593C0A0718E5A1874823C5CF95 | SHA256:ABB152D2172487AB1066E8BE77BDE31C1CAFDBAEECBB13F65B9D076B9A37E57B | |||
| 3780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3780.7471\WinRAR-Activator-main\LICENSE | text | |
MD5:1EBBD3E34237AF26DA5DC08A4E440464 | SHA256:3972DC9744F6499F0F9B2DBF76696F2AE7AD8AF9B23DDE66D6AF86C9DFB36986 | |||
| 3836 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\logo-winrar-rarlab[1].gif | image | |
MD5:5F412DFD080BCFB0AE5D9E96BD0B4B2B | SHA256:C36DDB37D737E658C4CCC010AF640A14FA69DEBAD4FF85CCF0606A96BABDF931 | |||
| 3836 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\oldprice-cut[1].png | image | |
MD5:ECBDC0ABE14373C21A08B03086C3EABF | SHA256:17AAAF144BFD72B717C202A363AC12F3F2E602EDC7792120486EBDCDE8C1B287 | |||
| 3836 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\wr_64_53[1].png | image | |
MD5:B1A08980E8F6C5F0CB4F2112CCC51AEF | SHA256:0C8D0A2FDC0E451492541A1E746A447E9B0D882A901EF361D20DF0E298C24817 | |||
| 3836 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\button_buy_blank[1].png | image | |
MD5:5653146F28B4A490577AFCDE13EC4F2B | SHA256:2B150D073799B07AA68360FCF1FFA56A2B85F99EECA144BD876511AF8D79F9D9 | |||
| 4968 | cmd.exe | C:\Program Files\WinRAR\rarreg.key | text | |
MD5:7C3704DD59E1C9F8D1F5FDA816929D56 | SHA256:A4A71767C95F963CEB2C0F89960E2D2F8310109C3225AE71472E706AE9FC74E4 | |||
| 3836 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\checkmark-green-alpha[1].png | image | |
MD5:0E1BE01E16CC19A54CAD840E7B12C093 | SHA256:CD3DF66F0E89C359838AC3DD91D9286366E4027C39C7DA285CCBE3D2694EACF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3836 | WinRAR.exe | GET | 200 | 104.18.20.213:80 | http://e6.c.lencr.org/26.crl | unknown | — | — | whitelisted |
4816 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1652 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4816 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4864 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3836 | WinRAR.exe | 51.195.68.173:443 | notifier.win-rar.com | OVH SAS | FR | malicious |
3836 | WinRAR.exe | 104.18.20.213:80 | e6.c.lencr.org | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
notifier.win-rar.com |
| malicious |
e6.c.lencr.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
naeembolchhi.github.io |
| unknown |
login.live.com |
| whitelisted |