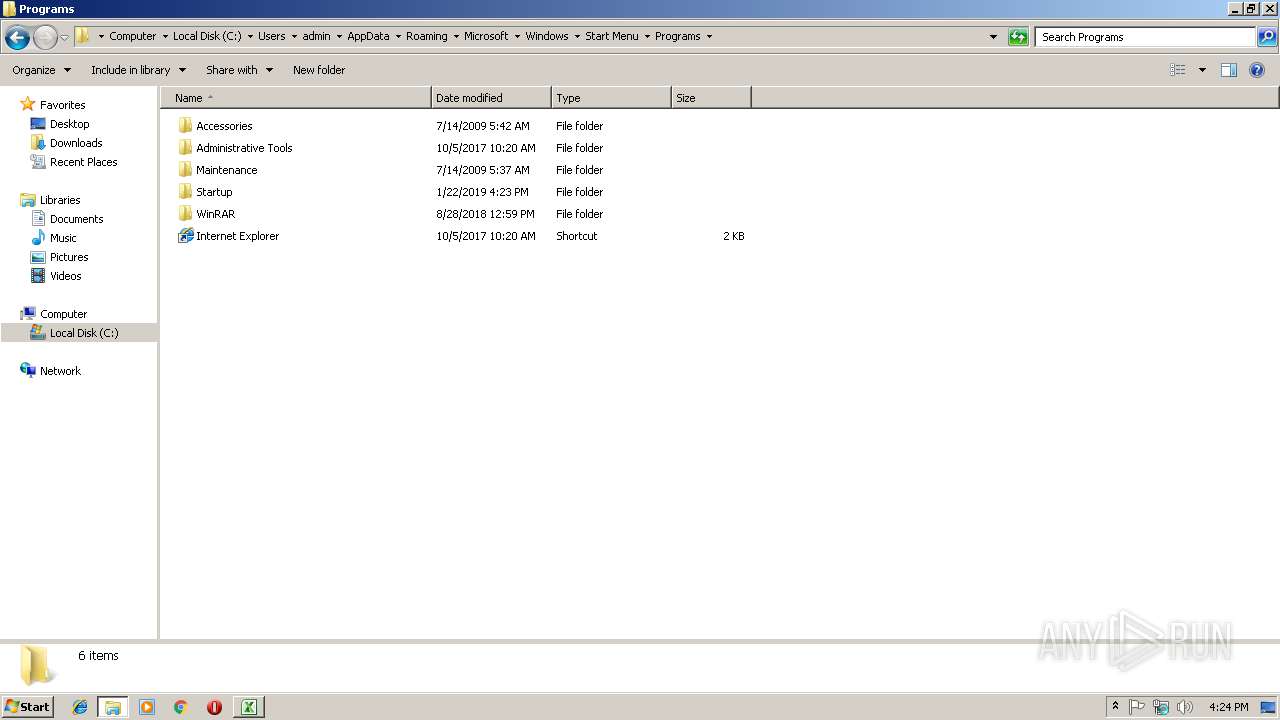
| File name: | 4e40f80114e5bd44a762f6066a3e56ccdc0d01ab2a18397ea12e0bc5508215b8.xlsm |
| Full analysis: | https://app.any.run/tasks/70f917ce-2fff-4c03-a8b2-828080f9ac86 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2019, 16:23:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 89E50D52E498C34F1E976CF9A1017A39 |
| SHA1: | 1B8FE1D2194E685C0CCE2F00C33E7F069F3A4D54 |
| SHA256: | 4E40F80114E5BD44A762F6066A3E56CCDC0D01AB2A18397EA12E0BC5508215B8 |
| SSDEEP: | 768:+N8smH+NiXwkvscronhoVvmSOJGZmoVHshQ5SjkL5pKSCPUK1tgtIxsfG2u:+asmH+MXtshoV+XNot2QEjkL5pK0Kstw |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3012)
Writes to a start menu file
- powershell.exe (PID: 2992)
SUSPICIOUS
Executes PowerShell scripts
- regsvr32.exe (PID: 2712)
Creates files in the user directory
- powershell.exe (PID: 2992)
- notepad++.exe (PID: 3032)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3012)
Creates files in the user directory
- EXCEL.EXE (PID: 3012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (50.8) |
|---|---|---|
| .xlsx | | | Excel Microsoft Office Open XML Format document (30) |
| .zip | | | Open Packaging Conventions container (15.4) |
| .zip | | | ZIP compressed archive (3.5) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x513599ac |
| ZipCompressedSize: | 367 |
| ZipUncompressedSize: | 1087 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | - |
|---|
XML
| LastModifiedBy: | - |
|---|---|
| CreateDate: | 2006:09:16 00:00:00Z |
| ModifyDate: | 2018:12:23 05:45:43Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Sheet1 |
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15.03 |
Total processes
42
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2712 | regsvr32.exe /s /n /u /i:C:\Users\admin\AppData\Local\Temp\12-B-366.txt scrobj.dll | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 2992 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit -exec bypass -File C:\Users\admin\AppData\Local\Temp\WINDOWSTEMP.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | regsvr32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
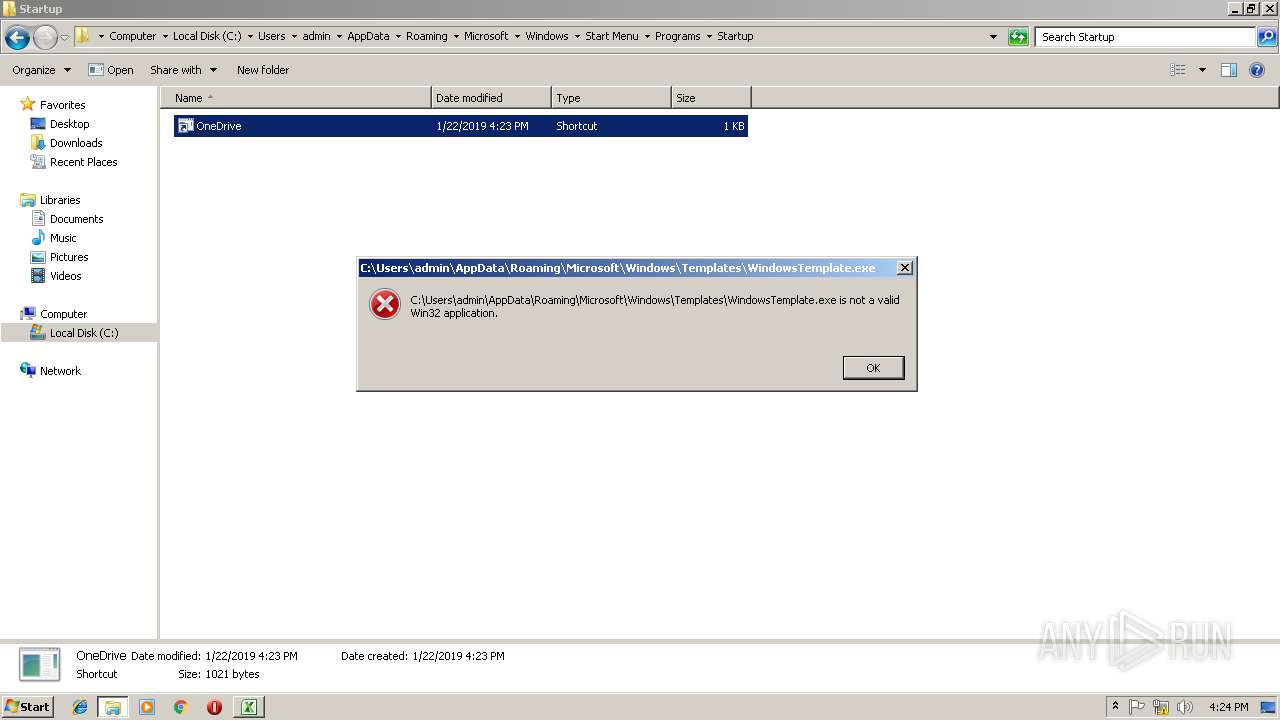
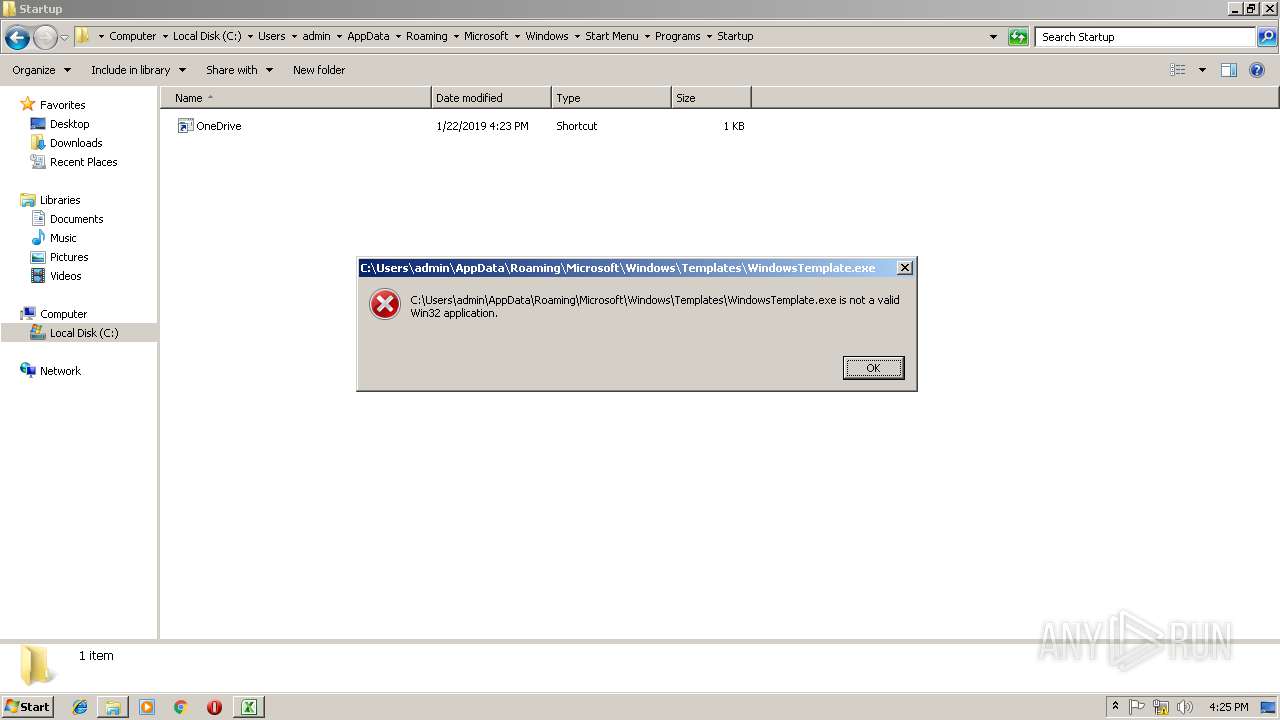
| 3032 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\WindowsTemplate.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
Total events
1 088
Read events
981
Write events
100
Delete events
7
Modification events
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | m30 |
Value: 6D333000C40B0000010000000000000000000000 | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: C40B00007A902BDC6EB2D40100000000 | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | m30 |
Value: 6D333000C40B0000010000000000000000000000 | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\247205 |
| Operation: | write | Name: | 247205 |
Value: 04000000C40B00005C00000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C0034006500340030006600380030003100310034006500350062006400340034006100370036003200660036003000360036006100330065003500360063006300640063003000640030003100610062003200610031003800330039003700650061003100320065003000620063003500350030003800320031003500620038002E0078006C0073006D00000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C000100000000000000B0CA82DD6EB2D401057224000572240000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
2
Text files
10
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3012 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6B4D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2992 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ND7M44W662NISEMA79IT.temp | — | |
MD5:— | SHA256:— | |||
| 3012 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\WINDOWSTEMP.ps1 | text | |
MD5:— | SHA256:— | |||
| 3012 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\12-B-366.txt | xml | |
MD5:— | SHA256:— | |||
| 3012 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\4e40f80114e5bd44a762f6066a3e56ccdc0d01ab2a18397ea12e0bc5508215b8.xlsm.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3012 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2992 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF24789b.TMP | binary | |
MD5:— | SHA256:— | |||
| 2992 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
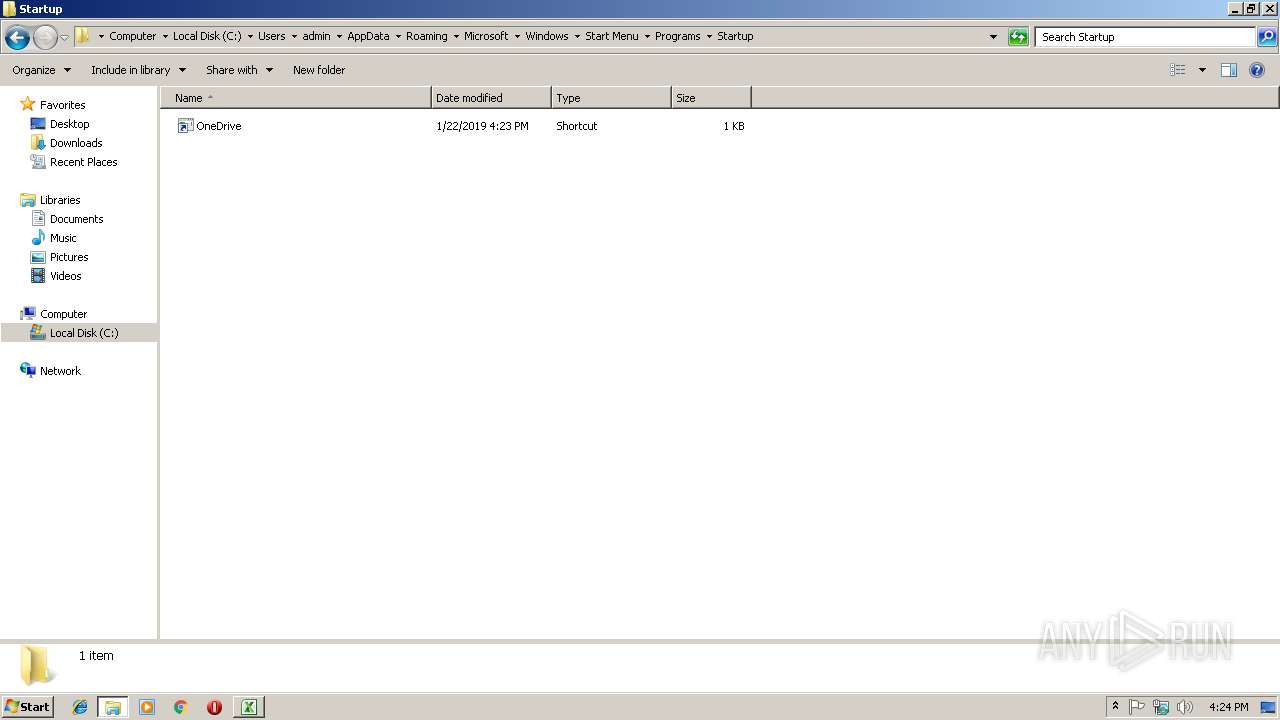
| 2992 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\OneDrive.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3032 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:E792264BEC29005B9044A435FBA185AB | SHA256:5298FD2F119C43D04F6CF831F379EC25B4156192278E40E458EC356F9B49D624 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.106.50:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | unknown | der | 471 b | whitelisted |
— | — | GET | 200 | 2.16.106.50:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | unknown | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2900 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
— | — | 2.16.106.50:80 | ocsp.usertrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|