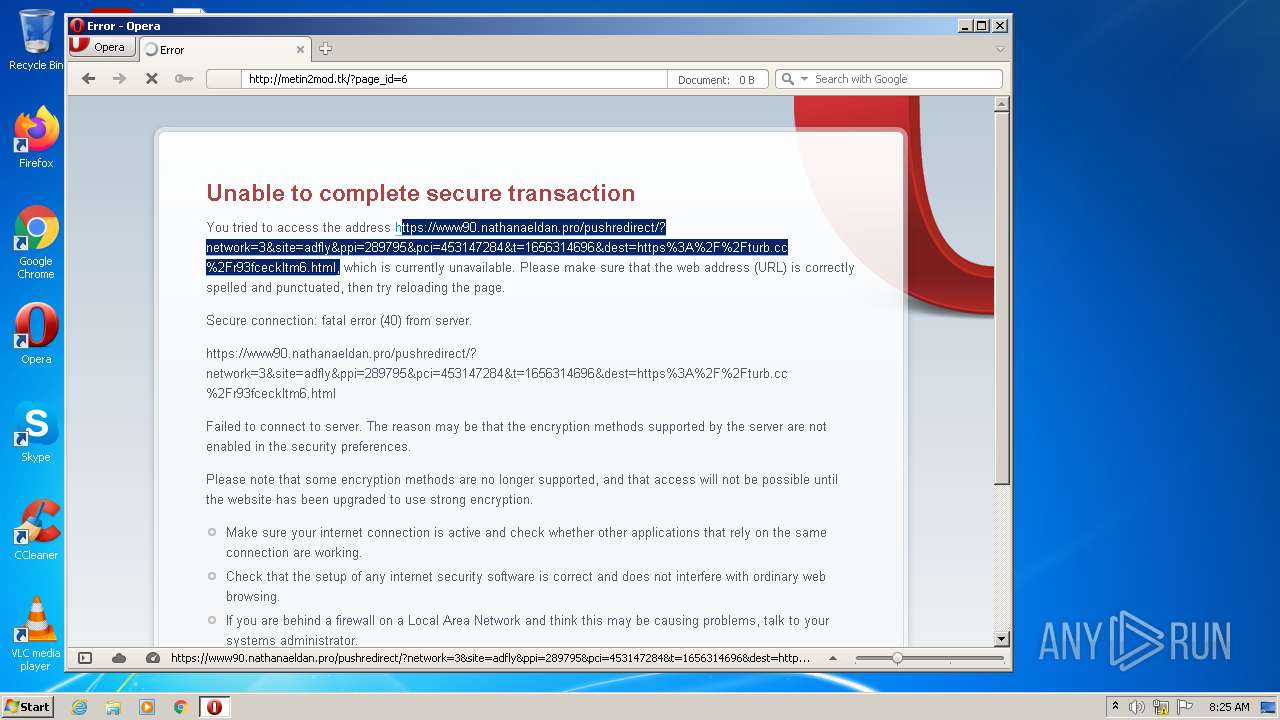
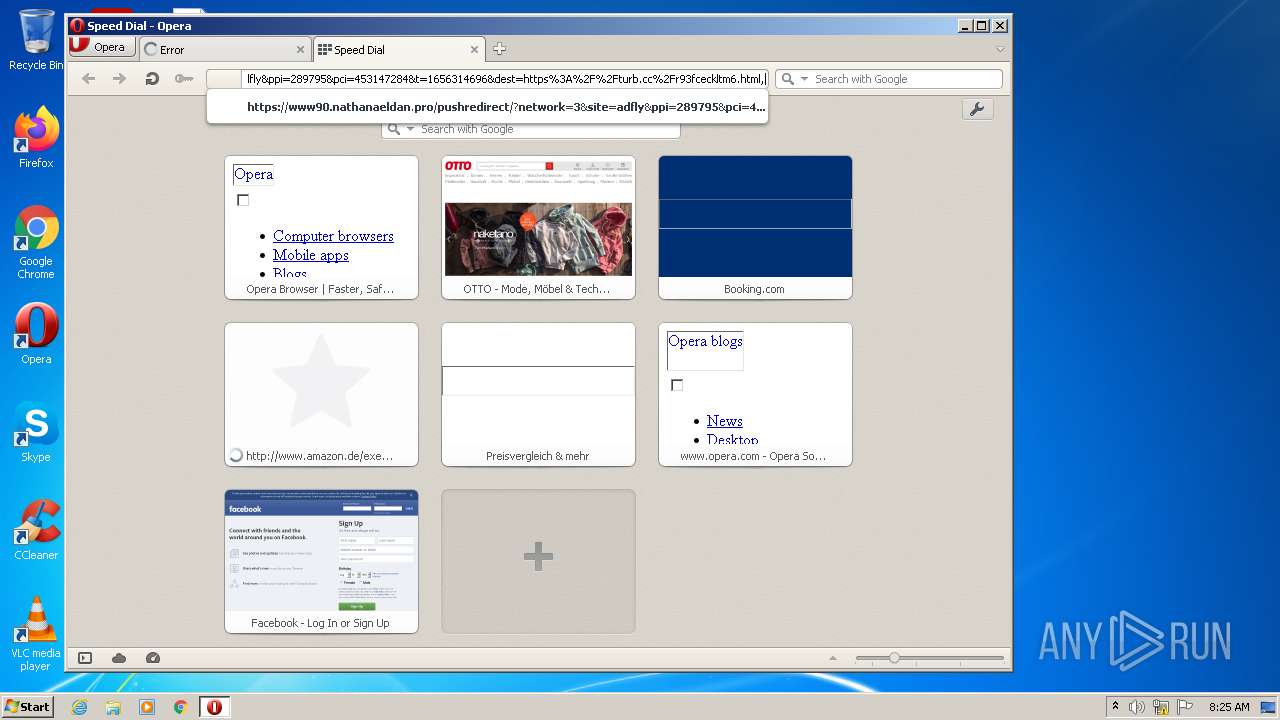
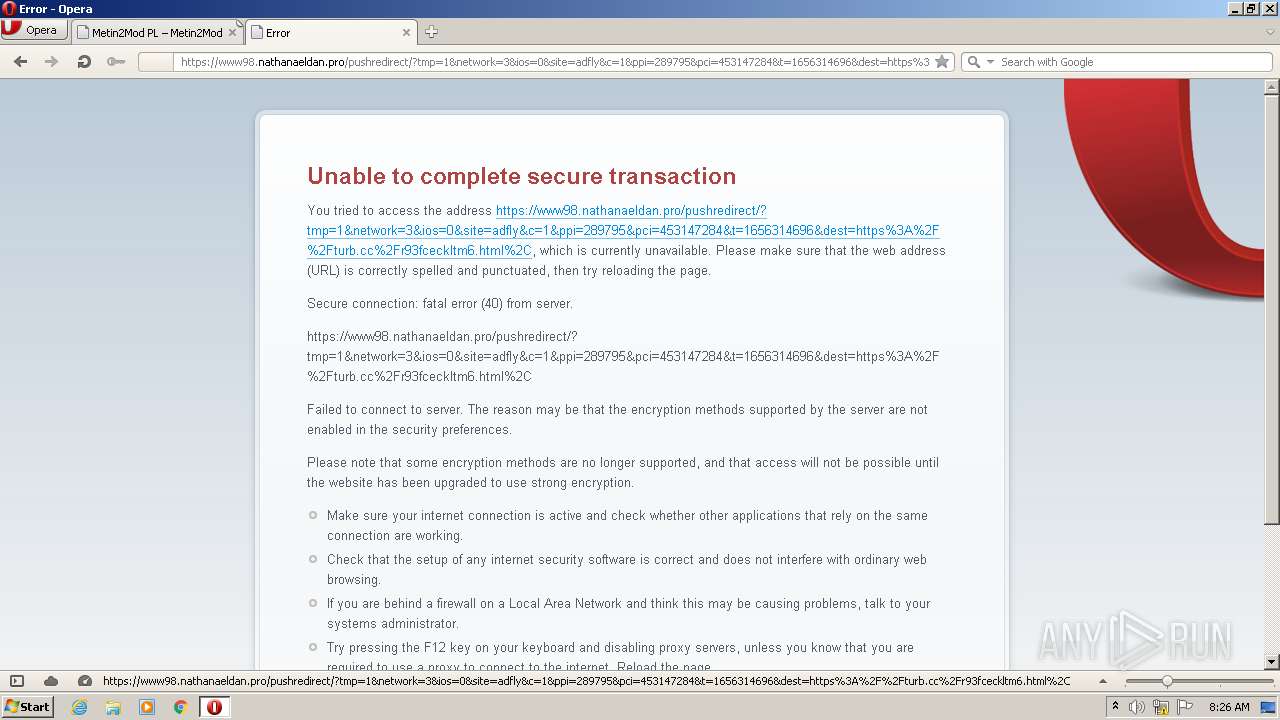
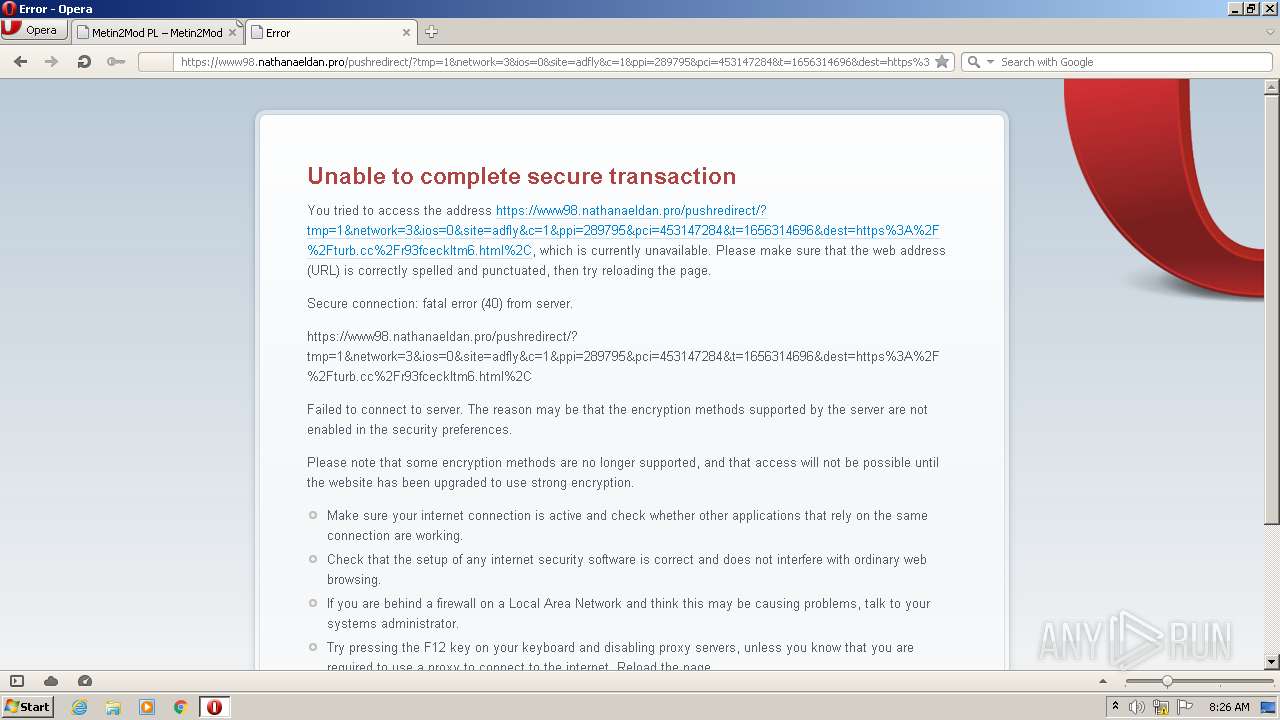
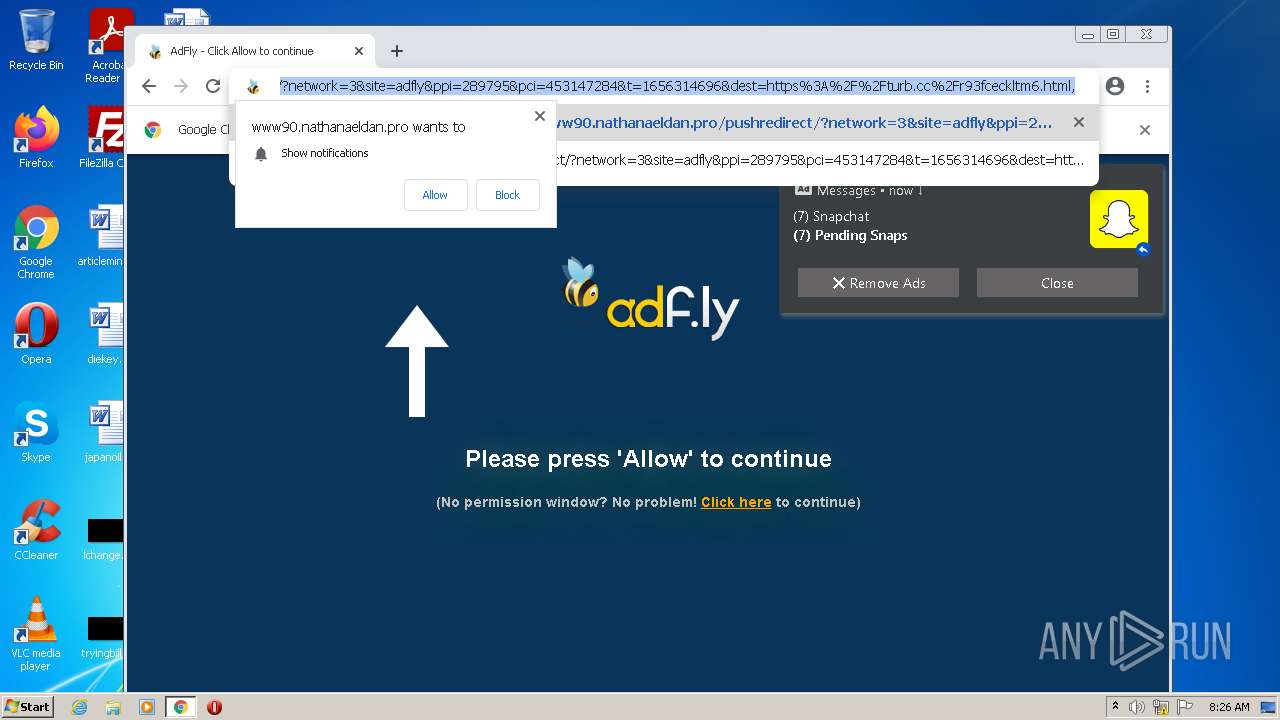
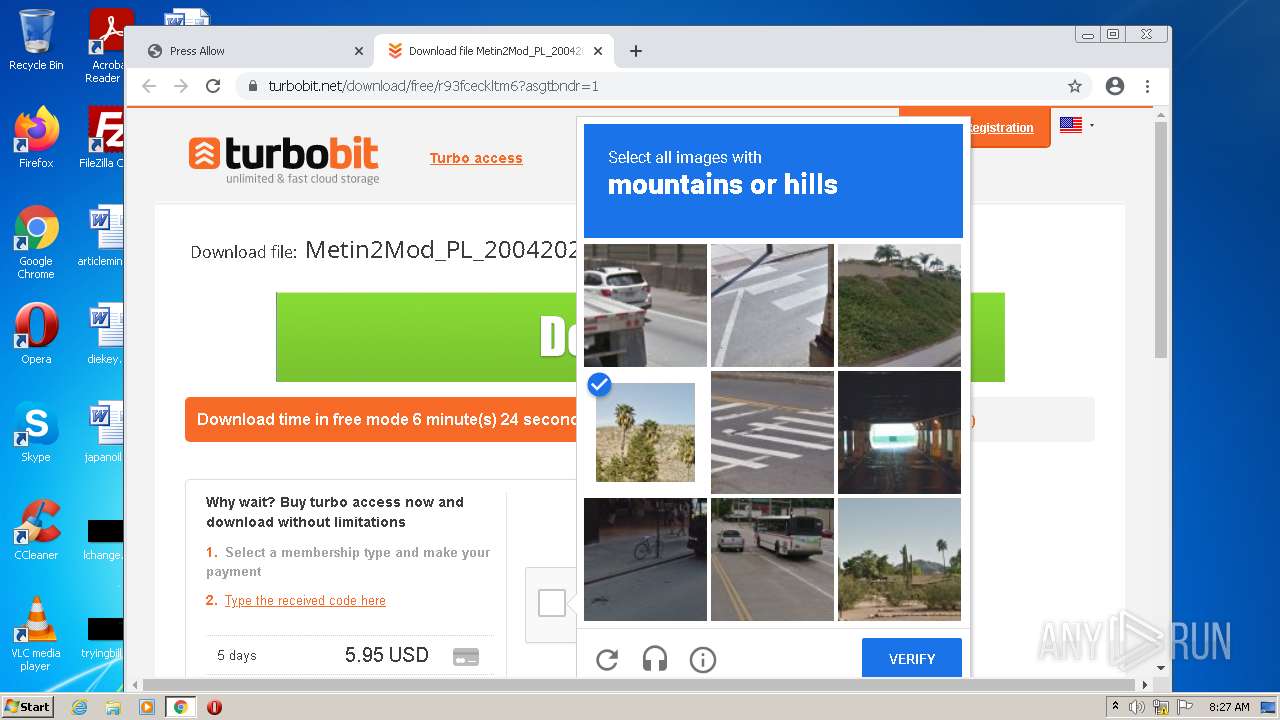
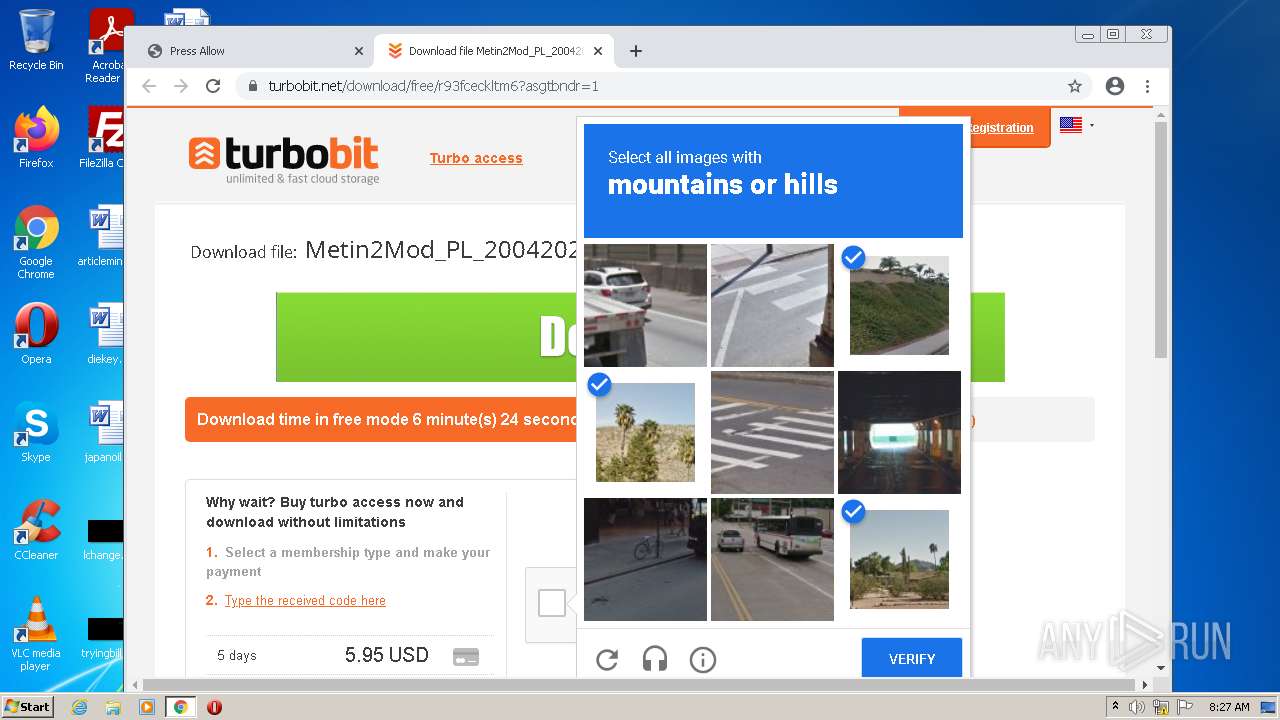
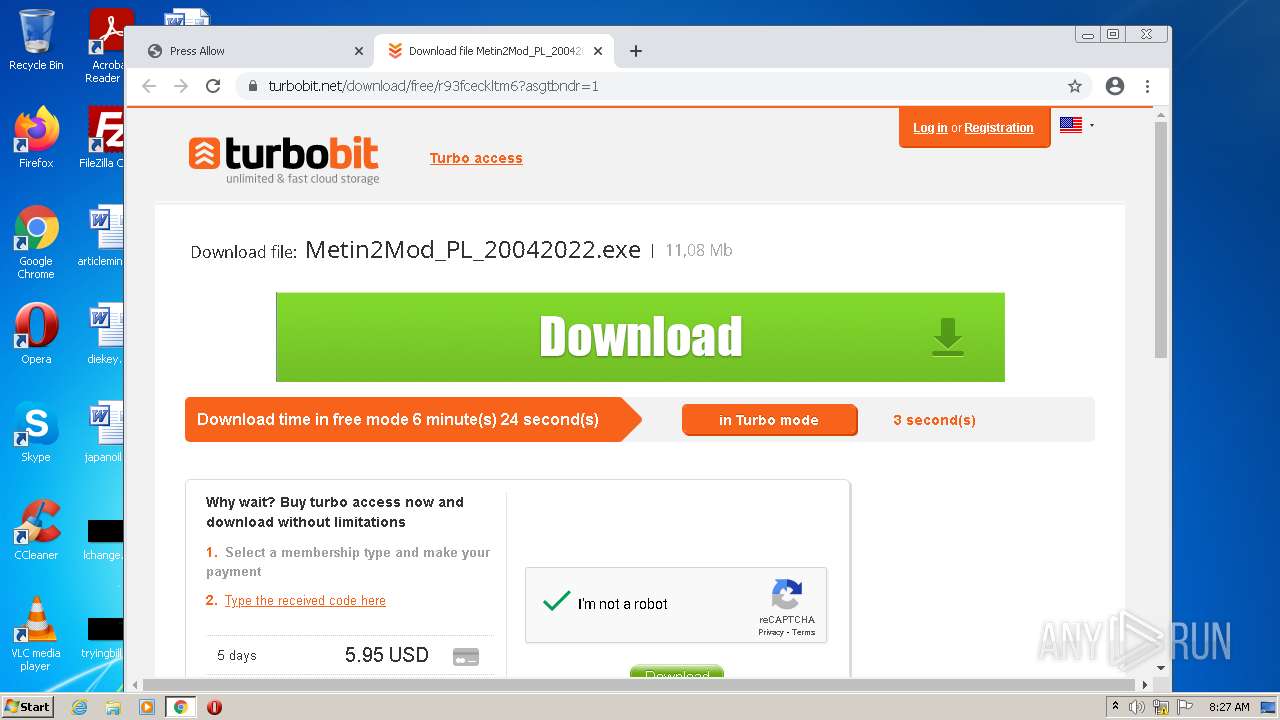
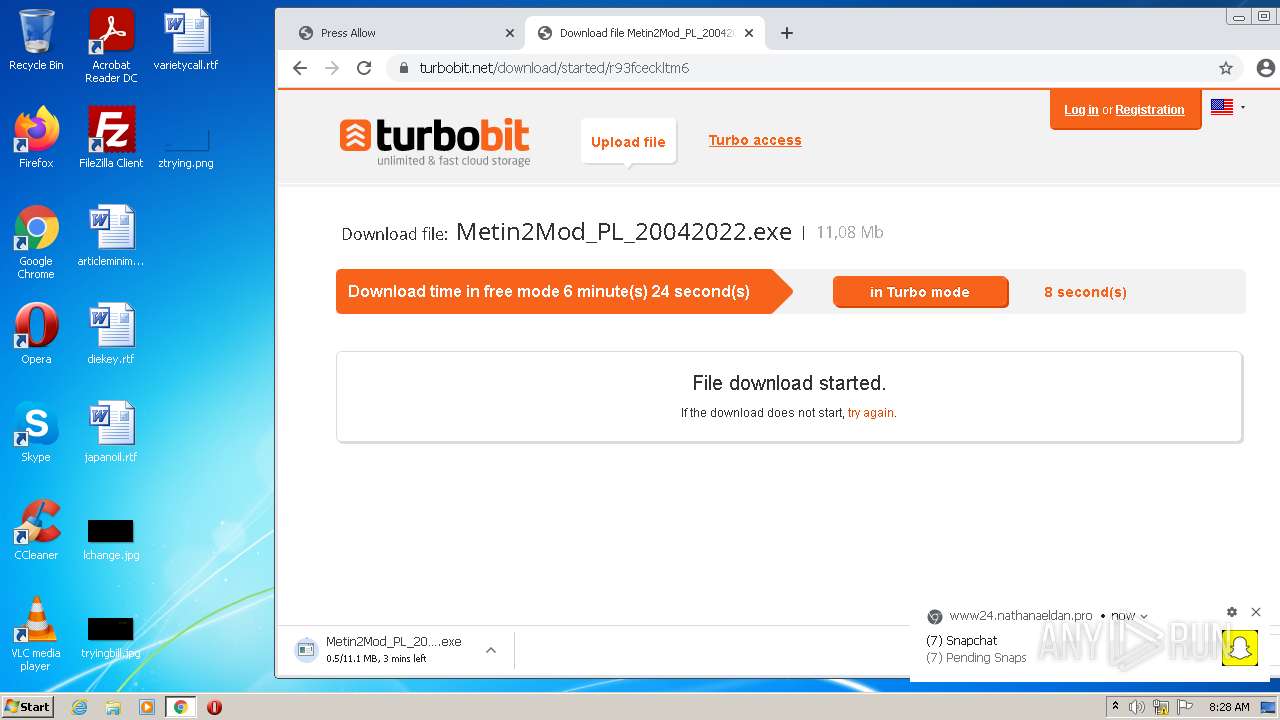
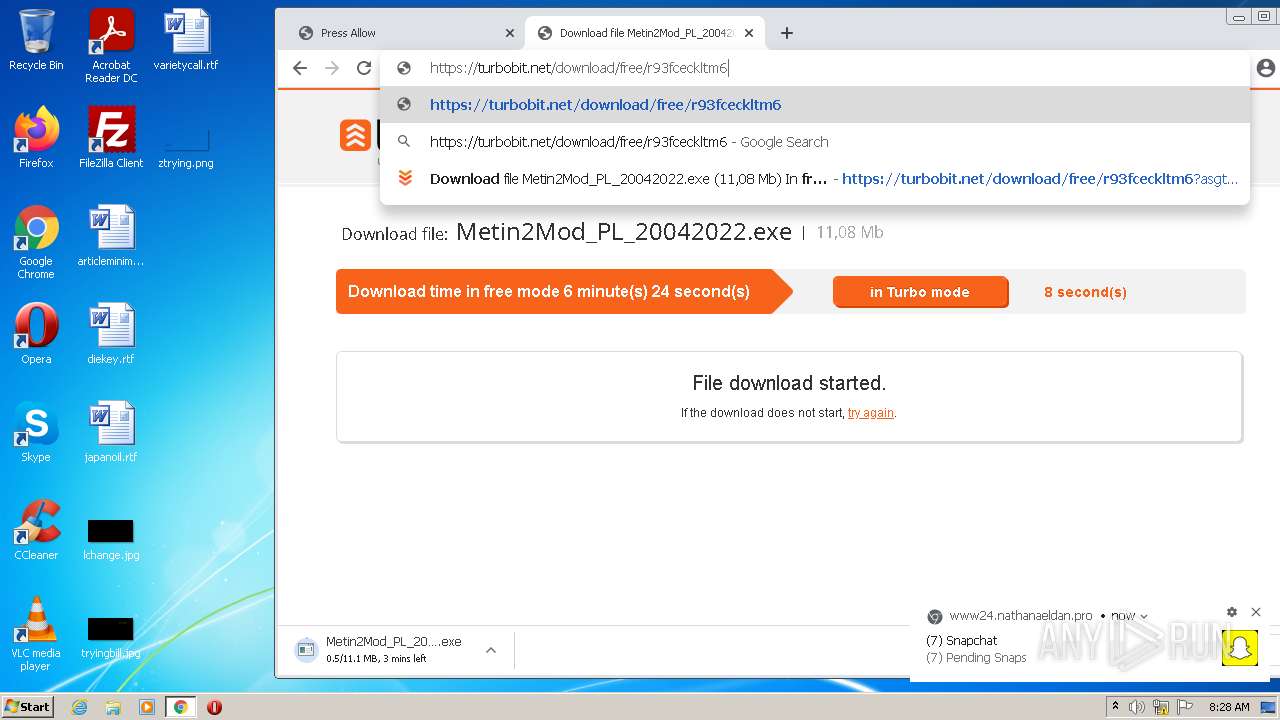
| URL: | http://metin2mod.tk/?page_id=6 |
| Full analysis: | https://app.any.run/tasks/0d606fa9-0ad6-4e94-b3ee-0b75d72c2ce6 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 07:24:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 281B247C14B7EA1D5C2FD4CC75A73D1A |
| SHA1: | 6B528C29F1FF990A18D98D466205763BC67FAD06 |
| SHA256: | 4F00D44A2BB433653E6A67B77CF5A49FA15BFFC71ABE0CF44AEB4D3D042ECA53 |
| SSDEEP: | 3:N1KT1Lt6MB+:CZLtnB+ |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 2812)
- chrome.exe (PID: 2896)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 912)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2812)
Drops a file with a compile date too recent
- chrome.exe (PID: 2812)
- chrome.exe (PID: 2896)
Executable content was dropped or overwritten
- chrome.exe (PID: 2812)
- chrome.exe (PID: 2896)
INFO
Reads the computer name
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 912)
- opera.exe (PID: 2608)
- chrome.exe (PID: 2812)
- chrome.exe (PID: 3648)
- chrome.exe (PID: 3256)
- chrome.exe (PID: 1280)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 3864)
- chrome.exe (PID: 3344)
- chrome.exe (PID: 3968)
Checks supported languages
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 912)
- opera.exe (PID: 2608)
- chrome.exe (PID: 2812)
- chrome.exe (PID: 3072)
- chrome.exe (PID: 3648)
- chrome.exe (PID: 3256)
- chrome.exe (PID: 3940)
- chrome.exe (PID: 3520)
- chrome.exe (PID: 1872)
- chrome.exe (PID: 3980)
- chrome.exe (PID: 740)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 1280)
- chrome.exe (PID: 3148)
- chrome.exe (PID: 708)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 3000)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 980)
- chrome.exe (PID: 2172)
- chrome.exe (PID: 3200)
- chrome.exe (PID: 2944)
- chrome.exe (PID: 3796)
- chrome.exe (PID: 3392)
- chrome.exe (PID: 2364)
- chrome.exe (PID: 2924)
- chrome.exe (PID: 3932)
- chrome.exe (PID: 3480)
- chrome.exe (PID: 3796)
- chrome.exe (PID: 780)
- chrome.exe (PID: 540)
- chrome.exe (PID: 1080)
- chrome.exe (PID: 2244)
- chrome.exe (PID: 2040)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 3788)
- chrome.exe (PID: 3344)
- chrome.exe (PID: 3576)
- chrome.exe (PID: 1736)
- chrome.exe (PID: 3864)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 3988)
- chrome.exe (PID: 2316)
- chrome.exe (PID: 3736)
- chrome.exe (PID: 1648)
- chrome.exe (PID: 528)
- chrome.exe (PID: 564)
- chrome.exe (PID: 3232)
- chrome.exe (PID: 3696)
- chrome.exe (PID: 3344)
- chrome.exe (PID: 3852)
- chrome.exe (PID: 2596)
- chrome.exe (PID: 1588)
- chrome.exe (PID: 2060)
- chrome.exe (PID: 2800)
- chrome.exe (PID: 1032)
- chrome.exe (PID: 3968)
- chrome.exe (PID: 2112)
- chrome.exe (PID: 1792)
- chrome.exe (PID: 2896)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 1776)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 600)
- chrome.exe (PID: 2392)
Reads the date of Windows installation
- iexplore.exe (PID: 2684)
- opera.exe (PID: 2608)
- chrome.exe (PID: 3864)
Check for Java to be installed
- opera.exe (PID: 2608)
Changes internet zones settings
- iexplore.exe (PID: 2684)
Checks Windows Trust Settings
- iexplore.exe (PID: 2684)
Reads settings of System Certificates
- iexplore.exe (PID: 2684)
- chrome.exe (PID: 3256)
Application launched itself
- iexplore.exe (PID: 2684)
- chrome.exe (PID: 2812)
Manual execution by user
- chrome.exe (PID: 2812)
- opera.exe (PID: 2608)
Creates files in the user directory
- opera.exe (PID: 2608)
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 2608)
Reads the hosts file
- chrome.exe (PID: 2812)
- chrome.exe (PID: 3256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
105
Monitored processes
68
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=44 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2432 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2804 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=45 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1208 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4328 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3592 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 740 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2840 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2044 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2684 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3788 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,14096856180708568554,14834952099704867000,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1752 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
26 777
Read events
26 420
Write events
348
Delete events
9
Modification events
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30968310 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 52735444 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30968311 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
390
Text files
355
Unknown types
72
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2EE60D49-F5EA-11EC-B7B7-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFEDFE31ACD3474E66.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{35A69628-F5EA-11EC-B7B7-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF8CAE6D3B298883DF.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF5FA1099D1D4B8A8F.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2608 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprC64F.tmp | text | |
MD5:— | SHA256:— | |||
| 2608 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprC6AE.tmp | xml | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2608 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
192
TCP/UDP connections
319
DNS requests
153
Threats
106
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/images/pattern.svg | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/style.css?ver=5.1.13 | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-includes/css/dist/block-library/style.min.css?ver=5.1.13 | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-content/plugins/popups/public/assets/css/public.css?ver=1.9.3.8 | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/js/hide-search.js?ver=20120206 | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/js/navigation.js?ver=20120206 | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-includes/js/jquery/jquery-migrate.min.js?ver=1.4.1 | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/js/superfish.min.js?ver=20140328 | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/images/new2.gif | FR | — | — | suspicious |
2608 | opera.exe | GET | — | 46.105.98.67:80 | http://metin2mod.tk/wp-includes/js/jquery/jquery.js?ver=1.12.4 | FR | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2684 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
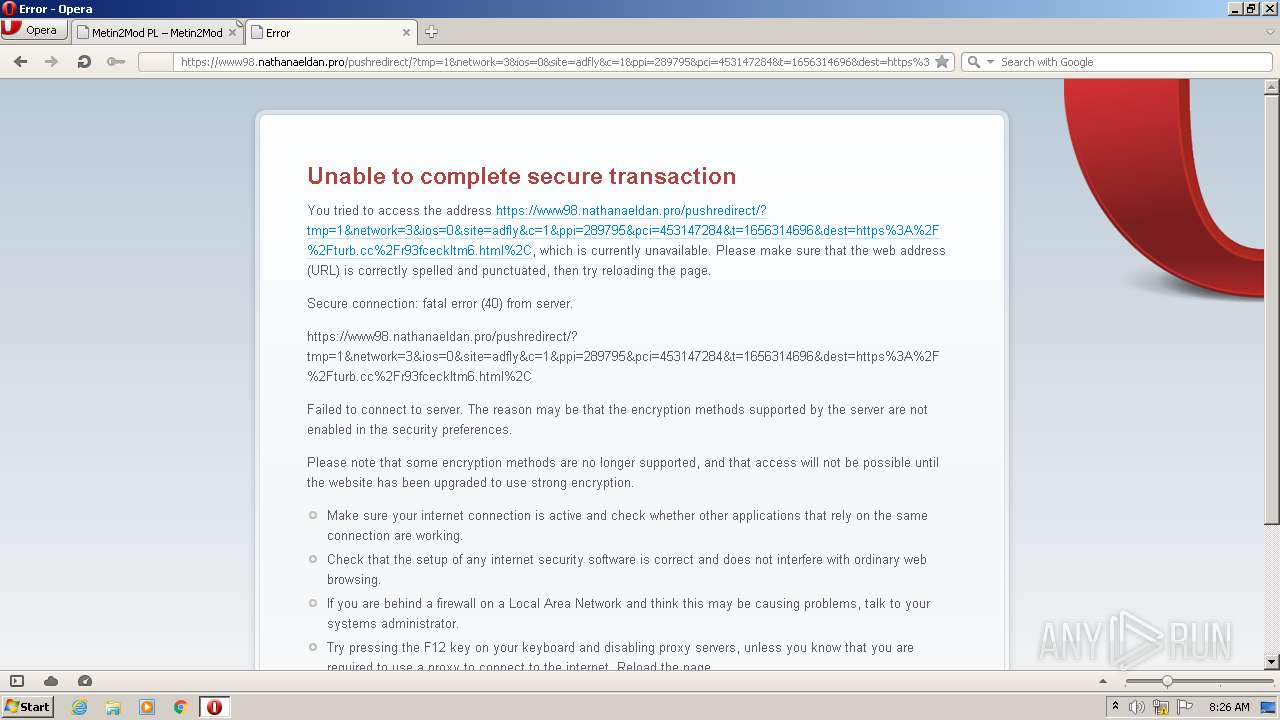
912 | iexplore.exe | 46.105.98.67:80 | metin2mod.tk | OVH SAS | FR | suspicious |
2684 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2684 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2608 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2608 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2608 | opera.exe | 104.20.66.244:443 | cdn.adf.ly | Cloudflare Inc | US | unknown |
2608 | opera.exe | 142.250.186.67:80 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2608 | opera.exe | 142.250.185.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2608 | opera.exe | 104.20.66.244:80 | cdn.adf.ly | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
metin2mod.tk |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
2608 | opera.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |