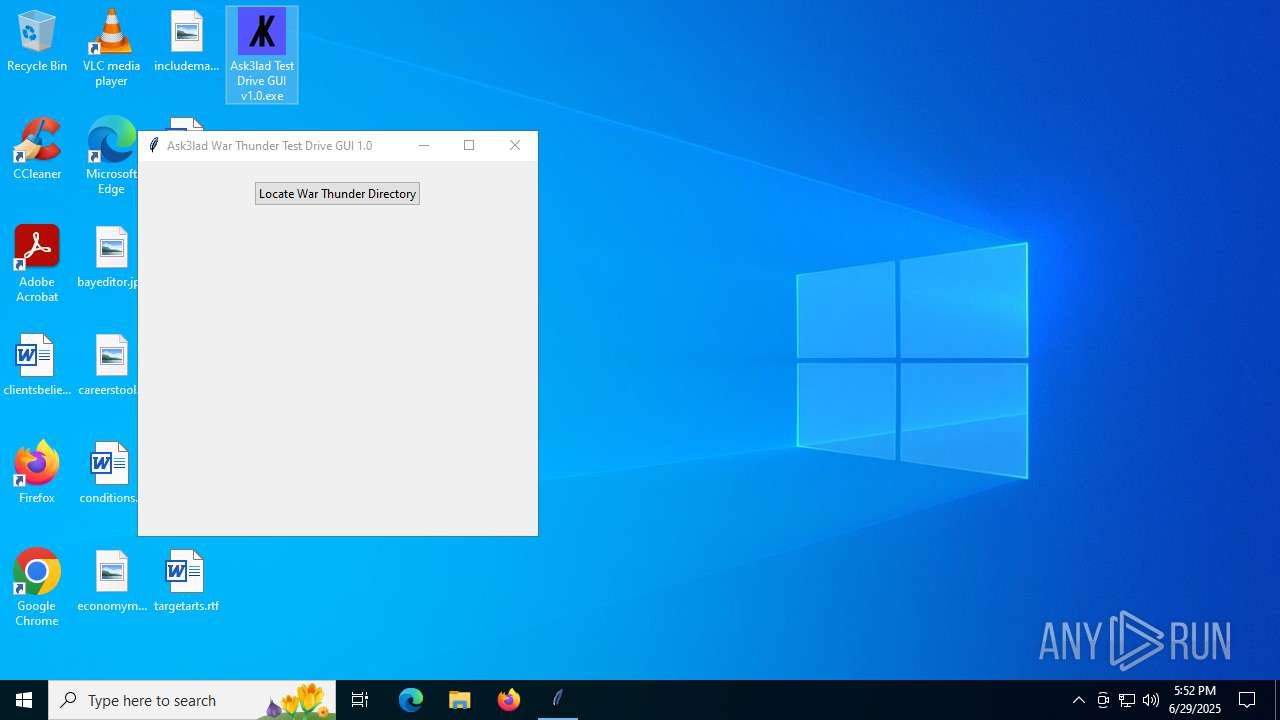
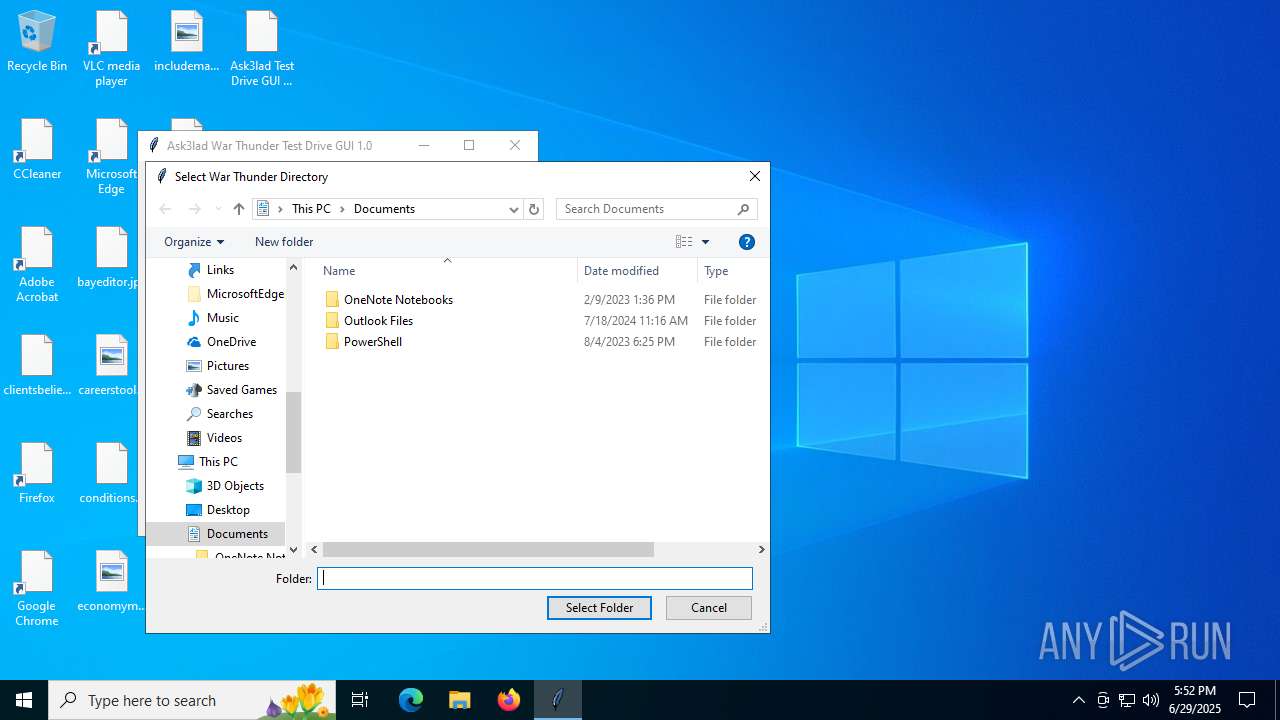
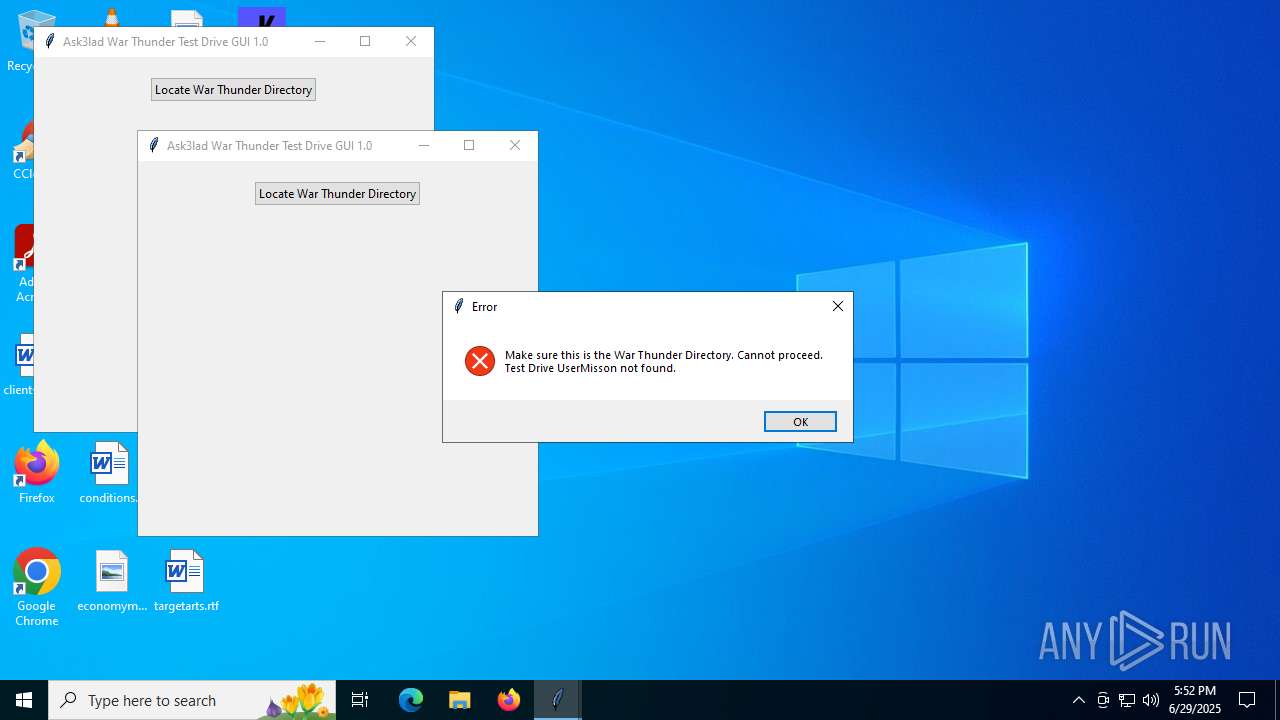
| File name: | Ask3lad Test Drive GUI v1.0.exe |
| Full analysis: | https://app.any.run/tasks/70e2399e-1445-4b76-990d-d82165d020f9 |
| Verdict: | Malicious activity |
| Analysis date: | June 29, 2025, 17:52:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | A6A82FD086C636466B7780D6AEE02E18 |
| SHA1: | 6DC3EA9AAA89BB7D6CD0FDC6E60DFFF915273204 |
| SHA256: | 4ED6E2CC2E4D2A2CDF0D33EEA4D085710BFFC359C6735C4A13385D17688CE62B |
| SSDEEP: | 98304:B1T2Q69eg7aLeiEtzUz6yW6H+lAJuz3R0z86VoIsvRPnPigA8SeSok24iVoumzy1:M6dI49LEEZ5KAOJdGV6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
Process drops legitimate windows executable
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
Process drops python dynamic module
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
Executable content was dropped or overwritten
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
There is functionality for taking screenshot (YARA)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
Application launched itself
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
Loads Python modules
- Ask3lad Test Drive GUI v1.0.exe (PID: 2468)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3624)
Reads security settings of Internet Explorer
- Ask3lad Test Drive GUI v1.0.exe (PID: 2468)
INFO
Checks supported languages
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
- Ask3lad Test Drive GUI v1.0.exe (PID: 2468)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3624)
Reads the computer name
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
- Ask3lad Test Drive GUI v1.0.exe (PID: 2468)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3624)
The sample compiled with english language support
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
Create files in a temporary directory
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
Manual execution by a user
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
- Ask3lad Test Drive GUI v1.0.exe (PID: 4320)
PyInstaller has been detected (YARA)
- Ask3lad Test Drive GUI v1.0.exe (PID: 2076)
- Ask3lad Test Drive GUI v1.0.exe (PID: 3908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:23 21:42:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 173568 |
| InitializedDataSize: | 109568 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce20 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
5
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2076 | "C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe" | C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe" | C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe | — | Ask3lad Test Drive GUI v1.0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe" | C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe | — | Ask3lad Test Drive GUI v1.0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3908 | "C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe" | C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4320 | "C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe" | C:\Users\admin\Desktop\Ask3lad Test Drive GUI v1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 747
Read events
3 711
Write events
35
Delete events
1
Modification events
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000003000000110000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000003000000050000000200000001000000FFFFFFFF | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 121 | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 9 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D3A002E80922B16D365937A46956B92703ACA08AF260001002600EFBE11000000FCD61862AF27D301269D8E065892DB01609C93A21EE9DB0114000000 | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 09000000070000000800000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2468) Ask3lad Test Drive GUI v1.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | FFlags |
Value: | |||
Executable files
57
Suspicious files
8
Text files
2 722
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\PIL\_imaging.cp311-win_amd64.pyd | executable | |
MD5:12B15796716A81A13B79A79D26C61F22 | SHA256:B231D11718A12994A32E744B93F830E931409AE13FAEB150D9F020A2E81CB18C | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_decimal.pyd | executable | |
MD5:C88282908BA54510EDA3887C488198EB | SHA256:980A63F2B39CF16910F44384398E25F24482346A482ADDB00DE42555B17D4278 | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_bz2.pyd | executable | |
MD5:AA1083BDE6D21CABFC630A18F51B1926 | SHA256:00B8CA9A338D2B47285C9E56D6D893DB2A999B47216756F18439997FB80A56E3 | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_lzma.pyd | executable | |
MD5:B86B9F292AF12006187EBE6C606A377D | SHA256:F5E01B516C2C23035F7703E23569DEC26C5616C05A929B2580AE474A5C6722C5 | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\PIL\_imagingmath.cp311-win_amd64.pyd | executable | |
MD5:F56EF1F1B506982ADBC1FC5650C9F869 | SHA256:8E633CB075B6110121CF2A9081DC79F074DE81CFCDF1C18FDF000BD256A14F60 | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\PIL\_imagingcms.cp311-win_amd64.pyd | executable | |
MD5:43B3768D75BE9F6635FBEC96633D70E0 | SHA256:CCD589E4B61B76F696B7B8DC8BB93A0E1DDF78A91BC78ED0E3A0DB0CEE101CEF | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_tcl_data\encoding\ascii.enc | text | |
MD5:9E3A454FA480E9A99D2D5ACDAA775233 | SHA256:FB87BF197F4F485B08EA81F7534BC07D9C3A538D022424BE11011A1FE3C413FD | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_tcl_data\encoding\cp1251.enc | text | |
MD5:83DAF47FD1F87B7B1E9E086F14C39E5B | SHA256:0AA66DFF8A7AE570FEE83A803F8F5391D9F0C9BD6311796592D9B6E8E36BE6FC | |||
| 2076 | Ask3lad Test Drive GUI v1.0.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_elementtree.pyd | executable | |
MD5:E31FD445C65AEC18C32A99828732264A | SHA256:02E30B6A2BEE5BE5336E40A9C89575603051BDE86F9C9CDC78B7FA7D9B7BD1F0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
640 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
640 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6672 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5504 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6672 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6672 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |