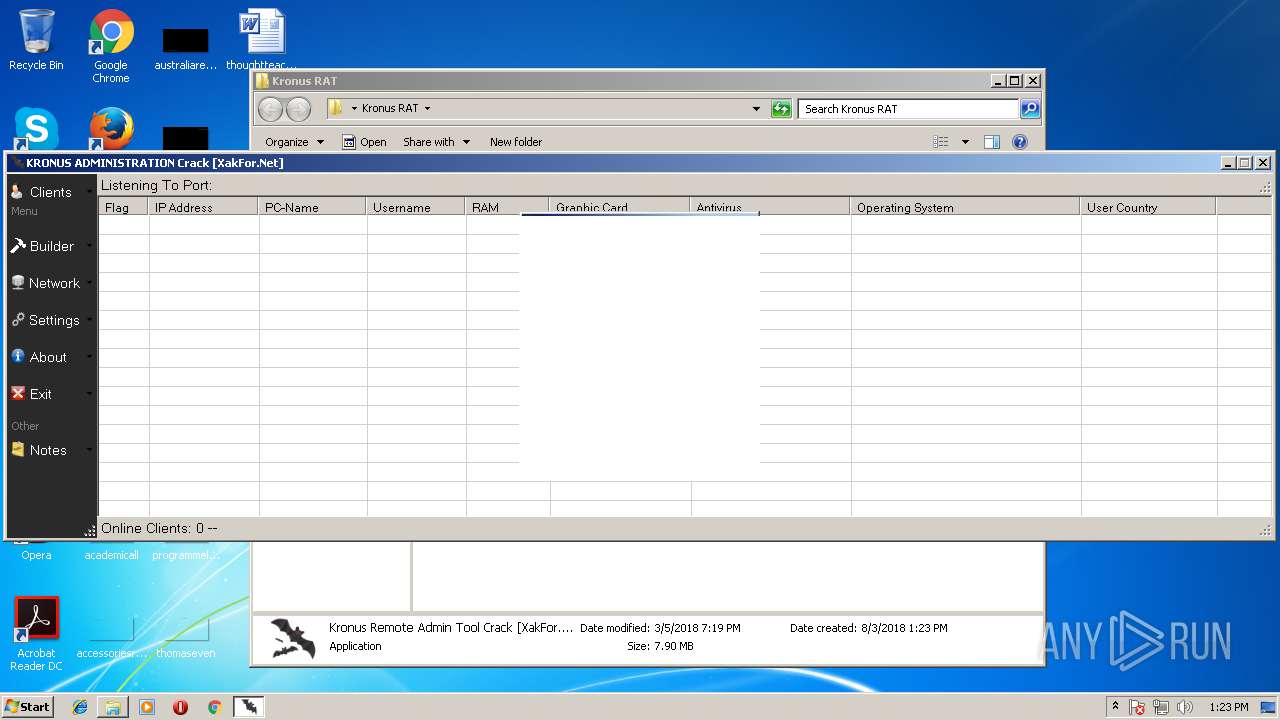
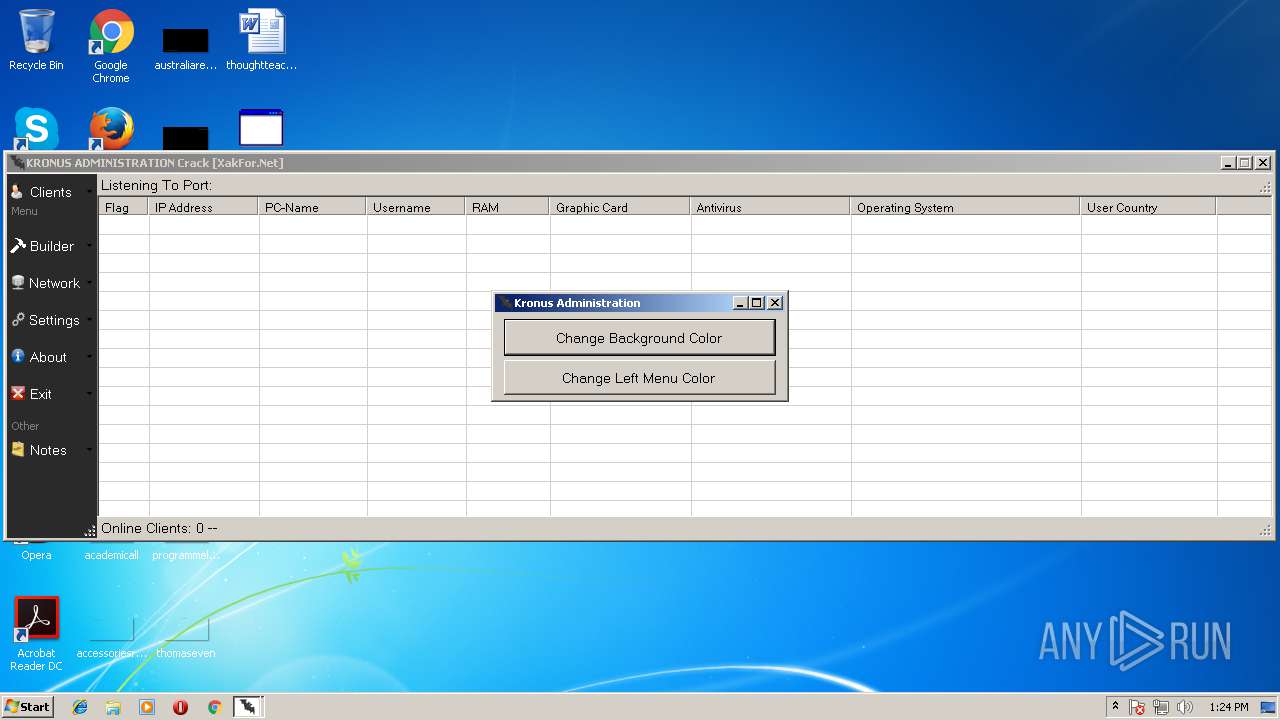
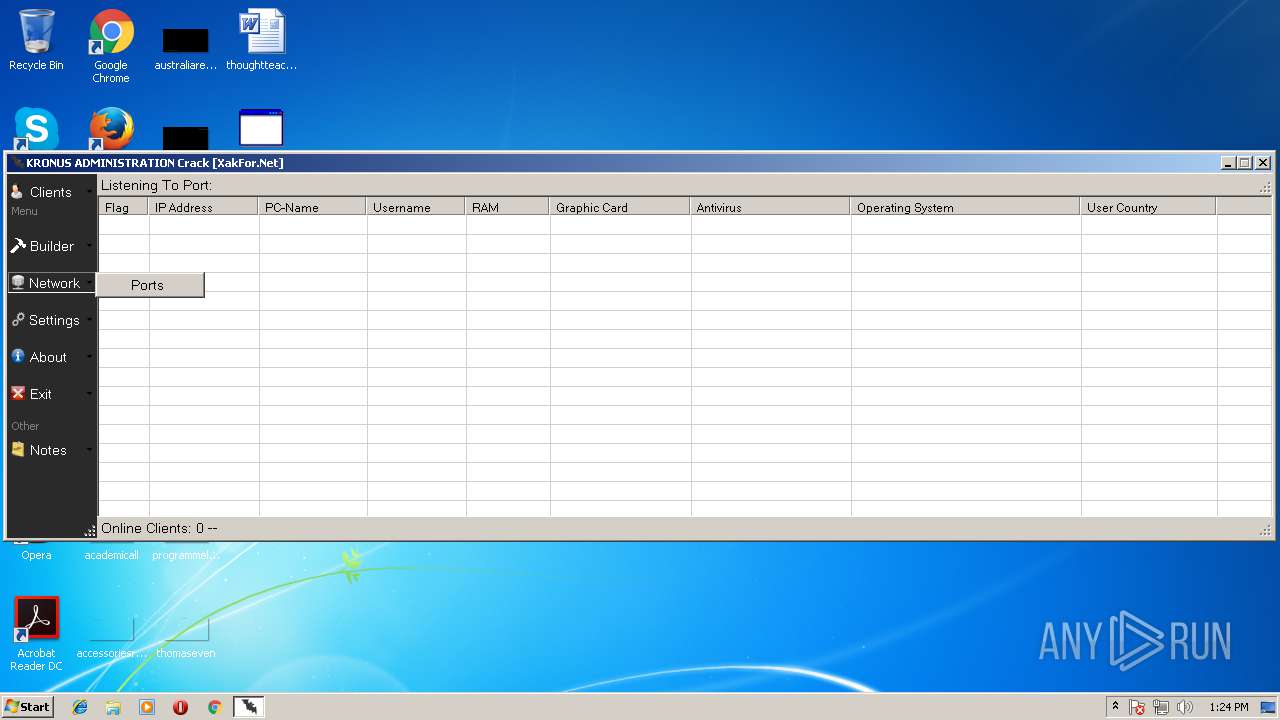
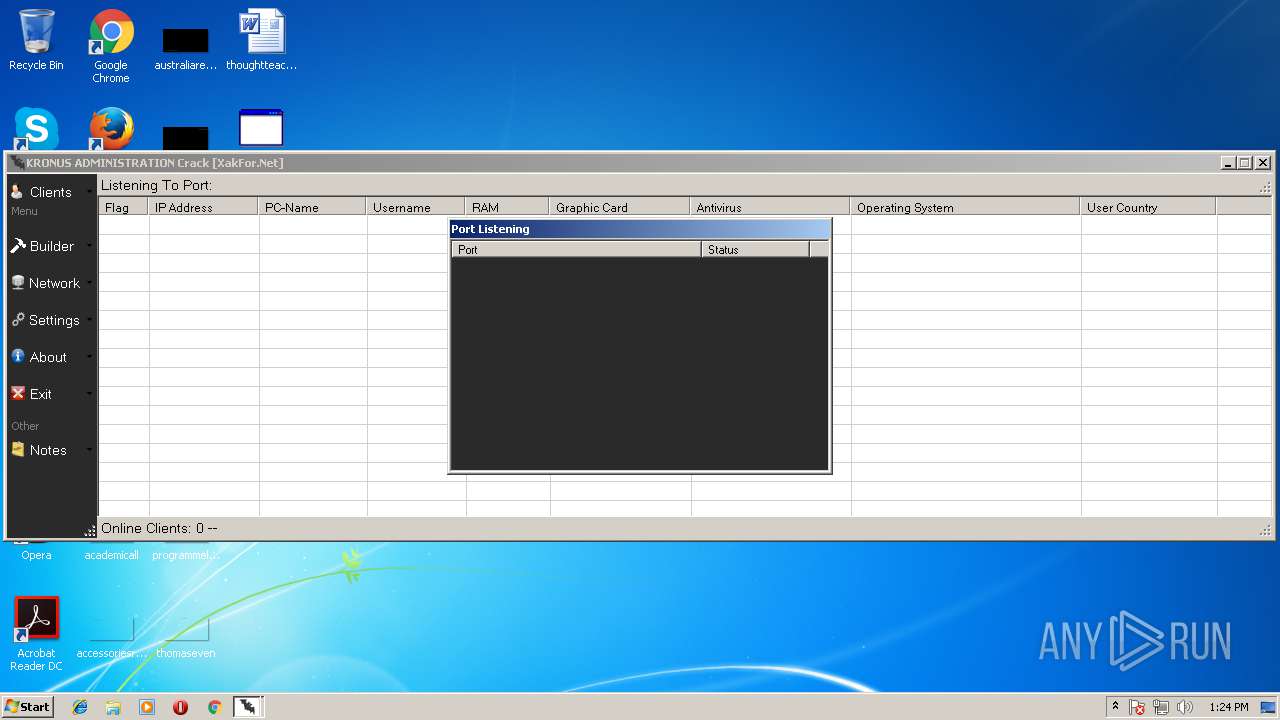
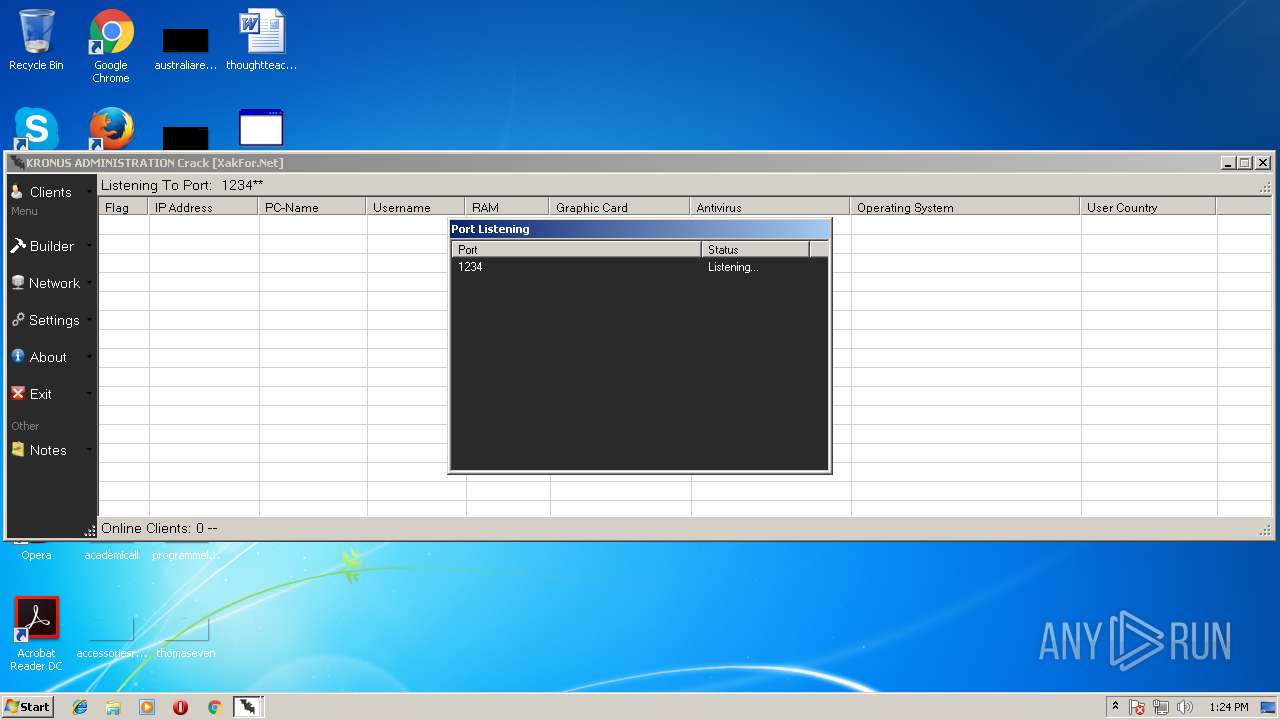
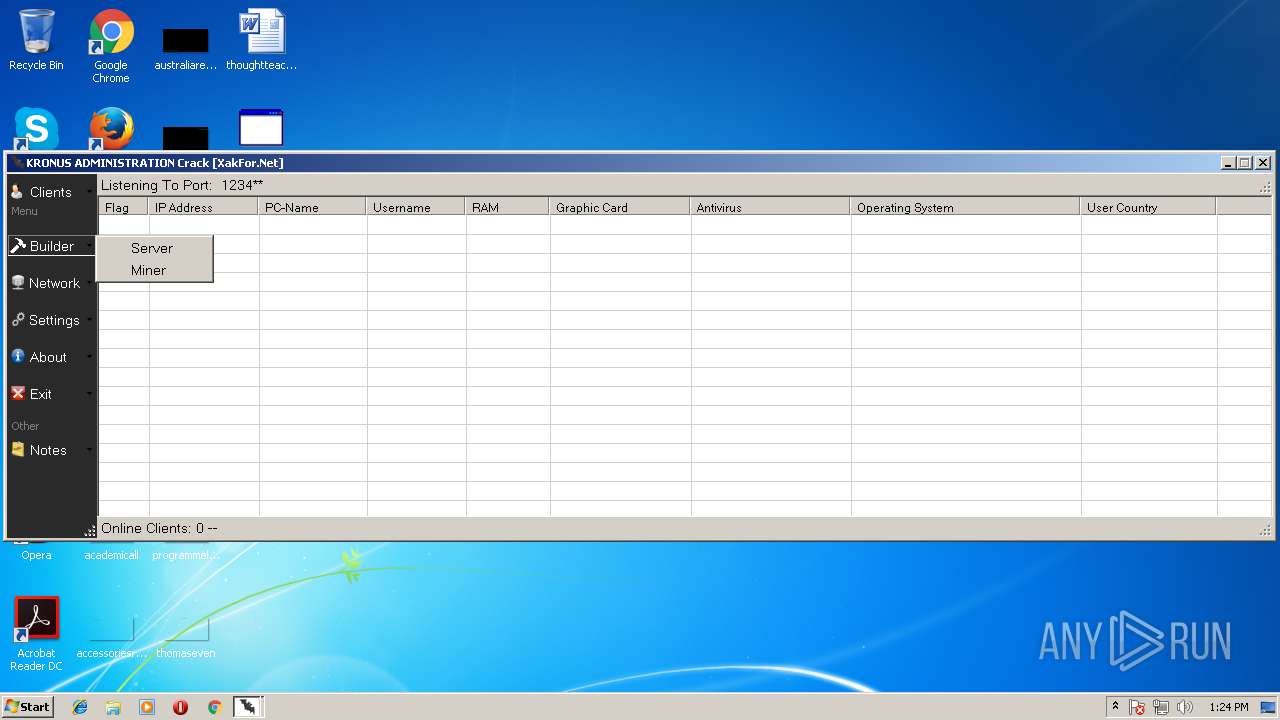
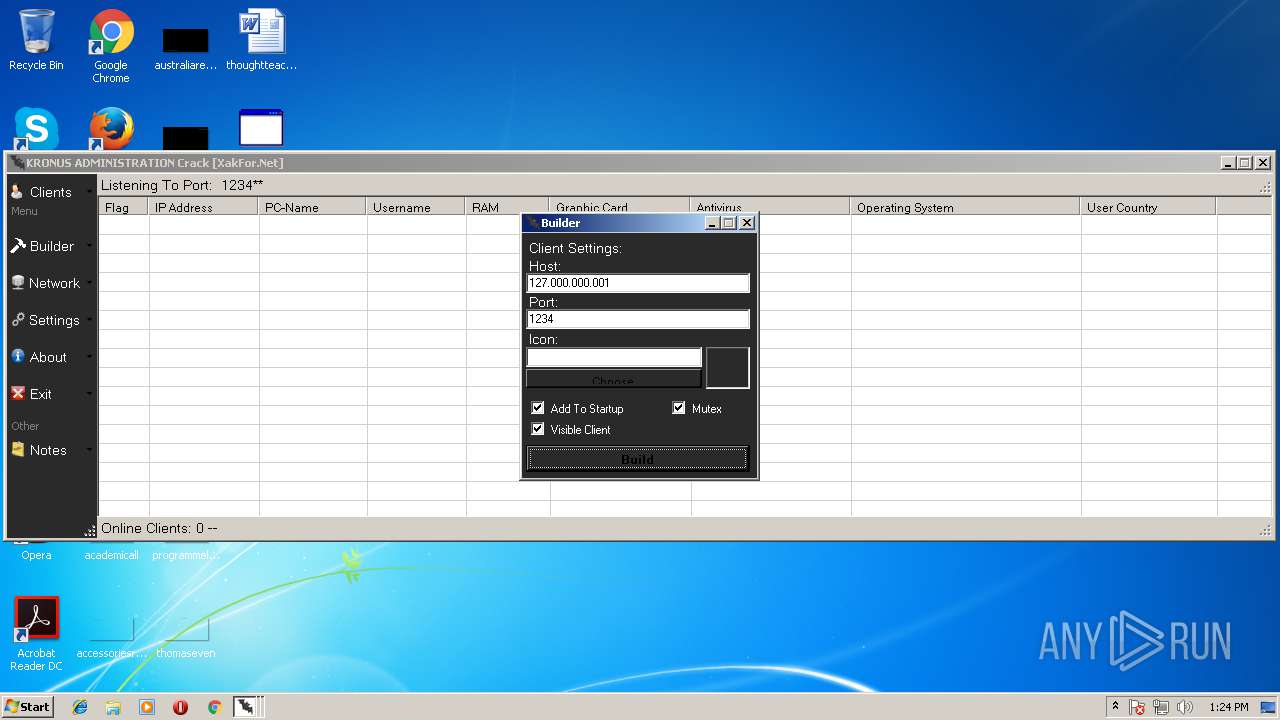
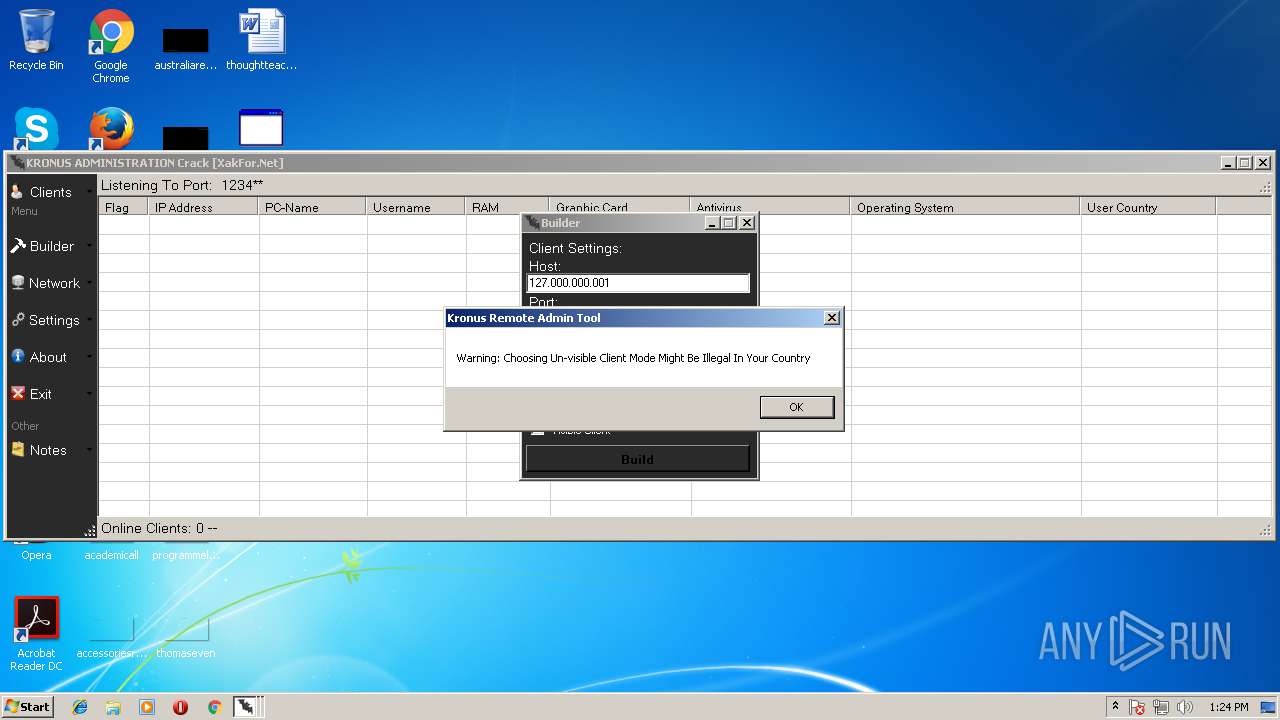
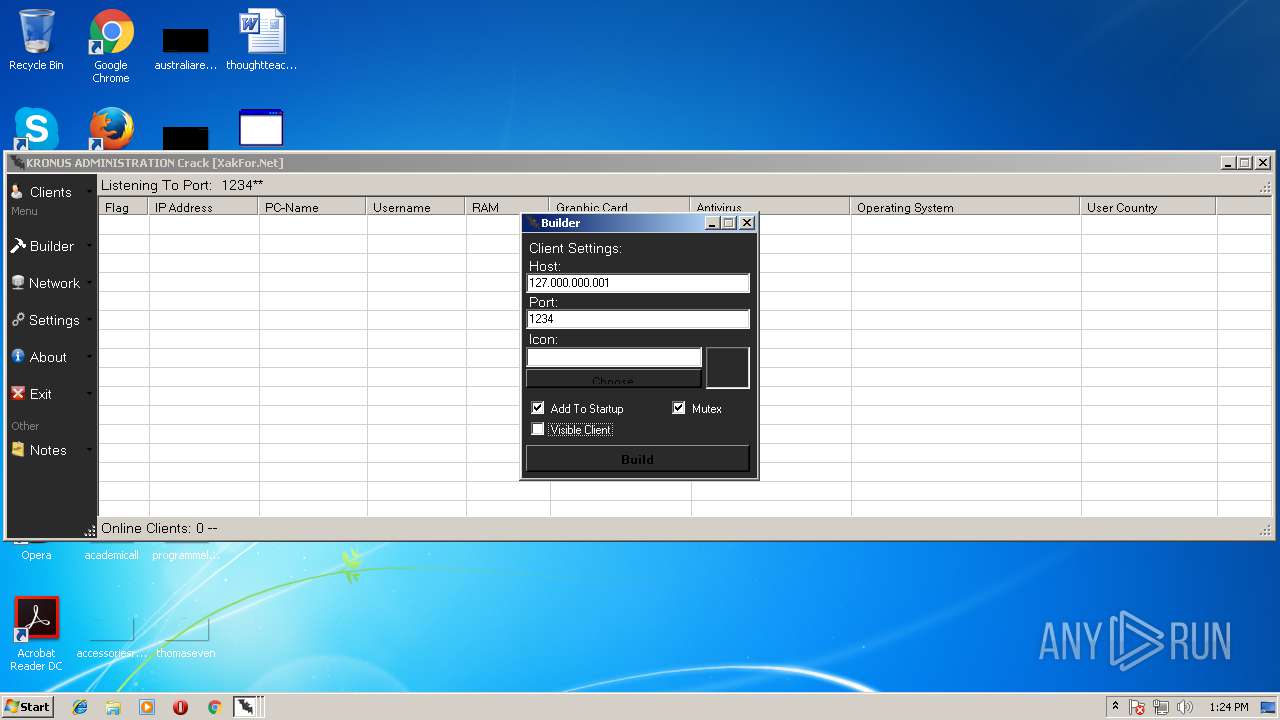
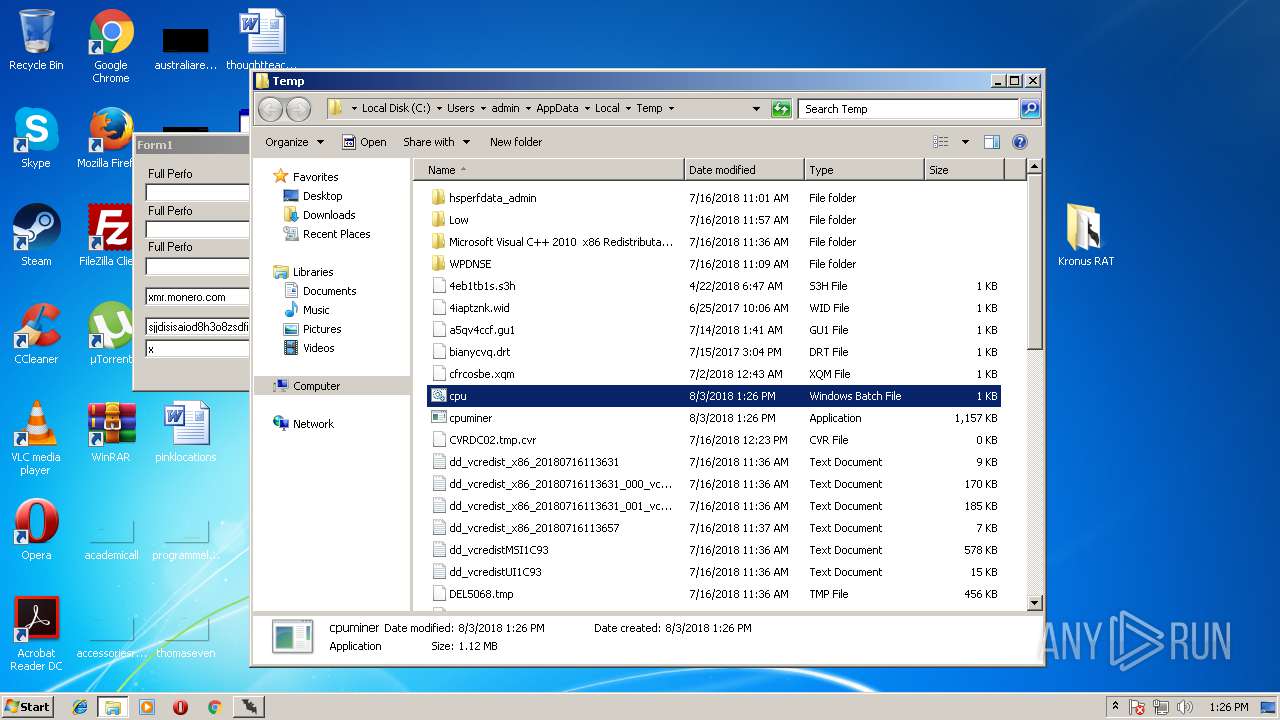
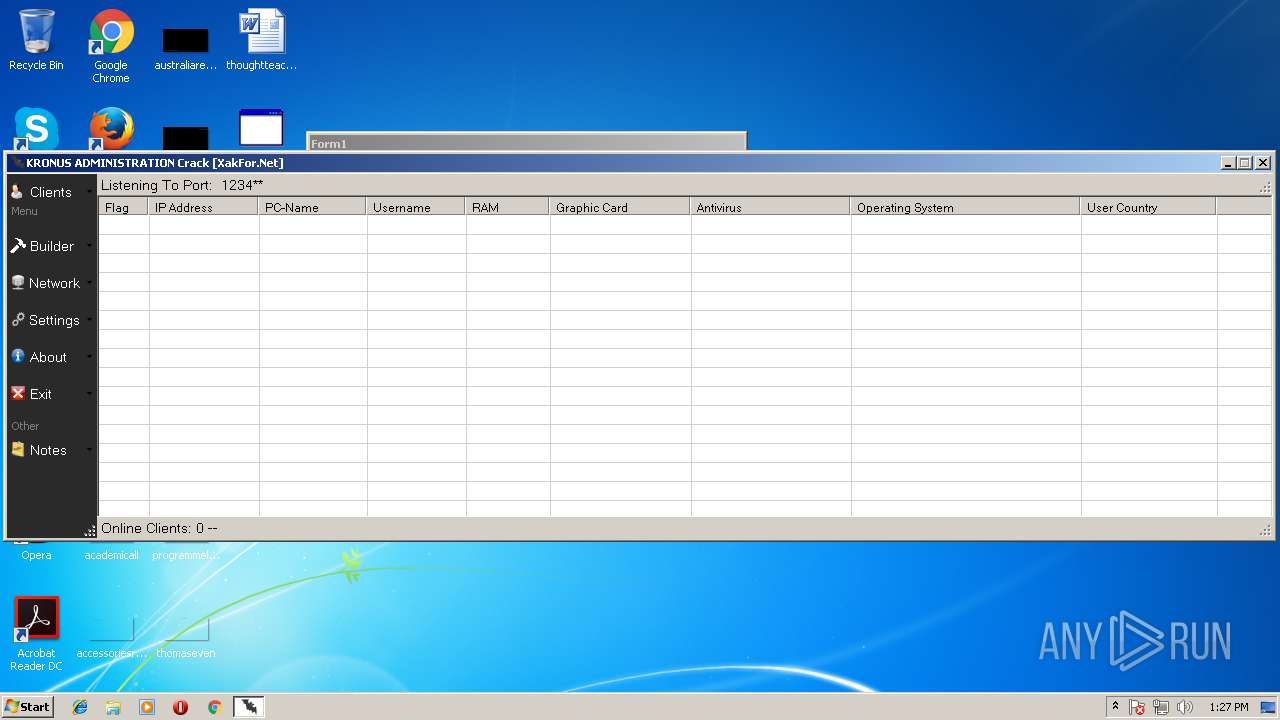
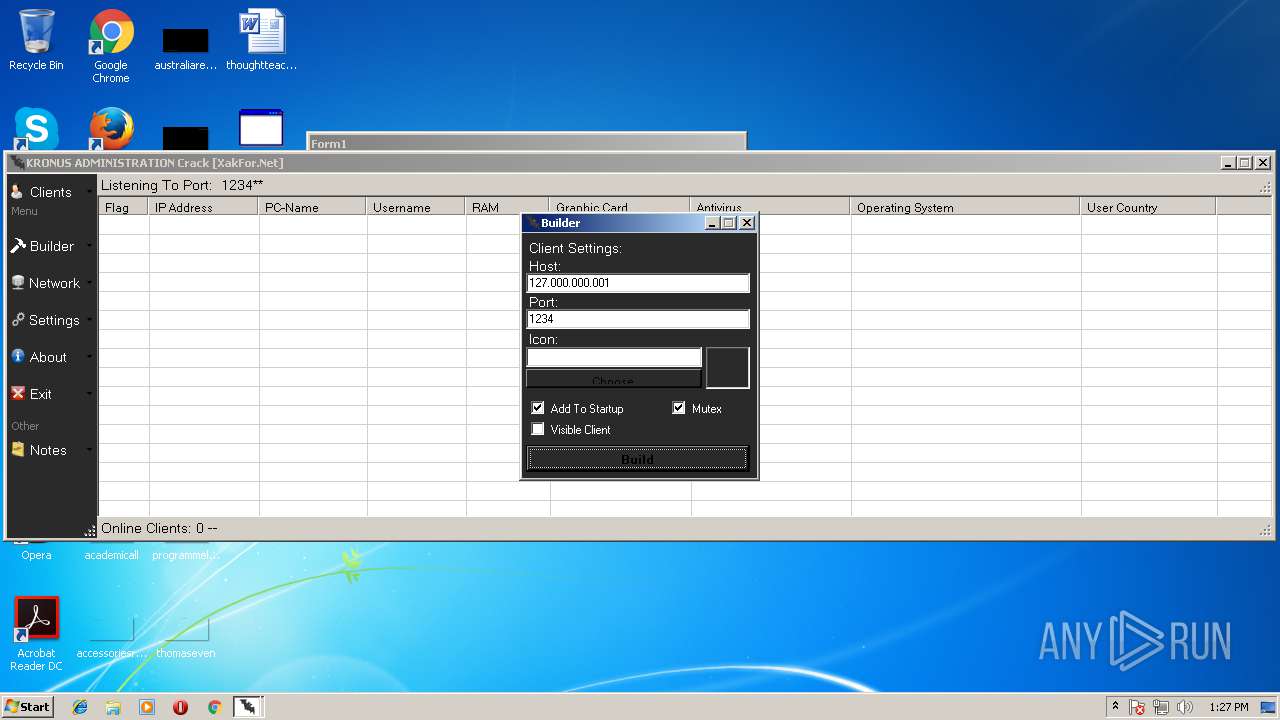
| File name: | Kronus RAT By Kronus Team.rar |
| Full analysis: | https://app.any.run/tasks/427f196e-e51f-4647-9c83-27af3bf6f1c0 |
| Verdict: | Malicious activity |
| Analysis date: | August 03, 2018, 12:22:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F1FDFE74EA6270D1C20F8363FCFC70D6 |
| SHA1: | A60D29955E5B4A23EE0BD79F29870F43D09638AB |
| SHA256: | 4EB82AE0FD11370EDF3FA8E933DA06E7F9AC1C9E5031ADB61B70737CBB3564A5 |
| SSDEEP: | 49152:yzxUF7IPbjnNqtqkD1aAeQqto6J0KNm+BlQz3jY1OlPgqWUVFnwM2:yzmITxRkJaA+jJ0KNm+LlclYKFnwd |
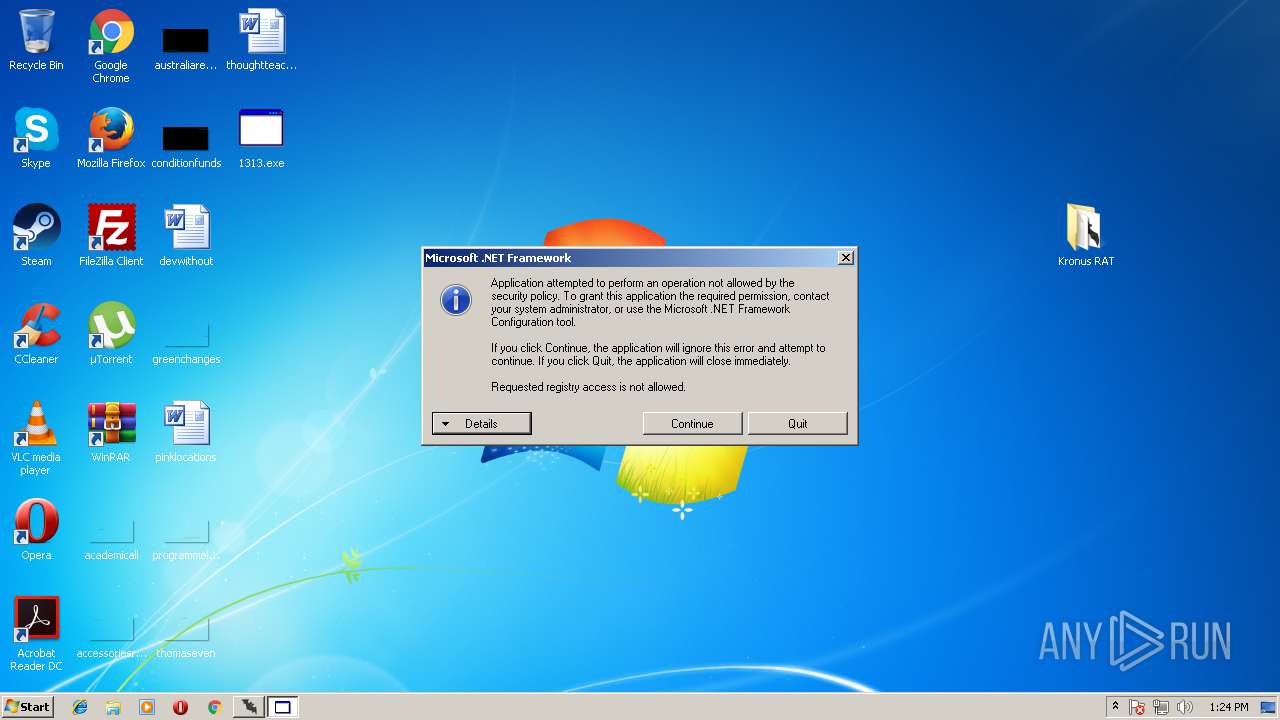
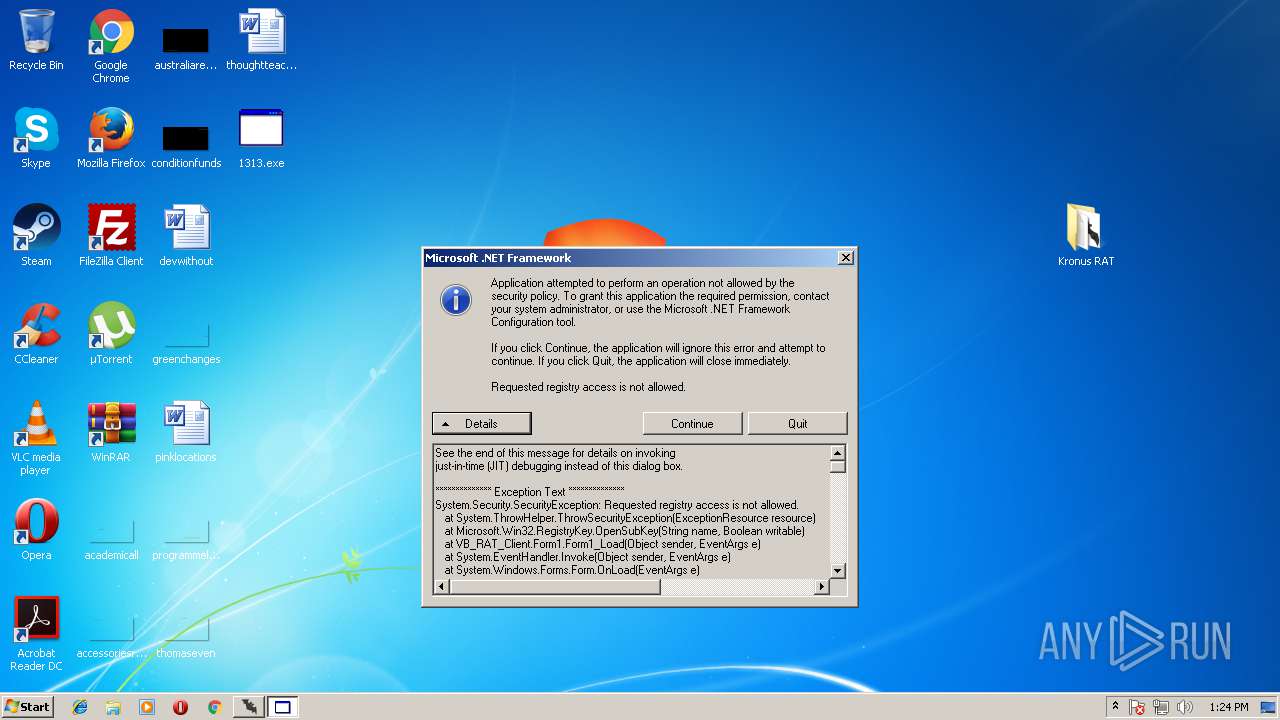
MALICIOUS
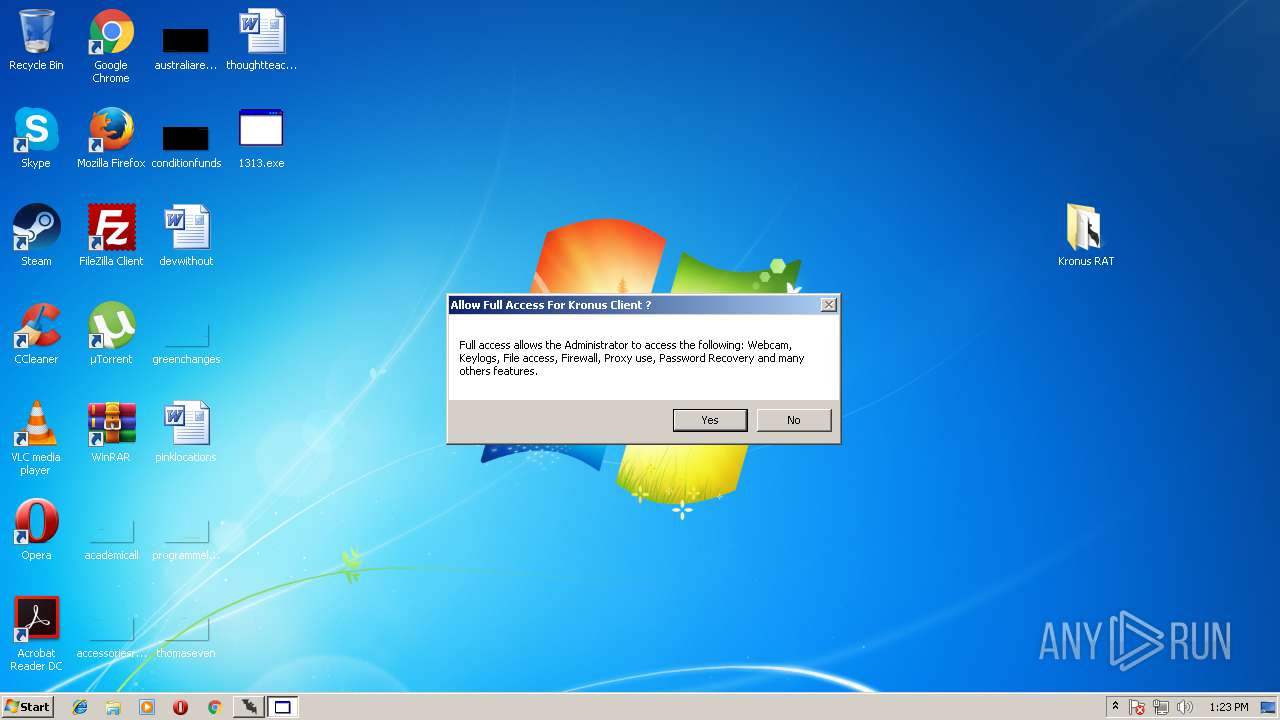
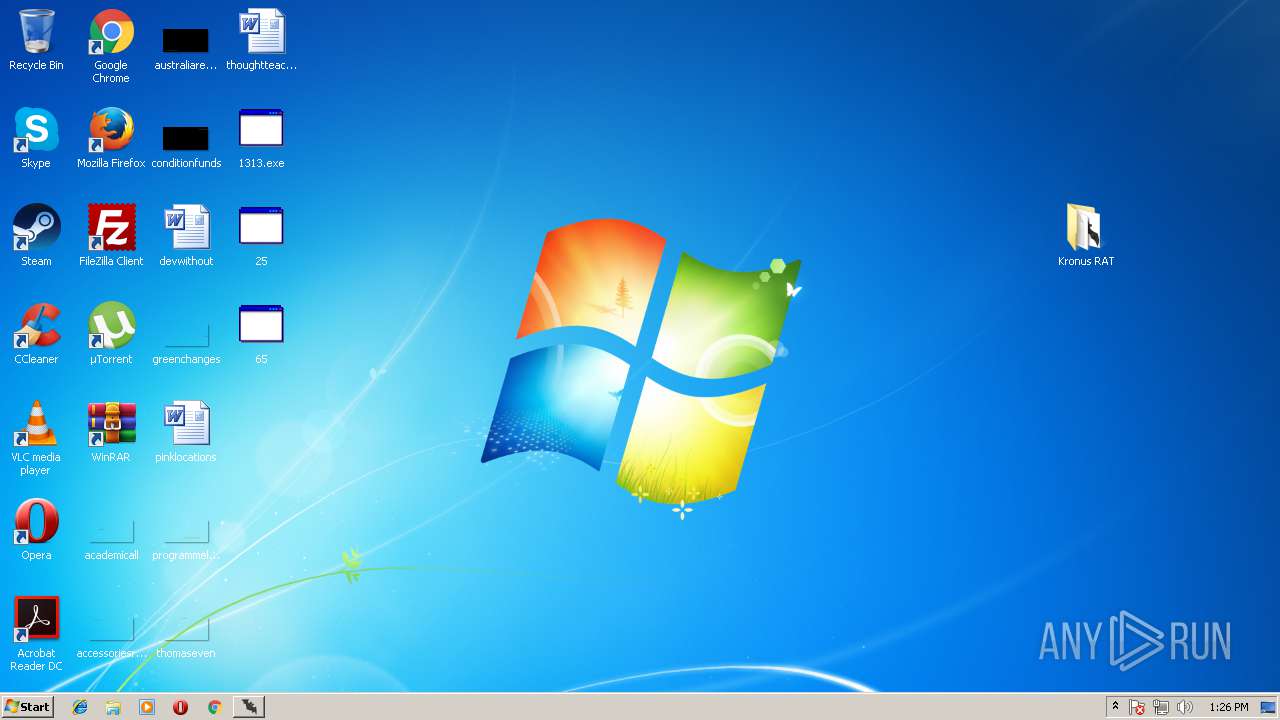
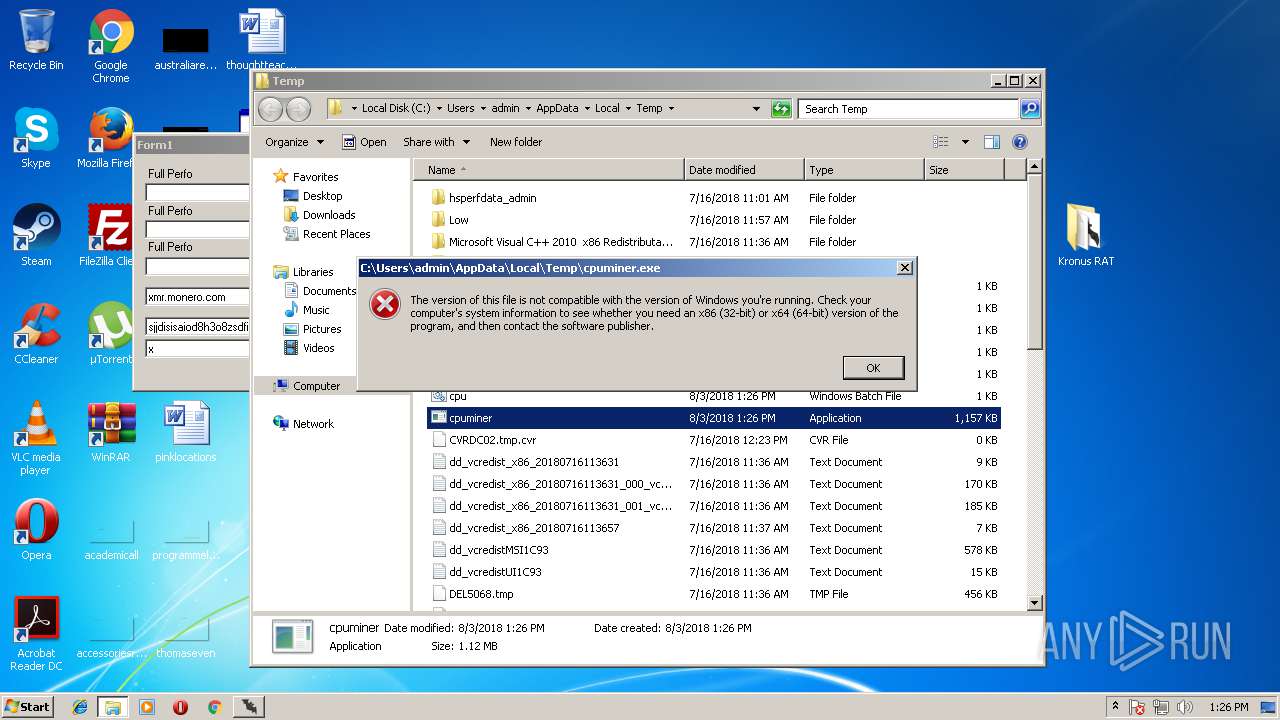
Application was dropped or rewritten from another process
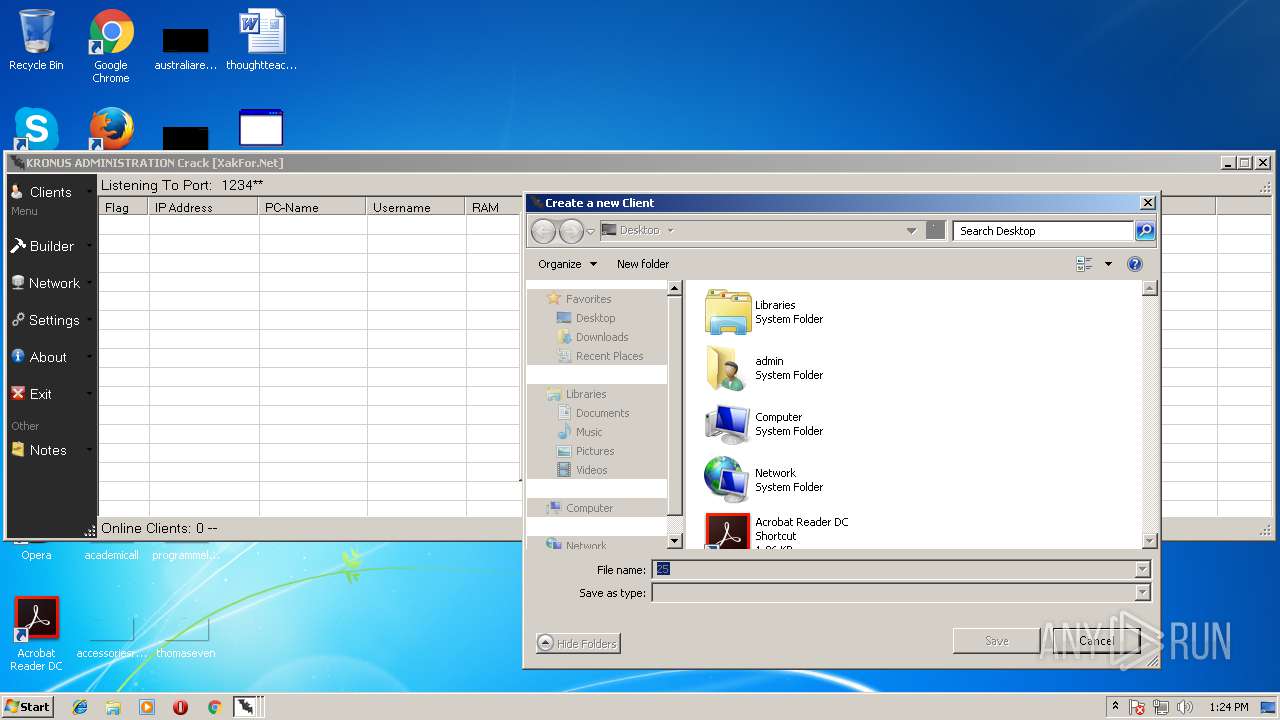
- 65.exe (PID: 2792)
- 25.exe (PID: 128)
- 1313.exe.exe (PID: 1196)
- 25.exe (PID: 2116)
SUSPICIOUS
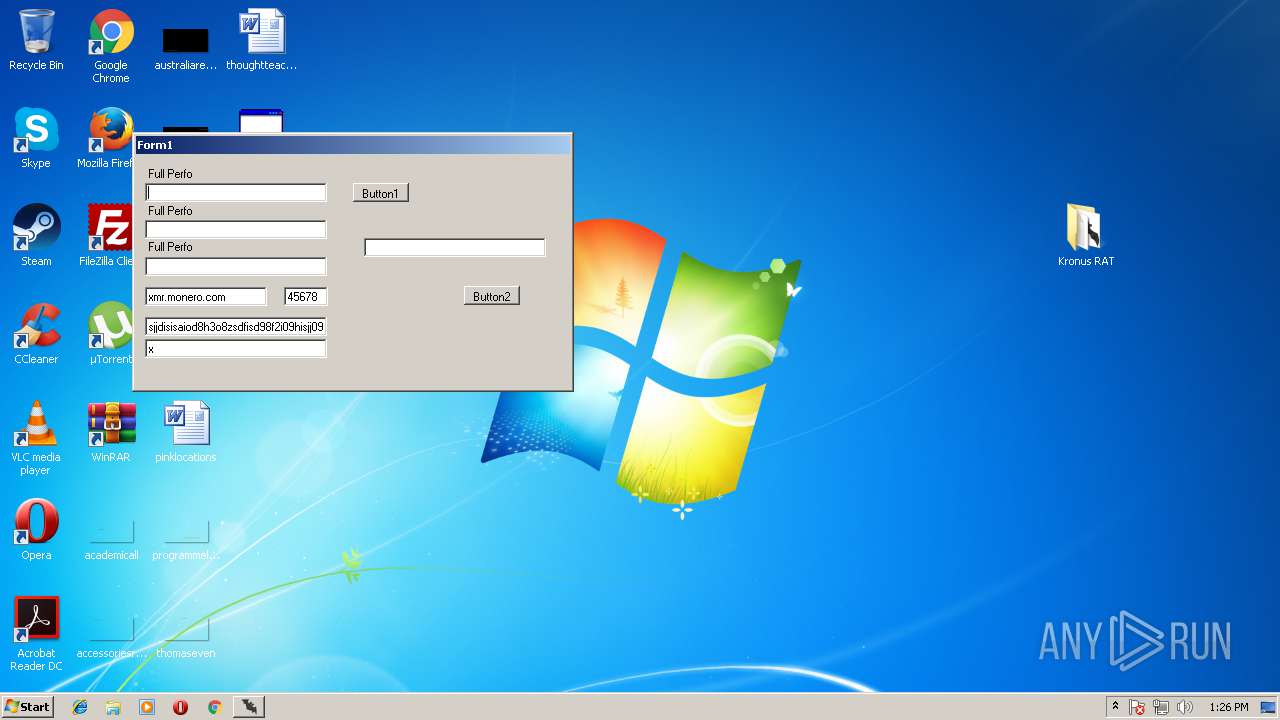
Executable content was dropped or overwritten
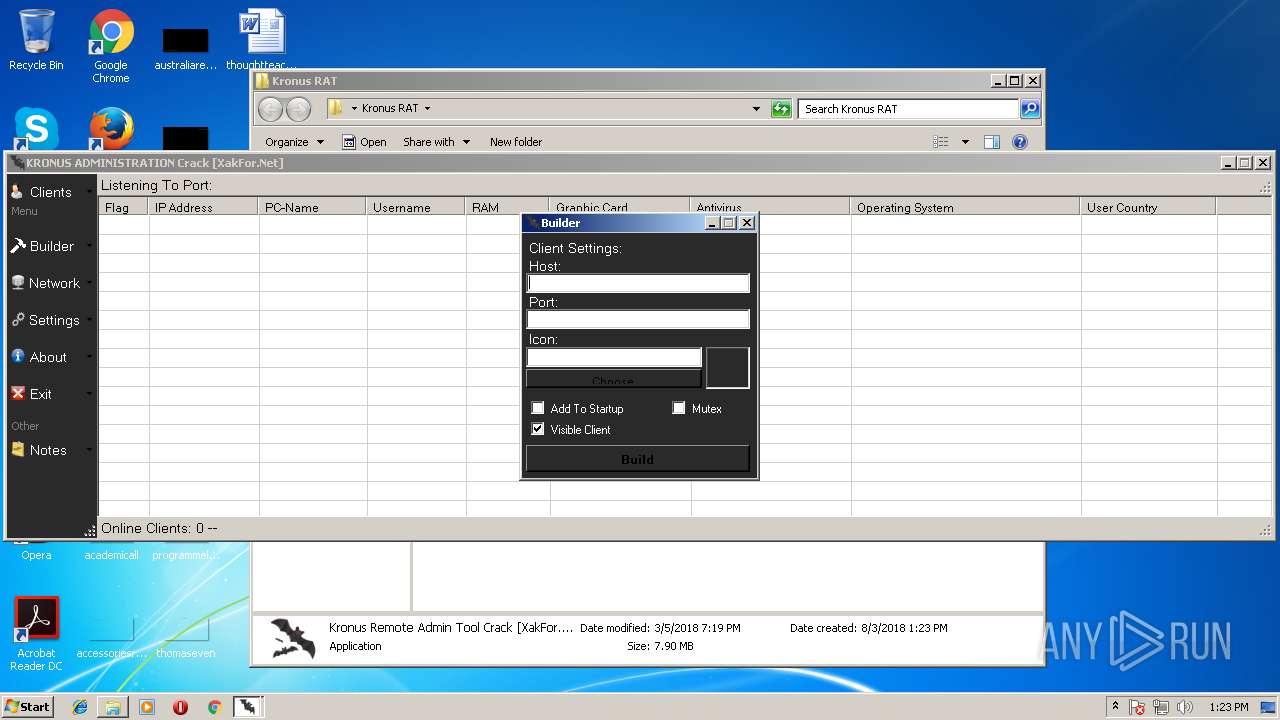
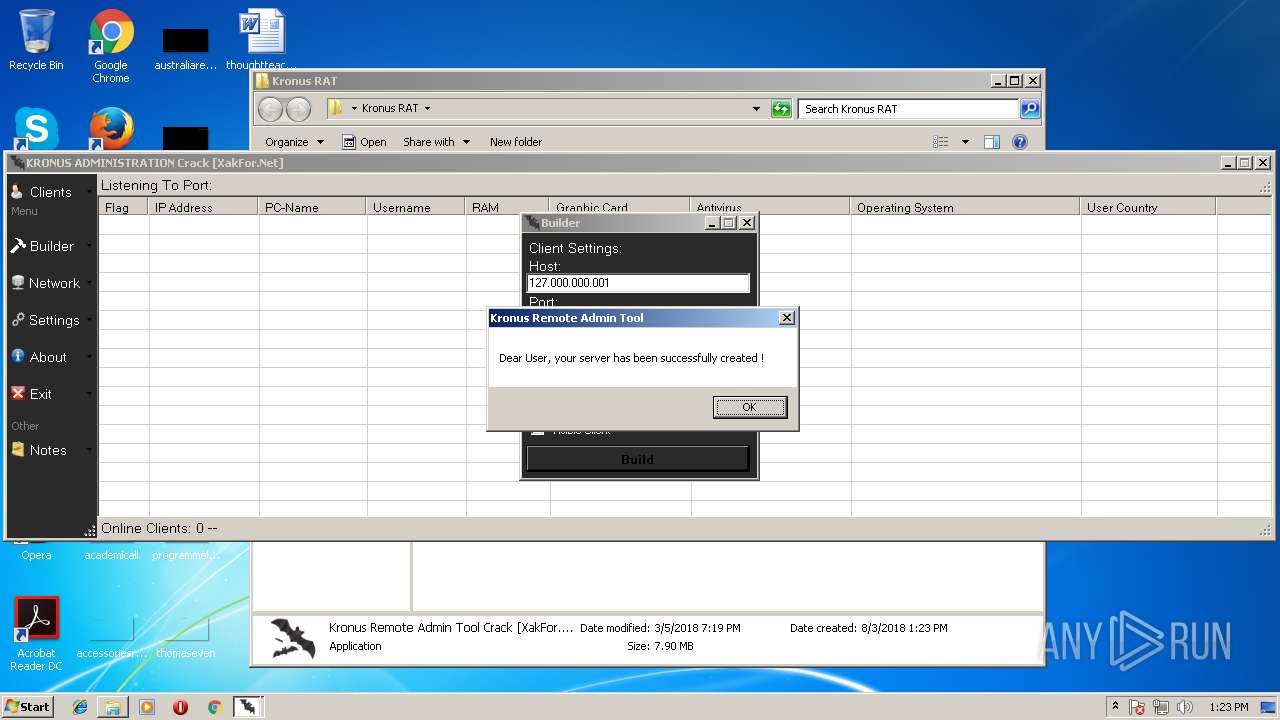
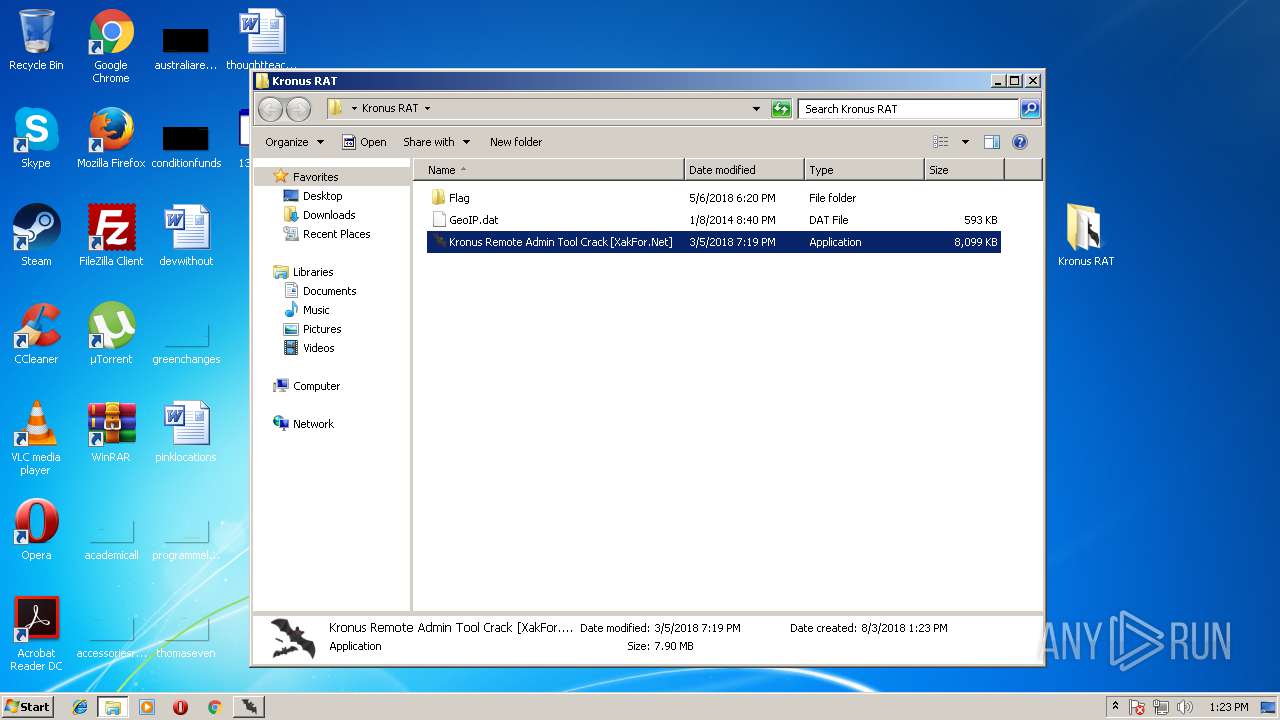
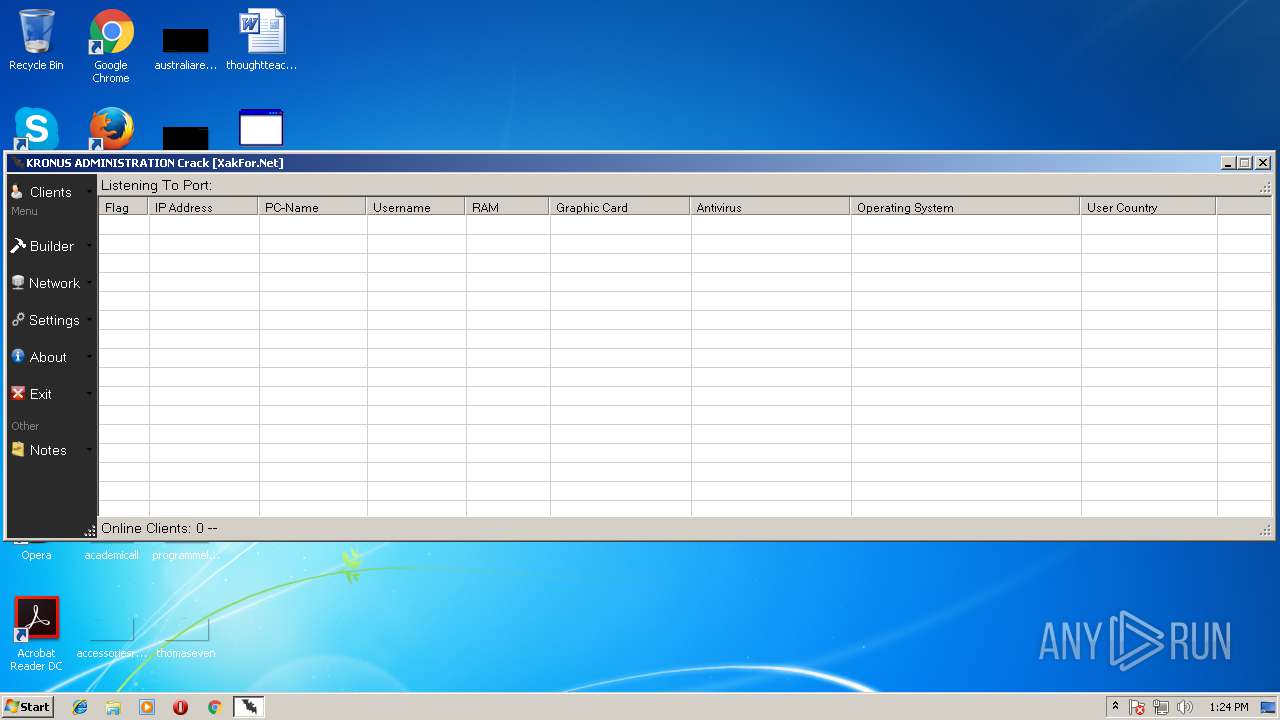
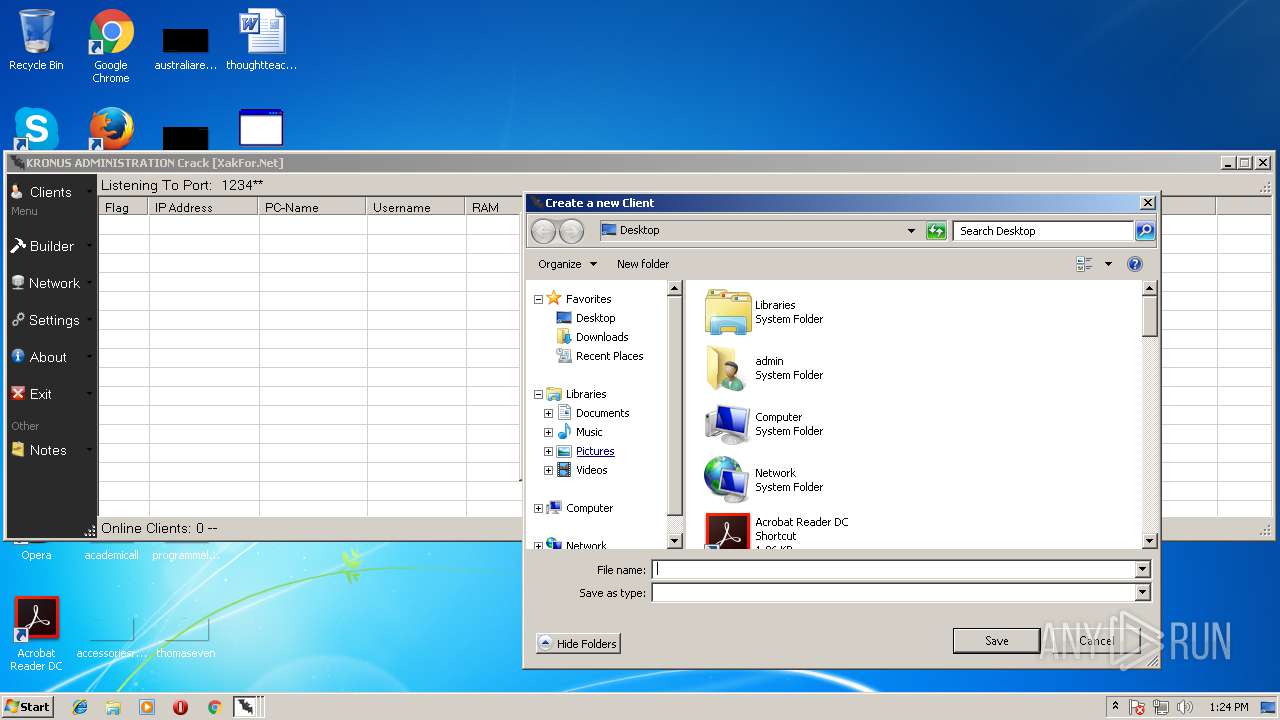
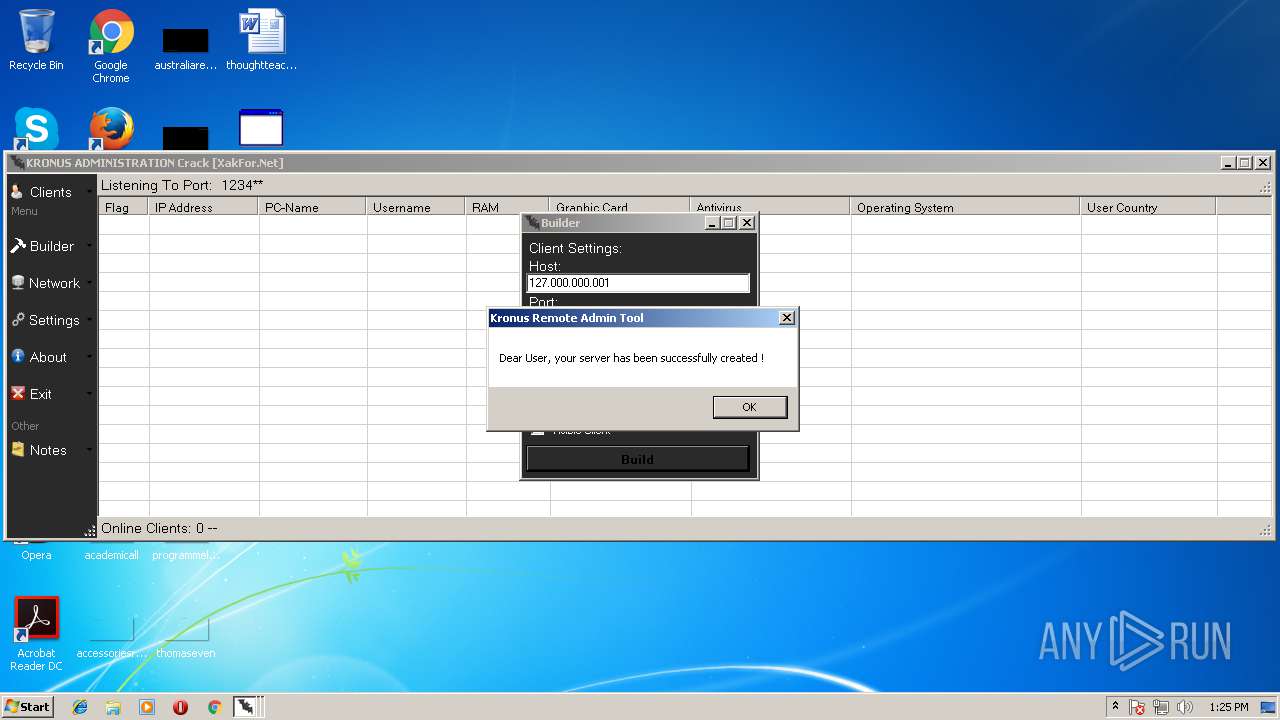
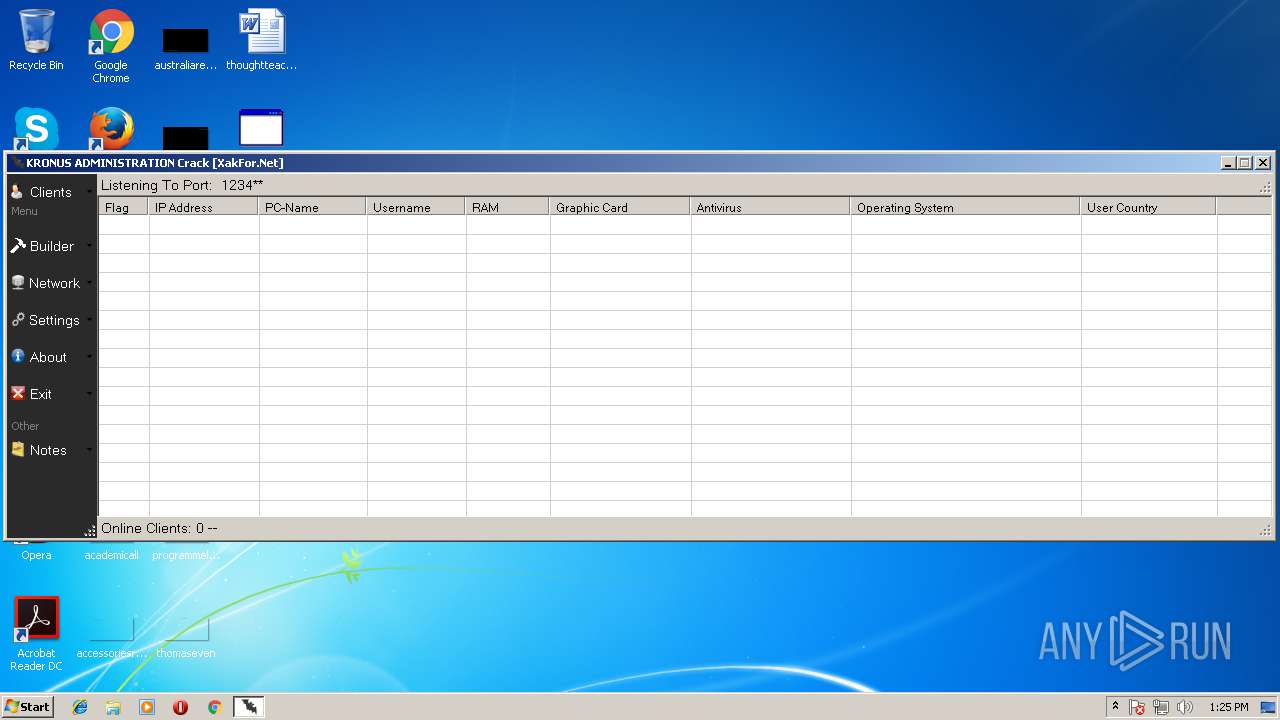
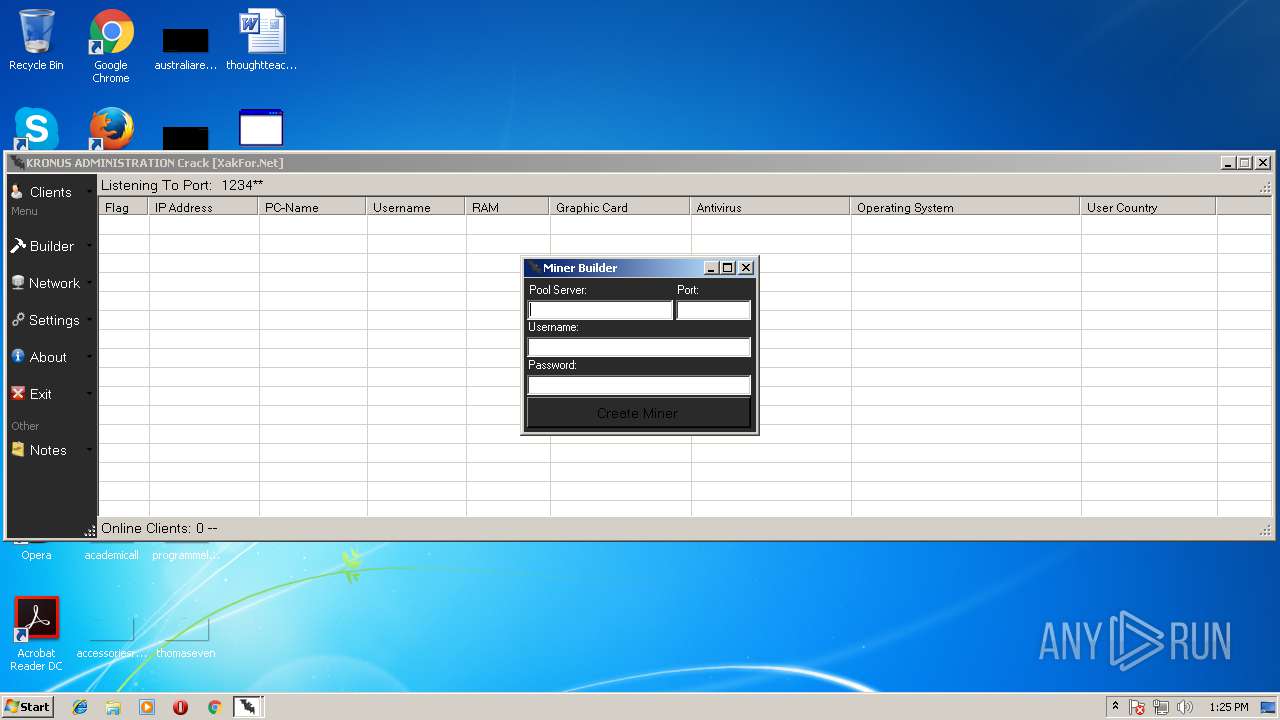
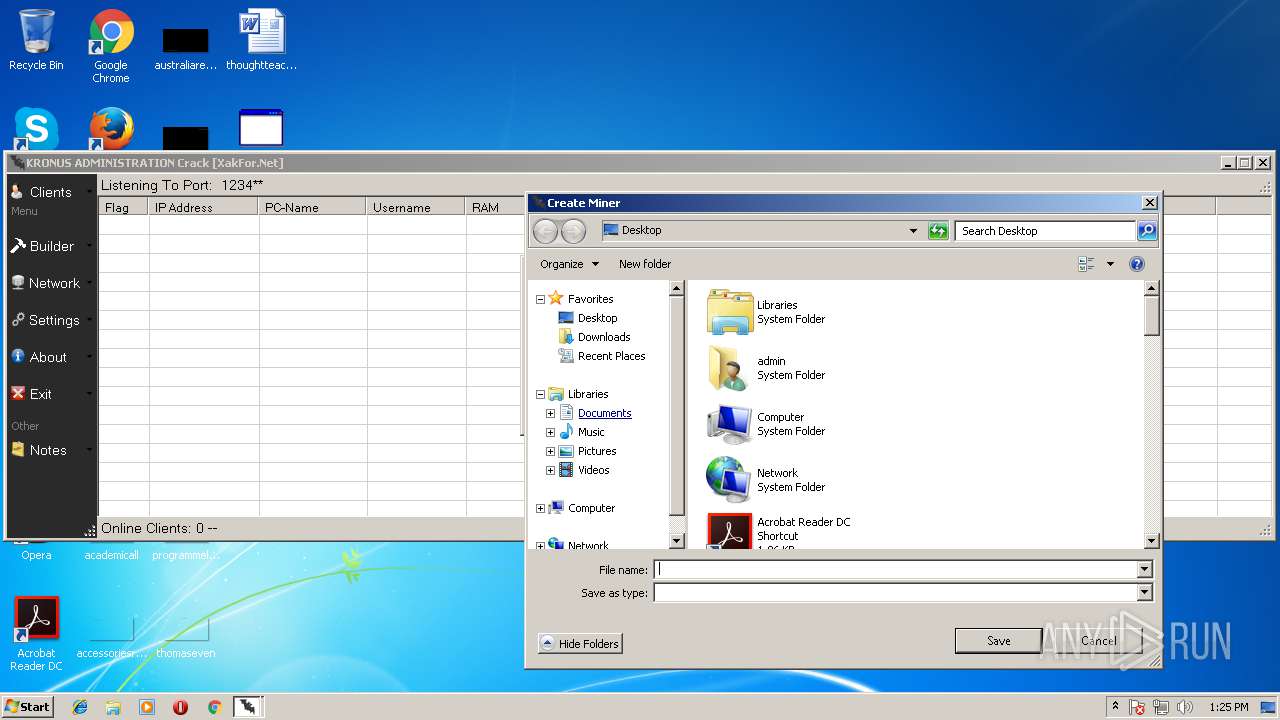
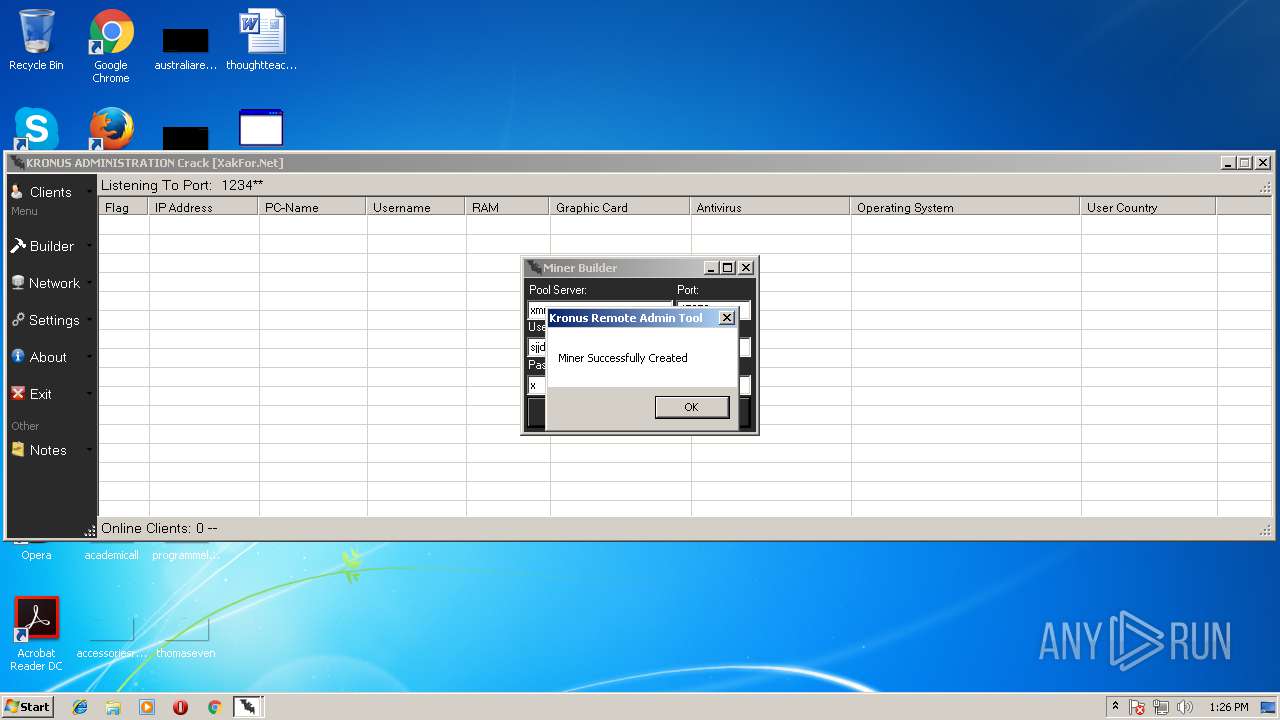
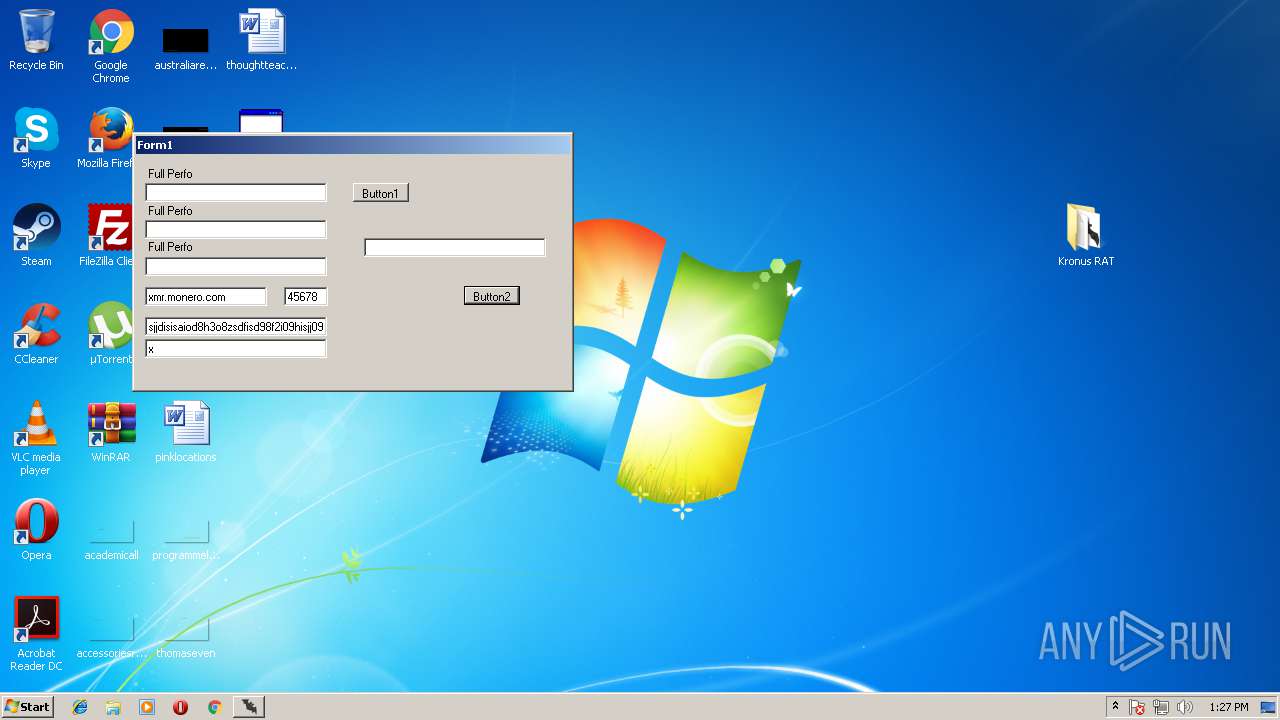
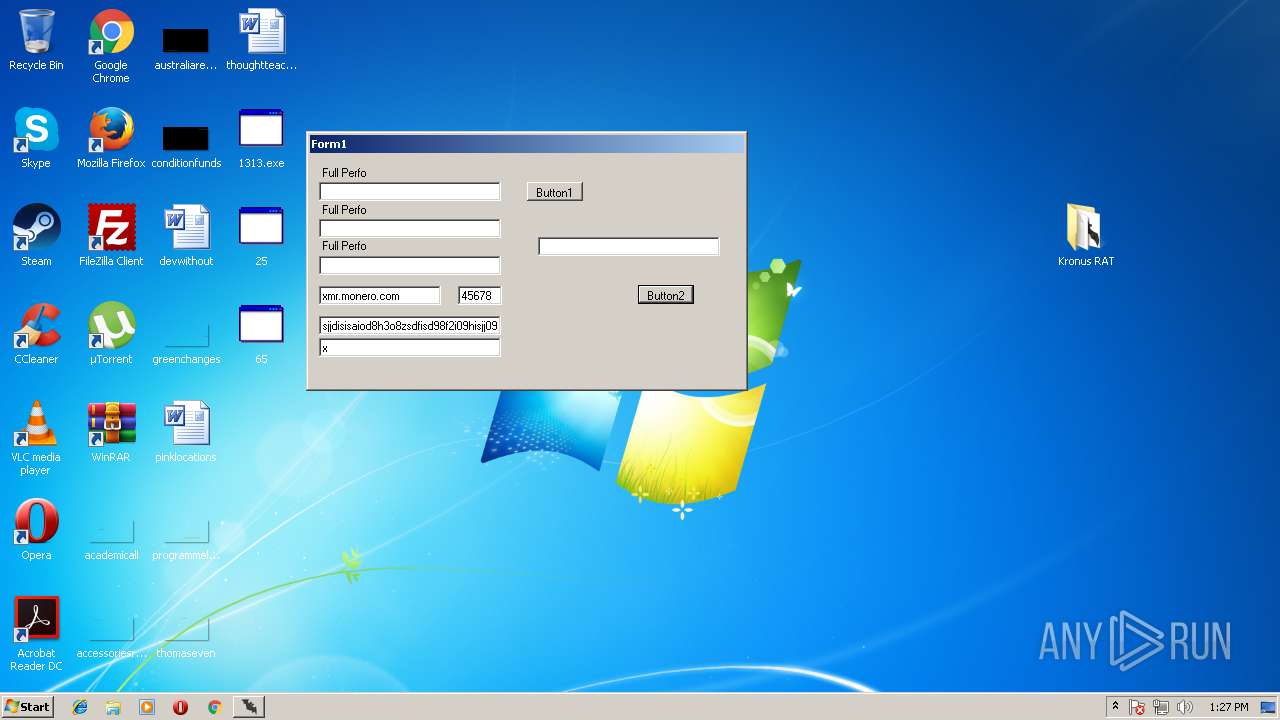
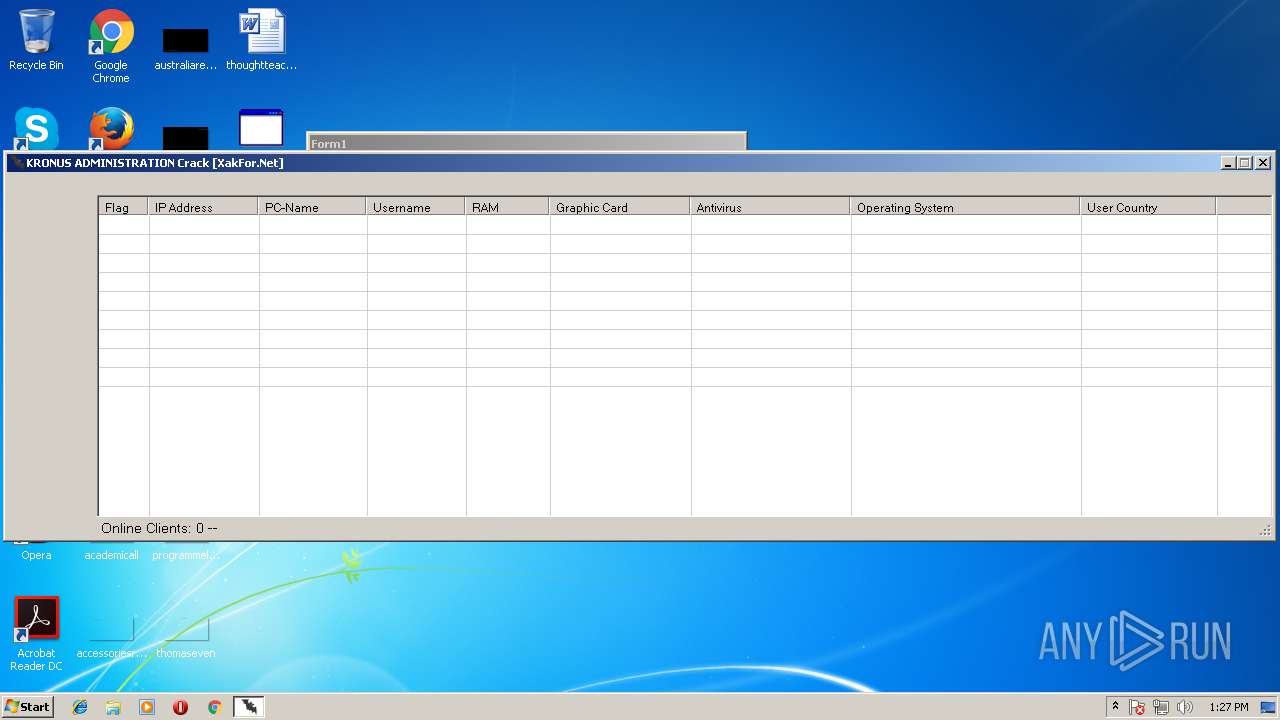
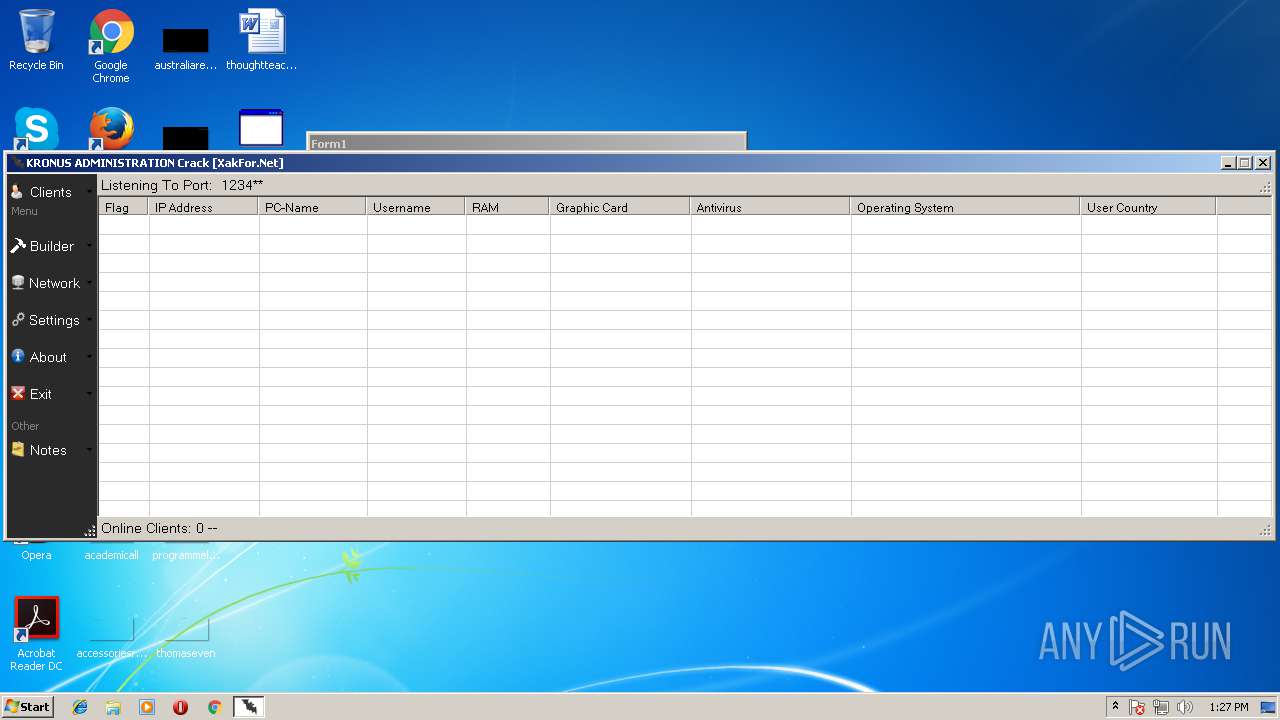
- Kronus Remote Admin Tool Crack [XakFor.Net].exe (PID: 1544)
- 65.exe (PID: 2792)
Starts CMD.EXE for commands execution
- 65.exe (PID: 2792)
Creates files in the user directory
- notepad++.exe (PID: 3524)
INFO
Dropped object may contain URL's
- Kronus Remote Admin Tool Crack [XakFor.Net].exe (PID: 1544)
- notepad++.exe (PID: 3524)
- 65.exe (PID: 2792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
63
Monitored processes
12
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\Desktop\25.exe" | C:\Users\admin\Desktop\25.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Kronus Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\Desktop\1313.exe.exe" | C:\Users\admin\Desktop\1313.exe.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Kronus Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1544 | "C:\Users\admin\Desktop\Kronus RAT\Kronus Remote Admin Tool Crack [XakFor.Net].exe" | C:\Users\admin\Desktop\Kronus RAT\Kronus Remote Admin Tool Crack [XakFor.Net].exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Kronus Administrator Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1568 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Kronus RAT By Kronus Team.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
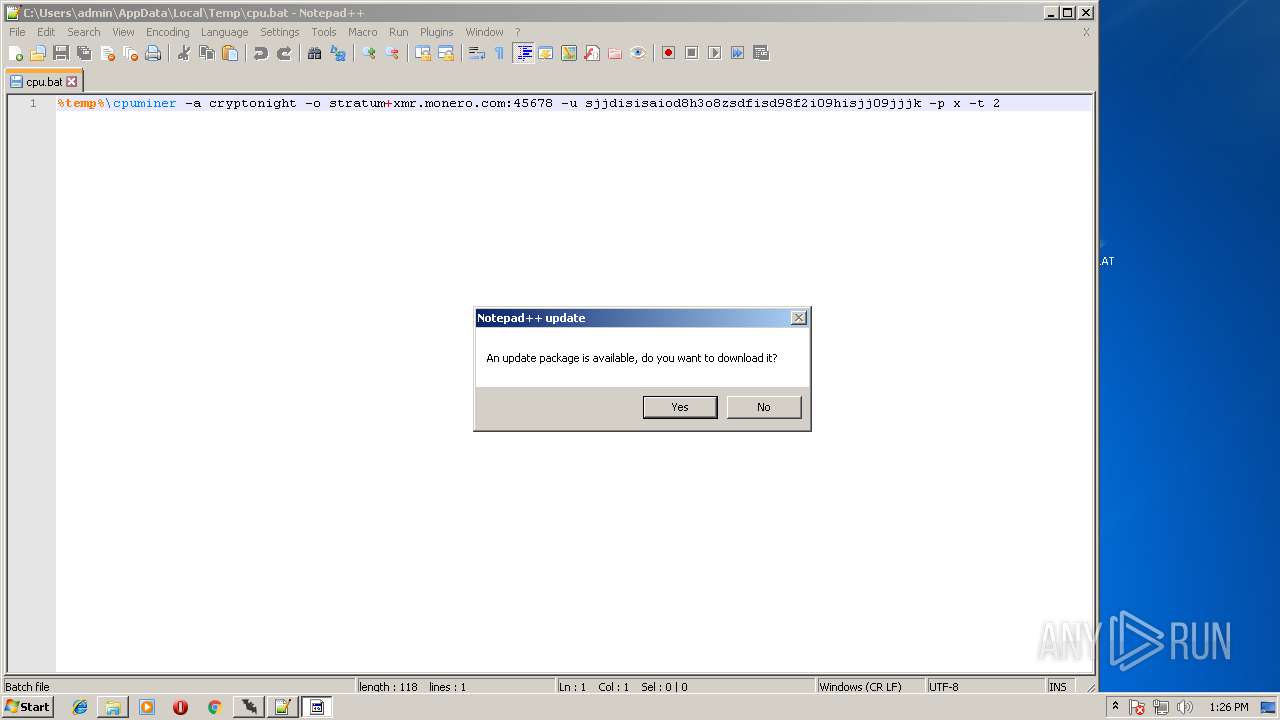
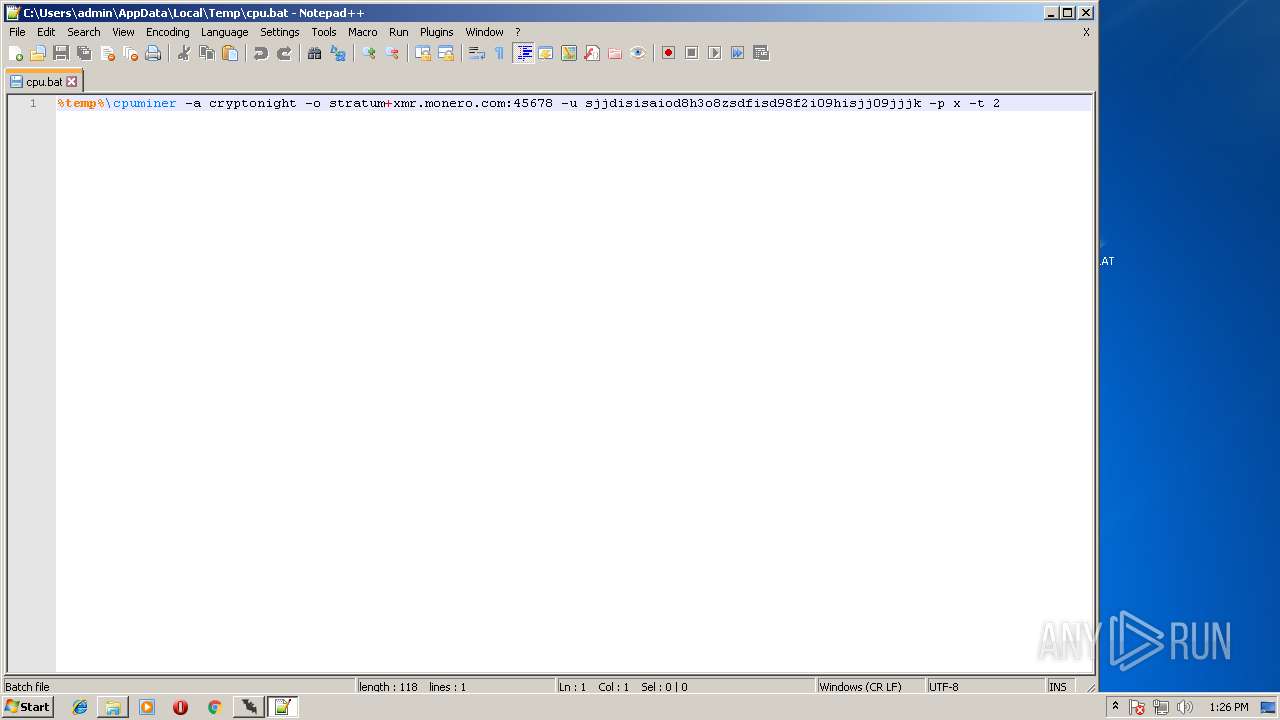
| 1988 | cmd /c ""C:\Users\admin\AppData\Local\Temp\cpu.bat" " | C:\Windows\system32\cmd.exe | — | 65.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2116 | "C:\Users\admin\Desktop\25.exe" | C:\Users\admin\Desktop\25.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Kronus Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2684 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2792 | "C:\Users\admin\Desktop\65.exe" | C:\Users\admin\Desktop\65.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WindowsApplication1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2896 | cmd /c ""C:\Users\admin\AppData\Local\Temp\cpu.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
Total events
1 738
Read events
1 504
Write events
216
Delete events
18
Modification events
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\59\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Kronus RAT By Kronus Team.rar | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF2C0000002C000000EC03000021020000 | |||
Executable files
15
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\--.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\ad.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\ae.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\af.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\ag.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\ai.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\al.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\am.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\an.png | — | |
MD5:— | SHA256:— | |||
| 1568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1568.15900\Kronus RAT\Flag\ao.png | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.186.41:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | unknown | der | 471 b | whitelisted |
— | — | GET | 200 | 2.16.186.41:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | unknown | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2952 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
— | — | 2.16.186.41:80 | ocsp.usertrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabl |
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|