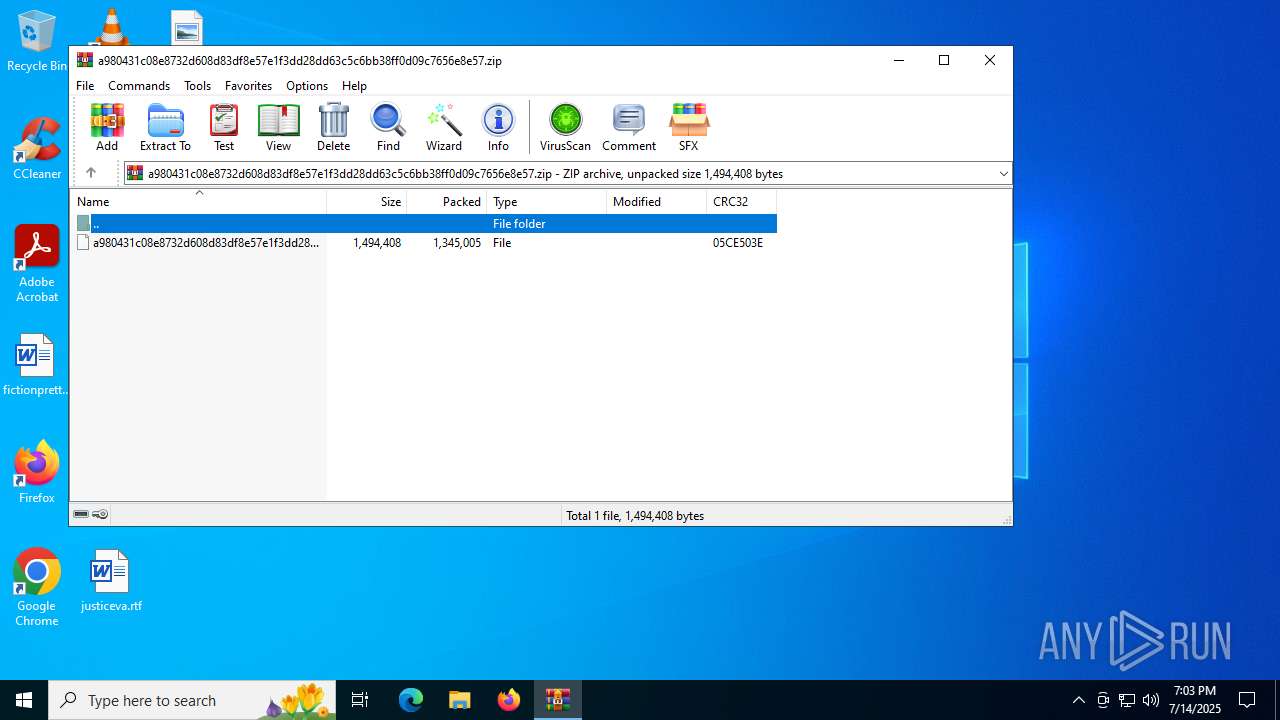
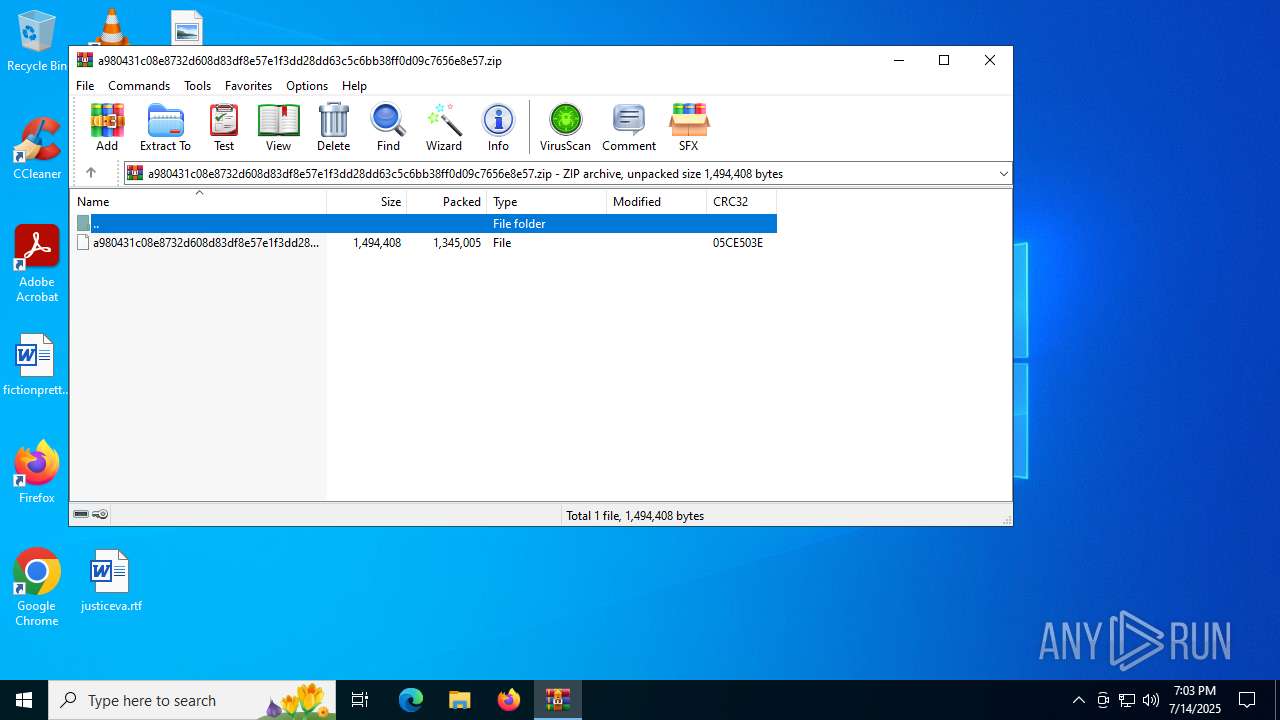
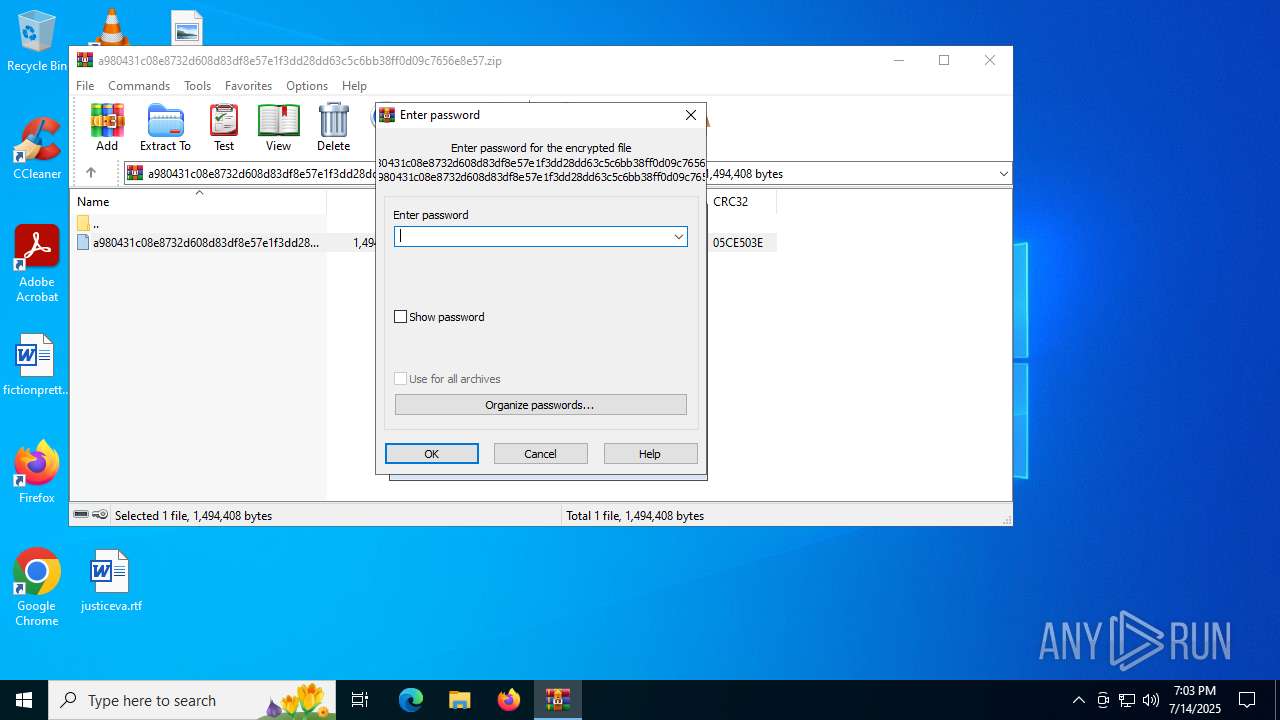
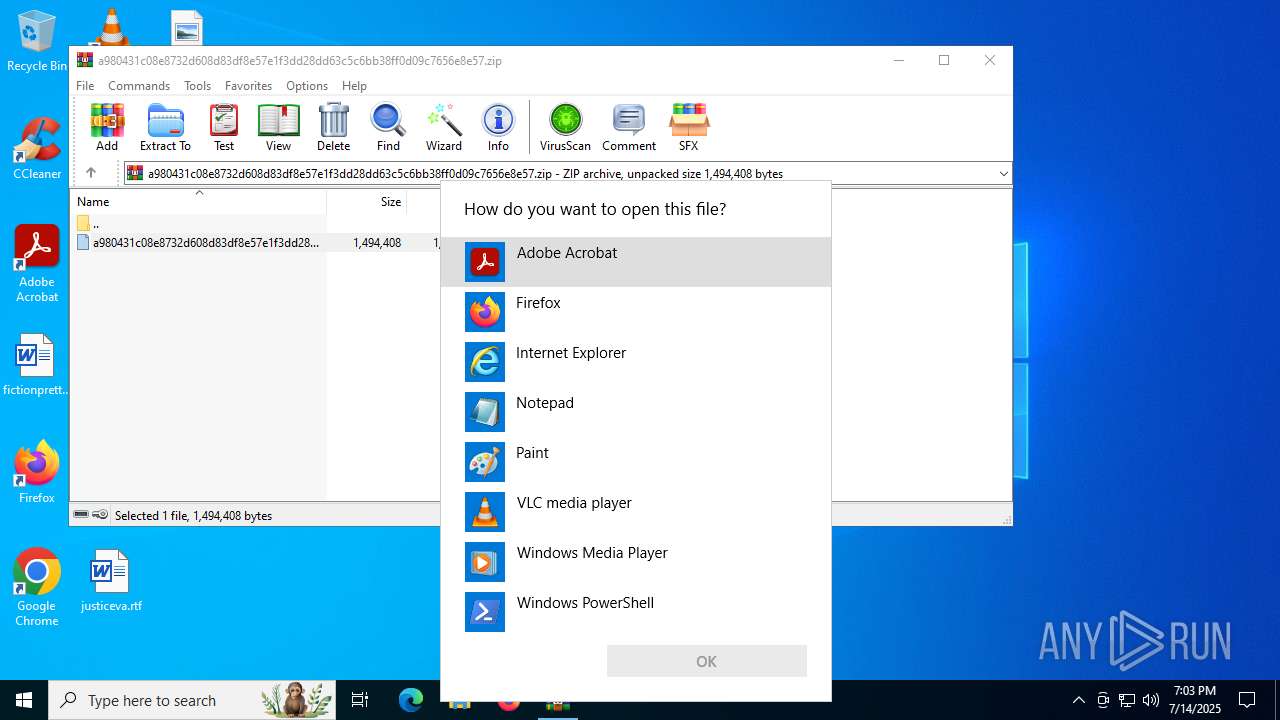
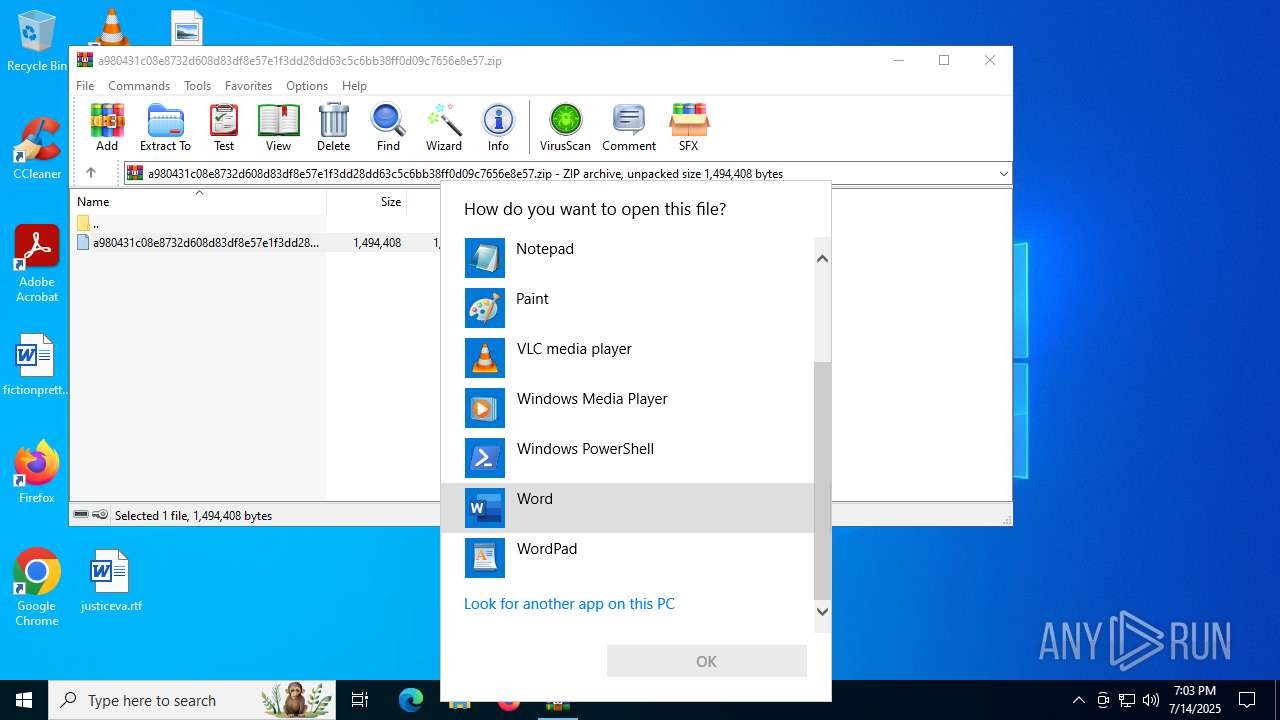
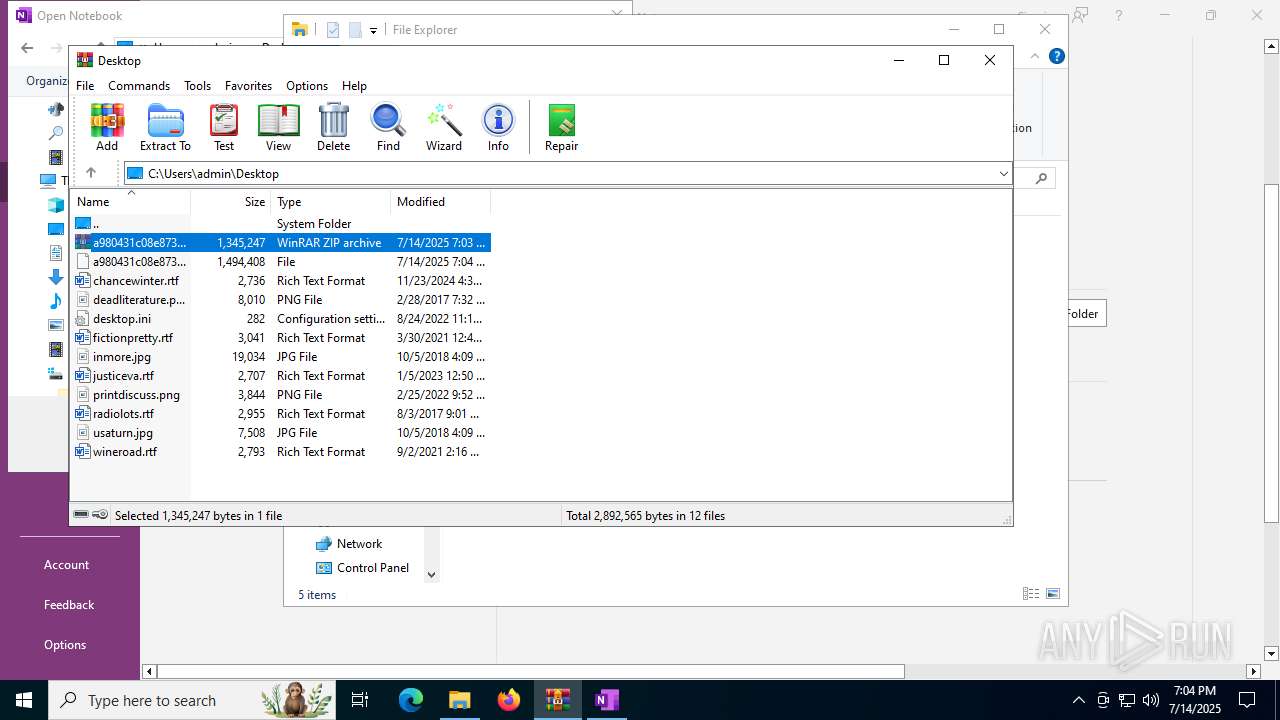
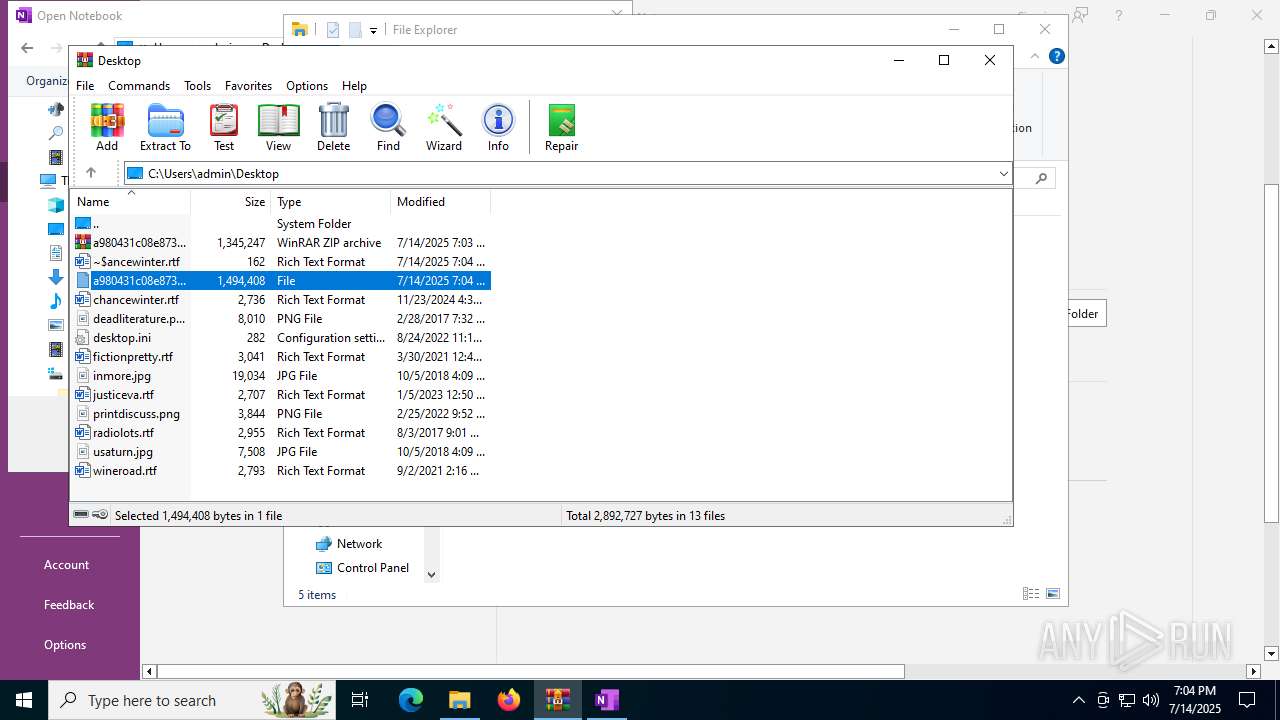
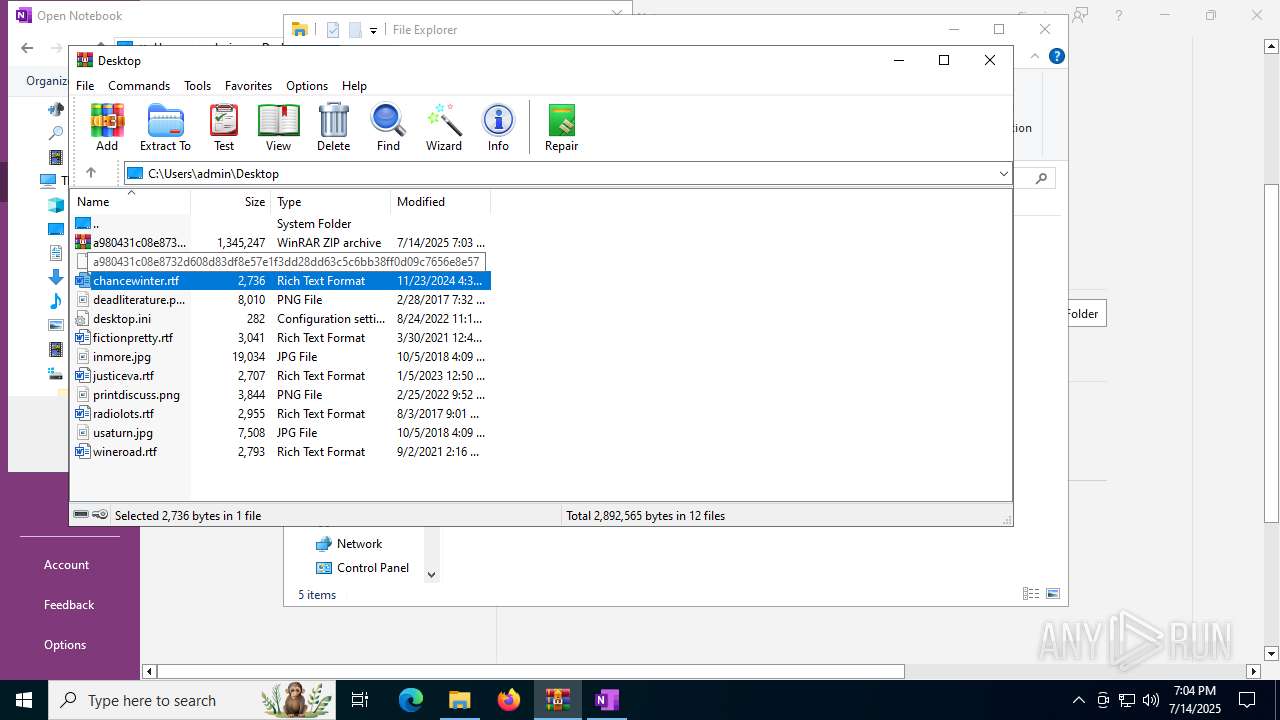
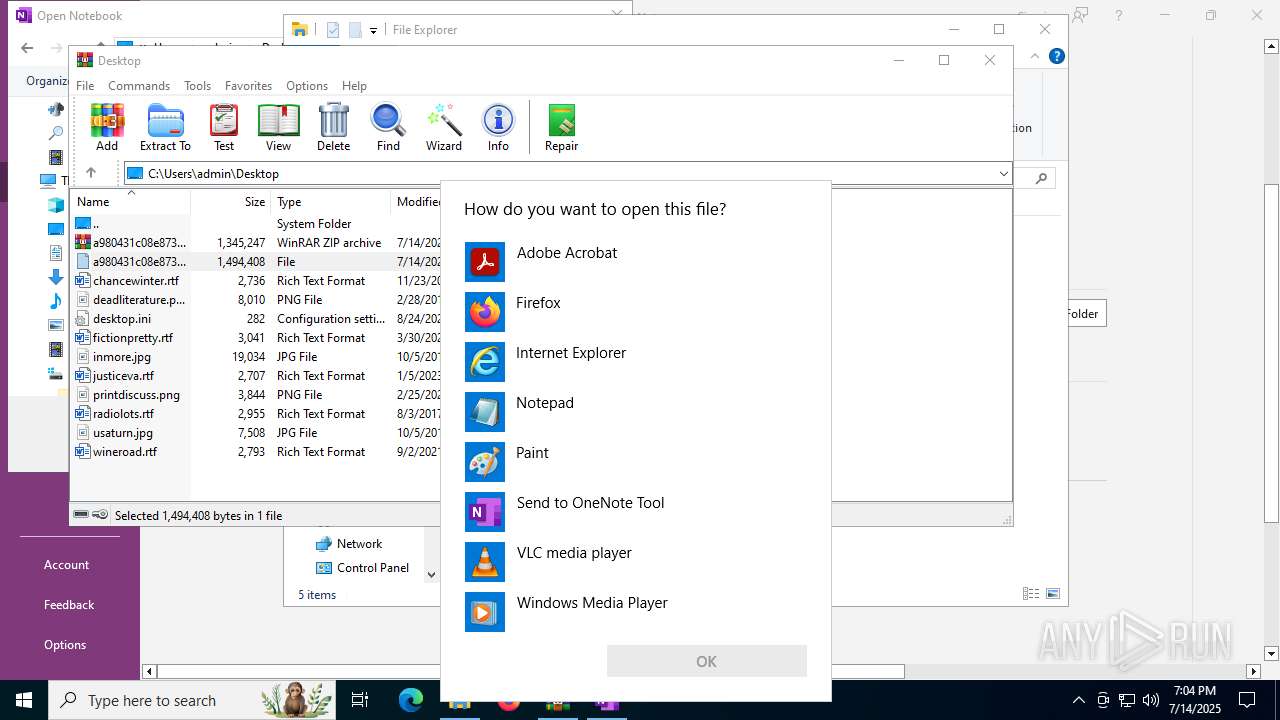
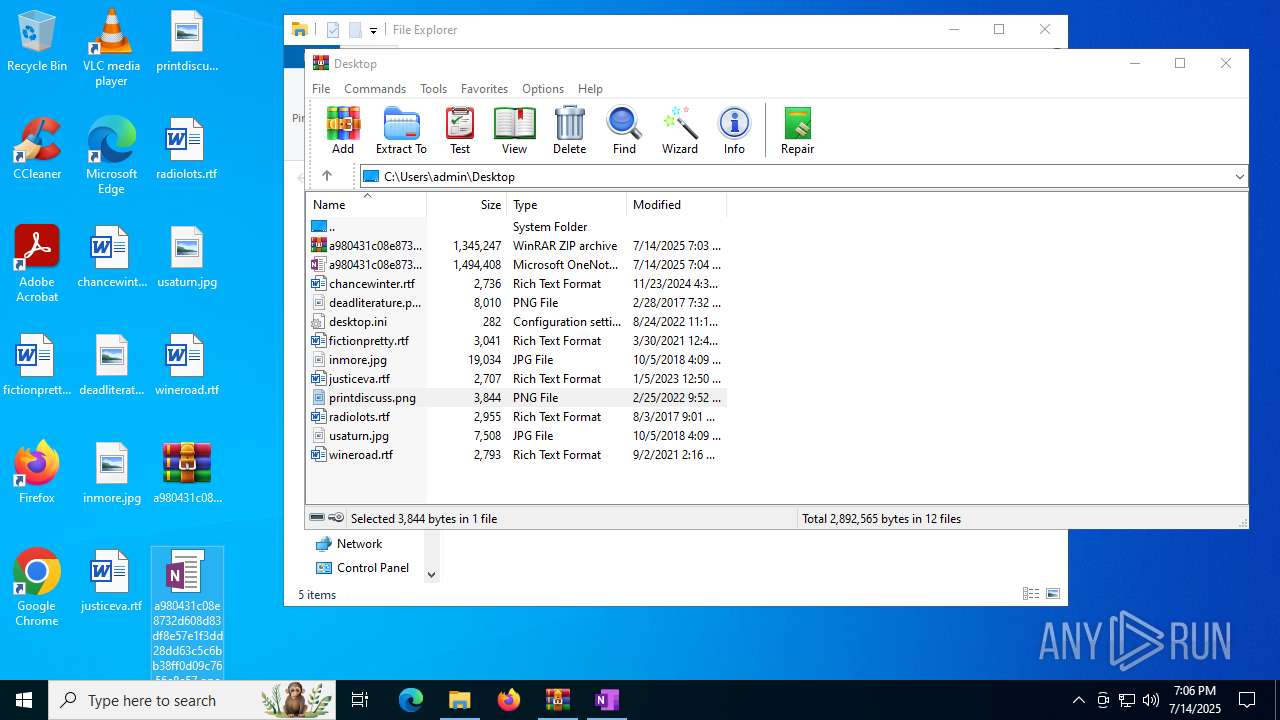
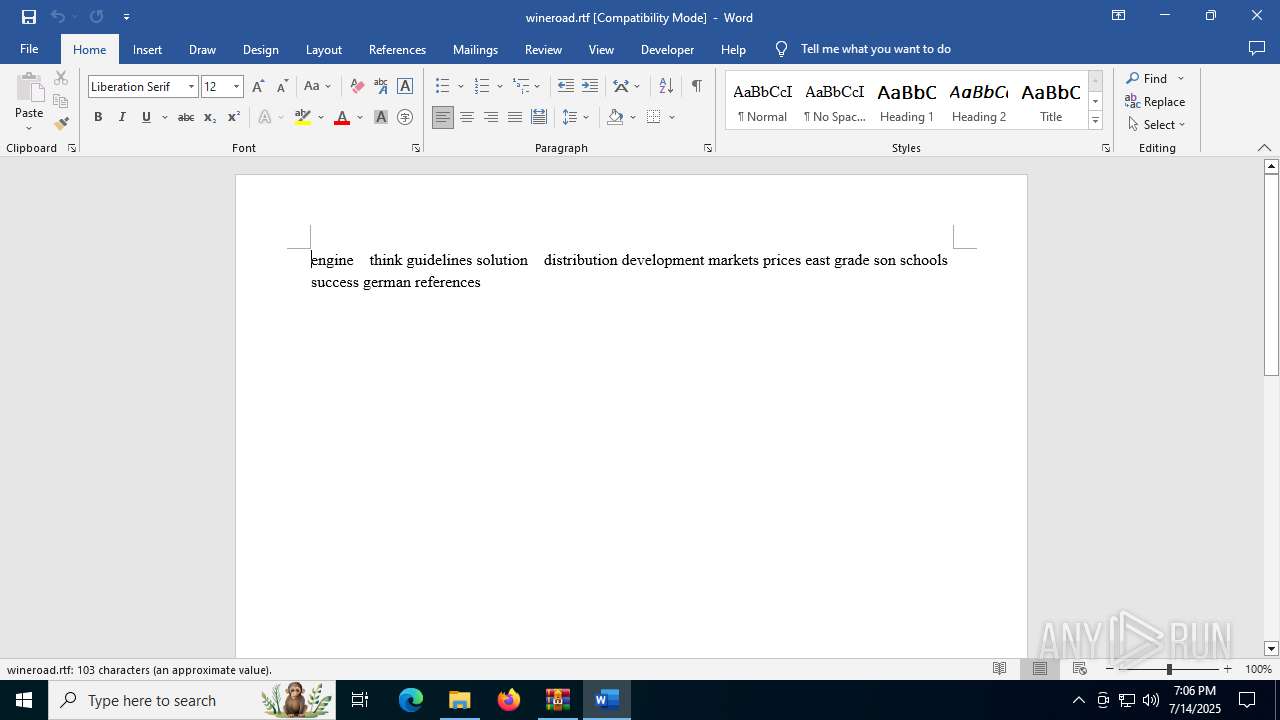
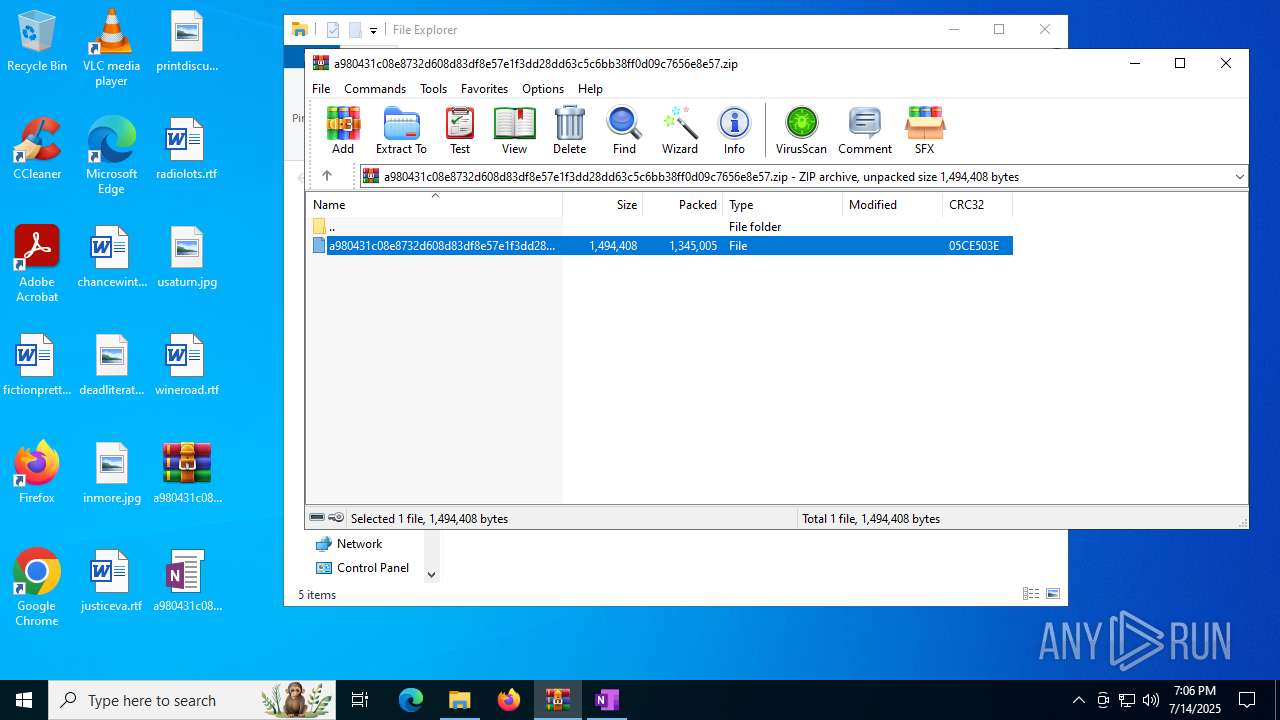
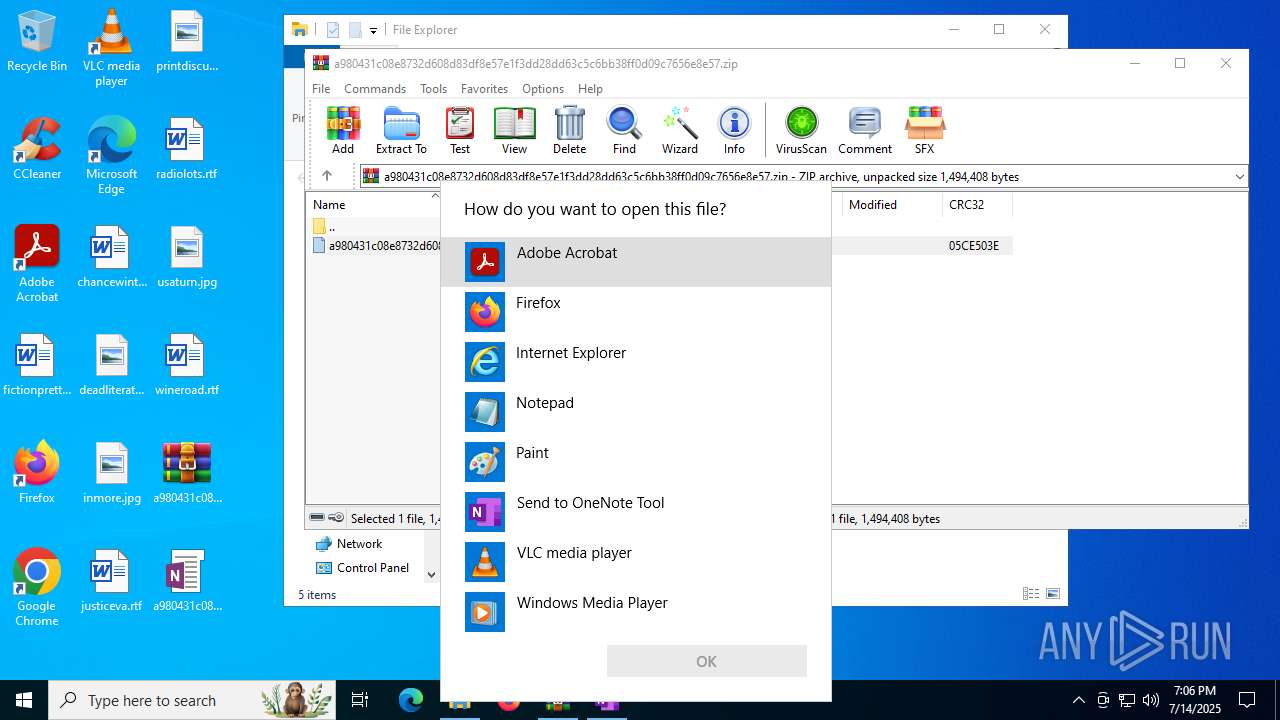
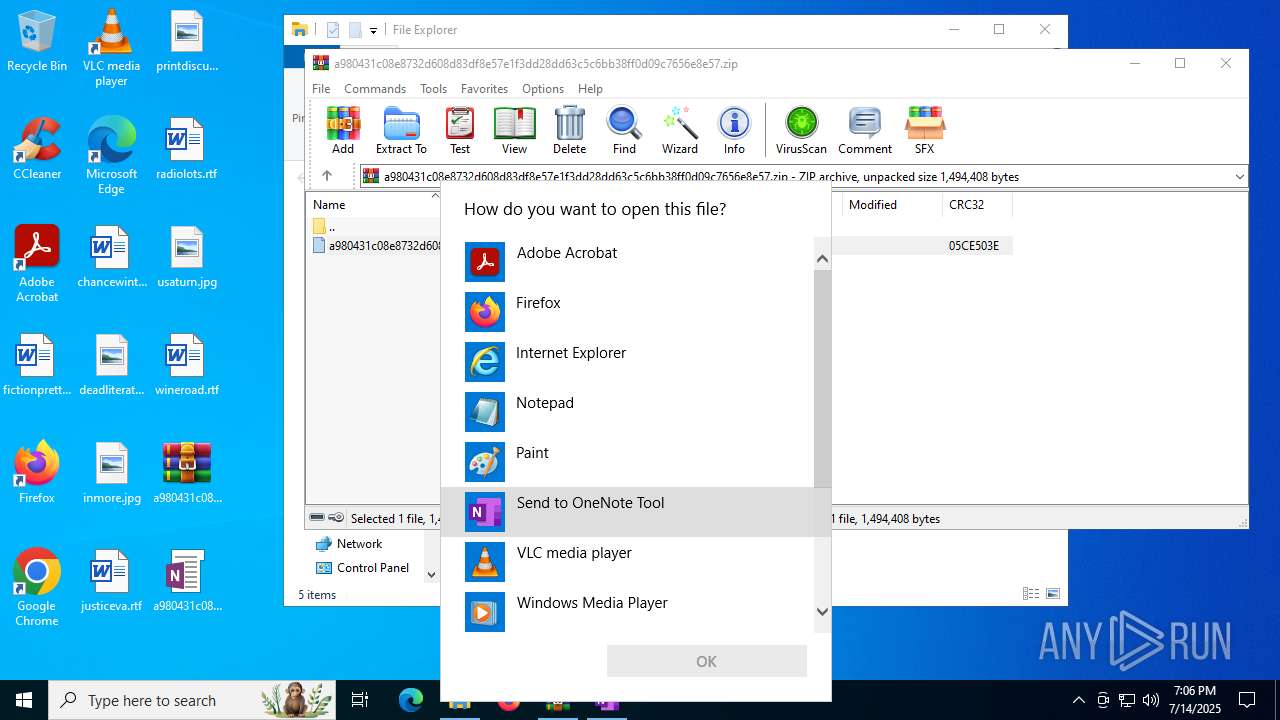
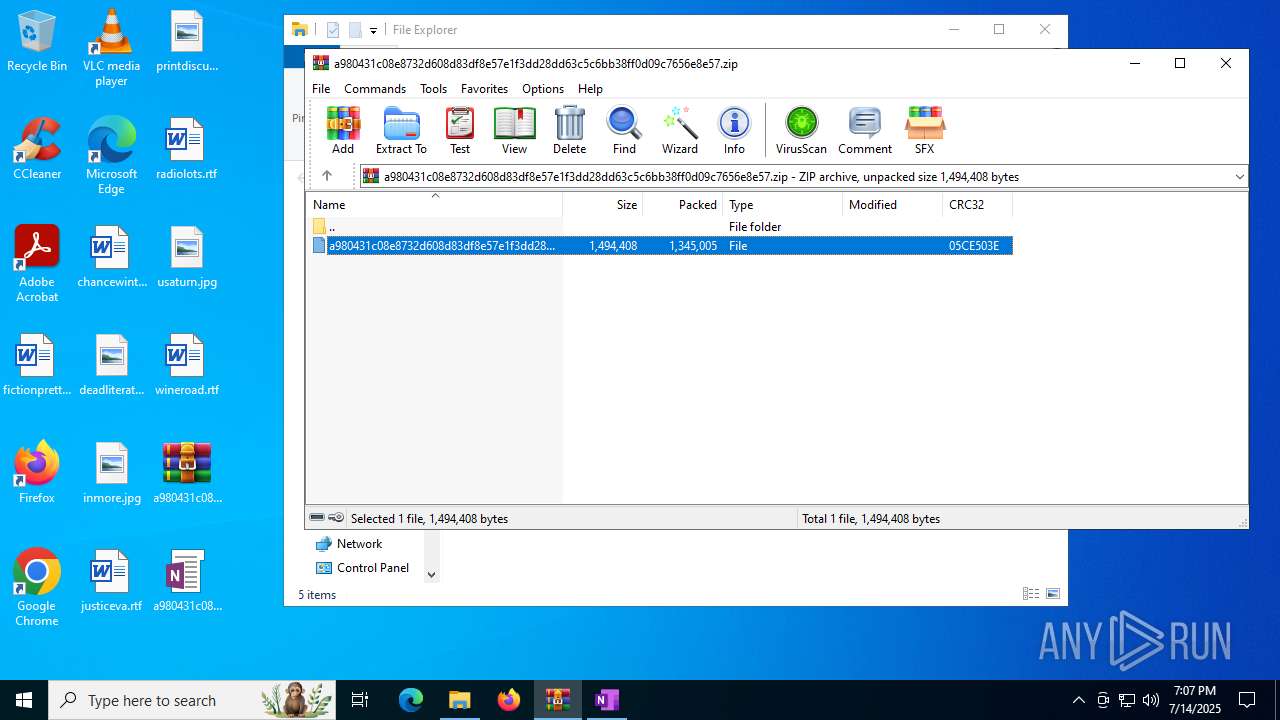
| File name: | a980431c08e8732d608d83df8e57e1f3dd28dd63c5c6bb38ff0d09c7656e8e57.zip |
| Full analysis: | https://app.any.run/tasks/0cf9dcb5-c048-409a-a865-9f4fac332800 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2025, 19:03:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 26F667C99E762A4BC952A586DA02651F |
| SHA1: | A1AC3140CF456D8B22A4810F2C09BD2E43EB91D2 |
| SHA256: | 4ECE6281C01823A92470BF642DE65D7D1252E858A3249B10948A3175D80EDD11 |
| SSDEEP: | 49152:HnmefhAZcsY/eDHpoId4ZZdRVEmBd2UA2ogedzhhz7WaipmlqXNLYzUlJry87UvI:HmqOZieDHpoIypfEmBcUztKqXpml0PAs |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 316)
Creates file in the systems drive root
- OpenWith.exe (PID: 6664)
- ONENOTE.EXE (PID: 2660)
- ONENOTE.EXE (PID: 3872)
Detected use of alternative data streams (AltDS)
- ONENOTE.EXE (PID: 2660)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 316)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 316)
INFO
Checks supported languages
- ONENOTEM.EXE (PID: 5876)
- ONENOTEM.EXE (PID: 1976)
- ONENOTEM.EXE (PID: 6748)
- MpCmdRun.exe (PID: 1028)
- ONENOTEM.EXE (PID: 5220)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6664)
- ONENOTEM.EXE (PID: 5876)
- WinRAR.exe (PID: 316)
- ONENOTEM.EXE (PID: 1976)
- OpenWith.exe (PID: 5236)
- ONENOTEM.EXE (PID: 6748)
- OpenWith.exe (PID: 5248)
- ONENOTEM.EXE (PID: 5220)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 6664)
- OpenWith.exe (PID: 5248)
Reads the computer name
- ONENOTEM.EXE (PID: 5876)
- ONENOTEM.EXE (PID: 1976)
- ONENOTEM.EXE (PID: 6748)
- ONENOTEM.EXE (PID: 5220)
- MpCmdRun.exe (PID: 1028)
Manual execution by a user
- ONENOTE.EXE (PID: 2660)
- ONENOTE.EXE (PID: 6460)
Checks proxy server information
- slui.exe (PID: 4800)
Reads the software policy settings
- slui.exe (PID: 4800)
Create files in a temporary directory
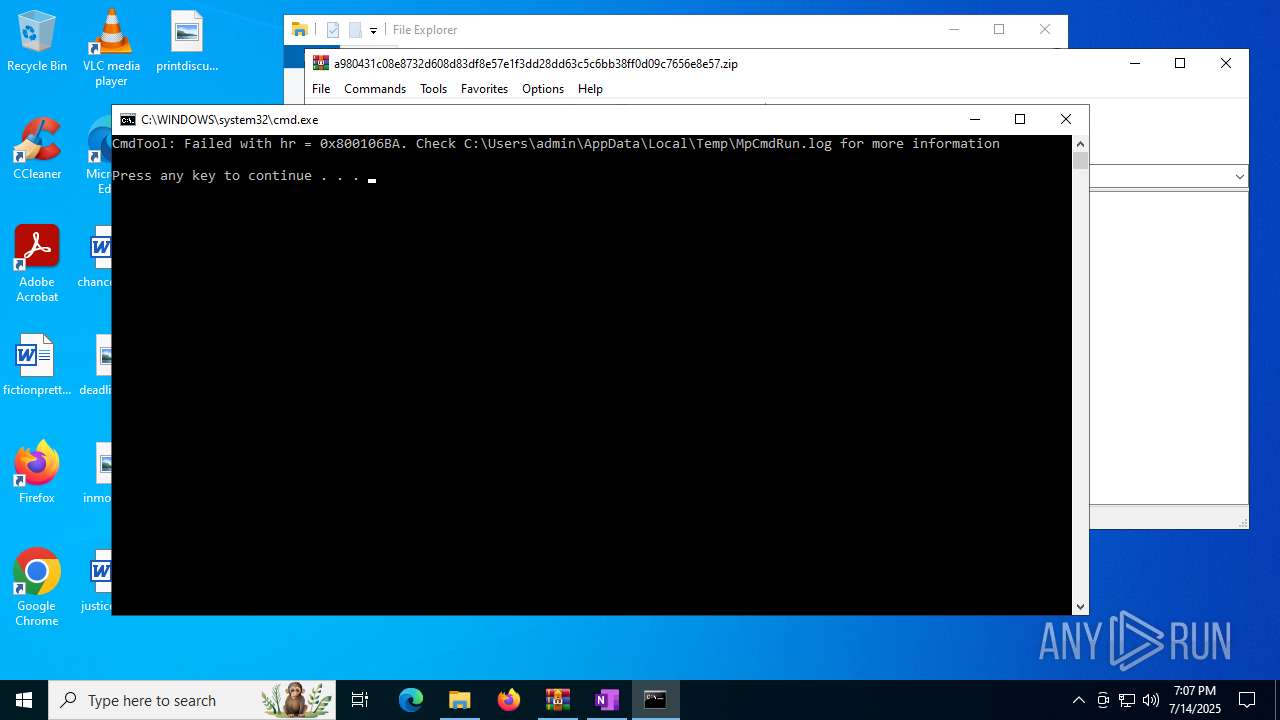
- MpCmdRun.exe (PID: 1028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
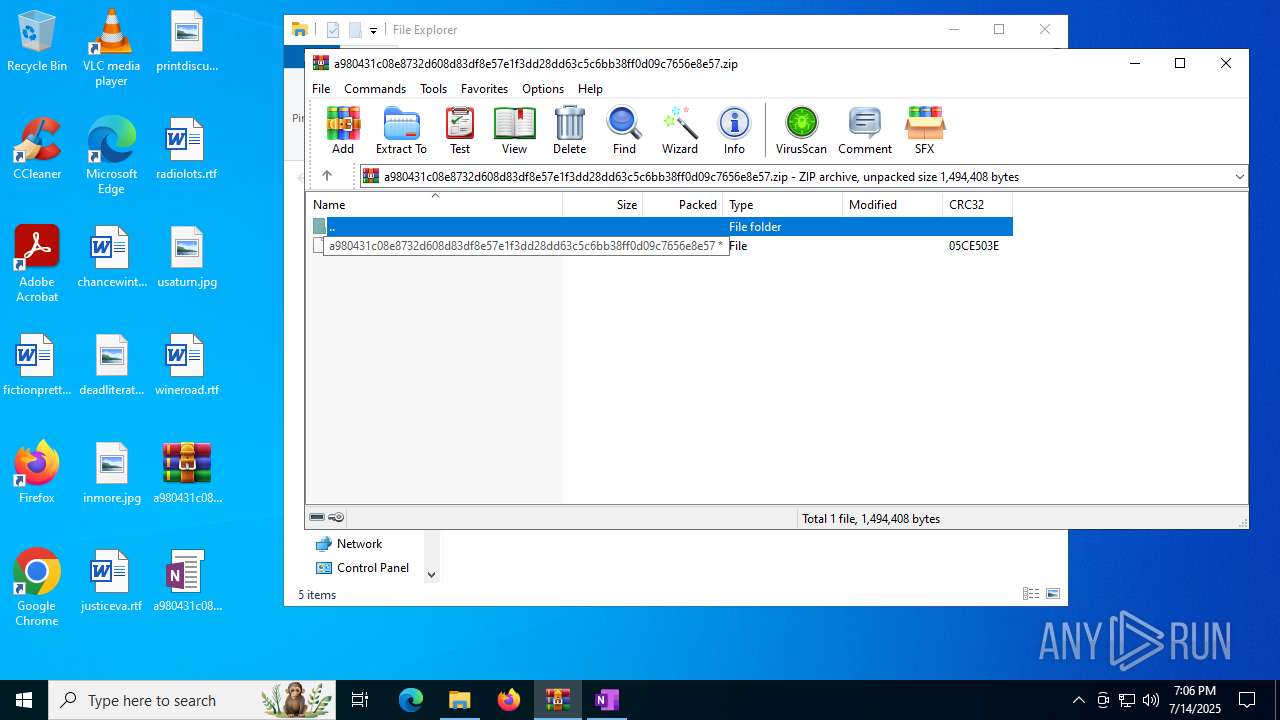
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x05ce503e |
| ZipCompressedSize: | 1345005 |
| ZipUncompressedSize: | 1494408 |
| ZipFileName: | a980431c08e8732d608d83df8e57e1f3dd28dd63c5c6bb38ff0d09c7656e8e57 |
Total processes
183
Monitored processes
27
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
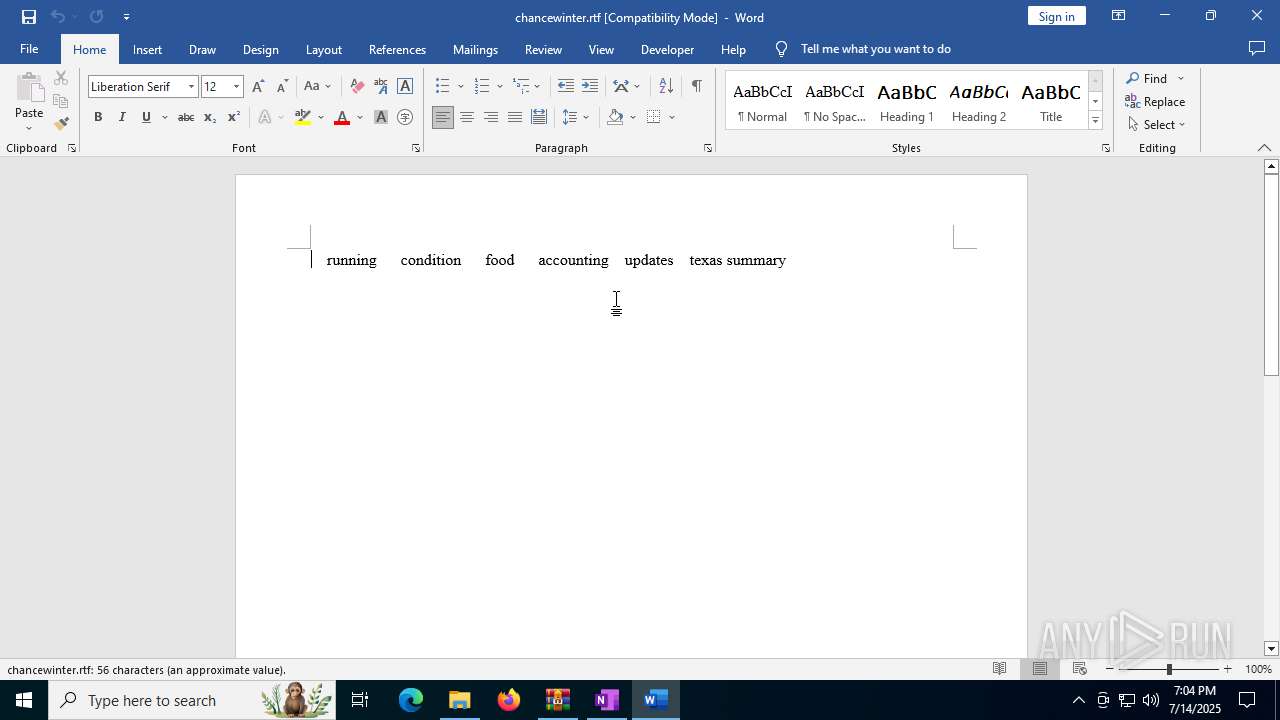
| 304 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\chancewinter.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 316 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\a980431c08e8732d608d83df8e57e1f3dd28dd63c5c6bb38ff0d09c7656e8e57.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
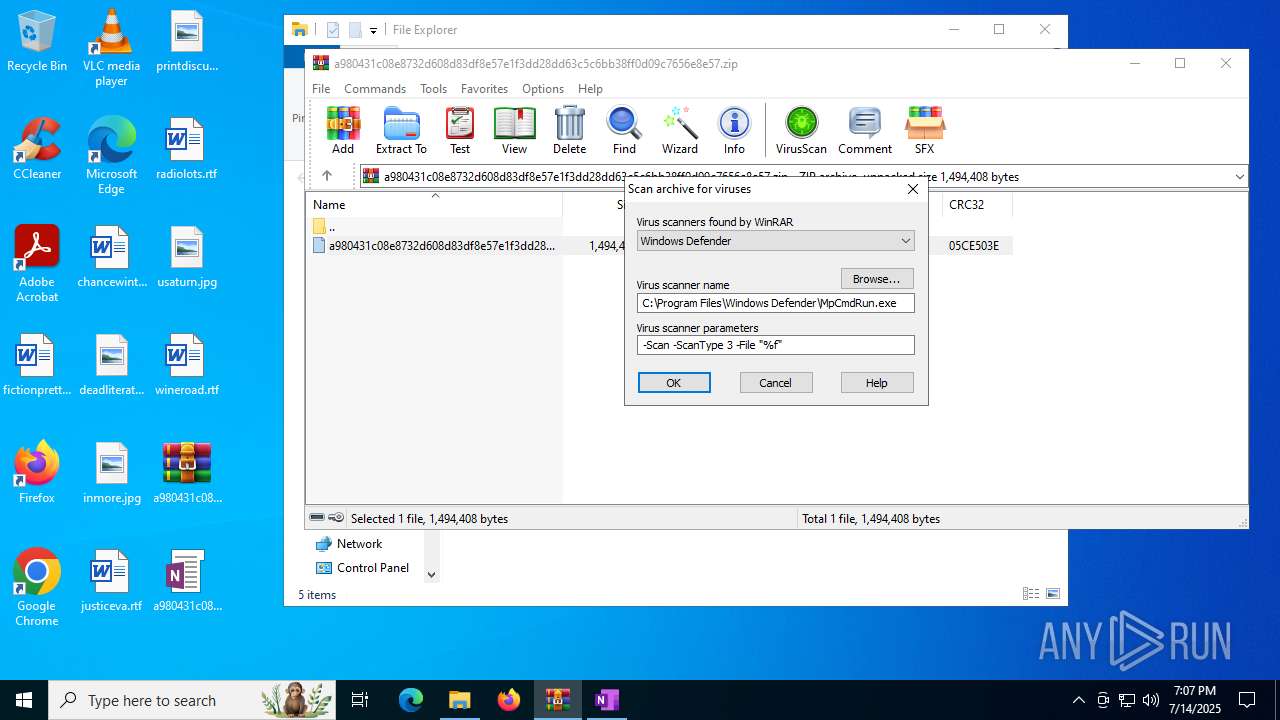
| 1028 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR316.36905" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1508 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "56FA5D8B-FB72-4B91-827A-91A3E30DB2BB" "413D6F7E-21F7-47E7-A212-7B10871D0FEB" "4052" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 1948 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "ED59113E-7F48-4E2D-ACEB-700C068609C3" "D305B1B2-89D7-4719-8832-614382730EAF" "4808" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 1976 | /tsr | C:\Program Files\Microsoft Office\root\Office16\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Send to OneNote Tool Exit code: 1 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "CF6B806F-6132-4945-994A-1FE95A6787AA" "B0F92F0F-E07B-43C1-873B-C9745634B448" "304" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 2660 | "C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE" | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\radiolots.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3160 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "4578DF62-38FA-4961-AC15-984FDDA07446" "3A55C6DA-EC22-4016-A25E-93706B99431A" "4080" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
83 140
Read events
80 796
Write events
2 070
Delete events
274
Modification events
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\a980431c08e8732d608d83df8e57e1f3dd28dd63c5c6bb38ff0d09c7656e8e57.zip | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
61
Text files
203
Unknown types
53
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\cdn.odc.officeapps.live.com\7124A45C-465C-46B0-959A-E3FAFAA091F7 | image | |
MD5:7EFC92CE7851A17F24516EA8172177AA | SHA256:859A9EF5BBCDB1C10719EDF50E25BB7D8185452D10E9DDE5C26791C9A92BE1AE | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:CBB785C72E549C2FAADDD546FC030751 | SHA256:36ED75611D3E1FFC03066227D6442E4BD234DB499BA1B3FC2300B04987A49F9F | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:2C59CB0C0DE314D52D07AF5B22D9F3A9 | SHA256:FD007A23AD9AF28586A5CD7E6C70DC062DC599AFCF696AEC93B3632572B27A1A | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\cdn.odc.officeapps.live.com\7BABA0D2-7EBB-4FE7-9A78-FE200B4B8999 | image | |
MD5:1A530E055C19348A93B87DCE52D2FECE | SHA256:443D0A49C819DFAFEB634BAE1AB824A271D7A8988C9ABC0245184246F1570ED6 | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | der | |
MD5:8AD723A6AF3BD07AAEA1D80DD33033B2 | SHA256:F9DDC71663DE7938757EA5CEA836338B2066064001A5F71BAB9ABD9410173D6C | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\0B7EAC2C-E9B7-4C4C-A51E-023C34CCFC94 | xml | |
MD5:A23233FB3BCDC7F912A51FE76D2B5BF2 | SHA256:EB9466EECF0A2B0EC57CE710865CD0CF139874A4BB71ED2D74001B31C71D2A8F | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:7BA26B7532949D2FECC731F30B51F96B | SHA256:2CB873C02801634A207E56645ACDBD9CBBA8EA77D54B74A9D9C0265F1FCC65C1 | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\cdn.odc.officeapps.live.com\9549343C-DF56-4D29-BA89-FB38DC5819A6 | image | |
MD5:1A530E055C19348A93B87DCE52D2FECE | SHA256:443D0A49C819DFAFEB634BAE1AB824A271D7A8988C9ABC0245184246F1570ED6 | |||
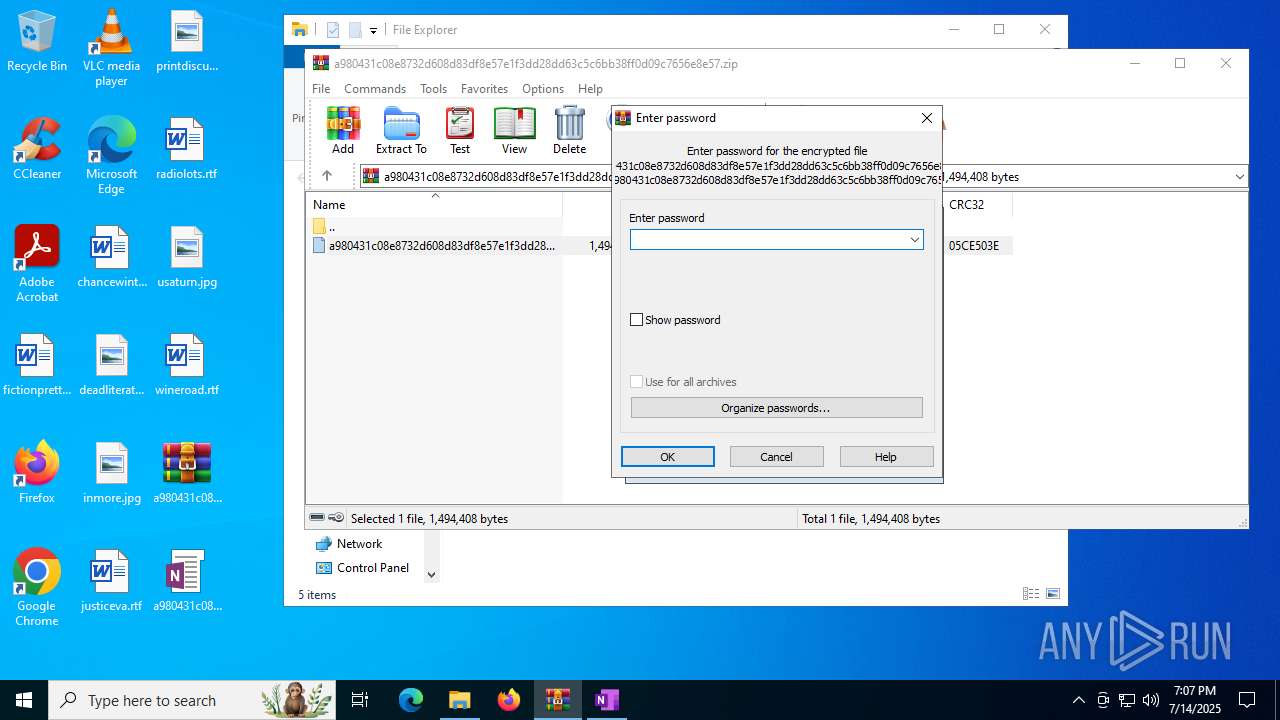
| 316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb316.11896\a980431c08e8732d608d83df8e57e1f3dd28dd63c5c6bb38ff0d09c7656e8e57 | one | |
MD5:E21F953C94729C5A705F2E48F676374B | SHA256:A980431C08E8732D608D83DF8E57E1F3DD28DD63C5C6BB38FF0D09C7656E8E57 | |||
| 2660 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\cdn.odc.officeapps.live.com\817B39B6-79EF-4BC4-A739-C4117C7C6620 | image | |
MD5:1A530E055C19348A93B87DCE52D2FECE | SHA256:443D0A49C819DFAFEB634BAE1AB824A271D7A8988C9ABC0245184246F1570ED6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
106
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4580 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2660 | ONENOTE.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2660 | ONENOTE.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6936 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5328 | SearchApp.exe | 92.123.104.41:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5328 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|