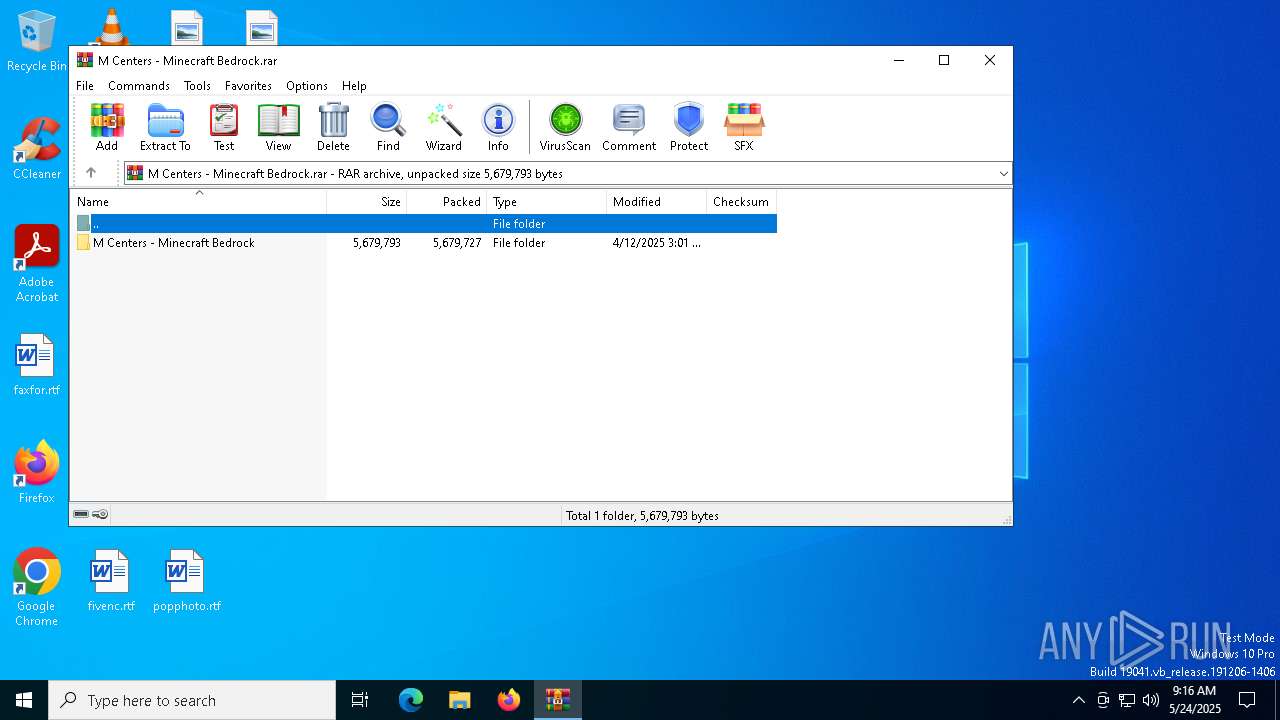
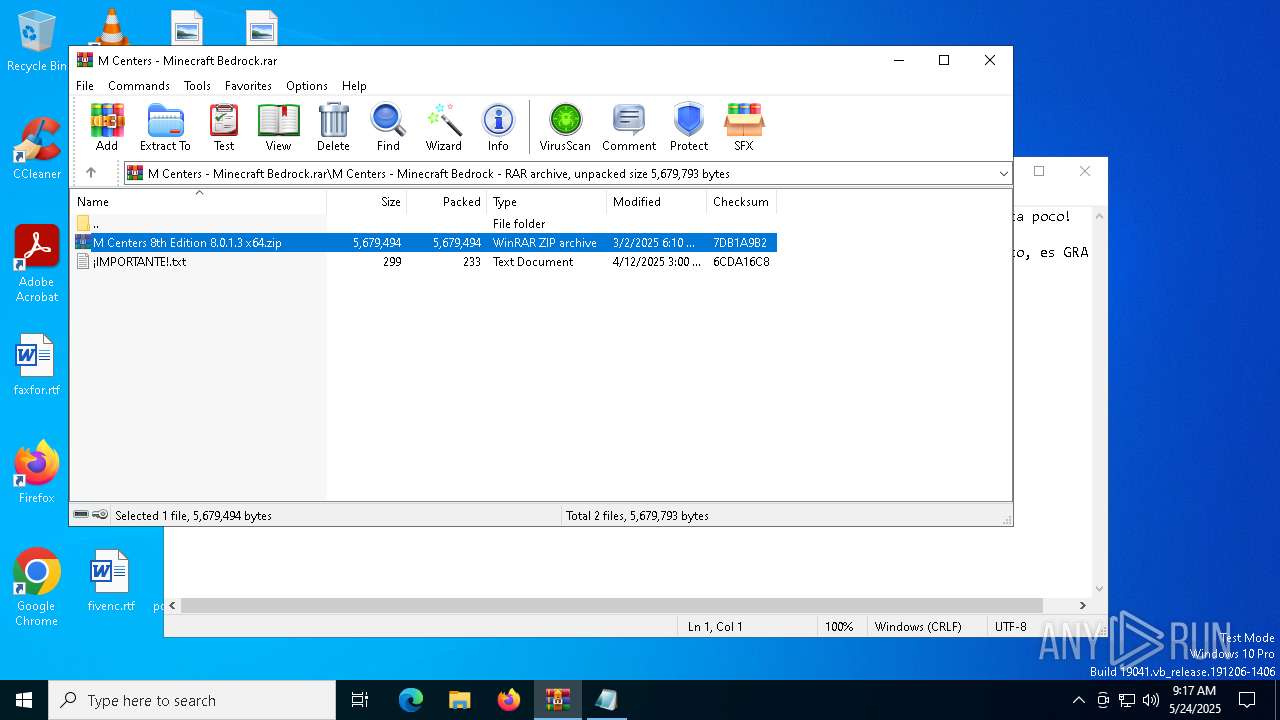
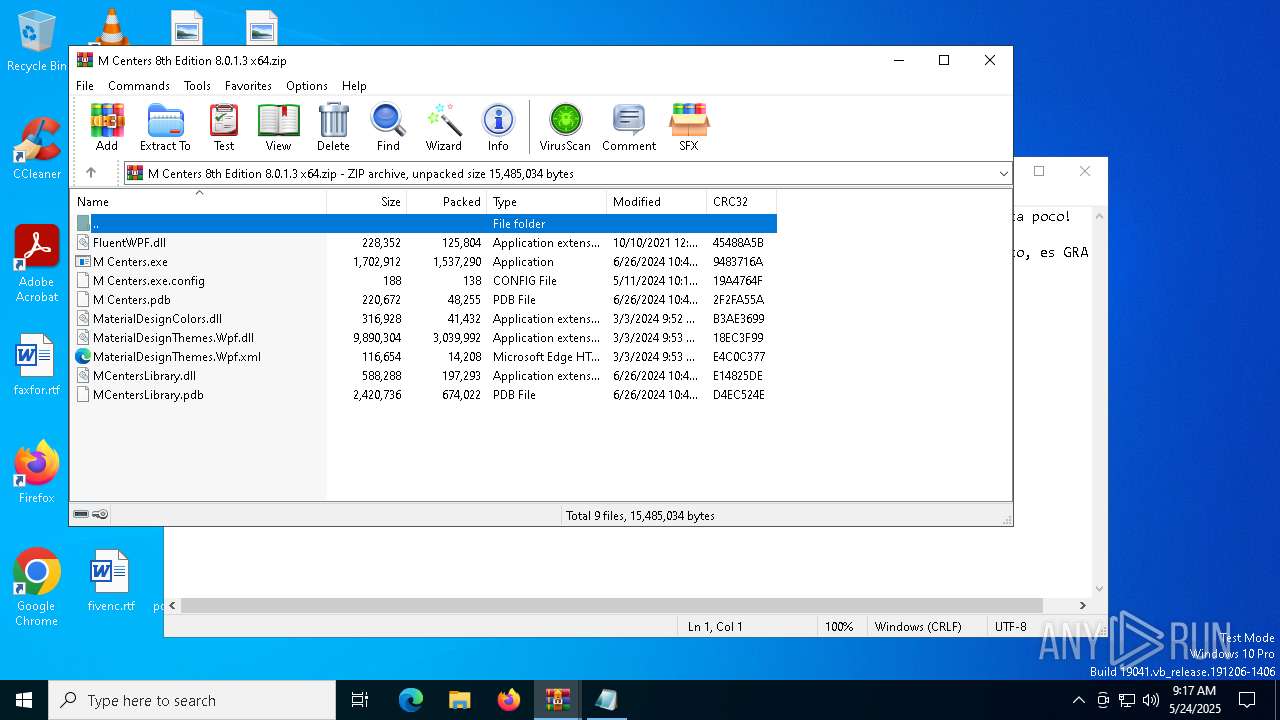
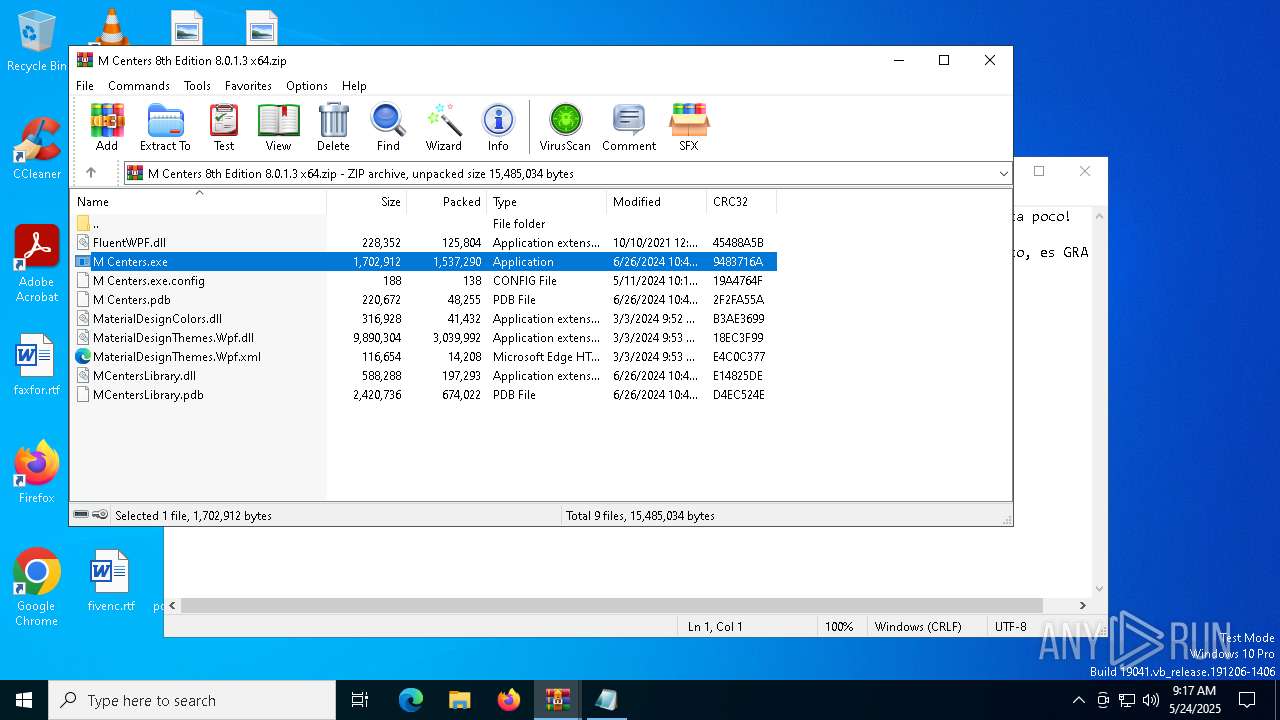
| File name: | M Centers - Minecraft Bedrock.rar |
| Full analysis: | https://app.any.run/tasks/893b3a8f-6592-45c4-b6b6-2b83cfd388d8 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 09:16:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CDE1D4CC14D14126D8FD4C6864F1F1A3 |
| SHA1: | BAD83C37598BCB09F8AA1B702F62F6D86E5A4145 |
| SHA256: | 4E5FB4E49B63C775C2F07D4B0E8D04B3AE70ECC112CA6EDE82A5594AE2ECA565 |
| SSDEEP: | 98304:crdi5SFDA2BoLpKuiZUwHKvCecouqe1QnG43FX1fezTCO8zP8beNokNabAbxAk6E:mkBT5Ky0KT |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7276)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7276)
- WinRAR.exe (PID: 2104)
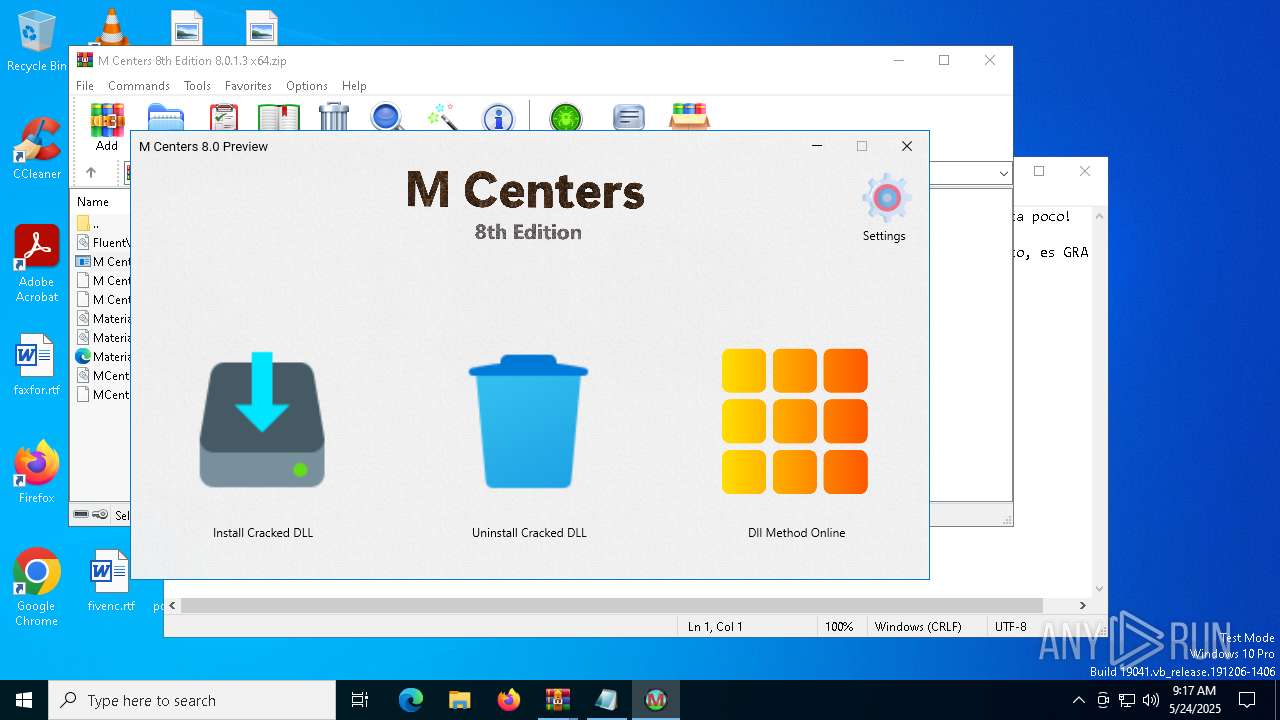
- M Centers.exe (PID: 920)
Application launched itself
- WinRAR.exe (PID: 7276)
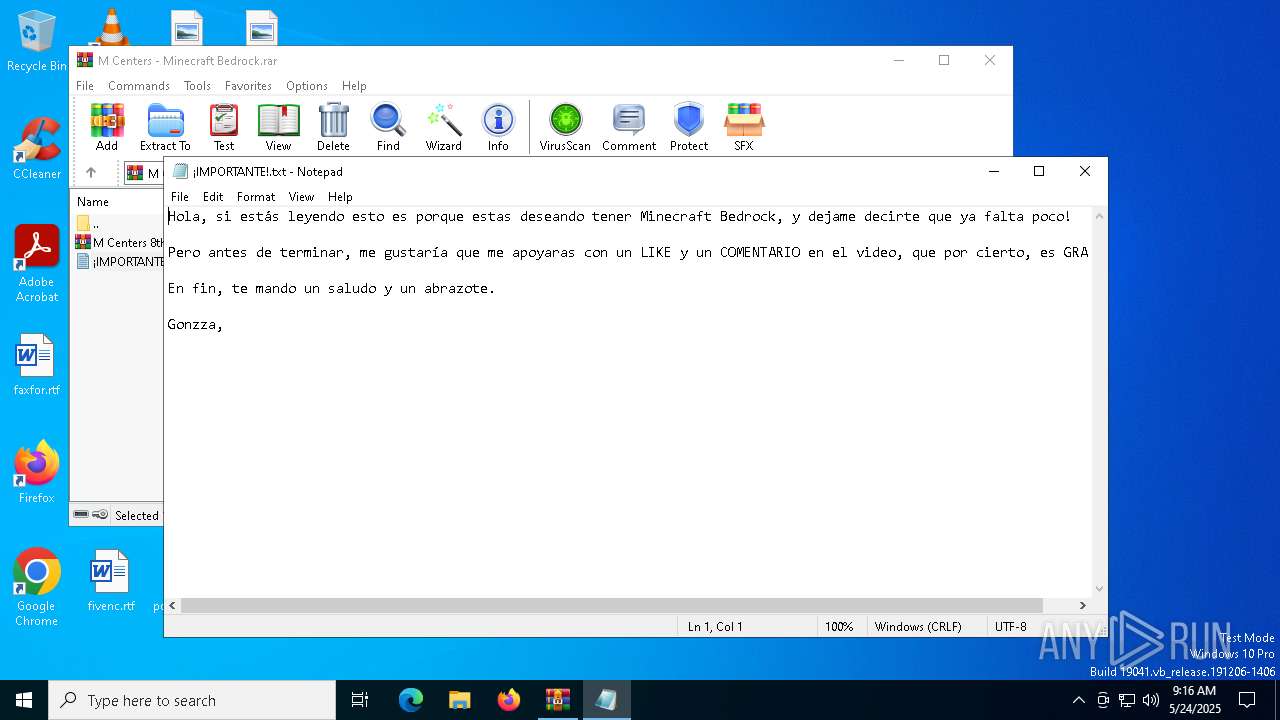
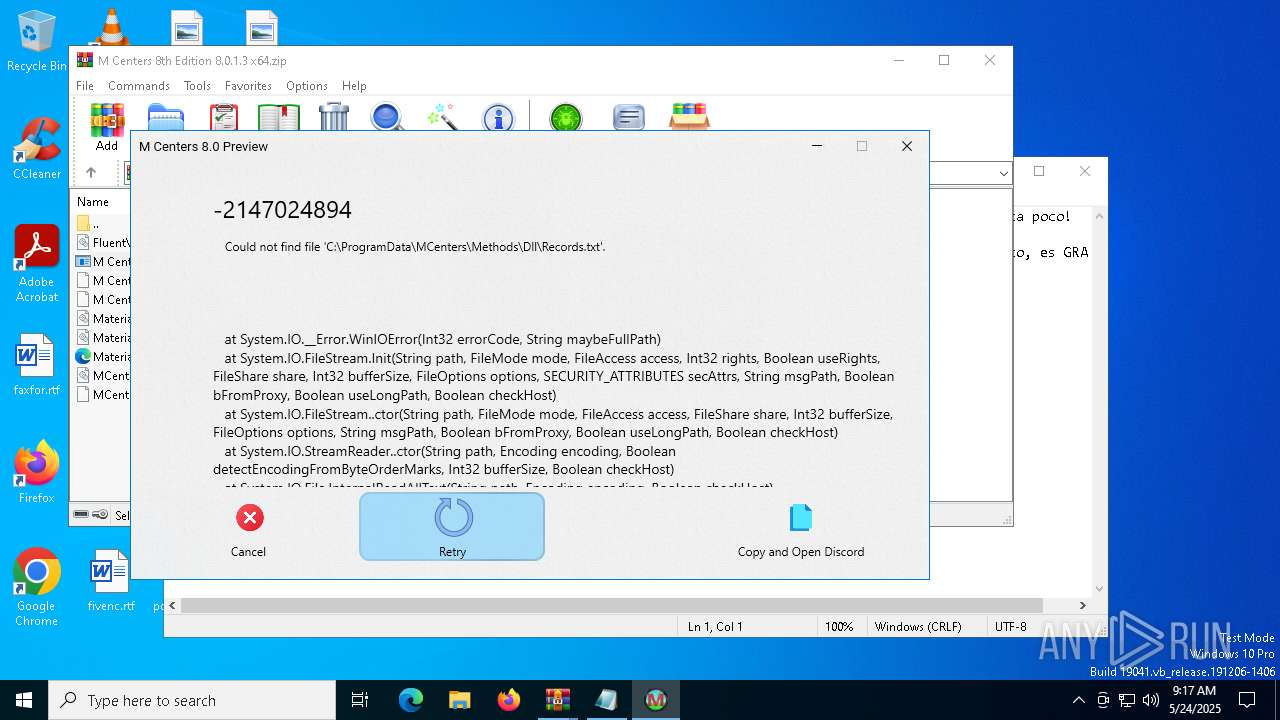
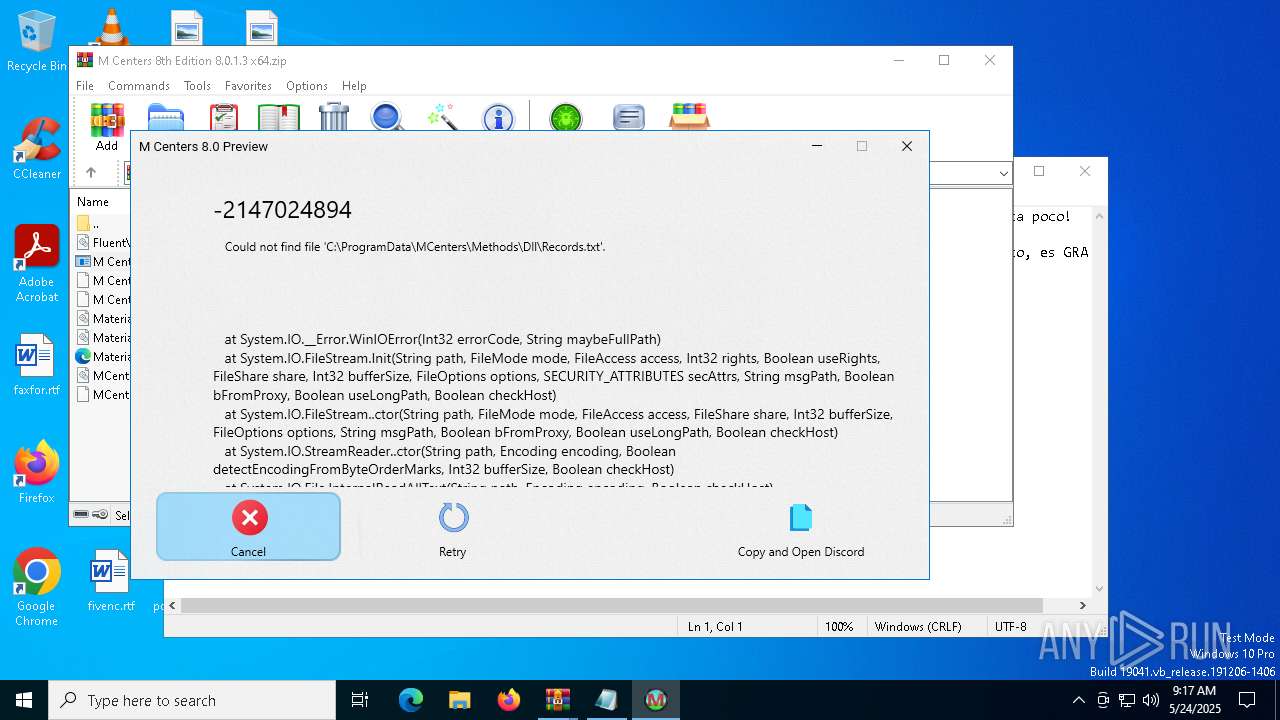
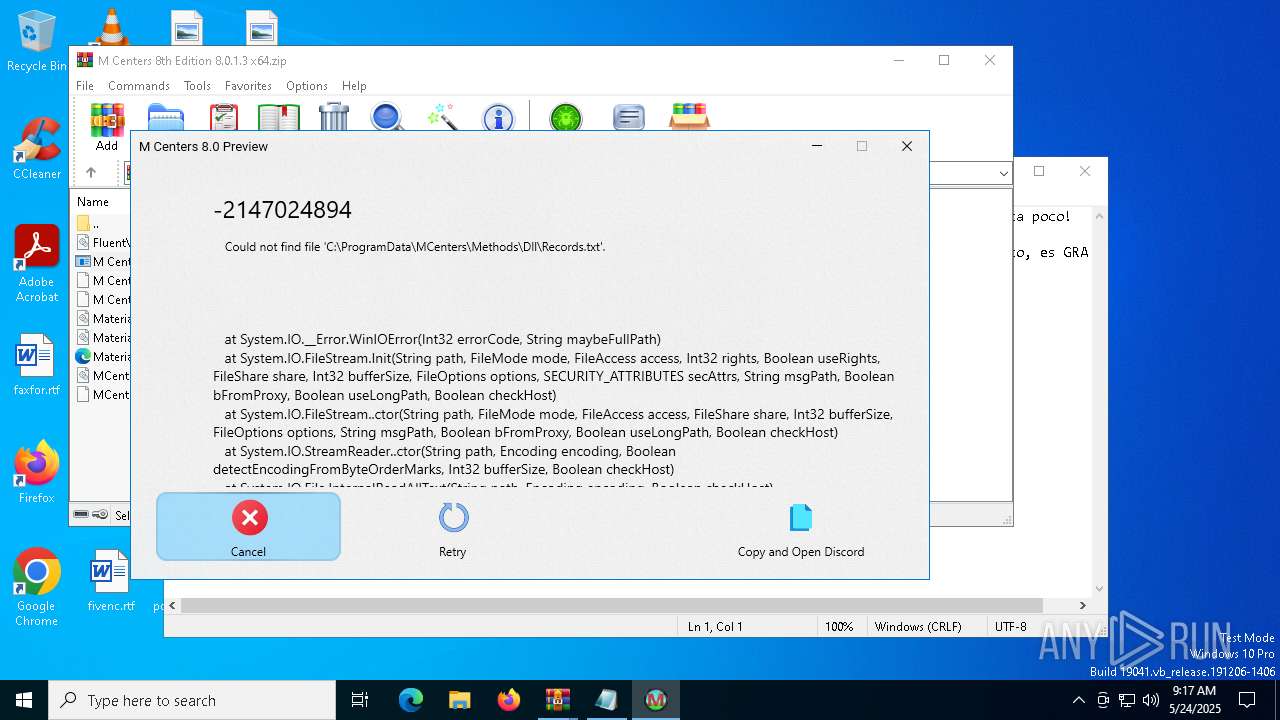
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 7276)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7276)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5256)
The sample compiled with english language support
- WinRAR.exe (PID: 7276)
- WinRAR.exe (PID: 2104)
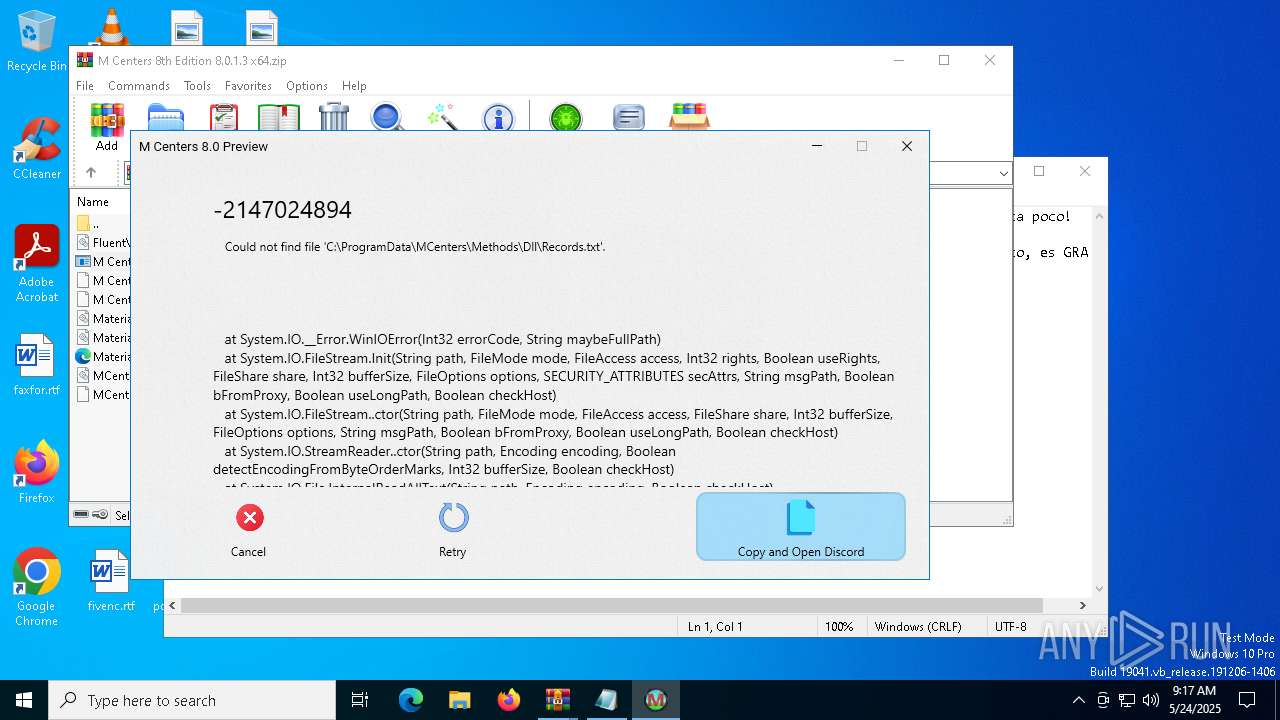
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2104)
Checks supported languages
- M Centers.exe (PID: 920)
Reads the computer name
- M Centers.exe (PID: 920)
Reads the machine GUID from the registry
- M Centers.exe (PID: 920)
Reads Environment values
- M Centers.exe (PID: 920)
Disables trace logs
- M Centers.exe (PID: 920)
Checks proxy server information
- M Centers.exe (PID: 920)
Creates files in the program directory
- M Centers.exe (PID: 920)
Reads the software policy settings
- M Centers.exe (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 5679494 |
| UncompressedSize: | 5679494 |
| OperatingSystem: | Win32 |
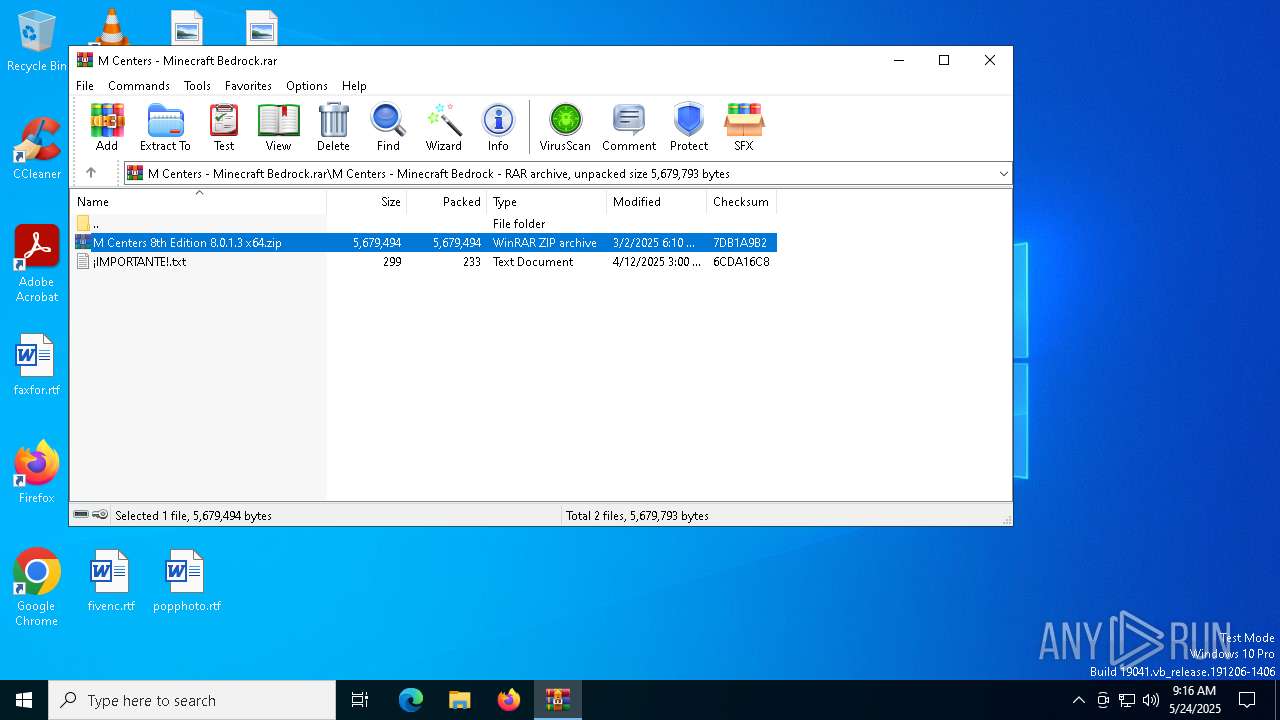
| ArchivedFileName: | M Centers - Minecraft Bedrock/M Centers 8th Edition 8.0.1.3 x64.zip |
Total processes
126
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\M Centers.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\M Centers.exe | WinRAR.exe | ||||||||||||
User: admin Company: M Centers Integrity Level: HIGH Description: M Centers 8th Edition Version: 8.0.1.3 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa7276.3515\M Centers 8th Edition 8.0.1.3 x64.zip" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4812 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa7276.1892\¡IMPORTANTE!.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5428 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\M Centers.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\M Centers.exe | — | WinRAR.exe | |||||||||||
User: admin Company: M Centers Integrity Level: MEDIUM Description: M Centers 8th Edition Exit code: 3221226540 Version: 8.0.1.3 Modules
| |||||||||||||||
| 6040 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7276 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\M Centers - Minecraft Bedrock.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 409
Read events
6 378
Write events
31
Delete events
0
Modification events
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\M Centers - Minecraft Bedrock.rar | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
5
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7276.3515\M Centers 8th Edition 8.0.1.3 x64.zip | compressed | |
MD5:45E79C6885617D804B3CD32374B73C35 | SHA256:FD7AF6283FEED5A93D769D404BFC3A6F1F8361823CBB51D12A9EE9A5640AE654 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\FluentWPF.dll | executable | |
MD5:908668FFDE26AB371A2EF711206AA05D | SHA256:8E136EC981ED7D7ABF0C8153DB901FCD9E7A311A61E209D88A9CA2B51FC17838 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\M Centers.pdb | binary | |
MD5:A0D02EB06DFE43AEF9CB905E2B86EBD9 | SHA256:CA4C956947FDFCAE838FD27CF9A719A97AB43F85AB994FCCB352662ED0AFED37 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\MaterialDesignThemes.Wpf.dll | executable | |
MD5:05347205B59C343705C5B1DA21D8F9D3 | SHA256:F8144C2D063144A98E6FAA4E4D6F11CB3D08D20313E196CDD03ADDB8186CA6FD | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\MCentersLibrary.pdb | binary | |
MD5:3871173661F95706FC1E6A5A698D0E77 | SHA256:5BD064D84D0650070F855F5C56EF2116F963938E2AE992179041D4DD3977FA1A | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\MaterialDesignThemes.Wpf.xml | xml | |
MD5:1BB82BBB22468938D4B9D2D138C548FB | SHA256:D016AA634C248F9F6D954C4E8836996637C8D2F2E01077E99F58D3D64DAADDFD | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\MCentersLibrary.dll | executable | |
MD5:B7E0FAE475B740863FF755F83C797D81 | SHA256:A72909C32B024DD8304BD62472A18B778411456AF0FC1AC74DE762D1258917E3 | |||
| 7276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7276.1892\¡IMPORTANTE!.txt | text | |
MD5:B33309006BC0A50EAC862432E81B9E65 | SHA256:24E48B19FCB9A087CCA0EF8E8BA72CE75F6F5034B921BDE6B56B0C7946F33535 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\M Centers.exe | executable | |
MD5:1D3D75FA1C81B55D68500D95A92807FB | SHA256:5F405489A7F6C67BBCC130EBBB272A99BDE94B0D01B1B958F6F05580FB58A2D3 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.4283\M Centers.exe.config | xml | |
MD5:FC89142FBA7697E848F0E0C5951D86F1 | SHA256:D9FF2B6C916E5B42BC486855EEBFBD9E5E409C01D49FC264850FDE2AC9268820 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
12
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1388 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2560 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7000 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7000 | SIHClient.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |