| File name: | Internet Download Manager 6.42 Build 32.exe |
| Full analysis: | https://app.any.run/tasks/ae022906-34a7-4703-94c4-46e868734f37 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2025, 17:22:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 27308F126D50CA203B3454D94BC85368 |
| SHA1: | 24A3869DC7E0227BAD9A6E0C6F21E0732A6479CE |
| SHA256: | 4EF342B61D6EC240F58955C087ADA416EB300E02E6AD78A3A6259A1D7A06E822 |
| SSDEEP: | 98304:nDQPuum20W/5XfzUj0XFJk5u/Nbq9xbzIm6XXkWLdbDn75Xf7B5/I9ehctediwSs:SXWqN0nC62jPTN2YZvK2MDyz |
MALICIOUS
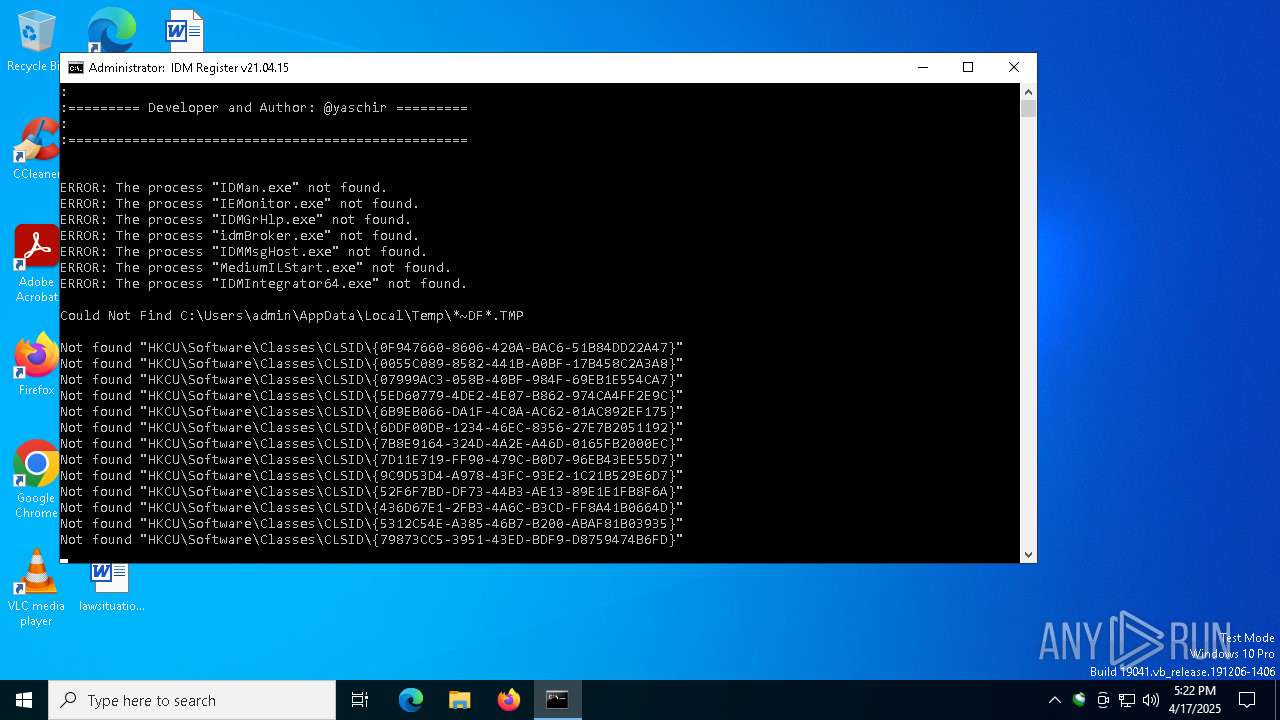
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 1328)
SUSPICIOUS
Reads security settings of Internet Explorer
- Internet Download Manager 6.42 Build 32.exe (PID: 6184)
- Kur.exe (PID: 920)
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
- IDM1.tmp (PID: 1328)
- IDMan.exe (PID: 2984)
Application launched itself
- Internet Download Manager 6.42 Build 32.exe (PID: 6184)
- cmd.exe (PID: 1628)
Executable content was dropped or overwritten
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
Process drops legitimate windows executable
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
Executing commands from a ".bat" file
- Kur.exe (PID: 920)
Starts CMD.EXE for commands execution
- Kur.exe (PID: 920)
- cmd.exe (PID: 1628)
Identifying current user with WHOAMI command
- cmd.exe (PID: 4688)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1628)
Starts application with an unusual extension
- Kur.exe (PID: 920)
There is functionality for taking screenshot (YARA)
- Internet Download Manager 6.42 Build 32.exe (PID: 6184)
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
- Kur.exe (PID: 920)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 1328)
Creates a software uninstall entry
- IDM1.tmp (PID: 1328)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 1328)
- regsvr32.exe (PID: 896)
- regsvr32.exe (PID: 6392)
- regsvr32.exe (PID: 1012)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1628)
INFO
Reads the computer name
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
- Internet Download Manager 6.42 Build 32.exe (PID: 6184)
- Kur.exe (PID: 920)
- IDM1.tmp (PID: 1328)
- IDMan.exe (PID: 2984)
- idmBroker.exe (PID: 2040)
The sample compiled with russian language support
- Internet Download Manager 6.42 Build 32.exe (PID: 6184)
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
Checks supported languages
- Internet Download Manager 6.42 Build 32.exe (PID: 6184)
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
- Kur.exe (PID: 920)
- IDM1.tmp (PID: 1328)
- IDMan.exe (PID: 2984)
- idmBroker.exe (PID: 2040)
Process checks computer location settings
- Internet Download Manager 6.42 Build 32.exe (PID: 6184)
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
- Kur.exe (PID: 920)
- IDM1.tmp (PID: 1328)
The sample compiled with english language support
- Internet Download Manager 6.42 Build 32.exe (PID: 1228)
Reads mouse settings
- Kur.exe (PID: 920)
Creates files in the program directory
- IDM1.tmp (PID: 1328)
- Kur.exe (PID: 920)
- IDMan.exe (PID: 2984)
Creates files or folders in the user directory
- IDM1.tmp (PID: 1328)
Reads the software policy settings
- IDMan.exe (PID: 2984)
Reads the machine GUID from the registry
- IDMan.exe (PID: 2984)
Disables trace logs
- IDMan.exe (PID: 2984)
The process uses AutoIt
- Kur.exe (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:31 00:38:51+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 101888 |
| InitializedDataSize: | 238592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1942f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.42.32.1 |
| ProductVersionNumber: | 6.42.32.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
| CompanyName: | SolidShare |
| FileDescription: | SolidShare.Net Unattended Installer |
| LegalCopyright: | © 2025 By KiNGHaZe |
| LegalTrademarks: | - |
| InternalName: | - |
| ProductName: | Internet Download Manager |
| OriginalFileName: | - |
| FileVersion: | 6.42.32.1 |
| ProductVersion: | 6.42.32.1 |
| Comments: | SolidShare.Net Unattended Installer |
| PrivateBuild: | - |
| SpecialBuild: | - |
Total processes
552
Monitored processes
422
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | REG DELETE "HKCU\Software\Classes\CLSID\{9C9D53D4-A978-43FC-93E2-1C21B529E6D7}" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | reg query "HKCU\Software\Classes\CLSID\{CDC95B92-E27C-4745-A8C5-64A52A78855D}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | reg query "HKCU\Software\Classes\Wow6432Node\CLSID\{9C9D53D4-A978-43FC-93E2-1C21B529E6D7}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | REG DELETE "HKLM\Software\Classes\Wow6432Node\CLSID\{436D67E1-2FB3-4A6C-B3CD-FF8A41B0664D}" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | reg query "HKU\.DEFAULT\Software\Classes\CLSID\{6B9EB066-DA1F-4C0A-AC62-01AC892EF175}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | reg query "HKU\.DEFAULT\Software\Classes\CLSID\{E8CF4E59-B7A3-41F2-86C7-82B03334F22A}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | REG DELETE "HKU\.DEFAULT\Software\Wow6432Node\Download Manager" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | REG DELETE "HKCU\Software\DownloadManager" /v "Email" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | reg query "HKCU\Software\Classes\CLSID\{C950922F-897A-4E13-BA38-66C8AF2E0BF7}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | reg query "HKCU\Software\Classes\CLSID\{D0FB58BB-2C07-492F-8BD0-A587E4874B4E}" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 304
Read events
15 156
Write events
138
Delete events
10
Modification events
| (PID) Process: | (2984) reg.exe | Key: | HKEY_LOCAL_MACHINE |
| Operation: | delete value | Name: | Model |
Value: | |||
| (PID) Process: | (1012) reg.exe | Key: | HKEY_LOCAL_MACHINE |
| Operation: | delete value | Name: | MData |
Value: | |||
| (PID) Process: | (6576) reg.exe | Key: | HKEY_LOCAL_MACHINE |
| Operation: | delete value | Name: | Therad |
Value: | |||
| (PID) Process: | (536) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Internet Download Manager |
| Operation: | write | Name: | LstCheck |
Value: 12/12/60 | |||
| (PID) Process: | (6592) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | scansk |
Value: 911DACD6905C42EABA1AAC081A182F162AA80AAA24BF0CFC4E7B3B76F77093585C03037E04ABB07E00000000000000000000 | |||
| (PID) Process: | (5608) reg.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C} |
| Operation: | write | Name: | scansk |
Value: 911DACD6905C42EABA1AAC081A182F162AA80AAA24BF0CFC4E7B3B76F77093585C03037E04ABB07E00000000000000000000 | |||
| (PID) Process: | (5228) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C} |
| Operation: | write | Name: | scansk |
Value: 911DACD6905C42EABA1AAC081A182F162AA80AAA24BF0CFC4E7B3B76F77093585C03037E04ABB07E00000000000000000000 | |||
| (PID) Process: | (896) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Internet Download Manager |
| Operation: | write | Name: | scansk |
Value: 911DACD6905C42EABA1AAC081A182F162AA80AAA24BF0CFC4E7B3B76F77093585C03037E04ABB07E00000000000000000000 | |||
| (PID) Process: | (920) Kur.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | bShLc2 |
Value: 1 | |||
| (PID) Process: | (1328) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayVersion |
Value: 6.42.32 | |||
Executable files
48
Suspicious files
37
Text files
169
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM1.tmp | executable | |
MD5:1C734D0DED634D8E17A87ABA3D44F41D | SHA256:645EE6E64ED04825B25964D992D0205963498BB9D61F5A52BE7E76DDB2074003 | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM104.tmp | text | |
MD5:E1C1EF12FD935E72F2E676A593AD8E68 | SHA256:DA36C077EC7C96128D0E5EE5941FAD1F779A58A33652D7190E814A75F8BC29CE | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM108.tmp | text | |
MD5:3DA98A953BCBCC9F1E9D143542437C20 | SHA256:14D51E3B9F5E68E97ED01A6BB1C598E3E09F9E330A90DBE363D6659AC725F679 | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM109.tmp | text | |
MD5:07A324E23BB33CE824A539CFA499BDA0 | SHA256:9619F587E3EF863B7FD69650DCBC1D655D6062C3F73EAF52ACA59754AD856B83 | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM103.tmp | text | |
MD5:16E2DAB5D2473C59DEA2B2BD316517E8 | SHA256:07C8896550FBAA6E8FEC792E15D240DED0BCFFA258A928C1EFD8542FF0385511 | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM101.tmp | text | |
MD5:F50ACF2F4AF9EA575B643576F3A190EF | SHA256:EA297E912D0CF36F2D973B9259BF8FABF622195D5481A11E7BD30967F213D950 | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM110.tmp | executable | |
MD5:3114BB1630E44CFBD48B09E0D6057C8F | SHA256:1621FD14DD72DCCE8BBA2E7F46D656744D2975F8AD94B36D2ADE01415F48022A | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM106.tmp | executable | |
MD5:1B4800DDCA76B060DDCAC8B5E7F1C460 | SHA256:471387FEFF538F001457E0FB485109853301C5ACE327722427F20EF48A2307C4 | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM11.tmp | text | |
MD5:E7A9F01178B8F6CEB1D02333D6916B4F | SHA256:92F60CDA7A7395D5D4CACE82C7270AFAC5D1B68A2B7714BB1510058FAC23879F | |||
| 1228 | Internet Download Manager 6.42 Build 32.exe | C:\Kinghaze\Kur\IDM114.tmp | compressed | |
MD5:10D9220EA4E455276734E884E830A0D2 | SHA256:E691EBADD8C6E7A07D9C8C931F4760F9AADD2B151019E4F17A76A1665057C9CB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2096 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2096 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |