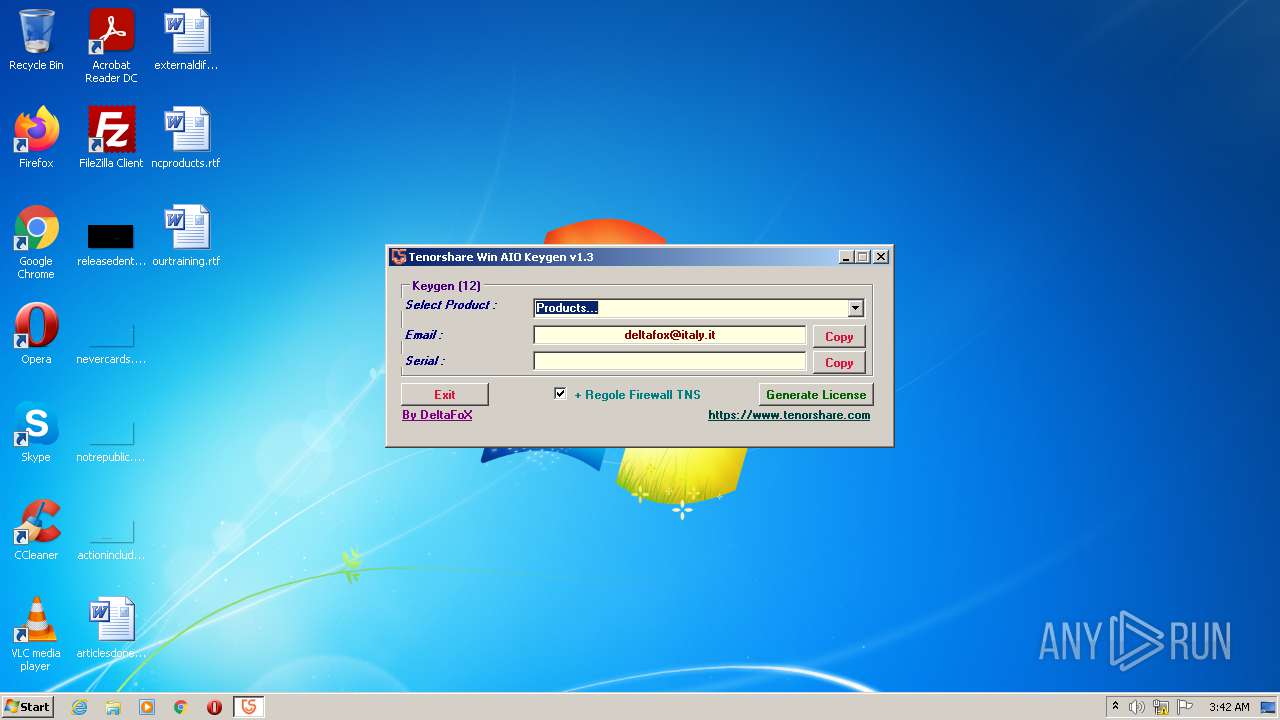
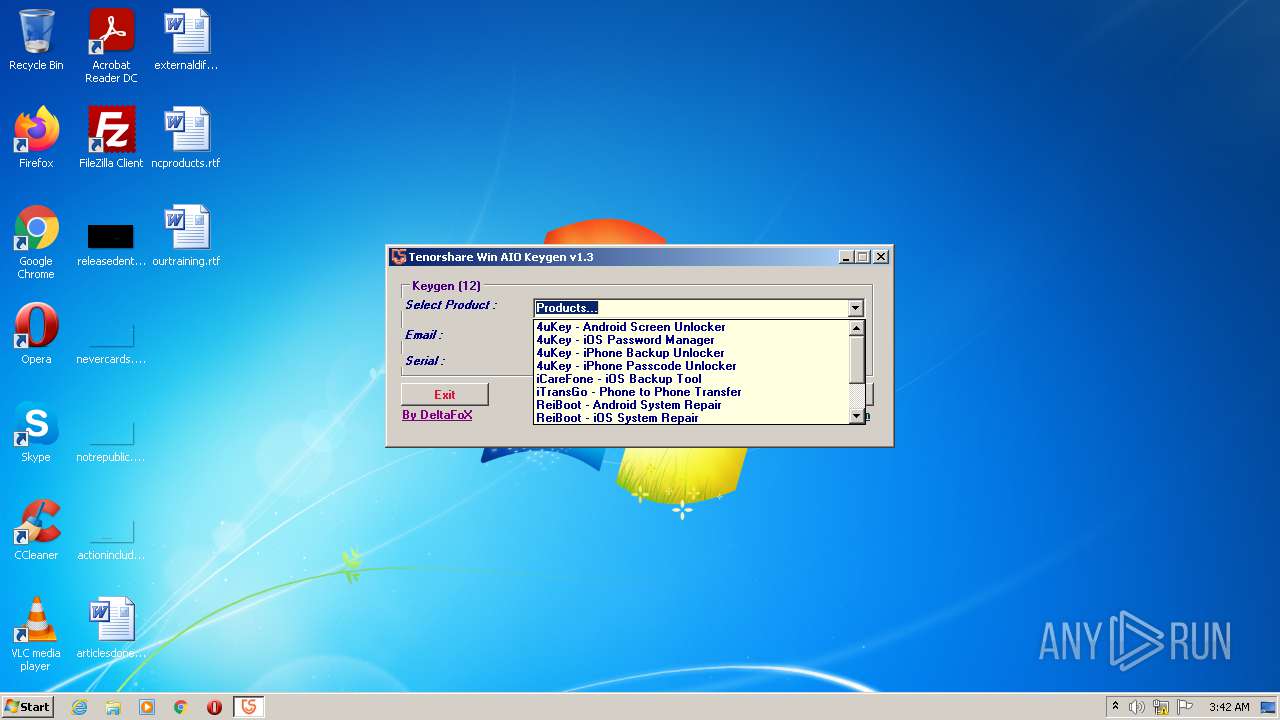
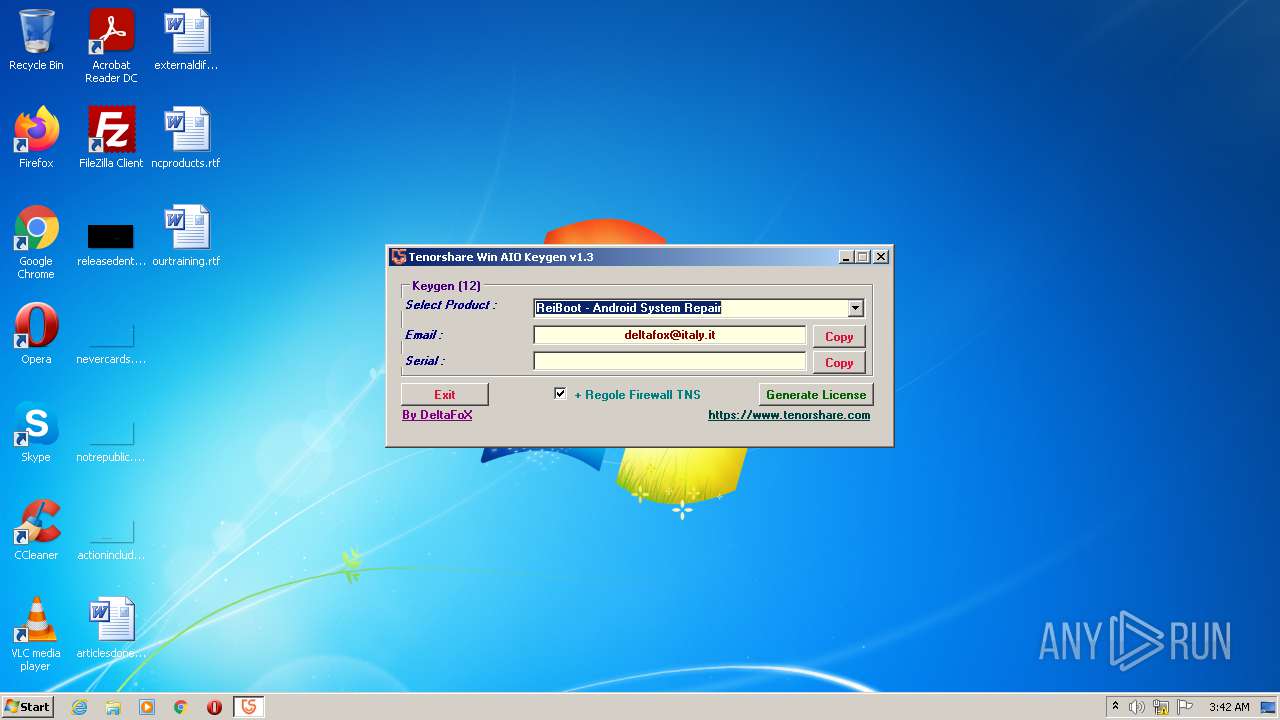
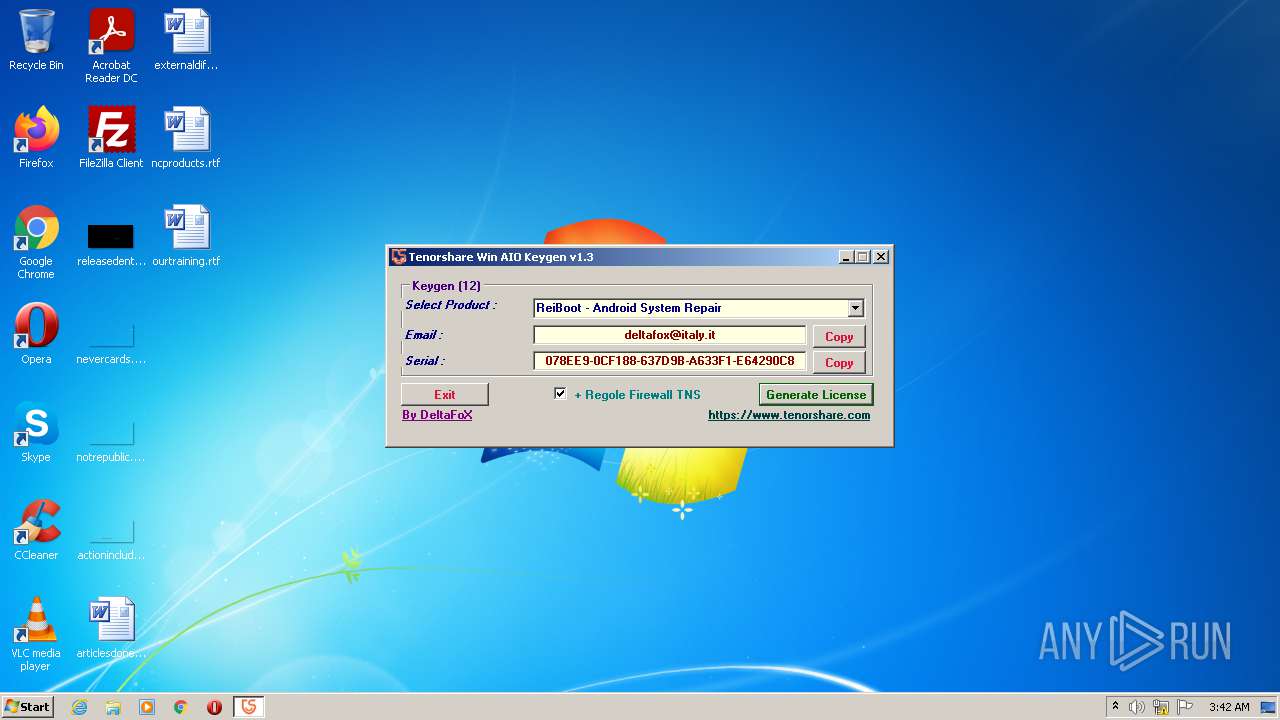
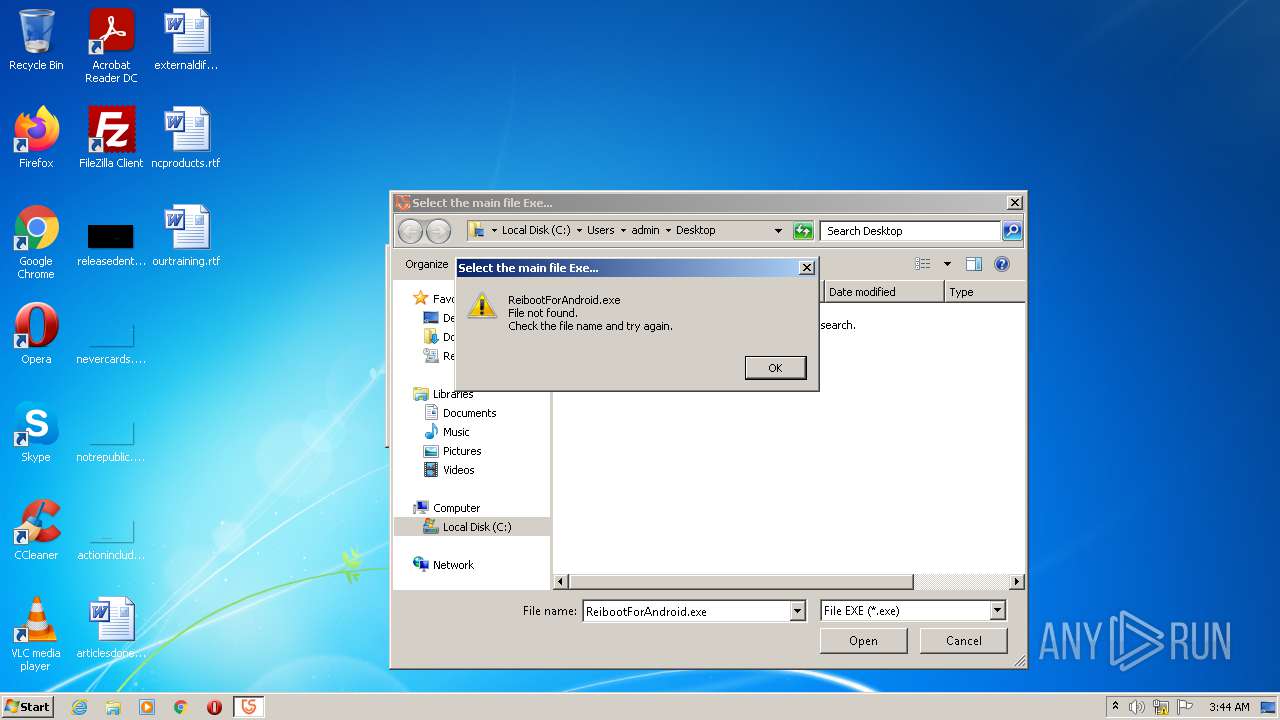
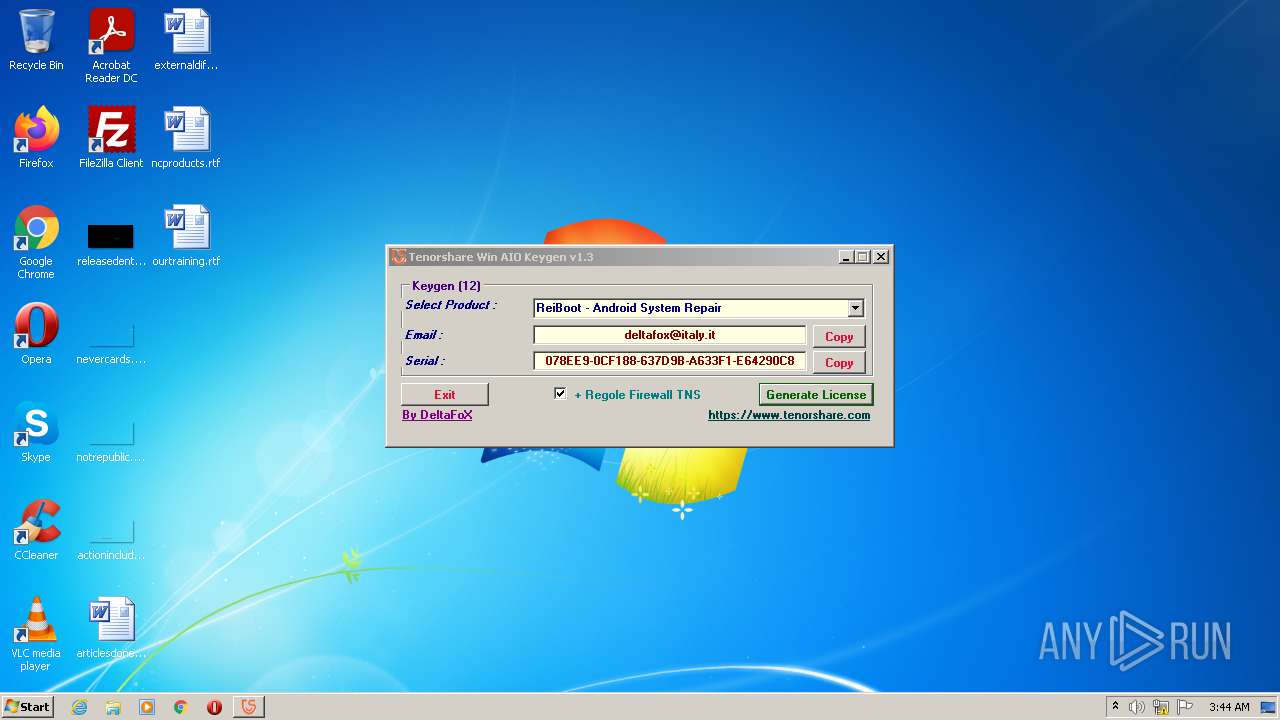
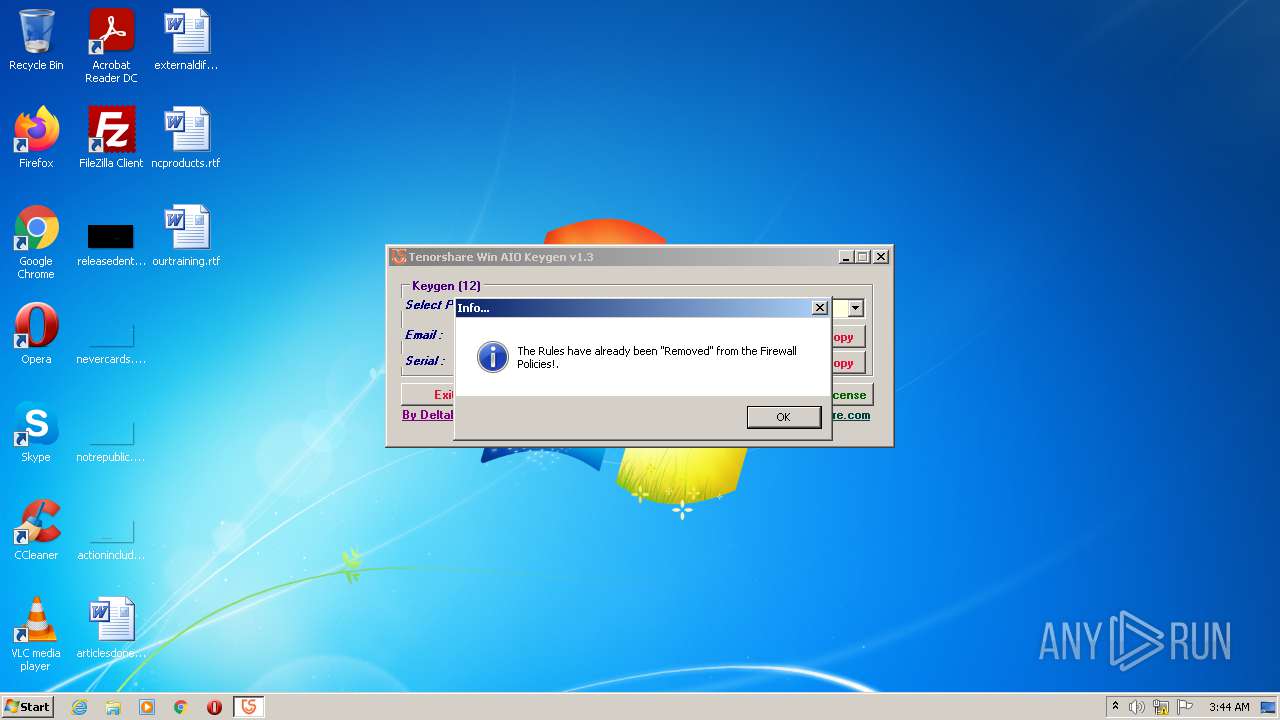
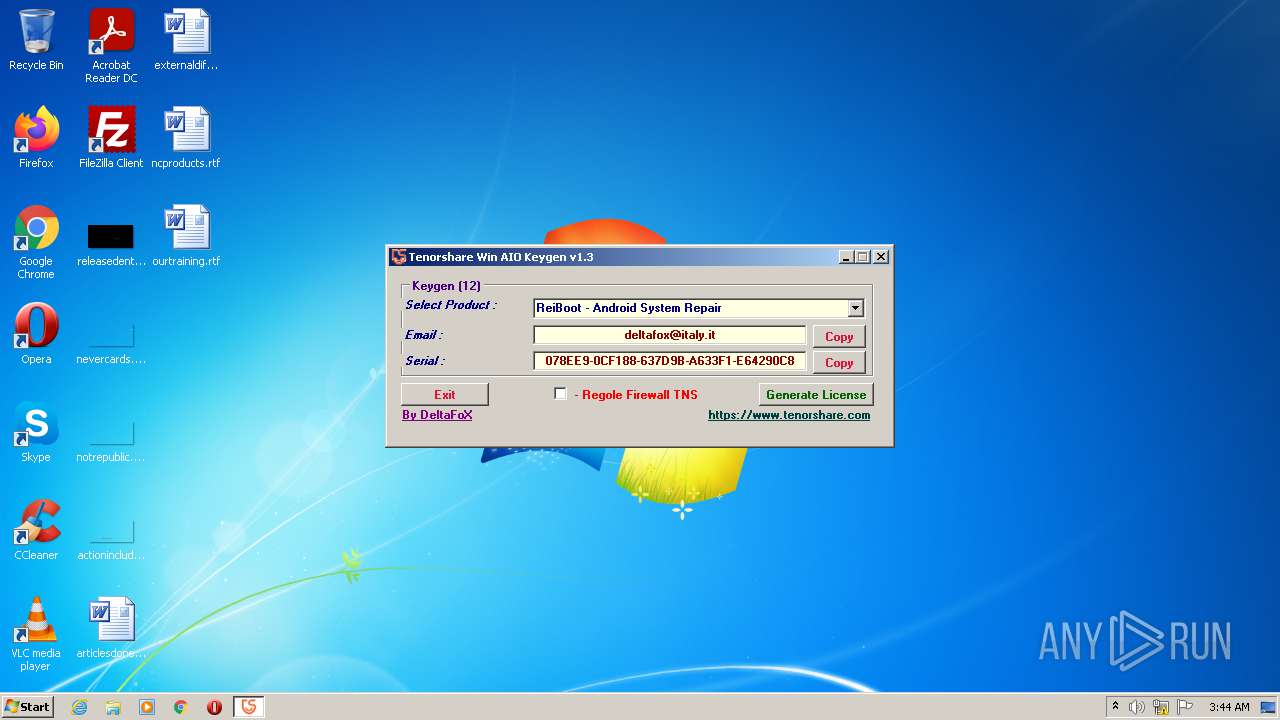
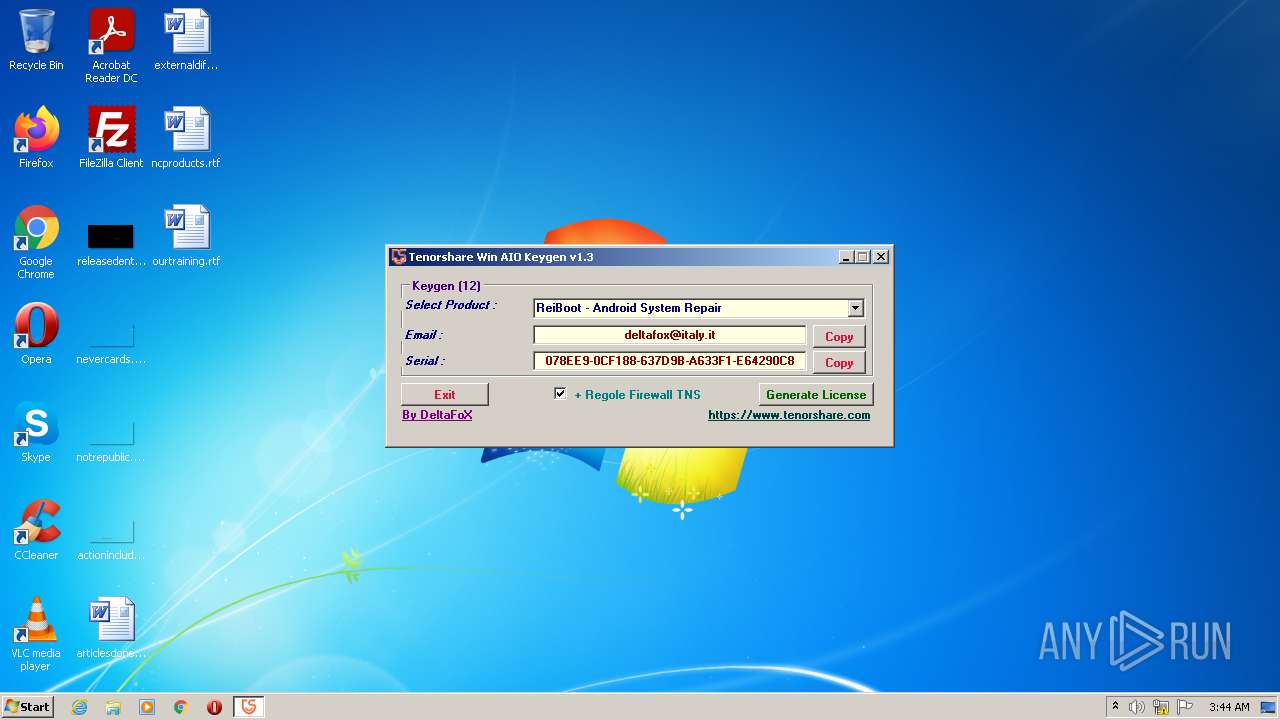
| File name: | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe |
| Full analysis: | https://app.any.run/tasks/1ea97696-943a-492b-9cdd-37ddc332e813 |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2021, 03:41:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 799F58A6C68E17378FADAB1B839A5BD0 |
| SHA1: | D831477A87B7F798402D3A57DC80B58CD4BF5F4A |
| SHA256: | 4E9E3296030DF5EADED9C3E7522A956342361A6AACD8C148A98F01B3F8FDCA34 |
| SSDEEP: | 6144:AMlJRN1lT6G2MAadgtN32flllMHggg6ggg6ggg6ggg4gvO0OlllMHggg6ggg6gg7:NXNvk2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2960)
Reads the computer name
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 3548)
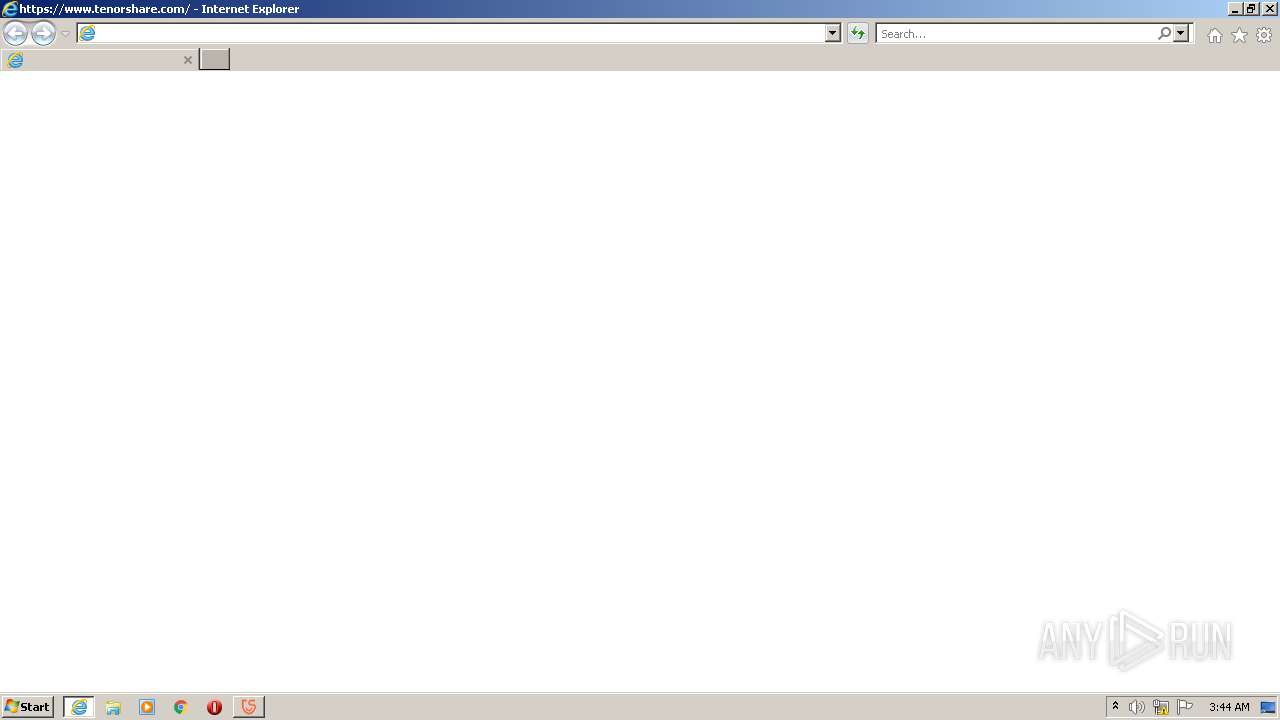
Starts Internet Explorer
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 3548)
Checks supported languages
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 3548)
INFO
Checks Windows Trust Settings
- iexplore.exe (PID: 2960)
Checks supported languages
- iexplore.exe (PID: 2960)
- iexplore.exe (PID: 772)
Changes internet zones settings
- iexplore.exe (PID: 772)
Application launched itself
- iexplore.exe (PID: 772)
Reads the computer name
- iexplore.exe (PID: 2960)
- iexplore.exe (PID: 772)
Reads settings of System Certificates
- iexplore.exe (PID: 2960)
Reads the date of Windows installation
- iexplore.exe (PID: 772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (49) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (20.9) |
| .exe | | | Win64 Executable (generic) (18.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.4) |
| .exe | | | Win32 Executable (generic) (3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2104:09:19 15:57:51+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 218112 |
| InitializedDataSize: | 112640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x373ae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.0 |
| ProductVersionNumber: | 1.3.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Keygen for all Win 12 Tenorshare Products |
| CompanyName: | DeFconX |
| FileDescription: | Tenorshare_Aio_Keygen_By_DFoX |
| FileVersion: | 1.3.0.0 |
| InternalName: | Tenorshare_Aio_Keygen_By_DFoX.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | DeltaFoX |
| OriginalFileName: | Tenorshare_Aio_Keygen_By_DFoX.exe |
| ProductName: | Tenorshare_Aio_Keygen_By_DFoX |
| ProductVersion: | 1.3.0.0 |
| AssemblyVersion: | 1.3.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 13-Aug-1968 07:29:35 |
| Debug artifacts: |
|
| Comments: | Keygen for all Win 12 Tenorshare Products |
| CompanyName: | DeFconX |
| FileDescription: | Tenorshare_Aio_Keygen_By_DFoX |
| FileVersion: | 1.3.0.0 |
| InternalName: | Tenorshare_Aio_Keygen_By_DFoX.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | DeltaFoX |
| OriginalFilename: | Tenorshare_Aio_Keygen_By_DFoX.exe |
| ProductName: | Tenorshare_Aio_Keygen_By_DFoX |
| ProductVersion: | 1.3.0.0 |
| Assembly Version: | 1.3.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 13-Aug-1968 07:29:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x000353B4 | 0x00035400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.78669 |
.sdata | 0x00038000 | 0x00000162 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.99892 |
.rsrc | 0x0003A000 | 0x0001B2D8 | 0x0001B400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.53345 |
.reloc | 0x00056000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.988 | 3481 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.03411 | 67624 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 5.38056 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 5.61813 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 5.88213 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 6.39159 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.79908 | 90 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
41
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 772 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.tenorshare.com/ | C:\Program Files\Internet Explorer\iexplore.exe | — | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2604 | "C:\Users\admin\AppData\Local\Temp\Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe" | C:\Users\admin\AppData\Local\Temp\Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | — | Explorer.EXE | |||||||||||
User: admin Company: DeFconX Integrity Level: MEDIUM Description: Tenorshare_Aio_Keygen_By_DFoX Exit code: 3221226540 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2960 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:772 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3548 | "C:\Users\admin\AppData\Local\Temp\Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe" | C:\Users\admin\AppData\Local\Temp\Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Explorer.EXE | ||||||||||||
User: admin Company: DeFconX Integrity Level: HIGH Description: Tenorshare_Aio_Keygen_By_DFoX Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
Total events
11 902
Read events
11 702
Write events
194
Delete events
6
Modification events
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 010000000D000000020000000C000000000000000B00000007000000060000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0 |
| Operation: | write | Name: | MRUListEx |
Value: 000000000200000004000000050000000100000003000000FFFFFFFF | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\0\0 |
| Operation: | write | Name: | 2 |
Value: 7A00310000000000E152696B11004465736B746F7000640008000400EFBE454B814AE152696B2A0000007B0100000000020000000000000000003A00000000004400650073006B0074006F007000000040007300680065006C006C00330032002E0064006C006C002C002D0032003100370036003900000016000000 | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\0\0 |
| Operation: | write | Name: | MRUListEx |
Value: 020000000000000001000000FFFFFFFF | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\0\0\2 |
| Operation: | write | Name: | NodeSlot |
Value: 184 | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\0\0\2 |
| Operation: | write | Name: | MRUListEx |
Value: FFFFFFFF | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\184\Shell |
| Operation: | write | Name: | KnownFolderDerivedFolderType |
Value: {57807898-8C4F-4462-BB63-71042380B109} | |||
| (PID) Process: | (3548) Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\184\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
Executable files
0
Suspicious files
7
Text files
0
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Last Active\RecoveryStore.{00617898-3F7D-11EC-A58B-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Last Active\{00617899-3F7D-11EC-A58B-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | binary | |
MD5:— | SHA256:— | |||
| 2960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | der | |
MD5:— | SHA256:— | |||
| 772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCA66E877039ADC12.TMP | gmc | |
MD5:— | SHA256:— | |||
| 772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\RecoveryStore.{00617895-3F7D-11EC-A58B-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1FE7CDCBACEFDCE4.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFFB22693DB3E63319.TMP | gmc | |
MD5:— | SHA256:— | |||
| 772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{00617897-3F7D-11EC-A58B-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2960 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2960 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f89cf2f6f375c2bc | US | compressed | 4.70 Kb | whitelisted |
2960 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?eb76e74152e78459 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2960 | iexplore.exe | 104.18.24.249:443 | www.tenorshare.com | Cloudflare Inc | US | suspicious |
2960 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2960 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.tenorshare.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |