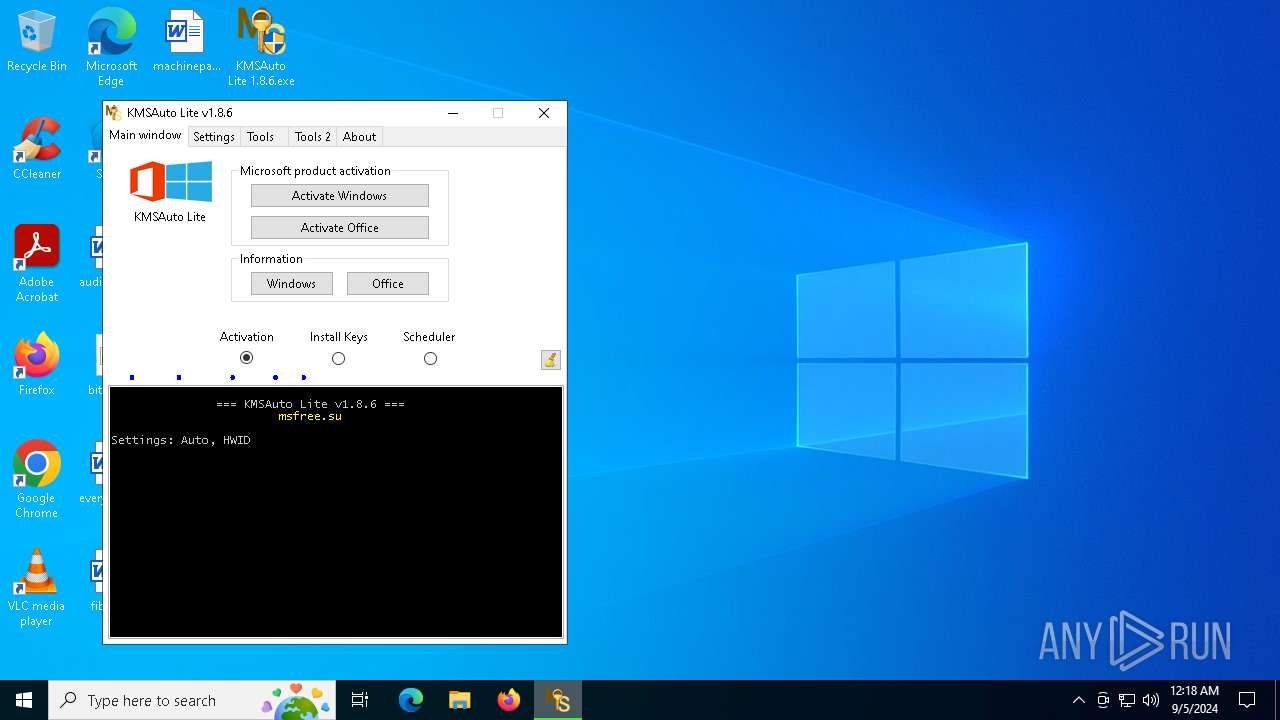
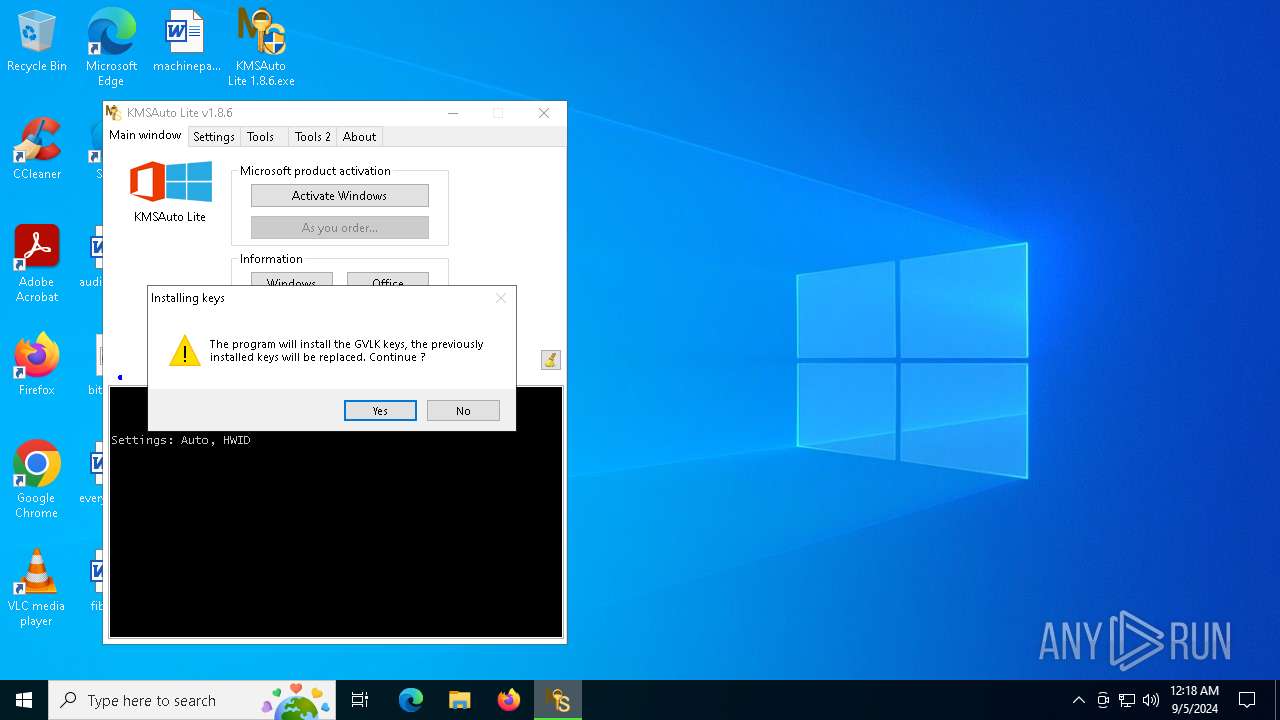
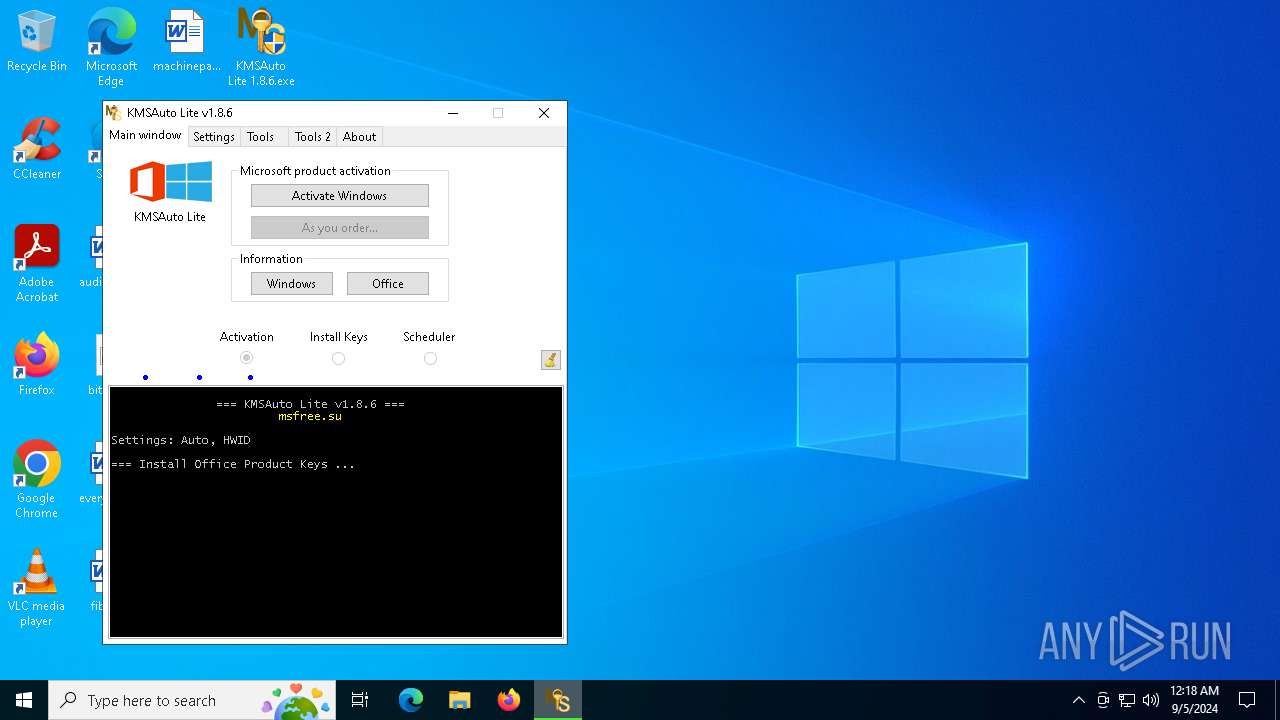
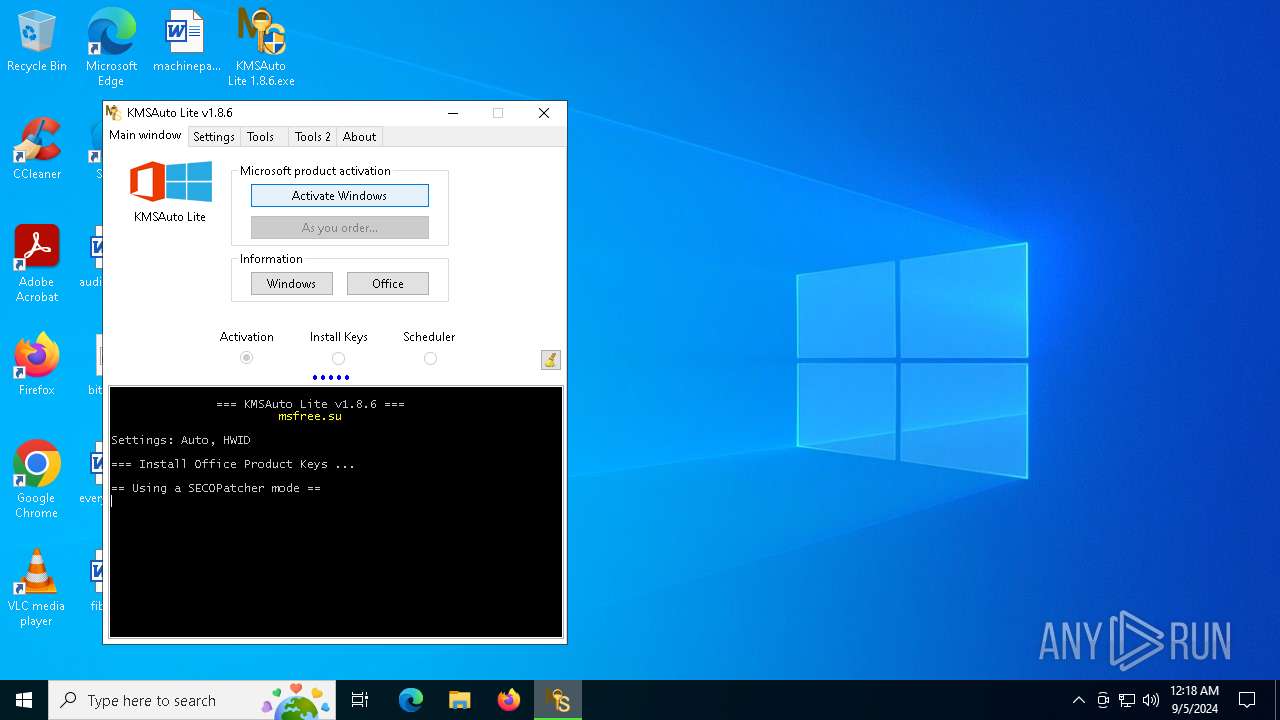
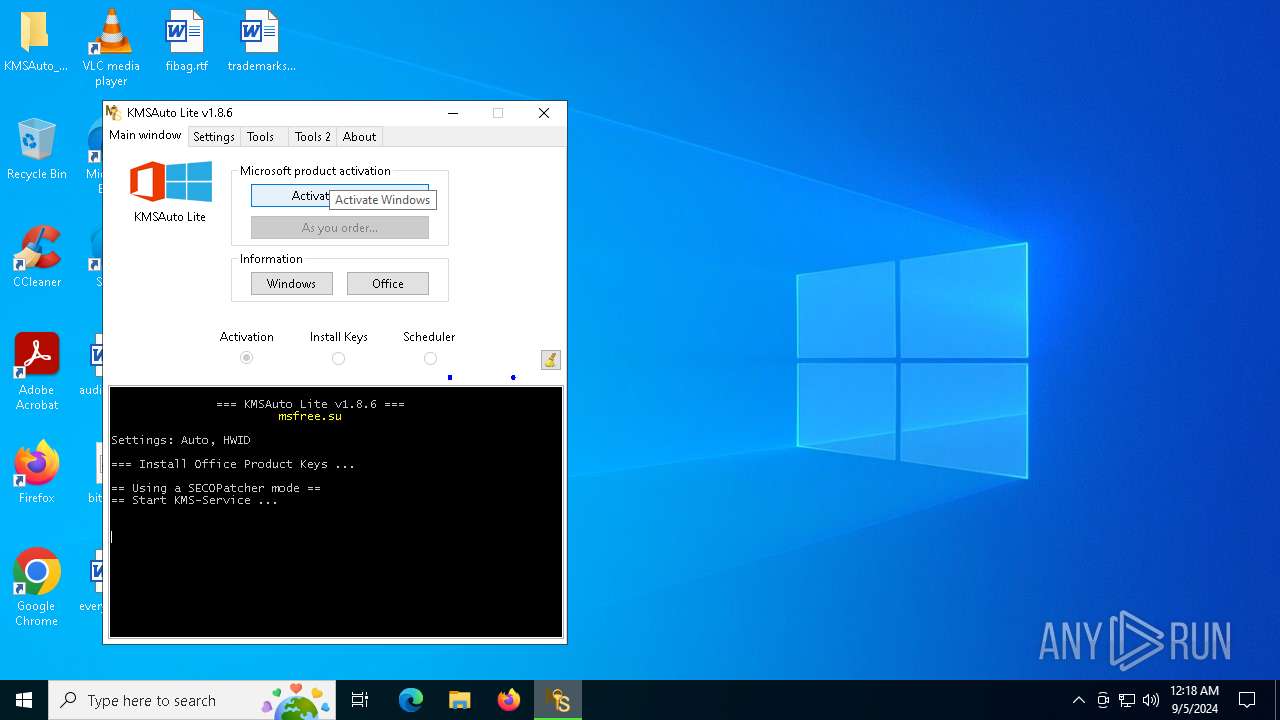
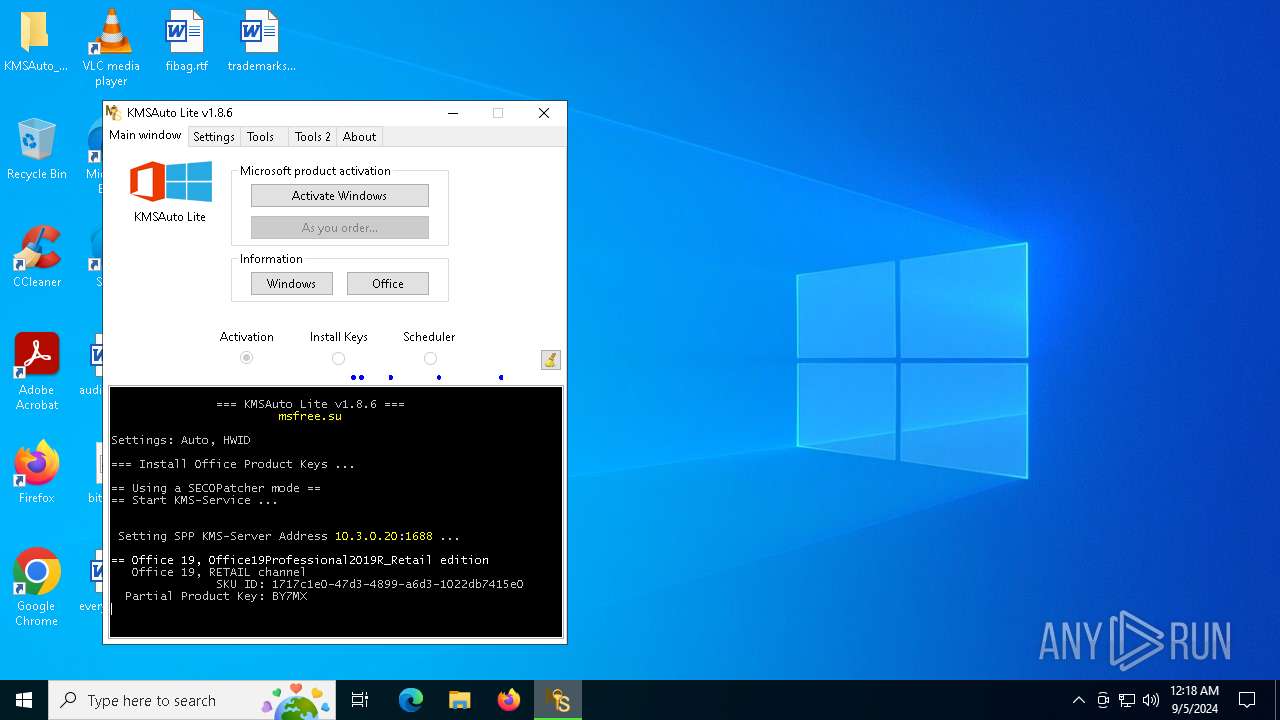
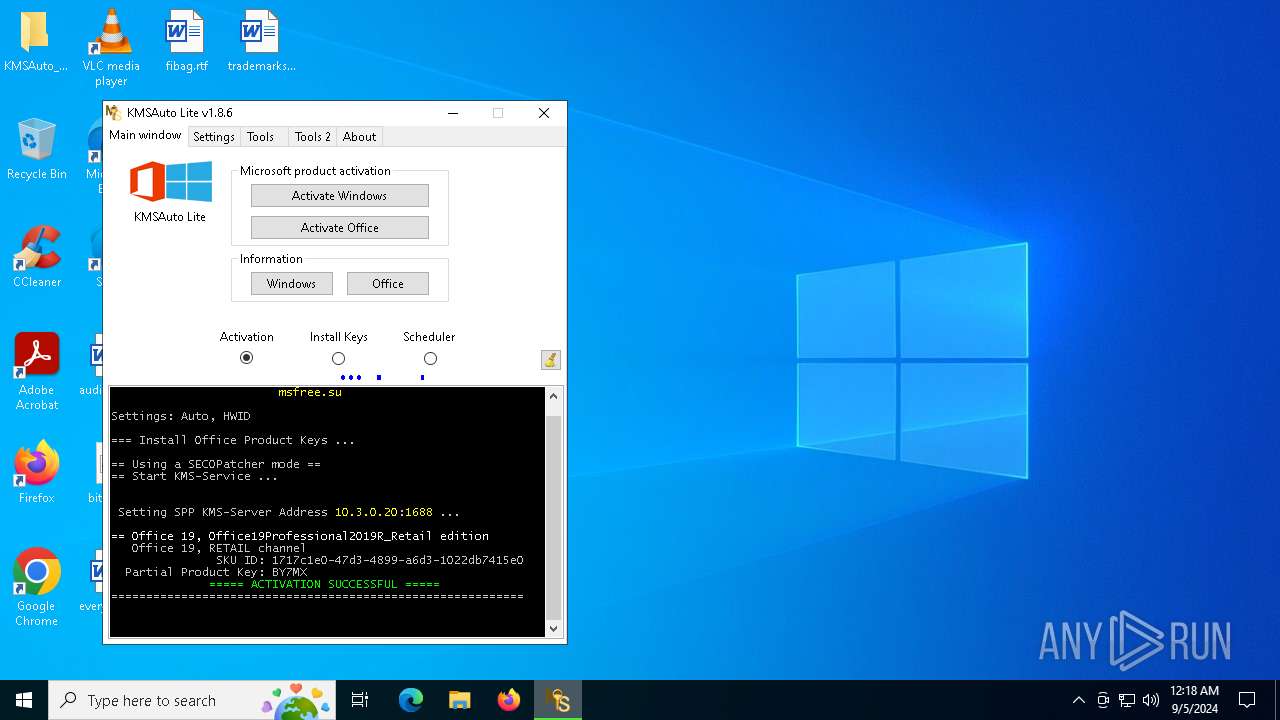
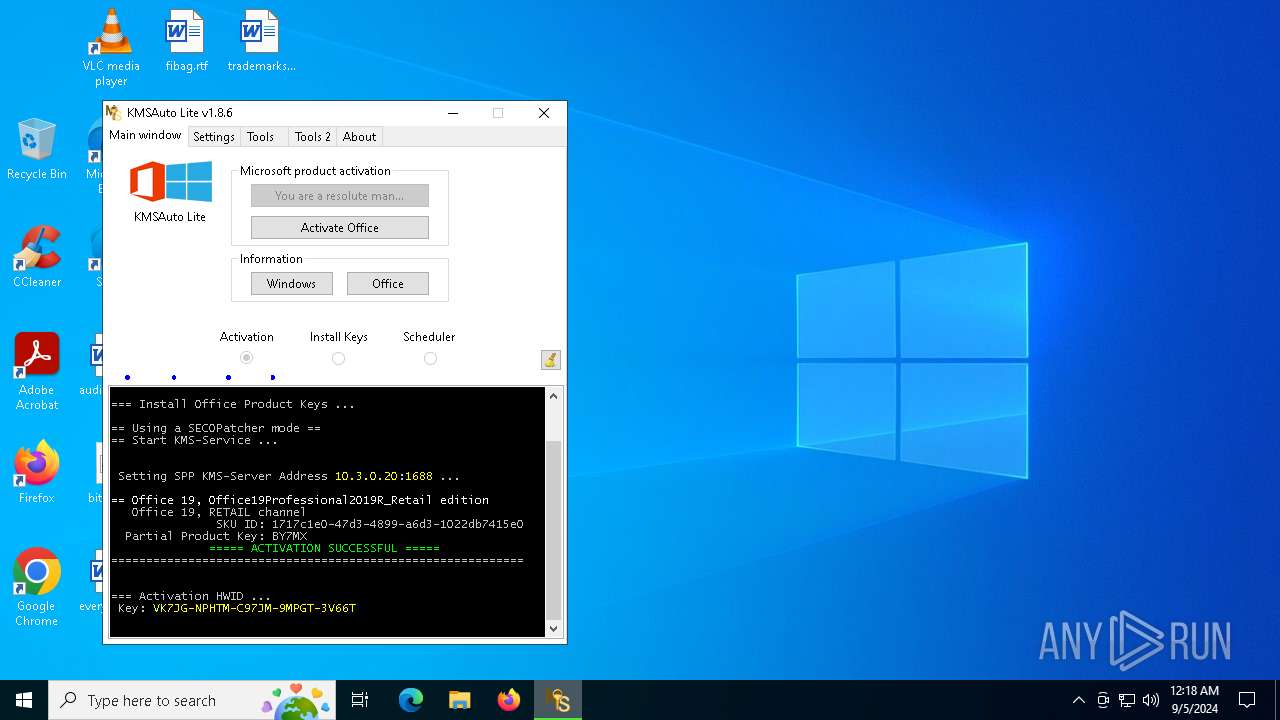
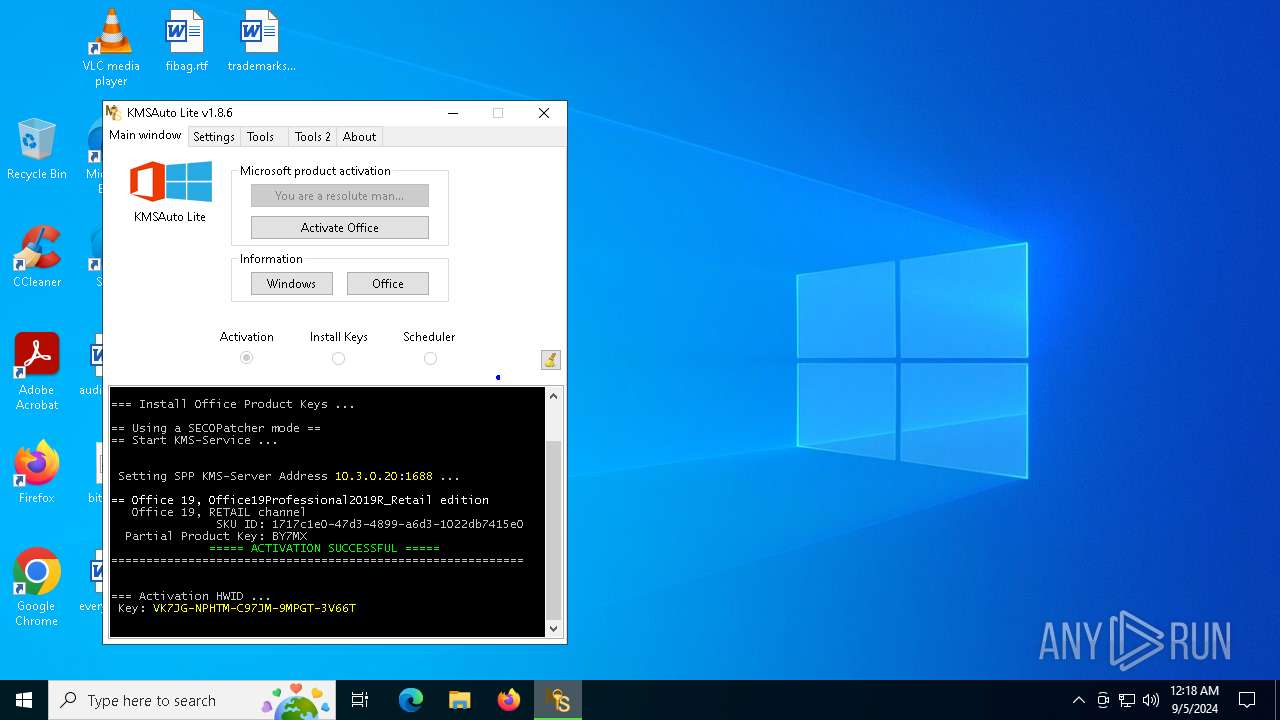
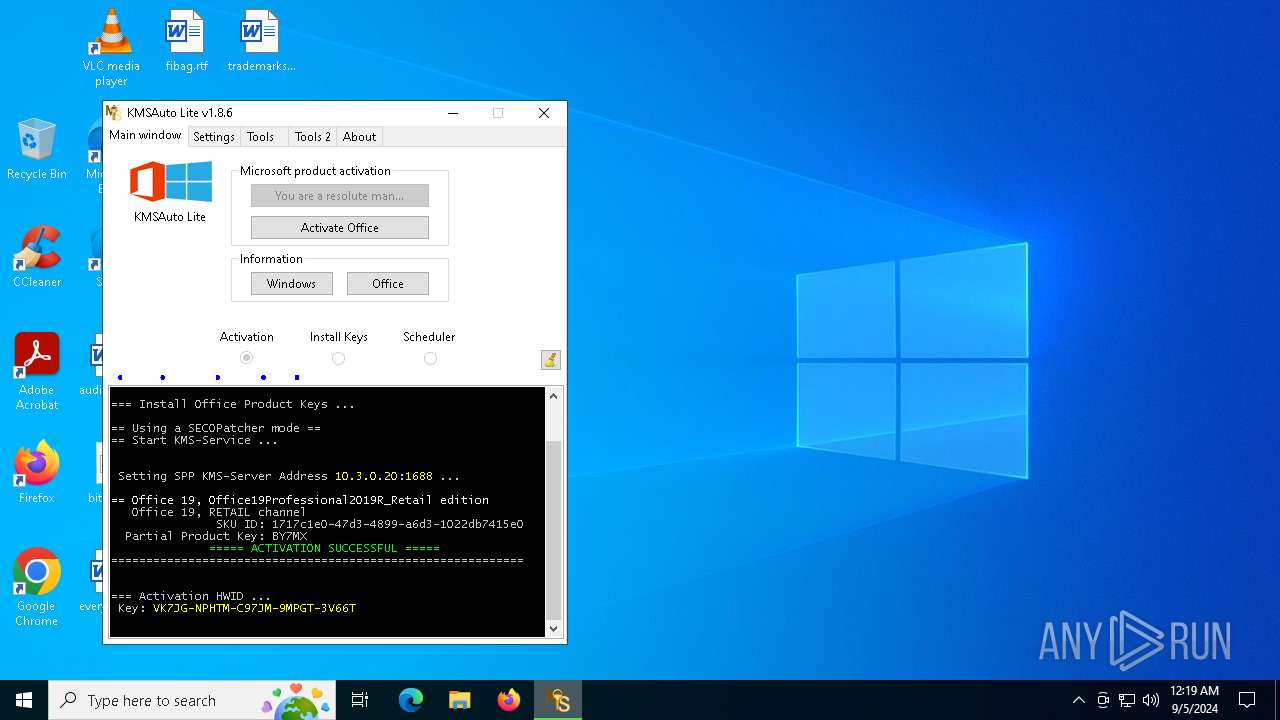
| File name: | KMSAuto Lite 1.8.6.exe |
| Full analysis: | https://app.any.run/tasks/54691634-9c97-4042-aa03-94319a3fbb47 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2024, 00:18:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8B8E3A7DA8862CC23D3D5FFF228EC3A4 |
| SHA1: | EC7A4ECE4CC291733B2D02B4462BDAFE43465A7D |
| SHA256: | 4E7D955F96FA0AAB312DA3D1B8312D9BE671C1A2C84CED4048AC25EDBE5C31E7 |
| SSDEEP: | 98304:2poZrBqVEGXmZb3YBM07fq1EfbknlhaEs/Laln7Y61HR02TlpSpgR7gawNVDQtZe:89MnPXVS |
MALICIOUS
Changes image file execution options
- reg.exe (PID: 6188)
Starts NET.EXE for service management
- net.exe (PID: 1448)
- net.exe (PID: 6956)
- net.exe (PID: 5708)
- net.exe (PID: 2208)
- net.exe (PID: 7092)
- cmd.exe (PID: 7140)
- net.exe (PID: 5128)
- net.exe (PID: 1060)
SUSPICIOUS
Checks Windows Trust Settings
- signtool.exe (PID: 6040)
Starts SC.EXE for service management
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 2032)
- cmd.exe (PID: 7156)
- cmd.exe (PID: 1480)
- cmd.exe (PID: 6148)
- cmd.exe (PID: 32)
- cmd.exe (PID: 5092)
- cmd.exe (PID: 7140)
Executable content was dropped or overwritten
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- Dism.exe (PID: 2208)
Process drops legitimate windows executable
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- Dism.exe (PID: 2208)
Starts CMD.EXE for commands execution
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- cmd.exe (PID: 7140)
Reads security settings of Internet Explorer
- signtool.exe (PID: 6040)
Adds/modifies Windows certificates
- signtool.exe (PID: 6040)
Uses WMIC.EXE
- KMSAuto Lite 1.8.6.exe (PID: 5344)
Uses WMIC.EXE to obtain Windows Installer data
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 3292)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3316)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 1288)
Uses WMIC.EXE to obtain service application data
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- cmd.exe (PID: 7140)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6952)
- cmd.exe (PID: 6128)
- cmd.exe (PID: 5064)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 5532)
- cmd.exe (PID: 4540)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 6168)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 5160)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 2056)
- cmd.exe (PID: 7140)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6684)
- cmd.exe (PID: 2524)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6308)
- cmd.exe (PID: 6648)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 6724)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 5548)
- cmd.exe (PID: 2128)
Creates or modifies Windows services
- KMSAuto Lite 1.8.6.exe (PID: 5344)
Executes as Windows Service
- KMSSS.exe (PID: 7088)
The process executes VB scripts
- cmd.exe (PID: 6884)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 7140)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 5484)
- cscript.exe (PID: 5044)
- cscript.exe (PID: 6648)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 5484)
- cscript.exe (PID: 5044)
- cscript.exe (PID: 6648)
Executing commands from ".cmd" file
- KMSAuto Lite 1.8.6.exe (PID: 5344)
Application launched itself
- cmd.exe (PID: 7140)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6004)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 5708)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 4976)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7140)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7140)
Hides command output
- cmd.exe (PID: 940)
- cmd.exe (PID: 7044)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 4364)
- cmd.exe (PID: 6864)
- cmd.exe (PID: 6444)
- cmd.exe (PID: 3292)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7044)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 6648)
The process creates files with name similar to system file names
- Dism.exe (PID: 2208)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 6056)
INFO
Reads the machine GUID from the registry
- signtool.exe (PID: 6040)
- KMSSS.exe (PID: 7088)
Reads the software policy settings
- signtool.exe (PID: 6040)
Create files in a temporary directory
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- Dism.exe (PID: 2208)
Checks supported languages
- signtool.exe (PID: 6040)
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- KMSSS.exe (PID: 7088)
- DismHost.exe (PID: 6056)
Reads product name
- KMSAuto Lite 1.8.6.exe (PID: 5344)
Reads Environment values
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- DismHost.exe (PID: 6056)
Reads the computer name
- KMSAuto Lite 1.8.6.exe (PID: 5344)
- KMSSS.exe (PID: 7088)
- DismHost.exe (PID: 6056)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6596)
- WMIC.exe (PID: 1812)
- WMIC.exe (PID: 4688)
- WMIC.exe (PID: 2492)
- WMIC.exe (PID: 2876)
- WMIC.exe (PID: 3852)
- WMIC.exe (PID: 6612)
- WMIC.exe (PID: 5064)
- WMIC.exe (PID: 1044)
- WMIC.exe (PID: 2368)
- WMIC.exe (PID: 6056)
- WMIC.exe (PID: 1616)
- WMIC.exe (PID: 5164)
- WMIC.exe (PID: 5136)
- WMIC.exe (PID: 6160)
- WMIC.exe (PID: 7052)
- WMIC.exe (PID: 6928)
- WMIC.exe (PID: 6908)
- cscript.exe (PID: 5044)
- WMIC.exe (PID: 3112)
- WMIC.exe (PID: 5944)
- cscript.exe (PID: 5484)
- WMIC.exe (PID: 6696)
- WMIC.exe (PID: 6040)
- WMIC.exe (PID: 7088)
- cscript.exe (PID: 6648)
- WMIC.exe (PID: 2400)
- WMIC.exe (PID: 940)
- WMIC.exe (PID: 3256)
- WMIC.exe (PID: 1404)
UPX packer has been detected
- KMSAuto Lite 1.8.6.exe (PID: 5344)
Checks operating system version
- cmd.exe (PID: 7140)
Sends debugging messages
- DismHost.exe (PID: 6056)
- Dism.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (30.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (26.7) |
| .exe | | | UPX compressed Win32 Executable (26.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.3) |
| .exe | | | Win32 Executable (generic) (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:16 02:31:31+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 1085440 |
| InitializedDataSize: | 5081088 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.8.6.0 |
| ProductVersionNumber: | 1.8.6.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
Total processes
502
Monitored processes
363
Malicious processes
5
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\WINDOWS\Sysnative\cmd.exe" /c C:\WINDOWS\System32\sc.exe start wuauserv | C:\Windows\System32\cmd.exe | — | KMSAuto Lite 1.8.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | sc start KeyIso | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1056 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | C:\WINDOWS\system32\cmd.exe /c ping -n 1 l.root-servers.net | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | reg query HKLM\SYSTEM\CurrentControlSet\Services\KeyIso /v ObjectName | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\State" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | C:\WINDOWS\system32\cmd.exe /c reg query "HKLM\SYSTEM\CurrentControlSet\Control\ProductOptions" /v OSProductPfn 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | reg query HKLM\SYSTEM\CurrentControlSet\Services\sppsvc /v Type | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | wmic path SoftwareLicensingProduct where (ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f') get ID /VALUE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 196
Read events
35 171
Write events
19
Delete events
6
Modification events
| (PID) Process: | (5344) KMSAuto Lite 1.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6040) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
Value: | |||
| (PID) Process: | (6040) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000001BFE69D191B71933A372A80FE155E5B51D0000000100000010000000885010358D29A38F059B028559C95F90620000000100000020000000E793C9B02FD8AA13E21C31228ACCB08119643B749C898964B1746D46C3D4CBD2090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F000000010000003000000066B764A96581128168CF208E374DDA479D54E311F32457F4AEE0DBD2A6C8D171D531289E1CD22BFDBBD4CFD9796254830300000001000000140000002B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E190000000100000010000000EA6089055218053DD01E37E1D806EEDF53000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C01400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB0B00000001000000100000005300650063007400690067006F0000002000000001000000E2050000308205DE308203C6A003020102021001FD6D30FCA3CA51A81BBC640E35032D300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A3423040301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201005CD47C0DCFF7017D4199650C73C5529FCBF8CF99067F1BDA43159F9E0255579614F1523C27879428ED1F3A0137A276FC5350C0849BC66B4EBA8C214FA28E556291F36915D8BC88E3C4AA0BFDEFA8E94B552A06206D55782919EE5F305C4B241155FF249A6E5E2A2BEE0B4D9F7FF70138941495430709FB60A9EE1CAB128CA09A5EA7986A596D8B3F08FBC8D145AF18156490120F73282EC5E2244EFC58ECF0F445FE22B3EB2F8ED2D9456105C1976FA876728F8B8C36AFBF0D05CE718DE6A66F1F6CA67162C5D8D083720CF16711890C9C134C7234DFBCD571DFAA71DDE1B96C8C3C125D65DABD5712B6436BFFE5DE4D661151CF99AEEC17B6E871918CDE49FEDD3571A21527941CCF61E326BB6FA36725215DE6DD1D0B2E681B3B82AFEC836785D4985174B1B9998089FF7F78195C794A602E9240AE4C372A2CC9C762C80E5DF7365BCAE0252501B4DD1A079C77003FD0DCD5EC3DD4FABB3FCC85D66F7FA92DDFB902F7F5979AB535DAC367B0874AA9289E238EFF5C276BE1B04FF307EE002ED45987CB524195EAF447D7EE6441557C8D590295DD629DC2B9EE5A287484A59BB790C70C07DFF589367432D628C1B0B00BE09C4CC31CD6FCE369B54746812FA282ABD3634470C48DFF2D33BAAD8F7BB57088AE3E19CF4028D8FCC890BB5D9922F552E658C51F883143EE881DD7C68E3C436A1DA718DE7D3D16F162F9CA90A8FD | |||
| (PID) Process: | (6040) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000001000000B00000001000000100000005300650063007400690067006F0000001400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB53000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000EA6089055218053DD01E37E1D806EEDF0300000001000000140000002B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E0F000000010000003000000066B764A96581128168CF208E374DDA479D54E311F32457F4AEE0DBD2A6C8D171D531289E1CD22BFDBBD4CFD979625483090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B06010505070308620000000100000020000000E793C9B02FD8AA13E21C31228ACCB08119643B749C898964B1746D46C3D4CBD21D0000000100000010000000885010358D29A38F059B028559C95F900400000001000000100000001BFE69D191B71933A372A80FE155E5B52000000001000000E2050000308205DE308203C6A003020102021001FD6D30FCA3CA51A81BBC640E35032D300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A3423040301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201005CD47C0DCFF7017D4199650C73C5529FCBF8CF99067F1BDA43159F9E0255579614F1523C27879428ED1F3A0137A276FC5350C0849BC66B4EBA8C214FA28E556291F36915D8BC88E3C4AA0BFDEFA8E94B552A06206D55782919EE5F305C4B241155FF249A6E5E2A2BEE0B4D9F7FF70138941495430709FB60A9EE1CAB128CA09A5EA7986A596D8B3F08FBC8D145AF18156490120F73282EC5E2244EFC58ECF0F445FE22B3EB2F8ED2D9456105C1976FA876728F8B8C36AFBF0D05CE718DE6A66F1F6CA67162C5D8D083720CF16711890C9C134C7234DFBCD571DFAA71DDE1B96C8C3C125D65DABD5712B6436BFFE5DE4D661151CF99AEEC17B6E871918CDE49FEDD3571A21527941CCF61E326BB6FA36725215DE6DD1D0B2E681B3B82AFEC836785D4985174B1B9998089FF7F78195C794A602E9240AE4C372A2CC9C762C80E5DF7365BCAE0252501B4DD1A079C77003FD0DCD5EC3DD4FABB3FCC85D66F7FA92DDFB902F7F5979AB535DAC367B0874AA9289E238EFF5C276BE1B04FF307EE002ED45987CB524195EAF447D7EE6441557C8D590295DD629DC2B9EE5A287484A59BB790C70C07DFF589367432D628C1B0B00BE09C4CC31CD6FCE369B54746812FA282ABD3634470C48DFF2D33BAAD8F7BB57088AE3E19CF4028D8FCC890BB5D9922F552E658C51F883143EE881DD7C68E3C436A1DA718DE7D3D16F162F9CA90A8FD | |||
| (PID) Process: | (6188) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | Debugger |
Value: rundll32.exe SECOPatcher.dll,PatcherMain | |||
| (PID) Process: | (5344) KMSAuto Lite 1.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\KMSEmulator |
| Operation: | write | Name: | ImagePath |
Value: "C:\Users\admin\Desktop\KMSAuto_Files\bin\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -PO16 RandomKMSPID -AI 43200 -RI 43200 KillProcessOnPort -Log -IP | |||
| (PID) Process: | (5344) KMSAuto Lite 1.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\KMSEmulator |
| Operation: | write | Name: | Description |
Value: KMS-Service | |||
| (PID) Process: | (5344) KMSAuto Lite 1.8.6.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (4920) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: 10.3.0.20 | |||
| (PID) Process: | (7048) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
Executable files
55
Suspicious files
1
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:82EA8526AD519FB43F52C981D67EA693 | SHA256:91298FCE7FF765321D3D82381C3D0B2001A62A4B441DED0F8EF7388F6302FBB4 | |||
| 5344 | KMSAuto Lite 1.8.6.exe | C:\Users\admin\Desktop\KMSAuto_Files\bin\driver\x64WDV\SECOPatcher.dll | executable | |
MD5:8998BE879286D69A2522109650FEC7B8 | SHA256:03B9136FB9414EBA54D0890D9EFAD1CC0E40ABD55EBE2A5BD5554EA7BCC6D2BE | |||
| 5344 | KMSAuto Lite 1.8.6.exe | C:\Users\admin\AppData\Local\Temp\slmgr.vbs | text | |
MD5:3903BCAB32A4A853DFA54962112D4D02 | SHA256:95FC646D222D324DB46F603A7F675C329FE59A567ED27FDAED2A572A19206816 | |||
| 5344 | KMSAuto Lite 1.8.6.exe | C:\Users\admin\AppData\Local\Temp\BIN\gatherosstate.exe | executable | |
MD5:B13BC5B62F54607C334A6464D9B85CC8 | SHA256:51791625054B01802FD5AAA6C4A929827B369DFEF7B2891B5F55E0FA61AF0C7D | |||
| 7036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bx2zj5oa.mxr.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7088 | KMSSS.exe | C:\Users\admin\Desktop\KMSAuto_Files\bin\KMSSS.log | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 2208 | Dism.exe | C:\Windows\Logs\DISM\dism.log | text | |
MD5:962E40C5E0A48F5782949244E031AC2F | SHA256:081DD31A1069C8DB255B5EBE8D8162177C888EA5777EA241284EF385531476A8 | |||
| 5344 | KMSAuto Lite 1.8.6.exe | C:\Users\admin\AppData\Local\Temp\BIN\slc.dll | executable | |
MD5:31E221D3B930629A14ED2AF067F777E3 | SHA256:32073D9D5706476785E3FBCB208B65DFF56038C6CA9A8A2B15D2AB1590CC8E04 | |||
| 7048 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xti10lnw.mcq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7048 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tvyi3ozg.bo0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4364 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4364 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
608 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
608 | svchost.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6248 | RUXIMICS.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
608 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
608 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3652 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
l.root-servers.net |
| unknown |
Threats
Process | Message |
|---|---|
Dism.exe | PID=2208 TID=6052 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=2208 TID=6052 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=2208 TID=6052 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=2208 TID=6052 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=2208 TID=6052 Loading Provider from location C:\WINDOWS\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=2208 TID=6052 Connecting to the provider located at C:\WINDOWS\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=6056 TID=2700 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=6056 TID=2700 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=6056 TID=2700 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=2208 TID=6052 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |