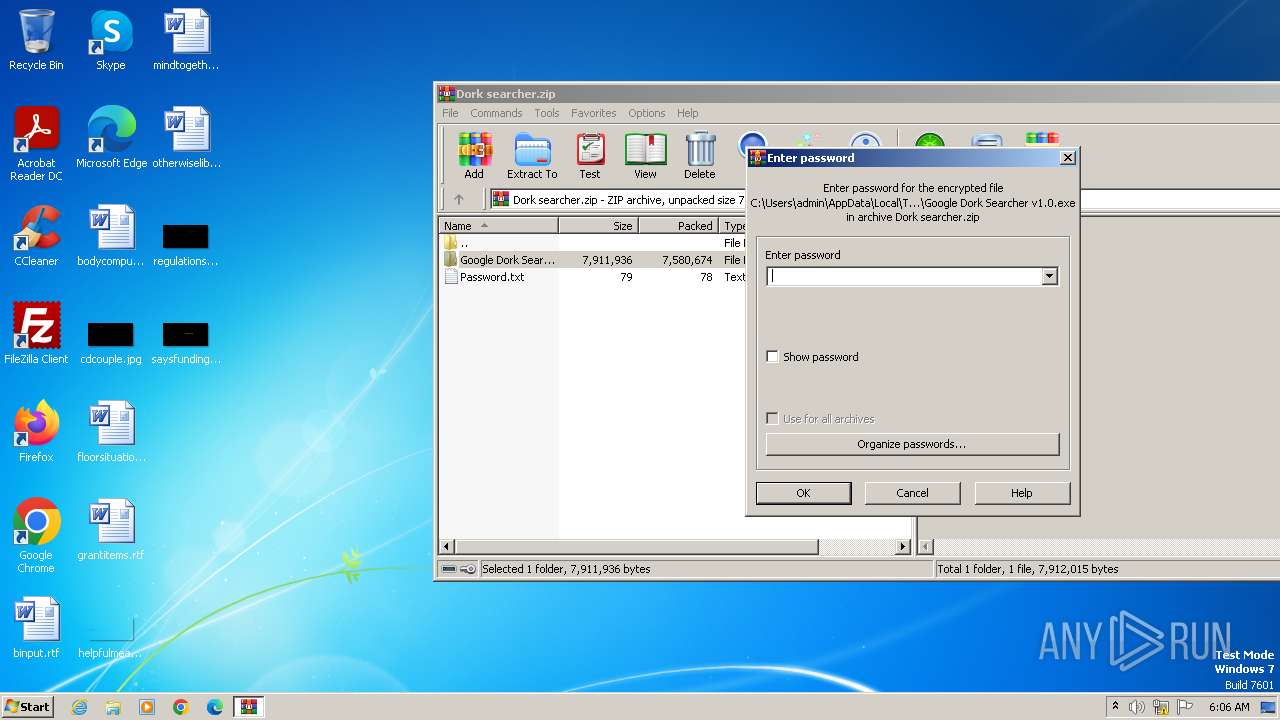
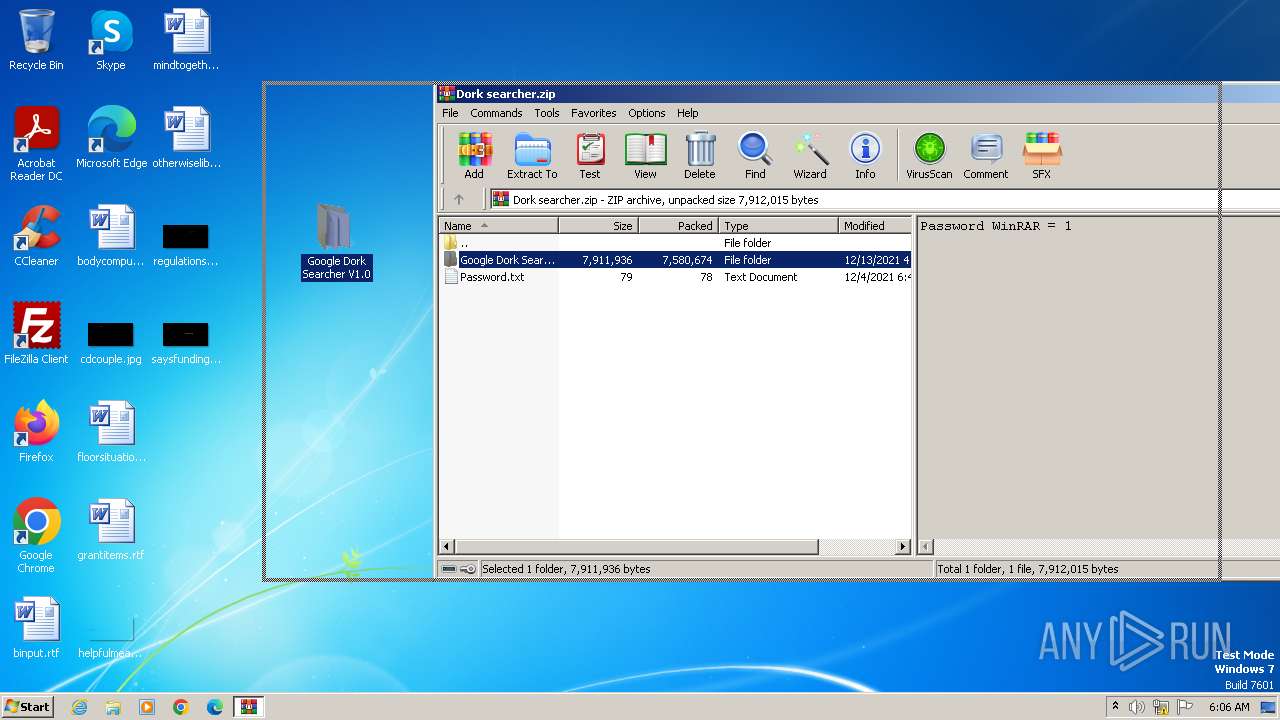
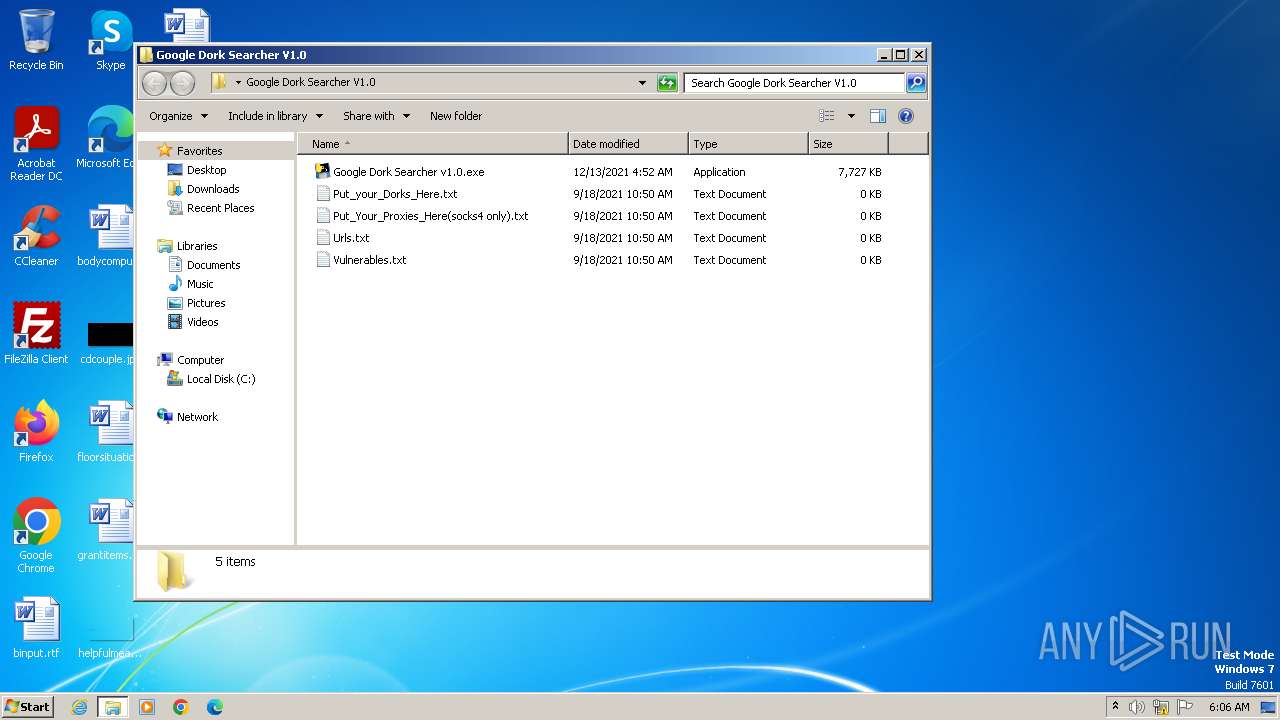
| File name: | Dork searcher.zip |
| Full analysis: | https://app.any.run/tasks/bbccaa26-779b-49f2-9ebe-43f973284bf5 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2024, 05:05:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 0C833420B26C649481F0FFF10CCC2BF6 |
| SHA1: | 2D35B9A6B167C0385EA297AB930A4A9FEABFF3A3 |
| SHA256: | 4E2C197F05671B57CF97DB3E5DB9374472430F412BE968DB7B5C626ABA31D712 |
| SSDEEP: | 98304:bkKj5JGnFBfcTzgqvnTR1/Sa8+sl8F3tmZazPtah+iOKx/iPJ4WrYAQzZ9hvac6T:nbJ5xe+w7UlH |
MALICIOUS
Drops the executable file immediately after the start
- Google Dork Searcher v1.0.exe (PID: 2108)
- Setup.exe (PID: 1064)
- svchost.exe (PID: 2304)
Changes the autorun value in the registry
- Setup.exe (PID: 1064)
- svchost.exe (PID: 2304)
- Setup.exe (PID: 2092)
REVENGERAT has been detected (YARA)
- explorer.exe (PID: 1488)
SUSPICIOUS
Executable content was dropped or overwritten
- Google Dork Searcher v1.0.exe (PID: 2108)
- Setup.exe (PID: 1064)
- svchost.exe (PID: 2304)
Reads the Internet Settings
- Google Dork Searcher v1.0.exe (PID: 2108)
- Setup.exe (PID: 1064)
- explorer.exe (PID: 1488)
- Google Dork Searcher v1.0.exe (PID: 2008)
- Setup.exe (PID: 2092)
- svchost.exe (PID: 1788)
- svchost.exe (PID: 2304)
Reads security settings of Internet Explorer
- Google Dork Searcher v1.0.exe (PID: 2108)
- svchost.exe (PID: 2304)
- Setup.exe (PID: 2092)
- Google Dork Searcher v1.0.exe (PID: 2008)
- Setup.exe (PID: 1064)
The process creates files with name similar to system file names
- Setup.exe (PID: 1064)
- svchost.exe (PID: 2304)
Process drops legitimate windows executable
- svchost.exe (PID: 2304)
Reads settings of System Certificates
- svchost.exe (PID: 2304)
- explorer.exe (PID: 1488)
Connects to unusual port
- explorer.exe (PID: 1488)
INFO
Create files in a temporary directory
- Google Dork Searcher v1.0.exe (PID: 2108)
- svchost.exe (PID: 2304)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3988)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3988)
Checks supported languages
- Google Dork Searcher v1.0.exe (PID: 2108)
- Setup.exe (PID: 1064)
- Setup.exe (PID: 2116)
- svchost.exe (PID: 2304)
- explorer.exe (PID: 1488)
- wmpnscfg.exe (PID: 284)
- Google Dork Searcher v1.0.exe (PID: 2008)
- Setup.exe (PID: 2092)
- svchost.exe (PID: 1788)
Manual execution by a user
- Google Dork Searcher v1.0.exe (PID: 2108)
- wmpnscfg.exe (PID: 284)
- Google Dork Searcher v1.0.exe (PID: 2008)
Creates files or folders in the user directory
- Setup.exe (PID: 1064)
- svchost.exe (PID: 2304)
Reads the computer name
- Google Dork Searcher v1.0.exe (PID: 2108)
- Setup.exe (PID: 2116)
- Setup.exe (PID: 1064)
- svchost.exe (PID: 2304)
- explorer.exe (PID: 1488)
- wmpnscfg.exe (PID: 284)
- Google Dork Searcher v1.0.exe (PID: 2008)
- Setup.exe (PID: 2092)
- svchost.exe (PID: 1788)
Reads the machine GUID from the registry
- Setup.exe (PID: 2116)
- Google Dork Searcher v1.0.exe (PID: 2108)
- Setup.exe (PID: 1064)
- svchost.exe (PID: 2304)
- explorer.exe (PID: 1488)
- Google Dork Searcher v1.0.exe (PID: 2008)
- Setup.exe (PID: 2092)
- svchost.exe (PID: 1788)
Reads the software policy settings
- svchost.exe (PID: 2304)
- explorer.exe (PID: 1488)
Reads Environment values
- explorer.exe (PID: 1488)
- svchost.exe (PID: 1788)
- svchost.exe (PID: 2304)
Disables trace logs
- explorer.exe (PID: 1488)
- svchost.exe (PID: 1788)
- svchost.exe (PID: 2304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RevengeRat
(PID) Process(1488) explorer.exe
C2 (1)amazon.capeturk.com
Ports (1)100
BotnetNyanCatRevenge
Options
Mutexeea5a83186824927836
KeyRevenge-RAT
Splitter!@#%^NYAN#!@$
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:12:13 11:54:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Google Dork Searcher V1.0/ |
Total processes
44
Monitored processes
10
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1064 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | Google Dork Searcher v1.0.exe | ||||||||||||
User: admin Company: Intel Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7800.8900 Modules
RevengeRat(PID) Process(1488) explorer.exe C2 (1)amazon.capeturk.com Ports (1)100 BotnetNyanCatRevenge Options Mutexeea5a83186824927836 KeyRevenge-RAT Splitter!@#%^NYAN#!@$ | |||||||||||||||
| 1788 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | Setup.exe | ||||||||||||
User: admin Company: Intel Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 8.1.1.7900 Modules
| |||||||||||||||
| 2008 | "C:\Users\admin\Desktop\Google Dork Searcher V1.0\Google Dork Searcher v1.0.exe" | C:\Users\admin\Desktop\Google Dork Searcher V1.0\Google Dork Searcher v1.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2092 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | Google Dork Searcher v1.0.exe | ||||||||||||
User: admin Company: Intel Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2108 | "C:\Users\admin\Desktop\Google Dork Searcher V1.0\Google Dork Searcher v1.0.exe" | C:\Users\admin\Desktop\Google Dork Searcher V1.0\Google Dork Searcher v1.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2116 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | Google Dork Searcher v1.0.exe | |||||||||||
User: admin Company: Intel Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2304 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | Setup.exe | ||||||||||||
User: admin Company: Intel Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 8.1.1.7900 Modules
| |||||||||||||||
| 3988 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Dork searcher.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
26 383
Read events
26 255
Write events
128
Delete events
0
Modification events
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Dork searcher.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2304 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe | executable | |
MD5:D298454882CAAC154FC9217FC7E90499 | SHA256:BADAA2312457F3D08CA1F72287989456F9E62D6B417AF6FB9B5E39CA1E8C8100 | |||
| 2304 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.zip | compressed | |
MD5:6A1458168AE6FD4A7F2229E20A3417D2 | SHA256:00B374182D46A617C25B04CFA294331DD496572762903D54BE9F9043AEBB5207 | |||
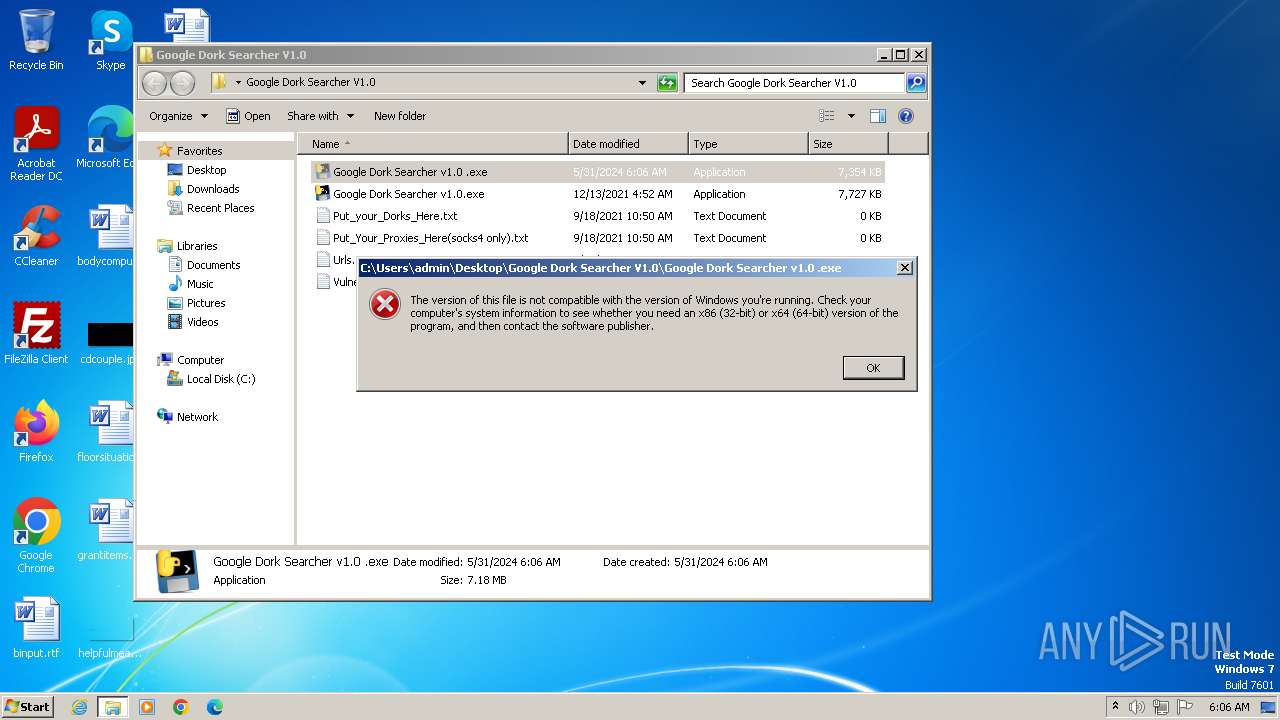
| 2108 | Google Dork Searcher v1.0.exe | C:\Users\admin\Desktop\Google Dork Searcher V1.0\Google Dork Searcher v1.0 .exe | executable | |
MD5:C715E67E7CB9AFB0752C219733742657 | SHA256:9085CED212F5EC31BD648F397B57B1D3202DB0EF990D4ECAA31D4A9A21633E5C | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3988.29020\Google Dork Searcher V1.0\Google Dork Searcher v1.0.exe | executable | |
MD5:7C0E13345130B46CD0A38D0EFC96149F | SHA256:0E6B9B6397E7F450226BBC08B74AFA0344E06D630396D96FA3C0F267F3CD1147 | |||
| 1064 | Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | executable | |
MD5:C4E4407B5FCF49586DDD5D5573AE4B95 | SHA256:8F1E6EB0269FBE449678CE4863D494FDA78BC648F27AD1C129270575EFCE4F7A | |||
| 1064 | Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.zip | compressed | |
MD5:5F71FAD242AC5E7D2AEB52225E008A06 | SHA256:7567DF4EB56966FD92876C3CCC4E73661AE8E22663BF801AB1EB0C13C715A051 | |||
| 2108 | Google Dork Searcher v1.0.exe | C:\Users\admin\AppData\Local\Temp\Setup.exe | executable | |
MD5:FA0B327ABD82686BB9D676A30FA89B46 | SHA256:D01728070486E1ABBF024DB0EEEACF232E02FE326C4C0B762AF73F728FC9392D | |||
| 2304 | svchost.exe | C:\Users\admin\AppData\Local\Temp\explorer.txt | text | |
MD5:3448CA7C547444156EF52D03A8402C29 | SHA256:27FE26C96B6987106A6CE93D8A001CEF5B8F9C8BF6AD7B9CB6B95A5DEE7B9672 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
15
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1788 | svchost.exe | HEAD | 200 | 107.180.41.239:80 | http://capeturk.com/explorer.txt | unknown | — | — | unknown |
2304 | svchost.exe | GET | 200 | 107.180.41.239:80 | http://capeturk.com/explorer.txt | unknown | — | — | unknown |
2304 | svchost.exe | GET | 200 | 107.180.41.239:80 | http://capeturk.com/explorer.txt | unknown | — | — | unknown |
2304 | svchost.exe | HEAD | 200 | 107.180.41.239:80 | http://capeturk.com/explorer.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2304 | svchost.exe | 107.180.41.239:80 | capeturk.com | AS-26496-GO-DADDY-COM-LLC | US | unknown |
2304 | svchost.exe | 172.217.16.129:443 | aaaabbbb-1000.blogspot.com | GOOGLE | US | whitelisted |
1488 | explorer.exe | 172.217.16.129:443 | aaaabbbb-1000.blogspot.com | GOOGLE | US | whitelisted |
1488 | explorer.exe | 103.190.107.26:100 | amazon.capeturk.com | HTTVSERVER TECHNOLOGY COMPANY LIMITED | VN | unknown |
1788 | svchost.exe | 107.180.41.239:80 | capeturk.com | AS-26496-GO-DADDY-COM-LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
capeturk.com |
| whitelisted |
aaaabbbb-1000.blogspot.com |
| whitelisted |
amazon.capeturk.com |
| malicious |