| File name: | .exe |
| Full analysis: | https://app.any.run/tasks/f8279e36-b6ba-4ee4-821b-a04a0b42313c |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 17:54:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 5 sections |
| MD5: | 75D522502AFC10FBF04860F6BB314E24 |
| SHA1: | 25C3A34CA06CB430DD128C95A26DF3354D86BE7F |
| SHA256: | 4EFAA22F692B30BC8341D1FA8698B84524E2D5468E386B7B56589DAF097E26E6 |
| SSDEEP: | 24576:hilba9iNrXBsJY/Ega/qke/5ji+VXsYDOvDHrxmCB6lLW25D+SXCK:hilba9iNrXBsJY/Ega/qkw5ji+VXsYDh |
MALICIOUS
Application was injected by another process
- svchost.exe (PID: 4204)
- sihost.exe (PID: 4180)
- svchost.exe (PID: 4248)
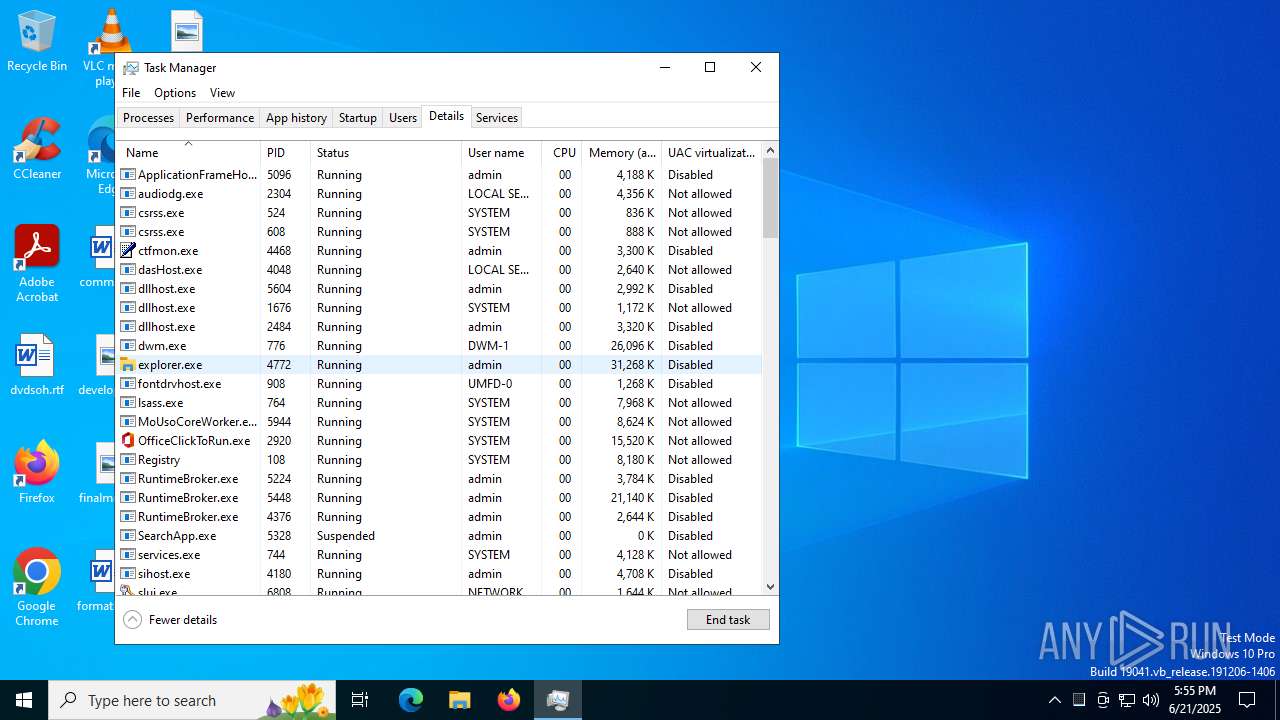
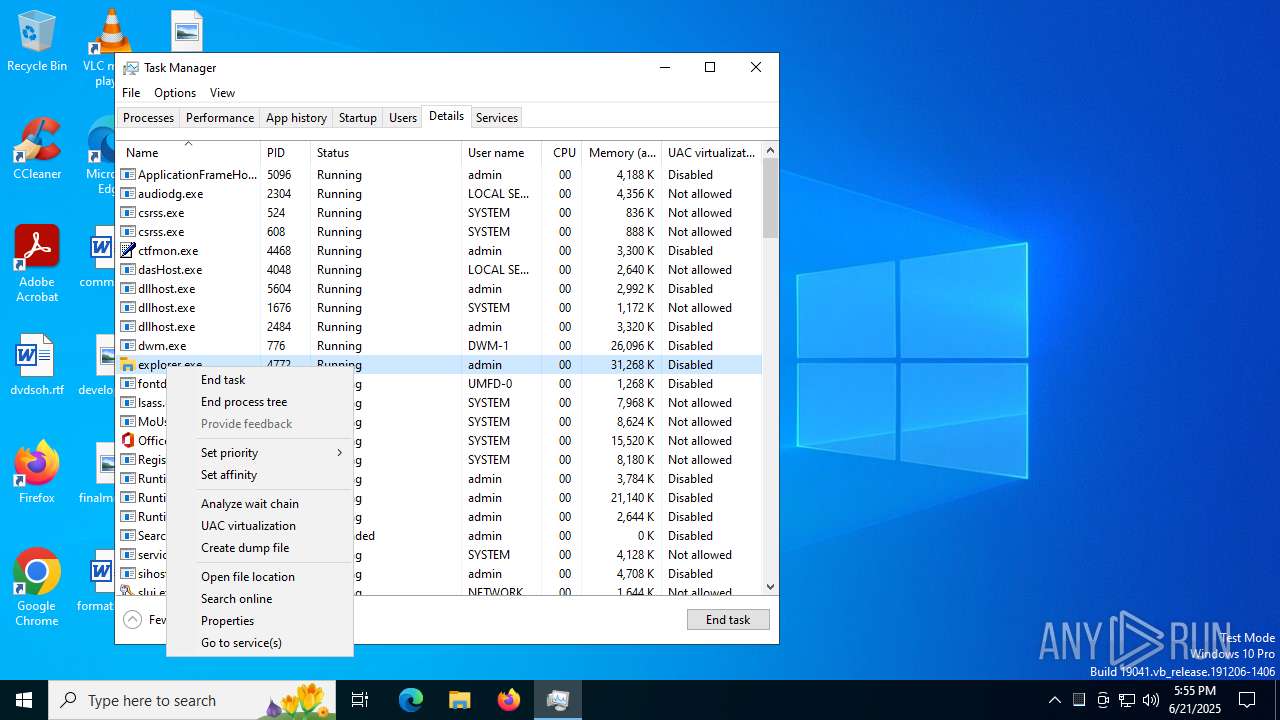
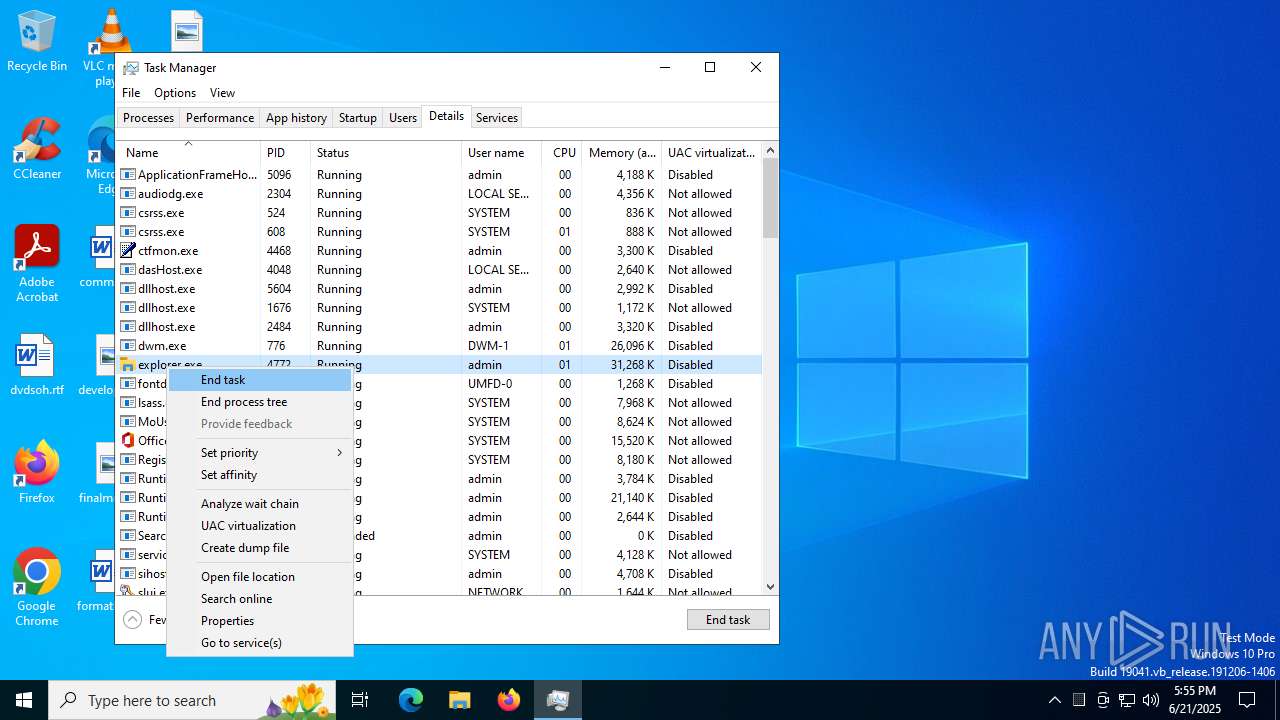
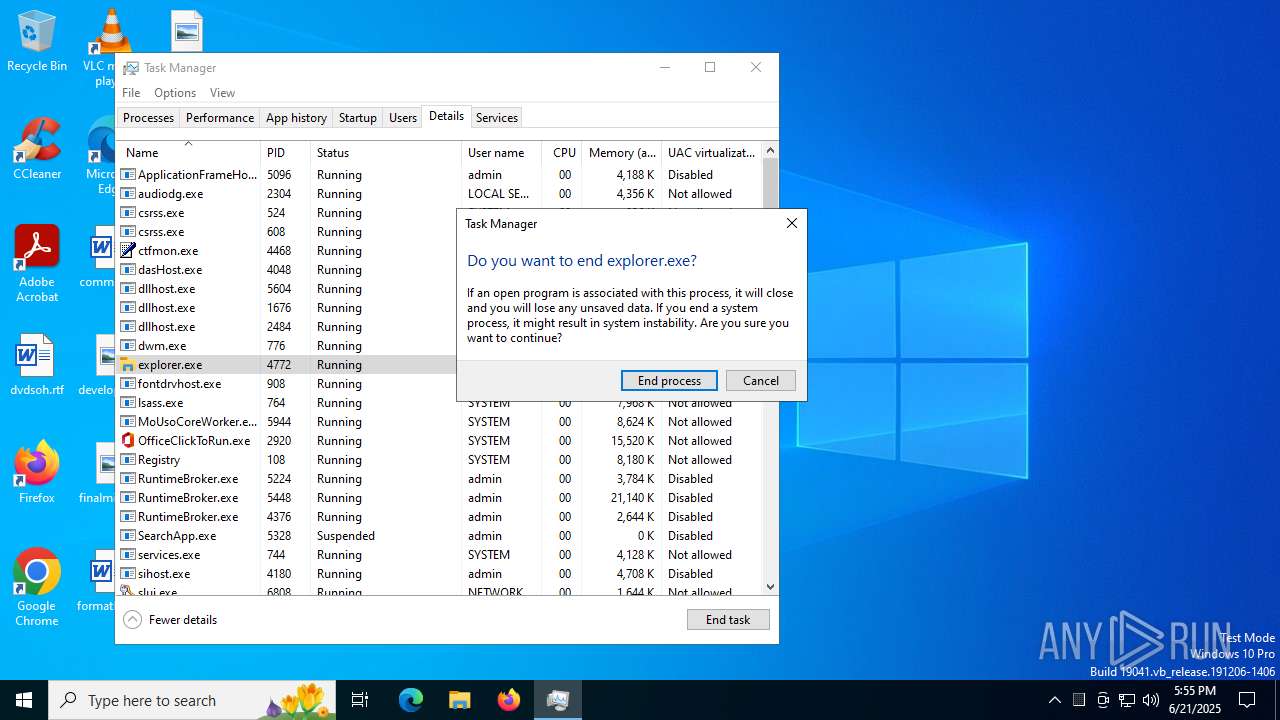
- explorer.exe (PID: 4772)
- svchost.exe (PID: 5048)
- StartMenuExperienceHost.exe (PID: 5160)
- RuntimeBroker.exe (PID: 5224)
- SearchApp.exe (PID: 5328)
- RuntimeBroker.exe (PID: 5448)
- TextInputHost.exe (PID: 2772)
- dllhost.exe (PID: 2484)
- default-browser-agent.exe (PID: 3148)
- RuntimeBroker.exe (PID: 7092)
- RuntimeBroker.exe (PID: 4376)
- dllhost.exe (PID: 5604)
- ApplicationFrameHost.exe (PID: 5096)
- svchost.exe (PID: 6984)
- UserOOBEBroker.exe (PID: 5936)
- firefox.exe (PID: 1644)
- firefox.exe (PID: 6960)
- taskhostw.exe (PID: 4868)
Runs injected code in another process
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
Changes the autorun value in the registry
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
- explorer.exe (PID: 4772)
DIAMOTRIX has been detected (SURICATA)
- explorer.exe (PID: 4772)
SUSPICIOUS
Executable content was dropped or overwritten
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 7032)
- SearchApp.exe (PID: 5116)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 7032)
Connects to the server without a host name
- explorer.exe (PID: 4772)
Creates file in the systems drive root
- explorer.exe (PID: 3800)
Application launched itself
- explorer.exe (PID: 3800)
INFO
Reads security settings of Internet Explorer
- taskhostw.exe (PID: 4868)
- explorer.exe (PID: 1480)
- explorer.exe (PID: 4772)
- Taskmgr.exe (PID: 1472)
- explorer.exe (PID: 3800)
- RuntimeBroker.exe (PID: 5224)
Checks supported languages
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
- default-browser-agent.exe (PID: 3148)
- StartMenuExperienceHost.exe (PID: 7032)
- TextInputHost.exe (PID: 4676)
- SearchApp.exe (PID: 5116)
Reads the computer name
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
- StartMenuExperienceHost.exe (PID: 7032)
- TextInputHost.exe (PID: 4676)
- SearchApp.exe (PID: 5116)
Reads the machine GUID from the registry
- StartMenuExperienceHost.exe (PID: 5160)
- TextInputHost.exe (PID: 2772)
- default-browser-agent.exe (PID: 3148)
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
- SearchApp.exe (PID: 5116)
Launching a file from a Registry key
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
- explorer.exe (PID: 4772)
Creates files in the program directory
- f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe (PID: 1568)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 7032)
- SearchApp.exe (PID: 5116)
Checks proxy server information
- explorer.exe (PID: 4772)
- explorer.exe (PID: 1480)
- SearchApp.exe (PID: 5116)
Creates files or folders in the user directory
- dllhost.exe (PID: 5604)
- explorer.exe (PID: 1480)
Reads the software policy settings
- SearchApp.exe (PID: 5116)
Reads Environment values
- SearchApp.exe (PID: 5116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 17:56:39+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 55808 |
| InitializedDataSize: | 541184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e78 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
154
Monitored processes
35
Malicious processes
3
Suspicious processes
19
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1232 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {3eef301f-b596-4c0b-bd92-013beafce793} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1472 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Users\admin\AppData\Local\Temp\f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe" | C:\Users\admin\AppData\Local\Temp\f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1644 | "C:\Program Files\Mozilla Firefox\firefox.exe" --backgroundtask defaultagent do-task 308046B0AF4A39CB | C:\Program Files\Mozilla Firefox\firefox.exe | default-browser-agent.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 2220 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | C:\WINDOWS\system32\DllHost.exe /Processid:{973D20D7-562D-44B9-B70B-5A0F49CCDF3F} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2648 | C:\WINDOWS\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {9BA05972-F6A8-11CF-A442-00A0C90A8F39} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Exit code: 1 Version: 123.26505.0.0 Modules
| |||||||||||||||
| 2804 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
47 763
Read events
47 463
Write events
280
Delete events
20
Modification events
| (PID) Process: | (4868) taskhostw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\CloudStore\Store\DefaultAccount\Current\default$windows.data.apps.appleveltileinfo$appleveltilelist\windows.data.apps.appleveltileinfo$w~microsoft.skype.skypedesktop |
| Operation: | write | Name: | Data |
Value: 434201000A0201002A06FDE3DBC2062A000000 | |||
| (PID) Process: | (4868) taskhostw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\AppListBackup\ListOfTaskBackedUpTiles_2476798090 |
| Operation: | write | Name: | ListOfTaskBackedUpTiles_2476798090 |
Value: {"tileId":"W~Microsoft.Skype.SkypeDesktop", "appIconLightAssetId":"", "appIconDarkAssetId":"", "displayName":"", "sortName":"", "suiteName":"", "packageId":"", "action":"2", "shortcutArgs":"", "targetPath":""} | |||
| (PID) Process: | (1568) f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\bbeecafdaeec |
| Operation: | write | Name: | CurrentPath |
Value: C:\Users\admin\AppData\Local\Temp\f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe | |||
| (PID) Process: | (1568) f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | bbeecafdaeec |
Value: "C:\ProgramData\bbeecafdaeec.exe" | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | bbeecafdaeec |
Value: "C:\Users\admin\AppData\Local\Temp\f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe" | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\bbeecafdaeec |
| Operation: | write | Name: | CurrentPath |
Value: C:\Users\admin\AppData\Local\Temp\f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\StartupFolder |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | bbeecafdaeec |
Value: "C:\ProgramData\bbeecafdaeec.exe" | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
3
Suspicious files
53
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5116 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:F7A7609E5A256900E6818BA56E9FDED9 | SHA256:DB8BC6CE9907E6573E965D67D8FCB472119EE8B1E537DAB3787450C191ADA16F | |||
| 5116 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:93C2665E2C62E2143F4D5063836B688A | SHA256:2842068E32CE3298230718DD40915A3C5D8F24B97B2A0801B2B0FD4FDEF79244 | |||
| 6960 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\datareporting\glean\db\data.safe.tmp | binary | |
MD5:9C5B8DB6410704CD9BADB267BA8FECD1 | SHA256:F94C3077089A0CCBA345322AB9498A8AF59C291B58861769D49A5D1C7B12FF3E | |||
| 5604 | dllhost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\appcache[1].man | text | |
MD5:15F8A83AE8EE49313779C8A2A461FDFD | SHA256:46E6B38B3605545995D0C888227BA22938943604AB967272FF739D40E7D292C5 | |||
| 1568 | f8279e36-b6ba-4ee4-821b-a04a0b42313c.exe | C:\ProgramData\bbeecafdaeec.exe | executable | |
MD5:75D522502AFC10FBF04860F6BB314E24 | SHA256:4EFAA22F692B30BC8341D1FA8698B84524E2D5468E386B7B56589DAF097E26E6 | |||
| 1472 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 5116 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:3099560D40F605122A1187DBA4DE5366 | SHA256:39195CDD98FA8B9880028378F108A985019CA440FB0EEBF8D1A19AFB6C6819A1 | |||
| 6772 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:76BDB6D827C20D4631C4ABF54147A174 | SHA256:2F0E3A889D070404C0073F90C81DAF165B2C95D32AC5EEEB60C22B2301BAA99D | |||
| 5116 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:061AB6147E9F088EF0D02E60F4AC4E28 | SHA256:945BA06F006C65CA9944395CE26DDC3E21390455855944C6339AA854BEEDB2DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
36
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7020 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4772 | explorer.exe | POST | 200 | 185.156.72.89:80 | http://185.156.72.89/nzcwzue/pqrfxn.php | unknown | — | — | unknown |
1268 | svchost.exe | GET | 200 | 184.25.50.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4576 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4576 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5116 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3936 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7020 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7020 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4772 | explorer.exe | 185.156.72.89:80 | — | Tov Vaiz Partner | RU | unknown |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4772 | explorer.exe | A Network Trojan was detected | ET MALWARE Diamotrix POST Request M3 |