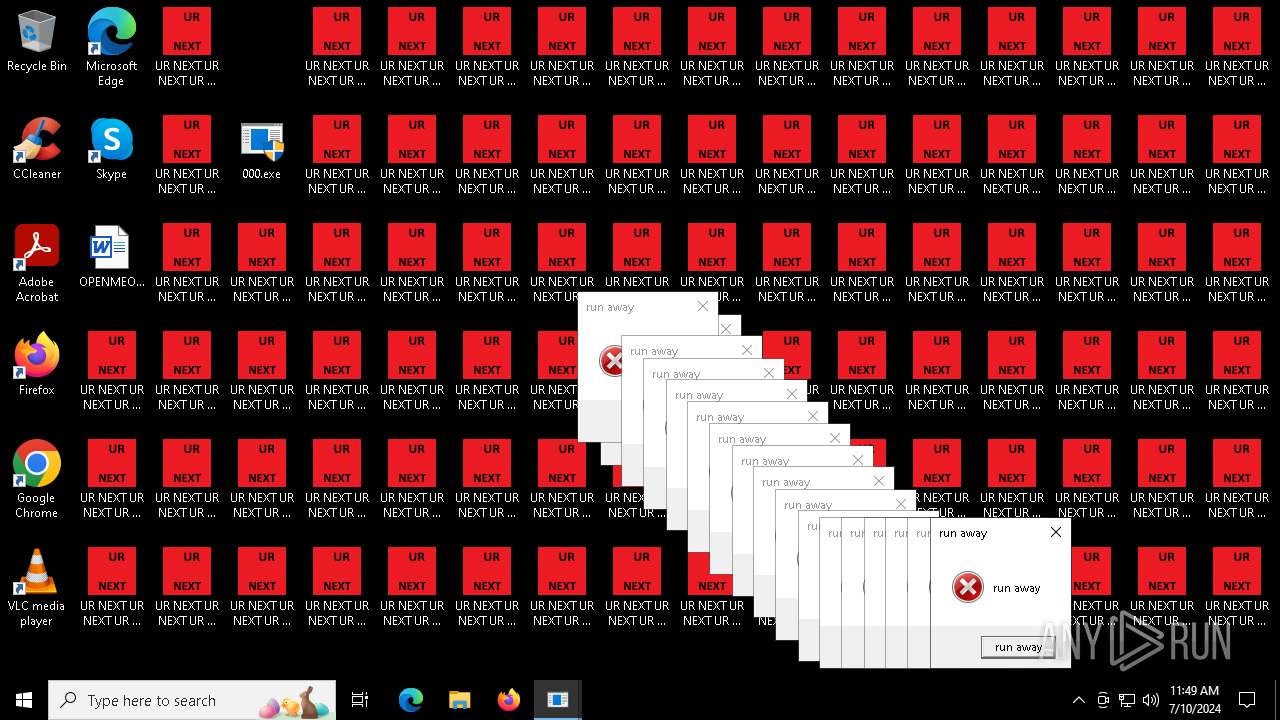
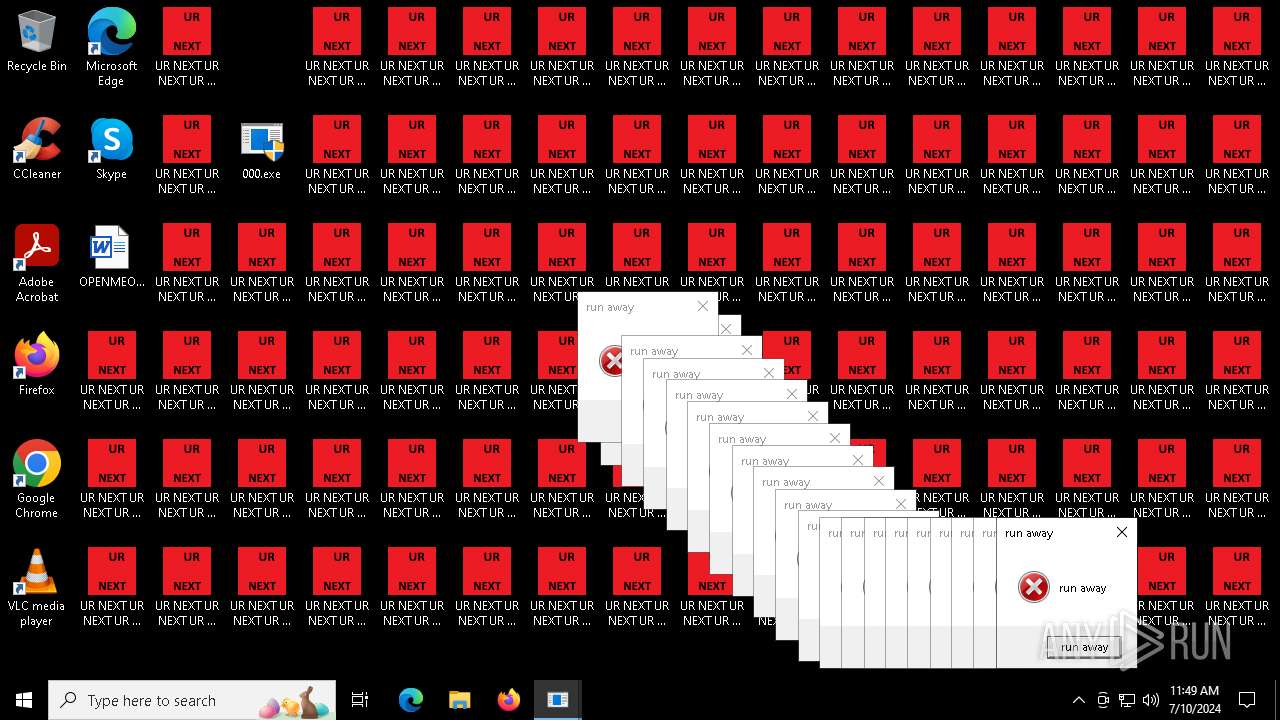
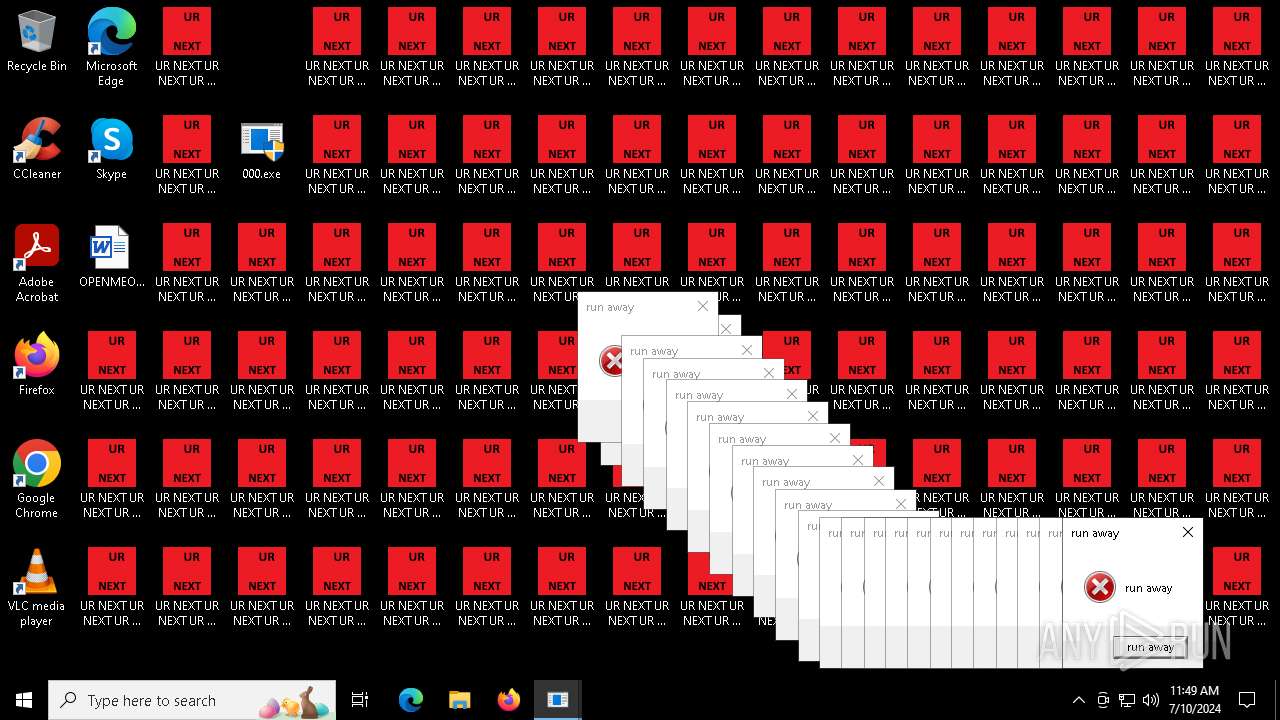
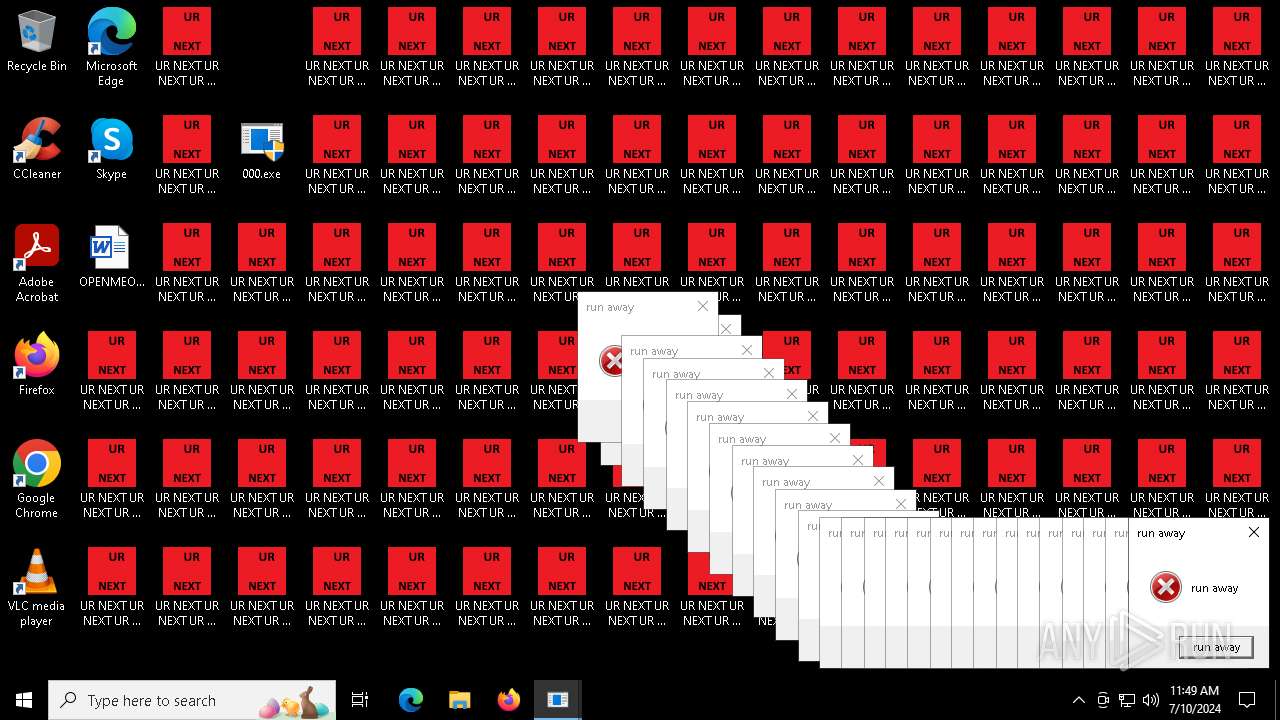
| File name: | 000.exe |
| Full analysis: | https://app.any.run/tasks/c14d7e02-4de3-4dae-a21b-c7dc24b49096 |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2024, 11:47:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F2B7074E1543720A9A98FDA660E02688 |
| SHA1: | 1029492C1A12789D8AF78D54ADCB921E24B9E5CA |
| SHA256: | 4EA1F2ECF7EB12896F2CBF8683DAE8546D2B8DC43CF7710D68CE99E127C0A966 |
| SSDEEP: | 3072:eaLA1++iCeFj0im6X/AXpT8vVMCcHVcdhghUuz1o9Yj:fLJlC6j0CX4XmvWHVcd62uO9+ |
MALICIOUS
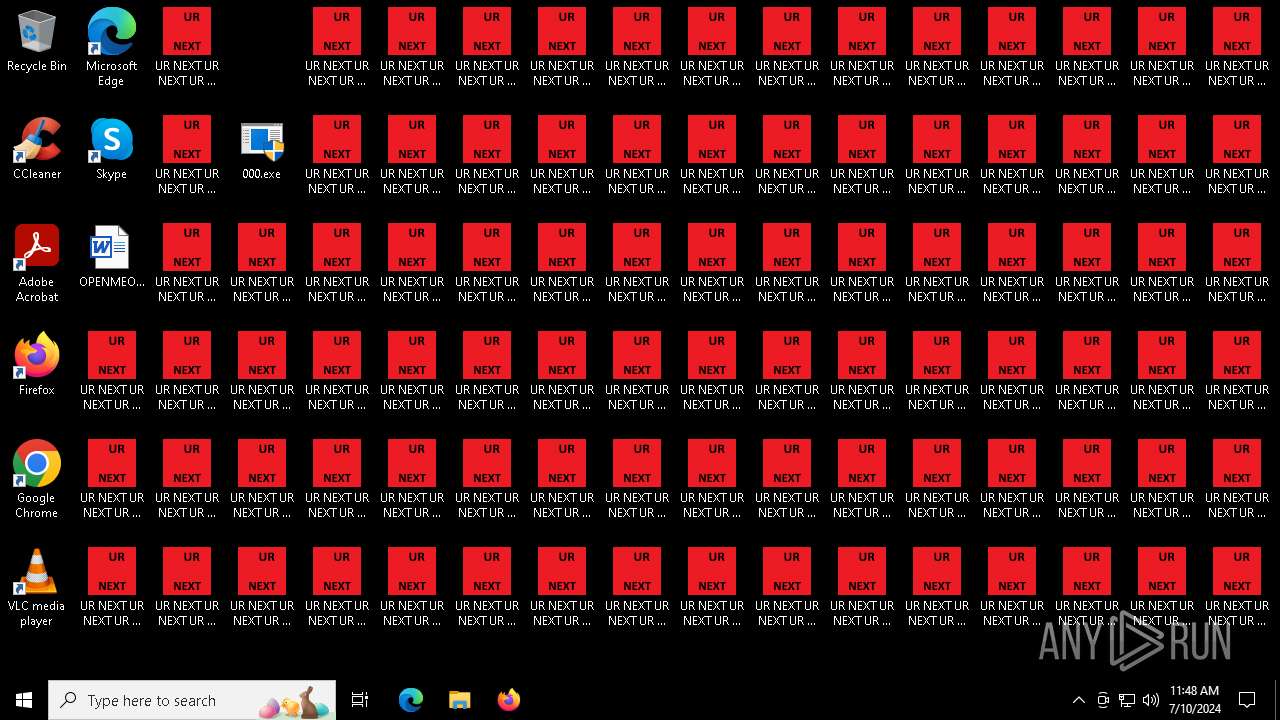
Changes the login/logoff helper path in the registry
- 000.exe (PID: 4532)
Create files in the Startup directory
- cmd.exe (PID: 5460)
Drops the executable file immediately after the start
- cmd.exe (PID: 5460)
- 000.exe (PID: 4532)
- rniw.exe (PID: 5916)
Scans artifacts that could help determine the target
- RUXIMICS.exe (PID: 4520)
SUSPICIOUS
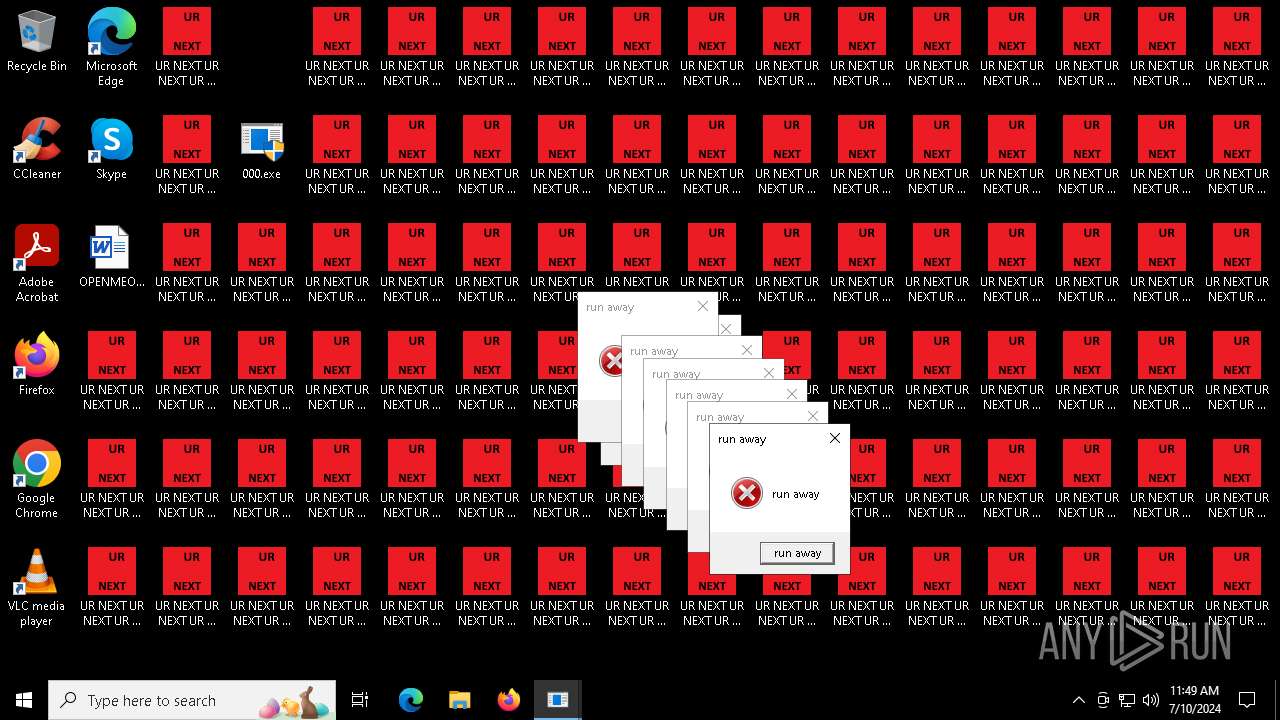
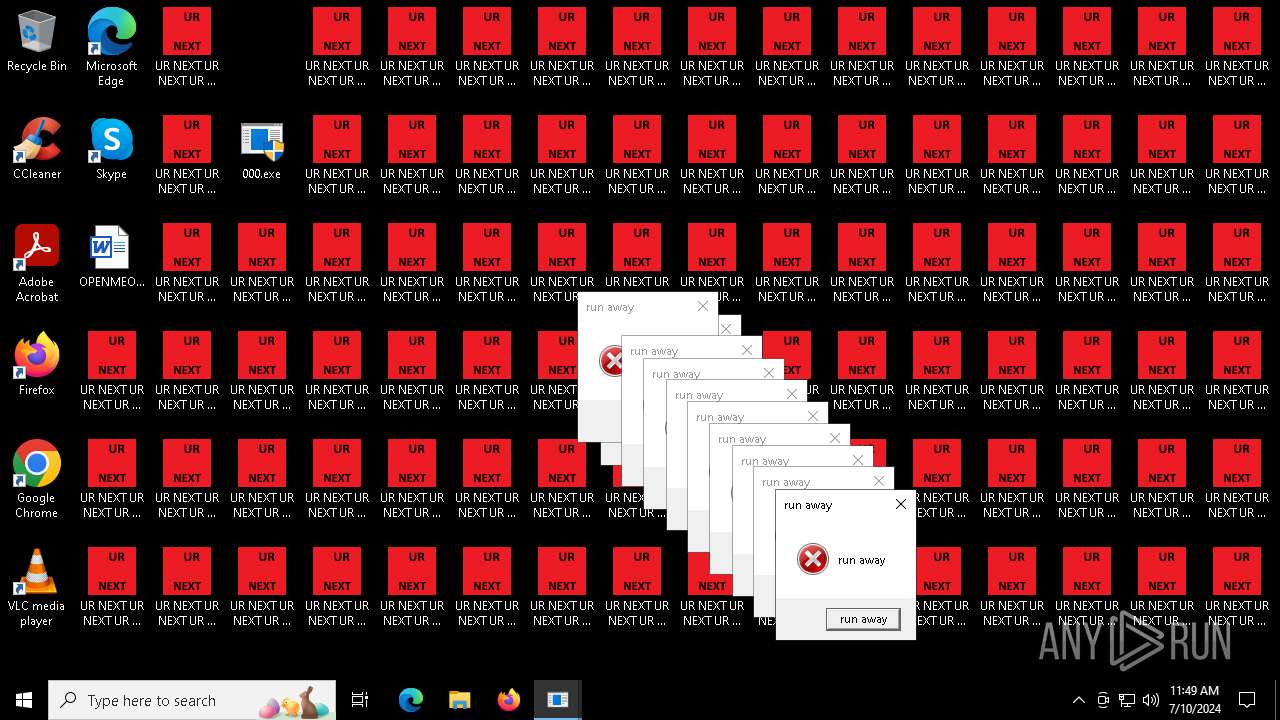
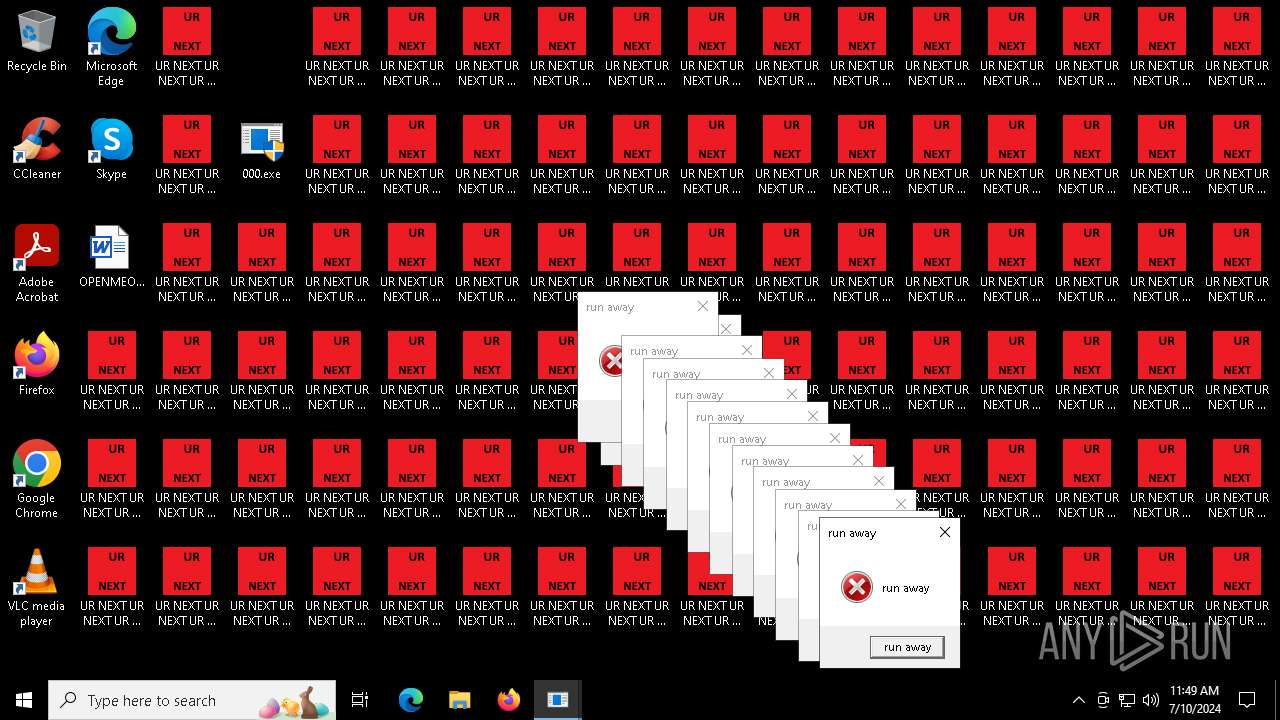
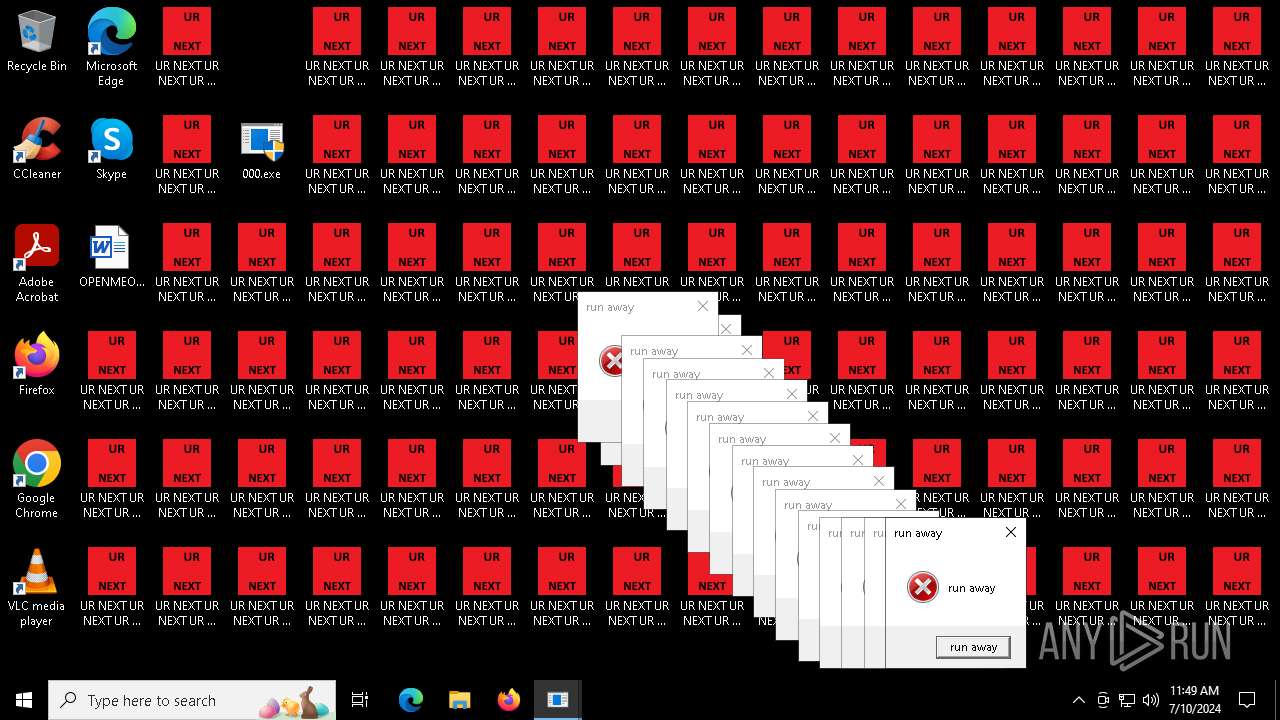
Changes the desktop background image
- 000.exe (PID: 4532)
Executable content was dropped or overwritten
- cmd.exe (PID: 5460)
- 000.exe (PID: 4532)
- rniw.exe (PID: 5916)
Executing commands from a ".bat" file
- 000.exe (PID: 4532)
- rniw.exe (PID: 5916)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5460)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 5460)
Starts CMD.EXE for commands execution
- 000.exe (PID: 4532)
- rniw.exe (PID: 5916)
Reads security settings of Internet Explorer
- 000.exe (PID: 4532)
- rniw.exe (PID: 5916)
The system shut down or reboot
- cmd.exe (PID: 5460)
Reads the date of Windows installation
- rniw.exe (PID: 5916)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3152)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5984)
INFO
Reads the machine GUID from the registry
- 000.exe (PID: 4532)
Reads the computer name
- 000.exe (PID: 4532)
- rniw.exe (PID: 5916)
- RUXIMICS.exe (PID: 4520)
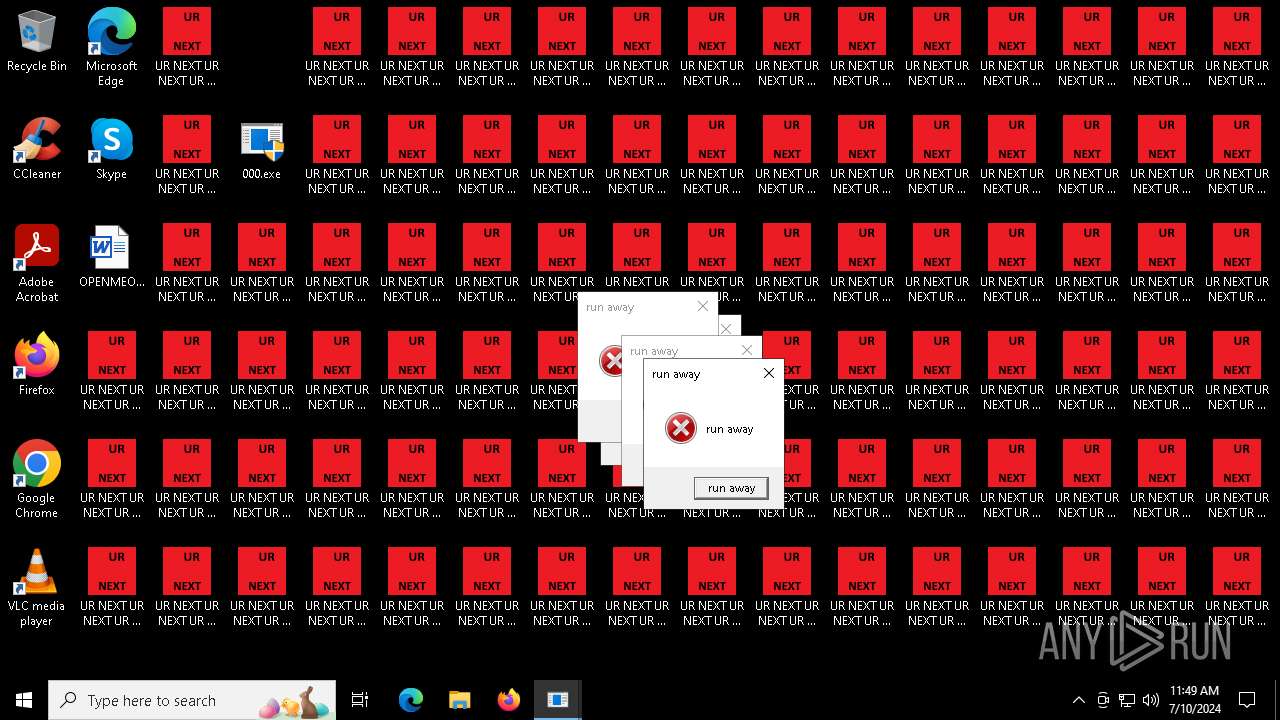
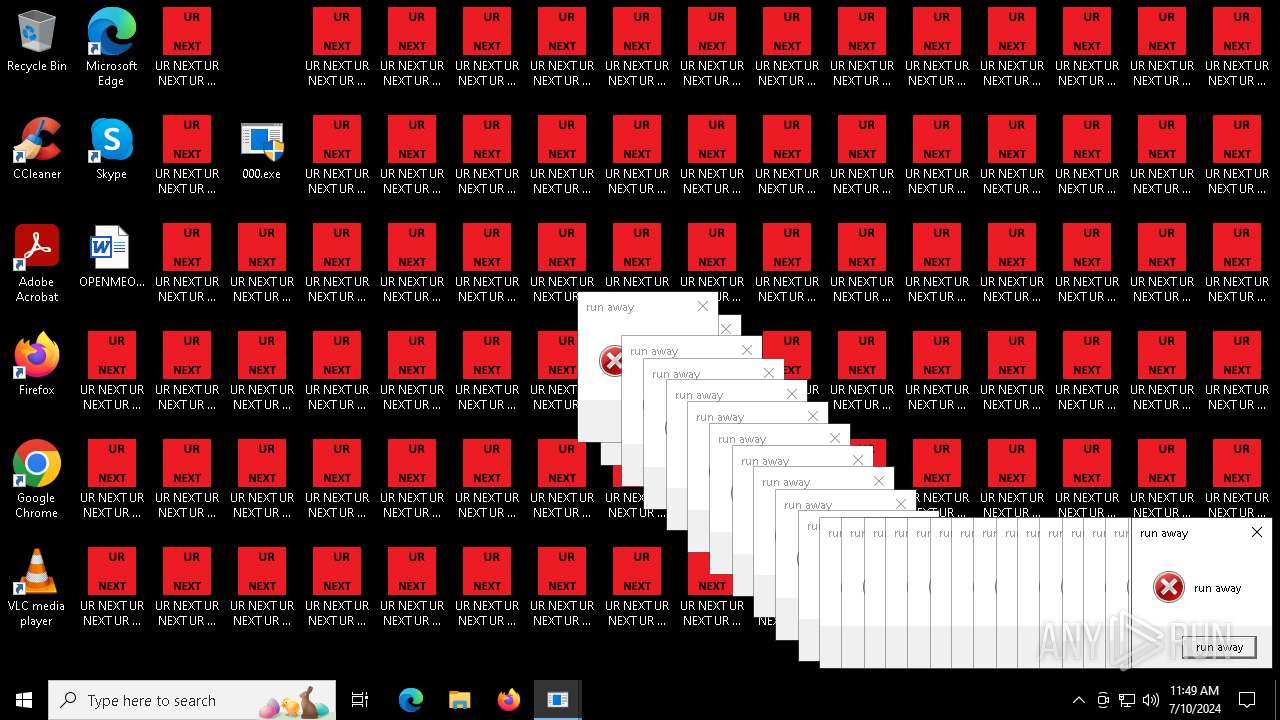
- runaway.exe (PID: 6120)
- runaway.exe (PID: 5300)
- PLUGScheduler.exe (PID: 3152)
- runaway.exe (PID: 1040)
- runaway.exe (PID: 5692)
- runaway.exe (PID: 5448)
- runaway.exe (PID: 5504)
- runaway.exe (PID: 5832)
- runaway.exe (PID: 4568)
- runaway.exe (PID: 6088)
- runaway.exe (PID: 5696)
- runaway.exe (PID: 528)
- runaway.exe (PID: 5328)
- runaway.exe (PID: 5432)
- runaway.exe (PID: 5552)
- runaway.exe (PID: 5336)
- runaway.exe (PID: 480)
- runaway.exe (PID: 732)
- runaway.exe (PID: 1536)
- runaway.exe (PID: 5540)
- runaway.exe (PID: 1052)
- runaway.exe (PID: 2648)
- runaway.exe (PID: 3892)
- runaway.exe (PID: 5796)
- runaway.exe (PID: 2300)
- runaway.exe (PID: 5472)
- runaway.exe (PID: 1152)
- runaway.exe (PID: 4336)
- runaway.exe (PID: 6196)
- runaway.exe (PID: 6512)
- runaway.exe (PID: 6380)
- runaway.exe (PID: 6320)
- runaway.exe (PID: 6260)
- runaway.exe (PID: 6448)
- runaway.exe (PID: 6580)
- runaway.exe (PID: 6644)
- runaway.exe (PID: 7016)
- runaway.exe (PID: 6904)
- runaway.exe (PID: 7088)
- runaway.exe (PID: 7156)
- runaway.exe (PID: 6708)
- runaway.exe (PID: 6772)
- runaway.exe (PID: 6836)
- runaway.exe (PID: 4868)
Checks supported languages
- 000.exe (PID: 4532)
- PLUGScheduler.exe (PID: 3152)
- RUXIMICS.exe (PID: 4520)
- rniw.exe (PID: 5916)
- runaway.exe (PID: 5300)
- RUXIMICS.exe (PID: 6088)
- runaway.exe (PID: 6120)
- runaway.exe (PID: 5448)
- runaway.exe (PID: 5336)
- runaway.exe (PID: 1040)
- runaway.exe (PID: 5692)
- runaway.exe (PID: 5832)
- runaway.exe (PID: 5696)
- runaway.exe (PID: 4568)
- runaway.exe (PID: 528)
- runaway.exe (PID: 6088)
- runaway.exe (PID: 5552)
- runaway.exe (PID: 5328)
- runaway.exe (PID: 5432)
- runaway.exe (PID: 5504)
- runaway.exe (PID: 732)
- runaway.exe (PID: 1052)
- runaway.exe (PID: 5540)
- runaway.exe (PID: 2300)
- runaway.exe (PID: 1536)
- runaway.exe (PID: 2648)
- runaway.exe (PID: 3892)
- runaway.exe (PID: 5796)
- runaway.exe (PID: 4336)
- runaway.exe (PID: 480)
- runaway.exe (PID: 5472)
- runaway.exe (PID: 1152)
- runaway.exe (PID: 6196)
- runaway.exe (PID: 6512)
- runaway.exe (PID: 6448)
- runaway.exe (PID: 6320)
- runaway.exe (PID: 6380)
- runaway.exe (PID: 6260)
- runaway.exe (PID: 6580)
- runaway.exe (PID: 6644)
- runaway.exe (PID: 6904)
- runaway.exe (PID: 7016)
- runaway.exe (PID: 4868)
- runaway.exe (PID: 7156)
- runaway.exe (PID: 6708)
- runaway.exe (PID: 6772)
- runaway.exe (PID: 6836)
- runaway.exe (PID: 7088)
Creates files in the program directory
- cmd.exe (PID: 5460)
- PLUGScheduler.exe (PID: 3152)
- 000.exe (PID: 4532)
- RUXIMICS.exe (PID: 6088)
Create files in a temporary directory
- 000.exe (PID: 4532)
- rniw.exe (PID: 5916)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4536)
- WMIC.exe (PID: 3976)
Creates files or folders in the user directory
- 000.exe (PID: 4532)
Checks proxy server information
- 000.exe (PID: 4532)
Reads Environment values
- RUXIMICS.exe (PID: 4520)
Manual execution by a user
- rniw.exe (PID: 5916)
Process checks computer location settings
- rniw.exe (PID: 5916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:09:22 13:02:11+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 6978560 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a9a8e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | 000 |
| FileVersion: | 0.0.0.0 |
| InternalName: | 000.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | 000.exe |
| ProductName: | 000 |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
323
Monitored processes
101
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | runaway.exe | C:\Users\admin\AppData\Local\Temp\9B46.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 528 | runaway.exe | C:\Users\admin\AppData\Local\Temp\9B46.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 732 | runaway.exe | C:\Users\admin\AppData\Local\Temp\9B46.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 856 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | runaway.exe | C:\Users\admin\AppData\Local\Temp\9B46.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1052 | runaway.exe | C:\Users\admin\AppData\Local\Temp\9B46.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1132 | taskkill /f /im explorer.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1152 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1152 | runaway.exe | C:\Users\admin\AppData\Local\Temp\9B46.tmp\runaway.exe | — | cmd.exe | |||||||||||
User: UR NEXT Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1164 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: UR NEXT Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 544
Read events
19 435
Write events
108
Delete events
1
Modification events
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | AutoRestartShell |
Value: 0 | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | UniqueID |
Value: {6C1125E9-8A67-48A2-B8F8-9184A4CB7692} | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | ComputerName |
Value: DESKTOP-JGLLJLD | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | VolumeSerialNumber |
Value: 649566714 | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Player\Settings |
| Operation: | delete value | Name: | Client ID |
Value: {CECDFD5C-8F08-4FEF-8713-FAA895A422EB} | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalBase |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | DTDFile |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | |||
| (PID) Process: | (4532) 000.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalDelta |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | |||
Executable files
3
Suspicious files
48
Text files
410
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4532 | 000.exe | C:\Users\admin\AppData\Local\Temp\windl.bat | text | |
MD5:A9401E260D9856D1134692759D636E92 | SHA256:B551FBA71DFD526D4916AE277D8686D83FFF36D22FCF6F18457924A070B30EF7 | |||
| 4532 | 000.exe | C:\Users\admin\AppData\Local\Temp\icon.ico | image | |
MD5:A4B9662CF3B6EA6626F6081C0D8C13F3 | SHA256:84A1C2713642090523F05D9FB015C537FD210D3200CADAF442BB67CF1834B356 | |||
| 4532 | 000.exe | C:\Users\admin\AppData\Local\Temp\text.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 5460 | cmd.exe | C:\Users\admin\Desktop\UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR N4XT.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 5460 | cmd.exe | C:\Users\admin\Desktop\UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR N5XT.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 5460 | cmd.exe | C:\Users\admin\Desktop\UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR NEXT UR N0XT.txt | text | |
MD5:9037EBF0A18A1C17537832BC73739109 | SHA256:38C889B5D7BDCB79BBCB55554C520A9CE74B5BFC29C19D1E4CB1419176C99F48 | |||
| 4532 | 000.exe | C:\Users\admin\AppData\Local\Temp\rniw.exe | executable | |
MD5:9232120B6FF11D48A90069B25AA30ABC | SHA256:70FAA0E1498461731F873D3594F20CBF2BEAA6F123A06B66F9DF59A9CDF862BE | |||
| 4532 | 000.exe | C:\Users\admin\AppData\Local\Temp\one.rtf | text | |
MD5:6FBD6CE25307749D6E0A66EBBC0264E7 | SHA256:E152B106733D9263D3CF175F0B6197880D70ACB753F8BDE8035A3E4865B31690 | |||
| 4532 | 000.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | text | |
MD5:5433EAB10C6B5C6D55B7CBD302426A39 | SHA256:23DBF7014E99E93AF5F2760F18EE1370274F06A453145C8D539B66D798DAD131 | |||
| 4532 | 000.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | xml | |
MD5:90BE2701C8112BEBC6BD58A7DE19846E | SHA256:644FBCDC20086E16D57F31C5BAD98BE68D02B1C061938D2F5F91CBE88C871FBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report