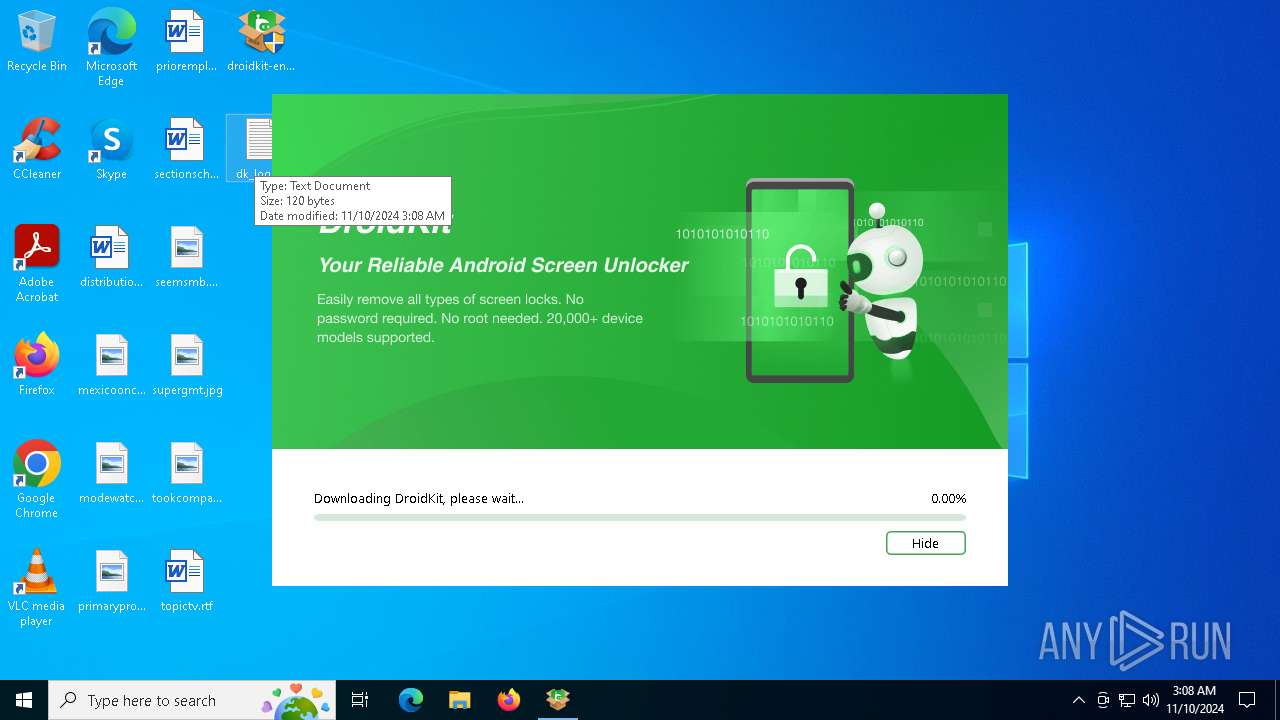
| File name: | droidkit-en-setup.exe |
| Full analysis: | https://app.any.run/tasks/bbd5fbd3-f4f1-4d41-98d6-038d05a0eb69 |
| Verdict: | Malicious activity |
| Analysis date: | November 10, 2024, 03:07:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 8635F94C18C6372A4DF1001CAC67E366 |
| SHA1: | C6B35959A3AFE487581509BA1853FF93C8E4E5DF |
| SHA256: | 4E7982C1A982141773E2A47F43D0212C6E966457A4F96F7D05F5476D3E18A9AF |
| SSDEEP: | 196608:YecQrTnOvHB/x85gZ55mXaCf5l5H7oMr/ev:nlaRwIGa8lx7LrGv |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- droidkit-en-setup.exe (PID: 2708)
Malware-specific behavior (creating "System.dll" in Temp)
- droidkit-en-setup.exe (PID: 2708)
Process drops legitimate windows executable
- droidkit-en-setup.exe (PID: 2708)
Reads security settings of Internet Explorer
- droidkit-en-setup.exe (PID: 2708)
The process creates files with name similar to system file names
- droidkit-en-setup.exe (PID: 2708)
Executable content was dropped or overwritten
- droidkit-en-setup.exe (PID: 2708)
Starts CMD.EXE for commands execution
- droidkit-en-setup.exe (PID: 2708)
Checks Windows Trust Settings
- droidkit-en-setup.exe (PID: 2708)
INFO
Create files in a temporary directory
- droidkit-en-setup.exe (PID: 2708)
Reads CPU info
- droidkit-en-setup.exe (PID: 2708)
Reads the computer name
- droidkit-en-setup.exe (PID: 2708)
- curl.exe (PID: 6136)
- curl.exe (PID: 1884)
The process uses the downloaded file
- droidkit-en-setup.exe (PID: 2708)
Process checks computer location settings
- droidkit-en-setup.exe (PID: 2708)
Checks supported languages
- droidkit-en-setup.exe (PID: 2708)
- curl.exe (PID: 6136)
- curl.exe (PID: 1884)
Creates files in the program directory
- droidkit-en-setup.exe (PID: 2708)
Checks proxy server information
- droidkit-en-setup.exe (PID: 2708)
Reads the machine GUID from the registry
- droidkit-en-setup.exe (PID: 2708)
Reads the software policy settings
- droidkit-en-setup.exe (PID: 2708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:04:10 12:19:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 26624 |
| InitializedDataSize: | 475136 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x3415 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.3 |
| ProductVersionNumber: | 1.0.1.3 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | iMobie Inc. |
| FileDescription: | DroidKit |
| FileVersion: | 1.0.1.3 |
| InternalName: | ${Name} |
| LegalCopyright: | Copyright (C) iMobie Inc. All rights reserved |
| LegalTrademarks: | iMobie Inc. All rights reserved |
| ProductName: | DroidKit |
| ProductVersion: | 1.0.1.3 |
Total processes
130
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1884 | curl -X POST -H "Content-Type: application/json" -d "{\"client_id\":\"dk-Windows\",\"user_id\":\"26B799FA\",\"events\":[{\"name\":\"Install_SW\",\"params\":{\"engagement_time_msec\":\"1\",\"ea\":\"Start Download\",\"el\":\"1\",\"pv\":\"dk-win\",\"install_productversion\":\"Official-com\",\"install_trackversion\":\"1.0.1.3\",\"soft_os_version\":\"Windows_64\"}}]}" "https://www.google-analytics.com/mp/collect?measurement_id=G-VR4P911QVY&api_secret=RrQJtReGS520apjVhJz5xw" | C:\Windows\SysWOW64\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 35 Version: 8.4.0 Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\Desktop\droidkit-en-setup.exe" | C:\Users\admin\Desktop\droidkit-en-setup.exe | explorer.exe | ||||||||||||
User: admin Company: iMobie Inc. Integrity Level: HIGH Description: DroidKit Version: 1.0.1.3 Modules
| |||||||||||||||
| 4476 | "C:\Windows\System32\cmd.exe" /c "curl -X POST -H "Content-Type: application/json" -d "{\"client_id\":\"dk-Windows\",\"user_id\":\"26B799FA\",\"events\":[{\"name\":\"Install_SW\",\"params\":{\"engagement_time_msec\":\"1\",\"ea\":\"Start Download\",\"el\":\"1\",\"pv\":\"dk-win\",\"install_productversion\":\"Official-com\",\"install_trackversion\":\"1.0.1.3\",\"soft_os_version\":\"Windows_64\"}}]}" "https://www.google-analytics.com/mp/collect?measurement_id=G-VR4P911QVY&api_secret=RrQJtReGS520apjVhJz5xw"" | C:\Windows\SysWOW64\cmd.exe | — | droidkit-en-setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 35 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6136 | curl -X POST -H "Content-Type: application/json" -d "{\"client_id\":\"dk-Windows\",\"user_id\":\"26B799FA\",\"events\":[{\"name\":\"Install_SW\",\"params\":{\"engagement_time_msec\":\"1\",\"ea\":\"Launch App\",\"el\":\"1\",\"pv\":\"dk-win\",\"install_productversion\":\"Official-com\",\"install_trackversion\":\"1.0.1.3\",\"soft_os_version\":\"Windows_64\"}}]}" "https://www.google-analytics.com/mp/collect?measurement_id=G-VR4P911QVY&api_secret=RrQJtReGS520apjVhJz5xw" | C:\Windows\SysWOW64\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 35 Version: 8.4.0 Modules
| |||||||||||||||
| 6696 | "C:\Users\admin\Desktop\droidkit-en-setup.exe" | C:\Users\admin\Desktop\droidkit-en-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: iMobie Inc. Integrity Level: MEDIUM Description: DroidKit Exit code: 3221226540 Version: 1.0.1.3 Modules
| |||||||||||||||
| 6808 | "C:\Windows\System32\cmd.exe" /c "curl -X POST -H "Content-Type: application/json" -d "{\"client_id\":\"dk-Windows\",\"user_id\":\"26B799FA\",\"events\":[{\"name\":\"Install_SW\",\"params\":{\"engagement_time_msec\":\"1\",\"ea\":\"Launch App\",\"el\":\"1\",\"pv\":\"dk-win\",\"install_productversion\":\"Official-com\",\"install_trackversion\":\"1.0.1.3\",\"soft_os_version\":\"Windows_64\"}}]}" "https://www.google-analytics.com/mp/collect?measurement_id=G-VR4P911QVY&api_secret=RrQJtReGS520apjVhJz5xw"" | C:\Windows\SysWOW64\cmd.exe | — | droidkit-en-setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 35 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 393
Read events
4 390
Write events
3
Delete events
0
Modification events
| (PID) Process: | (2708) droidkit-en-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2708) droidkit-en-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2708) droidkit-en-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
10
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\uninstall.ini | text | |
MD5:E978A46D7E23C139E4DF7B526F86745F | SHA256:435288E587018AA375E8A4BF3F35CD8DFFFD559053F5CA6A0E487A61FF23E5DB | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\Setup.ico | image | |
MD5:9CA6D8DCDC3A93521270FCB52C33E491 | SHA256:7056EDA1128F8A3A0C7217885972359CEE99B6A62A62D4BD7BAD79B04D7DB227 | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\modern-install.ico | image | |
MD5:9F49CD02B213AEC852ACE2F045CFAB18 | SHA256:CED6BD38E3B6731DDF63ED4E5E41D11D9935E220ADDD0A2D798CE2B7ADA8D394 | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\Help.ico | image | |
MD5:9CA6D8DCDC3A93521270FCB52C33E491 | SHA256:7056EDA1128F8A3A0C7217885972359CEE99B6A62A62D4BD7BAD79B04D7DB227 | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\CheckProVs.dll | executable | |
MD5:5422E399FABD3A344E8DCC807A48637E | SHA256:64E6AAD5D6628BC743196A42E28DF3F8DC71CDF0D2AD4C250BAB872D2A3991C7 | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\track_Official-com.txt | text | |
MD5:FA52EC95F4829013CDFD7EC9B8B1E533 | SHA256:8BDD7A58EFB7679D680D94E1A5067699D4B06161700335E05FC20268E53C75B2 | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\msvcp100.dll | executable | |
MD5:D029339C0F59CF662094EDDF8C42B2B5 | SHA256:934D882EFD3C0F3F1EFBC238EF87708F3879F5BB456D30AF62F3368D58B6AA4C | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\System.dll | executable | |
MD5:86A488BF743DFAB80FF142713ADB5D48 | SHA256:3924B57F8993A880D53E1E4E18EB6BA9B5DC610CBB00345C954C7E8A9078C309 | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\nsDui.dll | executable | |
MD5:368841AF8B0074E348418F106716E603 | SHA256:3BE54DEA5AEDC0D8D16D6C4BD4E046E2D93BFC550A1A035A94768C2D5901E327 | |||
| 2708 | droidkit-en-setup.exe | C:\Users\admin\AppData\Local\Temp\nsbCABC.tmp\dotNetFx45_Full_setup.exe | executable | |
MD5:9E8253F0A993E53B4809DBD74B335227 | SHA256:E434828818F81E6E1F5955E84CAEC08662BD154A80B24A71A2EDA530D8B2F66A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7048 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7048 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 67.225.249.166:443 | https://dl.imobie.com/droidkit64.7z | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7048 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7048 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
dl.imobie.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |