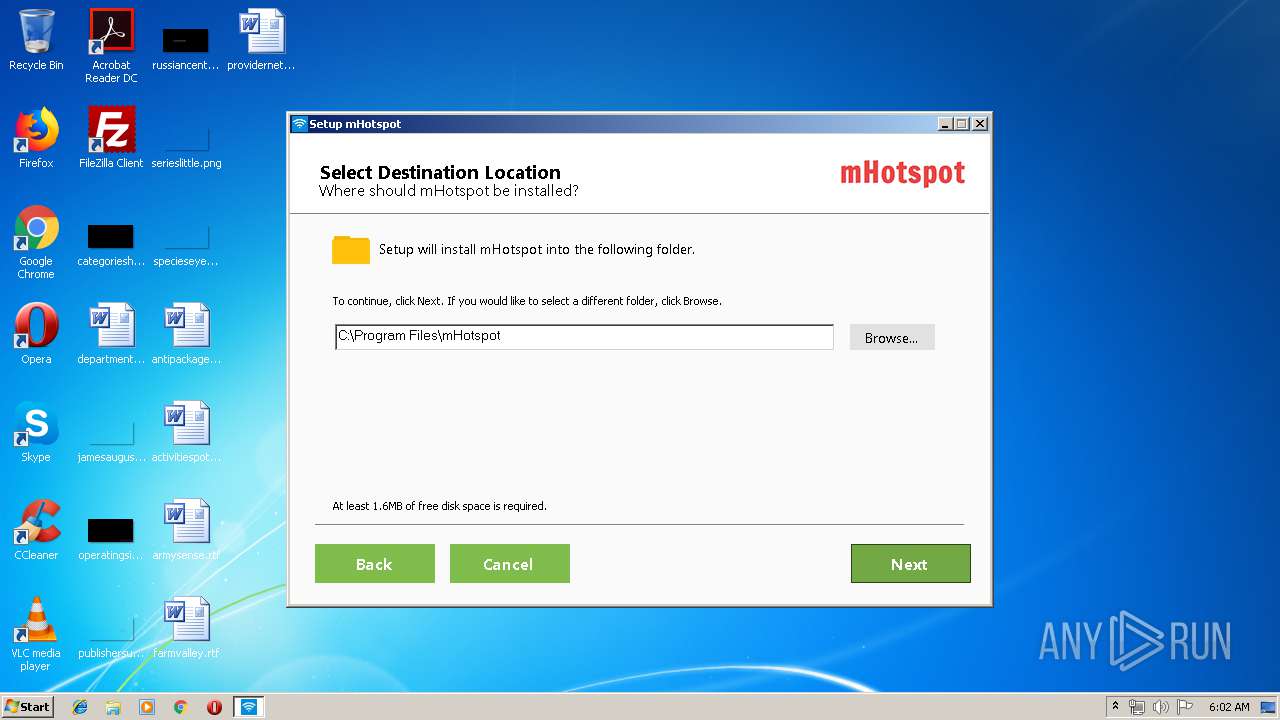
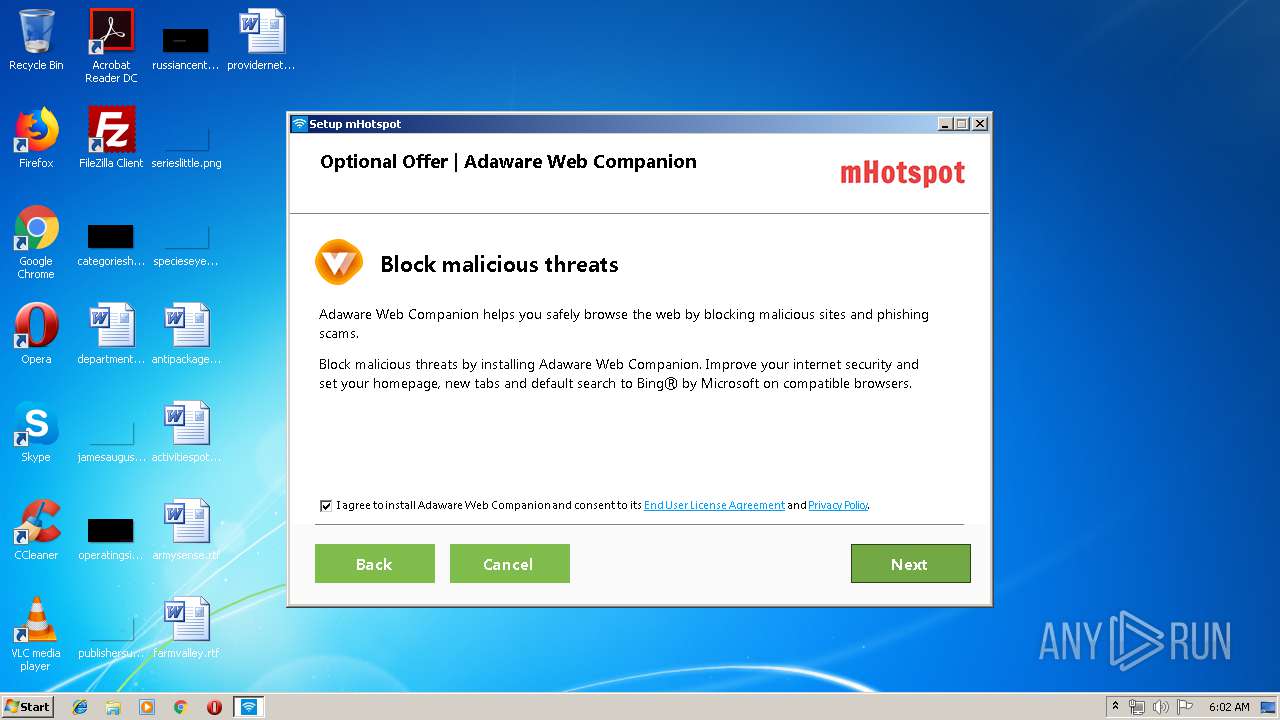
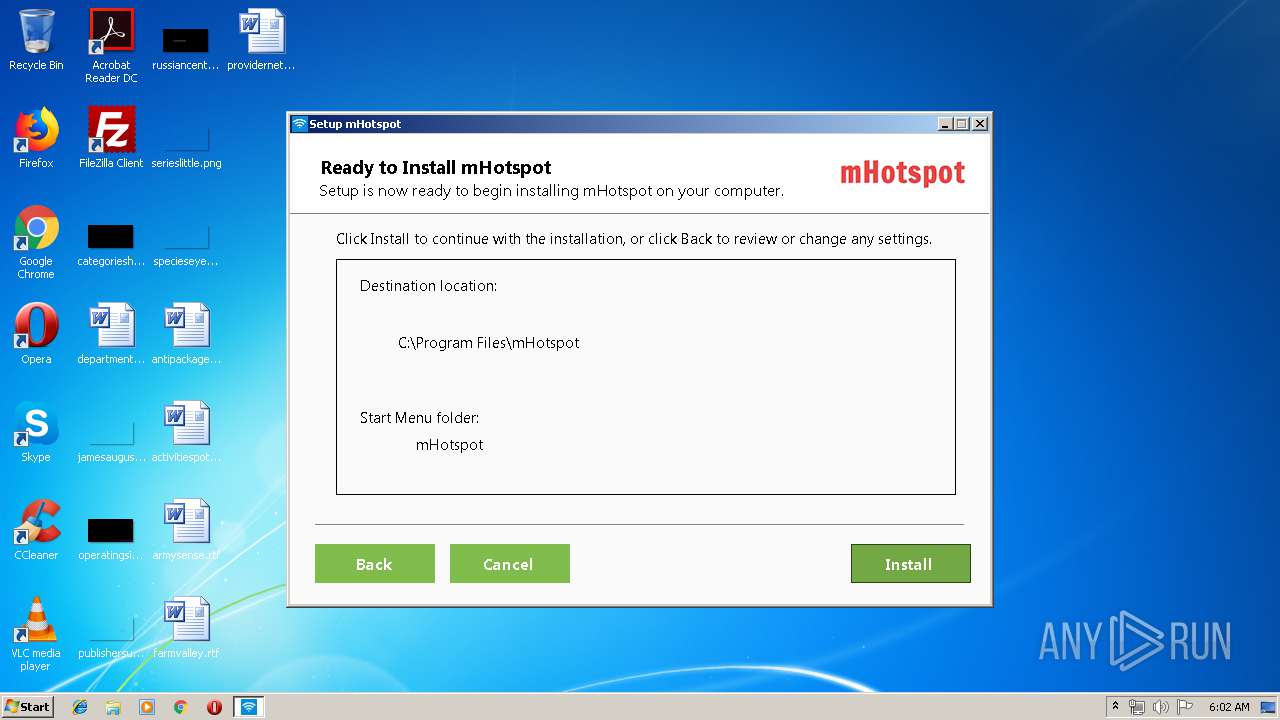
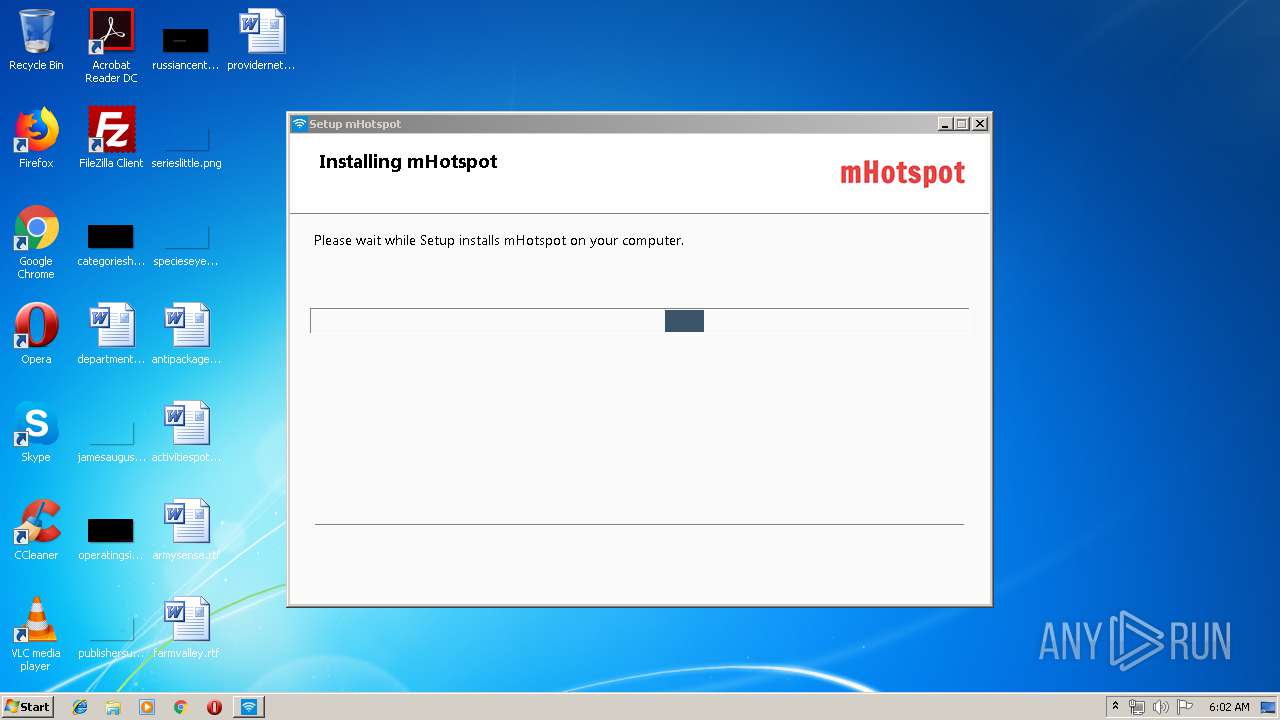
| File name: | mHotspot_setup_latest_2.exe |
| Full analysis: | https://app.any.run/tasks/0c02f848-be87-4025-92f1-e4360703edca |
| Verdict: | Malicious activity |
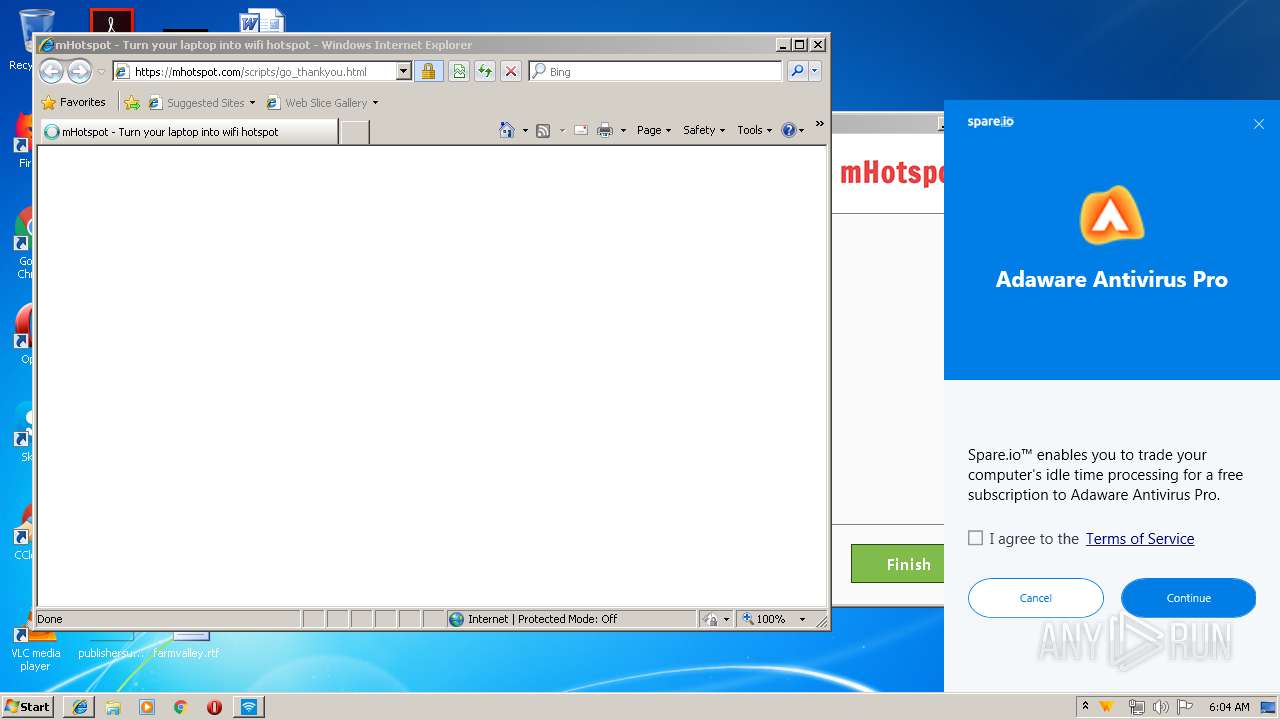
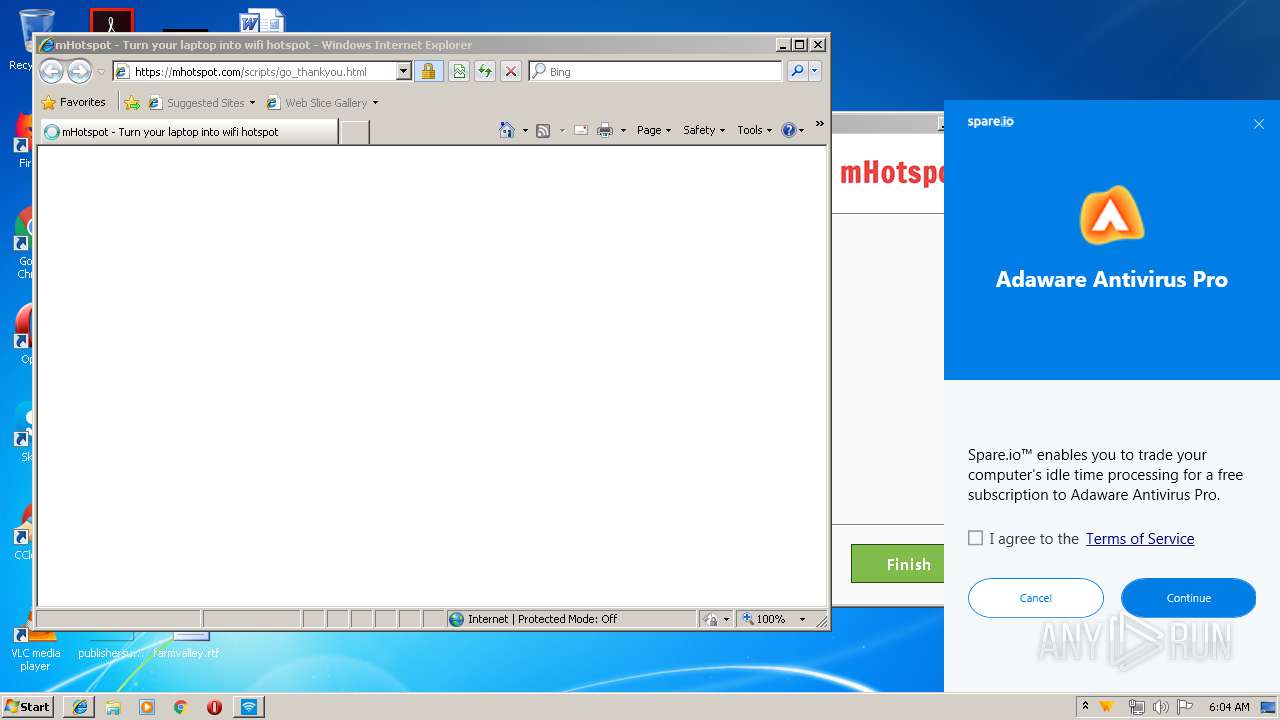
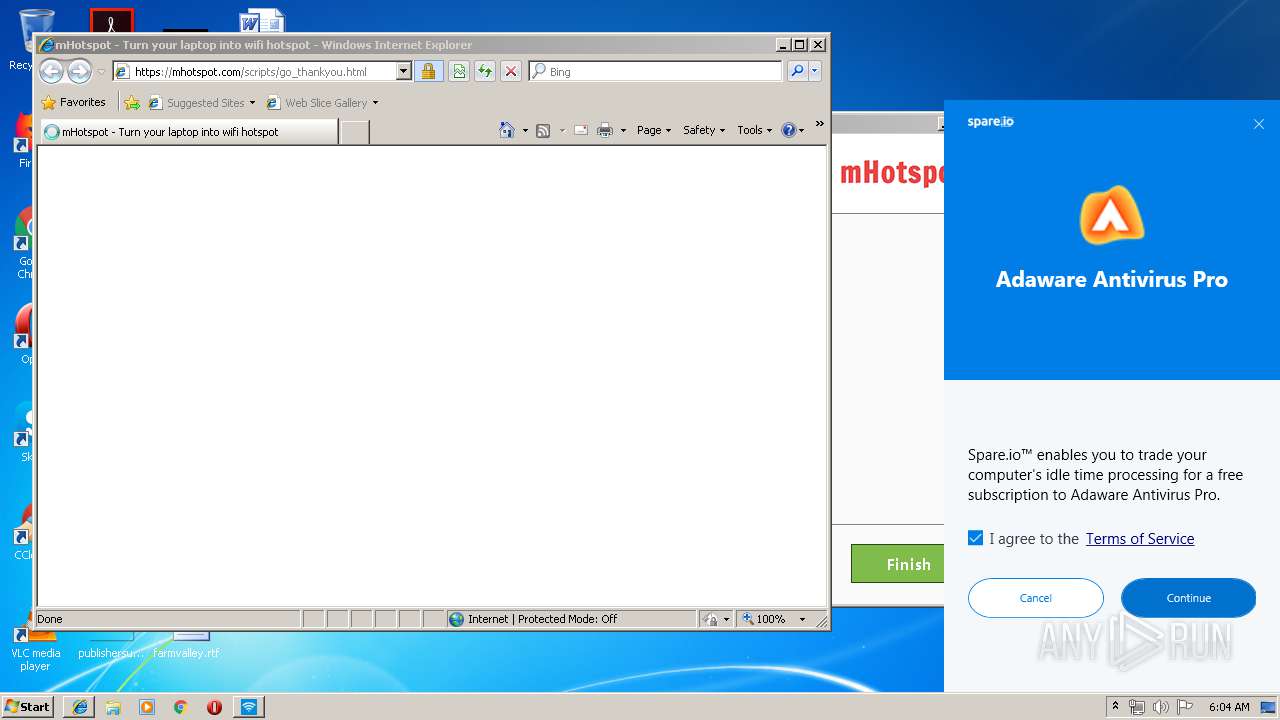
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | April 27, 2019, 05:01:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 67303E6191E0D251D7FBACE129E7BA62 |
| SHA1: | 1F6890B0CF4D6497C3A352E8ED033D44B8396D4A |
| SHA256: | 4E8BC297E8BBB7F2D818B55234A82E198667AA25D2C69785D121396108A7D08C |
| SSDEEP: | 24576:XG50ZfFK84agNXQ1g5JruMCapWPTFHic3wxqhade3e6FMoAmEkeEzFvlqOoP54jS:XG5UfgnZ5XWapKTX3phade3Fj3E6zF7Y |
MALICIOUS
Application was dropped or rewritten from another process
- installer.exe (PID: 948)
- GenericSetup.exe (PID: 1740)
- Carrier.exe (PID: 3932)
- wwqbmdhq.ctz.exe (PID: 1972)
- c4c554lp.hmc.exe (PID: 2820)
- WebCompanionInstaller.exe (PID: 2920)
- SpareioInstaller.exe (PID: 1832)
- SpareioInstaller.exe (PID: 2068)
- SpareioWinService.exe (PID: 876)
- Spareio.exe (PID: 2456)
- Spareio.exe (PID: 3884)
- WebCompanion.exe (PID: 3524)
- Lavasoft.WCAssistant.WinService.exe (PID: 2228)
- Ad-Aware Web Companion.exe (PID: 3188)
- WebCompanion.exe (PID: 1648)
- 0gbxa5iq.0v3.exe (PID: 3956)
- avast_free_antivirus_setup_online.exe (PID: 2448)
- instup.exe (PID: 2460)
- instup.exe (PID: 2156)
- sbr.exe (PID: 4080)
- SetupInf.exe (PID: 3172)
- SetupInf.exe (PID: 3984)
- SetupInf.exe (PID: 3936)
- SetupInf.exe (PID: 3712)
- AvEmUpdate.exe (PID: 2180)
- AvEmUpdate.exe (PID: 2688)
- mHotspot.exe (PID: 3764)
- AvEmUpdate.exe (PID: 3952)
- AvEmUpdate.exe (PID: 2584)
- CCUpdate.exe (PID: 460)
- avBugReport.exe (PID: 3160)
- CCUpdate.exe (PID: 3664)
- CCUpdate.exe (PID: 3812)
- CCUpdate.exe (PID: 1524)
- AvastNM.exe (PID: 2428)
- overseer.exe (PID: 2988)
- AvastSvc.exe (PID: 2624)
- aswEngSrv.exe (PID: 2116)
- wsc_proxy.exe (PID: 836)
Loads dropped or rewritten executable
- GenericSetup.exe (PID: 1740)
- WebCompanionInstaller.exe (PID: 2920)
- SpareioInstaller.exe (PID: 2068)
- SpareioWinService.exe (PID: 876)
- WebCompanion.exe (PID: 3524)
- Spareio.exe (PID: 2456)
- Spareio.exe (PID: 3884)
- Lavasoft.WCAssistant.WinService.exe (PID: 2228)
- WebCompanion.exe (PID: 1648)
- instup.exe (PID: 2460)
- instup.exe (PID: 2156)
- AvEmUpdate.exe (PID: 2180)
- AvEmUpdate.exe (PID: 2584)
- AvEmUpdate.exe (PID: 3952)
- AvEmUpdate.exe (PID: 2688)
- avBugReport.exe (PID: 3160)
- RegSvr.exe (PID: 1212)
- RegSvr.exe (PID: 184)
- aswRunDll.exe (PID: 776)
- engsup.exe (PID: 1256)
- engsup.exe (PID: 1688)
- AvastSvc.exe (PID: 2624)
- aswEngSrv.exe (PID: 2116)
LAVASOFT was detected
- installer.exe (PID: 948)
Changes settings of System certificates
- GenericSetup.exe (PID: 1740)
- wwqbmdhq.ctz.exe (PID: 1972)
- AvastSvc.exe (PID: 2624)
Downloads executable files from the Internet
- GenericSetup.exe (PID: 1740)
- 0gbxa5iq.0v3.exe (PID: 3956)
- AvEmUpdate.exe (PID: 2688)
- CCUpdate.exe (PID: 3664)
Changes internet zones settings
- WebCompanionInstaller.exe (PID: 2920)
Changes the autorun value in the registry
- Spareio.exe (PID: 2456)
- WebCompanion.exe (PID: 3524)
- instup.exe (PID: 2156)
Loads the Task Scheduler COM API
- AvEmUpdate.exe (PID: 2180)
- AvEmUpdate.exe (PID: 2688)
- CCUpdate.exe (PID: 3664)
- CCUpdate.exe (PID: 920)
- overseer.exe (PID: 2988)
SUSPICIOUS
Reads Windows owner or organization settings
- GenericSetup.exe (PID: 1740)
Executable content was dropped or overwritten
- mHotspot_setup_latest_2.exe (PID: 2408)
- Carrier.tmp (PID: 2828)
- Carrier.exe (PID: 3932)
- GenericSetup.exe (PID: 1740)
- c4c554lp.hmc.exe (PID: 2820)
- wwqbmdhq.ctz.exe (PID: 1972)
- SpareioInstaller.exe (PID: 1832)
- WebCompanionInstaller.exe (PID: 2920)
- SpareioInstaller.exe (PID: 2068)
- 0gbxa5iq.0v3.exe (PID: 3956)
- avast_free_antivirus_setup_online.exe (PID: 2448)
- instup.exe (PID: 2460)
- instup.exe (PID: 2156)
- AvEmUpdate.exe (PID: 2688)
- AvEmUpdate.exe (PID: 2584)
- SpareioWinService.exe (PID: 876)
- CCUpdate.exe (PID: 460)
- CCUpdate.exe (PID: 3812)
- AvastSvc.exe (PID: 2624)
Adds / modifies Windows certificates
- GenericSetup.exe (PID: 1740)
- wwqbmdhq.ctz.exe (PID: 1972)
Reads the Windows organization settings
- GenericSetup.exe (PID: 1740)
Reads Environment values
- GenericSetup.exe (PID: 1740)
- SpareioInstaller.exe (PID: 2068)
- SpareioWinService.exe (PID: 876)
- Spareio.exe (PID: 2456)
- Spareio.exe (PID: 3884)
- AvastSvc.exe (PID: 2624)
Starts Internet Explorer
- Carrier.tmp (PID: 2828)
Starts CMD.EXE for commands execution
- GenericSetup.exe (PID: 1740)
- WebCompanionInstaller.exe (PID: 2920)
- SpareioWinService.exe (PID: 876)
- Lavasoft.WCAssistant.WinService.exe (PID: 2228)
Creates files in the program directory
- WebCompanionInstaller.exe (PID: 2920)
- SpareioInstaller.exe (PID: 2068)
- SpareioWinService.exe (PID: 876)
- Spareio.exe (PID: 2456)
- WebCompanion.exe (PID: 3524)
- Lavasoft.WCAssistant.WinService.exe (PID: 2228)
- WebCompanion.exe (PID: 1648)
- avast_free_antivirus_setup_online.exe (PID: 2448)
- instup.exe (PID: 2460)
- AvEmUpdate.exe (PID: 2180)
- AvEmUpdate.exe (PID: 2688)
- CCUpdate.exe (PID: 460)
- instup.exe (PID: 2156)
- CCUpdate.exe (PID: 3664)
- CCUpdate.exe (PID: 920)
- CCUpdate.exe (PID: 3812)
- avBugReport.exe (PID: 3160)
- AvastNM.exe (PID: 2428)
- dw20.exe (PID: 1464)
- engsup.exe (PID: 1256)
- AvastSvc.exe (PID: 2624)
- engsup.exe (PID: 1688)
- wsc_proxy.exe (PID: 836)
Starts SC.EXE for service management
- SpareioInstaller.exe (PID: 2068)
- WebCompanionInstaller.exe (PID: 2920)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3404)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 2148)
Creates files in the user directory
- WebCompanionInstaller.exe (PID: 2920)
- Spareio.exe (PID: 2456)
- SpareioWinService.exe (PID: 876)
- Spareio.exe (PID: 3884)
- WebCompanion.exe (PID: 3524)
Creates a software uninstall entry
- SpareioInstaller.exe (PID: 2068)
- WebCompanionInstaller.exe (PID: 2920)
- instup.exe (PID: 2156)
- AvEmUpdate.exe (PID: 2584)
Searches for installed software
- SpareioWinService.exe (PID: 876)
- SpareioInstaller.exe (PID: 2068)
- GenericSetup.exe (PID: 1740)
Reads Internet Cache Settings
- Spareio.exe (PID: 3884)
- instup.exe (PID: 2156)
Creates files in the Windows directory
- Lavasoft.WCAssistant.WinService.exe (PID: 2228)
- WebCompanion.exe (PID: 3524)
- 0gbxa5iq.0v3.exe (PID: 3956)
- WebCompanionInstaller.exe (PID: 2920)
- avast_free_antivirus_setup_online.exe (PID: 2448)
- instup.exe (PID: 2460)
- instup.exe (PID: 2156)
- AvEmUpdate.exe (PID: 2688)
- AvastSvc.exe (PID: 2624)
Removes files from Windows directory
- Lavasoft.WCAssistant.WinService.exe (PID: 2228)
- WebCompanionInstaller.exe (PID: 2920)
- instup.exe (PID: 2460)
- instup.exe (PID: 2156)
- AvEmUpdate.exe (PID: 2688)
- avast_free_antivirus_setup_online.exe (PID: 2448)
Changes the started page of IE
- WebCompanion.exe (PID: 3524)
Low-level read access rights to disk partition
- 0gbxa5iq.0v3.exe (PID: 3956)
- avast_free_antivirus_setup_online.exe (PID: 2448)
- instup.exe (PID: 2460)
- instup.exe (PID: 2156)
- AvEmUpdate.exe (PID: 2688)
- AvEmUpdate.exe (PID: 3952)
- AvEmUpdate.exe (PID: 2584)
- CCUpdate.exe (PID: 460)
- CCUpdate.exe (PID: 3812)
- CCUpdate.exe (PID: 1524)
- CCUpdate.exe (PID: 3664)
- CCUpdate.exe (PID: 920)
- avBugReport.exe (PID: 3160)
- overseer.exe (PID: 2988)
- AvastSvc.exe (PID: 2624)
Starts itself from another location
- instup.exe (PID: 2460)
- CCUpdate.exe (PID: 3812)
Creates COM task schedule object
- instup.exe (PID: 2156)
- RegSvr.exe (PID: 184)
- RegSvr.exe (PID: 1212)
Creates files in the driver directory
- instup.exe (PID: 2156)
- AvEmUpdate.exe (PID: 2688)
Modifies the open verb of a shell class
- instup.exe (PID: 2156)
Creates or modifies windows services
- instup.exe (PID: 2156)
- AvastSvc.exe (PID: 2624)
Application launched itself
- AvEmUpdate.exe (PID: 2688)
- CCUpdate.exe (PID: 3664)
Reads the cookies of Mozilla Firefox
- engsup.exe (PID: 1688)
Reads the cookies of Google Chrome
- engsup.exe (PID: 1688)
INFO
Creates files in the program directory
- Carrier.tmp (PID: 2828)
Creates a software uninstall entry
- Carrier.tmp (PID: 2828)
Application was dropped or rewritten from another process
- Carrier.tmp (PID: 2828)
Loads dropped or rewritten executable
- Carrier.tmp (PID: 2828)
Changes internet zones settings
- iexplore.exe (PID: 3120)
Changes settings of System certificates
- iexplore.exe (PID: 2452)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2452)
Reads internet explorer settings
- iexplore.exe (PID: 2452)
- iexplore.exe (PID: 916)
Reads Internet Cache Settings
- iexplore.exe (PID: 2452)
- iexplore.exe (PID: 916)
Dropped object may contain Bitcoin addresses
- WebCompanionInstaller.exe (PID: 2920)
- SpareioInstaller.exe (PID: 2068)
- WebCompanion.exe (PID: 3524)
- instup.exe (PID: 2156)
Reads settings of System Certificates
- SpareioInstaller.exe (PID: 2068)
- Spareio.exe (PID: 2456)
- Spareio.exe (PID: 3884)
- SpareioWinService.exe (PID: 876)
Creates files in the user directory
- iexplore.exe (PID: 3120)
- iexplore.exe (PID: 916)
Application launched itself
- iexplore.exe (PID: 3120)
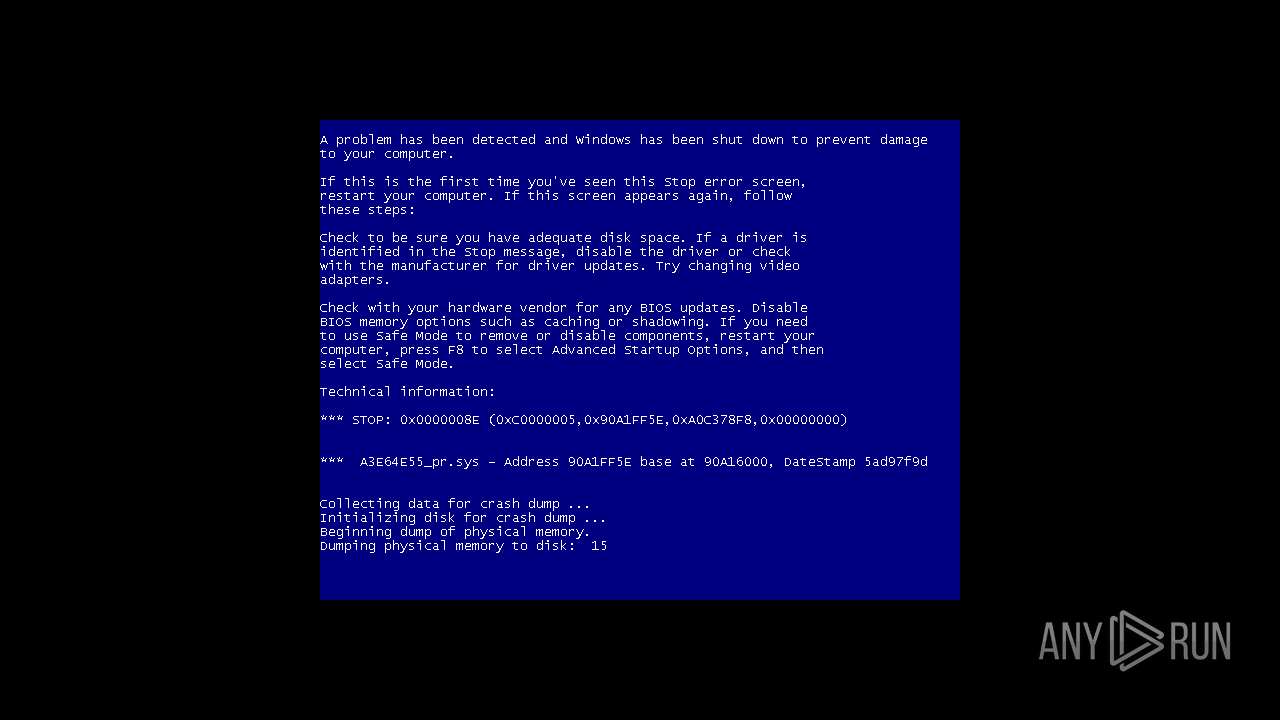
Application was crashed
- mHotspot.exe (PID: 3764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:04:18 20:54:06+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 104448 |
| InitializedDataSize: | 83968 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x148d4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.8.8.9 |
| ProductVersionNumber: | 7.8.8.9 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 7.8.8.9 |
| ProductVersion: | 7.8.8.9 |
| CompanyName: | 1BN Software & IT Solutions Pvt. Ltd. |
| FileDescription: | mHotspot Setup |
| InternalName: | - |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | mHotspot |
Total processes
129
Monitored processes
76
Malicious processes
33
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\AVAST Software\Avast\RegSvr.exe" "C:\Program Files\AVAST Software\Avast\aswAMSI.dll" | C:\Program Files\AVAST Software\Avast\RegSvr.exe | — | instup.exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Antivirus Installer Exit code: 0 Version: 19.4.4318.0 Modules
| |||||||||||||||
| 292 | "sc.exe" failure WCAssistantService reset= 30 actions= restart/60000 | C:\Windows\system32\sc.exe | — | WebCompanionInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 460 | "C:\Users\admin\AppData\Local\Temp\\CCUpdate.exe" /applycab "C:\Users\admin\AppData\Local\Temp\cc44E8.tmp" | C:\Users\admin\AppData\Local\Temp\CCUpdate.exe | AvEmUpdate.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner emergency updater Exit code: 0 Version: 17, 8, 77, 0 Modules
| |||||||||||||||
| 536 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\uuwrvb-s.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | WebCompanion.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 552 | netsh http add urlacl url=http://+:9007/ user=Everyone | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 776 | "C:\Program Files\AVAST Software\Avast\aswRunDll.exe" "C:\Program Files\AVAST Software\Avast\ashMaiSv.dll,Install" | C:\Program Files\AVAST Software\Avast\aswRunDll.exe | — | instup.exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Antivirus Installer Exit code: 0 Version: 19.4.4318.0 Modules
| |||||||||||||||
| 836 | "C:\Program Files\AVAST Software\Avast\wsc_proxy.exe" /av_as /signatures:up_to_date /state:on /svc /update | C:\Program Files\AVAST Software\Avast\wsc_proxy.exe | — | AvastSvc.exe | |||||||||||
User: SYSTEM Company: AVAST Software Integrity Level: SYSTEM Description: Avast remediation exe Exit code: 0 Version: 19.4.4318.0 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Spareio\SpareioApp\SpareioWinService.exe" | C:\Program Files\Spareio\SpareioApp\SpareioWinService.exe | services.exe | ||||||||||||
User: SYSTEM Company: Spare.io Integrity Level: SYSTEM Description: Spareio Exit code: 0 Version: 0.9.54.0 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3120 CREDAT:14339 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | dummy /emupdater | C:\Program Files\CCleaner\CCUpdate.exe | CCUpdate.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner emergency updater Exit code: 0 Version: 19.2.566.0 Modules
| |||||||||||||||
Total events
16 535
Read events
10 522
Write events
5 993
Delete events
20
Modification events
| (PID) Process: | (1740) GenericSetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1740) GenericSetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1740) GenericSetup.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1740) GenericSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 0F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE09000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030353000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C01400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB5748501D00000001000000100000005B3B67000EEB80022E42605B6B3B72400B000000010000000E000000740068006100770074006500000003000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B812000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (1740) GenericSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 190000000100000010000000DC73F9B71E16D51D26527D32B11A6A3D03000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B810B000000010000000E00000074006800610077007400650000001D00000001000000100000005B3B67000EEB80022E42605B6B3B72401400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB57485053000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C009000000010000002A000000302806082B0601050507030106082B0601050507030206082B0601050507030406082B060105050703030F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE2000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (2828) Carrier.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 0C0B000054471F70B6FCD401 | |||
| (PID) Process: | (2828) Carrier.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 2DC14CE040CA3239D5EBFC55EE05DE856AB63FD9BB0C9C12515CD67251198E84 | |||
| (PID) Process: | (2828) Carrier.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2828) Carrier.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\mHotspot\mHotspot.exe | |||
| (PID) Process: | (2828) Carrier.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: B97C50D02D3B6F80626090818CA9F931E1696666C897D6483A4E2062A80713CD | |||
Executable files
543
Suspicious files
128
Text files
673
Unknown types
62
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\installer.exe | executable | |
MD5:— | SHA256:— | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\GenericSetup.exe | executable | |
MD5:— | SHA256:— | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\en\DevLib.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 1740 | GenericSetup.exe | C:\Users\admin\AppData\Local\Temp\mHotspot.log | text | |
MD5:— | SHA256:— | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\BundleConfig.xml | text | |
MD5:— | SHA256:— | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\DevLib.dll | executable | |
MD5:— | SHA256:— | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\ru\DevLib.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\Microsoft.Win32.TaskScheduler.dll | executable | |
MD5:— | SHA256:— | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\GenericSetup.exe.config | xml | |
MD5:D8B647033179F18B7BD01518746FBFB5 | SHA256:388E965DD296E3FB0841E891D9D09F32F8FC2DC52CD1FAD26CC0FB5D48866435 | |||
| 2408 | mHotspot_setup_latest_2.exe | C:\Users\admin\AppData\Local\Temp\7zS86999411\WizardPages.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
192
TCP/UDP connections
173
DNS requests
145
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1740 | GenericSetup.exe | GET | 200 | 104.17.177.102:80 | http://webcompanion.com/nano_download.php?partner=MH170601 | US | executable | 347 Kb | malicious |
1740 | GenericSetup.exe | GET | 200 | 104.17.178.102:80 | http://rt.webcompanion.com/notifications/download/rt/Installer/SpareioSDK.exe | US | executable | 44.6 Kb | malicious |
1972 | wwqbmdhq.ctz.exe | GET | 200 | 8.248.131.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.6 Kb | whitelisted |
2920 | WebCompanionInstaller.exe | GET | 200 | 104.17.61.19:80 | http://wcdownloadercdn.lavasoft.com/4.6.1974.3869/WebCompanion-4.6.1974.3869-prod.zip | US | compressed | 9.06 Mb | whitelisted |
1972 | wwqbmdhq.ctz.exe | POST | 200 | 35.227.19.75:80 | http://api.spare.io/api/v1/worker/register/ | US | text | 22 b | unknown |
2920 | WebCompanionInstaller.exe | POST | 200 | 64.18.87.81:80 | http://wc-tracking.lavasoft.com/Install.asmx | CA | xml | 294 b | whitelisted |
948 | installer.exe | POST | 200 | 104.17.61.19:80 | http://flow.lavasoft.com/v1/event-stat?ProductID=IS&Type=StubBundleStart | US | text | 29 b | whitelisted |
2920 | WebCompanionInstaller.exe | POST | 200 | 64.18.87.81:80 | http://wc-tracking.lavasoft.com/Install.asmx | CA | xml | 294 b | whitelisted |
2920 | WebCompanionInstaller.exe | POST | 200 | 64.18.87.81:80 | http://wc-tracking.lavasoft.com/Install.asmx | CA | xml | 294 b | whitelisted |
2920 | WebCompanionInstaller.exe | POST | 200 | 64.18.87.81:80 | http://wc-tracking.lavasoft.com/Install.asmx | CA | xml | 294 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
948 | installer.exe | 104.17.61.19:80 | flow.lavasoft.com | Cloudflare Inc | US | shared |
1740 | GenericSetup.exe | 104.17.60.19:443 | flow.lavasoft.com | Cloudflare Inc | US | shared |
1972 | wwqbmdhq.ctz.exe | 8.248.131.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3120 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2452 | iexplore.exe | 68.183.82.64:443 | mhotspot.com | DSL Extreme | US | unknown |
2920 | WebCompanionInstaller.exe | 64.18.87.81:80 | wc-tracking.lavasoft.com | COGECODATA | CA | unknown |
1972 | wwqbmdhq.ctz.exe | 35.227.19.75:80 | api.spare.io | — | US | unknown |
2920 | WebCompanionInstaller.exe | 104.17.61.19:80 | flow.lavasoft.com | Cloudflare Inc | US | shared |
1972 | wwqbmdhq.ctz.exe | 172.217.16.144:443 | storage.googleapis.com | Google Inc. | US | whitelisted |
2068 | SpareioInstaller.exe | 172.217.16.144:443 | storage.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
flow.lavasoft.com |
| whitelisted |
www.google.com |
| malicious |
sos.adaware.com |
| whitelisted |
webcompanion.com |
| malicious |
rt.webcompanion.com |
| malicious |
www.download.windowsupdate.com |
| whitelisted |
mhotspot.com |
| malicious |
www.bing.com |
| whitelisted |
wc-tracking.lavasoft.com |
| whitelisted |
wc-update-service.lavasoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
948 | installer.exe | A Network Trojan was detected | ET MALWARE Lavasoft PUA/Adware Client Install |
1740 | GenericSetup.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
1740 | GenericSetup.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1740 | GenericSetup.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1740 | GenericSetup.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1740 | GenericSetup.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1740 | GenericSetup.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3956 | 0gbxa5iq.0v3.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3956 | 0gbxa5iq.0v3.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2156 | instup.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
Process | Message |
|---|---|
wwqbmdhq.ctz.exe | Register
|
WebCompanionInstaller.exe | Detecting windows culture
|
wwqbmdhq.ctz.exe | Machine ID fingerPrint -- > CPU >> 1F8BFBFF000506E3
BIOS >> DELLDELL20110101000000.000000+000DELL - 1
BASE >>
DISK >> WDC WD20EARS ATA Device(Standard disk drives)1660034144255
VIDEO >> 6.1.7600.16385Standard VGA Graphics Adapter
MAC >> 52:54:00:4A:04:AF
WCID >> WCID20
|
wwqbmdhq.ctz.exe | Machine ID hash UUID -- > 735550BB-0FAF-AAB3-C4F6-BBAC563DACB9
|
wwqbmdhq.ctz.exe | Getting SysInfo
|
wwqbmdhq.ctz.exe | cpuInfo
|
WebCompanionInstaller.exe | 4/27/2019 6:02:46 AM :-> Starting installer 4.6.1974.3869 with: .\WebCompanionInstaller.exe --partner=MH170601 --version=4.6.1974.3869 --prod --silent --homepage=1 --search=1 --partner=MH170601, Run as admin: True
|
WebCompanionInstaller.exe | Preparing for installing Web Companion
|
wwqbmdhq.ctz.exe | gpuInfo
|
wwqbmdhq.ctz.exe | uptimePct
|