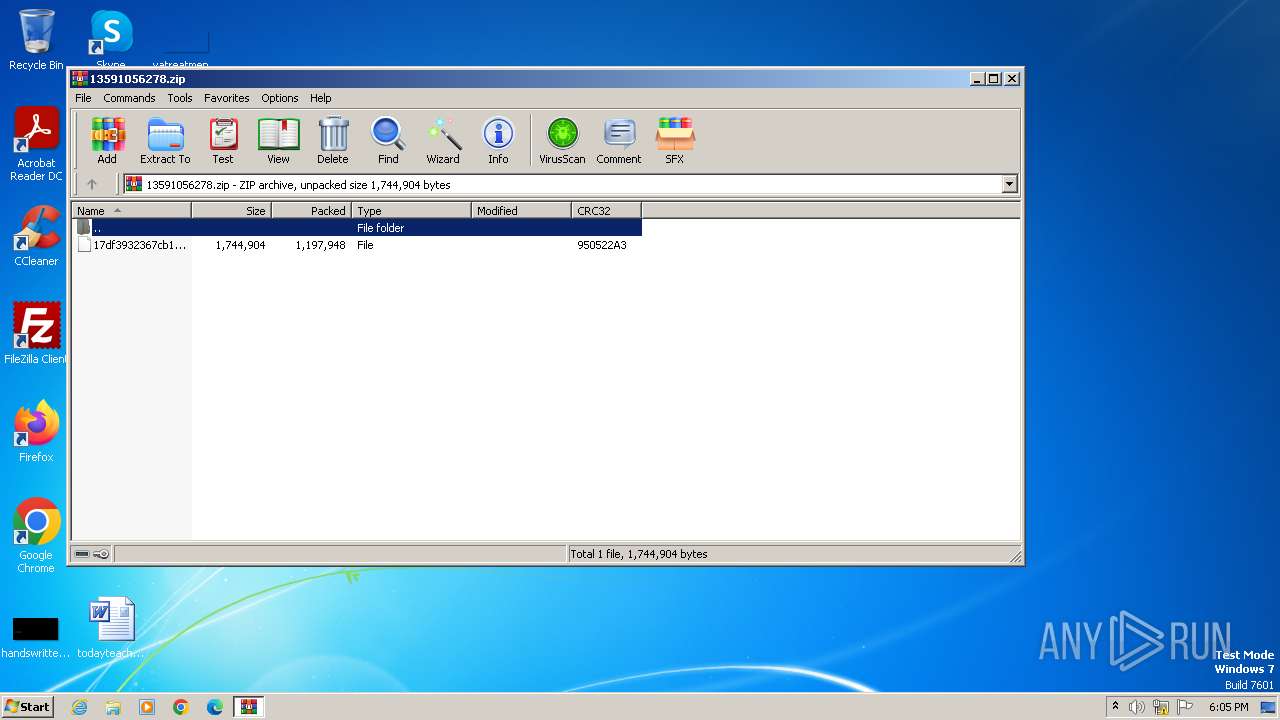
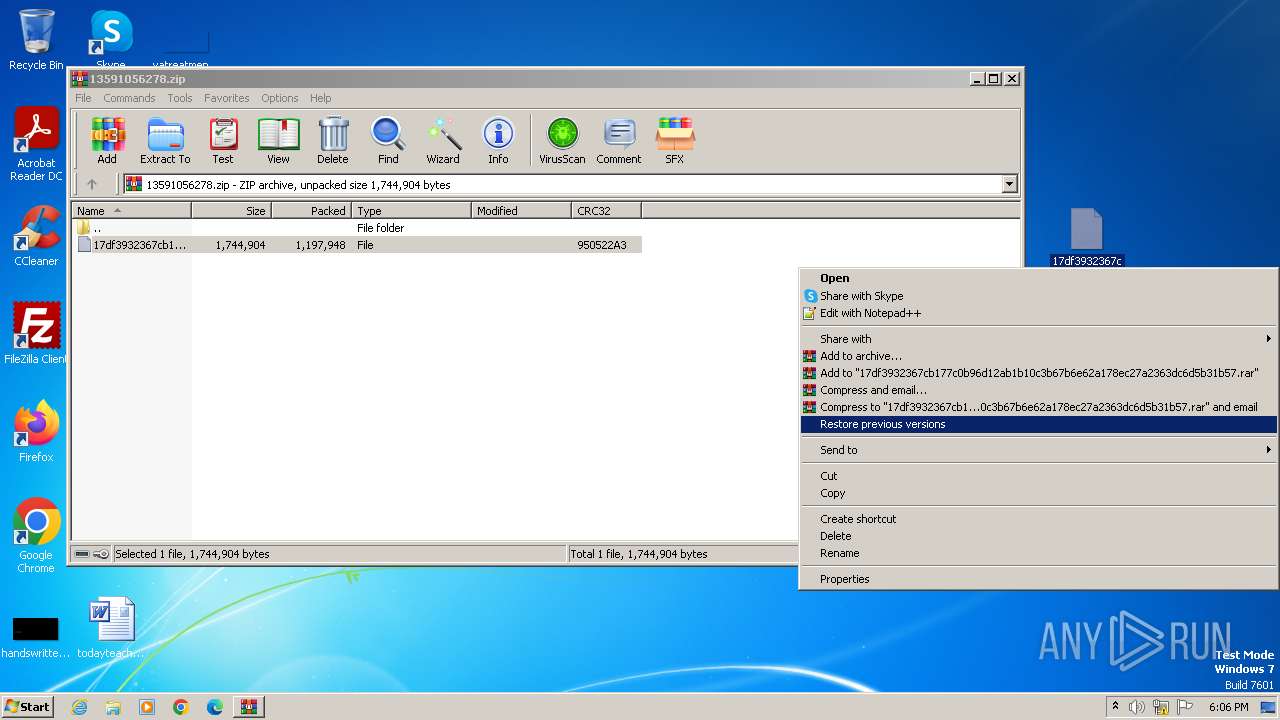
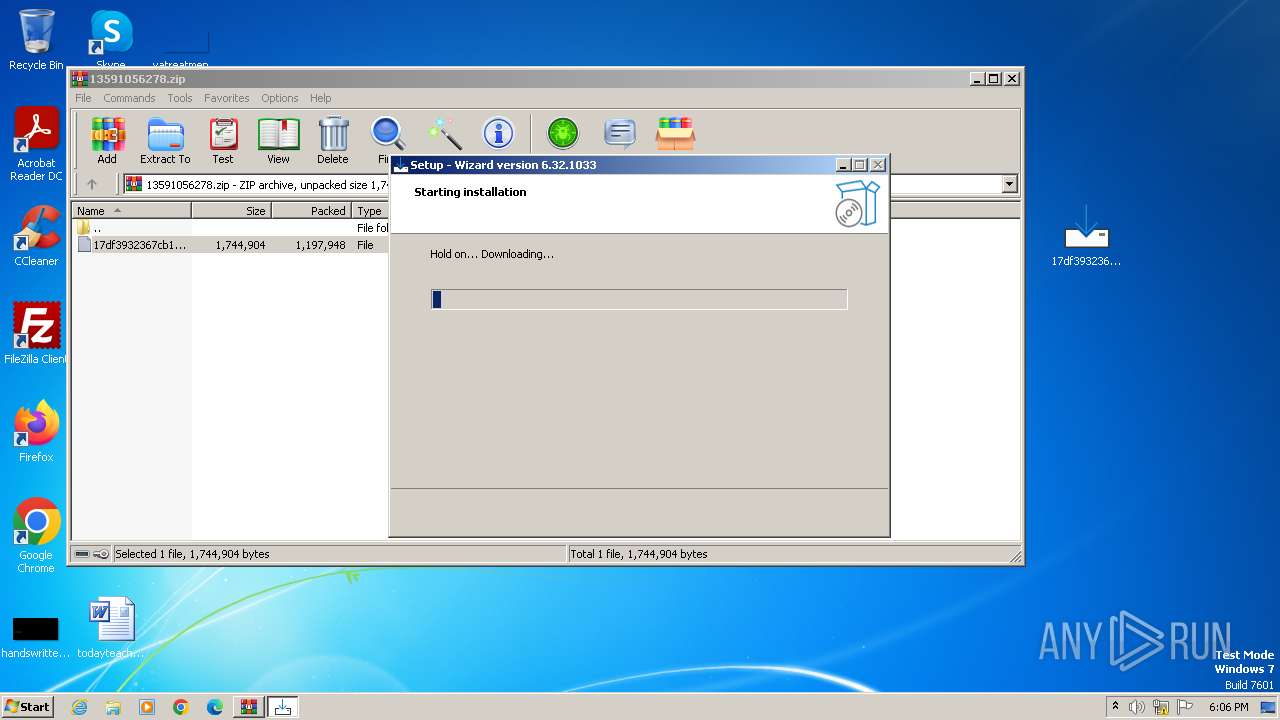
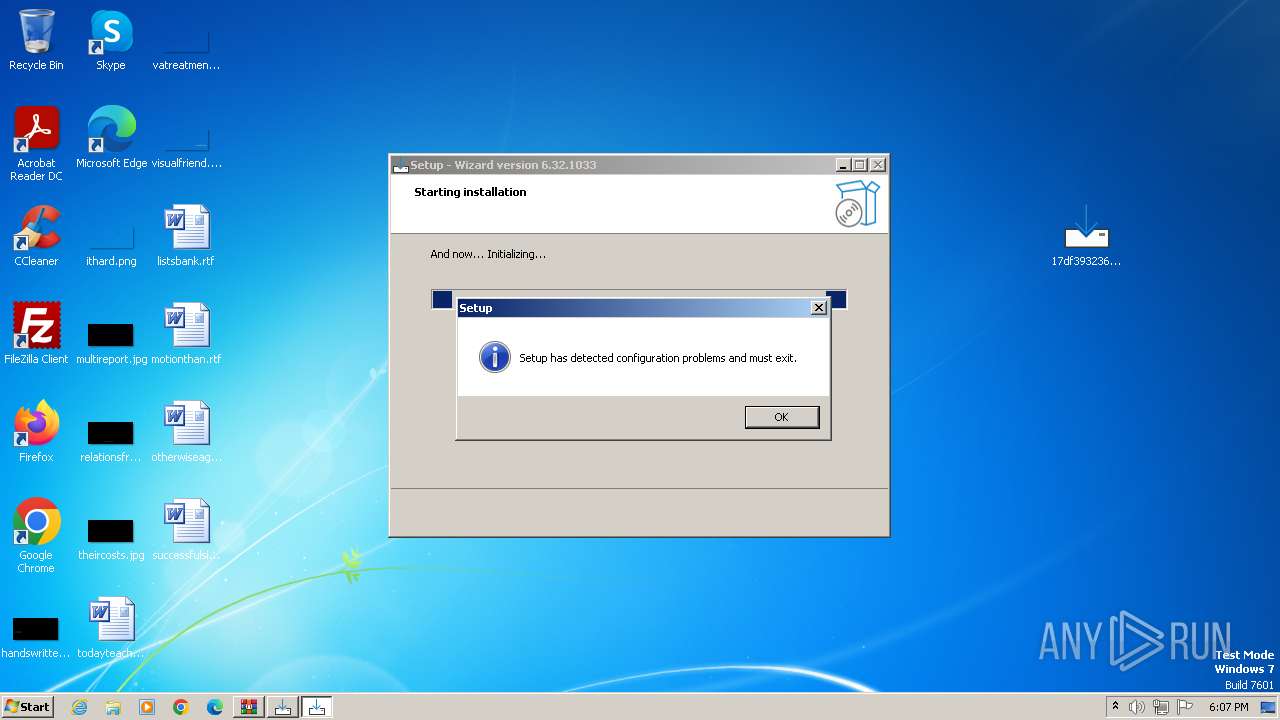
| File name: | 13591056278.zip |
| Full analysis: | https://app.any.run/tasks/75cce01d-5140-4406-abb5-397145bdc672 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2023, 18:05:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 90551487DA12042EC8648DAB41AA607D |
| SHA1: | C84D0B9AB199E47634F8582D92B7EA030FF6F510 |
| SHA256: | 4E2D4AD0D8FB41D7394216D300647A1193FCD6C517D407418FA6F860BC923DCF |
| SSDEEP: | 49152:5O9IGDWOIUNddX4tLeEK7RM2U6REZg7slyleTJYVvQYOfMZd5BwdjL0vPCZH0Tqq:54D8DFGVM/SwylqJYZCSIjL86ZHyqCAy |
MALICIOUS
Drops the executable file immediately after the start
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 1360)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 3468)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- file_.exe (PID: 3168)
- file_.tmp (PID: 2536)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 3360)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 4016)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
- file_.exe (PID: 1064)
- file_.tmp (PID: 3736)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3048)
Reads the Windows owner or organization settings
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- file_.tmp (PID: 2536)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
- file_.tmp (PID: 3736)
Reads settings of System Certificates
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- file_.tmp (PID: 2536)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
- file_.tmp (PID: 3736)
Reads the Internet Settings
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3048)
Manual execution by a user
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 1360)
- wmpnscfg.exe (PID: 3528)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 3360)
Checks supported languages
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3216)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 3468)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 1360)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- file_.exe (PID: 3168)
- file_.tmp (PID: 2536)
- wmpnscfg.exe (PID: 3528)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 3360)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 2224)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
- file_.exe (PID: 1064)
- file_.tmp (PID: 3736)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 4016)
Reads the computer name
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3216)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- file_.tmp (PID: 2536)
- wmpnscfg.exe (PID: 3528)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
- file_.tmp (PID: 3736)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 2224)
Create files in a temporary directory
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 1360)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 3468)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- file_.tmp (PID: 2536)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 3360)
- file_.exe (PID: 3168)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
- file_.exe (PID: 1064)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe (PID: 4016)
- file_.tmp (PID: 3736)
Reads the machine GUID from the registry
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 1696)
- file_.tmp (PID: 2536)
- 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp (PID: 3608)
- file_.tmp (PID: 3736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x950522a3 |
| ZipCompressedSize: | 1197948 |
| ZipUncompressedSize: | 1744904 |
| ZipFileName: | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57 |
Total processes
58
Monitored processes
15
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1064 | "C:\Users\admin\AppData\Local\Temp\is-FDI1I.tmp\file_.exe" /LANG=en /NA=Rh85hR64 | C:\Users\admin\AppData\Local\Temp\is-FDI1I.tmp\file_.exe | — | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | |||||||||||
User: admin Company: Integrity Level: HIGH Description: Exit code: 1 Version: 3.12.1003 Modules
| |||||||||||||||
| 1360 | "C:\Users\admin\Desktop\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe" | C:\Users\admin\Desktop\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe | — | explorer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Wizard Exit code: 0 Version: 6.32.1033 Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\AppData\Local\Temp\is-C1RCS.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp" /SL5="$E0220,832512,832512,C:\Users\admin\Desktop\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe" /SPAWNWND=$130180 /NOTIFYWND=$1501AC | C:\Users\admin\AppData\Local\Temp\is-C1RCS.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2224 | "C:\Users\admin\AppData\Local\Temp\is-AUK4V.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp" /SL5="$16012E,832512,832512,C:\Users\admin\Desktop\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe" | C:\Users\admin\AppData\Local\Temp\is-AUK4V.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | — | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2536 | "C:\Users\admin\AppData\Local\Temp\is-DRNPR.tmp\file_.tmp" /SL5="$16015C,1611420,832512,C:\Users\admin\AppData\Local\Temp\is-HT283.tmp\file_.exe" /LANG=en /NA=Rh85hR64 | C:\Users\admin\AppData\Local\Temp\is-DRNPR.tmp\file_.tmp | file_.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2620 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb3048.14260\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57 | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\13591056278.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3168 | "C:\Users\admin\AppData\Local\Temp\is-HT283.tmp\file_.exe" /LANG=en /NA=Rh85hR64 | C:\Users\admin\AppData\Local\Temp\is-HT283.tmp\file_.exe | — | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | |||||||||||
User: admin Company: Integrity Level: HIGH Description: Exit code: 1 Version: 3.12.1003 Modules
| |||||||||||||||
| 3216 | "C:\Users\admin\AppData\Local\Temp\is-H5OOB.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp" /SL5="$1501AC,832512,832512,C:\Users\admin\Desktop\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe" | C:\Users\admin\AppData\Local\Temp\is-H5OOB.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | — | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3360 | "C:\Users\admin\Desktop\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe" | C:\Users\admin\Desktop\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe | — | explorer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Wizard Exit code: 0 Version: 6.32.1033 Modules
| |||||||||||||||
Total events
13 149
Read events
13 066
Write events
66
Delete events
17
Modification events
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
16
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3048.15577\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57 | executable | |
MD5:B0EEE66BF0EB45069FB89593120BD046 | SHA256:17DF3932367CB177C0B96D12AB1B10C3B67B6E62A178EC27A2363DC6D5B31B57 | |||
| 3468 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe | C:\Users\admin\AppData\Local\Temp\is-C1RCS.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | executable | |
MD5:B4107A576702C64AEDC9838C2BF8D422 | SHA256:E74854263FF92F48C49E5C155BC0D76F1FCD9C7C7D1AE40D4D8407C724C86A87 | |||
| 1360 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.exe | C:\Users\admin\AppData\Local\Temp\is-H5OOB.tmp\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | executable | |
MD5:B4107A576702C64AEDC9838C2BF8D422 | SHA256:E74854263FF92F48C49E5C155BC0D76F1FCD9C7C7D1AE40D4D8407C724C86A87 | |||
| 2536 | file_.tmp | C:\Users\admin\AppData\Local\Temp\is-LTK44.tmp\Helper.dll | executable | |
MD5:4EB0347E66FA465F602E52C03E5C0B4B | SHA256:C73E53CBB7B98FEAFE27CC7DE8FDAD51DF438E2235E91891461C5123888F73CC | |||
| 3048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3048.14260\17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57 | executable | |
MD5:B0EEE66BF0EB45069FB89593120BD046 | SHA256:17DF3932367CB177C0B96D12AB1B10C3B67B6E62A178EC27A2363DC6D5B31B57 | |||
| 1696 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | C:\Users\admin\AppData\Local\Temp\is-HT283.tmp\is-6420L.tmp | executable | |
MD5:B734A2B5F197CF37D013B6CB2EEA1743 | SHA256:5BA0C35E1989112364A6A7AF54AECEDF6BC614C67B8FCCE3CDFE6B4F734E6117 | |||
| 1696 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | C:\Users\admin\AppData\Local\Temp\is-HT283.tmp\file_.exe | executable | |
MD5:B734A2B5F197CF37D013B6CB2EEA1743 | SHA256:5BA0C35E1989112364A6A7AF54AECEDF6BC614C67B8FCCE3CDFE6B4F734E6117 | |||
| 3168 | file_.exe | C:\Users\admin\AppData\Local\Temp\is-DRNPR.tmp\file_.tmp | executable | |
MD5:1968CA694D9B1FB54EDF2A8380F1E0FE | SHA256:43D461412CDCF836D6304848DD621B541193B0021AA29385DA4E0C50DC84DF46 | |||
| 2536 | file_.tmp | C:\Users\admin\AppData\Local\Temp\is-LTK44.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 3608 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | C:\Users\admin\AppData\Local\Temp\is-FDI1I.tmp\file_.exe | executable | |
MD5:B734A2B5F197CF37D013B6CB2EEA1743 | SHA256:5BA0C35E1989112364A6A7AF54AECEDF6BC614C67B8FCCE3CDFE6B4F734E6117 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
9
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1696 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | 18.66.212.29:443 | dy5wf71dvafjw.cloudfront.net | — | US | unknown |
1696 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | 18.66.212.18:443 | dy5wf71dvafjw.cloudfront.net | — | US | unknown |
2536 | file_.tmp | 18.66.188.106:443 | d1i3c1dyhuowa7.cloudfront.net | AMAZON-02 | US | whitelisted |
3608 | 17df3932367cb177c0b96d12ab1b10c3b67b6e62a178ec27a2363dc6d5b31b57.tmp | 18.66.212.29:443 | dy5wf71dvafjw.cloudfront.net | — | US | unknown |
3736 | file_.tmp | 18.66.188.106:443 | d1i3c1dyhuowa7.cloudfront.net | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dy5wf71dvafjw.cloudfront.net |
| unknown |
d1i3c1dyhuowa7.cloudfront.net |
| unknown |