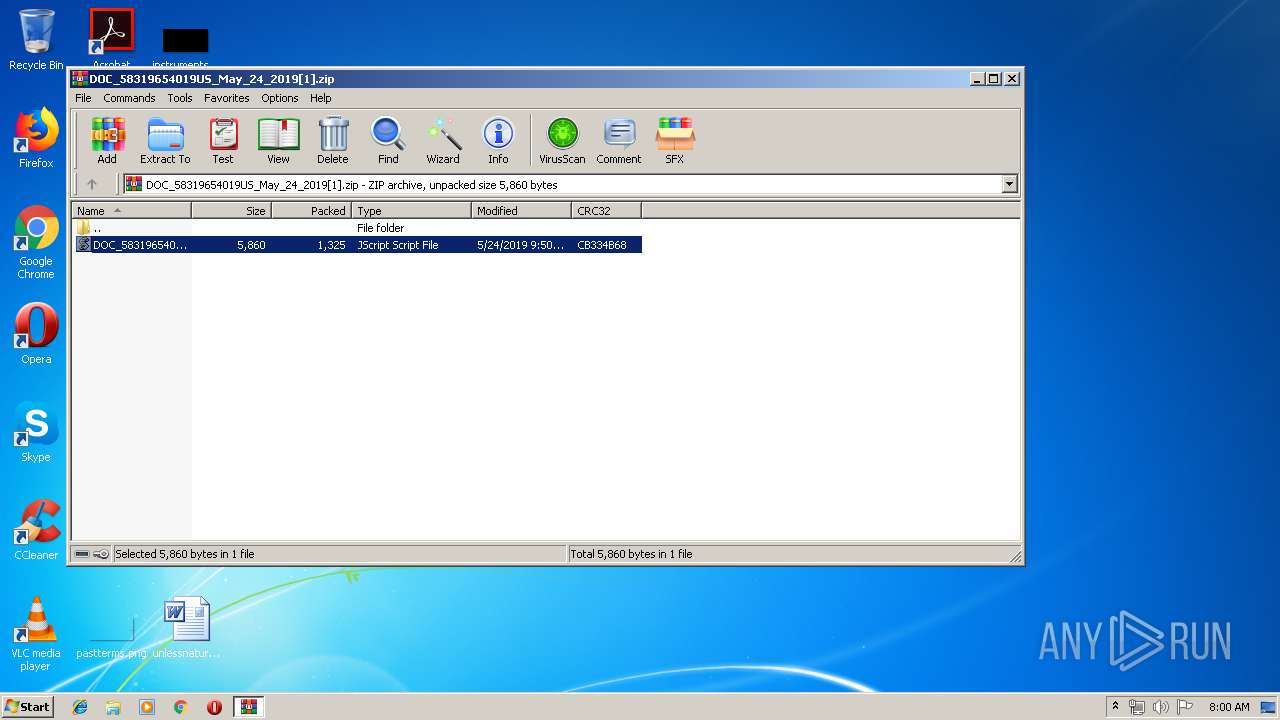
| URL: | http://pianogiaretphcm.com/wp-snapshots/qcTilRKePEJSGkQegx/ |
| Full analysis: | https://app.any.run/tasks/1f164014-86be-48e8-a4ba-0bd5b15f2c71 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 24, 2019, 06:59:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 75D0D5083D559A9A0F558860CBA603E4 |
| SHA1: | C0DA7D3F37CC74E0F9927357D6E64291A78B8C89 |
| SHA256: | 4E2F4F83E16E6224E671959965C04C6A3929048D8464B6B1F88107247A5002D7 |
| SSDEEP: | 3:N1KOME9WNfQfEVWNK/aCI:COF9WRQscKSV |
MALICIOUS
Application was dropped or rewritten from another process
- h42qg3oe5.exe (PID: 2152)
- soundser.exe (PID: 3644)
- h42qg3oe5.exe (PID: 1140)
- soundser.exe (PID: 2652)
Emotet process was detected
- soundser.exe (PID: 3644)
Changes settings of System certificates
- WScript.exe (PID: 2976)
SUSPICIOUS
Adds / modifies Windows certificates
- WScript.exe (PID: 2976)
Executes scripts
- WinRAR.exe (PID: 3100)
Executable content was dropped or overwritten
- WScript.exe (PID: 2976)
- h42qg3oe5.exe (PID: 2152)
Creates files in the user directory
- WScript.exe (PID: 2976)
Connects to server without host name
- soundser.exe (PID: 2652)
Starts itself from another location
- h42qg3oe5.exe (PID: 2152)
Application launched itself
- soundser.exe (PID: 3644)
INFO
Creates files in the user directory
- iexplore.exe (PID: 936)
Changes settings of System certificates
- iexplore.exe (PID: 880)
Changes internet zones settings
- iexplore.exe (PID: 880)
Reads settings of System Certificates
- iexplore.exe (PID: 880)
Reads Internet Cache Settings
- iexplore.exe (PID: 936)
Adds / modifies Windows certificates
- iexplore.exe (PID: 880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
8
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 936 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:880 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\AppData\Local\Temp\h42qg3oe5.exe" | C:\Users\admin\AppData\Local\Temp\h42qg3oe5.exe | — | WScript.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2152 | --b5b3418c | C:\Users\admin\AppData\Local\Temp\h42qg3oe5.exe | h42qg3oe5.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2652 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2976 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3100.20701\DOC_58319654019US_May_24_2019.js" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
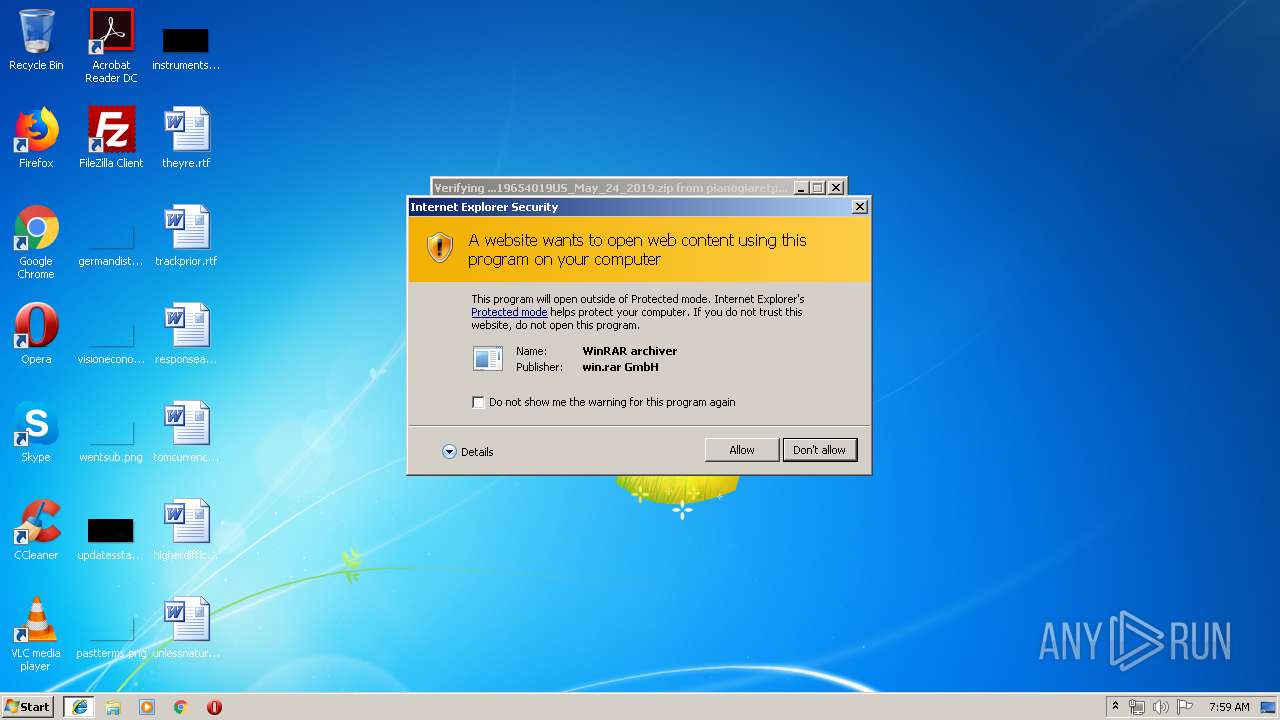
| 3100 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\GF1CO757\DOC_58319654019US_May_24_2019[1].zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | h42qg3oe5.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 548
Read events
1 429
Write events
113
Delete events
6
Modification events
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {832EEB15-7DF1-11E9-B63D-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30705000500180006003B002E004402 | |||
Executable files
2
Suspicious files
2
Text files
13
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 880 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 880 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 880 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFBC3D94A3D511DFBD.TMP | — | |
MD5:— | SHA256:— | |||
| 880 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF314C4D844949BFCC.TMP | — | |
MD5:— | SHA256:— | |||
| 880 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{832EEB15-7DF1-11E9-B63D-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 936 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 936 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@pianogiaretphcm[1].txt | text | |
MD5:— | SHA256:— | |||
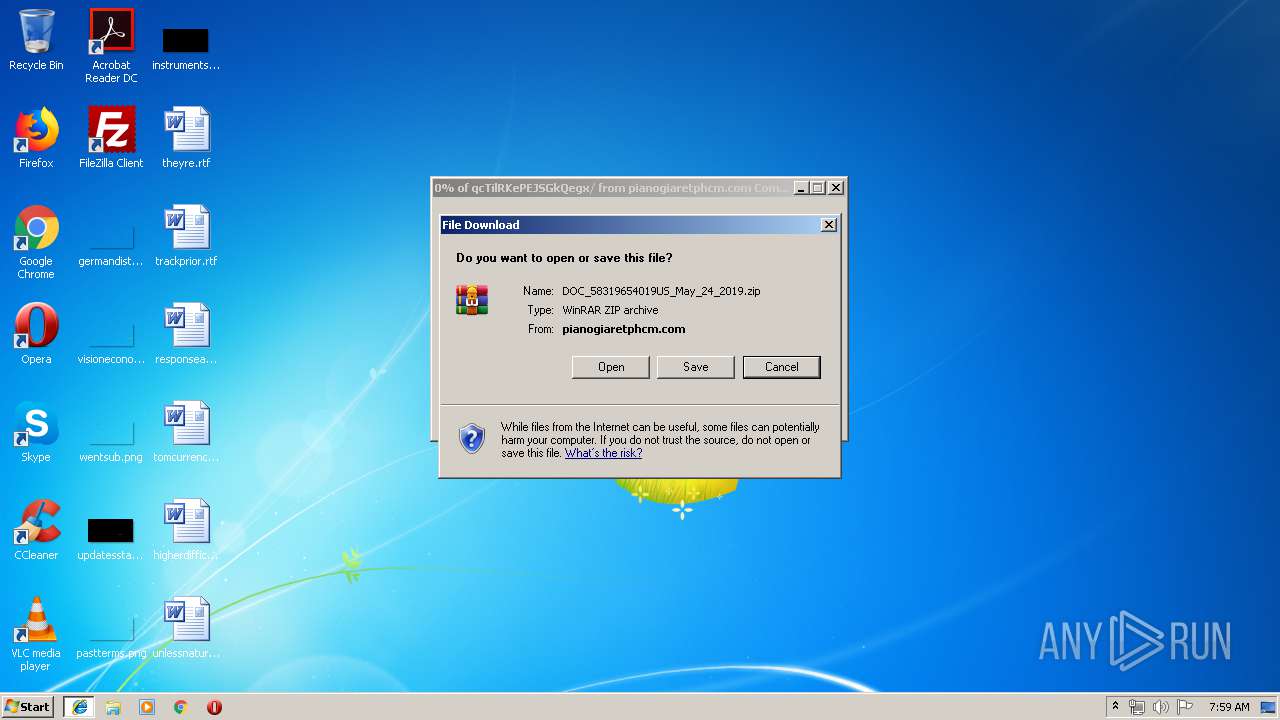
| 936 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\GF1CO757\DOC_58319654019US_May_24_2019[1].zip | compressed | |
MD5:— | SHA256:— | |||
| 2976 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@dnmartin[1].txt | text | |
MD5:— | SHA256:— | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3100.20701\DOC_58319654019US_May_24_2019.js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
936 | iexplore.exe | GET | 200 | 210.211.121.143:80 | http://pianogiaretphcm.com/wp-snapshots/qcTilRKePEJSGkQegx/ | VN | compressed | 1.47 Kb | unknown |
2652 | soundser.exe | POST | — | 76.86.20.103:80 | http://76.86.20.103/forced/sess/ringin/merge/ | US | — | — | malicious |
880 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
880 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2652 | soundser.exe | 76.86.20.103:80 | — | Time Warner Cable Internet LLC | US | malicious |
936 | iexplore.exe | 210.211.121.143:80 | pianogiaretphcm.com | CHT Compamy Ltd | VN | unknown |
2976 | WScript.exe | 51.38.185.91:443 | dnmartin.net | — | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
pianogiaretphcm.com |
| unknown |
dnmartin.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
936 | iexplore.exe | Misc activity | ET INFO SUSPICIOUS Single JS file inside of ZIP Download (Observed as lure in malspam campaigns) |