| File name: | with-editor.exe |
| Full analysis: | https://app.any.run/tasks/e5e2a862-04d2-4ee4-9e18-1751b818b5d0 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 12:41:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 60D463B942EB11EB141C0611BC3BC346 |
| SHA1: | B5C64B01AC4AC4C8D42EF830ACB80729A0AED180 |
| SHA256: | 4EF4CAE28CA3CFE2C1571C6BA074351A1AD410FDDB53BDDA1A299F2B6578BBB5 |
| SSDEEP: | 98304:VrGQnAU+5lecFGCJm7p9s5I1lqI6cMatsleim+HtkuCGH83gbrUl8mY15PsEP5cv:z0hrU8MaeBfQaL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- with-editor.tmp (PID: 7508)
- with-editor.exe (PID: 7492)
Reads the Windows owner or organization settings
- with-editor.tmp (PID: 7508)
There is functionality for taking screenshot (YARA)
- ReMouse.exe (PID: 7660)
INFO
Reads the computer name
- with-editor.tmp (PID: 7508)
- ReMouse.exe (PID: 7660)
Checks supported languages
- with-editor.tmp (PID: 7508)
- with-editor.exe (PID: 7492)
- ReMouse.exe (PID: 7660)
Create files in a temporary directory
- with-editor.exe (PID: 7492)
- with-editor.tmp (PID: 7508)
- ReMouse.exe (PID: 7660)
Creates files or folders in the user directory
- with-editor.tmp (PID: 7508)
The sample compiled with english language support
- with-editor.tmp (PID: 7508)
Creates a software uninstall entry
- with-editor.tmp (PID: 7508)
Reads mouse settings
- ReMouse.exe (PID: 7660)
The process uses AutoIt
- ReMouse.exe (PID: 7660)
Reads the software policy settings
- slui.exe (PID: 7572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.6.0.0 |
| ProductVersionNumber: | 5.6.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
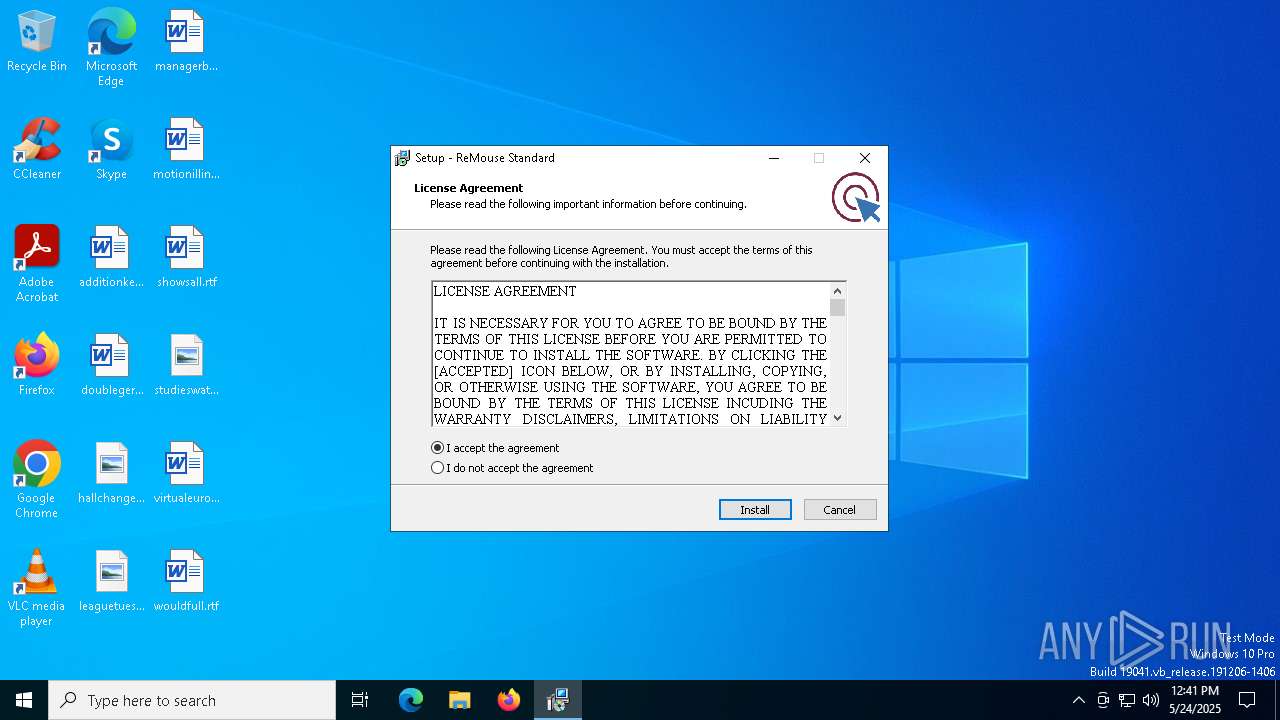
| Comments: | This installation was built with Inno Setup. |
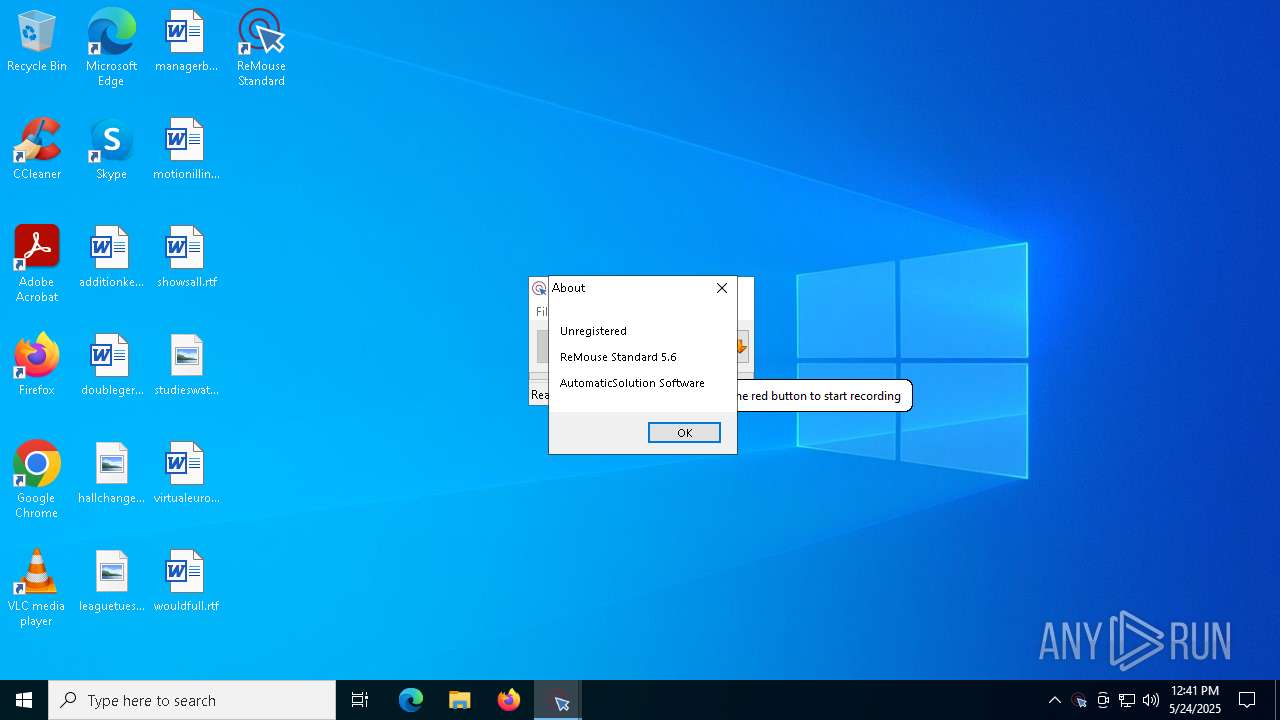
| CompanyName: | AutomaticSolution Software |
| FileDescription: | ReMouse |
| FileVersion: | ReMouse Standard V5. |
| LegalCopyright: | AutomaticSolution Software |
| ProductName: | ReMouse Standard |
| ProductVersion: | Standard V5.6 |
Total processes
132
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 7492 | "C:\Users\admin\AppData\Local\Temp\with-editor.exe" | C:\Users\admin\AppData\Local\Temp\with-editor.exe | explorer.exe | |
User: admin Company: AutomaticSolution Software Integrity Level: MEDIUM Description: ReMouse Exit code: 0 Version: ReMouse Standard V5. | ||||
| 7508 | "C:\Users\admin\AppData\Local\Temp\is-Q46TM.tmp\with-editor.tmp" /SL5="$40308,5411417,57856,C:\Users\admin\AppData\Local\Temp\with-editor.exe" | C:\Users\admin\AppData\Local\Temp\is-Q46TM.tmp\with-editor.tmp | with-editor.exe | |
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 | ||||
| 7540 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | ||||
| 7572 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
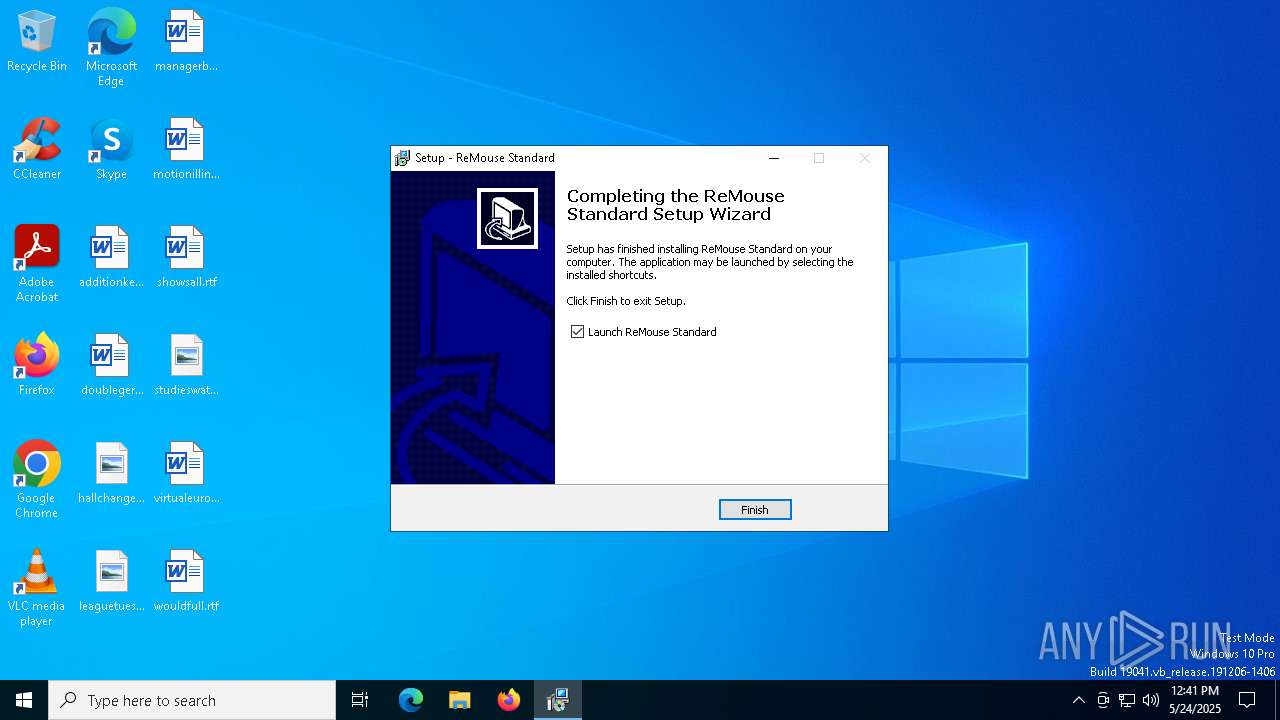
| 7660 | "C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\ReMouse.exe" | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\ReMouse.exe | — | with-editor.tmp |
User: admin Integrity Level: MEDIUM Description: ReMouse Standard Exit code: 0 Version: 5.6 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
22
Suspicious files
14
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\is-L22TI.tmp | executable | |
MD5:806FA8F8139A42BDB2DB874AAE80EEEB | SHA256:5580952DDC00BDA249DB0E718AFB09AB8C5AC828418A45766EA39ED941EC76D6 | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\is-E2N51.tmp | executable | |
MD5:95EDCB135FD8AE184FF9B604BEB77F13 | SHA256:4C62259F8797612FD58E154FF9E5BA7FE114BCBF5FD310F2C9B2A013F2B84013 | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Local\Temp\is-6MR0S.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\is-OG5H8.tmp | executable | |
MD5:6FC61A2907F2E39A1E450D7801ECAE43 | SHA256:4E31D3155A3408805C91D1714BB45DE7847E77780BF3D91F3405FEB3EF9AC15B | |||
| 7492 | with-editor.exe | C:\Users\admin\AppData\Local\Temp\is-Q46TM.tmp\with-editor.tmp | executable | |
MD5:832DAB307E54AA08F4B6CDD9B9720361 | SHA256:CC783A04CCBCA4EDD06564F8EC88FE5A15F1E3BB26CEC7DE5E090313520D98F3 | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\ReMouse.exe | executable | |
MD5:697D7FFC29417B81F4F2BBF8EACF2C7E | SHA256:D9D65769B6534CAD0FBC5E56412A76381929500B4B10E69B30A752D2F5E3B2BC | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\is-2P052.tmp | executable | |
MD5:697D7FFC29417B81F4F2BBF8EACF2C7E | SHA256:D9D65769B6534CAD0FBC5E56412A76381929500B4B10E69B30A752D2F5E3B2BC | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\conf\rms_tasks_conf.ini | text | |
MD5:3ED951C332C0C1176DCB20A99868B3A2 | SHA256:94C4BE28C7247CF7FE24E54D236403FEF381853DECBD6929565A7E52C00E3EF4 | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\conf\is-0TM4Q.tmp | binary | |
MD5:92EDBD5A48B9CDCEE8D6B9B0CC36030C | SHA256:AA43E6F744A00987FD779291D9318CF689C198972E46ABB779F4166D7C571BC9 | |||
| 7508 | with-editor.tmp | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Standard\conf\rms_conf.ini | text | |
MD5:A245E07BCC44CC10882E3C9D53292ECA | SHA256:90DD9C55D4C67621B9F6CB67084F067A95BAA73066C70E0F31E8F5E4346E8DC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7852 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7852 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5756 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7852 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7852 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |