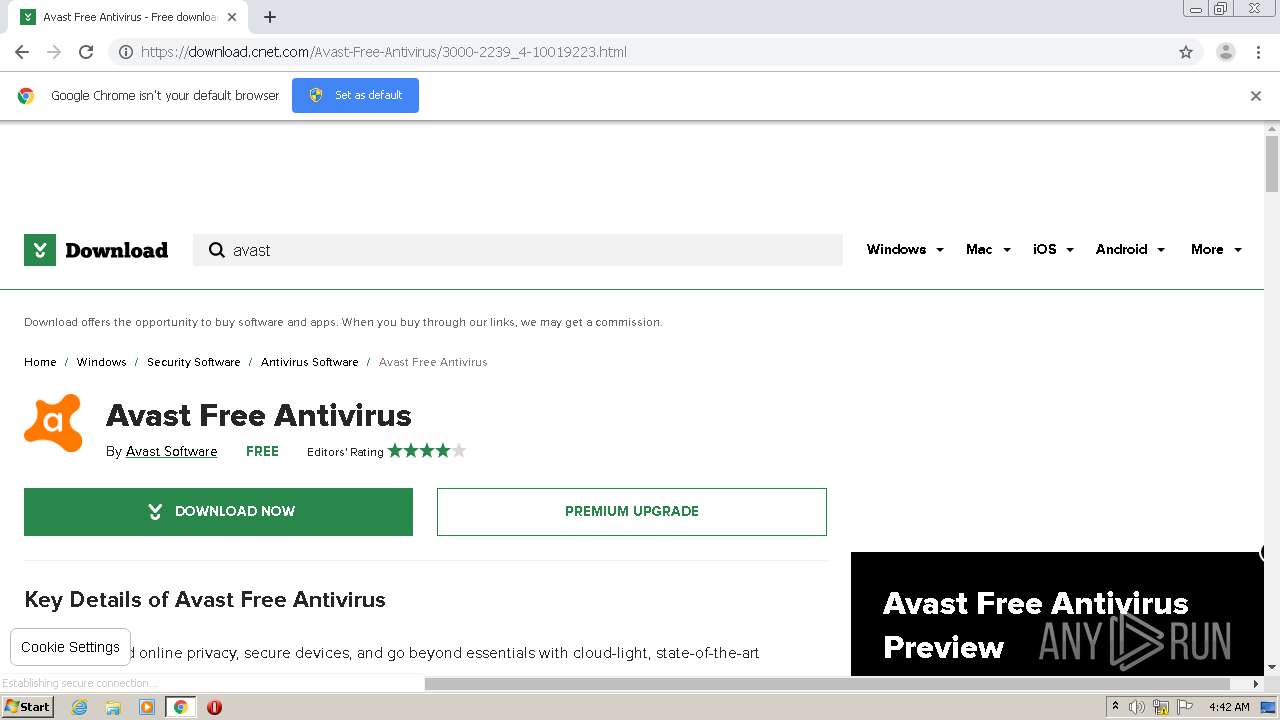
| URL: | https://download.cnet.com |
| Full analysis: | https://app.any.run/tasks/9b759011-c00f-4474-868b-a4ee1db5e838 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 04:41:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C723A854F6DC861558ED1F1113640514 |
| SHA1: | EF6B096B4FD229FFA0D2DCDF11363856CD9C21CE |
| SHA256: | 4E48F50212796E0E285D4A35AAF822C2DAE1D1325360CE9FB956BE82F03593E7 |
| SSDEEP: | 3:N8SElbKn:2SKmn |
MALICIOUS
Application was dropped or rewritten from another process
- ccsetup570.exe (PID: 3808)
- ccsetup570.exe (PID: 3392)
- avira_en_sptl1_329929279-1606711496__adwg.exe (PID: 4004)
- avira_en_sptl1_329929279-1606711496__adwg.exe (PID: 3188)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 3724)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- Avira.OE.Setup.Bundle.exe (PID: 2588)
- Avira.OE.Setup.Prerequisites.exe (PID: 2712)
- Avira.OE.Setup.Prerequisites.exe (PID: 2692)
- Avira.ServiceHost.exe (PID: 2080)
- ccsetup570.exe (PID: 904)
- Avira.Systray.exe (PID: 2172)
- Avira.Systray.exe (PID: 2952)
- ccsetup570.exe (PID: 620)
- avira_system_speedup.exe (PID: 2548)
- Avira.SystemSpeedup.Core.Common.Starter.exe (PID: 4056)
Changes settings of System certificates
- ccsetup570.exe (PID: 3808)
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- Avira.ServiceHost.exe (PID: 2080)
Loads dropped or rewritten executable
- ccsetup570.exe (PID: 3808)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- rundll32.exe (PID: 2424)
- rundll32.exe (PID: 3592)
- rundll32.exe (PID: 3308)
- rundll32.exe (PID: 3480)
- rundll32.exe (PID: 3876)
- rundll32.exe (PID: 2052)
- rundll32.exe (PID: 3304)
- rundll32.exe (PID: 1716)
- rundll32.exe (PID: 1068)
- rundll32.exe (PID: 2828)
- rundll32.exe (PID: 1704)
- rundll32.exe (PID: 3324)
- rundll32.exe (PID: 2552)
- Avira.ServiceHost.exe (PID: 2080)
- rundll32.exe (PID: 3044)
- rundll32.exe (PID: 2924)
- rundll32.exe (PID: 4020)
- Avira.Systray.exe (PID: 2172)
- rundll32.exe (PID: 328)
- Avira.Systray.exe (PID: 2952)
- rundll32.exe (PID: 1996)
- ccsetup570.exe (PID: 620)
- Avira.SystemSpeedup.Core.Common.Starter.exe (PID: 4056)
Actions looks like stealing of personal data
- ccsetup570.exe (PID: 3808)
- Avira.ServiceHost.exe (PID: 2080)
Drops executable file immediately after starts
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 3724)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- Avira.OE.Setup.Bundle.exe (PID: 2588)
- rundll32.exe (PID: 3308)
- rundll32.exe (PID: 2424)
- rundll32.exe (PID: 3480)
- rundll32.exe (PID: 1716)
- rundll32.exe (PID: 2052)
- rundll32.exe (PID: 2828)
- rundll32.exe (PID: 1068)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 3044)
- rundll32.exe (PID: 2924)
- rundll32.exe (PID: 4020)
- rundll32.exe (PID: 328)
- avira_system_speedup.exe (PID: 2548)
- avira_system_speedup.tmp (PID: 2340)
- rundll32.exe (PID: 1996)
- cmd.exe (PID: 1140)
Changes the autorun value in the registry
- Avira.OE.Setup.Bundle.exe (PID: 2588)
Uses Task Scheduler to run other applications
- MsiExec.exe (PID: 2488)
- avira_system_speedup.tmp (PID: 2340)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2424)
- schtasks.exe (PID: 1792)
- schtasks.exe (PID: 2524)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2236)
- ccsetup570.exe (PID: 3808)
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 3724)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- Avira.OE.Setup.Bundle.exe (PID: 2588)
- rundll32.exe (PID: 3308)
- rundll32.exe (PID: 2424)
- rundll32.exe (PID: 3480)
- msiexec.exe (PID: 2984)
- rundll32.exe (PID: 2052)
- rundll32.exe (PID: 1716)
- rundll32.exe (PID: 1068)
- rundll32.exe (PID: 2828)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 3044)
- rundll32.exe (PID: 2924)
- rundll32.exe (PID: 4020)
- rundll32.exe (PID: 328)
- rundll32.exe (PID: 1996)
- ccsetup570.exe (PID: 620)
- avira_system_speedup.exe (PID: 2548)
- avira_system_speedup.tmp (PID: 2340)
- cmd.exe (PID: 1140)
Drops a file with a compile date too recent
- chrome.exe (PID: 2236)
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 3724)
- Avira.OE.Setup.Bundle.exe (PID: 2588)
- rundll32.exe (PID: 2424)
- rundll32.exe (PID: 3308)
- rundll32.exe (PID: 3480)
- rundll32.exe (PID: 2052)
- rundll32.exe (PID: 1716)
- msiexec.exe (PID: 2984)
- rundll32.exe (PID: 2828)
- rundll32.exe (PID: 1068)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 3044)
- rundll32.exe (PID: 2924)
- rundll32.exe (PID: 4020)
- rundll32.exe (PID: 328)
- rundll32.exe (PID: 1996)
- avira_system_speedup.tmp (PID: 2340)
Uses RUNDLL32.EXE to load library
- chrome.exe (PID: 2236)
- MsiExec.exe (PID: 2488)
Low-level read access rights to disk partition
- ccsetup570.exe (PID: 3808)
- ccsetup570.exe (PID: 620)
Drops a file that was compiled in debug mode
- ccsetup570.exe (PID: 3808)
- chrome.exe (PID: 2236)
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 3724)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- Avira.OE.Setup.Bundle.exe (PID: 2588)
- rundll32.exe (PID: 2424)
- rundll32.exe (PID: 3308)
- rundll32.exe (PID: 3480)
- rundll32.exe (PID: 2052)
- rundll32.exe (PID: 1716)
- msiexec.exe (PID: 2984)
- rundll32.exe (PID: 2828)
- rundll32.exe (PID: 1068)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 3044)
- rundll32.exe (PID: 2924)
- rundll32.exe (PID: 328)
- rundll32.exe (PID: 4020)
- rundll32.exe (PID: 1996)
- avira_system_speedup.tmp (PID: 2340)
- ccsetup570.exe (PID: 620)
Starts application with an unusual extension
- ccsetup570.exe (PID: 3808)
- ccsetup570.exe (PID: 620)
Reads Environment values
- ccsetup570.exe (PID: 3808)
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- Avira.ServiceHost.exe (PID: 2080)
- avira_system_speedup.tmp (PID: 2340)
- ccsetup570.exe (PID: 620)
Adds / modifies Windows certificates
- ccsetup570.exe (PID: 3808)
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- Avira.ServiceHost.exe (PID: 2080)
Reads CPU info
- ccsetup570.exe (PID: 3808)
- ccsetup570.exe (PID: 620)
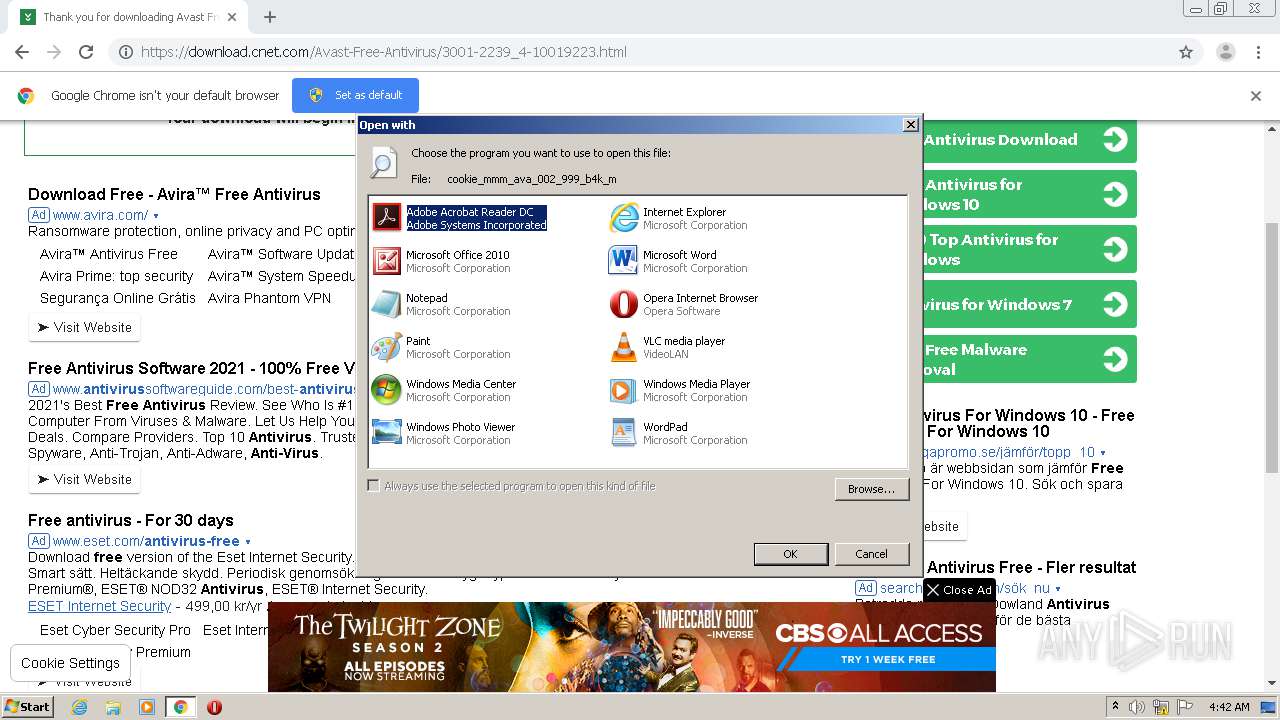
Reads the cookies of Mozilla Firefox
- ccsetup570.exe (PID: 3808)
- Avira.ServiceHost.exe (PID: 2080)
Creates files in the user directory
- ccsetup570.exe (PID: 3808)
- Avira.ServiceHost.exe (PID: 2080)
Searches for installed software
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- Avira.ServiceHost.exe (PID: 2080)
Reads internet explorer settings
- ccsetup570.exe (PID: 3808)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
Reads the cookies of Google Chrome
- ccsetup570.exe (PID: 3808)
- Avira.ServiceHost.exe (PID: 2080)
Creates files in the Windows directory
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 3724)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- Avira.ServiceHost.exe (PID: 2080)
- avira_system_speedup.tmp (PID: 2340)
Changes IE settings (feature browser emulation)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- Avira.Systray.exe (PID: 2952)
- Avira.Systray.exe (PID: 2172)
Starts itself from another location
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
Creates files in the program directory
- Avira.OE.Setup.Bundle.exe (PID: 2588)
- rundll32.exe (PID: 3592)
- rundll32.exe (PID: 1704)
- Avira.ServiceHost.exe (PID: 2080)
- rundll32.exe (PID: 4020)
- Avira.Systray.exe (PID: 2952)
- cmd.exe (PID: 1140)
Creates a software uninstall entry
- Avira.OE.Setup.Bundle.exe (PID: 2588)
- rundll32.exe (PID: 1716)
- rundll32.exe (PID: 3044)
Removes files from Windows directory
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 1768)
- Avira.ServiceHost.exe (PID: 2080)
- avira_en__329929279-1606711496__adwg-spotlight-default.exe (PID: 3724)
Creates a directory in Program Files
- msiexec.exe (PID: 2984)
- avira_system_speedup.tmp (PID: 2340)
Drops a file with too old compile date
- msiexec.exe (PID: 2984)
Changes the autorun value in the registry
- msiexec.exe (PID: 2984)
Executed as Windows Service
- Avira.ServiceHost.exe (PID: 2080)
Reads Windows owner or organization settings
- avira_system_speedup.tmp (PID: 2340)
Reads the Windows organization settings
- avira_system_speedup.tmp (PID: 2340)
Creates COM task schedule object
- RegAsm.exe (PID: 2788)
Starts CMD.EXE for commands execution
- avira_system_speedup.tmp (PID: 2340)
INFO
Application launched itself
- chrome.exe (PID: 2236)
- msiexec.exe (PID: 2984)
Reads the hosts file
- chrome.exe (PID: 2236)
- chrome.exe (PID: 2664)
Reads settings of System Certificates
- chrome.exe (PID: 2236)
- chrome.exe (PID: 2664)
- ccsetup570.exe (PID: 3808)
- Avira.Spotlight.Bootstrapper.exe (PID: 2216)
- rundll32.exe (PID: 3876)
- Avira.ServiceHost.exe (PID: 2080)
Manual execution by user
- explorer.exe (PID: 3896)
- ccsetup570.exe (PID: 904)
- ccsetup570.exe (PID: 620)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2488)
- msiexec.exe (PID: 2984)
- avira_system_speedup.tmp (PID: 2340)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 2984)
Creates files in the program directory
- msiexec.exe (PID: 2984)
- avira_system_speedup.tmp (PID: 2340)
Creates a software uninstall entry
- msiexec.exe (PID: 2984)
Application was dropped or rewritten from another process
- avira_system_speedup.tmp (PID: 2340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
147
Monitored processes
86
Malicious processes
35
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | rundll32.exe "C:\Windows\Installer\MSIBCA.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1903546 235 Avira.OE.Setup.CustomActions!Avira.OE.Setup.CustomActions.ServiceHostLogFilesFolderAccess.SetServiceHostLogFileFolderAccess | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15907635839552640485,10760742883903349,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5774531414306062463 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3824 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,15907635839552640485,10760742883903349,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=522988911484476397 --mojo-platform-channel-handle=5124 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
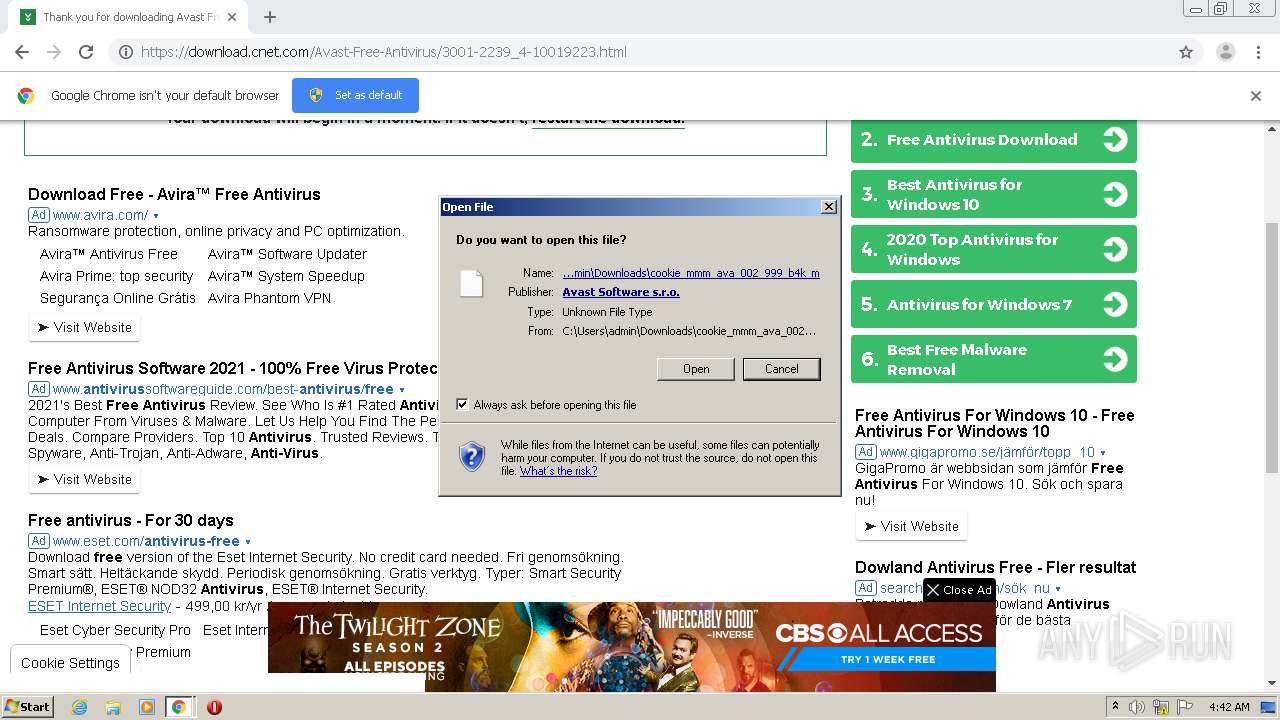
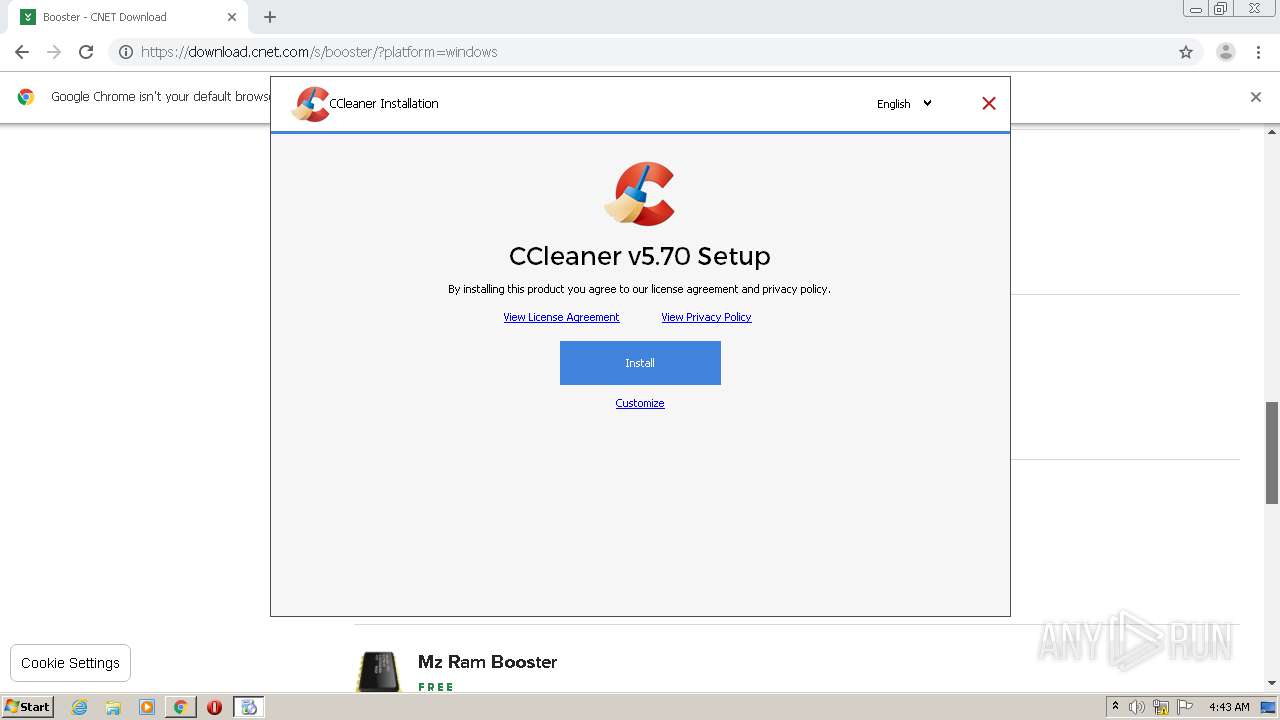
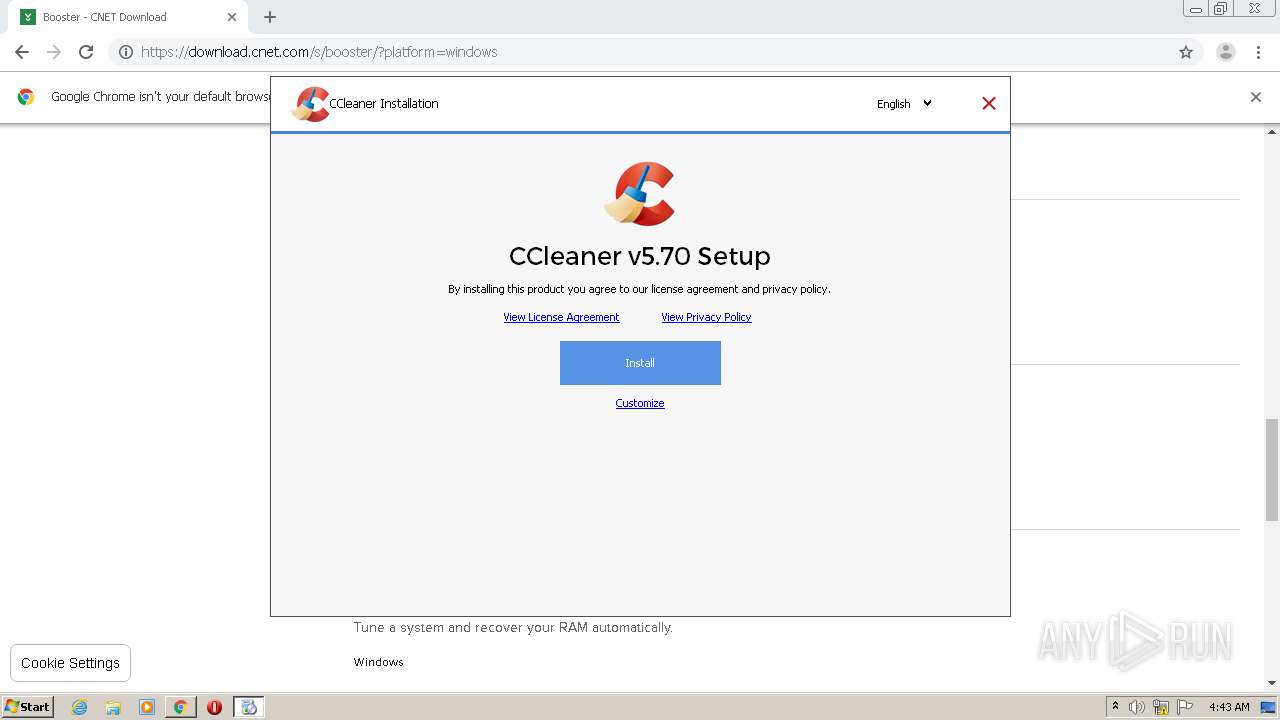
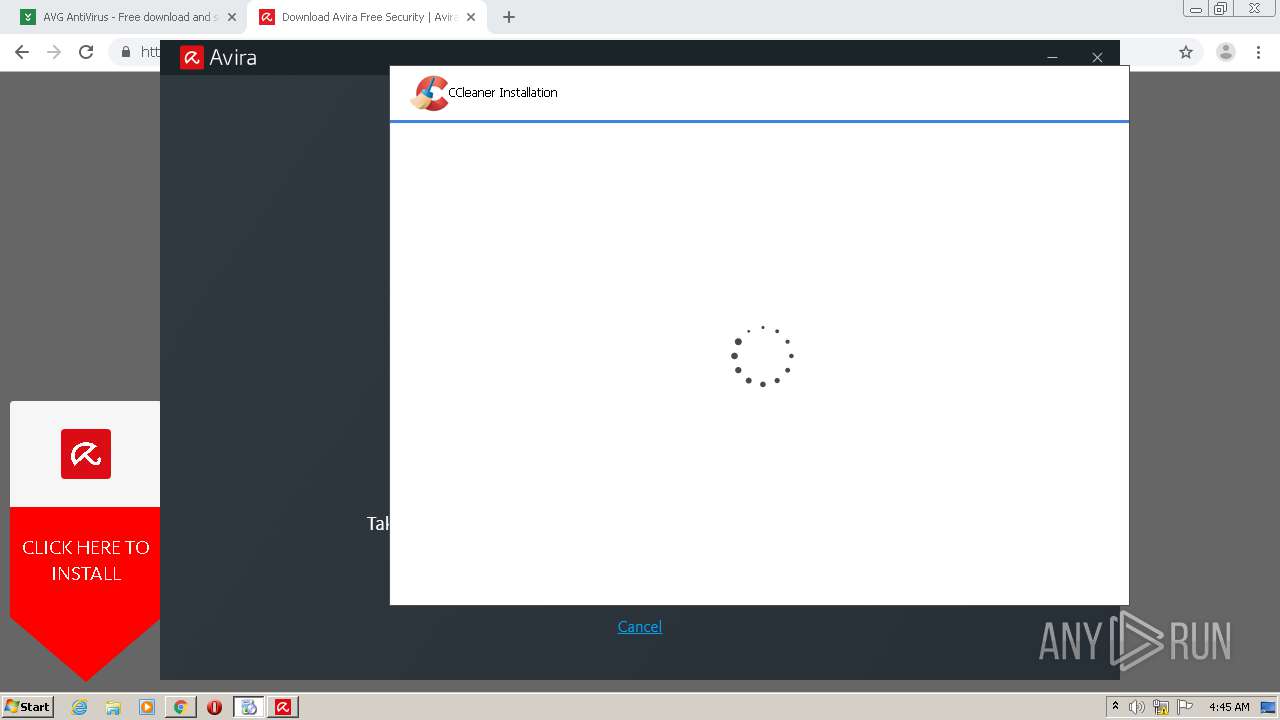
| 620 | "C:\Users\admin\Downloads\ccsetup570.exe" | C:\Users\admin\Downloads\ccsetup570.exe | explorer.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Installer Exit code: 0 Version: 5.70.0.7909 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15907635839552640485,10760742883903349,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17014137983718327764 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5220 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15907635839552640485,10760742883903349,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15265777124904587974 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3848 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\Downloads\ccsetup570.exe" | C:\Users\admin\Downloads\ccsetup570.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Installer Exit code: 3221226540 Version: 5.70.0.7909 Modules
| |||||||||||||||
| 912 | C:\Windows\system32\ping.exe -n 1 -w 1000 www.ccleaner.com | C:\Windows\system32\ping.exe | — | ns3D5D.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,15907635839552640485,10760742883903349,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8573637663415630482 --mojo-platform-channel-handle=3856 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1068 | rundll32.exe "C:\Windows\Installer\MSIC174.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1884515 171 Avira.OE.Setup.CustomActions!Avira.OE.Setup.CustomActions.Configuration.SetGdprConsentDate | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 304
Read events
7 535
Write events
744
Delete events
25
Modification events
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2804) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2236-13251184887899125 |
Value: 259 | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2236) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
315
Suspicious files
304
Text files
785
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FC477F8-8BC.pma | — | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\58125e93-3b8d-46d4-a7d4-f380e891494a.tmp | — | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF18d329.TMP | text | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF18d368.TMP | text | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | text | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT~RF18d3d5.TMP | text | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2236 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF18d50e.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
222
DNS requests
143
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3808 | ccsetup570.exe | GET | 200 | 151.101.0.64:80 | http://service.piriform.com/installcheck.aspx?p=1&v=5.70.7909&vx=5.35.6210&l=1033&b=1&o=6.1W3&g=0&i=1&a=0&c=770&d=2&e=31&n=ccsetup570.exe&id=003&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-HZ8S&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gd=26becbe5-c9a9-47b6-b550-917d4a6baf85 | US | text | 4 b | whitelisted |
1768 | avira_en__329929279-1606711496__adwg-spotlight-default.exe | GET | 200 | 93.184.220.29:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR3enuod9bxDxzpICGW%2B2sabjf17QQUkFj%2FsJx1qFFUd7Ht8qNDFjiebMUCEAhpwjriHwb%2BBA3oHNrcctU%3D | US | der | 471 b | whitelisted |
3808 | ccsetup570.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3808 | ccsetup570.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3808 | ccsetup570.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
1768 | avira_en__329929279-1606711496__adwg-spotlight-default.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAVG%2Fhgj9%2BGUHaOfzhTEYXM%3D | US | der | 471 b | whitelisted |
2664 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAKXB1YM1Knrv%2BJy8eCW2II%3D | US | der | 471 b | whitelisted |
3808 | ccsetup570.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
1044 | svchost.exe | GET | 200 | 2.18.233.62:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | der | 813 b | whitelisted |
2080 | Avira.ServiceHost.exe | GET | 200 | 2.16.186.17:80 | http://www.msftncsi.com/ncsi.txt | unknown | text | 14 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2664 | chrome.exe | 151.101.13.188:443 | download.cnet.com | Fastly | US | malicious |
2664 | chrome.exe | 172.217.16.205:443 | accounts.google.com | Google Inc. | US | whitelisted |
2664 | chrome.exe | 104.16.148.64:443 | cdn.cookielaw.org | Cloudflare Inc | US | unknown |
2664 | chrome.exe | 172.217.21.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2664 | chrome.exe | 151.101.129.188:443 | — | Fastly | US | unknown |
2664 | chrome.exe | 104.75.88.141:443 | c.go-mpulse.net | Akamai Technologies, Inc. | NL | unknown |
2664 | chrome.exe | 13.224.190.125:443 | static.chartbeat.com | — | US | unknown |
2664 | chrome.exe | 216.58.212.162:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
2664 | chrome.exe | 151.101.194.202:443 | mab.chartbeat.com | Fastly | US | suspicious |
2664 | chrome.exe | 104.20.184.68:443 | geolocation.onetrust.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.cnet.com |
| whitelisted |
accounts.google.com |
| shared |
dl1.cbsistatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
cdn.cookielaw.org |
| whitelisted |
cmg1.cbsistatic.com |
| unknown |
c.go-mpulse.net |
| whitelisted |
at.cbsi.com |
| suspicious |
securepubads.g.doubleclick.net |
| whitelisted |
static.chartbeat.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
avira_en__329929279-1606711496__adwg-spotlight-default.exe | Launcher Install Start |
avira_en__329929279-1606711496__adwg-spotlight-default.exe | Launcher Install Start |
Avira.ServiceHost.exe | SQLite error (2570): os_win.c:42430: (32) winDelete(C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cookies-journal) - The process cannot access the file because it is being used by another process.
|
Avira.ServiceHost.exe | SQLite error (2570): os_win.c:42430: (32) winDelete(C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cookies-journal) - The process cannot access the file because it is being used by another process.
|
Avira.ServiceHost.exe | SQLite notice (539): recovered 3 pages from C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cookies-journal
|
Avira.ServiceHost.exe | SQLite error (2570): disk I/O error
|
avira_en__329929279-1606711496__adwg-spotlight-default.exe | Launcher Install End |
avira_en__329929279-1606711496__adwg-spotlight-default.exe | ~WebBrowser: Finished
|
avira_en__329929279-1606711496__adwg-spotlight-default.exe | ~WebBrowser: Finished
|
avira_system_speedup.tmp | *** Initialize |