| download: | / |
| Full analysis: | https://app.any.run/tasks/a32dd408-d0b8-4a00-9654-aca1f2ae4842 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2024, 04:21:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 text, with very long lines (9773), with CRLF, LF line terminators |
| MD5: | 24480084A654D9772CB08B34E0A4F52D |
| SHA1: | BB1784EA065C27561EF7196CB28CF0E3AD326E6D |
| SHA256: | 4EE58E460A42B300E5709C416EEF43BA88C6A677F49760E6227BEC362D9FAB5E |
| SSDEEP: | 1536:ZNwaporz67UmQSR1qEYtYxqNBrqYdUYHLaYsmpA/KPf5vRkP5O:ZhjwER1qEYtYxqbrqVYsmp6K355kP5O |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3980)
- iexplore.exe (PID: 4040)
Reads the computer name
- wmpnscfg.exe (PID: 1948)
Checks supported languages
- wmpnscfg.exe (PID: 1948)
Manual execution by a user
- wmpnscfg.exe (PID: 1948)
- explorer.exe (PID: 1976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Viewport: | width=device-width, initial-scale=1 |
|---|---|
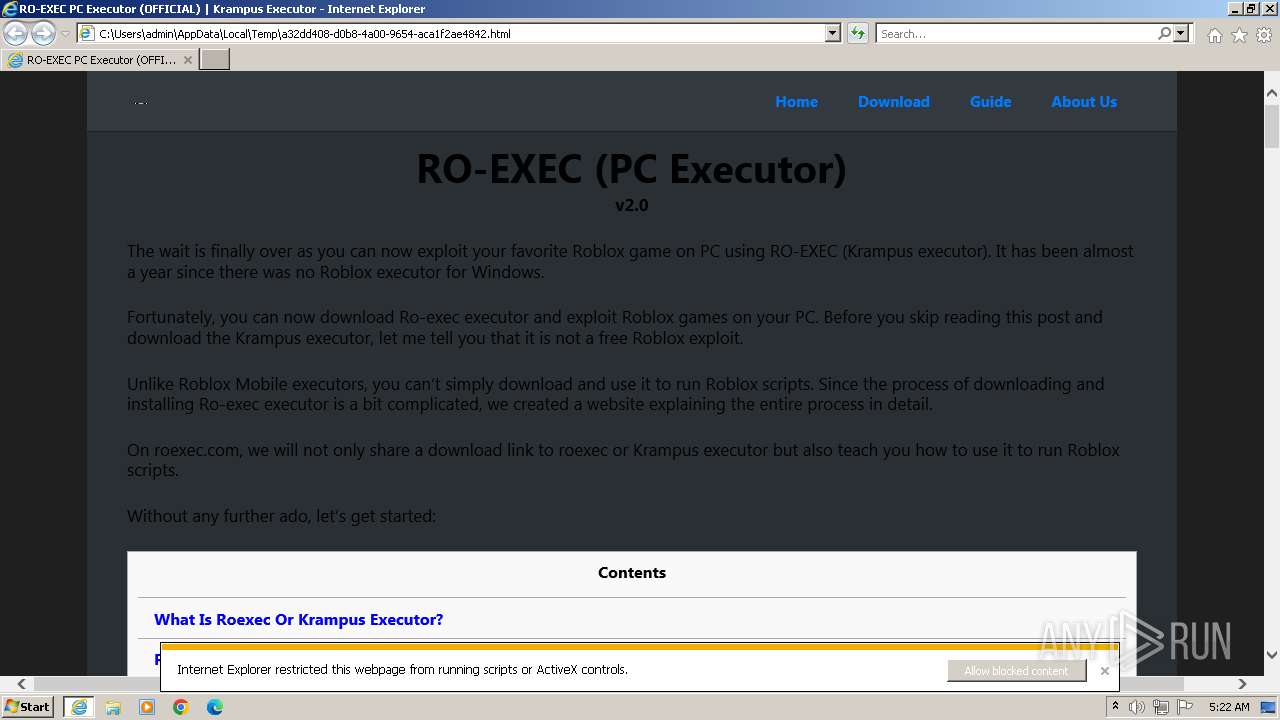
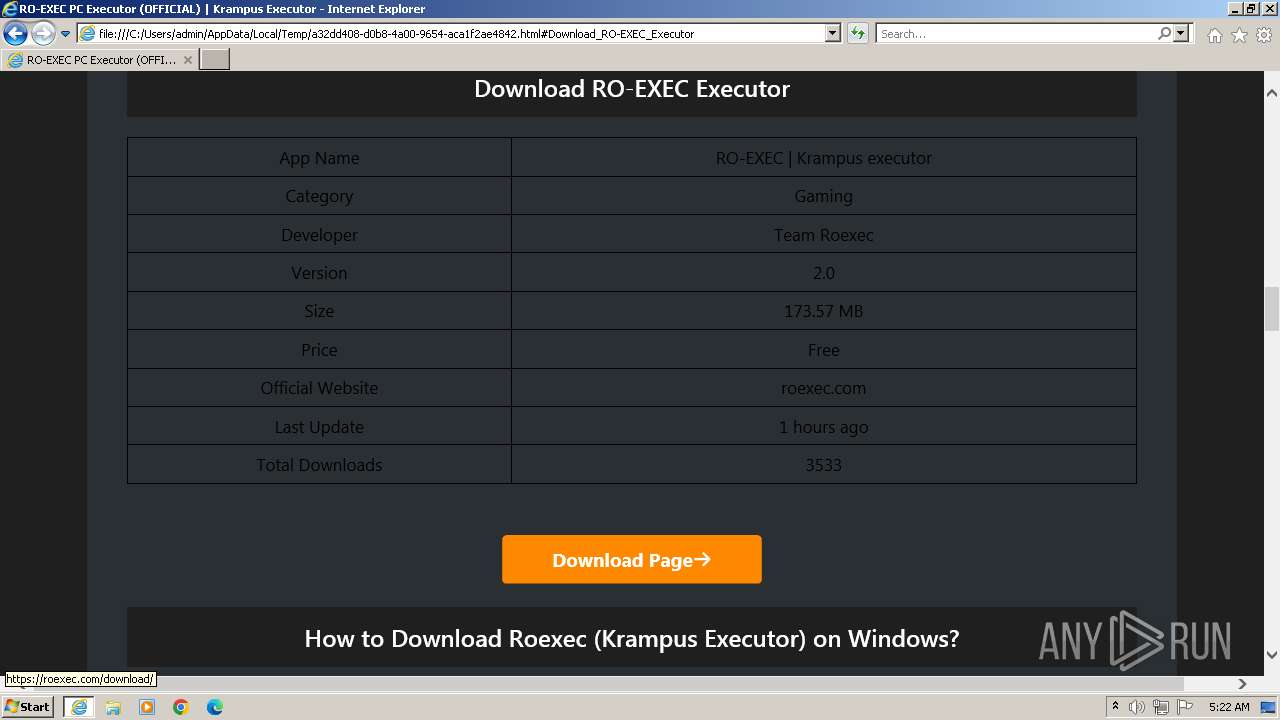
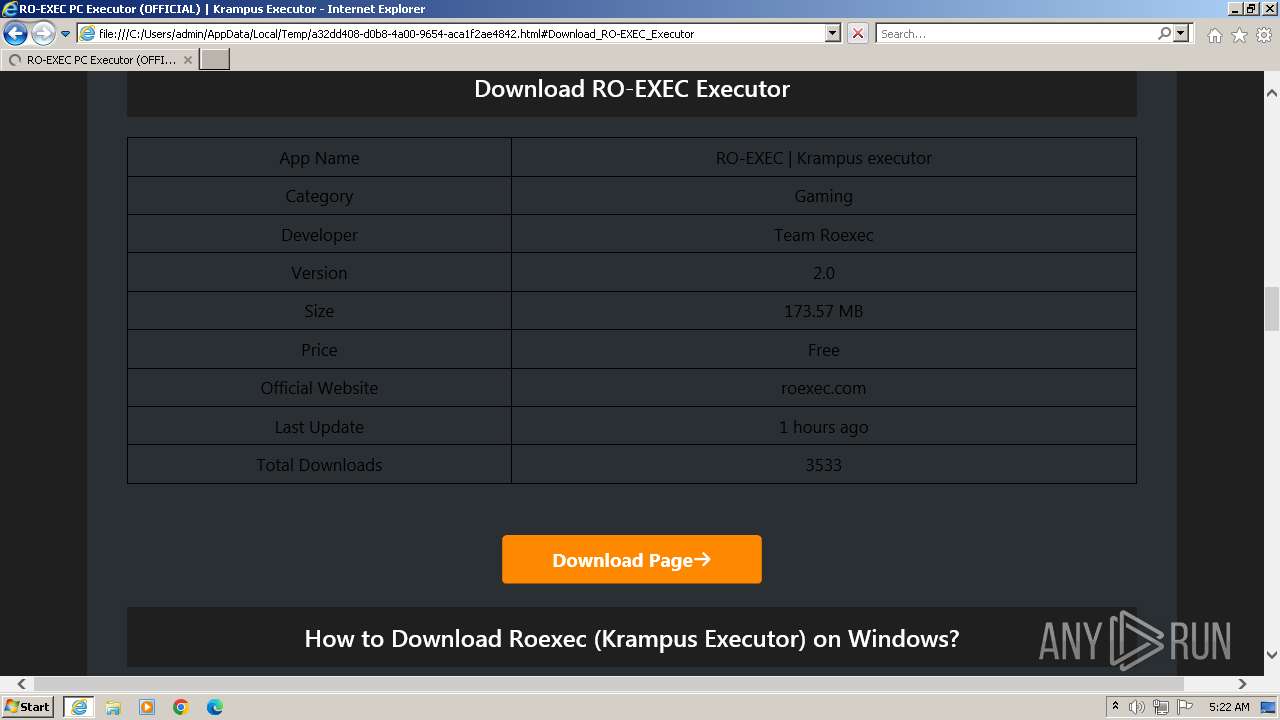
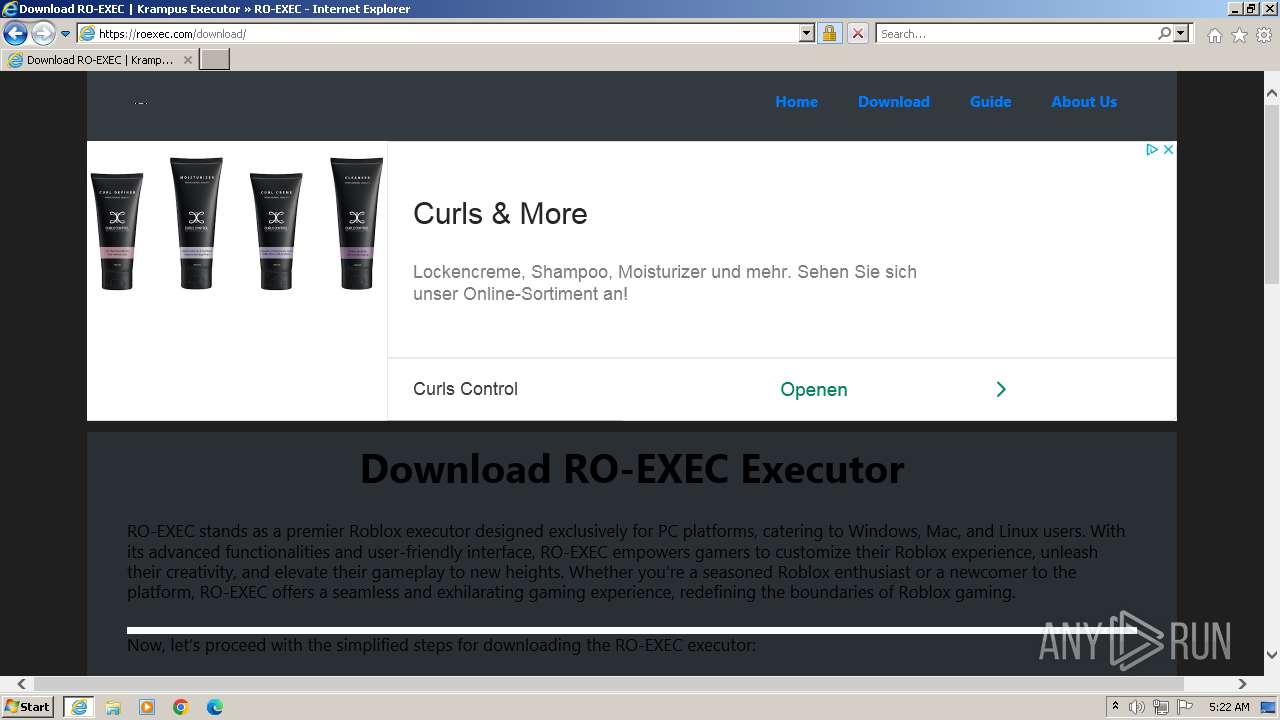
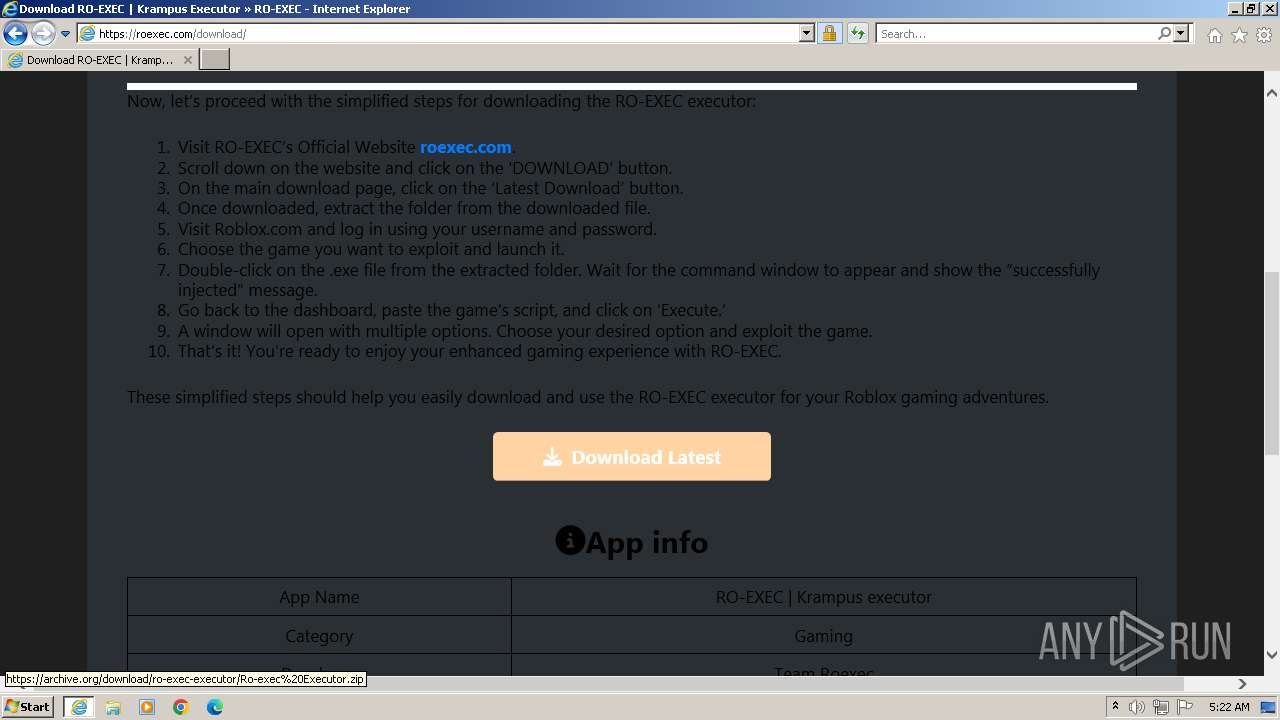
| Title: | RO-EXEC PC Executor (OFFICIAL) | Krampus Executor |
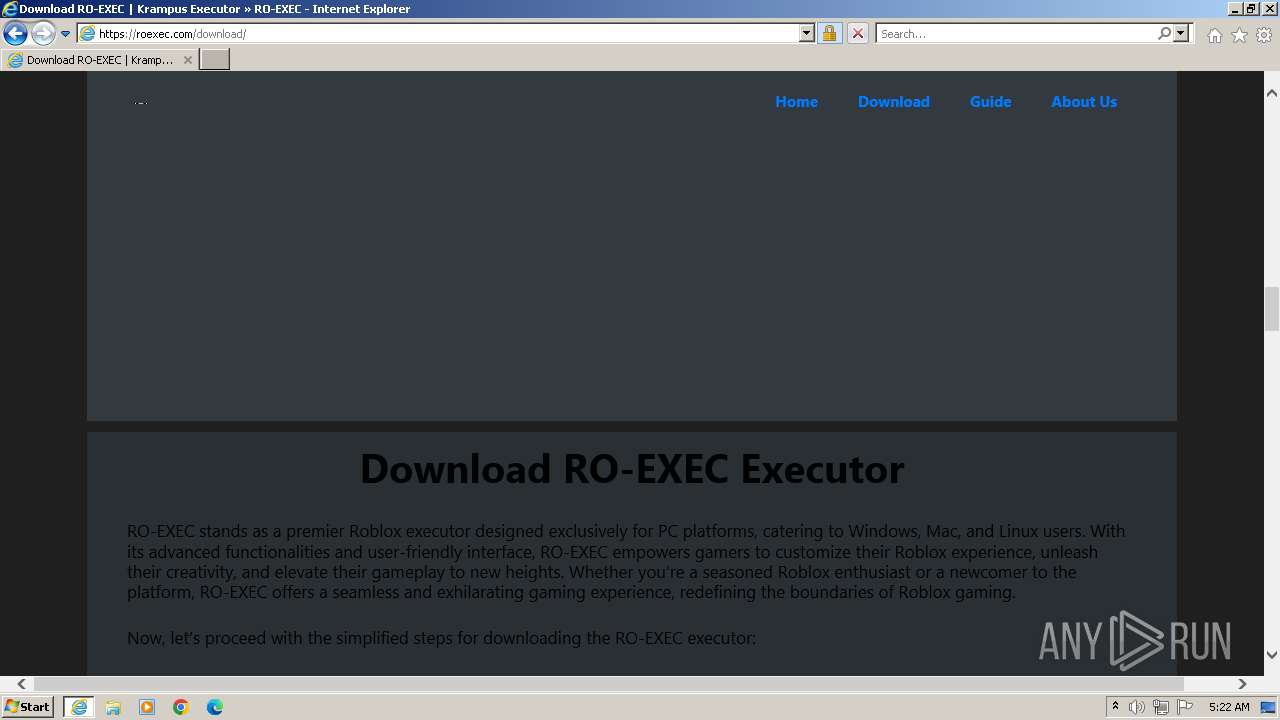
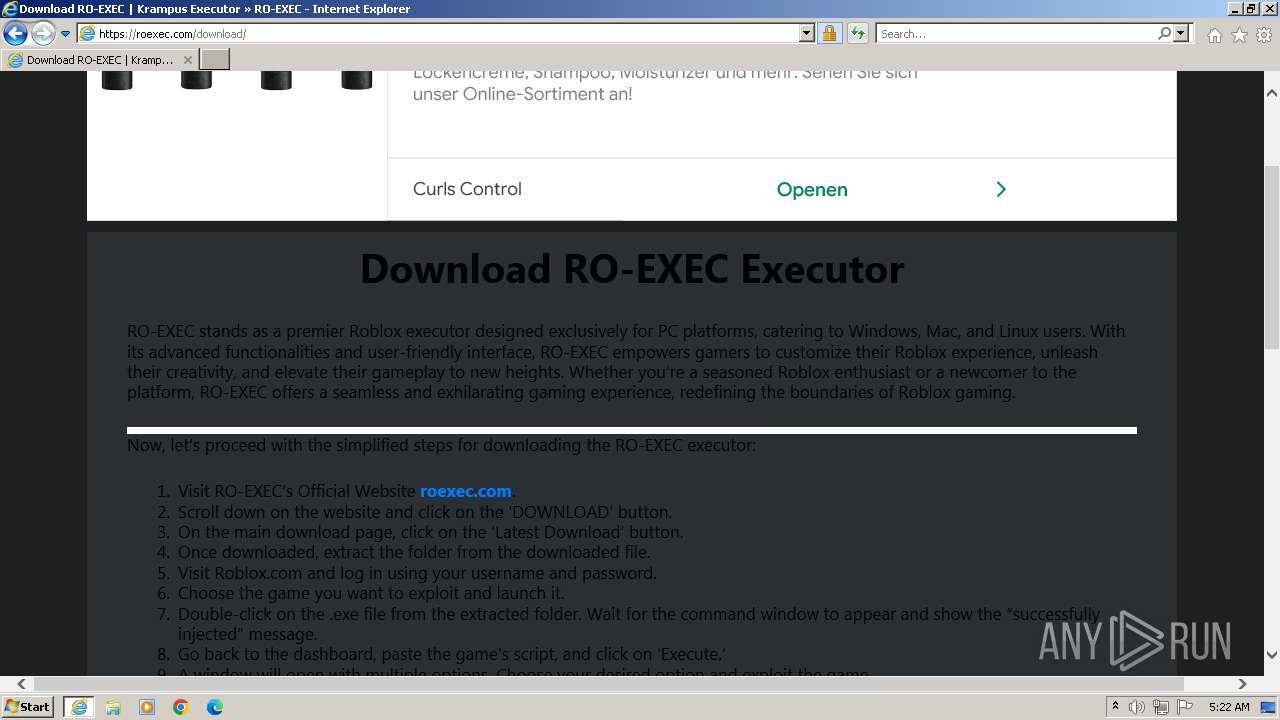
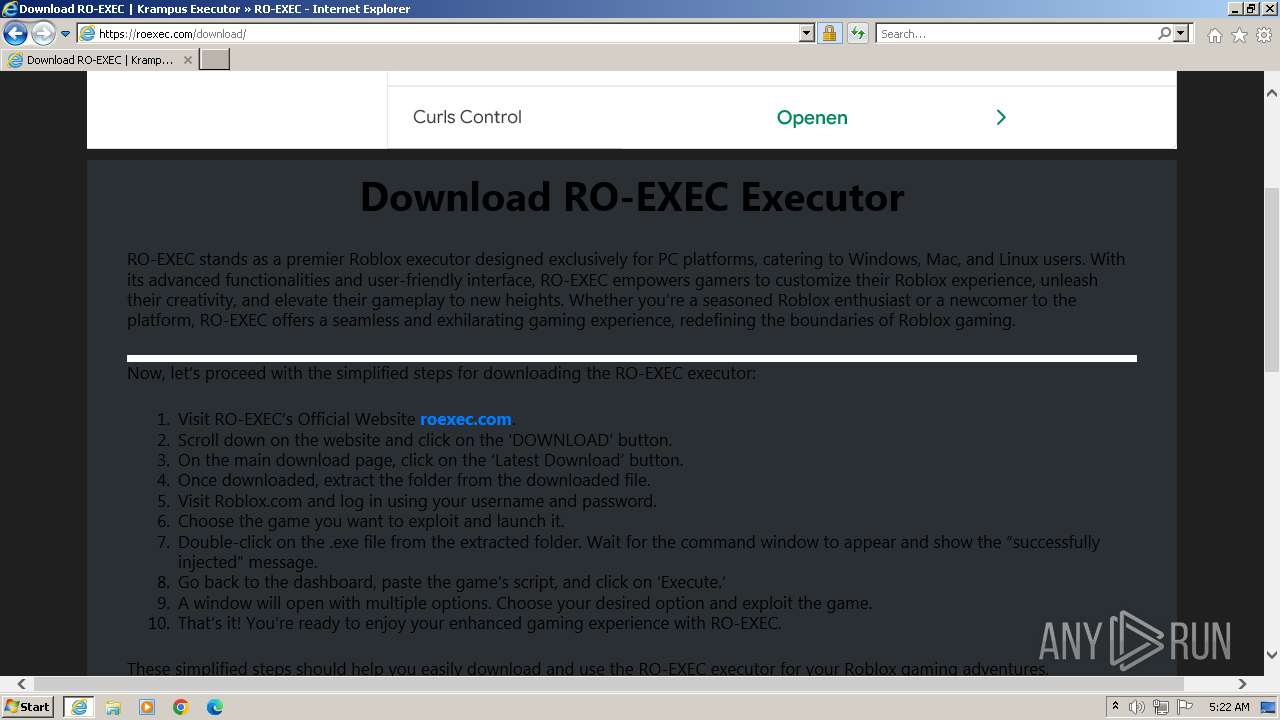
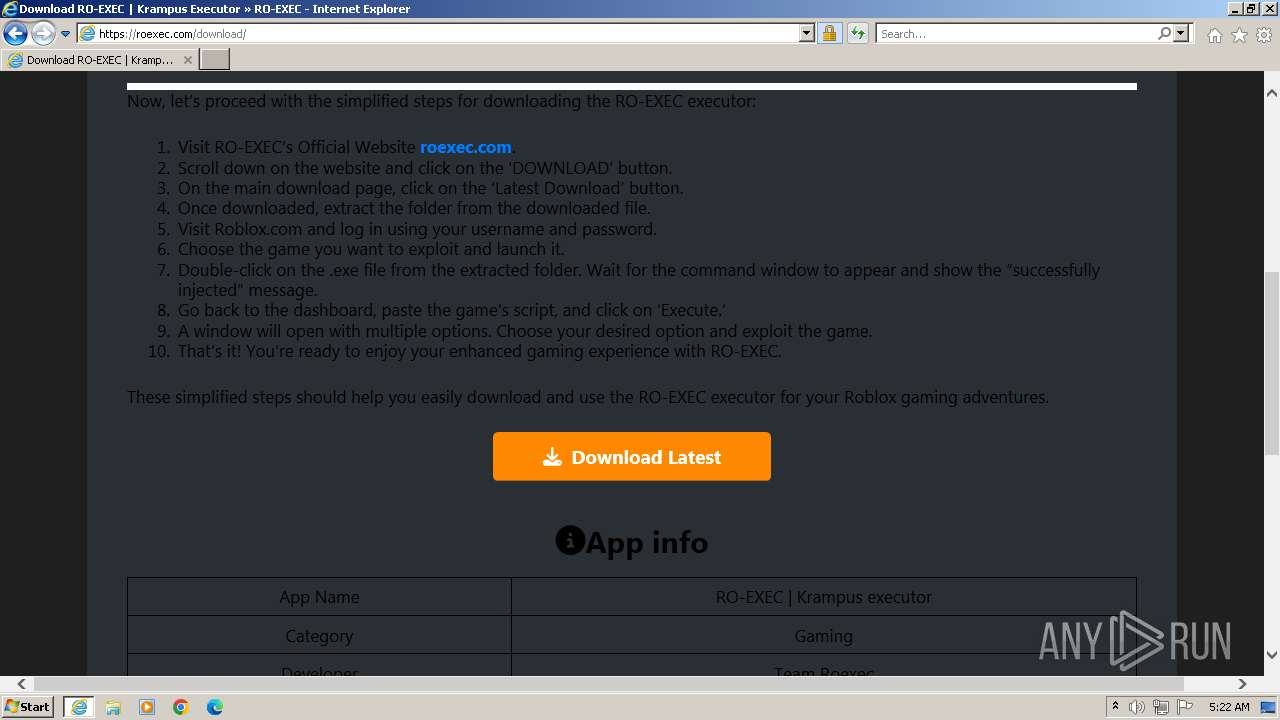
| Description: | RO-EXEC or Krampus executor is developed for PC Windows, Mac and Linux devices to run Roblox scripts. For the unversed, Roblox scripts offer a bunch of additional features but they can’t be accessed without using executors like RO-EXEC. |
| Robots: | follow, index, max-snippet:-1, max-video-preview:-1, max-image-preview:large |
| TwitterCard: | summary_large_image |
| TwitterTitle: | RO-EXEC PC Executor (OFFICIAL) | Krampus Executor |
| TwitterDescription: | RO-EXEC or Krampus executor is developed for PC Windows, Mac and Linux devices to run Roblox scripts. For the unversed, Roblox scripts offer a bunch of additional features but they can’t be accessed without using executors like RO-EXEC. |
| TwitterLabel1: | Written by |
| TwitterData1: | Team Roexec |
| TwitterLabel2: | Time to read |
| TwitterData2: | 6 minutes |
| Generator: | WordPress 6.5.3 |
| Msvalidate01: | 2AC306E85118241DDDBF20AB109CB39E |
| MsapplicationTileImage: | https://roexec.com/wp-content/uploads/2024/02/RO-EXEC-Icon.webp |
Total processes
40
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1948 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1976 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3980 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\a32dd408-d0b8-4a00-9654-aca1f2ae4842.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3980 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
57 522
Read events
57 233
Write events
176
Delete events
113
Modification events
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31105681 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31105681 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
52
Text files
64
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:7F7BE58FAADBF1858684D3652E53B25C | SHA256:179A0034637BFD5C884E0ED8898B76576D253FB310BCCD3CEFAF36F20A3CC0F2 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:B6E71ADF7324685D8F60C97BDB99F892 | SHA256:40A181E9A8B85B862AFC89A604EB290BE3B5CD68937FEB9CCFC467D3589E8E5C | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:BA40CAE22F62073DB4F5D279BE419BBA | SHA256:486D8E6F52AB11DAA10EA9535DEABB432FABBDE202A12CC46F3F34DD10F7B316 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\rank-math-snippet[1].css | text | |
MD5:149A0B20BCECFDF2662724BD4F15AA66 | SHA256:9D650FA59C49B549CEB7FE45C93C1F139C27D2BA5BD379522E3A80D9FA69FDD2 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\style-11[1].css | text | |
MD5:34839ACE6CBCBBFB3A849BBFF6B6D3C6 | SHA256:FF8B3DE8A1898C5686A327F32657B8423A538426553836FBCDD3865062850E60 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:75CED20BA3C434DA4E310B0132FE2CC4 | SHA256:CA775BF55E97D9B7B9BF0BD158A02C0A6A7F75F1456748BFE1FE2B6477D7CB12 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\jquery.scrollTo.min[1].js | binary | |
MD5:4F3D9D7281A2828E319DE38B9142F860 | SHA256:ED04B5707B07EF987720582B14AB1D8662871E95AA17CDAC6FFF6F34BA9CAACD | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\screen.min[1].css | text | |
MD5:C36A54231034D43C59838CFFD223AE0E | SHA256:2E36BD3BDBB929F427E79A6C84B7922B4375589386981EBA29EB0CFF57B02B1B | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\style.min[1].css | text | |
MD5:51A8390B47AA0582CF2D9C96C5ADDEE2 | SHA256:98CECF88A23542FA047CE46EEDB650B5C5128761ED4386C0977B847094DDFA20 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
85
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4040 | iexplore.exe | GET | 304 | 173.222.245.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bf076dfe6f22cdd6 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 173.222.245.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a76a59998ead8fcc | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 2.16.135.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?668da2777c908bf3 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 173.222.245.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?386151522f624b4f | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 173.222.245.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?244304fed332727e | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 2.16.135.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3246d2a31b163535 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 173.222.245.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c217e55963a0e9a4 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 173.222.245.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fa31f03270691d40 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 173.222.245.51:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c9c7af3a0358978d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4040 | iexplore.exe | 192.0.76.3:443 | stats.wp.com | AUTOMATTIC | US | unknown |
4040 | iexplore.exe | 216.58.206.66:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
4040 | iexplore.exe | 188.114.97.3:443 | roexec.com | CLOUDFLARENET | NL | unknown |
4040 | iexplore.exe | 216.58.206.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
4040 | iexplore.exe | 2.16.135.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | IT | unknown |
4040 | iexplore.exe | 173.222.245.51:80 | ctldl.windowsupdate.com | Akamai International B.V. | IT | unknown |
4040 | iexplore.exe | 216.58.212.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
4040 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
3980 | iexplore.exe | 2.16.135.179:443 | www.bing.com | Akamai International B.V. | IT | unknown |
3980 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.googletagmanager.com |
| whitelisted |
roexec.com |
| unknown |
pagead2.googlesyndication.com |
| whitelisted |
stats.wp.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |