| File name: | psiphon3.exe |
| Full analysis: | https://app.any.run/tasks/bcf88bb6-08d2-465c-b000-7b2deffb625b |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 15:37:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 03A796B1CF377E857151727353D3E33C |
| SHA1: | 14DB38BEF5B502D7E0D1F0F318A58A2209E0A144 |
| SHA256: | 4EB5F85203B0AE38F5D9785B1F28C3FCAB144A648E56E87C0677768813046CE8 |
| SSDEEP: | 98304:EN7MQoVvmCEh0tI+6N+K7P4lPjyCKUYIHXXvj3hdUIuUKQ/3rbzjI8pZV:EN76VvA0tI/NH7AlmfI3Xvj3zj4O |
MALICIOUS
Application was dropped or rewritten from another process
- psiphon-tunnel-core.exe (PID: 2264)
SUSPICIOUS
Creates files in the user directory
- psiphon3.exe (PID: 3276)
- psiphon-tunnel-core.exe (PID: 2264)
Reads Internet Cache Settings
- psiphon3.exe (PID: 3276)
- rundll32.exe (PID: 2712)
Reads internet explorer settings
- psiphon3.exe (PID: 3276)
Uses RUNDLL32.EXE to load library
- psiphon3.exe (PID: 3276)
Starts Internet Explorer
- psiphon3.exe (PID: 3276)
Executable content was dropped or overwritten
- psiphon3.exe (PID: 3276)
Connects to unusual port
- psiphon-tunnel-core.exe (PID: 2264)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2988)
Application launched itself
- iexplore.exe (PID: 2988)
Reads Internet Cache Settings
- iexplore.exe (PID: 2688)
Creates files in the user directory
- iexplore.exe (PID: 2688)
- iexplore.exe (PID: 2988)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2288)
Reads internet explorer settings
- iexplore.exe (PID: 2688)
Reads settings of System Certificates
- iexplore.exe (PID: 2988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:11 03:54:27+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 6029312 |
| InitializedDataSize: | 90112 |
| UninitializedDataSize: | 11665408 |
| EntryPoint: | 0x10e07e0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Mar-2019 02:54:27 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 11-Mar-2019 02:54:27 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00B20000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00B21000 | 0x005C0000 | 0x005BFC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.93021 |
.rsrc | 0x010E1000 | 0x00016000 | 0x00015C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.48749 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.0192 | 744 | UNKNOWN | English - United States | RT_ICON |
3 | 5.62289 | 1384 | UNKNOWN | English - United States | RT_ICON |
4 | 5.86281 | 2216 | UNKNOWN | English - United States | RT_ICON |
5 | 5.32737 | 3752 | UNKNOWN | English - United States | RT_ICON |
6 | 5.87817 | 1128 | UNKNOWN | English - United States | RT_ICON |
7 | 5.40402 | 66 | UNKNOWN | English - United States | RT_STRING |
8 | 4.79539 | 9640 | UNKNOWN | English - United States | RT_ICON |
9 | 7.96592 | 19543 | UNKNOWN | English - United States | RT_ICON |
10 | 7.94804 | 41745 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
CRYPT32.dll |
GDI32.dll |
KERNEL32.DLL |
OLEAUT32.dll |
RASAPI32.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
Total processes
38
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2264 | C:\Users\admin\AppData\Local\Temp\psiphon-tunnel-core.exe --config "C:\Users\admin\AppData\Roaming\Psiphon3\psiphon.config" --serverList "C:\Users\admin\AppData\Roaming\Psiphon3\server_list.dat" | C:\Users\admin\AppData\Local\Temp\psiphon-tunnel-core.exe | psiphon3.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2288 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2688 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2988 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2712 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | psiphon3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2988 | "C:\Program Files\Internet Explorer\iexplore.exe" https://ipfounder.net/?sponsor_id=4BA4DEF917101460&sponsor=psiphon_bbg&client_region=CH&client_platform=windows&secret=580EfjEI29xL3hoyU6dgP4vSEVxdcGI7JDFkxgjds7PHulSEF0wmORpvzbqxyTwYtpowsY4xMFnfWEnTghe6l8jiV9K5QSZoir2i6fDeKJD6EhL6DkoYTEMu2EE9YJvy3LdCUZ7ncdVC6ipgWx06wznvDLbY1ajfcfRGCpfsQJei2q6tb0GSFh1QK3x3qXKwyjmNPc5J | C:\Program Files\Internet Explorer\iexplore.exe | psiphon3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3276 | "C:\Users\admin\AppData\Local\Temp\psiphon3.exe" | C:\Users\admin\AppData\Local\Temp\psiphon3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
649
Read events
524
Write events
122
Delete events
3
Modification events
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_CURRENT_USER\Software\Psiphon3 |
| Operation: | write | Name: | SkipBrowser |
Value: 0 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_CURRENT_USER\Software\Psiphon3 |
| Operation: | write | Name: | SkipProxySettings |
Value: 0 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_CURRENT_USER\Software\Psiphon3 |
| Operation: | write | Name: | SkipAutoConnect |
Value: 0 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\psiphon3_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\psiphon3_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\psiphon3_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\psiphon3_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3276) psiphon3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\psiphon3_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
1
Suspicious files
0
Text files
35
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2988 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2688 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@ipfounder[1].txt | — | |
MD5:— | SHA256:— | |||
| 2688 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\psiphon1[1].txt | — | |
MD5:— | SHA256:— | |||
| 3276 | psiphon3.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\main[1] | html | |
MD5:— | SHA256:— | |||
| 3276 | psiphon3.exe | C:\Users\admin\AppData\Roaming\Psiphon3\server_list.dat | text | |
MD5:— | SHA256:— | |||
| 3276 | psiphon3.exe | C:\Users\admin\AppData\Local\Temp\psiphon-tunnel-core.exe | executable | |
MD5:— | SHA256:— | |||
| 2688 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\app[1].css | text | |
MD5:— | SHA256:— | |||
| 2688 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\psiphon1[1].htm | html | |
MD5:— | SHA256:— | |||
| 2688 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@whatismyip[1].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
2
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2264 | psiphon-tunnel-core.exe | POST | 200 | 46.101.199.43:80 | http://underfunds.org/ | DE | binary | 572 b | suspicious |
2264 | psiphon-tunnel-core.exe | POST | — | 46.101.199.43:80 | http://underfunds.org/ | DE | — | — | suspicious |
2264 | psiphon-tunnel-core.exe | POST | — | 2.16.186.74:80 | http://www.yiboomerglobalbarcode.com/ | unknown | — | — | whitelisted |
2264 | psiphon-tunnel-core.exe | POST | 200 | 46.101.199.43:80 | http://underfunds.org/ | DE | binary | 6.24 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2264 | psiphon-tunnel-core.exe | 2.16.186.49:443 | a542.g.akamai.net | Akamai International B.V. | — | whitelisted |
2264 | psiphon-tunnel-core.exe | 82.223.54.95:443 | — | 1&1 Internet SE | ES | unknown |
2264 | psiphon-tunnel-core.exe | 194.187.251.178:53 | — | M247 Ltd | BE | unknown |
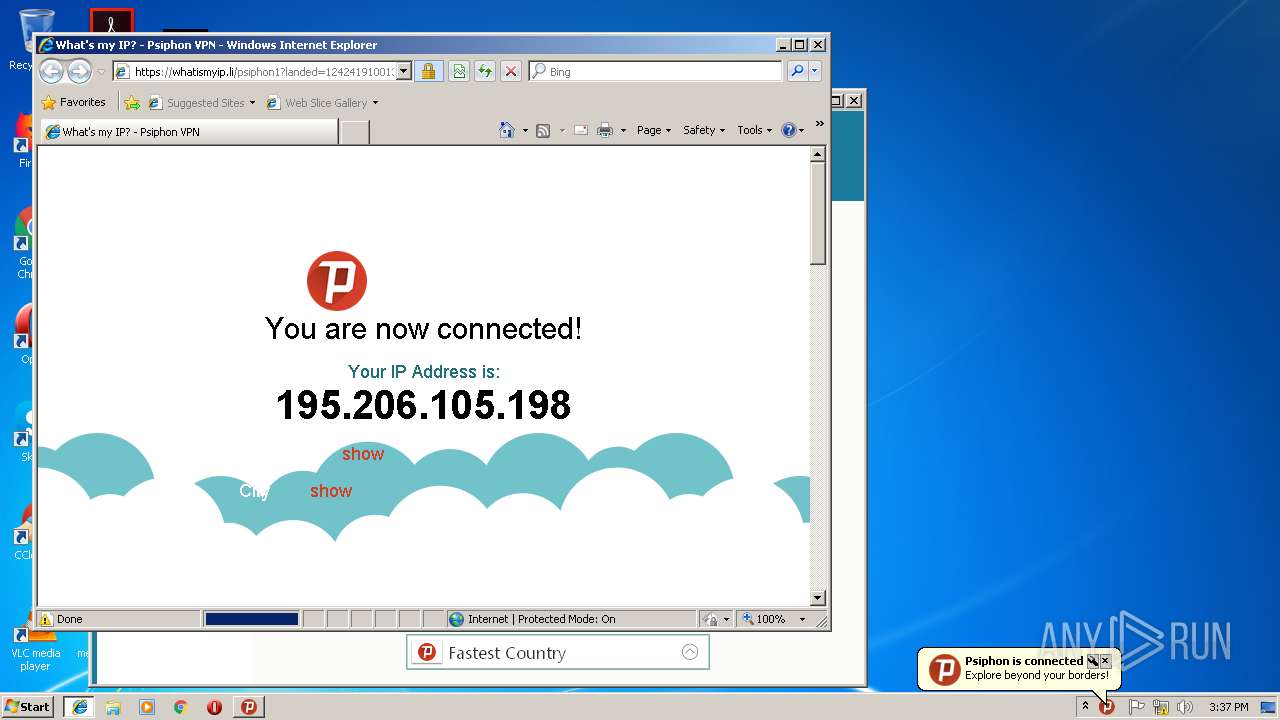
2264 | psiphon-tunnel-core.exe | 195.206.105.198:22 | — | — | — | unknown |
2264 | psiphon-tunnel-core.exe | 212.227.200.149:443 | — | 1&1 Internet SE | DE | unknown |
2264 | psiphon-tunnel-core.exe | 213.108.108.231:554 | — | Greenhost BV | NL | suspicious |
2264 | psiphon-tunnel-core.exe | 128.127.104.97:443 | — | AltusHost B.V. | SE | unknown |
2264 | psiphon-tunnel-core.exe | 74.208.81.170:53 | — | 1&1 Internet SE | US | unknown |
2264 | psiphon-tunnel-core.exe | 46.101.199.43:80 | — | Digital Ocean, Inc. | DE | suspicious |
2264 | psiphon-tunnel-core.exe | 2.16.186.74:80 | a1616.g.akamai.net | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a542.g.akamai.net |
| whitelisted |
a1616.g.akamai.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2264 | psiphon-tunnel-core.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Psiphon3 VPN connection |
2264 | psiphon-tunnel-core.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Psiphon3 VPN connection |
2264 | psiphon-tunnel-core.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Psiphon3 VPN connection |
2264 | psiphon-tunnel-core.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Psiphon3 VPN connection |
2264 | psiphon-tunnel-core.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Psiphon3 VPN connection |
2264 | psiphon-tunnel-core.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Psiphon3 VPN connection |
2264 | psiphon-tunnel-core.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Psiphon3 VPN connection |
Process | Message |
|---|---|
psiphon3.exe | |
psiphon3.exe | |
psiphon3.exe | Psiphon Tunnel connecting... |
psiphon3.exe | |
psiphon3.exe | {"data":{"data":{"message":"applied [11] parameters with tag ''"},"noticeType":"Info","showUser":false,"timestamp":"2019-03-14T15:37:40.418Z"},"msg":"CoreNotice","timestamp!!timestamp":"2019-03-14T15:37:40.508Z"}
|
psiphon3.exe | |
psiphon3.exe | thub.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/bifurcation/mint/syntax":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/cheekybits/genny/generic":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/golang/protobuf/proto":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/grafov/m3u8":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/hashicorp/golang-lru":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/hashicorp/golang-lru/simplelru":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/juju/ratelimit":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/aes12":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go-certificates":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/ackhandler":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/congestion":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/crypto":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/flowcontrol":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/handshake":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/protocol":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/utils":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/wire":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/qerr":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/refraction-networking/utls":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/refraction-networking/utls/cpu":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sergeyfrolov/bsbuffer":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sergeyfrolov/gotapdance/protobuf":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sergeyfrolov/gotapdance/tapdance":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sirupsen/logrus":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/zach-klippenstein/goregen":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/chacha20poly1305":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/curve25519":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/hkdf":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/internal/chacha20":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/poly1305":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/ssh/terminal":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/http/httpguts":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/http2/hpack":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/idna":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/proxy":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/sys/windows":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/secure/bidirule":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/transform":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/unicode/bidi":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/unicode/norm":"e5c97f8"},"goV |
psiphon3.exe | thub.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/bifurcation/mint/syntax":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/cheekybits/genny/generic":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/golang/protobuf/proto":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/grafov/m3u8":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/hashicorp/golang-lru":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/hashicorp/golang-lru/simplelru":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/juju/ratelimit":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/aes12":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go-certificates":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/ackhandler":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/congestion":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/crypto":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/flowcontrol":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/handshake":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/protocol":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/utils":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/internal/wire":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/lucas-clemente/quic-go/qerr":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/refraction-networking/utls":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/refraction-networking/utls/cpu":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sergeyfrolov/bsbuffer":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sergeyfrolov/gotapdance/protobuf":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sergeyfrolov/gotapdance/tapdance":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/sirupsen/logrus":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/github.com/zach-klippenstein/goregen":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/chacha20poly1305":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/curve25519":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/hkdf":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/internal/chacha20":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/poly1305":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/crypto/ssh/terminal":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/http/httpguts":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/http2/hpack":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/idna":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/net/proxy":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/sys/windows":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/secure/bidirule":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/transform":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/unicode/bidi":"e5c97f8","github.com/Psiphon-Labs/psiphon-tunnel-core/vendor/golang.org/x/text/unicode/norm":"e5c97f8"},"goV |
psiphon3.exe | ersion":"go1.11.5"}},"noticeType":"BuildInfo","showUser":false,"timestamp":"2019-03-14T15:37:40.418Z"},"msg":"CoreNotice","timestamp!!timestamp":"2019-03-14T15:37:40.508Z"}
|
psiphon3.exe | |